P 2 P and NAT How to traverse










![UPn. P NAT Traversal n n Internet Gateway Device (IGD) protocol[1] is defined by UPn. P NAT Traversal n n Internet Gateway Device (IGD) protocol[1] is defined by](https://slidetodoc.com/presentation_image_h/a7d72bb7419350c33a91e48b8019042c/image-43.jpg)

- Slides: 49

P 2 P and NAT How to traverse NAT Davide Carboni © 2005 -2006

License Attribution-Share. Alike 2. 5 You are free: to copy, distribute, display, and perform the work to make derivative works to make commercial use of the work Under the following conditions: Attribution. You must give the original author credit. Share Alike. If you alter, transform, or build upon this work, you may distribute the resulting work only under a licence identical to this one. For any reuse or distribution, you must make clear to others the licence terms of this work. Any of these conditions can be waived if you get permission from the copyright holder. Your fair use and other rights are in no way affected by the above. This is a human-readable summary of the Legal Code (the full licence). Disclaimer

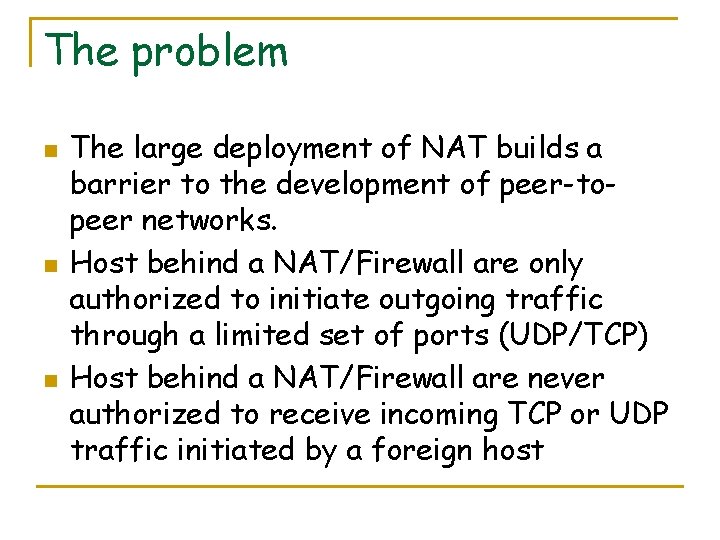
The problem n n n The large deployment of NAT builds a barrier to the development of peer-topeer networks. Host behind a NAT/Firewall are only authorized to initiate outgoing traffic through a limited set of ports (UDP/TCP) Host behind a NAT/Firewall are never authorized to receive incoming TCP or UDP traffic initiated by a foreign host

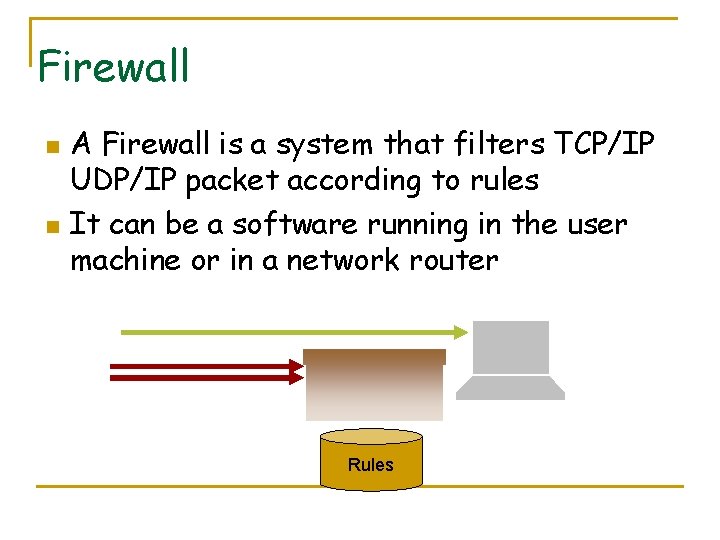
Firewall n n A Firewall is a system that filters TCP/IP UDP/IP packet according to rules It can be a software running in the user machine or in a network router Rules

Firewall (Global IP addresses) router Rules

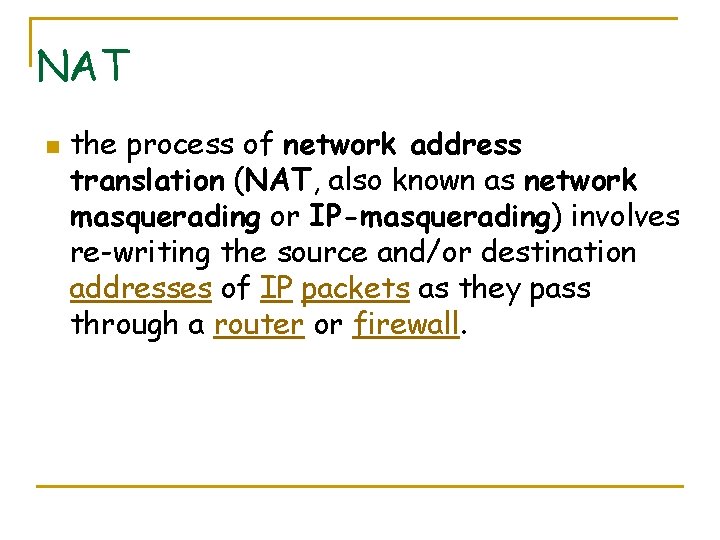
NAT n the process of network address translation (NAT, also known as network masquerading or IP-masquerading) involves re-writing the source and/or destination addresses of IP packets as they pass through a router or firewall.

