Transport Layer Flow control Connection management TCP UDP









- Slides: 44

Transport Layer Flow control Connection management TCP, UDP 1

Announcements n n n I hope you had a very happy Thanksgiving break! My sincere apologies for the Monday emergency cancellation!! SM 5 is out. Due in one week. Copyright Jorg Liebeherr 98, Modified with permission, Abdelzaher 2

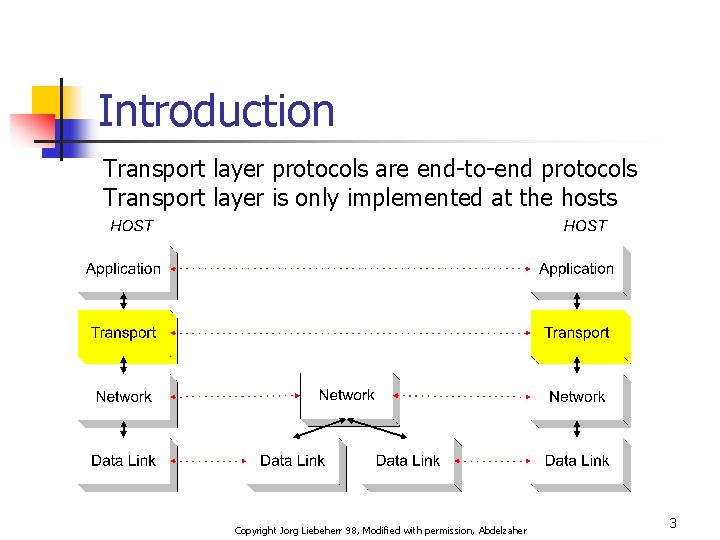
Introduction Transport layer protocols are end-to-end protocols Transport layer is only implemented at the hosts Copyright Jorg Liebeherr 98, Modified with permission, Abdelzaher 3

Functions of the Transport Layer n n n Reliability Connection Establishment Connection Termination Flow control Congestion control Copyright Jorg Liebeherr 98, Modified with permission, Abdelzaher 4

Reliability n How to achieve it? Copyright Jorg Liebeherr 98, Modified with permission, Abdelzaher 5

Reliability n How to achieve it? n n n Send data in chunks (called packets) Number the packets sequentially at the sender Make sure all numbers are received without gaps Copyright Jorg Liebeherr 98, Modified with permission, Abdelzaher 6

Reliability n How to achieve it? n n n Send data in chunks (called packets) Number the packets sequentially at the sender Make sure all numbers are received without gaps n n Acknowledge each packet number If sender sees an ack gap sender retransmits Copyright Jorg Liebeherr 98, Modified with permission, Abdelzaher 7

Reliability n How to achieve it? n n n Send data in chunks (called packets) Number the packets sequentially at the sender Make sure all numbers are received without gaps n n n Acknowledge each packet number If sender sees an ack gap sender retransmits Optimization: Cumulative acks (ACK N: acknowledge that all packets up to but not including packet N have been received). Copyright Jorg Liebeherr 98, Modified with permission, Abdelzaher 8

Reliability n How to achieve it? n n n Send data in chunks (called packets) Number the packets sequentially at the sender Make sure all numbers are received without gaps n n Acknowledge each packet number If sender sees an ack gap sender retransmits Optimization: Cumulative acks (ACK N: acknowledge that all packets up to but not including packet N have been received). What about the number of the first packet? Copyright Jorg Liebeherr 98, Modified with permission, Abdelzaher 9

Connection Establishment n Connection establishment is asymmetric: n n one side puts itself in a LISTEN state (server) one side issues a request for connection (client) Copyright Jorg Liebeherr 98, Modified with permission, Abdelzaher 10

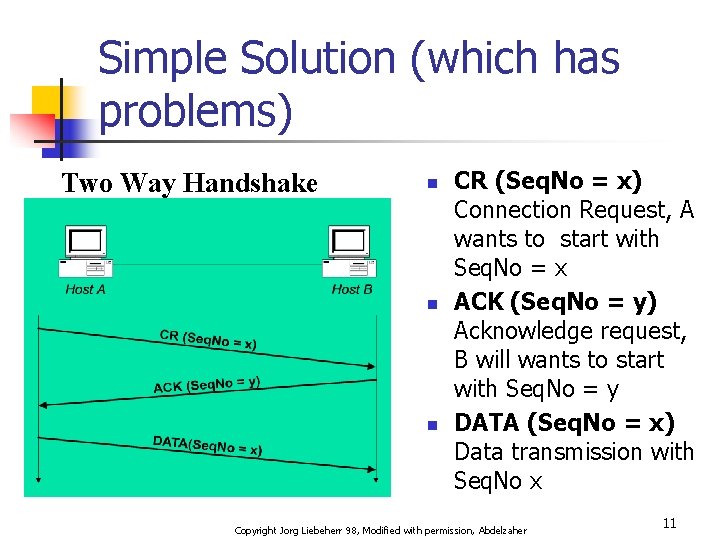
Simple Solution (which has problems) Two Way Handshake n n n CR (Seq. No = x) Connection Request, A wants to start with Seq. No = x ACK (Seq. No = y) Acknowledge request, B will wants to start with Seq. No = y DATA (Seq. No = x) Data transmission with Seq. No x Copyright Jorg Liebeherr 98, Modified with permission, Abdelzaher 11

