TCPIP DNS 53tcp udp FTP 20 21tcp udp



















































- Slides: 61





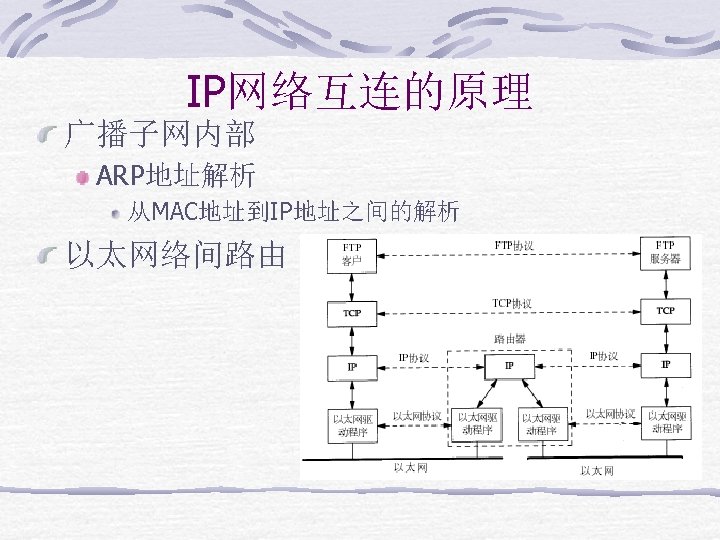
TCP/IP协议栈








常用的上层协议 DNS: 53/tcp, udp FTP: 20, 21/tcp, udp telnet: 23/tcp, udp HTTP: 80/tcp, udp NNTP: 119/tcp, udp SMTP: 25/tcp, udp POP 3: 110/tcp, udp 参考:IANA提供的port-numbers. txt

常用的网络 具 Netstat Ipconfig/ifconfig Ping Tracert ……









Linux内核 2. 2中的包的流向 output input sys_write() sys_read() sock_write() sock_read() inet_sendmsg() inet_recvmsg() tcp_v 4_sendmsg() tcp_do_sendmsg() tcp_send_skb() tcp_transmit_skb() tcp_recvmsg() tcp_v 4_recv() ip_queue_xmit() ip_output() ip_finish_output() dev_queue_xmit() hard_start_xmit() ip_local_deliver() ip_rcv() net_bh() Netif_rx() Block_input() ei_receive() ei_interrupt()

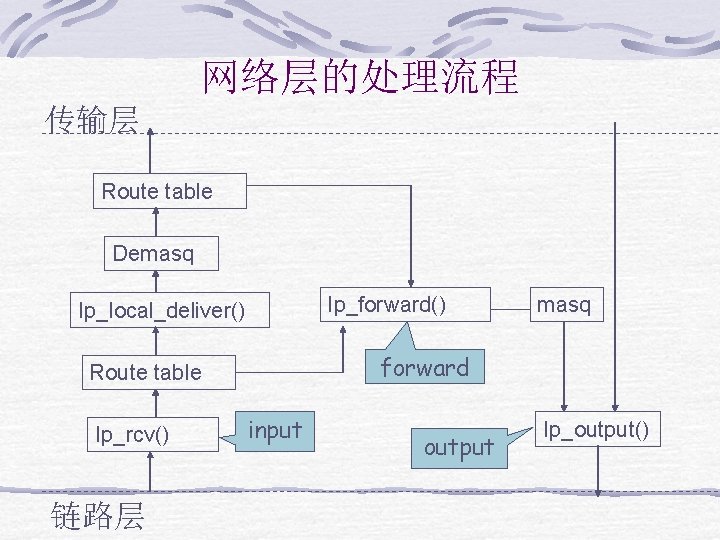
网络层的处理流程 传输层 Route table Demasq Ip_forward() Ip_local_deliver() forward Route table Ip_rcv() 链路层 masq input output Ip_output()

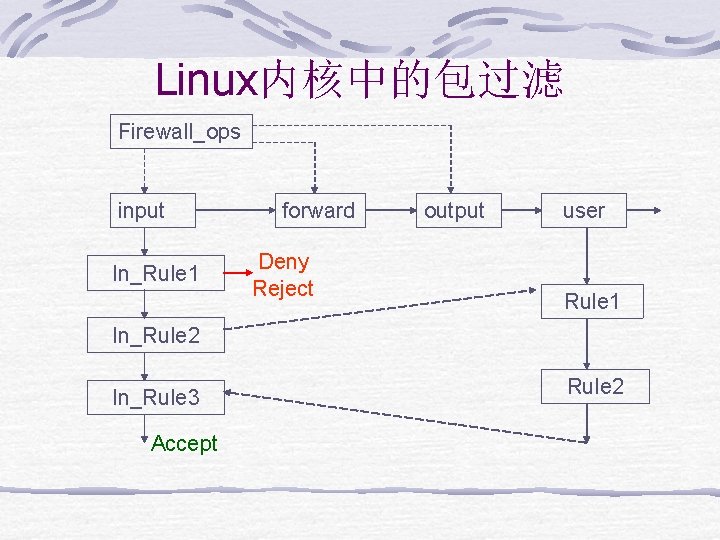
Linux内核中的包过滤 Firewall_ops input In_Rule 1 forward Deny Reject output user Rule 1 In_Rule 2 In_Rule 3 Accept Rule 2

