Computer Networks 2 The Internet Transport Protocol 10262020


- Slides: 71

Computer Networks 2 The Internet Transport Protocol 10/26/2020 Veton Këpuska 1

The Internet Transport Protocols o Internet has two main protocols in transport layer: n n o Connectionless Protocol (UDP), and Connection-oriented Protocol (TCP). UPD (User Datagram Protocol) n n UDP is IP with just a short header added. UDP provides a way for applications to send encapsulated UP datagrams and send them without having to establish a connection. 10/26/2020 Veton Këpuska 2

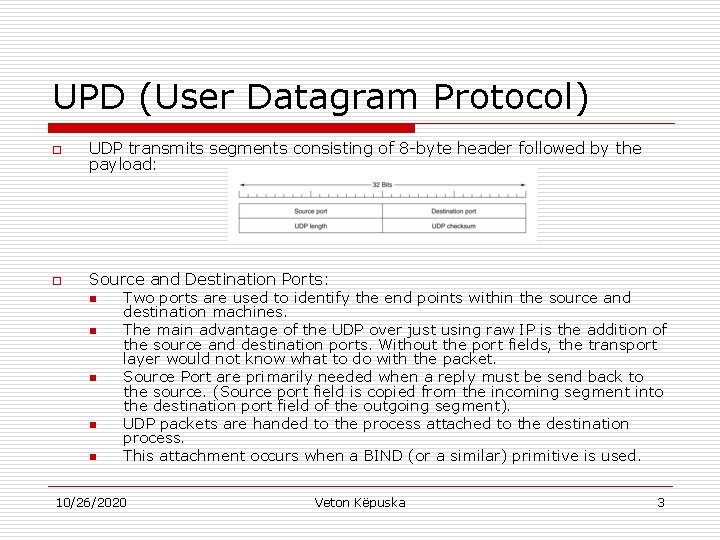
UPD (User Datagram Protocol) o UDP transmits segments consisting of 8 -byte header followed by the payload: o Source and Destination Ports: n n n Two ports are used to identify the end points within the source and destination machines. The main advantage of the UDP over just using raw IP is the addition of the source and destination ports. Without the port fields, the transport layer would not know what to do with the packet. Source Port are primarily needed when a reply must be send back to the source. (Source port field is copied from the incoming segment into the destination port field of the outgoing segment). UDP packets are handed to the process attached to the destination process. This attachment occurs when a BIND (or a similar) primitive is used. 10/26/2020 Veton Këpuska 3

UPD (User Datagram Protocol) o UDP length field: n o UDP Checksum: n o Optional field. What UDP does not do: n n n o Includes 80 -byte header and payload data. Flow Control Error Control Retransmission upon receipted of a bad segment. User application responsible for control over the packet flow, error control and timing. 10/26/2020 Veton Këpuska 4

UPD (User Datagram Protocol) o UDP useful in client-server situations: n n n o Client sends a short request to the server and expects a short reply back. If either the request or reply is lost, the client can just time out and try again. Simple code Fewer messages are required compared to protocols that require initial setup. Typical application using UDP is DNS (the Domain Name System). n n n An application that needs to look up the IP address of some host name (e. g. , www. cs. berkeley. edu) can send a UDP packet containing the host name to a DSN server. Server replies with a UDP packet containing the host’s IP address. No setup is needed in advance and no release is needed afterward. Just two messages go over the network. 10/26/2020 Veton Këpuska 5

Remote Procedure Call o o Sending a message to a remote host and getting a reply back, in a certain sense is a lot like making a function call in a programming language: Request/Reply interactions on network are cast in the form of procedure calls. n o Example: procedure get_IP_address(host_name); that works by sending a UDP packet to a DNS server and waiting for the reply, timing out and trying again if one is not forthcoming quickly enough. Remote Procedure Call – RPC technique that allows: n n A process on machine 1 to call a procedure on machine 2 The calling process on 1 is suspended and Execution of the called procedure takes place on 2. Information can be transported from the caller to the callee in the parameters and can come in the procedure result. No message passing is visible to the programmer. 10/26/2020 Veton Këpuska 6

Remote Procedure Call o The idea behind RPC is to make a remote procedure call look as much as possible like a local one. n n This is done using client stub (small library that represents server procedure in the client's address space) and server stub (similarly a small library that represents client procedure in the servers address space). Actual steps in making an RPC are shown if Fig. 6 -24. 10/26/2020 Veton Këpuska 7

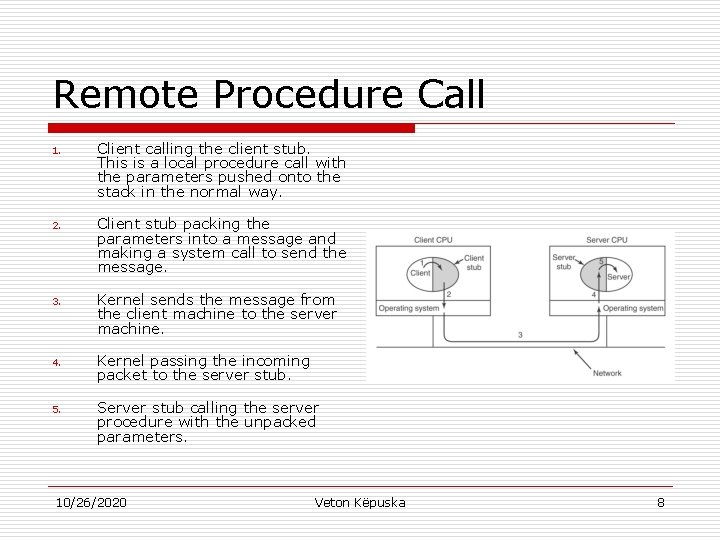
Remote Procedure Call 1. Client calling the client stub. This is a local procedure call with the parameters pushed onto the stack in the normal way. 2. Client stub packing the parameters into a message and making a system call to send the message. 3. Kernel sends the message from the client machine to the server machine. 4. Kernel passing the incoming packet to the server stub. 5. Server stub calling the server procedure with the unpacked parameters. 10/26/2020 Veton Këpuska 8

Remote Procedure Call o o Client Procedure (written by the user) makes a usual (i. e. , local) procedure call to the client stub, which has the same name as the server procedure. Since the client procedure and client stub are in the same address space, the parameters are passed in the usual way. Server Procedure in similar function is called by a procedure in its address space with the parameters it expects. To the server procedure nothing is unusual. In this way instead of I/O being done on sockets, network communication is done by faking a normal procedure call. 10/26/2020 Veton Këpuska 9

Remote Procedure Call o Difficulties of RPC model with weakly-typed languages (like C). n n Passing pointers (stub must pass the data were the pointer is pointing to and deliver a copy and its pointer to the server). Arrays that do not have a preset size impossible to handle. When it is not possible to deduce a type of the parameters (e. g. , printf) the RPC is difficult. Global variables when the called procedure is moved to a remote machine. 10/26/2020 Veton Këpuska 10

