Chapter 6 2 TCP Protocol The Internet Transport



- Slides: 40

Chapter 6 -2 TCP Protocol

The Internet Transport Protocols: TCP • • • Introduction to TCP The TCP Service Model The TCP Protocol The TCP Segment Header TCP Connection Management TCP Flow Control TCP Congestion Control TCP Timer Management Wireless TCP and UDP

TCP/IP protocol suite

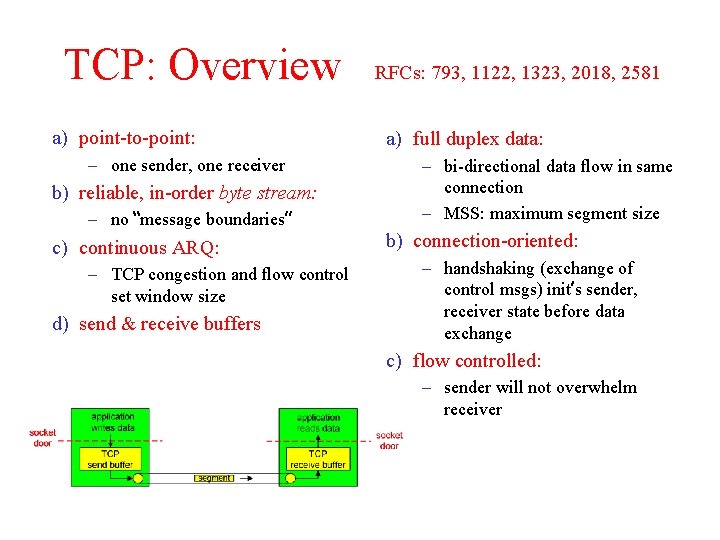
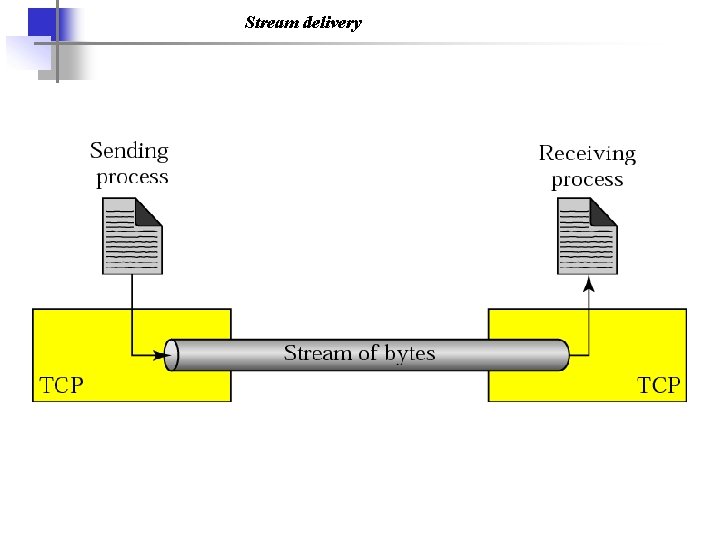
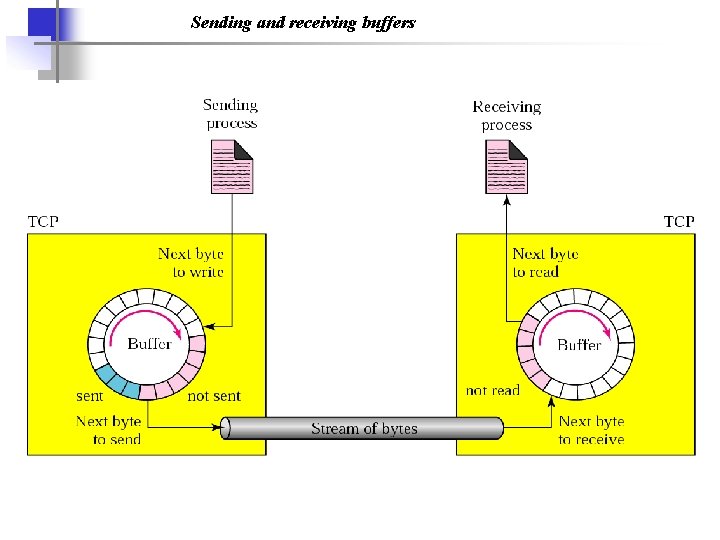
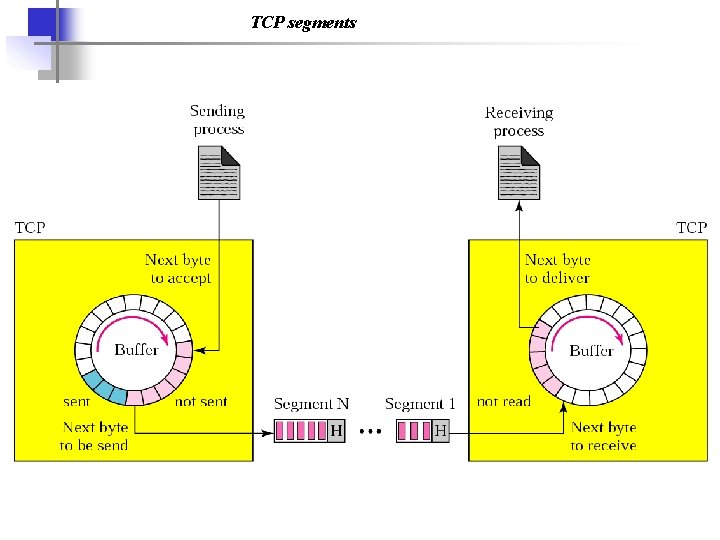
TCP: Overview a) point-to-point: – one sender, one receiver b) reliable, in-order byte stream: – no “message boundaries” c) continuous ARQ: – TCP congestion and flow control set window size d) send & receive buffers RFCs: 793, 1122, 1323, 2018, 2581 a) full duplex data: – bi-directional data flow in same connection – MSS: maximum segment size b) connection-oriented: – handshaking (exchange of control msgs) init’s sender, receiver state before data exchange c) flow controlled: – sender will not overwhelm receiver

TCP SERVICES Connection-Oriented Service Process-to-Process Communication Stream Delivery Service Full-Duplex Communication Reliable Service