Ipchains的用法示例 ipchains -A input -i eth 0 -s 192. 168. 1. 0/24 -j DENY ipchains -A input -p tcp -d 162. 105. 73. 192/26 any -y –i eth 0 -j DENY ipchains –A input –p tcp –d 162. 105. 73. 254 80 -i eth 0 –j ACCEPT




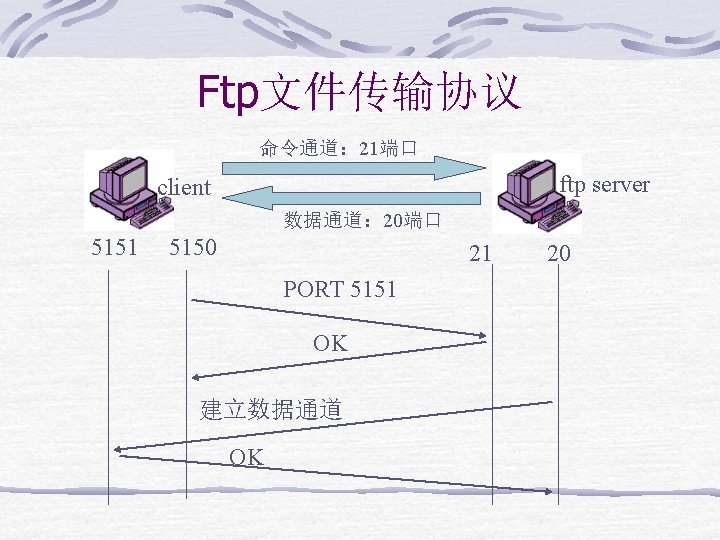
Ftp文件传输协议 命令通道: 21端口 ftp server client 数据通道: 20端口 5151 5150 21 PORT 5151 OK 建立数据通道 OK 20

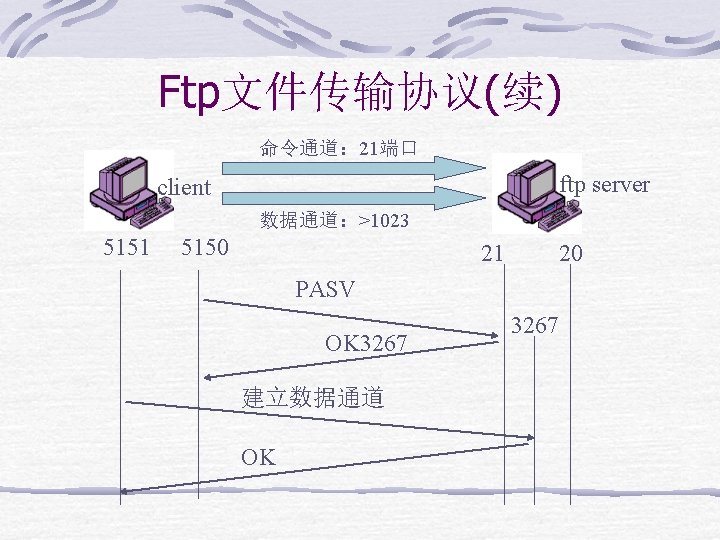
Ftp文件传输协议(续) 命令通道: 21端口 ftp server client 数据通道:>1023 5151 5150 21 20 PASV OK 3267 建立数据通道 OK 3267










Microsoft Proxy Server v 2管理示意图





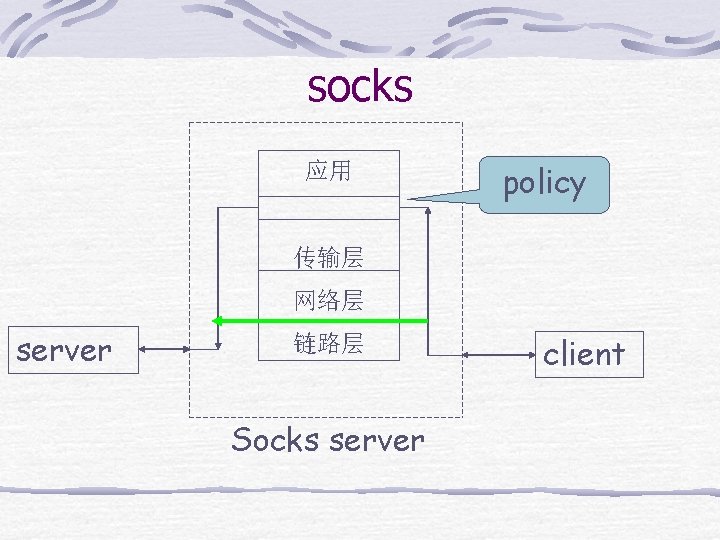
socks 应用 policy 传输层 网络层 server 链路层 Socks server client