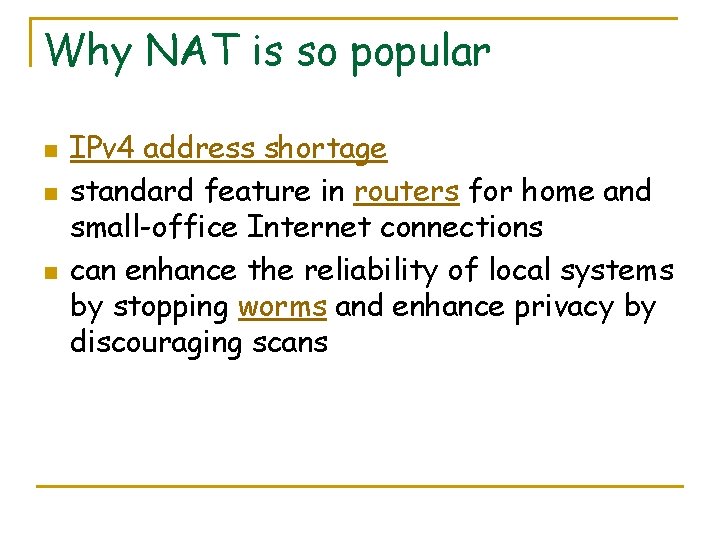
Why NAT is so popular n n n IPv 4 address shortage standard feature in routers for home and small-office Internet connections can enhance the reliability of local systems by stopping worms and enhance privacy by discouraging scans

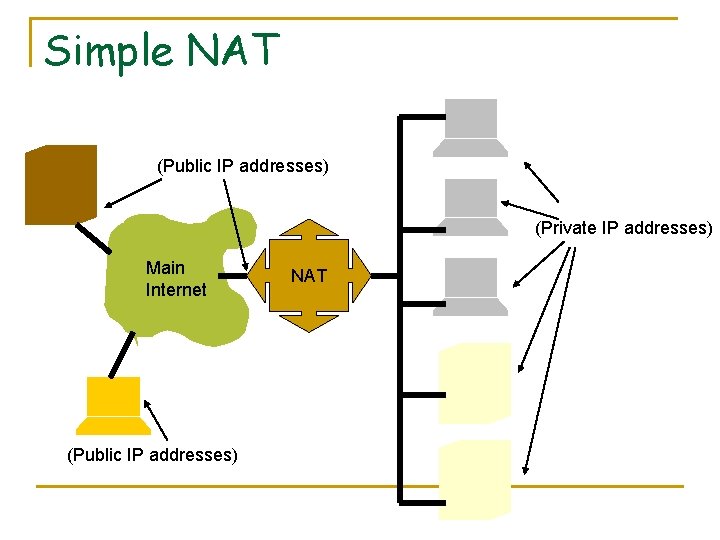
Simple NAT (Public IP addresses) (Private IP addresses) Main Internet (Public IP addresses) NAT

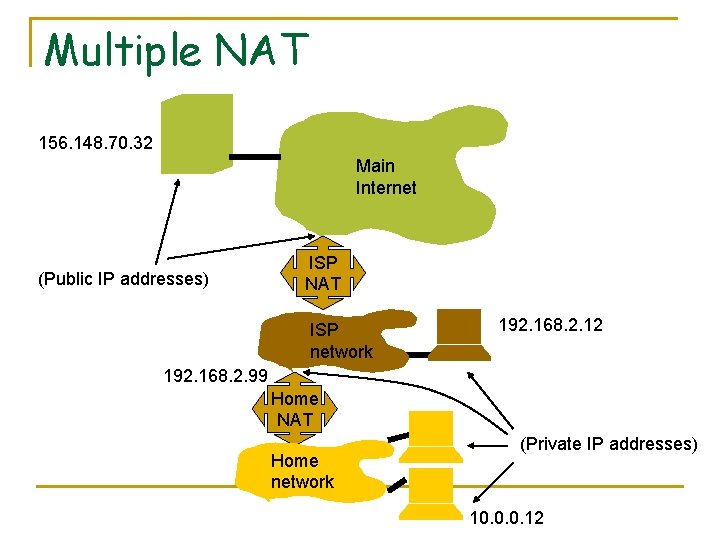
Multiple NAT 156. 148. 70. 32 Main Internet (Public IP addresses) ISP NAT ISP network 192. 168. 2. 12 192. 168. 2. 99 Home NAT Home network (Private IP addresses) 10. 0. 0. 12