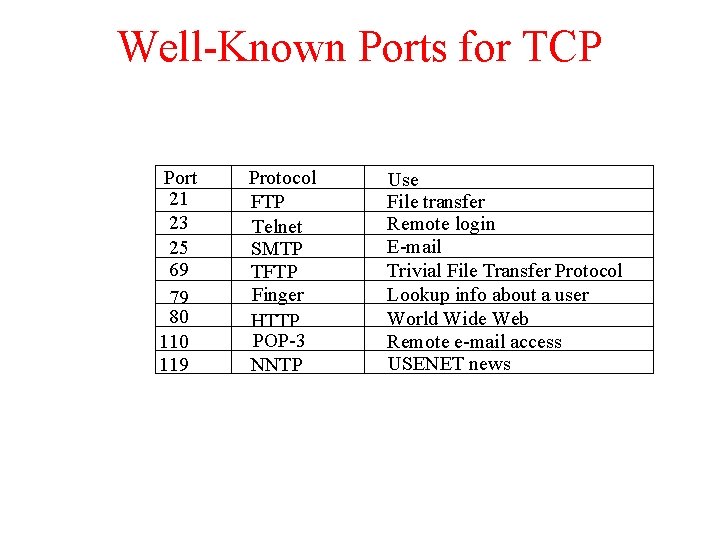
Well-Known Ports for TCP Port 21 23 25 69 79 80 119 Protocol FTP Telnet SMTP TFTP Finger HTTP POP-3 NNTP Use File transfer Remote login E-mail Trivial File Transfer Protocol Lookup info about a user World Wide Web Remote e-mail access USENET news

Stream delivery

Sending and receiving buffers

TCP segments

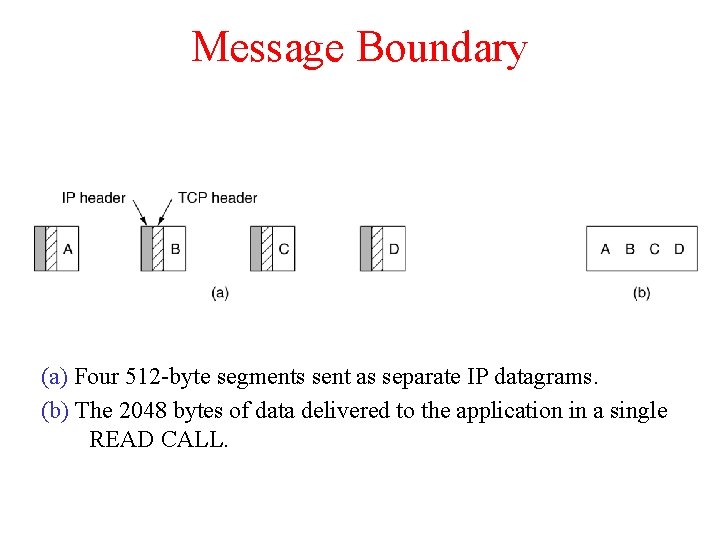
Message Boundary (a) Four 512 -byte segments sent as separate IP datagrams. (b) The 2048 bytes of data delivered to the application in a single READ CALL.

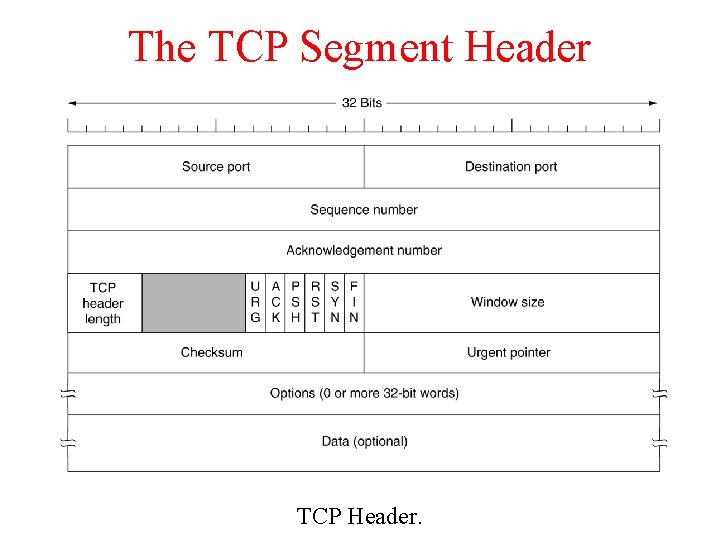
The TCP Segment Header TCP Header.