认证方案的协商 Client->Server: +----------+--------+ |VER | NMETHODS| METHODS | +----------+--------+ |1 | 1 to 255 | +----------+--------+ Method: Server->Client +------------+ X’ 00: No Authentication require |VER | METHOD | X’ 01: GSSAPI +------------+ |1 | X’ 02: Username/password +------------+ X’FF: No Acceptable Methods


服务器的应答 +-------+--------+---------------+ | VER| REP | RSV | ATYP | BND. ADDR | BND. PORT | +-------+--------+---------------+ | 1 | 1 | X‘ 00’ | 1 | Variable | 2 | +-------+--------+---------------+ REP 00: succeed 01: general SOCKS server failure 02: connection not allowed by ruleset 03: network unreachable 04: host unreachable 05: connection refused 06: TTL expired 07: Command not supported 08: address type not supported 09 -FF: not assigned BND. ADDR & BND. PORT: Specify the addr and port of the socks server which will accept an inbound connection

UDP客户的处理过程 请求命令为“UDP associate” 客户->UDP relay server ->目标机器 每一个UDP包包含一个UDP请求头 UDP packet +--------+--------------+-------+ |RSV | FRAG | ATYP | DST. ADDR | DST. PORT | DATA | +--------+--------------+-------+ |2 | 1 | Variable | 2 | Variable | +--------+--------------+-------+ FRAG: current fragment number









参考资料 书 William Stallings, Cryptography and network security: principles and practice, Second Edition 文章 SOCKS Protocol Version 5, RFC 1928 其他关于防火墙技术的书籍
 Comgeners
Comgeners Ftp.nifc.gov to ftp.wildfire.gov
Ftp.nifc.gov to ftp.wildfire.gov Dns ftp
Dns ftp Dns 53 udp
Dns 53 udp Osi vs tcp
Osi vs tcp Tcpip model
Tcpip model History of osi model
History of osi model Diagrama tcp
Diagrama tcp Tcpip
Tcpip Tcpip logo
Tcpip logo Modelo tcpip
Modelo tcpip Ganesh sittampalam
Ganesh sittampalam Netstat ftp
Netstat ftp Web browser ftp
Web browser ftp Ftp server spring 2017
Ftp server spring 2017 War ftp server
War ftp server Alteryx scrape website
Alteryx scrape website Ftp iut dijon
Ftp iut dijon Ftp passive mode command
Ftp passive mode command Ftp seac
Ftp seac Ftp icfes
Ftp icfes Ftp objectives
Ftp objectives Globus grid computing
Globus grid computing Patricio galdames
Patricio galdames Ftp vs tftp
Ftp vs tftp Http https ftp
Http https ftp Ftp topology
Ftp topology Autowu
Autowu In ftp protocol client contacts server using
In ftp protocol client contacts server using Ftp commands linux
Ftp commands linux Network layer
Network layer Ftp antibot
Ftp antibot Ftp kamsoft
Ftp kamsoft Ftp, telnet belongs to which layer in edi architecture?
Ftp, telnet belongs to which layer in edi architecture? Faceb oo
Faceb oo Ftp incident specific data
Ftp incident specific data Trivial ftp
Trivial ftp Which layer of the osi model includes vlans?
Which layer of the osi model includes vlans? Cpanel.byethost
Cpanel.byethost Ftp privileged port bounce scan
Ftp privileged port bounce scan Ftp slides size 11
Ftp slides size 11 Samba swat
Samba swat Purpose of ftp protocol
Purpose of ftp protocol Ataque ftp bounce
Ataque ftp bounce Telekom ftp
Telekom ftp Ahe ftp
Ahe ftp Ftp application layer
Ftp application layer Ftp and smtp
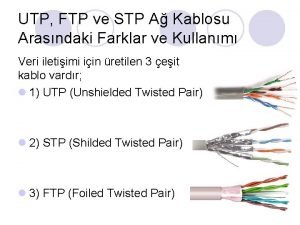
Ftp and smtp Ftp utp stp
Ftp utp stp Amber it ftp
Amber it ftp Entrezpub
Entrezpub Goanywhere ftp
Goanywhere ftp Odot ftp
Odot ftp Trivial flag transfer protocol
Trivial flag transfer protocol Metronet ftp server
Metronet ftp server Ivan maurits
Ivan maurits Ftp client api
Ftp client api Tftp vs ftp
Tftp vs ftp Doing business with fdot
Doing business with fdot Ftp energia bme
Ftp energia bme Sercel ftp
Sercel ftp Cnet ftp
Cnet ftp