Encapsulating MPLS in UDP draftxumplsinudp02 Xiaohu Xu Huawei

![Problem Statement (cont. ) n The existing method [RFC 5640] requires a change to Problem Statement (cont. ) n The existing method [RFC 5640] requires a change to](https://slidetodoc.com/presentation_image_h/37552e7ef92612c368843ceded42356b/image-3.jpg)


- Slides: 6

Encapsulating MPLS in UDP draft-xu-mpls-in-udp-02 Xiaohu Xu (Huawei) Marshall Eubanks (America. Free. TV) Lucy Yong (Huawei) Nischal Sheth (Juniper) Zhenbin Li (Huawei) Yongbing Fan (China Telecom) IETF 84, Vancouver www. huawei. com

Problem Statement n There are some MPLS-based L 2 VPN or L 3 VPN application scenarios where the underlying networks are IP enabled, rather than MPLS enabled (e. g. , multi-tenant cloud data center networks). p Moreover, load-balancing is much desirable in these scenarios (e. g. , to maximize the bisection bandwidth between servers within or across data centers). p However, since distinct customer traffic flows between a given PE pair would be encapsulated with the same IP/GRE tunnel as per normal operations, P routers (i. e. , core routers) could not achieve an ideal load-balancing for these tunneled traffic flows due to the lack of adequate entropy information. Page 2
![Problem Statement cont n The existing method RFC 5640 requires a change to Problem Statement (cont. ) n The existing method [RFC 5640] requires a change to](https://slidetodoc.com/presentation_image_h/37552e7ef92612c368843ceded42356b/image-3.jpg)
Problem Statement (cont. ) n The existing method [RFC 5640] requires a change to the data plane of core routers. p Core routers is required to be capable of performing hash calculation on the specific "load-balancing" field contained in the L 2 TPv 3 or GRE tunnel header. n Such requirement can not be met in some cases. p For example, some deployed core routers could only perform hash calculation on the five tuple of TCP/UDP packets or some fields in the IP header of non. TCP/UDP packets. Page 3

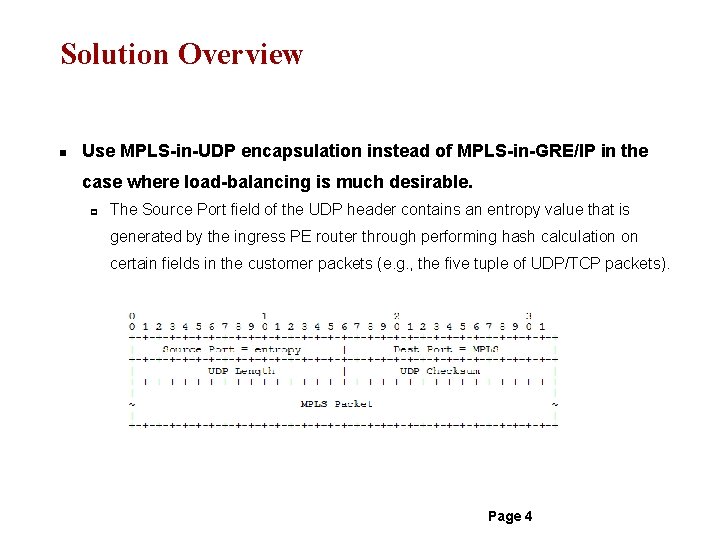
Solution Overview n Use MPLS-in-UDP encapsulation instead of MPLS-in-GRE/IP in the case where load-balancing is much desirable. p The Source Port field of the UDP header contains an entropy value that is generated by the ingress PE router through performing hash calculation on certain fields in the customer packets (e. g. , the five tuple of UDP/TCP packets). Page 4

Applicability n This approach is applicable to many technologies such as p L 3 VPN [RFC 4364] p L 2 VPN such as VPLS [RFC 4761, RFC 4762] and E-VPN [E-VPN]. p PWE 3 p 6 PE [RFC 4798] Page 5

Next-steps n Solicit more comments and suggestions. n WG adoption? Page 6