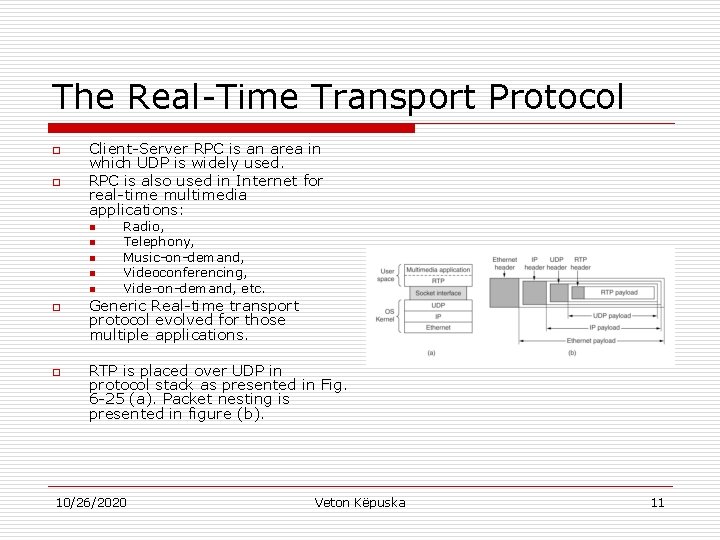
The Real-Time Transport Protocol o o Client-Server RPC is an area in which UDP is widely used. RPC is also used in Internet for real-time multimedia applications: n n n o o Radio, Telephony, Music-on-demand, Videoconferencing, Vide-on-demand, etc. Generic Real-time transport protocol evolved for those multiple applications. RTP is placed over UDP in protocol stack as presented in Fig. 6 -25 (a). Packet nesting is presented in figure (b). 10/26/2020 Veton Këpuska 11

The Real-Time Transport Protocol o Basic function of RTP is to multiplex several real-time data streams onto a single stream of UDP packets. n The UDP stream can be send to a single destination (unicasting) or to multiple destinations (multicasting). n Because RTP uses normal UDP there are no special guarantees about delivery, jitter, etc. n n Each RTP packet send is given a number one higher then its predecessor. This numbering allows the destination to determine if any packets are missing. If a packet is missing, the best action is to approximate the missing value by interpolation. Since retransmission is not a practical solution (real-time streaming) RTP does not do flow control, error control nor it does acknowledgments and it does not have mechanism to request retransmissions. 10/26/2020 Veton Këpuska 12

The Real-Time Transport Protocol o o Each RTP payload may contain multiple samples, and they may be coded differently. For this reason RTP defines several profiles (e. g. , single audio stream) and for each profile multiple coding formats may be allowed. n Single audio stream may be encoded as 8 -bit PCM samples at 8 k. Hz, delta encoding, predictive encoding, GSM encoding, MP 3, and so on. n RTP provides a header field (Payload type) in which the source can specify the encoding but it otherwise is not involved in encoding itself. RTP header has a timestamp field that is used to reduce jitter at the receiver. It also can be used to synchronize multiple streams (video, audio 1 of original sound, audio 2 of dubbed soundtrack). 10/26/2020 Veton Këpuska 13

The Real-Time Transport Protocol o o Real time Transport Control Protocol (RTCP) is a associated protocol to RTP that is used to handle feedback, synchronization and the user interfaces but does not transport any data. It is used to provide feedback on delay, jitter, bandwidth, congestion, and other network properties to the sources. n This information can be used by encoding process to o 10/26/2020 Increase the data rate (and give better quality) when the network is functioning well, and Decrease the data rate when there is trouble in the network. => Best possible quality under given circumstances. Veton Këpuska 14

The Internet Transport Protocols: TCP o o For some niche uses such as client-server interactions and multimedia UDP protocol is well suited. However, for most Internet applications where reliable, sequenced delivery is needed, UDP is not appropriate tool, so another protocol is needed. The protocol suitable for reliable delivery application is TCP is the main workhorse of the Internet. 10/26/2020 Veton Këpuska 15

Introduction to TCP (Transmission Control Protocol) n Specifically designed to provide reliable end-to-end byte stream over an unreliable inter-network. n An inter-network differs from a single network because different parts may have wildly different: o o o n Topologies, Bandwidths, Delays, Packet Sizes, Other parameters. TCP was designed to dynamically adapt to properties of the inter-network and to be robust in the face of many kinds of failures. 10/26/2020 Veton Këpuska 16

Introduction to TCP o Each machine supporting TCP has a TCP transport entity Library procedure, n User process, or n Part of the kernel. Which in either case manages TCP streams and interfaces to the IP layer. n o TCP entity accepts user data streams and n n n Breaks them up into pieces not exceeding 64 KB (in practice often 1460 data bytes in order to fit in a single Ethernet frame with the IP and TCP headers), Sends each piece as a separate IP datagram. When TCP data arrive, they are handled by TCP entity of that destination machine which reconstructs the original byte stream. Since IP layer gives no guarantee that datagrams will be delivered properly, it is up to TCP to time out and retransmit them as needed. Datagrams that do arrive may do so at the wrong order; thus it also up to TCP in the destination machine to reassemble them into messages in the proper sequence. 10/26/2020 Veton Këpuska 17

The TCP Service Model o TCP service is obtained by sender and receiver creating end points (sockets). n Each Socket has Socket Number (address) consisting of: o o o IP address of the host and 16 -bit number local to that host called port. (Port is a TCP name for Transport Service Access Point – TSAP). TCP service is obtained when a connection is explicitly established between a socket on the sending machine and a socket on the receiving machine. 10/26/2020 Veton Këpuska 18

The TCP Service Model o o A socket may be used for multiple connections at the same time. Connections are identified at both ends as (socket 1, socket 2). Port numbers bellow 1024 are called well-known ports and are used for standard services. A few of better know ports are listed in Fig. 6 -27. 10/26/2020 Veton Këpuska 19

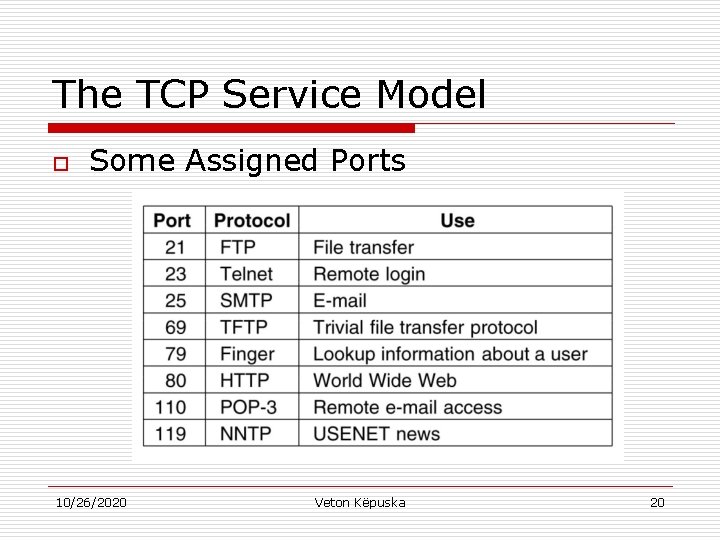
The TCP Service Model o Some Assigned Ports 10/26/2020 Veton Këpuska 20