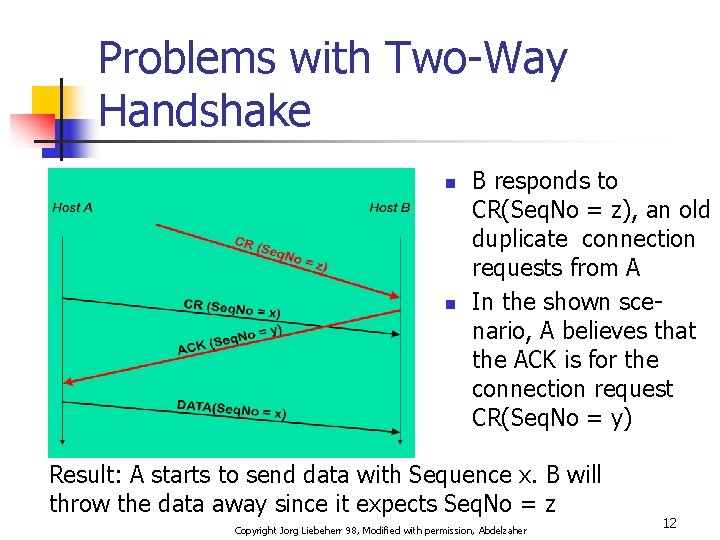
Problems with Two-Way Handshake n n B responds to CR(Seq. No = z), an old duplicate connection requests from A In the shown scenario, A believes that the ACK is for the connection request CR(Seq. No = y) Result: A starts to send data with Sequence x. B will throw the data away since it expects Seq. No = z Copyright Jorg Liebeherr 98, Modified with permission, Abdelzaher 12

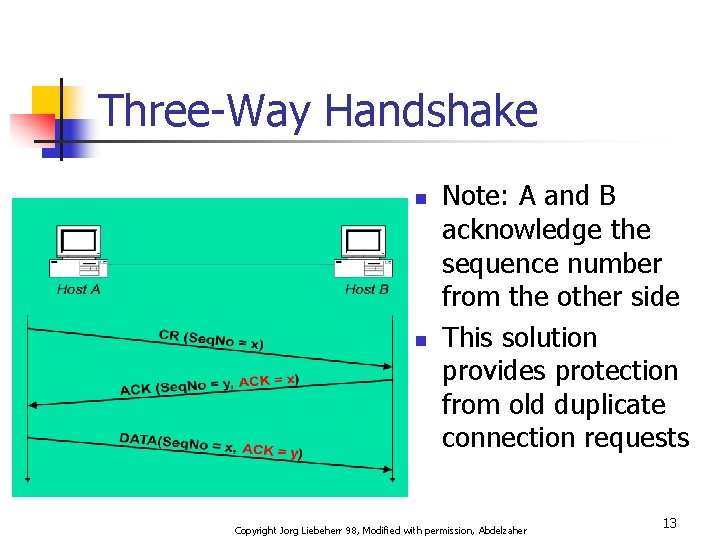
Three-Way Handshake n n Note: A and B acknowledge the sequence number from the other side This solution provides protection from old duplicate connection requests Copyright Jorg Liebeherr 98, Modified with permission, Abdelzaher 13

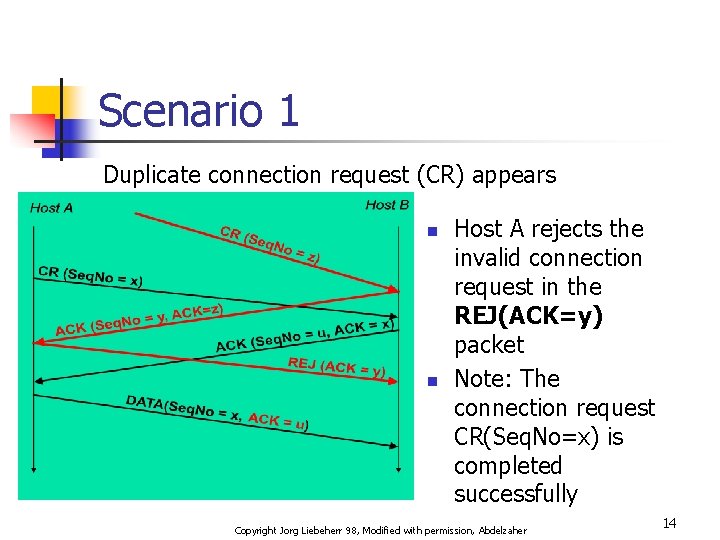
Scenario 1 Duplicate connection request (CR) appears n n Host A rejects the invalid connection request in the REJ(ACK=y) packet Note: The connection request CR(Seq. No=x) is completed successfully Copyright Jorg Liebeherr 98, Modified with permission, Abdelzaher 14

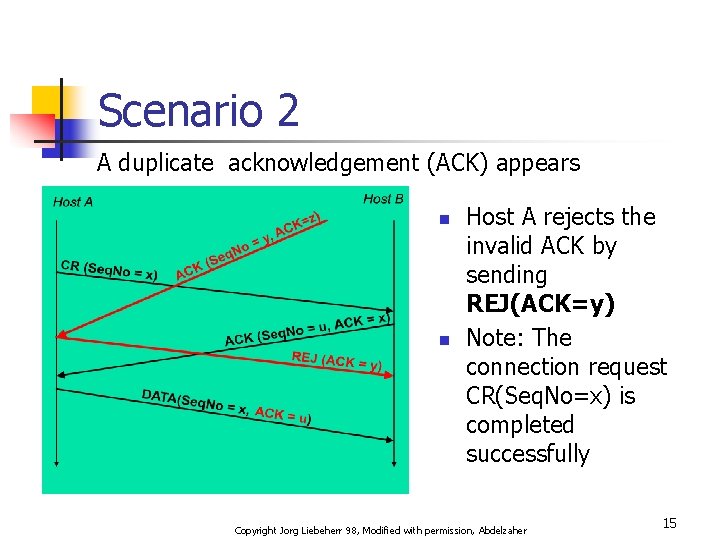
Scenario 2 A duplicate acknowledgement (ACK) appears n n Host A rejects the invalid ACK by sending REJ(ACK=y) Note: The connection request CR(Seq. No=x) is completed successfully Copyright Jorg Liebeherr 98, Modified with permission, Abdelzaher 15

