Chapter 11 User Datagram Protocol Kyung Hee University


- Slides: 45

Chapter 11 User Datagram Protocol Kyung Hee University 1

Introduction q Responsibilities of Transport Layer to create a process-to-process communication l using port numbers in case of UDP to provide a flow-and-error control mechanism at the transport level l l But, no flow control mechanism and no acknowledgment for received packets in UDP If UDP detects an error in the received packets, it silently drops it. to provide a connection mechanism for the processes l l Kyung Hee University sending streams of data to the transport layer by process making the connection, chopping the stream into transportable units, numbering them and sending them one by one 2

Introduction (cont’d) l Normally, at the receiving end, waiting until all the different units belonging to the transport layer have received, checking, passing those that are error free and delivering them to the receiving process as a stream q But, UDP does not do any of the above l can only receive a data unit from the process and deliver it, unreliably, to the receiver data unit must be small enough to fit in a UDP packet q UDP is called a connectionless, unreliable transport protocol providing process-to-process communication instead of host-to-host communication Kyung Hee University performing very limited error checking 3

Introduction (cont’d) q If UDP is so powerless, why would a process want to use it ? very simple protocol using a minimum of overhead l l Kyung Hee University if a process wants to send a small message and does not care much about reliability, it can use UDP if it sends a small message, taking much less interaction between the sender and receiver than it does using TCP 4

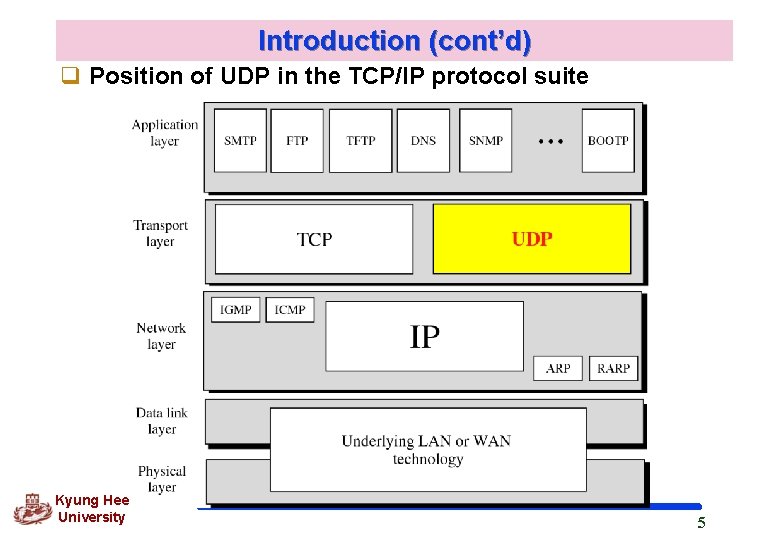
Introduction (cont’d) q Position of UDP in the TCP/IP protocol suite Kyung Hee University 5

11. 1 Process-to-process communication q IP is responsible for communication at the computer level (host-to-host communication) q UDP is responsible for delivery of the message to the appropriate process Kyung Hee University 6

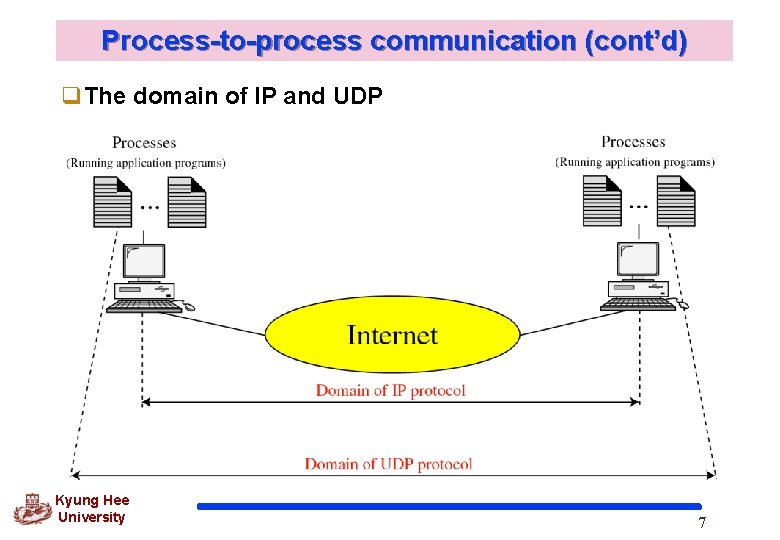
Process-to-process communication (cont’d) q. The domain of IP and UDP Kyung Hee University 7

Process-to-process communication (cont’d) q Port Numbers used in client-server paradigm used for defining processes integers between 0 and 65, 535 The client program defines itself with a port number, chosen randomly by the UDP software running on the client host l the ephemeral port number But, the server process must also define itself with a port number that is not randomly chosen l Kyung Hee University using well-known port number 8