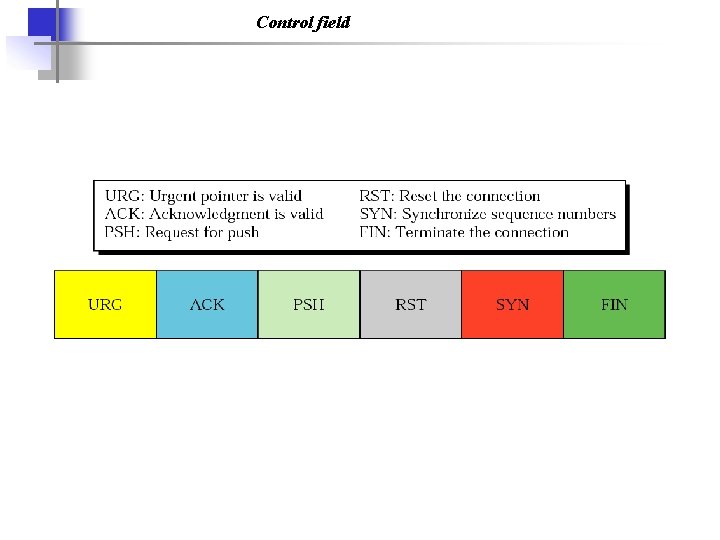
Control field

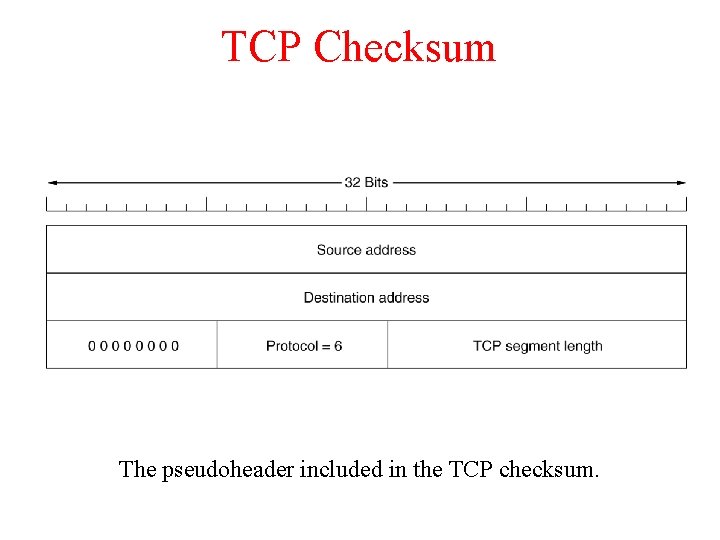
TCP Checksum The pseudoheader included in the TCP checksum.

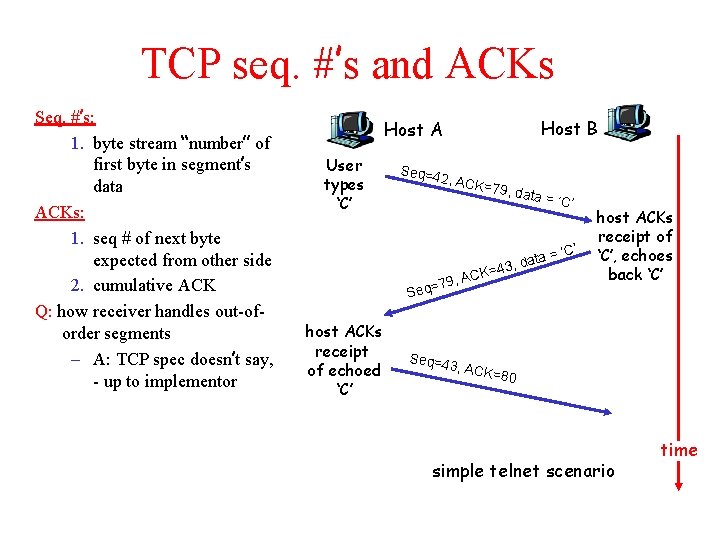
TCP seq. #’s and ACKs Seq. #’s: 1. byte stream “number” of first byte in segment’s data ACKs: 1. seq # of next byte expected from other side 2. cumulative ACK Q: how receiver handles out-oforder segments – A: TCP spec doesn’t say, - up to implementor Host B Host A User types ‘C’ Seq=4 2, ACK = 79, da ta ata = d , 3 4 K= , AC q=79 Se host ACKs receipt of echoed ‘C’ = ‘C’ host ACKs receipt of ‘C’, echoes back ‘C’ Seq=4 3, ACK =80 simple telnet scenario time

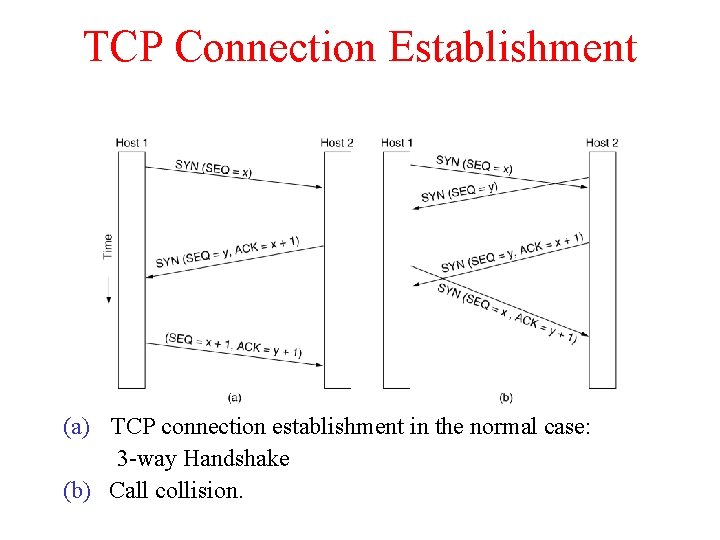
TCP Connection Establishment 6 -31 (a) TCP connection establishment in the normal case: 3 -way Handshake (b) Call collision.

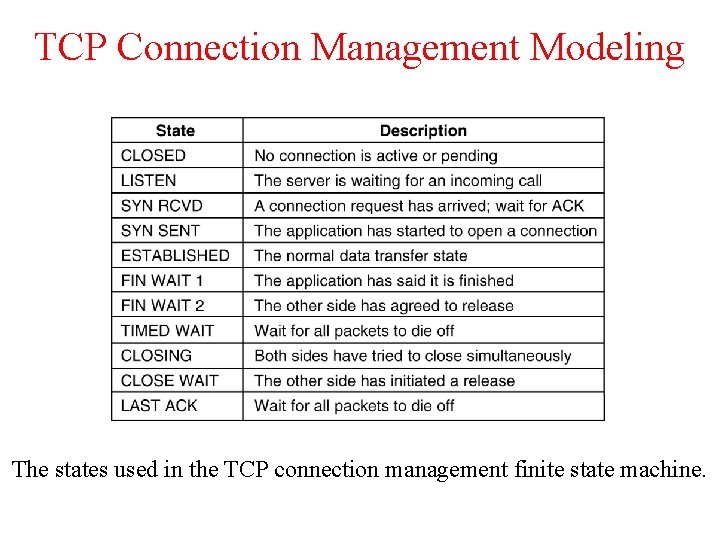
TCP Connection Management Modeling The states used in the TCP connection management finite state machine.