The TCP Service Model o o All TCP connections are full duplex and point-to-point. TCP does not support multicasting nor broadcasting. A TCP connection is a byte stream not a message stream. Message boundaries are not preserved end-to-end. n If the sending process does 4 X 512 -byte writes to a TCP stream, these data may be delivered to the receiving process as 4 X 512 -byte chunks, 2 X 1024 -byte chunks or 1 X 2048 -byte chunk or some other way. (See Fig. 6 -28). 10/26/2020 Veton Këpuska 21

The TCP Service Model o o TCP may buffer the data before sending it. If application requires that the data be send immediately it can use the PUSH flag which indicates to TCP not to delay the transmission. One additional feature of TCP service worth mentioning is urgent data. n If sending application puts some control information in the data stream and gives it to TCP along with the URGENT flag it causes TCP to stop accumulating data and transmit everything it has for that connection immediately. (CTRL-C or DEL) n At the receiving end when this packet arrives the application in the destination is interrupted so it can stop whatever it was doing and read the data stream to find the urgent data. The end of the urgent data is marked so the application knows when it is over. 10/26/2020 Veton Këpuska 22

The TCP Protocol o o A key feature which dominates the protocol design is that every byte on a TCP connection has its own 32 bit sequence number. n In the early days of Internet when lines between routers were mostly 56 -kbps the TCP host working at its full speed took over 1 week to cycle through the sequence numbers. n At modern network speeds, the sequence numbers can be consumed at an alarming rate. Separate sequence numbers are used for: n Acknowledgments and n Window mechanism As explained next. 10/26/2020 Veton Këpuska 23

The TCP Protocol o o o TCP entities exchange data in the form of segments. A TCP segment consists of a fixed 20 -byte header (plus optional part) followed by zero or more data bytes. TCP software decides how big segments should be. n n It can accumulate data from several writes, or It can split data from one write over multiple segments. 10/26/2020 Veton Këpuska 24

The TCP Protocol o TCP Segment. Two limits restrict segment size: n n Each segment must fit in the 65, 515 byte IP payload. Each network has a maximum transfer unit (MTU) and each segment must fit in the MTU. o 10/26/2020 In practice the MTU is generally 1500 bytes (the Ethernet payload size) and thus defines the upper bound on segment size. Veton Këpuska 25

The TCP Protocol o Sliding Window Protocol: n n The basic protocol used by TCP entities. When a sender transmits a segment, it also starts a timer. Destination sends back a segment (upon receiving the senders segment) containing acknowledgment number equal to the next sequence number it expects to receive. If sender’s timer goes off before the acknowledgment is received, the sender transmits the segment again. 10/26/2020 Veton Këpuska 26

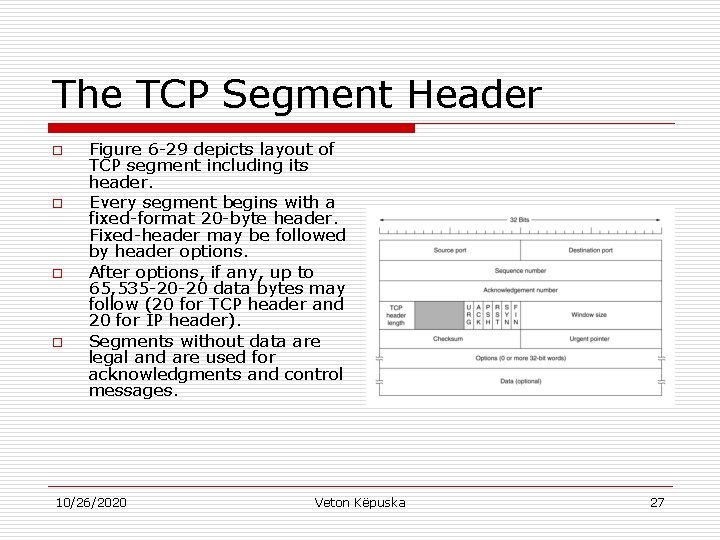
The TCP Segment Header o o Figure 6 -29 depicts layout of TCP segment including its header. Every segment begins with a fixed-format 20 -byte header. Fixed-header may be followed by header options. After options, if any, up to 65, 535 -20 -20 data bytes may follow (20 for TCP header and 20 for IP header). Segments without data are legal and are used for acknowledgments and control messages. 10/26/2020 Veton Këpuska 27

The TCP Segment Header o o Source and Destination Port fields. n Identify local end points of the connection. n Well-known ports are defined at www. iana. org n Port + host’s IP address forms a 48 -bit unique endpoint. The source and destination end-points together identify the connection. Sequence Number and Acknowledgment Number fields. n Sequence number identifies the byte number of a sequence of a transmission. n Acknowledgment Number specifies the next byte expected (NOT the last byte correctly received). n Both are 32 bits long because every byte of data is numbered in TCP stream. 10/26/2020 Veton Këpuska 28

The TCP Segment Header o TCP header length. n n o It specifies how many 32 -bit words are contained in the TCP header. This information is needed because of the Options field which makes overall header of variable length. 6 -bit Unused field. n The fact that this field has survived intact for over a quarter of century is testimony to how well thought out TCP is. 10/26/2020 Veton Këpuska 29

The TCP Segment Header o Six 1 -bit flags: n URG is set to 1 if Urgent Pointer is in use. Urgent Pointer itself is used to indicate a byte offset from the current sequence number at which urgent data are to be found. o n This facility is used in lieu of interrupt messages. It allows sender to signal the receiver without getting TCP itself involved in the reason for the interrupt. ACK bit is set to 1 to indicate that the Acknowledgment number is valid. If ACK is 0, the segment does not contain an acknowledgment so the Acknowledgment number field is ignored. 10/26/2020 Veton Këpuska 30

The TCP Segment Header o Six 1 -bit flags (cont): n n PSH bit indicates PUSHed data. The receiver is kindly requested to deliver the data to the application upon arrival and not to be buffered and delivered when buffer is full. RST bit is used to reset a connection that has become confused due to a host crash or some other reason. It is also used to reject an invalid segment or refuse an attempt to open a connection. In general, if segment has RST bit on, it indicates that there is a problem of a sort that needs special handling. 10/26/2020 Veton Këpuska 31

The TCP Segment Header n SYN bit is used to establish connections. If SYN=1 and ACK=0 indicates that the piggyback acknowledgment field is not in use. If connection reply does bear an acknowledgment then this is indicated by SYN=1 and ACK=1. o o n In essence SYN bit is used to denote CONNECTION REQUEST and CONNECTION ACCEPTED. The ACK-bit is used to distinguish between those two possibilities. FIN bit is used to release connection. It indicates that the sender has no more data to transmit. o o 10/26/2020 After closing a connection the closing process may continue indefinitely to receive data. This is because TCP is full-duplex connection. Both SYN and FIN segments have sequence numbers and are thus guaranteed to be processed in the correct order. Veton Këpuska 32