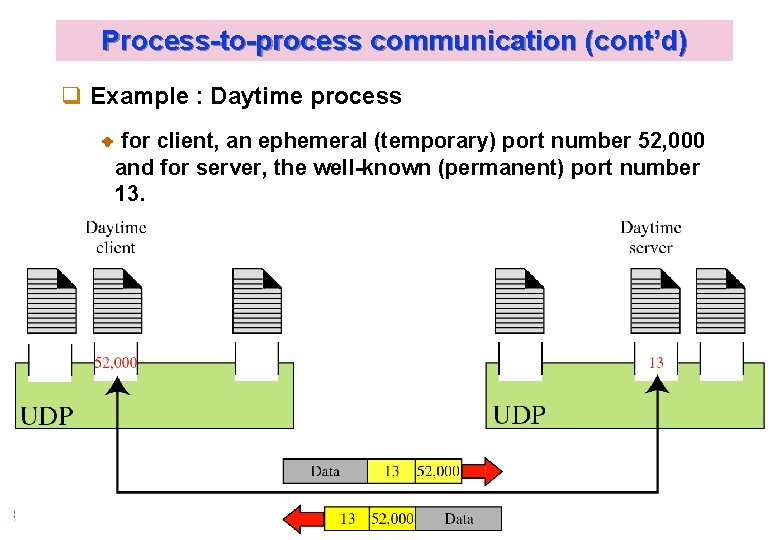
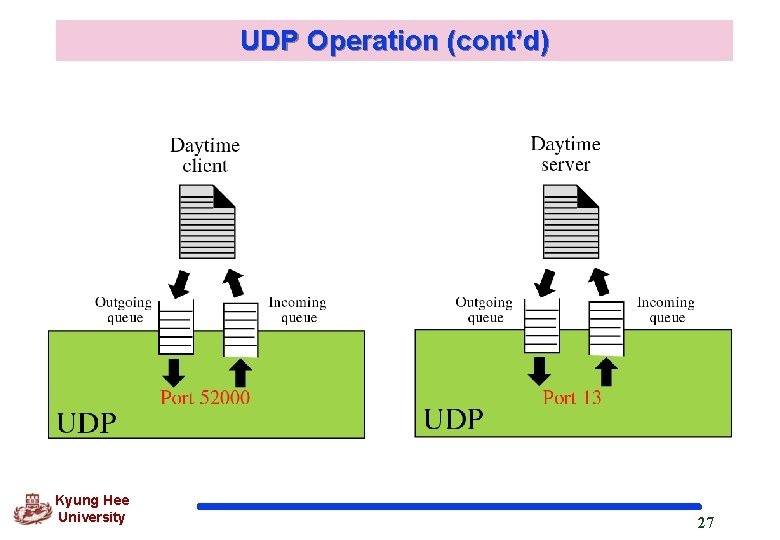
Process-to-process communication (cont’d) q Example : Daytime process for client, an ephemeral (temporary) port number 52, 000 and for server, the well-known (permanent) port number 13. Kyung Hee University 9

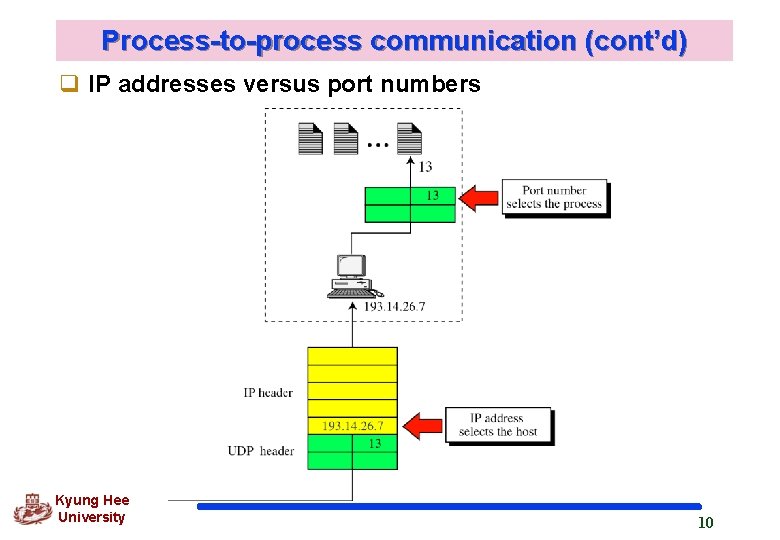
Process-to-process communication (cont’d) q IP addresses versus port numbers Kyung Hee University 10