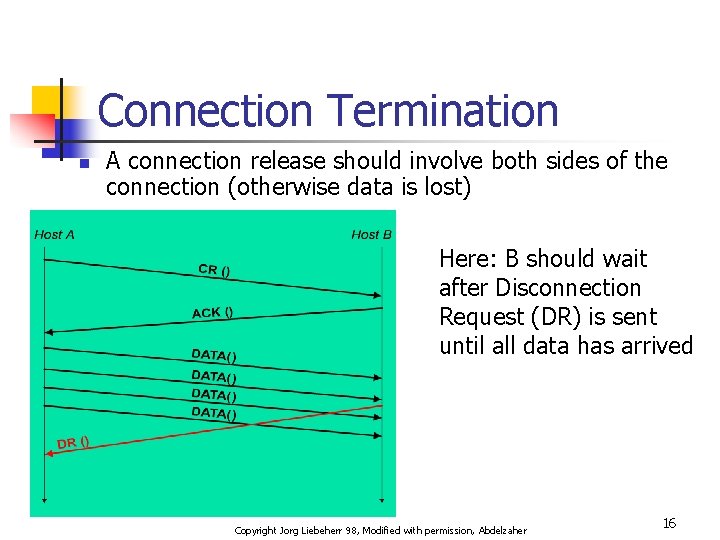
Connection Termination n A connection release should involve both sides of the connection (otherwise data is lost) Here: B should wait after Disconnection Request (DR) is sent until all data has arrived Copyright Jorg Liebeherr 98, Modified with permission, Abdelzaher 16

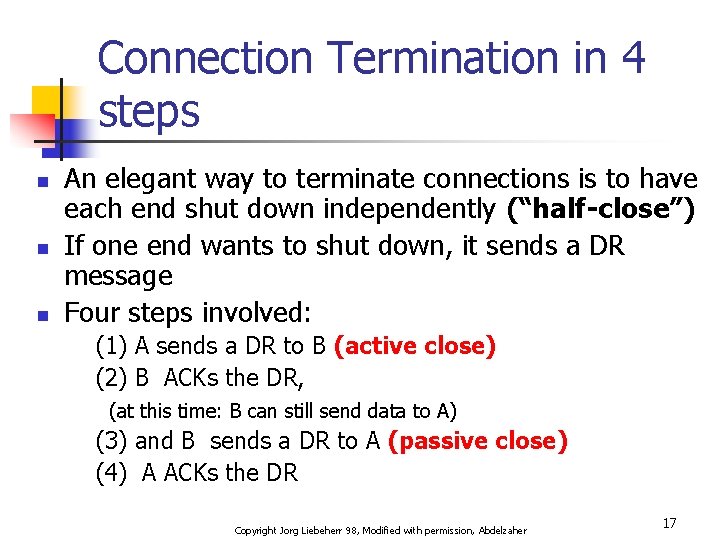
Connection Termination in 4 steps n n n An elegant way to terminate connections is to have each end shut down independently (“half-close”) If one end wants to shut down, it sends a DR message Four steps involved: (1) A sends a DR to B (active close) (2) B ACKs the DR, (at this time: B can still send data to A) (3) and B sends a DR to A (passive close) (4) A ACKs the DR Copyright Jorg Liebeherr 98, Modified with permission, Abdelzaher 17

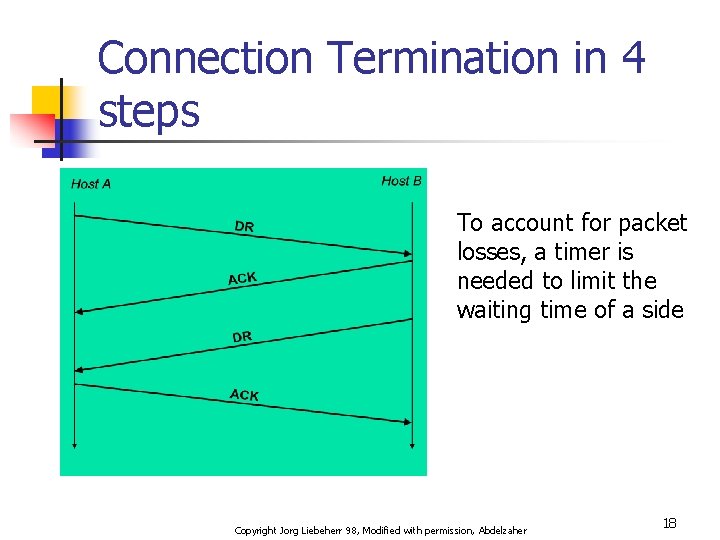
Connection Termination in 4 steps To account for packet losses, a timer is needed to limit the waiting time of a side Copyright Jorg Liebeherr 98, Modified with permission, Abdelzaher 18

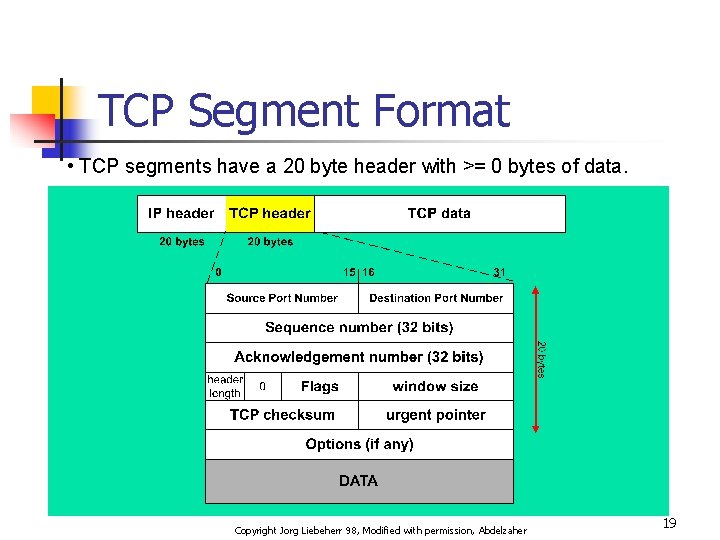
TCP Segment Format • TCP segments have a 20 byte header with >= 0 bytes of data. Copyright Jorg Liebeherr 98, Modified with permission, Abdelzaher 19

