UDP Improving UDP Hole Punching Technique For Io




















- Slides: 36

改良UDP洞穿技術設計物聯網通訊: 以遠端門鈴監控系統為例 Improving UDP Hole Punching Technique For Io. T Communications: A Remote Door-bell Monitoring System 楊凱勝 指導教授:柯開維 博士 2017/6/29

Outline Introduction Background n Network Address Translator (NAT) n UDP Hole Punching Proposed Method Experiment and Result Analysis Conclusion Reference 1

Introduction 2

Introduction The IPv 4 address is not enough and IPv 6 is still not widespread. The necessary of IP address in Io. T environment. Improve the existed NAT traversal method – UDP hole punching. Make an smart home Io. T application to verify the usability of the proposed method. 3

Background 4

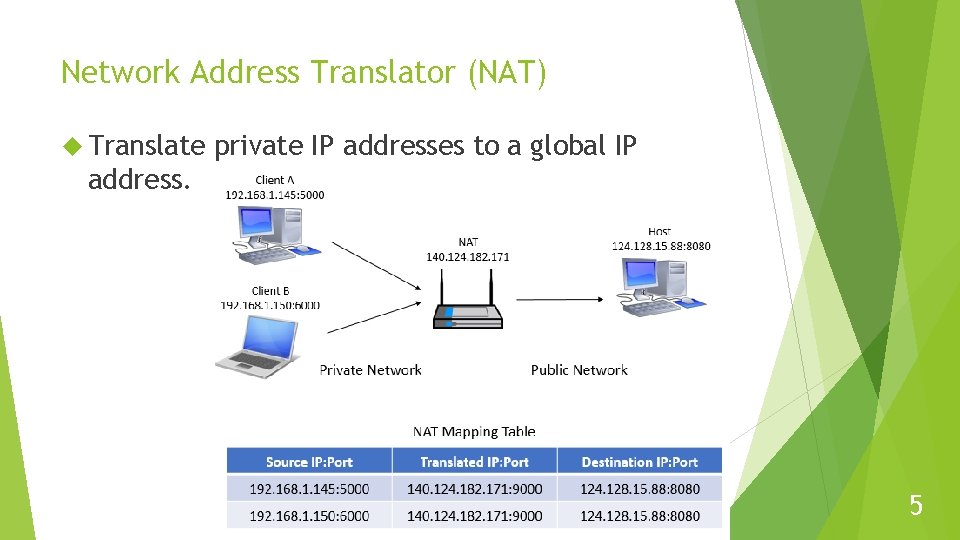
Network Address Translator (NAT) Translate private IP addresses to a global IP address. 5

Network Address Translator (NAT) In general, there are for types of NAT. l Full Cone NAT l Restricted Cone NAT l Port Restricted Cone NAT l Symmetric NAT 6