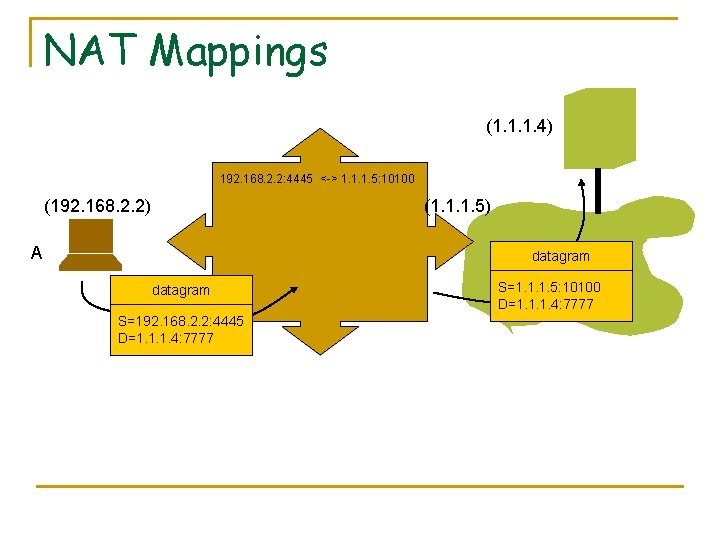
NAT Mappings (1. 1. 1. 4) 192. 168. 2. 2: 4445 <-> 1. 1. 1. 5: 10100 (192. 168. 2. 2) (1. 1. 1. 5) A datagram S=192. 168. 2. 2: 4445 D=1. 1. 1. 4: 7777 S=1. 1. 1. 5: 10100 D=1. 1. 1. 4: 7777

Traversing a NAT that does not collaborate

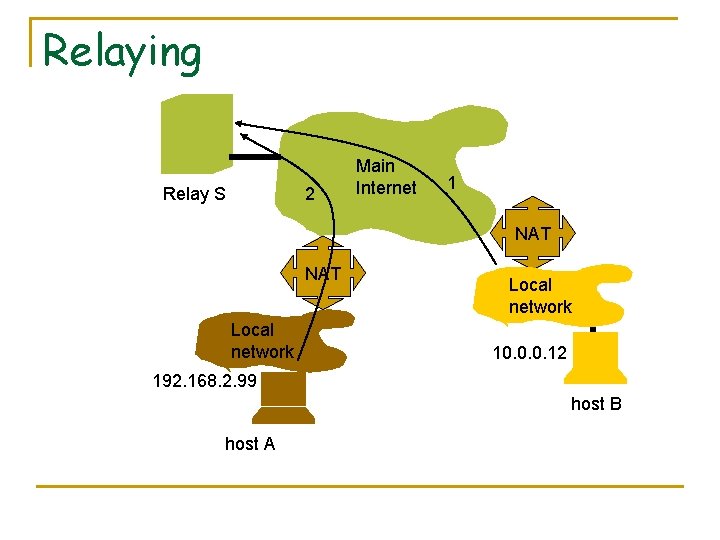
Relaying Relay S 2 Main Internet 1 NAT Local network 10. 0. 0. 12 192. 168. 2. 99 host B host A

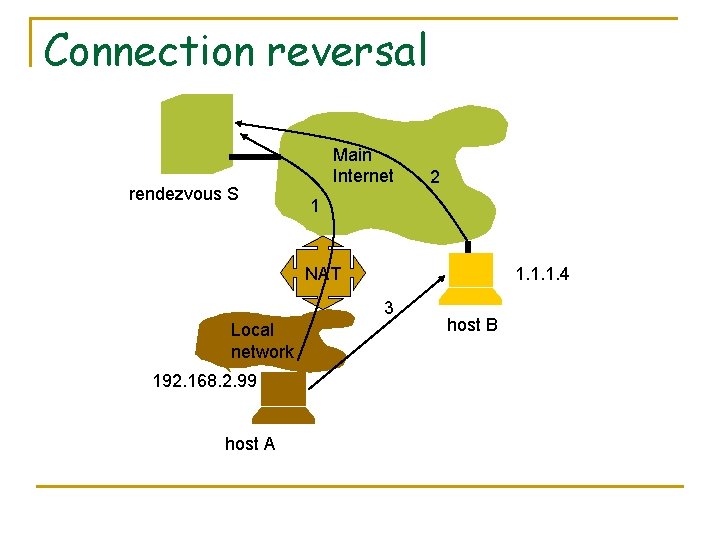
Connection reversal rendezvous S Main Internet 2 1 NAT 1. 1. 1. 4 3 Local network 192. 168. 2. 99 host A host B

NAT policies n n Full cone NAT is NAT where all requests from the same internal IP address and port are mapped to the same public IP address and port. Once a mapping is created, all incoming traffic to the public address is routed to the internal host without checking the address of the remote host. A restricted cone NAT: like full cone all requests from the same internal IP address and port are mapped to the same public IP address and port. Unlike a full cone NAT, a remote host (with IP address X) can send a packet to the internal host only if the internal host had previously sent a packet to IP address X. A port restricted cone NAT is like a restricted cone NAT, but the restriction includes port numbers. Specifically, an external host can send a packet, with source IP address X and source port P, to the internal host only if the internal host had previously sent a packet to IP address X and port P. A symmetric NAT is a NAT where all requests from the same internal IP address and port to a specific destination IP address and port are mapped to the same external source IP address and port. If the same internal host sends a packet with the same source address and port to a different destination, a different mapping is used. Furthermore, only the external host that receives a packet can send a UDP packet back to the internal host

UDP Hole Punching n n Hole punching is a tecnique to allow traffic from/to a host behind a firewall/NAT without the collaboration of the NAT itself The simplest way is to use UDP packets