The TCP Segment Header o Flow Control: n n TCP does Flow Control by using a variable-sized sliding window. Window Size field specifies how many bytes may be sent starting at the byte acknowledged. o A window size of 0 indicates that the bytes up to and including Acknowledgment number-1 have been received but the receiver can not accept more data at a moment. o The receiver can later grant permission to send by transmitting a segment with the same Acknowledgment number and a nonzero Window size field. 10/26/2020 Veton Këpuska 33

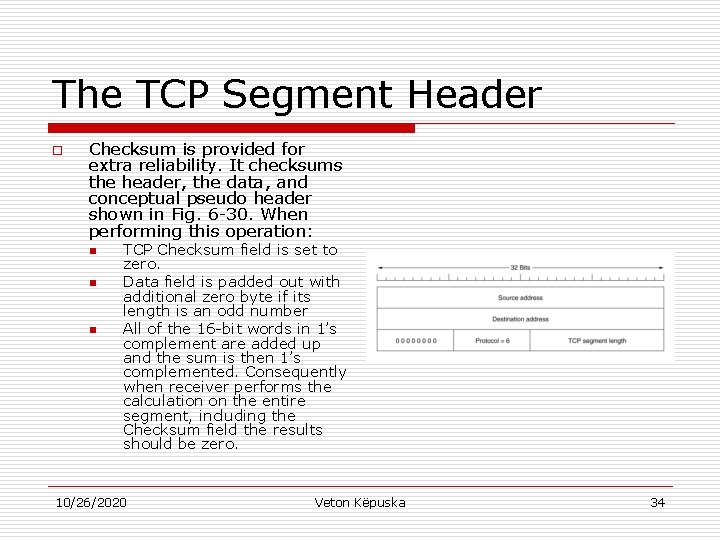
The TCP Segment Header o Checksum is provided for extra reliability. It checksums the header, the data, and conceptual pseudo header shown in Fig. 6 -30. When performing this operation: n n n TCP Checksum field is set to zero. Data field is padded out with additional zero byte if its length is an odd number All of the 16 -bit words in 1’s complement are added up and the sum is then 1’s complemented. Consequently when receiver performs the calculation on the entire segment, including the Checksum field the results should be zero. 10/26/2020 Veton Këpuska 34

The TCP Segment Header o The pseudo-header contains n n The 32 -bit IP addresses of the source and destination machines, Protocol number for TCP (6), and Byte count for the TCP segment (including header) Including pseudo-header in the TCP checksum computation helps detect miss-delivered packets. However including it violates the protocol hierarchy since the IP addresses in it belong to IP layer - not to the TCP layer. 10/26/2020 Veton Këpuska 35

The TCP Segment Header o The Options field provides a way to add extra facilities not covered by the regular header. n n n The most important option is the one that allows each host to specify the maximum TCP payload it is willing to accept. Using large segment it is more efficient than using small ones. However, small hosts may not be able to handle big segments. During connection setup, each side can announce its maximum. If a host does not use this option it defaults to a 536 -byte payload. o All internet hosts are required to accept TCP segments of 536+20=556 bytes. 10/26/2020 Veton Këpuska 36

The TCP Segment Header o For lines with: n n n High bandwidth, or High delay, or both the 64 KB window is often a problem. Example: T 3 line (44. 736 Mbts) it takes only 12 msec to output a full 64 -KB window. If round trip delay is 50 msec (typical for transcontinental fiber) the sender will be idle ¾ of the time waiting for acknowledgements. On a satellite connection the situation is even worse. o o 10/26/2020 With 16 -bit window size field there is no way to express larger window size. Window scale option was proposed allowing the sender and receiver to negotiate a window scale factor. This number allows both sides to shift the Window size field up to 14 bits to the left, thus allowing windows of up to 230 bytes. Veton Këpuska 37

The TCP Segment Header o Selective Repeat instead of go-back-n protocol. n n If the receiver gets one bad segment and then a large number of good ones the normal TCP protocol will eventually time out and retransmit all the unacknowledged segments, including all those that were received correctly (i. e. , go-backn protocol). Newly introduced protocol allow NAKs to ask for a specific segment (or segments) upon reception of which it can acknowledge all the buffered data thus reducing amount of data transmitted. 10/26/2020 Veton Këpuska 38

TCP Connection Establishment o Connections in TCP are established by means of threeway handshake (introduced earlier). n n To establish a connection one side (i. e. , server), passively waits for an incoming connection by executing the LISTEN and ACCEPT primitives. The other side (i. e. , client) executes CONNECT primitive specifying: o o o n IP address and port to which it wants to connect too. Maximum TCP segment it is willing to accept, and Optionally some user specific information (e. g. , password). CONNECT primitive sends a TCP segment with SYN=1 and ACK=0 and waits for response. 10/26/2020 Veton Këpuska 39

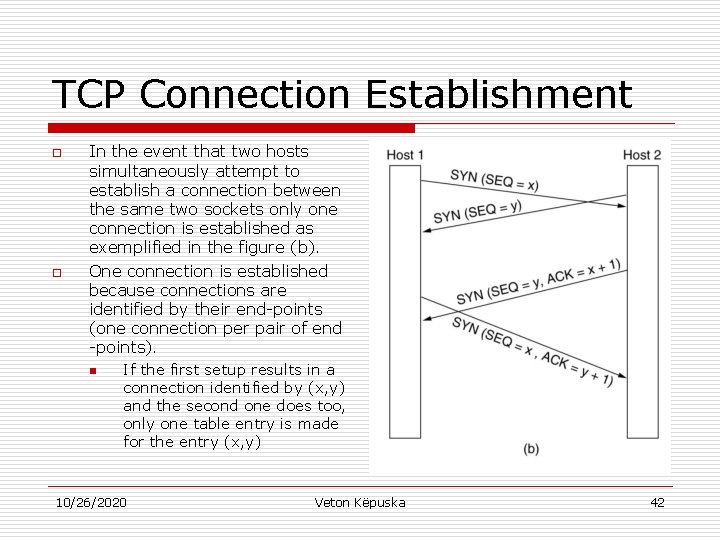
n When this TCP segment arrives at the destination, TCP entity there checks to see if there is a process that has done a LISTEN on the port given in the Destination port field. o o n If not it sends a reply with the RST bit on (RST=1) to reject the connection. If some process is listening to the port that process is given that TCP segment. This process then can accept or reject the connection. If it is accepted the normal case is shown if Fig. 6 -31(a). (SYN segment consumes byte of sequence space so that it can be acknowledged unambigously). The case of two hosts simultaneously attempting to establish a connection between the same two sockets is presented in Fig. 6 -31(b). The result of these events is that just one connection is established. 10/26/2020 Veton Këpuska 40