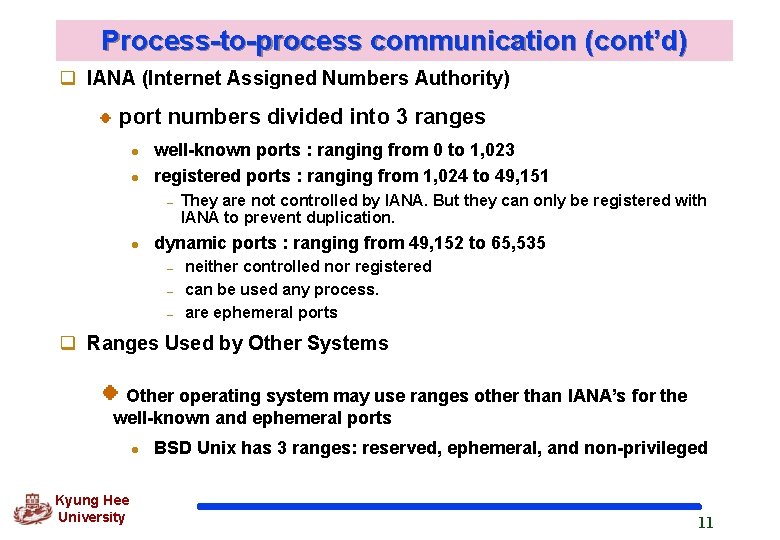
Process-to-process communication (cont’d) q IANA (Internet Assigned Numbers Authority) port numbers divided into 3 ranges l l well-known ports : ranging from 0 to 1, 023 registered ports : ranging from 1, 024 to 49, 151 – l They are not controlled by IANA. But they can only be registered with IANA to prevent duplication. dynamic ports : ranging from 49, 152 to 65, 535 – – – neither controlled nor registered can be used any process. are ephemeral ports q Ranges Used by Other Systems Other operating system may use ranges other than IANA’s for the well-known and ephemeral ports l Kyung Hee University BSD Unix has 3 ranges: reserved, ephemeral, and non-privileged 11

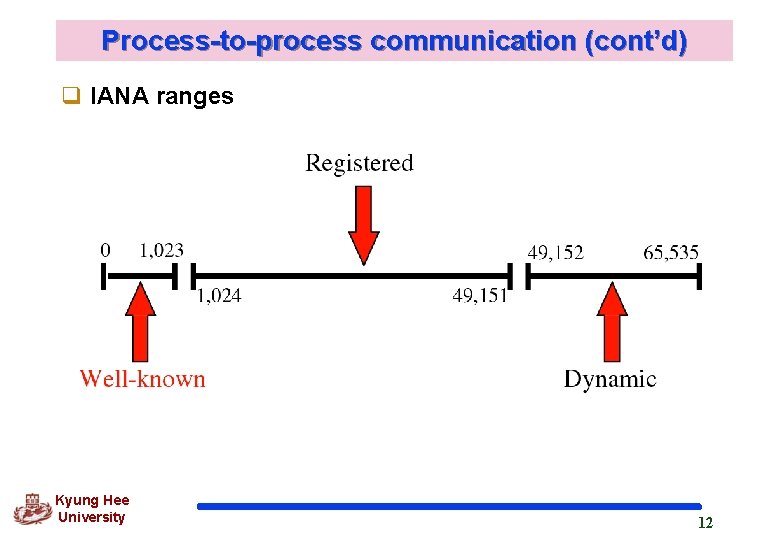
Process-to-process communication (cont’d) q IANA ranges Kyung Hee University 12

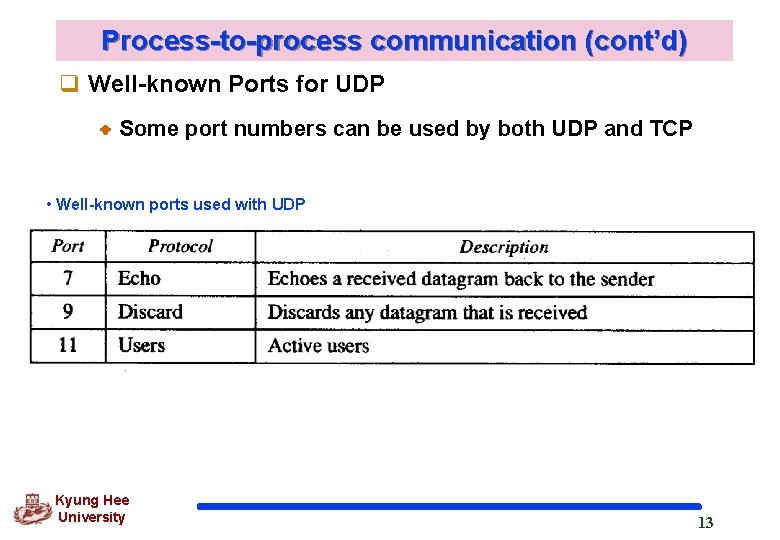
Process-to-process communication (cont’d) q Well-known Ports for UDP Some port numbers can be used by both UDP and TCP • Well-known ports used with UDP Kyung Hee University 13