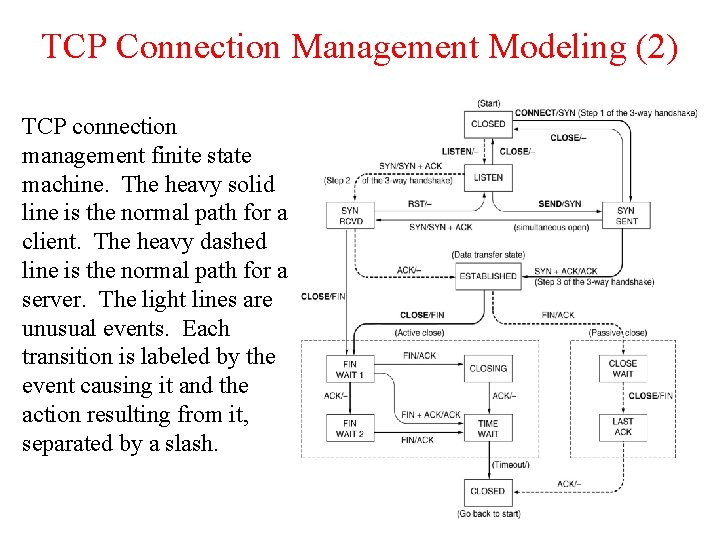
TCP Connection Management Modeling (2) TCP connection management finite state machine. The heavy solid line is the normal path for a client. The heavy dashed line is the normal path for a server. The light lines are unusual events. Each transition is labeled by the event causing it and the action resulting from it, separated by a slash.

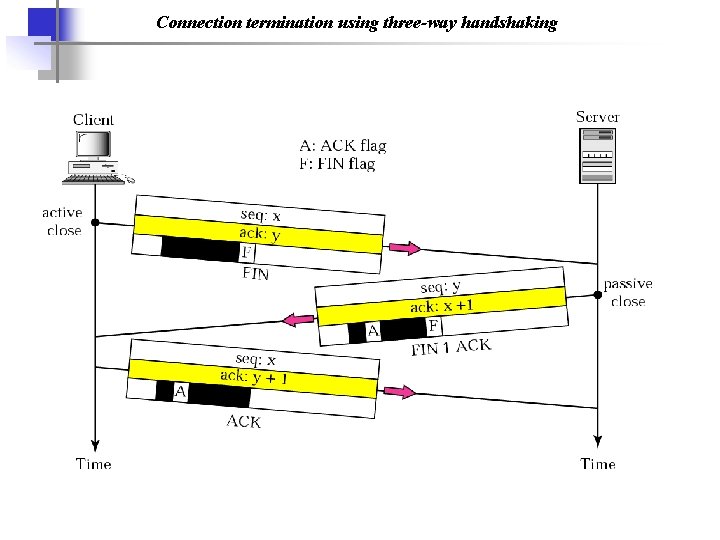
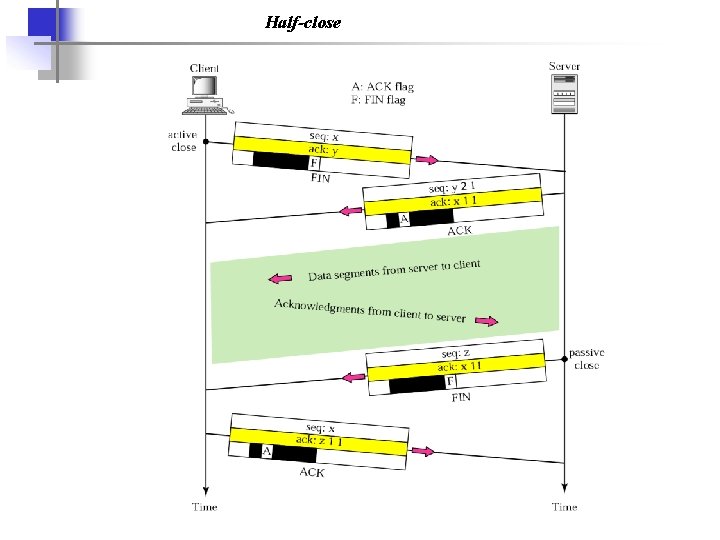
Connection termination using three-way handshaking

Half-close

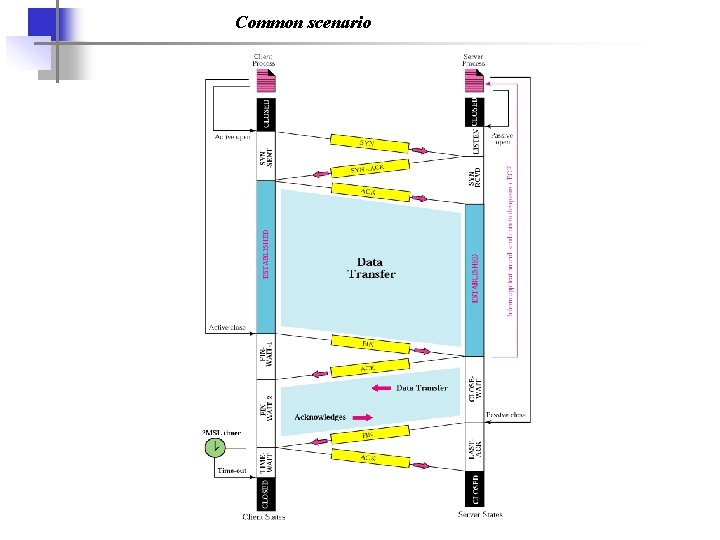
Common scenario

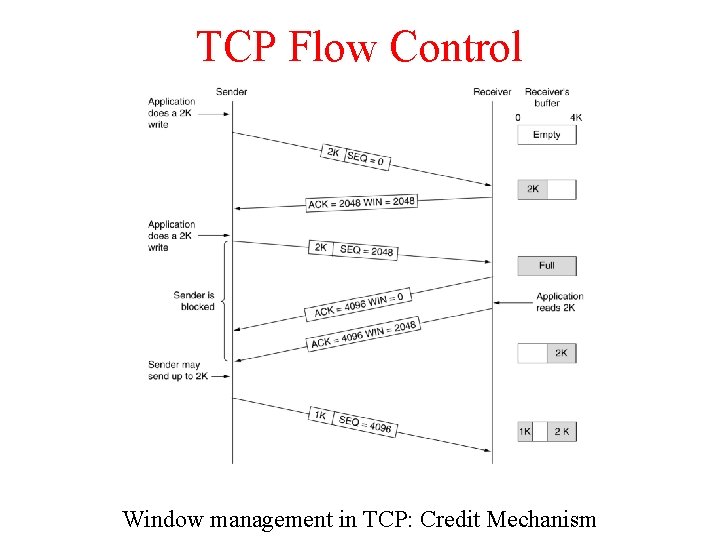
TCP Flow Control Window management in TCP: Credit Mechanism