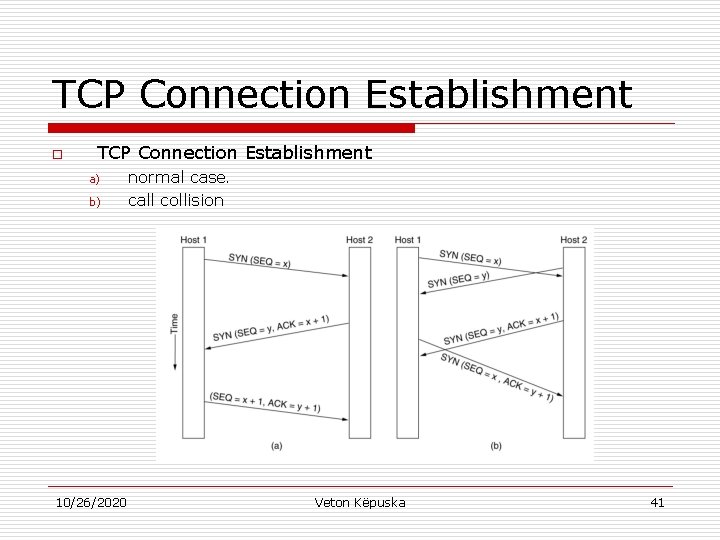
TCP Connection Establishment o TCP Connection Establishment a) b) 10/26/2020 normal case. call collision Veton Këpuska 41

TCP Connection Establishment o o In the event that two hosts simultaneously attempt to establish a connection between the same two sockets only one connection is established as exemplified in the figure (b). One connection is established because connections are identified by their end-points (one connection per pair of end -points). n If the first setup results in a connection identified by (x, y) and the second one does too, only one table entry is made for the entry (x, y) 10/26/2020 Veton Këpuska 42

TCP Connection Release o TCP connections are full duplex. n n o To release a connection: n n o Either party can send a TCP segment with the FIN bit set (no more data to send). When FIN is acknowledged that direction is shut down for new data. Data may continue to flow indefinitely in the other direction. When both connections are terminated the connection is released. Normally 4 segments are needed for release of a connection: n o Connection Release is best understood if full duplex connection is viewed as a pair of simplex connections. Each simplex connection is released independently. 1 FIN and 1 ACK for each direction. Two avoid the “two-army” problem, timers are used: n n If a response to a FIN is not forthcoming within two maximum packet lifetimes, the sender of the FIN releases the connection. The other side will eventually notice that nobody seems to be listening to it any more and will time out as well. 10/26/2020 Veton Këpuska 43

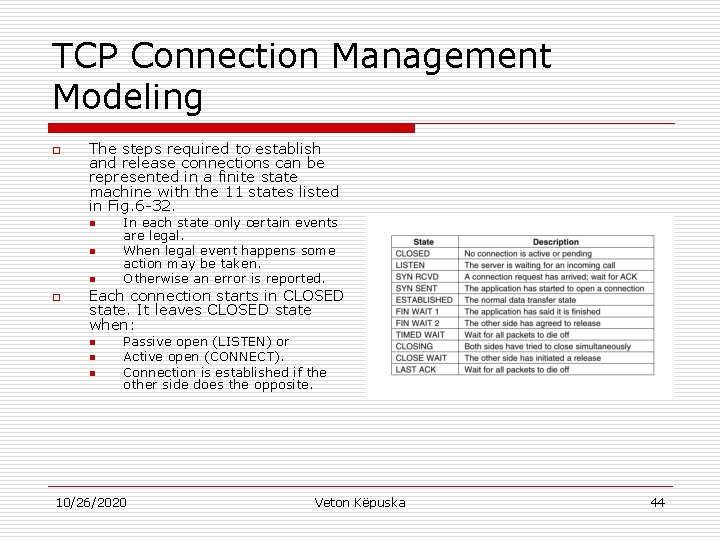
TCP Connection Management Modeling o The steps required to establish and release connections can be represented in a finite state machine with the 11 states listed in Fig. 6 -32. n n n o In each state only certain events are legal. When legal event happens some action may be taken. Otherwise an error is reported. Each connection starts in CLOSED state. It leaves CLOSED state when: n n n Passive open (LISTEN) or Active open (CONNECT). Connection is established if the other side does the opposite. 10/26/2020 Veton Këpuska 44

TCP Connection Management Modeling o o The common case of client actively connecting to a passive server is with heavy lines: n Solid for client n Dotted for server. Each line is marked as event/action pair. n Event can be: o o o n User initiated call (CONNECT, LISTEN, SEND, or CLOSE) Segment arrival (SYN, FIN, ACK, or RST), or Timeout of twice the maximum packet lifetime. Action can be: o o 10/26/2020 Sending of a control segment (SYN, FIN, or RST), or Nothing (indicated by ___). Veton Këpuska 45

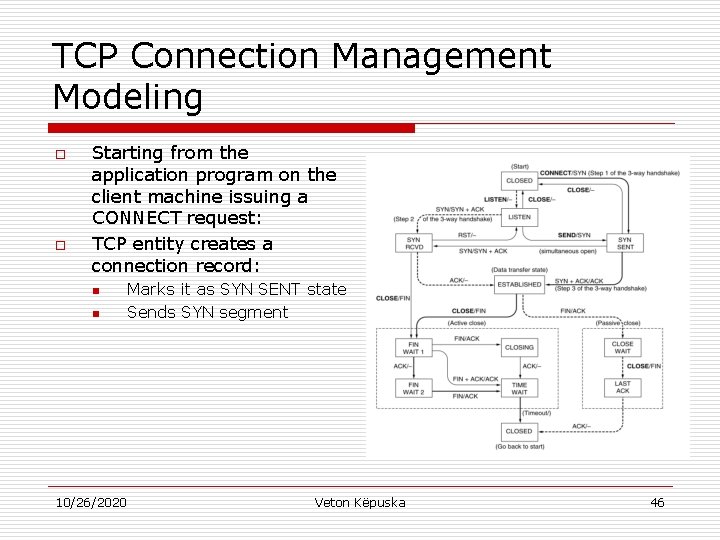
TCP Connection Management Modeling o o Starting from the application program on the client machine issuing a CONNECT request: TCP entity creates a connection record: n n Marks it as SYN SENT state Sends SYN segment 10/26/2020 Veton Këpuska 46

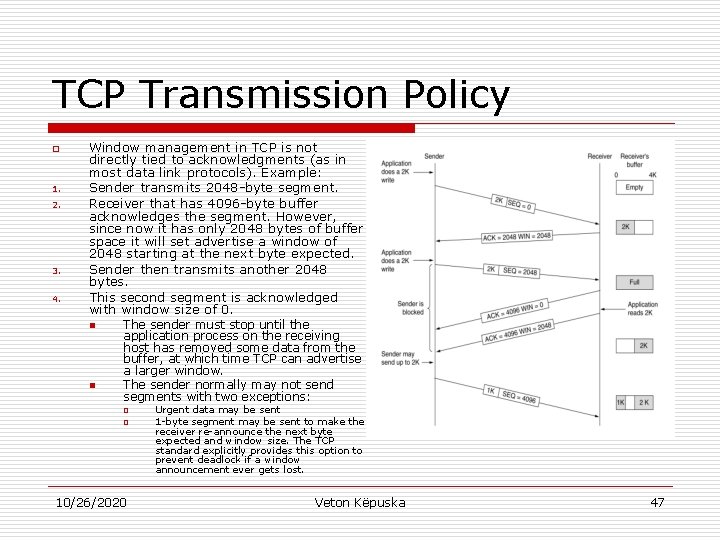
TCP Transmission Policy o 1. 2. 3. 4. Window management in TCP is not directly tied to acknowledgments (as in most data link protocols). Example: Sender transmits 2048 -byte segment. Receiver that has 4096 -byte buffer acknowledges the segment. However, since now it has only 2048 bytes of buffer space it will set advertise a window of 2048 starting at the next byte expected. Sender then transmits another 2048 bytes. This second segment is acknowledged with window size of 0. n n The sender must stop until the application process on the receiving host has removed some data from the buffer, at which time TCP can advertise a larger window. The sender normally may not send segments with two exceptions: o o 10/26/2020 Urgent data may be sent 1 -byte segment may be sent to make the receiver re-announce the next byte expected and window size. The TCP standard explicitly provides this option to prevent deadlock if a window announcement ever gets lost. Veton Këpuska 47