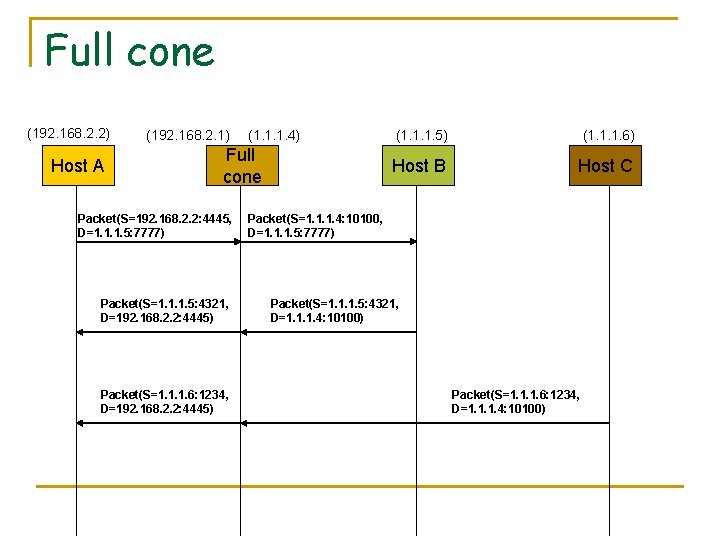
Full cone (192. 168. 2. 2) Host A (192. 168. 2. 1) (1. 1. 1. 4) Full cone Packet(S=192. 168. 2. 2: 4445, D=1. 1. 1. 5: 7777) Packet(S=1. 1. 1. 5: 4321, D=192. 168. 2. 2: 4445) Packet(S=1. 1. 1. 6: 1234, D=192. 168. 2. 2: 4445) (1. 1. 1. 6) Host B Host C Packet(S=1. 1. 1. 4: 10100, D=1. 1. 1. 5: 7777) Packet(S=1. 1. 1. 5: 4321, D=1. 1. 1. 4: 10100) Packet(S=1. 1. 1. 6: 1234, D=1. 1. 1. 4: 10100)

Full cone mapping and policy n Mapping q n 192. 168. 2. 2: 4445 <-> 1. 1. 1. 4: 10100 Policy q ALLOW ALL TO 1. 1. 1. 4: 10100

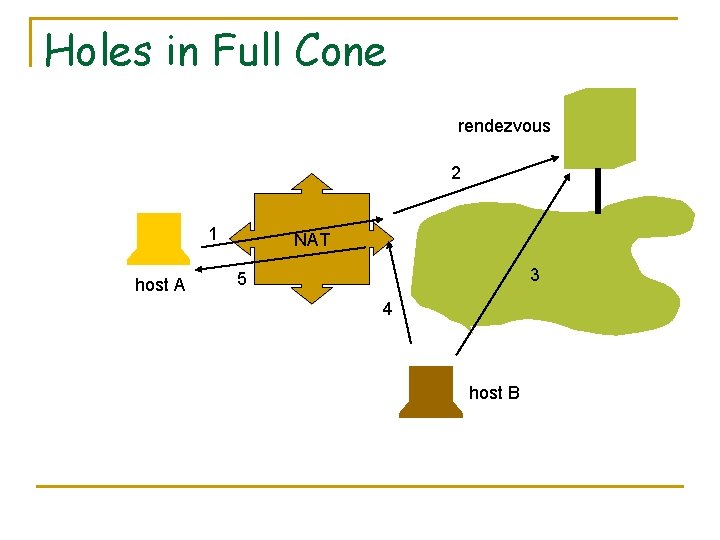
Holes in Full Cone rendezvous 2 1 host A NAT 3 5 4 host B

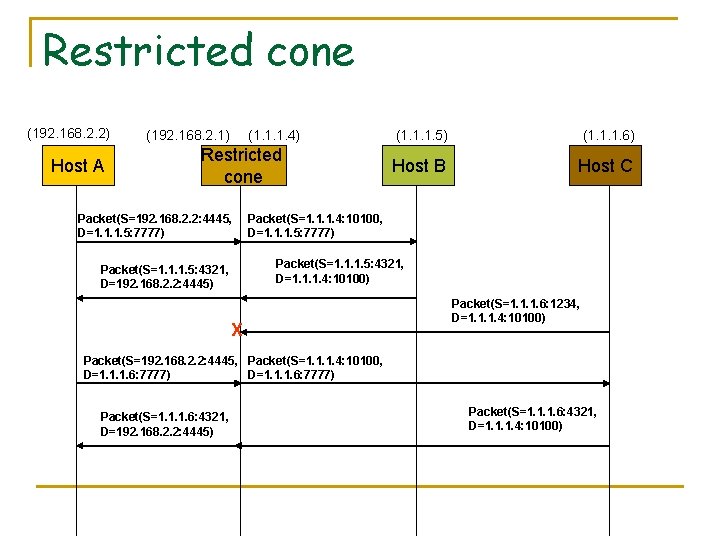
Restricted cone (192. 168. 2. 2) Host A (192. 168. 2. 1) (1. 1. 1. 4) Restricted cone Packet(S=192. 168. 2. 2: 4445, D=1. 1. 1. 5: 7777) (1. 1. 1. 5) (1. 1. 1. 6) Host B Host C Packet(S=1. 1. 1. 4: 10100, D=1. 1. 1. 5: 7777) Packet(S=1. 1. 1. 5: 4321, D=1. 1. 1. 4: 10100) Packet(S=1. 1. 1. 5: 4321, D=192. 168. 2. 2: 4445) X Packet(S=1. 1. 1. 6: 1234, D=1. 1. 1. 4: 10100) Packet(S=192. 168. 2. 2: 4445, Packet(S=1. 1. 1. 4: 10100, D=1. 1. 1. 6: 7777) Packet(S=1. 1. 1. 6: 4321, D=192. 168. 2. 2: 4445) Packet(S=1. 1. 1. 6: 4321, D=1. 1. 1. 4: 10100)