Process-to-process communication (cont’d) Kyung Hee University 14

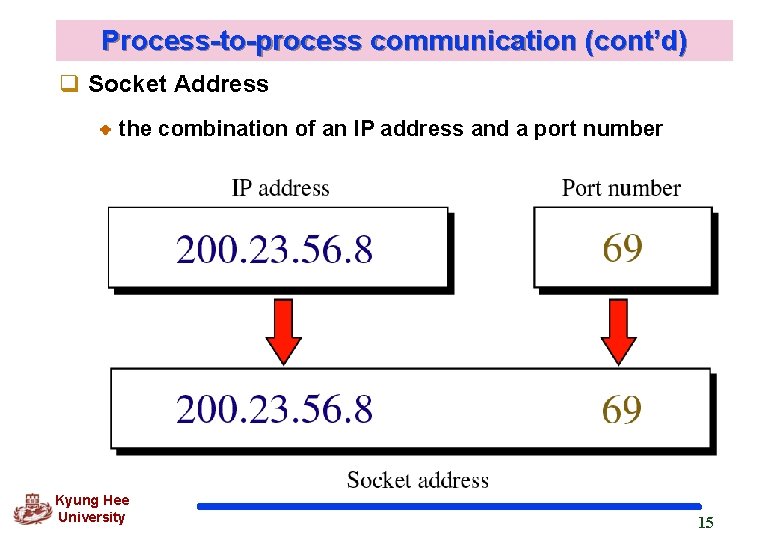
Process-to-process communication (cont’d) q Socket Address the combination of an IP address and a port number Kyung Hee University 15

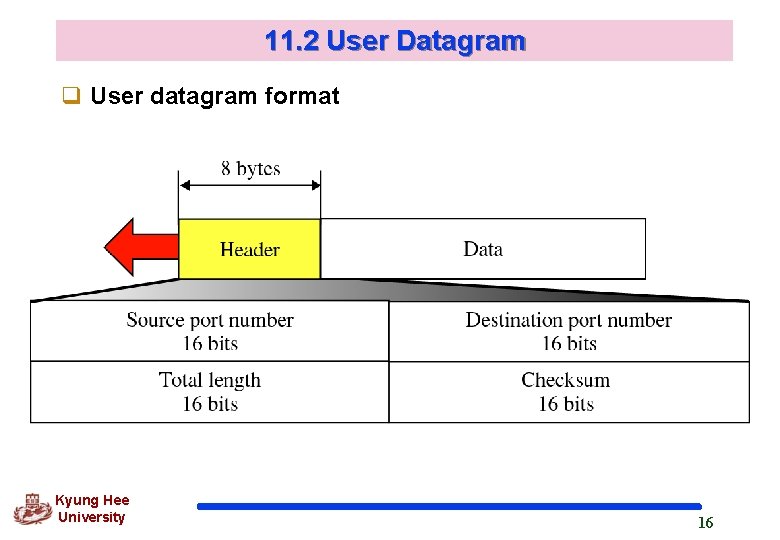
11. 2 User Datagram q User datagram format Kyung Hee University 16

11. 2 User Datagram Source port number l l In case of the client (a client sending a request), having ephemeral port number requested by the process In case of the server (a sever sending response), having a wellknown port number Destination port number l Used by the process running on the destination host Length l l Defining the total length of the user diagram, header + data Minimum 8 bytes. (header + no data) the length of data : 0 to 65, 507 (65, 535 – 20 – 8) bytes UDP length = IP Length – IP header’s length Checksum Kyung Hee l University used to detect errors over the entire user datagram 17

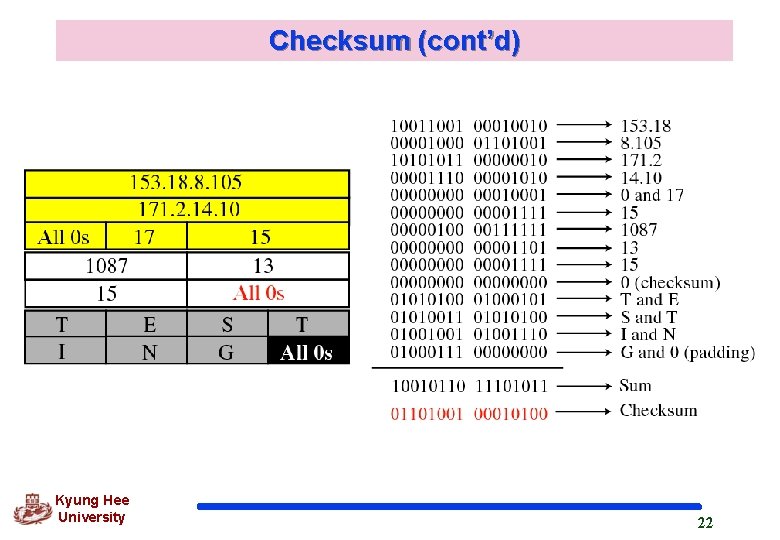
11. 3 Checksum q UDP checksum calculation is different from the checksum for IP and ICMP q. It includes as follows. pseudoheader : part of the header of the IP packet UDP header data from the application layer Kyung Hee University 18