TCP Transmission Policy o Senders are not required to transmit data as soon as they are available from the application. n o TCP (in previous example) knowing that 4 KB of window data is available could have waited after getting first 2 KB of data until its buffer is filled up to 4 KB. In that case it would transmit a segment with a 4 KB payload. Those strategies can be applied to improve performance. Receivers are not required to send acknowledgements as soon as possible. 10/26/2020 Veton Këpuska 48

TCP Transmission Policy o Consider a telnet connection to an interactive editor that reacts on every key-stroke. n When a character arrives at the sending TCP entity, TCP creates a 21 byte TCP segment. This segment is sent as a 41 byte IP datagram. n At the receiving side sends 40 bytes as ACK segment. n When application (editor) has read the byte, TCP sends a window update, moving the window 1 byte to the right. (This packet is also 40 bytes. ) n Finally, when the editor has processed the character, it echoes the character as a 41 byte packet. n 162 bytes of are transmitted and four segments are sent for each character typed: Inefficient and wasteful. 10/26/2020 Veton Këpuska 49

TCP Transmission Policy o o o One solution: Delay acknowledgments and window updates for 500 msec in order to piggyback on top of the data that needs to be send. If the application (editor) echoes within 500 msec, only one 41 byte packet need be sent back to the remote user. This rule reduces the load placed on the network by the receiver. The sender is still operating inefficiently. Nagle’s algorithm. n When data come into the sender one byte at a time, just send the first byte and buffer all the rest until the outstanding byte is acknowledged. n When outstanding byte is acknowledged send all the buffered characters in one TCP segment. 10/26/2020 Veton Këpuska 50

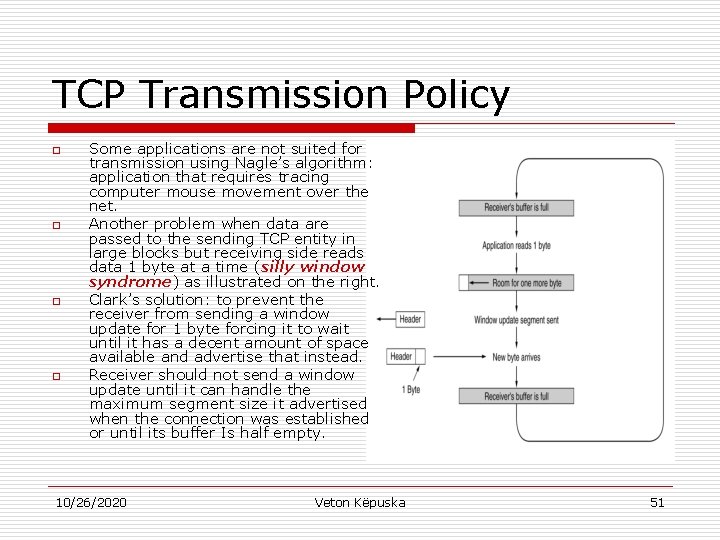
TCP Transmission Policy o o Some applications are not suited for transmission using Nagle’s algorithm: application that requires tracing computer mouse movement over the net. Another problem when data are passed to the sending TCP entity in large blocks but receiving side reads data 1 byte at a time (silly window syndrome) as illustrated on the right. Clark’s solution: to prevent the receiver from sending a window update for 1 byte forcing it to wait until it has a decent amount of space available and advertise that instead. Receiver should not send a window update until it can handle the maximum segment size it advertised when the connection was established or until its buffer Is half empty. 10/26/2020 Veton Këpuska 51

TCP Transmission Policy o Efficiency vs. response time tradeoff: n o In general the goal is for the sender not to send small segments and the receiver not to ask for them. Out-of-order Segments: n n n OOO segment scan be kept or discarded at the receivers discretion. Acknowledgments can be send only when all the data including the byte acknowledged has been received. Example: o o o 10/26/2020 If receiver gets segments 0, 1, 2, 4, 5, 6, and 7, it can acknowledge everything up to and including the last byte in segment 2. When the sender times-out it will retransmit segment 3. If receiver buffers all the packets (e. g. , 4 -7) upon receipt of segment 3 it can acknowledge all bytes up to the end of segment 7. Veton Këpuska 52

TCP Congestion Control o o When load to a network is larger then it can handle congestion occurs. Most of the burden in handling congestions falls on TCP even though network layer also tries to manage congestion. This is so because the only solution to congestion is to slow down the data rate at the sender’s side. In theory solution is to apply the principle of conservation of packets: n Not to inject a new packet into the network until an old one is delivered. n TCP tries to achieve this by manipulating window size. 10/26/2020 Veton Këpuska 53

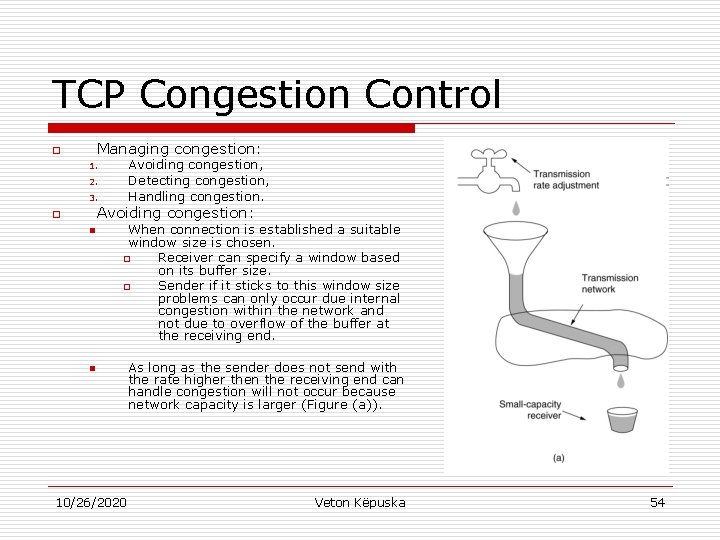
TCP Congestion Control Managing congestion: o Avoiding congestion, Detecting congestion, Handling congestion. 1. 2. 3. Avoiding congestion: o n When connection is established a suitable window size is chosen. o Receiver can specify a window based on its buffer size. o Sender if it sticks to this window size problems can only occur due internal congestion within the network and not due to overflow of the buffer at the receiving end. n 10/26/2020 As long as the sender does not send with the rate higher then the receiving end can handle congestion will not occur because network capacity is larger (Figure (a)). Veton Këpuska 54