Restricted cone mapping and policy n Mapping q n 192. 168. 2. 2: 4445 <-> 1. 1. 1. 4: 10100 Policy q q ALLOW 1. 1. 1. 5 TO 1. 1. 1. 4: 10100 ALLOW 1. 1. 1. 6 TO 1. 1. 1. 4: 10100

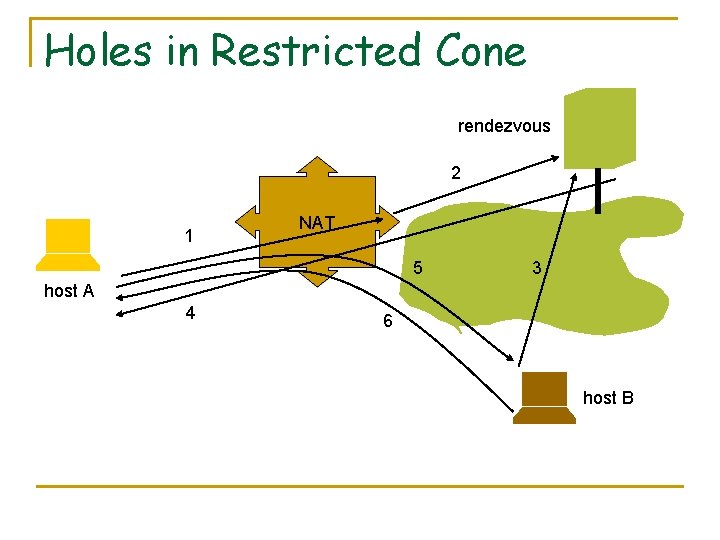
Holes in Restricted Cone rendezvous 2 1 NAT 5 3 host A 4 6 host B

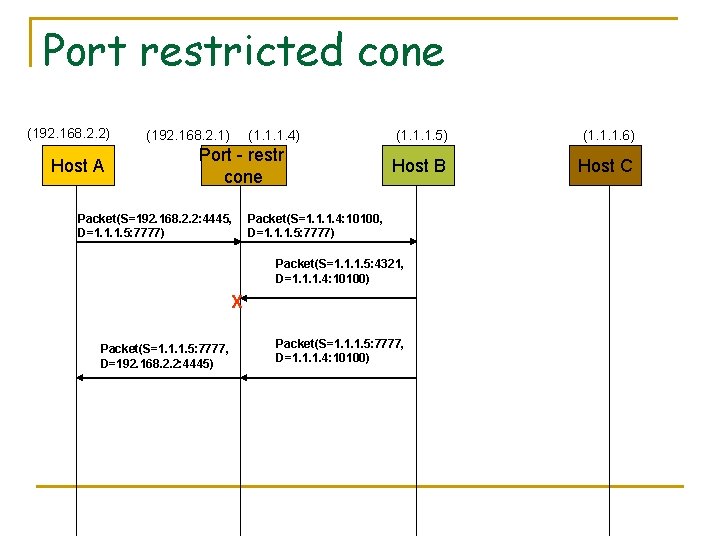
Port restricted cone (192. 168. 2. 2) Host A (192. 168. 2. 1) (1. 1. 1. 4) Port - restr cone Packet(S=192. 168. 2. 2: 4445, D=1. 1. 1. 5: 7777) (1. 1. 1. 5) (1. 1. 1. 6) Host B Host C Packet(S=1. 1. 1. 4: 10100, D=1. 1. 1. 5: 7777) Packet(S=1. 1. 1. 5: 4321, D=1. 1. 1. 4: 10100) X Packet(S=1. 1. 1. 5: 7777, D=192. 168. 2. 2: 4445) Packet(S=1. 1. 1. 5: 7777, D=1. 1. 1. 4: 10100)

Port restricted cone mapping and policy n Mapping q n 192. 168. 2. 2: 4445 <-> 1. 1. 1. 4: 10100 Policy q q ALLOW 1. 1. 1. 5: 7777 TO 1. 1. 1. 4: 10100 ALLOW 1. 1. 1. 6: 7777 TO 1. 1. 1. 4: 10100