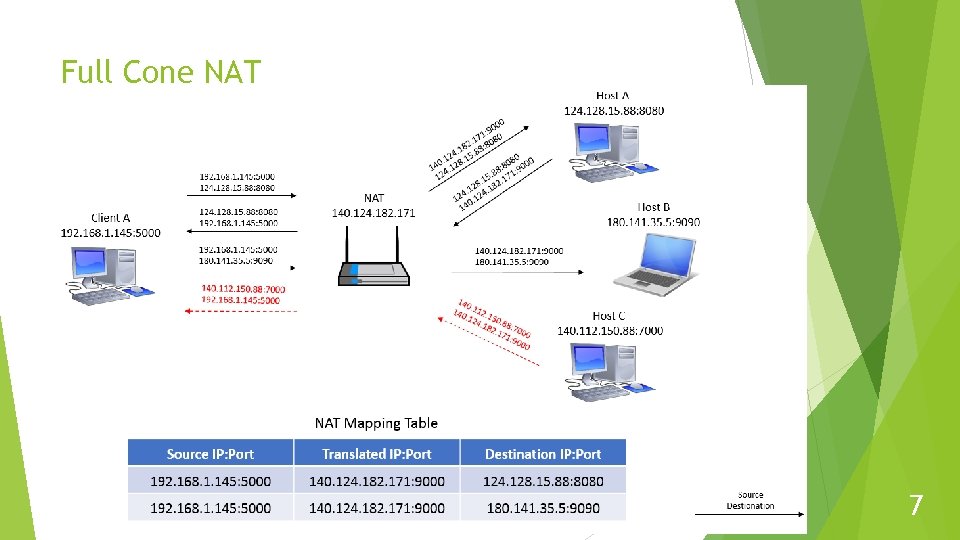
Full Cone NAT 7

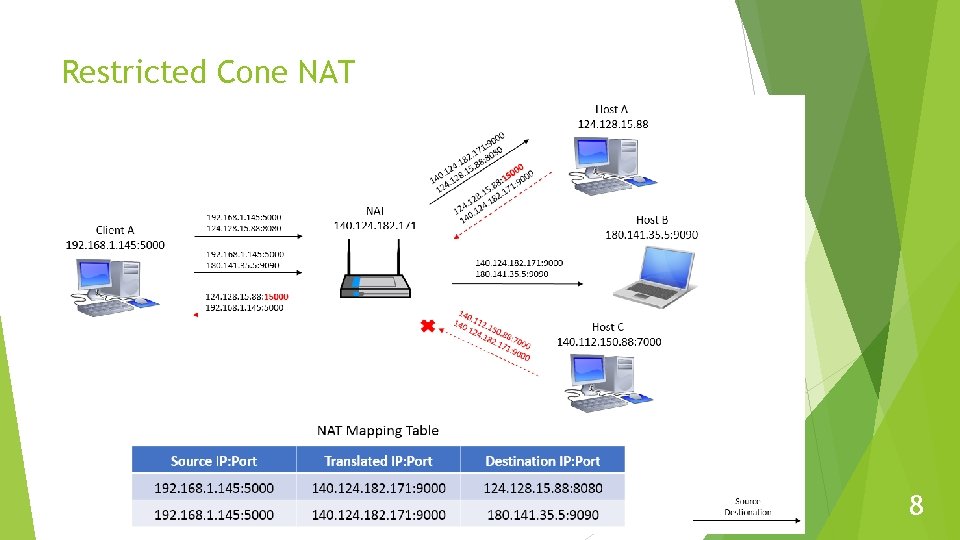
Restricted Cone NAT 8

Port Restricted Cone NAT 9

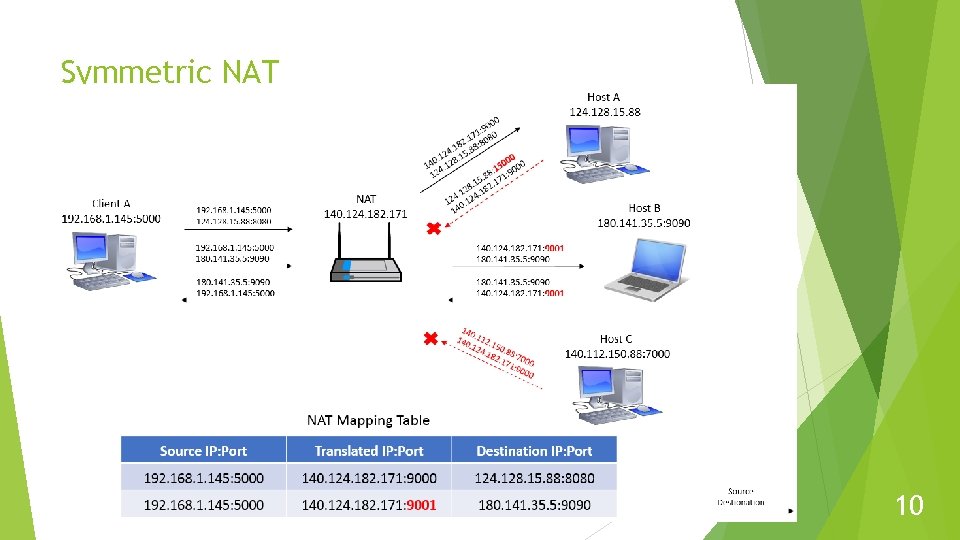
Symmetric NAT 10

UDP Hole Punching Technique 11