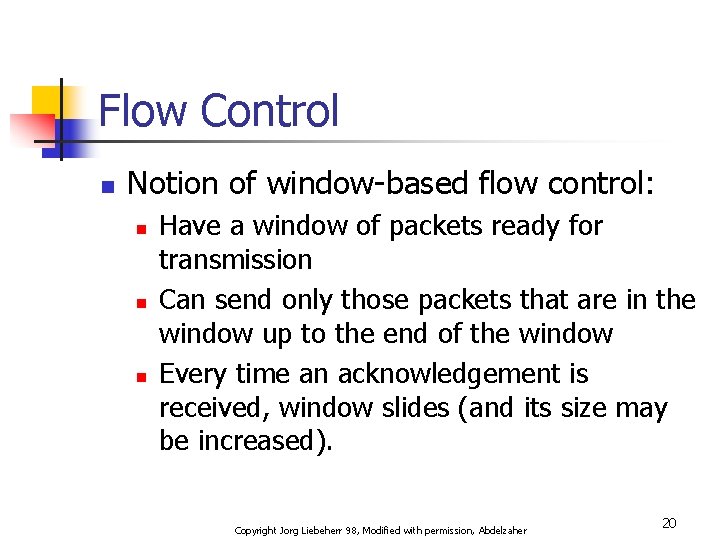
Flow Control n Notion of window-based flow control: n n n Have a window of packets ready for transmission Can send only those packets that are in the window up to the end of the window Every time an acknowledgement is received, window slides (and its size may be increased). Copyright Jorg Liebeherr 98, Modified with permission, Abdelzaher 20

Flow Control n n Flow Control is a technique for speed-matching of transmitter and receiver. Flow control ensures that a transmitting station does not overflow a receiving station with data We will discuss two protocols for flow control: n n Stop-and-Wait On-Off Sliding Window For the time being, we assume that we have a perfect channel (no errors) 21 Copyright Jorg Liebeherr 98, Modified with permission, Abdelzaher

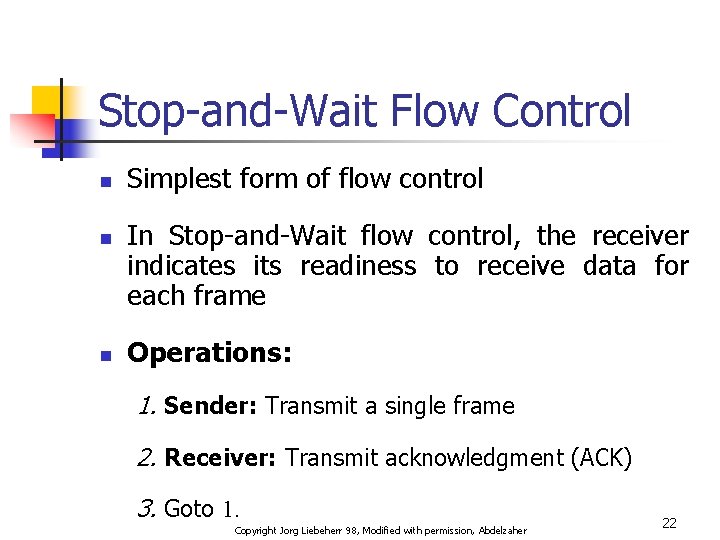
Stop-and-Wait Flow Control n n n Simplest form of flow control In Stop-and-Wait flow control, the receiver indicates its readiness to receive data for each frame Operations: 1. Sender: Transmit a single frame 2. Receiver: Transmit acknowledgment (ACK) 3. Goto 1. Copyright Jorg Liebeherr 98, Modified with permission, Abdelzaher 22

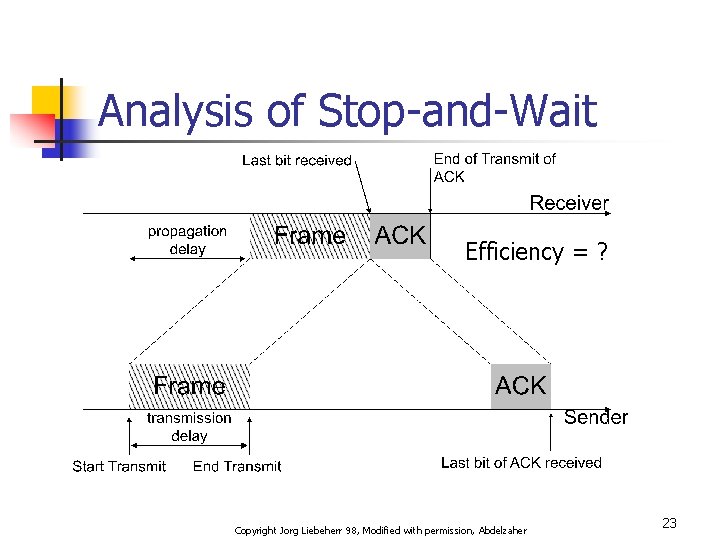
Analysis of Stop-and-Wait Efficiency = ? Copyright Jorg Liebeherr 98, Modified with permission, Abdelzaher 23

Sliding Window Flow Control n n n Allows transmission of multiple frames Assigns each frame a k-bit sequence number Range of sequence number is [0. . 2 k-1], i. e. , frames are counted modulo 2 k Copyright Jorg Liebeherr 98, Modified with permission, Abdelzaher 24