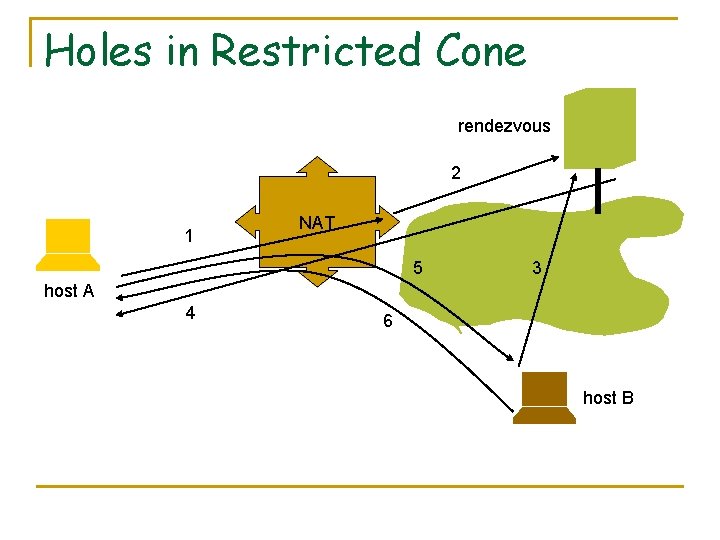
Holes in Restricted Cone rendezvous 2 1 NAT 5 3 host A 4 6 host B

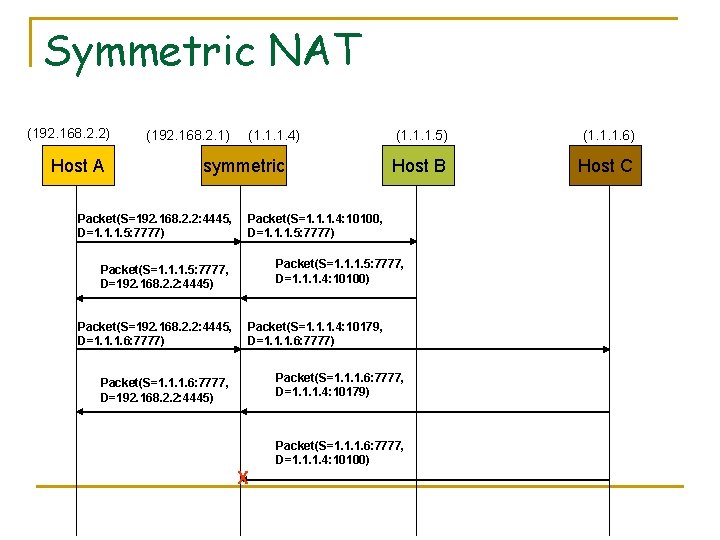
Symmetric NAT (192. 168. 2. 2) Host A (192. 168. 2. 1) (1. 1. 1. 4) symmetric Packet(S=192. 168. 2. 2: 4445, D=1. 1. 1. 5: 7777) (1. 1. 1. 6) Host B Host C Packet(S=1. 1. 1. 4: 10100, D=1. 1. 1. 5: 7777) Packet(S=1. 1. 1. 5: 7777, D=1. 1. 1. 4: 10100) Packet(S=1. 1. 1. 5: 7777, D=192. 168. 2. 2: 4445) Packet(S=192. 168. 2. 2: 4445, D=1. 1. 1. 6: 7777) (1. 1. 1. 5) Packet(S=1. 1. 1. 4: 10179, D=1. 1. 1. 6: 7777) Packet(S=1. 1. 1. 6: 7777, D=1. 1. 1. 4: 10179) Packet(S=1. 1. 1. 6: 7777, D=192. 168. 2. 2: 4445) Packet(S=1. 1. 1. 6: 7777, D=1. 1. 1. 4: 10100) X

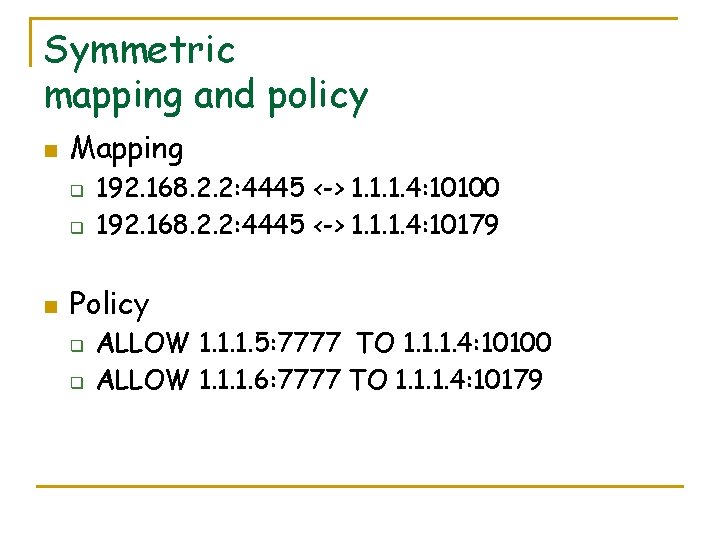
Symmetric mapping and policy n Mapping q q n 192. 168. 2. 2: 4445 <-> 1. 1. 1. 4: 10100 192. 168. 2. 2: 4445 <-> 1. 1. 1. 4: 10179 Policy q q ALLOW 1. 1. 1. 5: 7777 TO 1. 1. 1. 4: 10100 ALLOW 1. 1. 1. 6: 7777 TO 1. 1. 1. 4: 10179