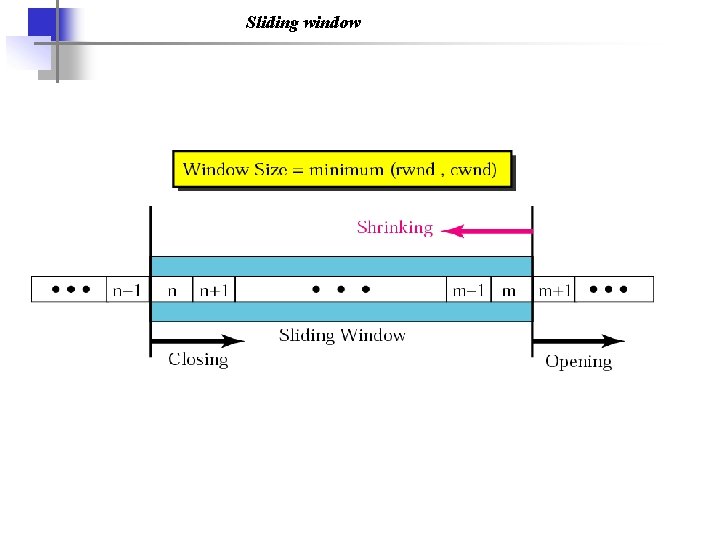
Sliding window

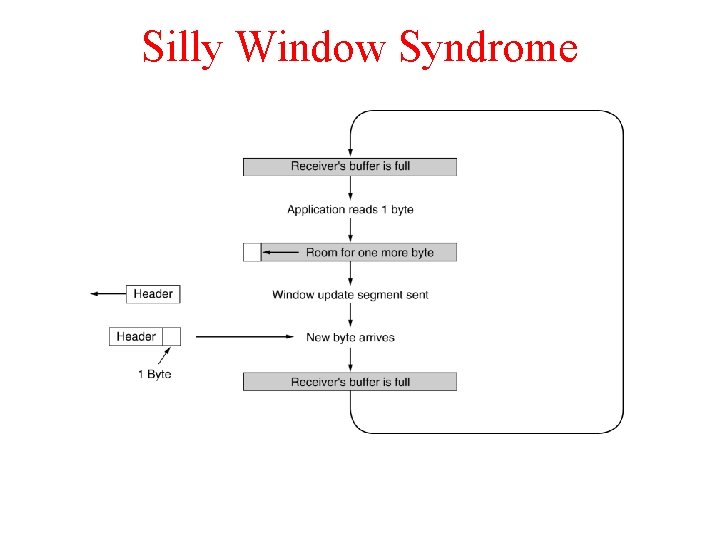
Silly Window Syndrome

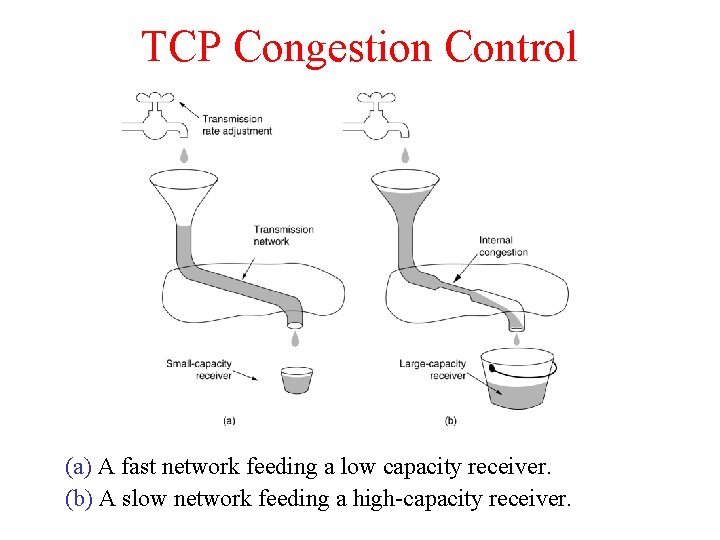
TCP Congestion Control (a) A fast network feeding a low capacity receiver. (b) A slow network feeding a high-capacity receiver.