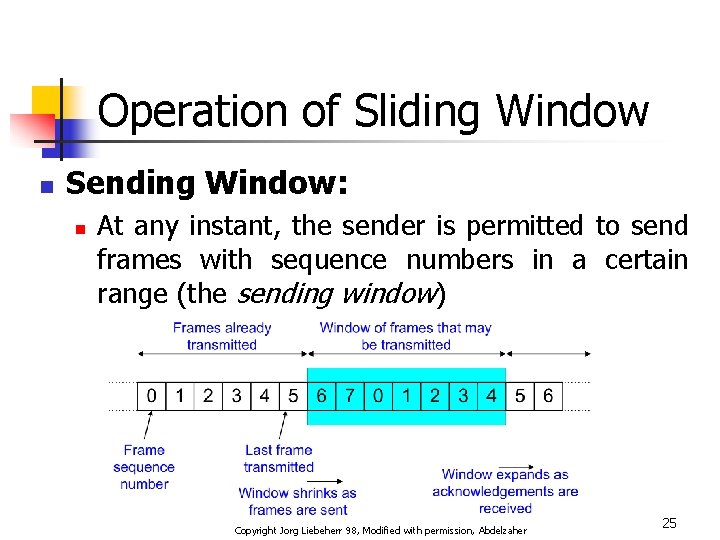
Operation of Sliding Window n Sending Window: n At any instant, the sender is permitted to send frames with sequence numbers in a certain range (the sending window) Copyright Jorg Liebeherr 98, Modified with permission, Abdelzaher 25

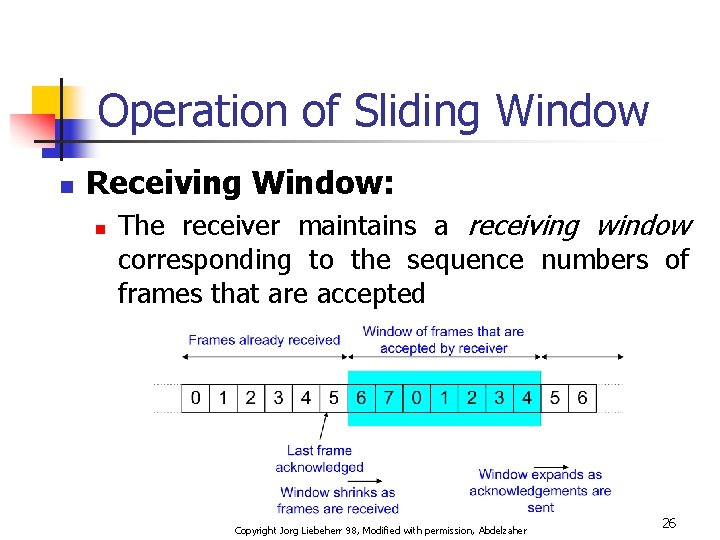
Operation of Sliding Window n Receiving Window: n The receiver maintains a receiving window corresponding to the sequence numbers of frames that are accepted Copyright Jorg Liebeherr 98, Modified with permission, Abdelzaher 26

Operation of Sliding Window n How is “flow control” achieved? n n n Receiver can control the size of the sending window By limiting the size of the sending window data flow from sender to receiver can be limited Interpretation of ACK N message: n Receiver acknowledges all packets until (but not including) sequence number N Copyright Jorg Liebeherr 98, Modified with permission, Abdelzaher 27

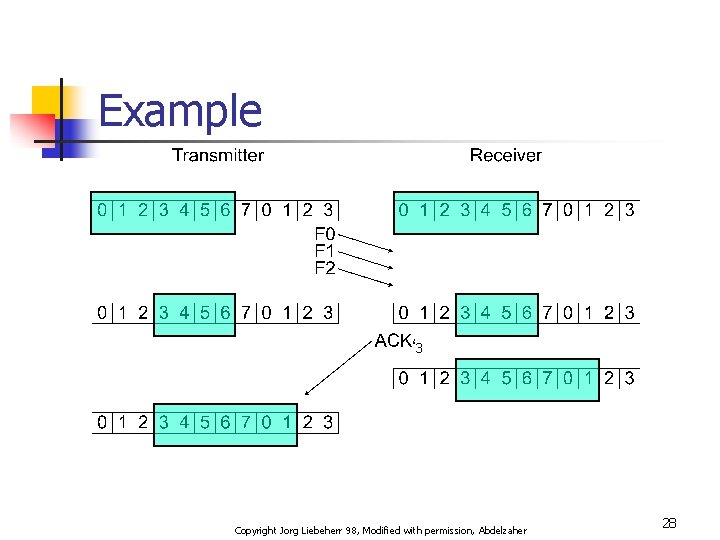
Example 3 Copyright Jorg Liebeherr 98, Modified with permission, Abdelzaher 28

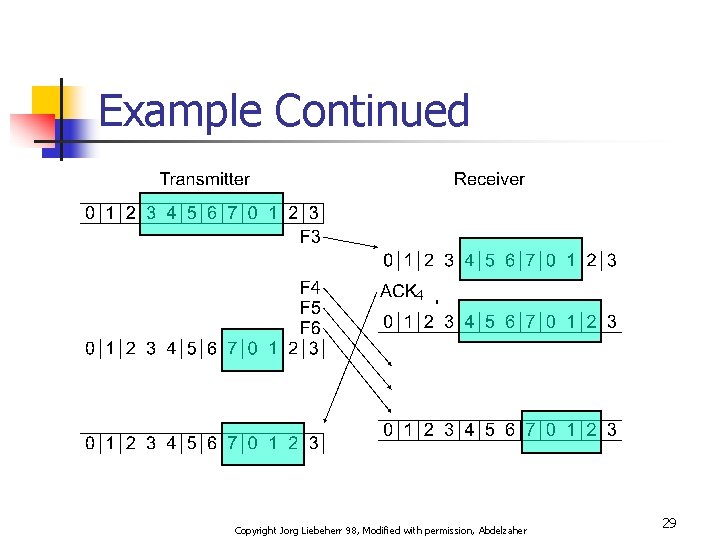
Example Continued 4 4 Copyright Jorg Liebeherr 98, Modified with permission, Abdelzaher 29