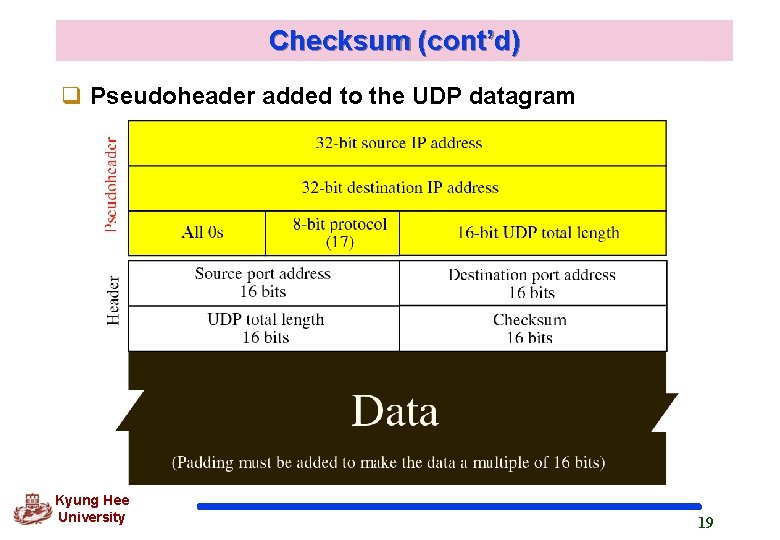
Checksum (cont’d) q Pseudoheader added to the UDP datagram Kyung Hee University 19

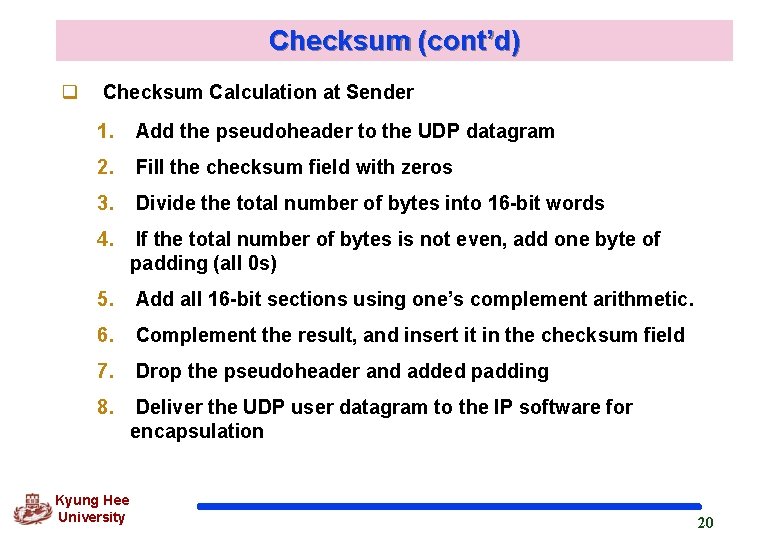
Checksum (cont’d) q Checksum Calculation at Sender 1. Add the pseudoheader to the UDP datagram 2. Fill the checksum field with zeros 3. Divide the total number of bytes into 16 -bit words 4. If the total number of bytes is not even, add one byte of padding (all 0 s) 5. Add all 16 -bit sections using one’s complement arithmetic. 6. Complement the result, and insert it in the checksum field 7. Drop the pseudoheader and added padding 8. Deliver the UDP user datagram to the IP software for encapsulation Kyung Hee University 20

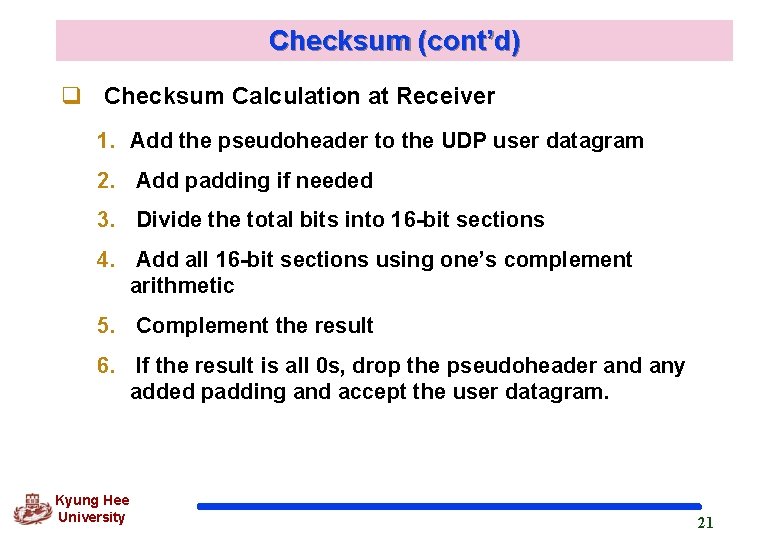
Checksum (cont’d) q Checksum Calculation at Receiver 1. Add the pseudoheader to the UDP user datagram 2. Add padding if needed 3. Divide the total bits into 16 -bit sections 4. Add all 16 -bit sections using one’s complement arithmetic 5. Complement the result 6. If the result is all 0 s, drop the pseudoheader and any added padding and accept the user datagram. Kyung Hee University 21