Proposed Method 12

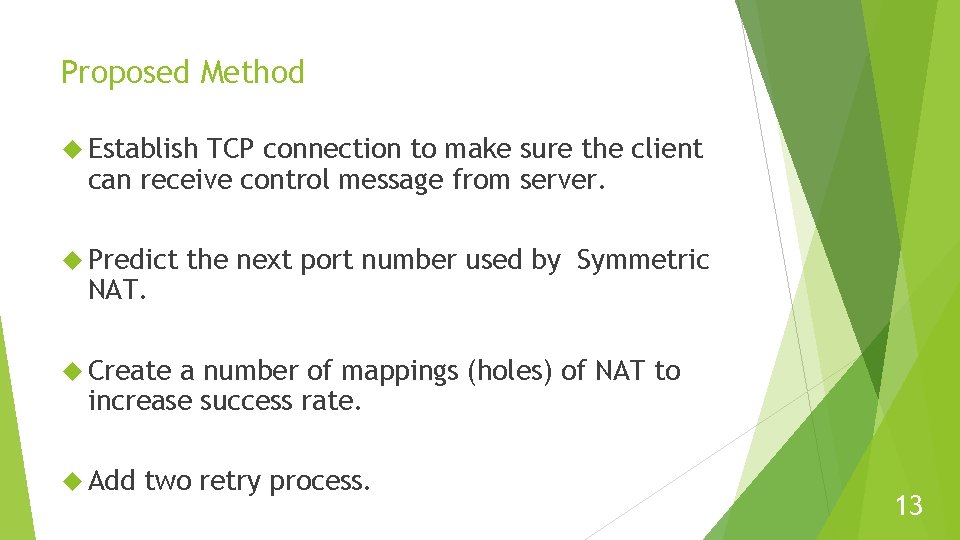
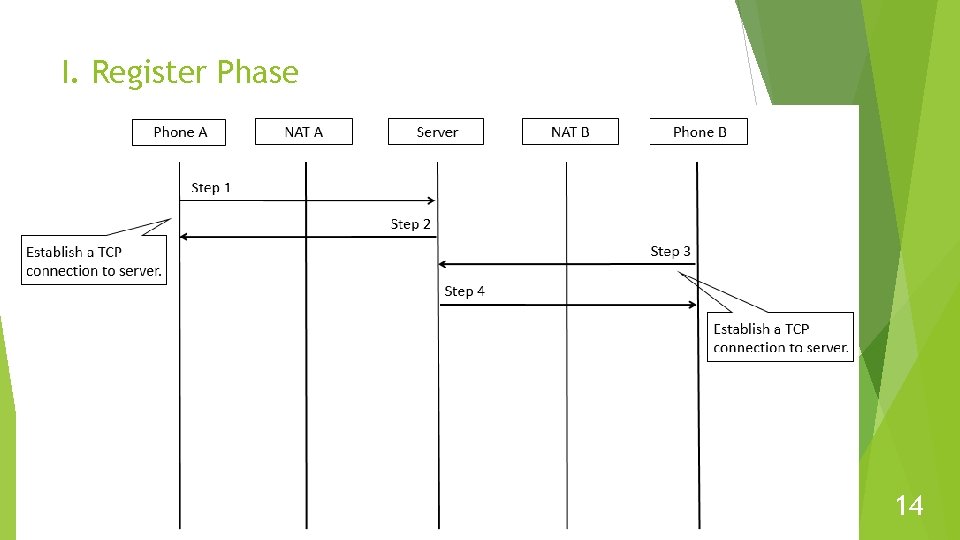
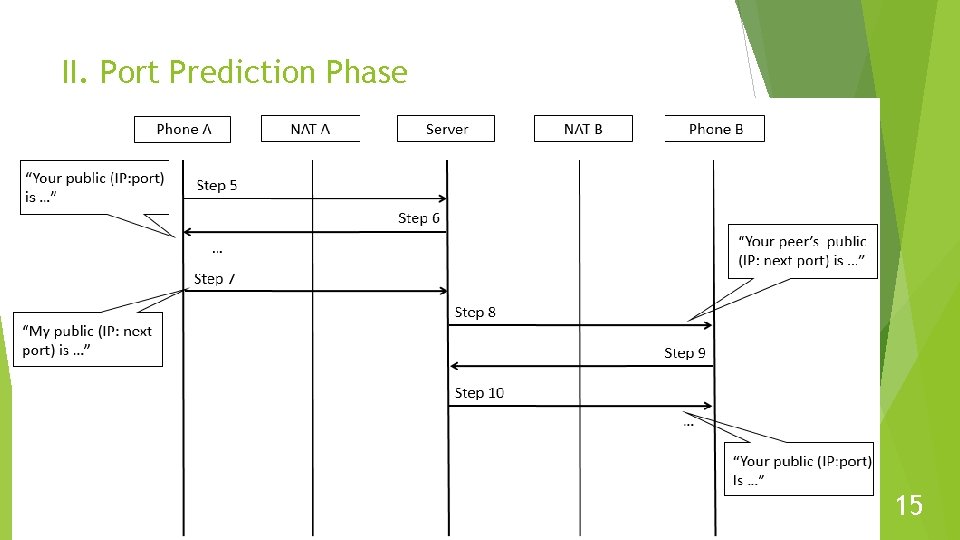
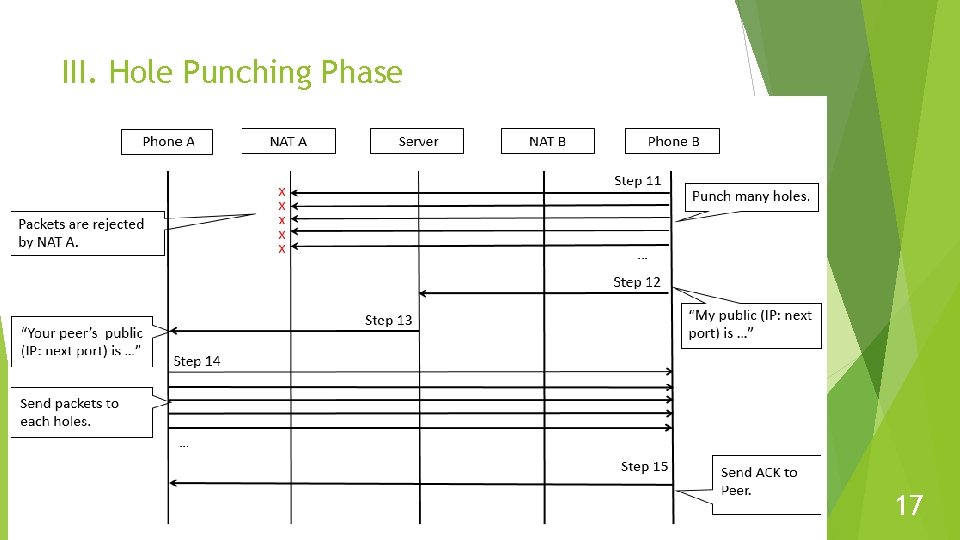
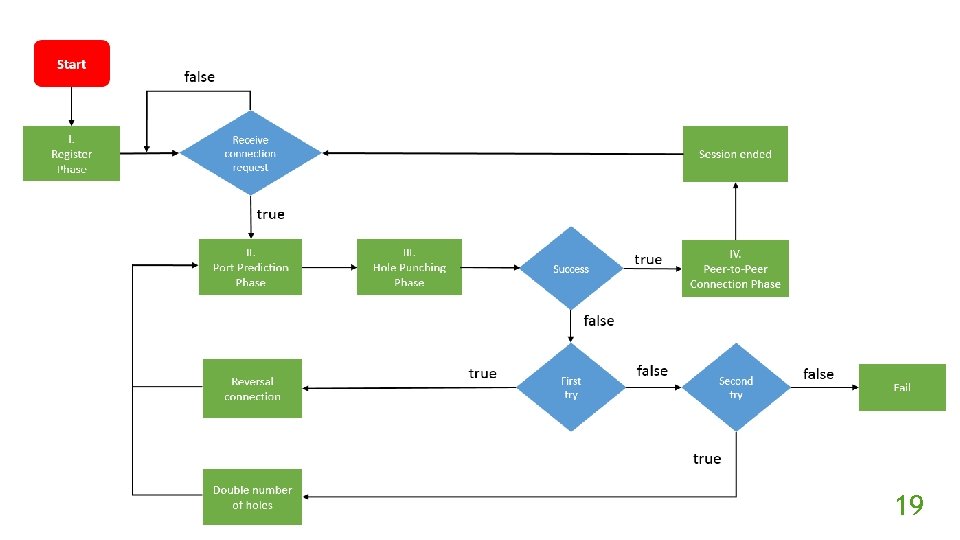
Proposed Method Establish TCP connection to make sure the client can receive control message from server. Predict NAT. the next port number used by Symmetric Create a number of mappings (holes) of NAT to increase success rate. Add two retry process. 13