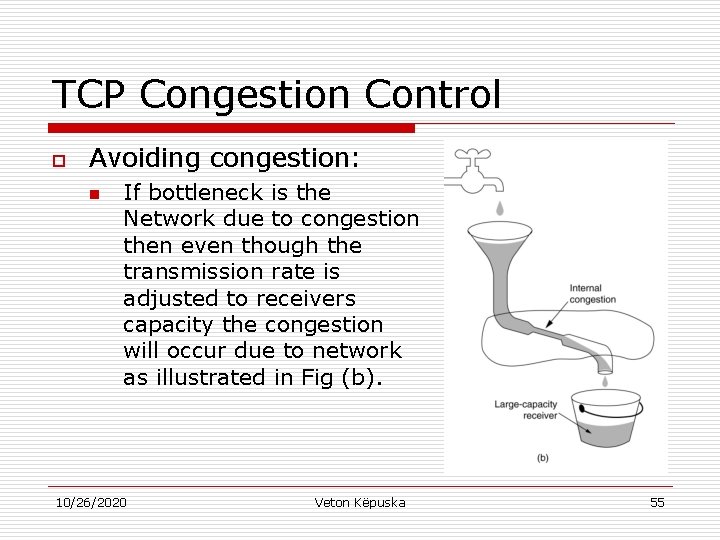
TCP Congestion Control o Avoiding congestion: n If bottleneck is the Network due to congestion then even though the transmission rate is adjusted to receivers capacity the congestion will occur due to network as illustrated in Fig (b). 10/26/2020 Veton Këpuska 55

TCP Congestion Control o Detecting congestion: n n Packet loss predominantly due to congestion (wireline communication, does not apply to wireless case). All TCP algorithms assume that timeouts are caused by congestion. o 10/26/2020 Timeouts are monitored to detect signs of congestion. Veton Këpuska 56

TCP Congestion Control In general there are two potential problems that can cause congestion: n o o Network capacity, and Receiver capacity. Two possible causes of congestion are accounted for separately: n o Each sender maintains two windows: n n 10/26/2020 Window the receiver has grated Congestion window. Both windows indicate the number of bytes the sender may transmit. Actual number of bytes send is the minimum of the two windows. Veton Këpuska 57

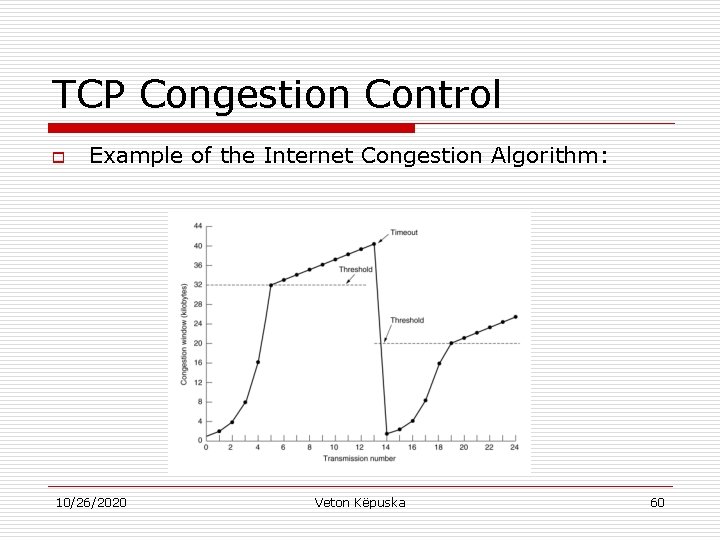
TCP Congestion Control o Handling Congestion: n When a connection is established the sender initializes the congestion window to the size of the maximum segment in use on the connection. n The next segment sent is of this maximum size. o o If the segment is acknowledged before timeout, next segment sent is doubled in size from the previous one. Congestion window keeps growing exponentially until: n n n 10/26/2020 Timeout occurs, or Receiver’s window is reached. This is called “slow start” algorithm. All TCP implementations are required to support it. Veton Këpuska 58

TCP Congestion Control o Handling Congestion – Internet Congestion Control Algorithm: n n Uses additional third parameter – threshold initialized at 64 KB. When a timeout occurs: o Threshold = threshold/2, and o Congestion window = 1 Maximum segment. o Slow start is used to determine what the network can handle. n 10/26/2020 Exponential growth of the window stops when threshold is reached and from that point on it only grows linearly. Veton Këpuska 59

TCP Congestion Control o Example of the Internet Congestion Algorithm: 10/26/2020 Veton Këpuska 60

TCP Timer Management o o Most important timer used by TCP is retransmission timer. Definition of the problem: n When a segment is sent a retransmission timer is started. o If the segment is acknowledged before timer expires the timer is stopped. o If the timer goes off before acknowledgment comes in the segment is retransmitted. o 10/26/2020 How long should the timeout interval be? Veton Këpuska 61

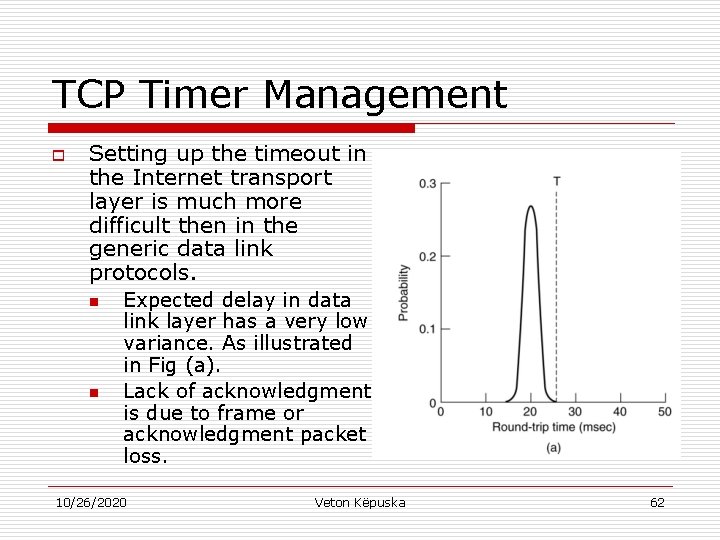
TCP Timer Management o Setting up the timeout in the Internet transport layer is much more difficult then in the generic data link protocols. n n Expected delay in data link layer has a very low variance. As illustrated in Fig (a). Lack of acknowledgment is due to frame or acknowledgment packet loss. 10/26/2020 Veton Këpuska 62

