Secure Socket Layer SSL Transport Layer Security TLS






- Slides: 11

Secure Socket Layer (SSL) Transport Layer Security (TLS) 1

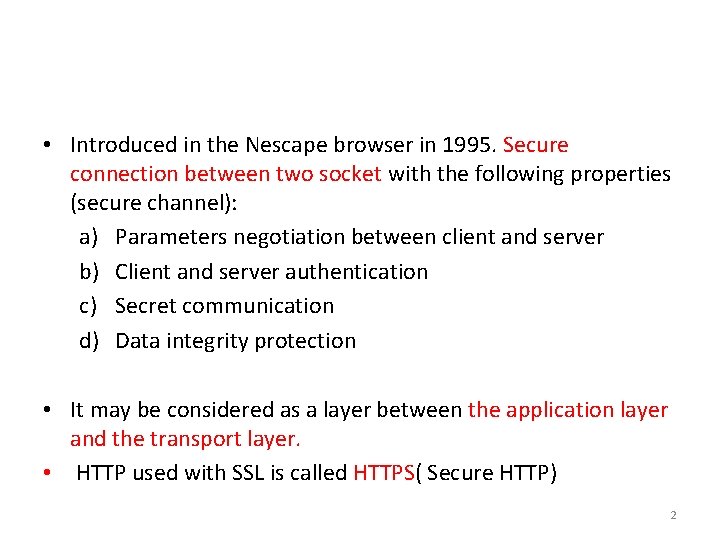
• Introduced in the Nescape browser in 1995. Secure connection between two socket with the following properties (secure channel): a) Parameters negotiation between client and server b) Client and server authentication c) Secret communication d) Data integrity protection • It may be considered as a layer between the application layer and the transport layer. • HTTP used with SSL is called HTTPS( Secure HTTP) 2

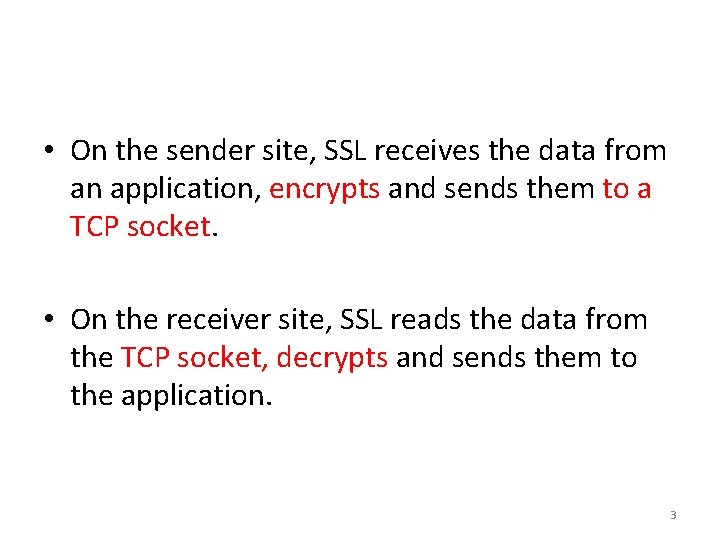
• On the sender site, SSL receives the data from an application, encrypts and sends them to a TCP socket. • On the receiver site, SSL reads the data from the TCP socket, decrypts and sends them to the application. 3

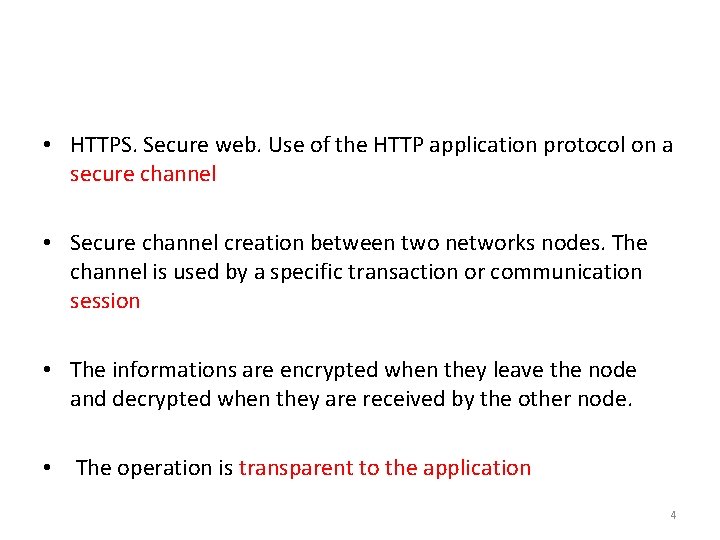
• HTTPS. Secure web. Use of the HTTP application protocol on a secure channel • Secure channel creation between two networks nodes. The channel is used by a specific transaction or communication session • The informations are encrypted when they leave the node and decrypted when they are received by the other node. • The operation is transparent to the application 4

SSL Widely used in the electronic commerce being implemented in the majority of web browsers and servers. It provides the following functions: -Server authentication. It allows a user to confirm the server identity. -Client authentication. It allows a server to confirm the user identity. - SSL session encrypted. All the informations sent from the client and the server are encrypted by the sending software (browser or server )and decrypted by the receiving software (browser or server) 5