I. Register Phase 14

II. Port Prediction Phase 15

16

III. Hole Punching Phase 17

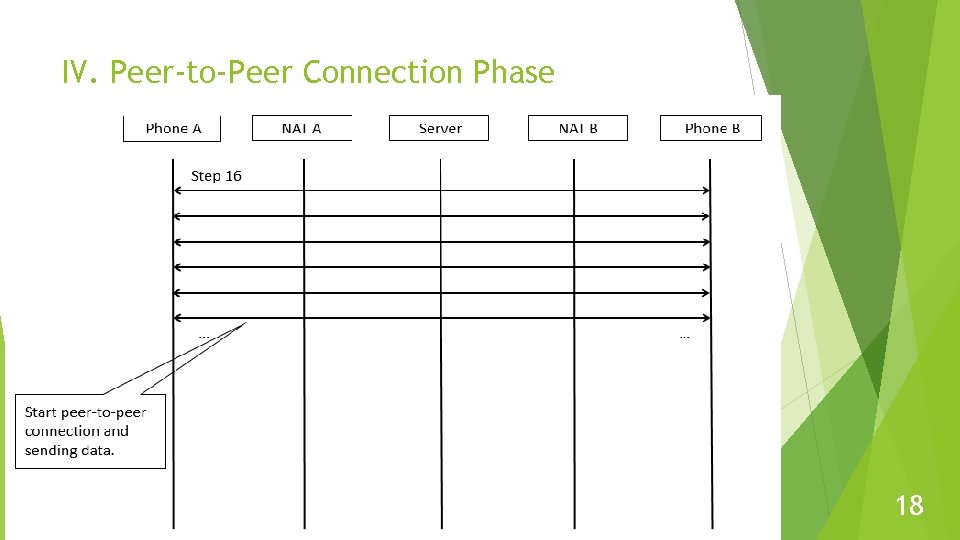
IV. Peer-to-Peer Connection Phase 18

19

Experiment and Result Analysis 20

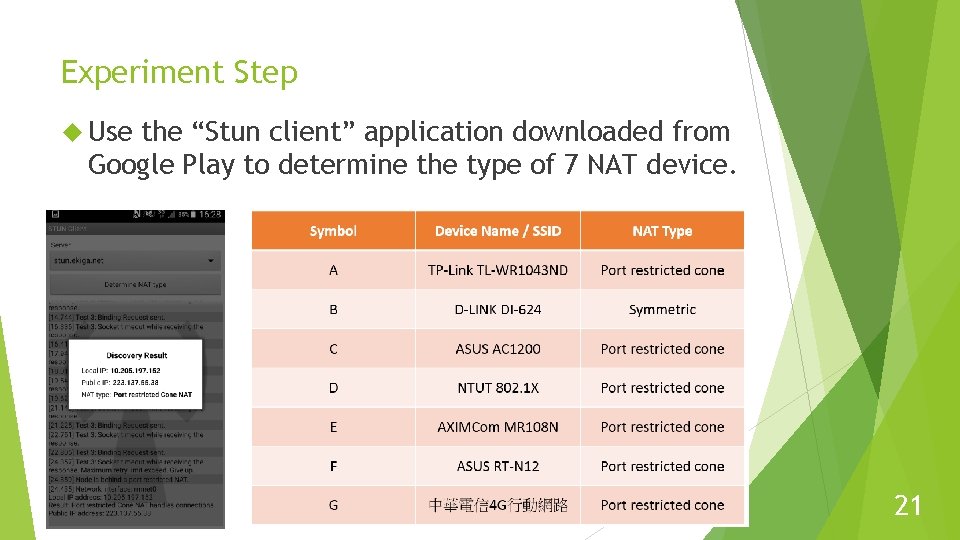
Experiment Step Use the “Stun client” application downloaded from Google Play to determine the type of 7 NAT device. 21