Checksum (cont’d) Kyung Hee University 22

11. 4 UDP Operation q Connectionless Services each user datagram sent by UDP is an independent datagram each user datagram can travel a different path Kyung Hee University 23

UDP Operation (cont’d) q Flow and error control no flow control, hence no windowing mechanism l The receiver may overflow with incoming messages no error control mechanism except for the checksum l the sender does not know if a message has been lost or duplicated So, the process using UDP provides these mechanism Kyung Hee University 24

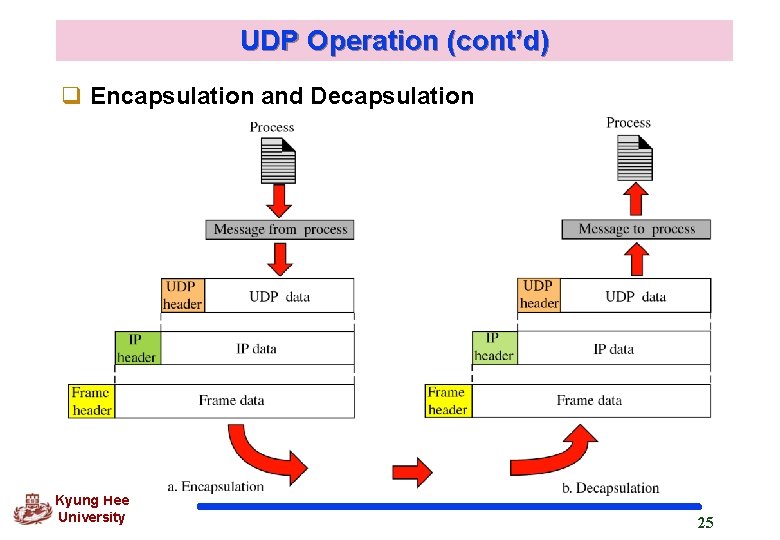
UDP Operation (cont’d) q Encapsulation and Decapsulation Kyung Hee University 25

UDP Operation (cont’d) q Queuing The queues function as long as the process is running. If an outgoing queue is happened overflow, the operating system can ask the client process to wait before sending any more messages. When a message arrives for a client, check an incoming queue. If there is no such incoming queue, UDP discard the user datagram and ask the ICMP protocols to send a port unreachable message to the server. At the server, the queues remain open as long as the server is running l Kyung Hee University An outgoing queue can overflow. If this happens, the operating system asks the server to wait before sending any more messages 26

UDP Operation (cont’d) Kyung Hee University 27

UDP Operation (cont’d) q Multiplexing At the sender site, there may be several processes that need to send user datagrams l differentiating by their assigned port numbers q Demultiplexing At the receiver site, there is only one UDP l l Kyung Hee University UDP receives user datagrams from IP. After error checking and dropping of the header, UDP delivers each message to the appropriate port based on the port numbers 28

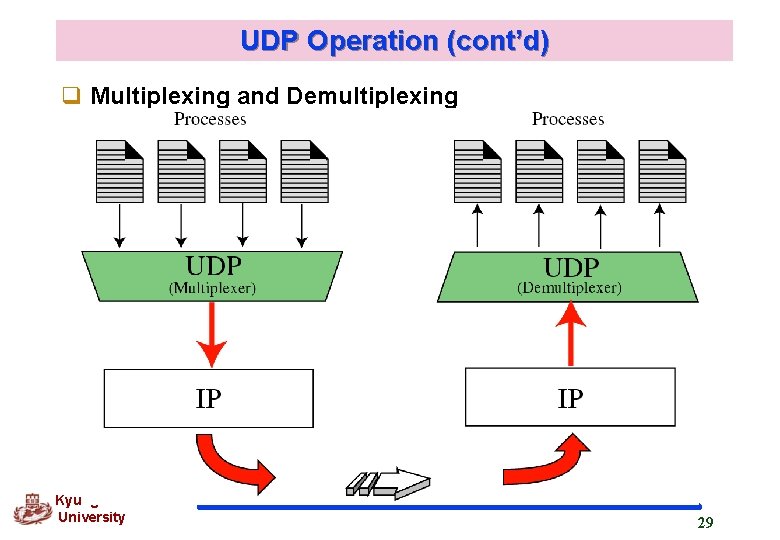
UDP Operation (cont’d) q Multiplexing and Demultiplexing Kyung Hee University 29