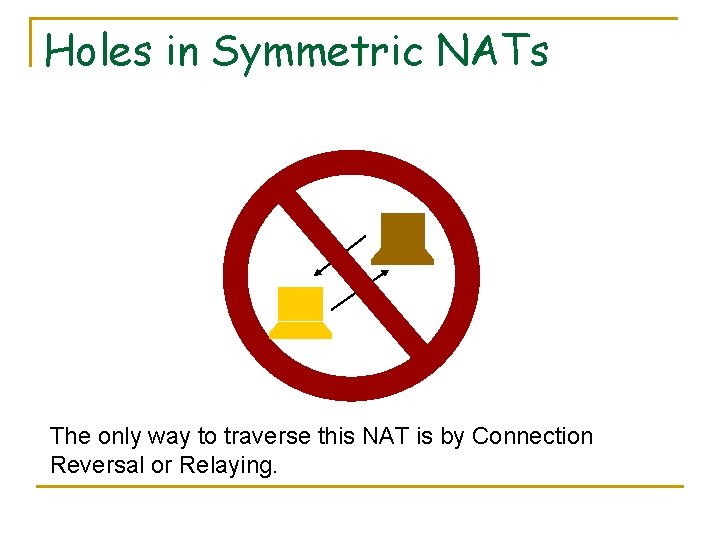
Holes in Symmetric NATs The only way to traverse this NAT is by Connection Reversal or Relaying.

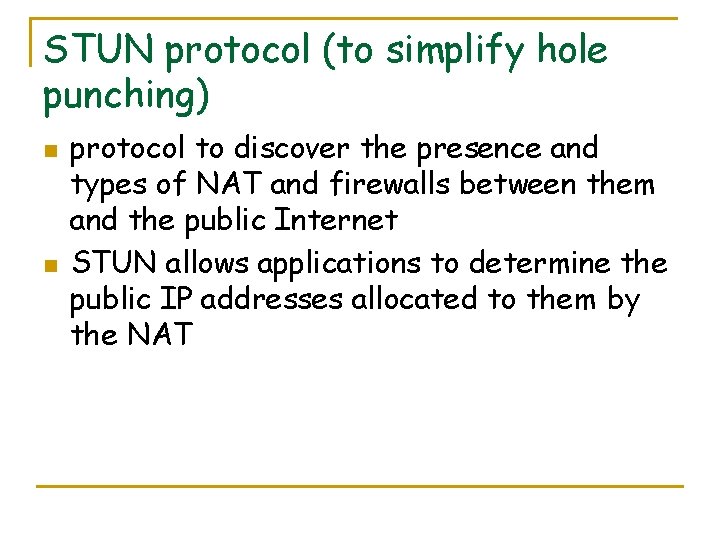
STUN protocol (to simplify hole punching) n n protocol to discover the presence and types of NAT and firewalls between them and the public Internet STUN allows applications to determine the public IP addresses allocated to them by the NAT

STUN protocol n STUN is specified in RFC 3489 and defines the operations and the message format needed to understand the type of NAT

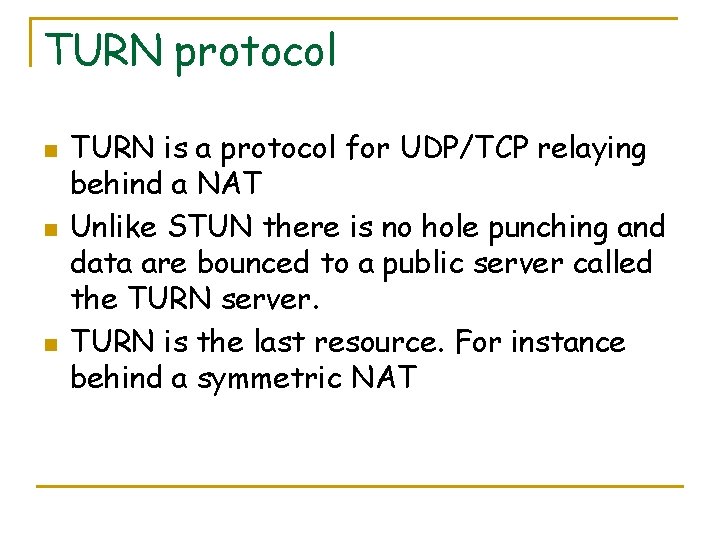
TURN protocol n n n TURN is a protocol for UDP/TCP relaying behind a NAT Unlike STUN there is no hole punching and data are bounced to a public server called the TURN server. TURN is the last resource. For instance behind a symmetric NAT

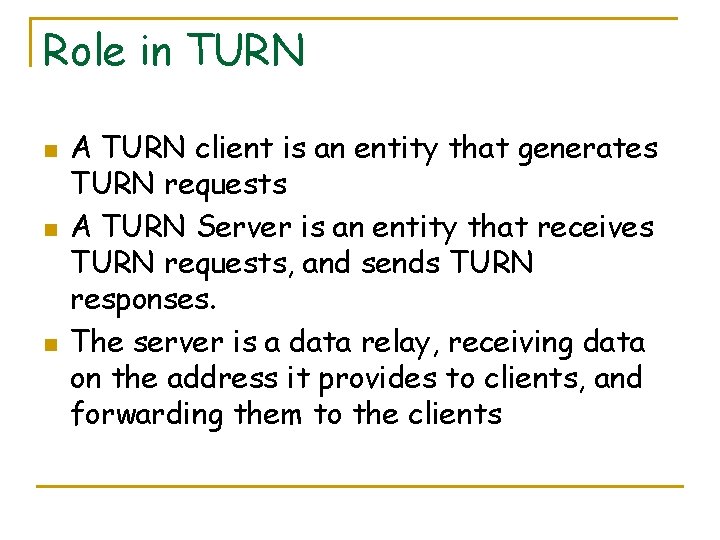
Role in TURN n n n A TURN client is an entity that generates TURN requests A TURN Server is an entity that receives TURN requests, and sends TURN responses. The server is a data relay, receiving data on the address it provides to clients, and forwarding them to the clients

TCP Hole Punching n n TCP connections between hosts behind NATs is slightly more complex than for UDP Berkeley sockets allows a TCP socket to initiate an outgoing or to listen for incoming connections but not both.