Slow Start n Whenever starting traffic on a new connection, or whenever increasing traffic after congestion was experienced: n n n Set cwnd = MSS bytes (=1 segment) Each time an ACK is received, slide the congestion window and increase size by 1 segment (= MSS bytes). Does Slow Start increment slowly? Not really. In fact, the increase of cwnd can be exponential Copyright Jorg Liebeherr 98, Modified with permission, Abdelzaher 30

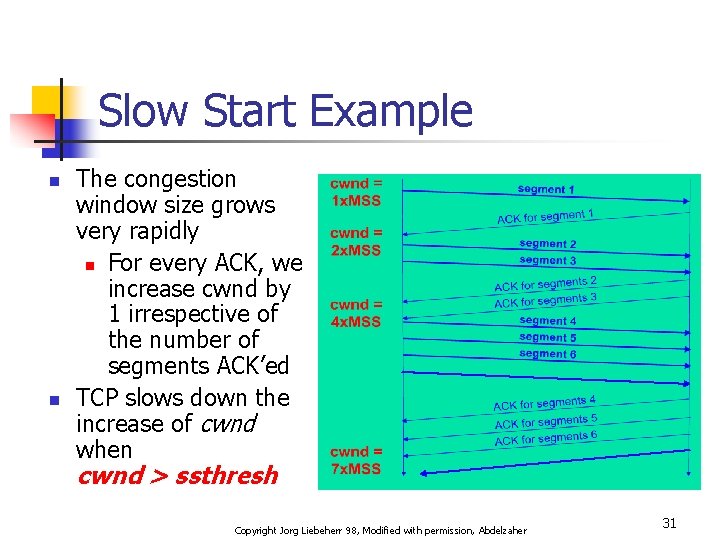
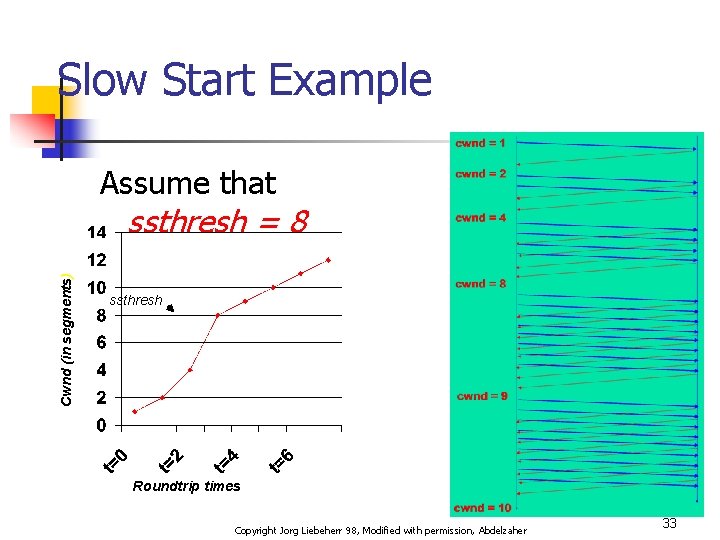
Slow Start Example n n The congestion window size grows very rapidly n For every ACK, we increase cwnd by 1 irrespective of the number of segments ACK’ed TCP slows down the increase of cwnd when cwnd > ssthresh Copyright Jorg Liebeherr 98, Modified with permission, Abdelzaher 31

Slow Start n n “Slow Start” slows down if the congestion window is larger than a threshold value If cwnd > ssthresh then each time an ACK is received, increment cwnd as follows: n n n cwnd = cwnd + MSS * MSS / cwnd So cwnd is increased by one only if all segments have been acknowledged. ssthresh is modified if there is congestion in the network Copyright Jorg Liebeherr 98, Modified with permission, Abdelzaher 32

Slow Start Example Assume that Cwnd (in segments) ssthresh = 8 ssthresh Roundtrip times Copyright Jorg Liebeherr 98, Modified with permission, Abdelzaher 33

Slow Start / Congestion Avoidance n Here we give a more accurate version than in our earlier discussion of Slow Start: If cwnd <= ssthresh then Each time an Ack is received: cwnd = cwnd + MSS else /* cwnd > ssthresh */ Each time an Ack is received : cwnd = cwnd + MSS * MSS / cwnd endif Copyright Jorg Liebeherr 98, Modified with permission, Abdelzaher 34

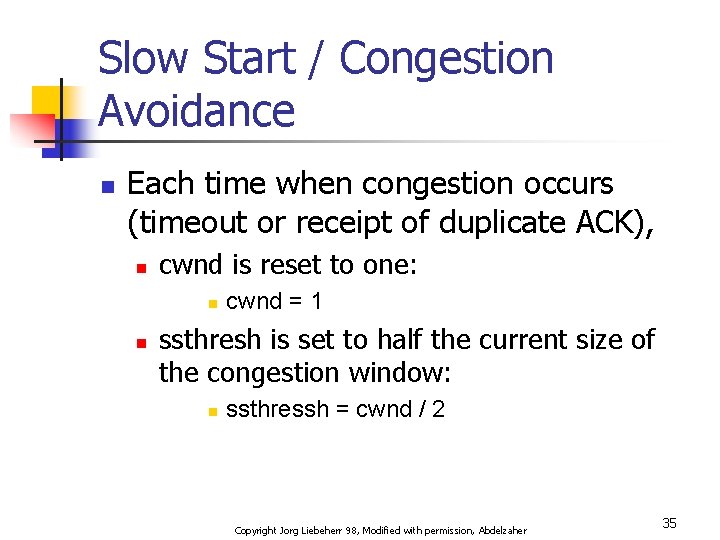
Slow Start / Congestion Avoidance n Each time when congestion occurs (timeout or receipt of duplicate ACK), n cwnd is reset to one: n n cwnd = 1 ssthresh is set to half the current size of the congestion window: n ssthressh = cwnd / 2 Copyright Jorg Liebeherr 98, Modified with permission, Abdelzaher 35