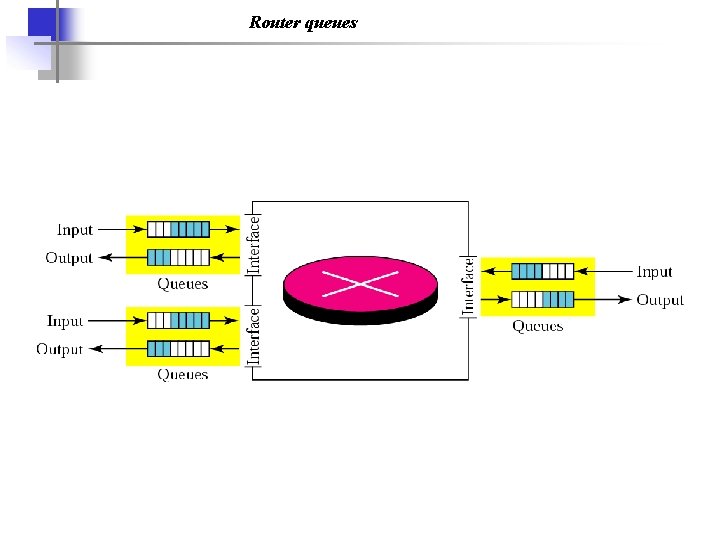
Router queues

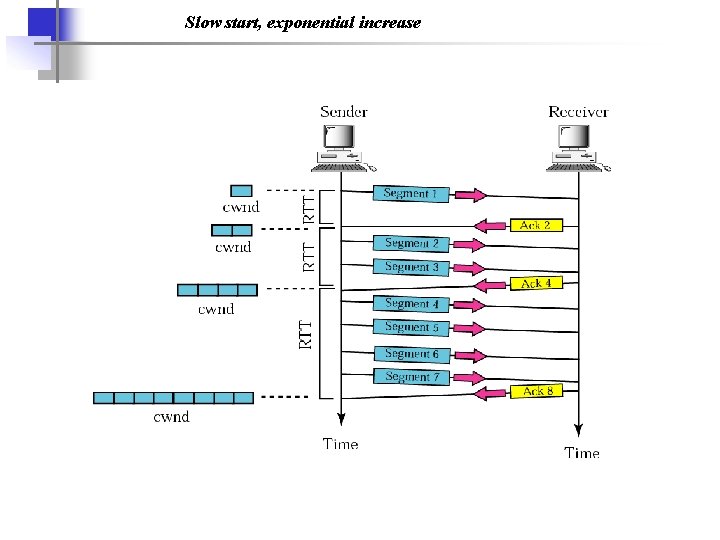
Slow start, exponential increase

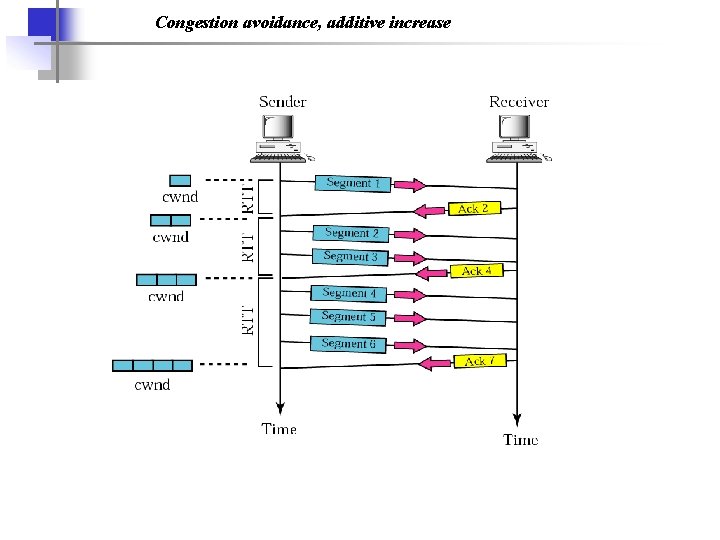
Congestion avoidance, additive increase

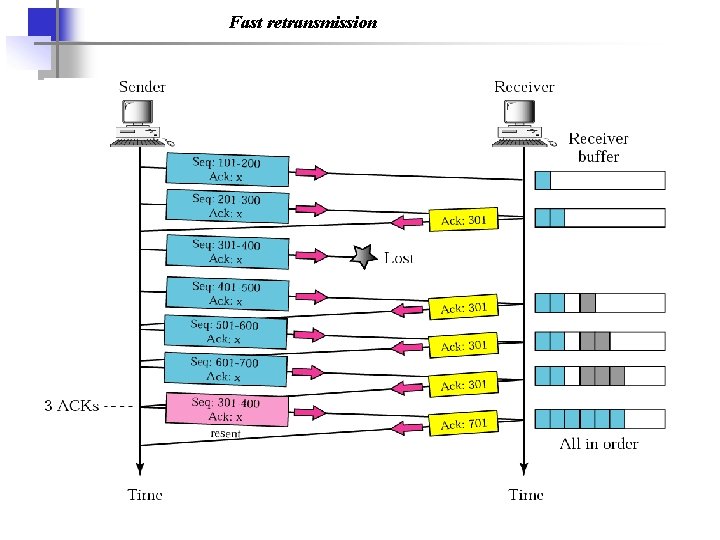
Fast retransmission

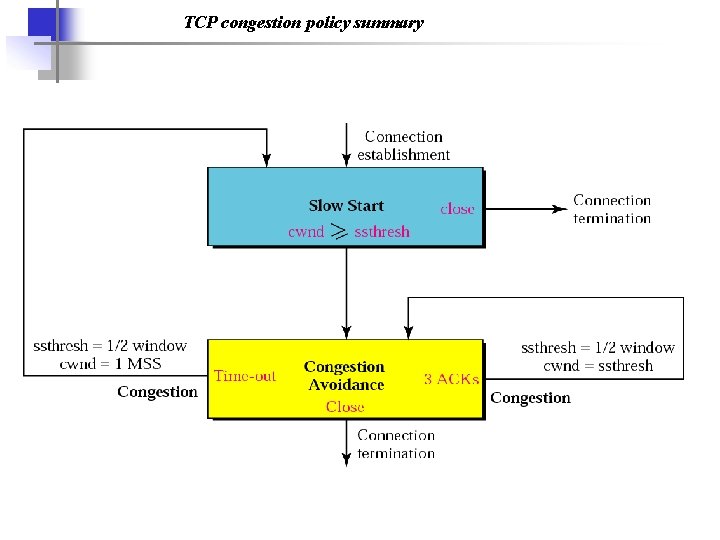
TCP congestion policy summary

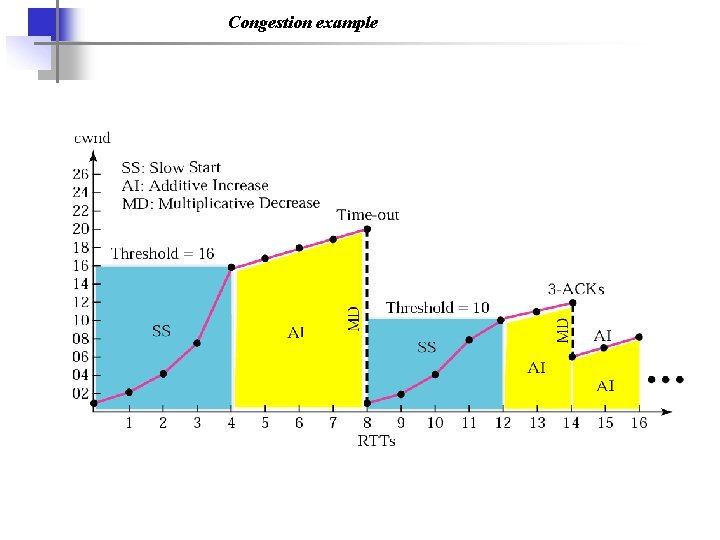
Congestion example

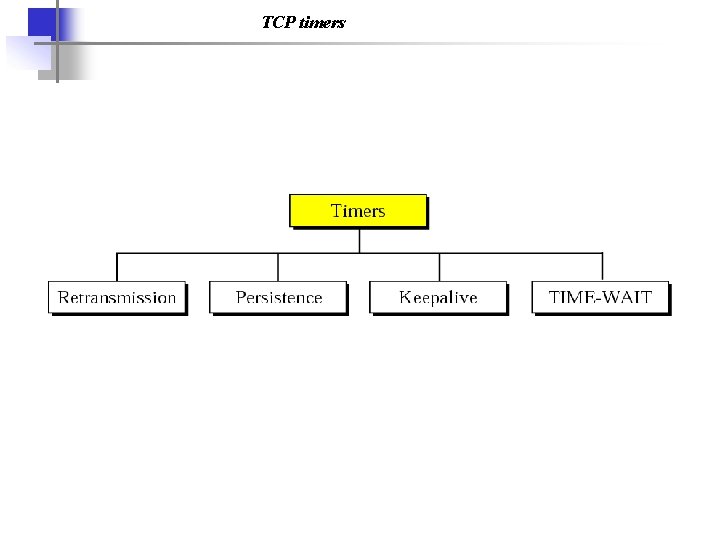
TCP timers

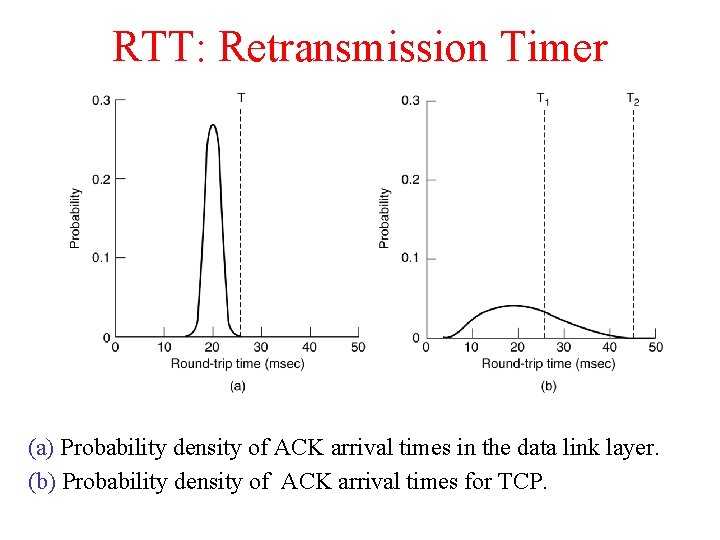
RTT: Retransmission Timer (a) Probability density of ACK arrival times in the data link layer. (b) Probability density of ACK arrival times for TCP.

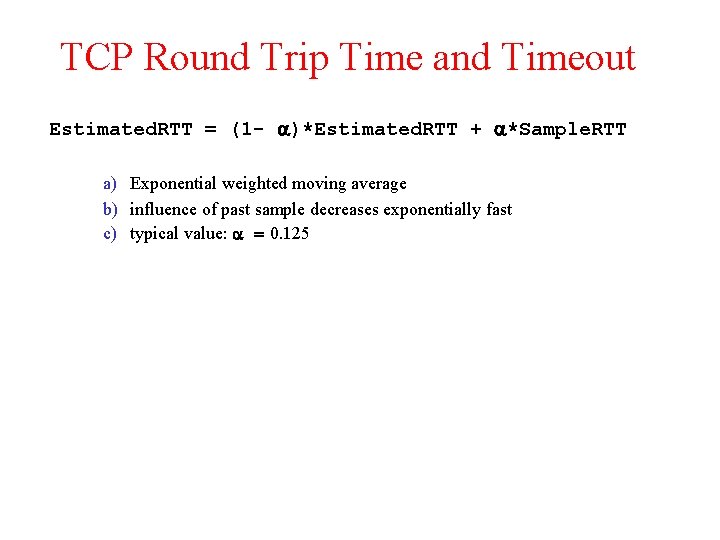