11. 5 Use of UDP q The following lists some uses of the UDP protocols suitable for a process that requires simple requestresponse communication and with little concern for flow and error control l not used for a process that needs to send bulk data, such as FTP suitable for a process with internal flow and error control mechanisms l TFTP process including flow and error control suitable transport protocol for multicasting and broadcasting l Kyung Hee University multicasting and broadcasting capabilities are embedded in the UDP software, but not in the TCP software 30

Use of UDP (cont’d) q used for management protocol such as SNMP q used for some route updating protocol such as RIP Kyung Hee University 31

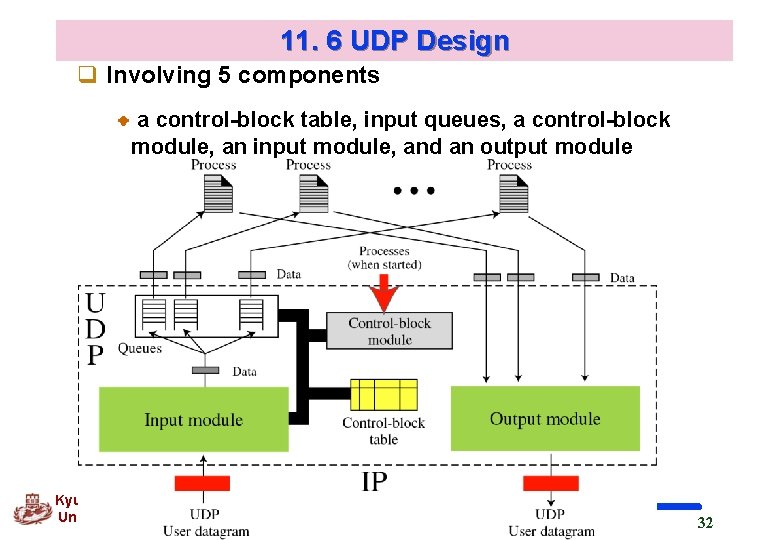
11. 6 UDP Design q Involving 5 components a control-block table, input queues, a control-block module, an input module, and an output module Kyung Hee University 32

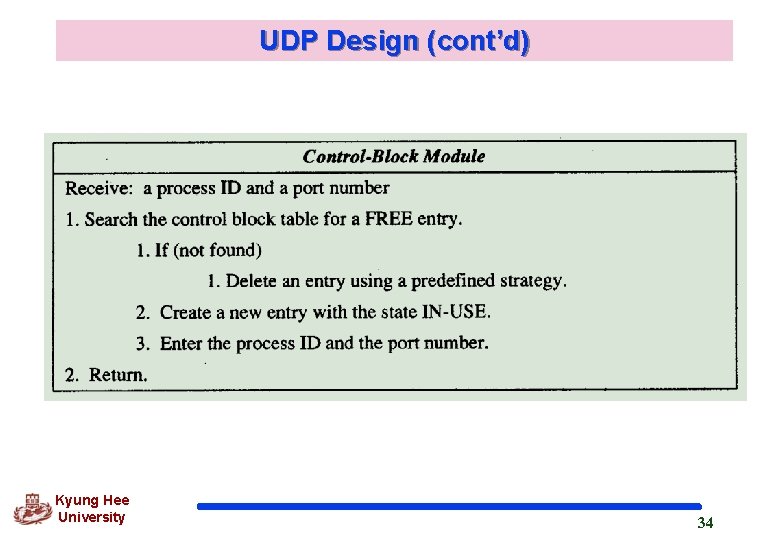
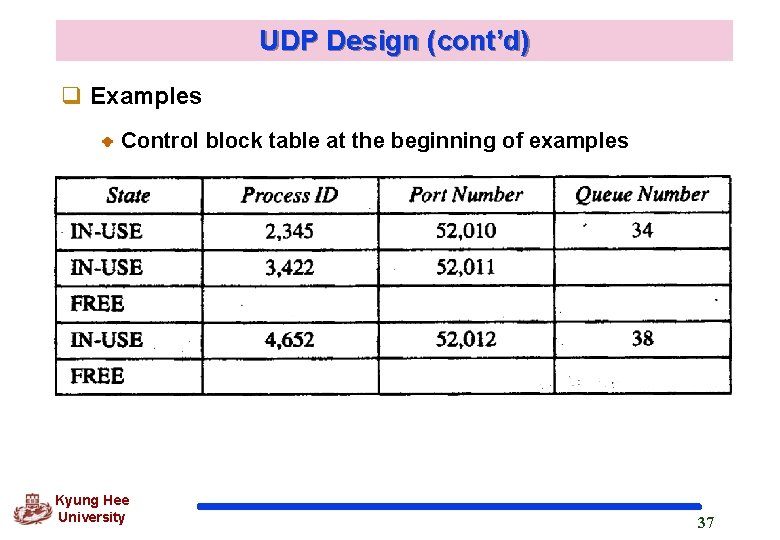
UDP Design (cont’d) q Control-Block Table Keeping track of the open ports Each entry having 4 field: the state, which can be FREE or INUSE, the process ID, the port number and the corresponding queue number q Input Queues One for each process q Control-block Module Responsible for management of the control-block table When a process starts, it asks for a port number from the OS OS assigns well-known port numbers to servers and ephemeral port number to clients Kyung Hee University 33