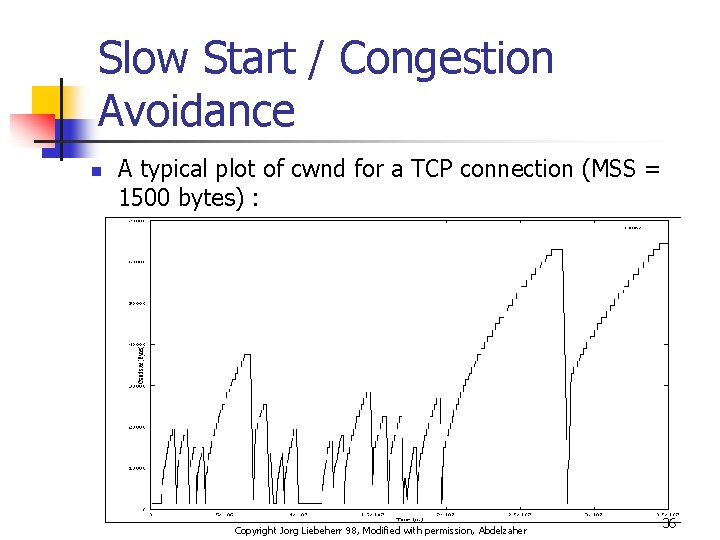
Slow Start / Congestion Avoidance n A typical plot of cwnd for a TCP connection (MSS = 1500 bytes) : Copyright Jorg Liebeherr 98, Modified with permission, Abdelzaher 36

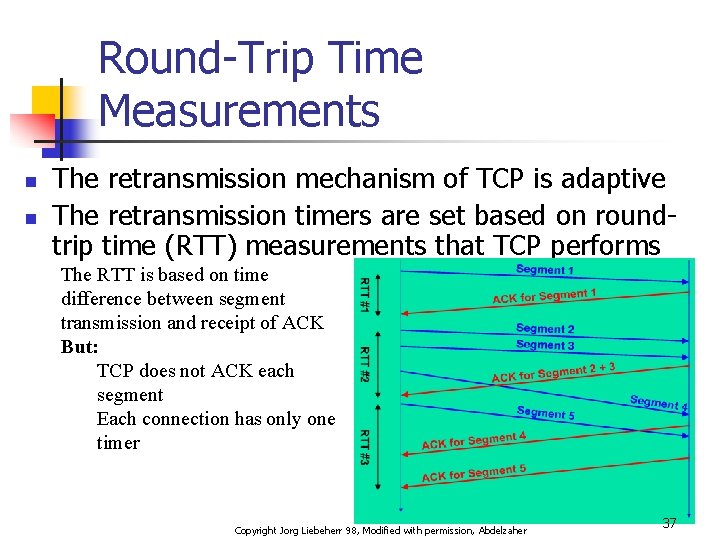
Round-Trip Time Measurements n n The retransmission mechanism of TCP is adaptive The retransmission timers are set based on roundtrip time (RTT) measurements that TCP performs The RTT is based on time difference between segment transmission and receipt of ACK But: TCP does not ACK each segment Each connection has only one timer Copyright Jorg Liebeherr 98, Modified with permission, Abdelzaher 37

Round-Trip Time Measurements n n n Retransmission timer is set to a Retransmission Timeout (RTO) value RTO is calculated based on the RTT measurements The RTT measurements are smoothed by the following estimators srtt and rttvar: srttn+1 = a RTT + (1 - a ) srttn rttvarn+1 = b ( | RTT - srttn+1 | ) + (1 - b ) rttvarn RTOn+1 = srttn+1 + 4 rttvarn+1 n The gains are set to a =1/4 and b =1/8 n srtt 0 = 0 sec, rttvar 0 = 3 sec, Also: RTO 0 = srtt 0 + 2 rttvar 0 Copyright Jorg Liebeherr 98, Modified with permission, Abdelzaher 38

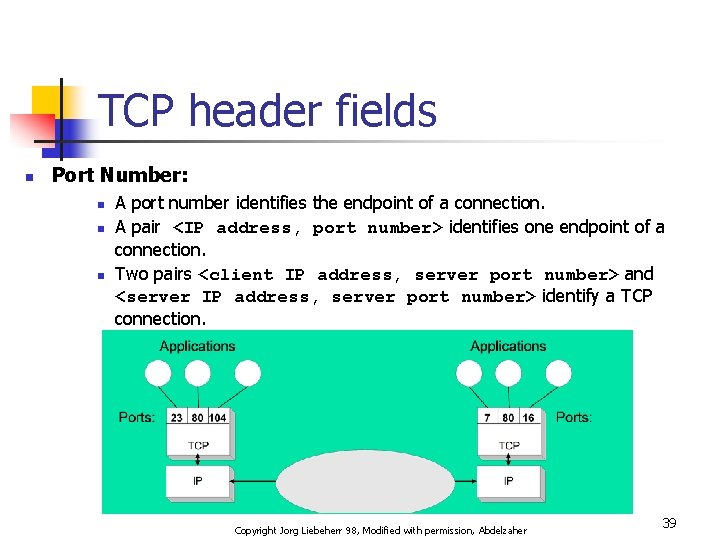
TCP header fields n Port Number: n n n A port number identifies the endpoint of a connection. A pair <IP address, port number> identifies one endpoint of a connection. Two pairs <client IP address, server port number> and <server IP address, server port number> identify a TCP connection. Copyright Jorg Liebeherr 98, Modified with permission, Abdelzaher 39