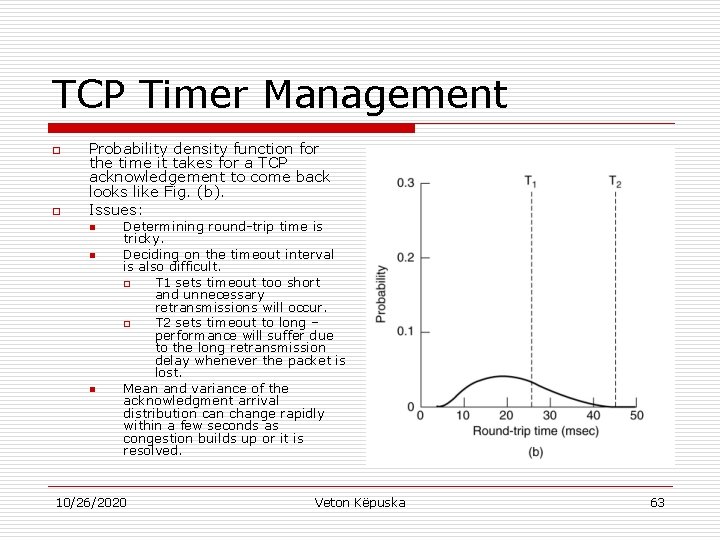
TCP Timer Management o o Probability density function for the time it takes for a TCP acknowledgement to come back looks like Fig. (b). Issues: n n n Determining round-trip time is tricky. Deciding on the timeout interval is also difficult. o T 1 sets timeout too short and unnecessary retransmissions will occur. o T 2 sets timeout to long – performance will suffer due to the long retransmission delay whenever the packet is lost. Mean and variance of the acknowledgment arrival distribution can change rapidly within a few seconds as congestion builds up or it is resolved. 10/26/2020 Veton Këpuska 63

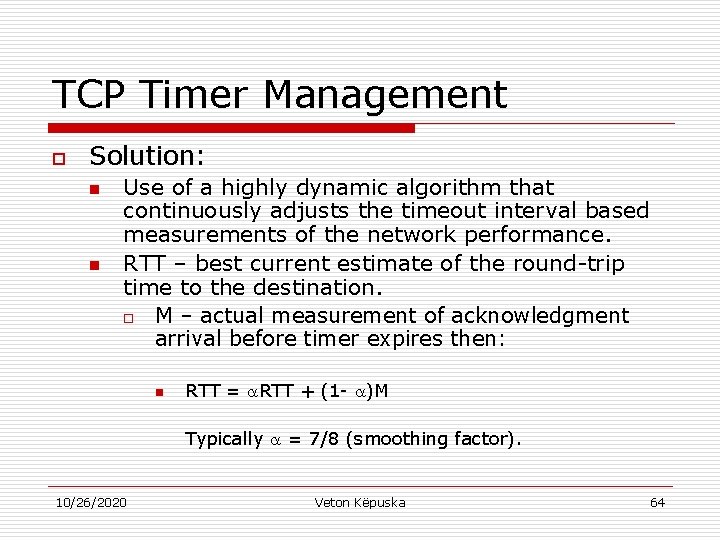
TCP Timer Management o Solution: n n Use of a highly dynamic algorithm that continuously adjusts the timeout interval based measurements of the network performance. RTT – best current estimate of the round-trip time to the destination. o M – actual measurement of acknowledgment arrival before timer expires then: n RTT = RTT + (1 - )M Typically = 7/8 (smoothing factor). 10/26/2020 Veton Këpuska 64

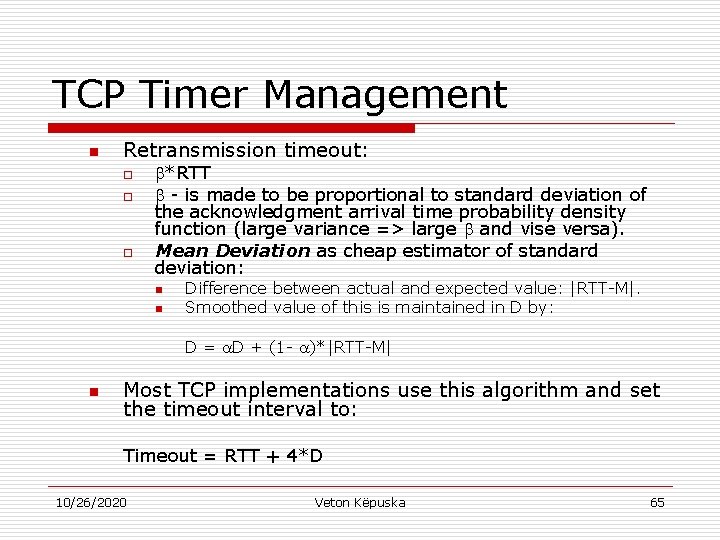
TCP Timer Management n Retransmission timeout: o o o *RTT - is made to be proportional to standard deviation of the acknowledgment arrival time probability density function (large variance => large and vise versa). Mean Deviation as cheap estimator of standard deviation: n n Difference between actual and expected value: |RTT-M|. Smoothed value of this is maintained in D by: D = D + (1 - )*|RTT-M| n Most TCP implementations use this algorithm and set the timeout interval to: Timeout = RTT + 4*D 10/26/2020 Veton Këpuska 65

TCP Timer Management o o Problem: What to do with the dynamic estimation of RTT when a segment times out and is send again. Karn’s algorithm: n n Do not update RTT on any segments that have been retransmitted. Timeout is doubled on each failure until the segments get through the first time. 10/26/2020 Veton Këpuska 66

TCP Timer Management o Persistence Timer: Additional timer that is used to prevent deadlocks as depicted in this scenario: n The receiver sends an acknowledgment with a window size of 0 (tells the sender to wait). n Later receiver updates the window but the packet with the update is lost. n Now both sender and receiver are waiting for each other. o When persistence timer goes off: n n 10/26/2020 The sender transmits a probe to the receiver, Response to the probe gives the window size if still zero the persistence timer is set again and the cycle repeats. If not zero data can be sent. Veton Këpuska 67

TCP Timer Management o Keep-alive timer: n o When a connection has been idle for along time, the keep-alive timer may go off to cause one side to check whether the other side is still there. If it fails to respond the connection is terminated. Timed Wait timer: n Is used while closing the connection. It runs for twice the maximum packet lifetime to make sure that when a connection is closed, all packets created by it have died off. 10/26/2020 Veton Këpuska 68

SUMMARY o Transport layer provides various services. The most important is an: End-to-End, n Reliable, n Connection oriented, byte stream from sender to receiver. n o It is accessed through service primitives that: n n n Establish, Use, and Release connections. 10/26/2020 Veton Këpuska 69

SUMMARY o Connection Management of Transport Layer: n n n Reliable in spite off Unreliable networks. Three-way handshaking is needed to establish connections. It must manage o o o 10/26/2020 service primitives Connections and corresponding timers, Allocate and utilize buffers. Veton Këpuska 70

SUMMARY o The Internet has two main transport protocols: n UDP (User Datagram Protocol): o Connectionless protocol used for client-server interactions using: n n n RPC (Remote Procedure Call), or Real-time applications using RTP. TCP (Transmission Control Protocol) o Provides reliable bi-directional (fully duplex) byte stream. o It uses a 20 -byute header on all segments. o Segments can be fragmented by routers within the Internet so host must be able to re-assable the segments. 10/26/2020 Veton Këpuska 71