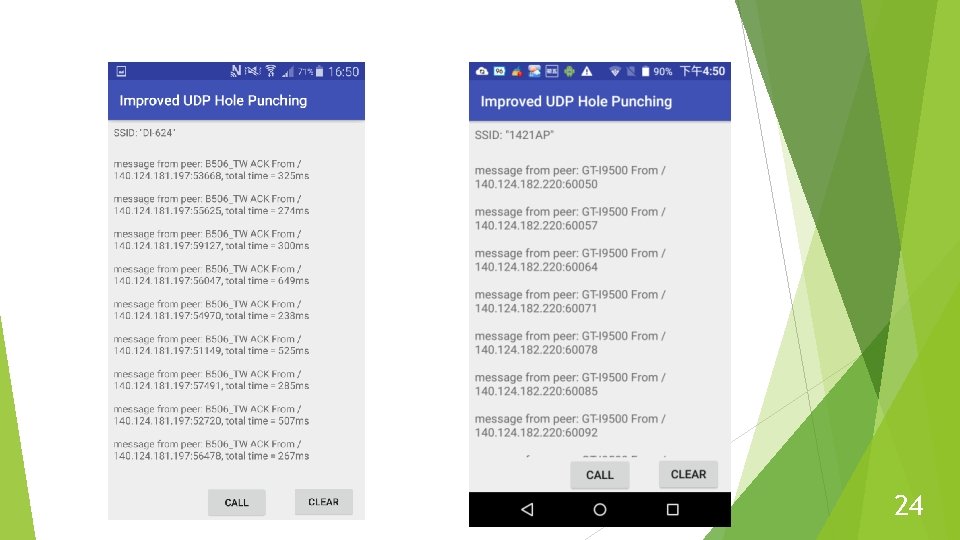
Experiment Step (con’t) Implement the original and proposed method. Use the methods 10 times per combinations of NAT devices to traverse the NAT. In each try, if two peers got packet from another, then success, otherwise fail. 22