TCP Round Trip Time and Timeout Estimated. RTT = (1 - )*Estimated. RTT + *Sample. RTT a) Exponential weighted moving average b) influence of past sample decreases exponentially fast c) typical value: = 0. 125

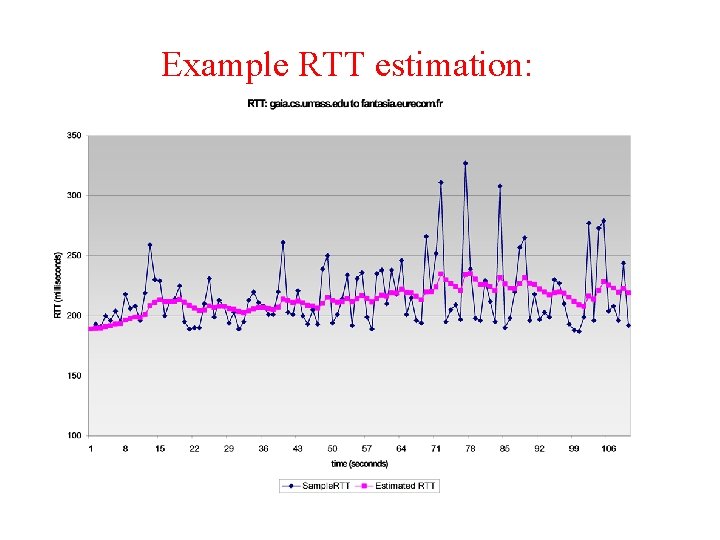
Example RTT estimation:

TCP Round Trip Time and Timeout Setting the timeout a) Estimted. RTT plus “safety margin” – large variation in Estimated. RTT -> larger safety margin b) first estimate of how much Sample. RTT deviates from Estimated. RTT: Dev. RTT = (1 - )*Dev. RTT + *|Sample. RTT-Estimated. RTT| (typically, = 0. 25) Then set timeout interval: Timeout. Interval = Estimated. RTT + 4*Dev. RTT