Autenticazione del server • Un browser SSL compatibile mantiene un elenco di fidate autorità di certificazione (CA) assieme alle chiavi pubbliche delle CA. • Quando il browser vuole contattare un web server SSL-compatibile, ottiene un certificato del server contenente la sua chiave pubblica. Il certificato è rilasciato (firmato digitalmente) sa un’autorità di certificazione (CA). • L’autenticazione del server consente a Bob di verificare che egli sta davvero spedendo il suo numero di carta di credito alla Alice Incorporated e non a qualcun altro che si spaccia per essa. 6

Handsake protocol • The protocol allows the server and the client to authenticate each other and to negotiate an encryption and hash algorithm and criyptographic keys to be used to protect data sent in a SSL record. • The handsake protocol is used before any application data is transmitted. 7

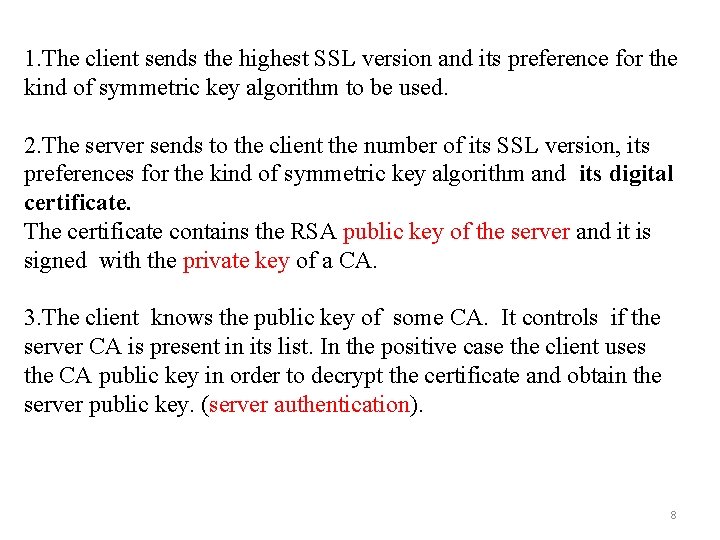
1. The client sends the highest SSL version and its preference for the kind of symmetric key algorithm to be used. 2. The server sends to the client the number of its SSL version, its preferences for the kind of symmetric key algorithm and its digital certificate. The certificate contains the RSA public key of the server and it is signed with the private key of a CA. 3. The client knows the public key of some CA. It controls if the server CA is present in its list. In the positive case the client uses the CA public key in order to decrypt the certificate and obtain the server public key. (server authentication). 8

Client authentication • Client certificates released by a CA are used (as in the case of server auythentication). This authentication is important if the server is, for example , a bank that is sending confidential financial informations to a client and it wants to check the receiver identity. . • The client authentication, although supported by SSL, is optional. 9

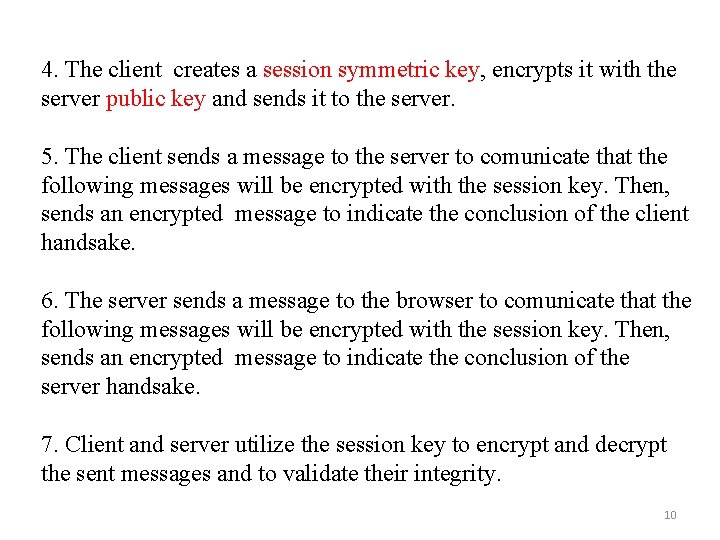
4. The client creates a session symmetric key, encrypts it with the server public key and sends it to the server. 5. The client sends a message to the server to comunicate that the following messages will be encrypted with the session key. Then, sends an encrypted message to indicate the conclusion of the client handsake. 6. The server sends a message to the browser to comunicate that the following messages will be encrypted with the session key. Then, sends an encrypted message to indicate the conclusion of the server handsake. 7. Client and server utilize the session key to encrypt and decrypt the sent messages and to validate their integrity. 10

SSL limits in e-commerce applications • SSL was thought for secure communication between a client and a server. It not allows a secure credit card utilization. • The certificate that Bob receives from Alice assures him that he is negotiating with Alice Incorporated and that Alice Incorporated is a reliable company. • However, the certificate does not indicate if Alice Incorporated is authorized to accept the payment with credit cards. • The same is valid for the client authorization. The certificate does not establish if the Bob credit card is valid. 11