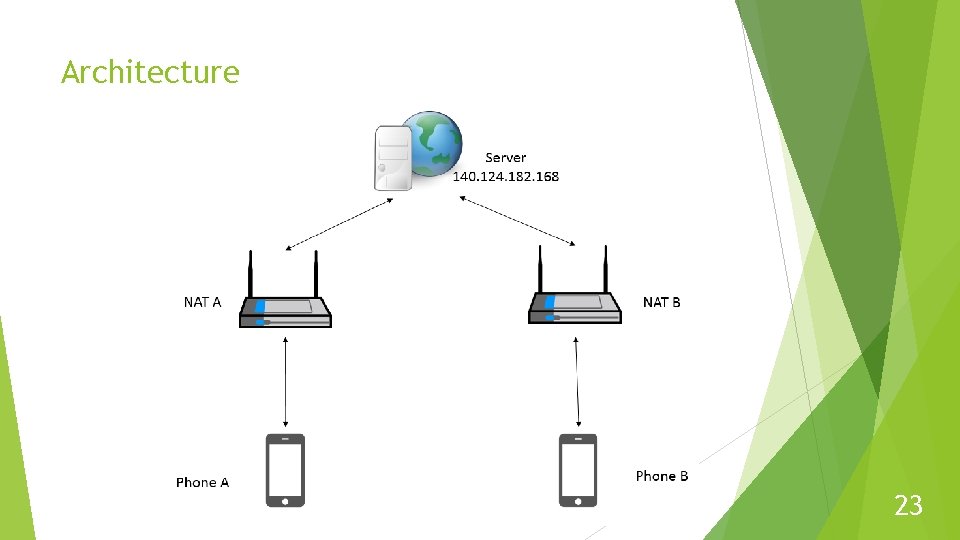
Architecture 23

24

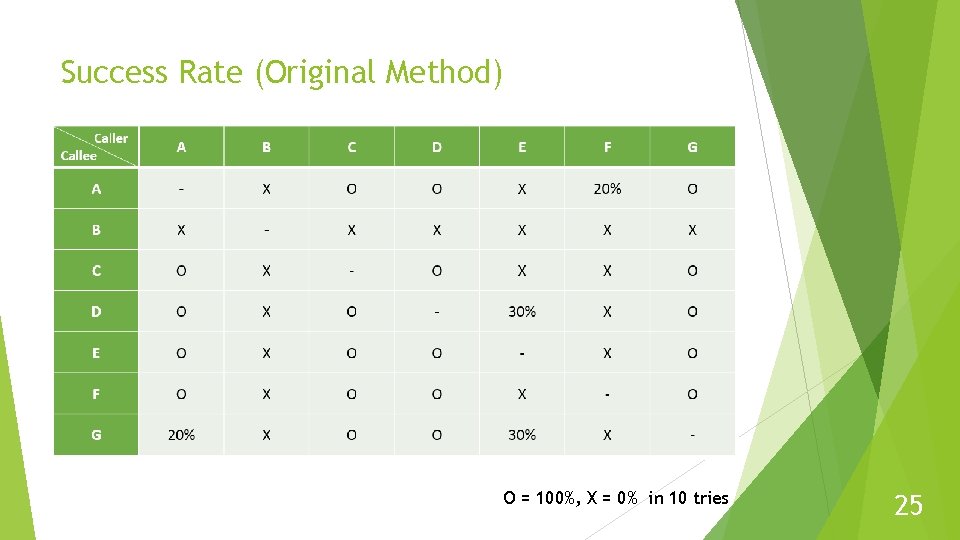
Success Rate (Original Method) O = 100%, X = 0% in 10 tries 25

Success Rate (Proposed Method) O = 100%, X = 0% in 10 tries 26

Time Cost (Original Method) 27

Time Cost (Proposed Method) 28

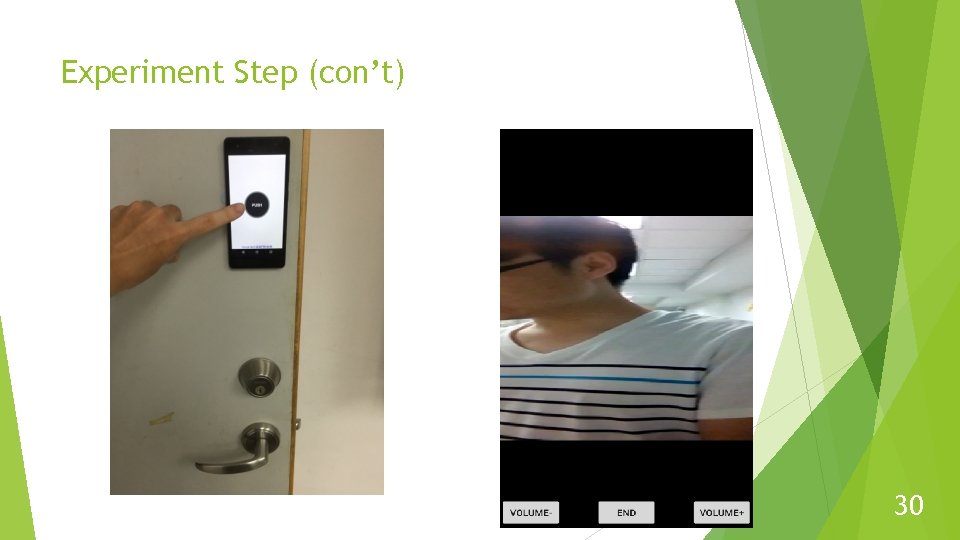
Experiment Step (con’t) A smart-home Io. T application to verify the usability of the proposed method – A remote doorbell monitoring system. Two android phones, one acts doorbell, the other one acts monitor. 29

Experiment Step (con’t) 30

Conclusion 31

Conclusion This proposed an improved UDP hole punching technique. The proposed method gets higher successful rate than the original one. Although it increases the cost of time, but the overhead can be ignored by human in most cases. The method can be applied to Android phone application and to smart home Io. T environment. 32

References P. Srisuresh, B. Ford, D. Kegel, “State of Peer-to-Peer (P 2 P) Communication across Network Address Translators (NATs), ” RFC- 5128, 2008 Wei, Y. , Yamada, D. , Yoshida, S. , Goto, S. , “A New Method for Symmetric NAT Traversal in UDP and TCP Network”, 2008 Kuan-Lin Chen, Shaw-Hwa Hwang, Cheng-Yu Yeh, "Symmetric NAT Traversal Method for Session Initial Protocol (SIP)", Applied Mechanics and Materials, pp. 2836 -2839, 2013. Ha Tran Thi Thu, Jaehyung Park, Yonggwan Won, Jinsul Kim, ”Combining STUN Protocol and UDP Hole Punching Technique for Peer-To-Peer Communication across Network Address Translation”, IT Convergence and Security (ICITCS) International Conference, 2014 33


Thanks. 35