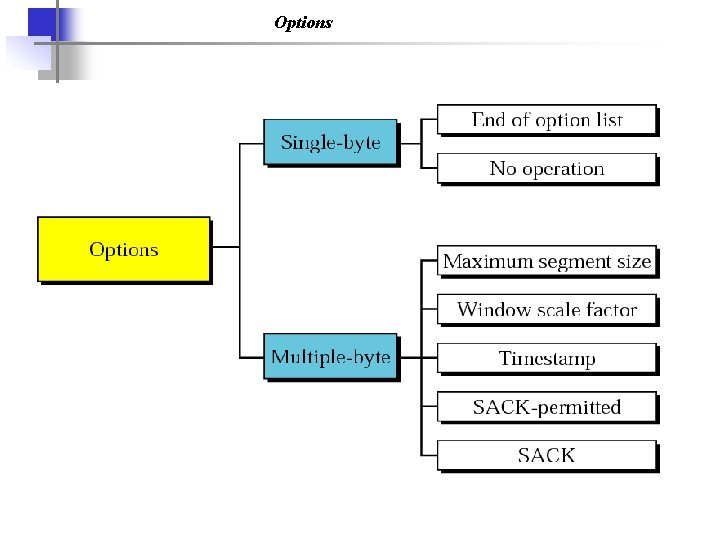
Options

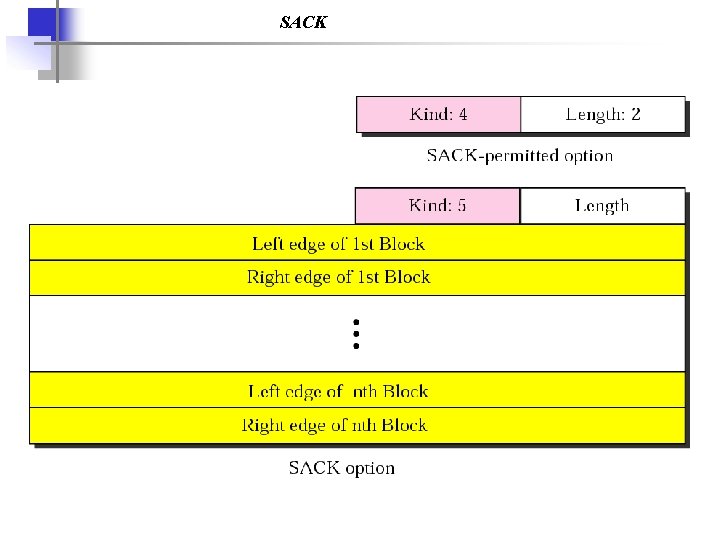
SACK

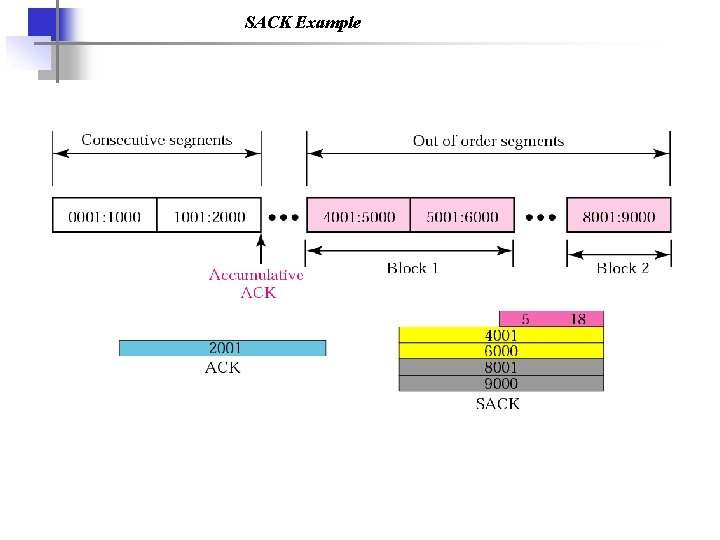
SACK Example

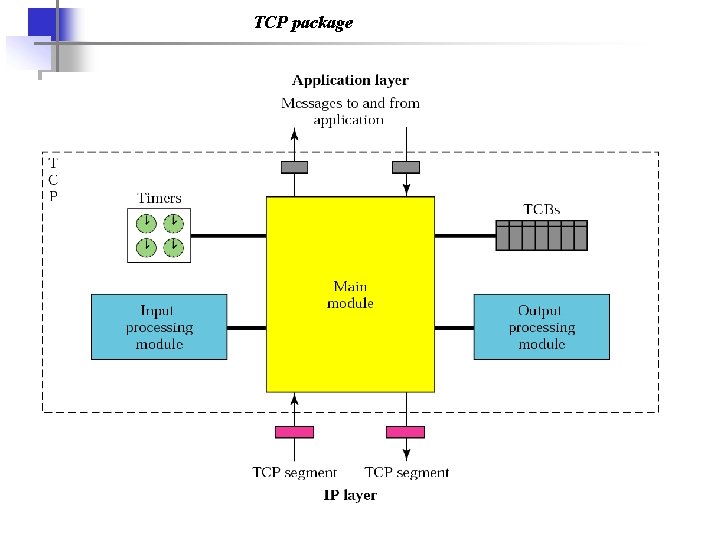
TCP package

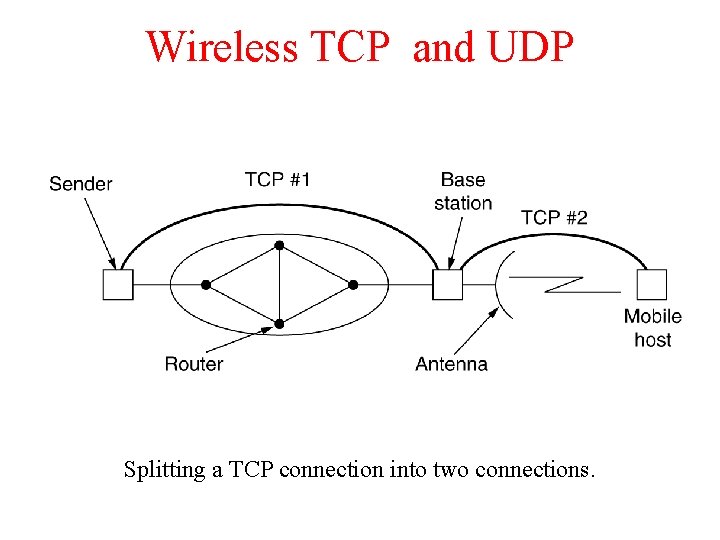
Wireless TCP and UDP Splitting a TCP connection into two connections.