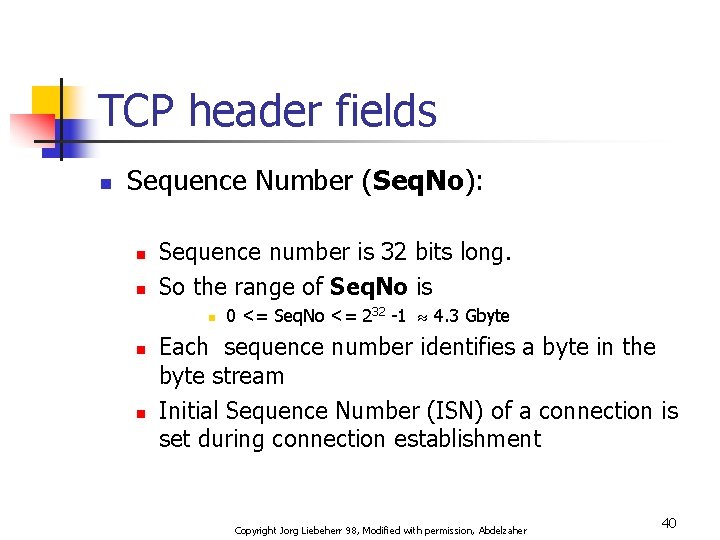
TCP header fields n Sequence Number (Seq. No): n n Sequence number is 32 bits long. So the range of Seq. No is n n n 0 <= Seq. No <= 232 -1 4. 3 Gbyte Each sequence number identifies a byte in the byte stream Initial Sequence Number (ISN) of a connection is set during connection establishment Copyright Jorg Liebeherr 98, Modified with permission, Abdelzaher 40

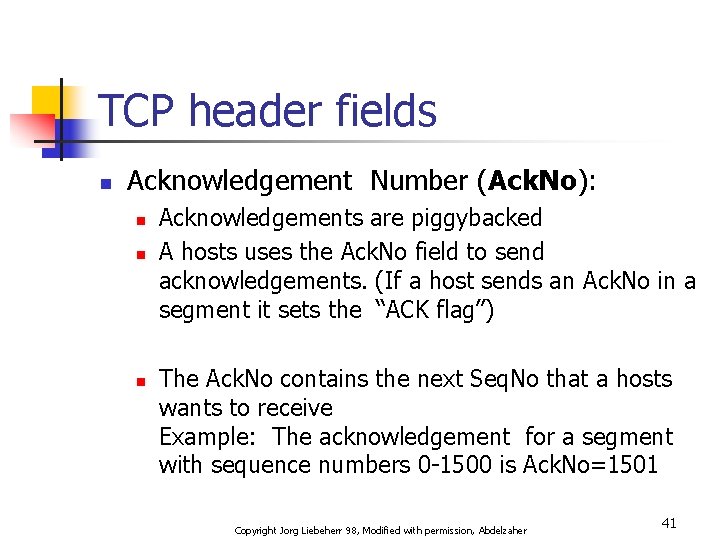
TCP header fields n Acknowledgement Number (Ack. No): n n n Acknowledgements are piggybacked A hosts uses the Ack. No field to send acknowledgements. (If a host sends an Ack. No in a segment it sets the “ACK flag”) The Ack. No contains the next Seq. No that a hosts wants to receive Example: The acknowledgement for a segment with sequence numbers 0 -1500 is Ack. No=1501 Copyright Jorg Liebeherr 98, Modified with permission, Abdelzaher 41

TCP header fields n Flag bits: n URG: Urgent pointer is valid n n n If the bit is set, the following bytes contain an urgent message in the sequence number range “Seq. No <= urgent message <= Seq. No+urgent pointer” ACK: Segment carries a valid acknowledgement PSH: PUSH Flag n n Notification from sender to the receiver that the receiver should pass all data that it has to the application. Normally set by sender when the sender’s buffer is empty Copyright Jorg Liebeherr 98, Modified with permission, Abdelzaher 42

TCP header fields n Flag bits: n RST: Reset the connection n SYN: Synchronize sequence numbers n n The flag causes the receiver to reset the connection Receiver of a RST terminates the connection and indicates higher layer application about the reset Sent in the first packet when initiating a connection FIN: Sender is finished with sending n n Used for closing a connection Both sides of a connection must send a FIN Copyright Jorg Liebeherr 98, Modified with permission, Abdelzaher 43

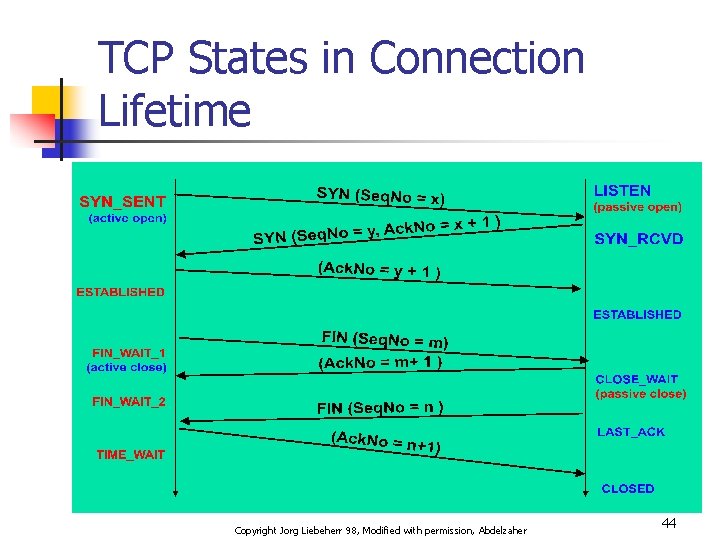
TCP States in Connection Lifetime Copyright Jorg Liebeherr 98, Modified with permission, Abdelzaher 44