UDP Design (cont’d) Kyung Hee University 34

UDP Design (cont’d) q Input Module Kyung Hee University 35

UDP Design (cont’d) q Output Module Kyung Hee University 36

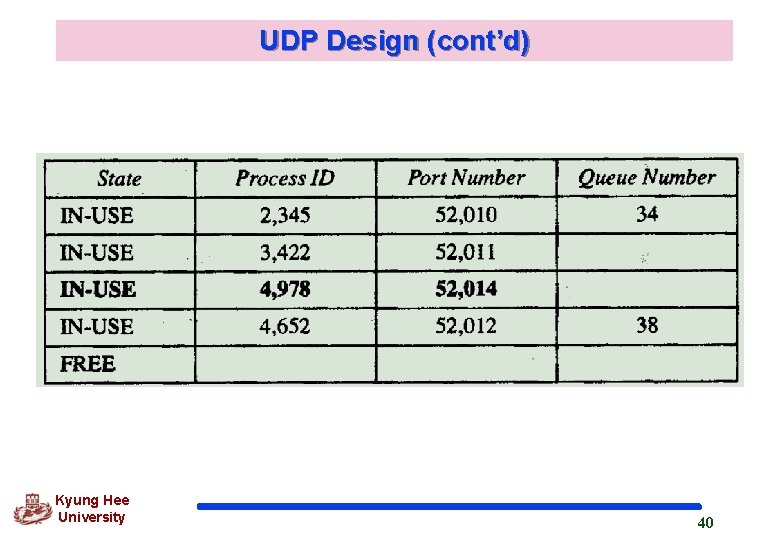
UDP Design (cont’d) q Examples Control block table at the beginning of examples Kyung Hee University 37

UDP Design (cont’d) q Example 1 Arrival of a user datagram with destination port number 52, 012 The input module searches for this port number and finds it. The input module sends the data to queue 38 The control block table does not change. Kyung Hee University 38

UDP Design (cont’d) q Example 2 A process starts Asking the OS for a port number and is granted port number 52, 014 Sending process ID (4, 978) and the port number to the control-block module to create an entry in the table Taking the first FREE entry No queue number assigned l Kyung Hee University No user diagrams have arrived for this destination 39

UDP Design (cont’d) Kyung Hee University 40

UDP Design (cont’d) q Example 3, A user datagram now arrives 52, 011 Input module checks the table and finds that no queue has been allocated for this destination l l Kyung Hee University since this is the first time a user datagram has arrived for this destination the module create a queue and gives it a number (43) 41

UDP Design (cont’d) Kyung Hee University 42

UDP Design (cont’d) q. Example 4 After a few seconds, a user datagram arrives for port 52, 222. Cannot find the entry for the this destination Dropping datagram and sending to the source ICMP message such as “unreachable port” q Example 5 After few seconds, process needs to send a user datagram. It delivers the data to the output module which adds the UDP header Kyung Hee University 43

Summary(1) q UDP is a transport protocol that creates a process-to-process communication. q UDP is a (mostly) unreliable and connectionless protocol that requires little overhead and offers fast delivery. q In the client-server paradigm, an application program on the local host, called the client, needs services from an application program on the remote host, called a server. q Each application program has a unique port number that distinguishes it from other programs running at the same time on the same machine. q The client program is assigned a random port number called an ephemeral port number. q The server program is assigned a universal port number called a well-known port number. q The ICANN has specified ranges for the different types of port numbers. q The combination of the IP address and the port number, called the socket address, uniquely defines a process and a host. q UDP requires a pair of socket addresses: the client socket address and the server socket address. q. Kyung Hee University 44

Summary(2) q The UDP packet is called a user datagram. q UDP's only attempt at error control is the checksum. q Inclusion of a pseudoheader in the checksum calculation allows source and destination IP address errors to be detected. q UDP has no flow-control mechanism. q A user datagram is encapsulated in the data field of an IP datagram. q Incoming and outgoing queues hold messages going to and from UDP. q UDP uses multiplexing to handle incoming user datagrams that go to different processes on the same host. q A UDP package can involve five components: a control-block table, a control-block module, input queues, an input module, and an output module. q The input queues hold incoming user datagrams. q The control-block module is responsible for maintenance of entries in the controlblock table. q The input module creates input queues; the output module sends out user datagrams. Kyung Hee University 45