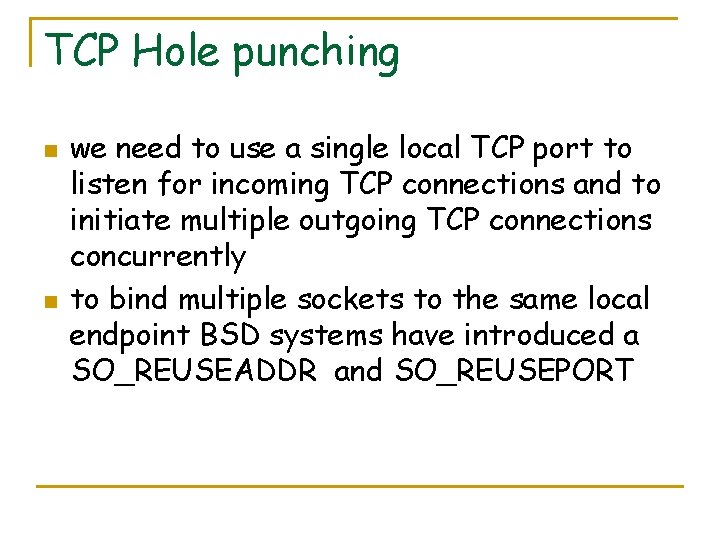
TCP Hole punching n n we need to use a single local TCP port to listen for incoming TCP connections and to initiate multiple outgoing TCP connections concurrently to bind multiple sockets to the same local endpoint BSD systems have introduced a SO_REUSEADDR and SO_REUSEPORT

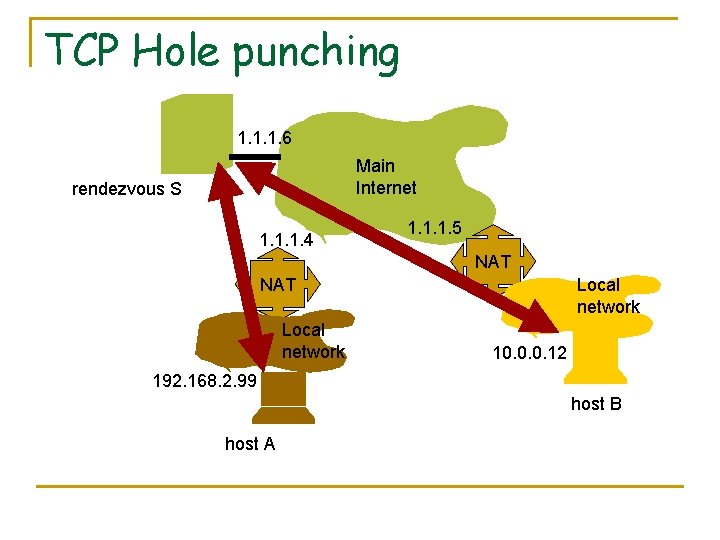
TCP Hole punching 1. 1. 1. 6 Main Internet rendezvous S 1. 1. 1. 4 1. 1. 1. 5 NAT Local network 10. 0. 0. 12 192. 168. 2. 99 host B host A

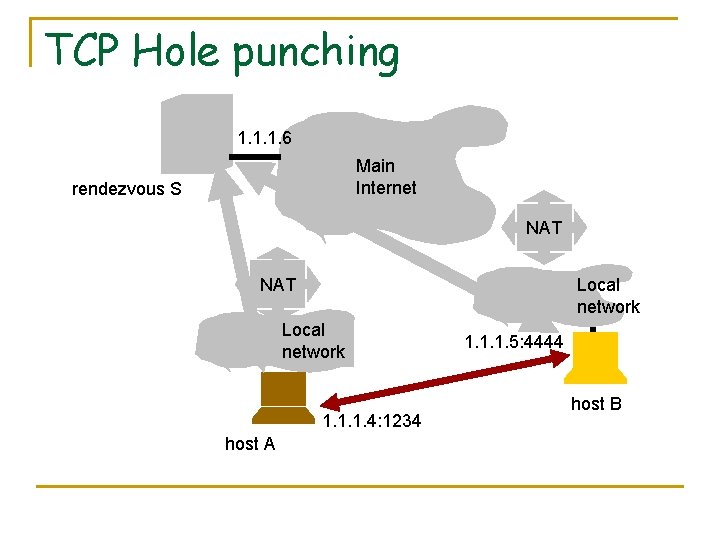
TCP Hole punching 1. 1. 1. 6 Main Internet rendezvous S NAT Local network 1. 1. 1. 4: 1234 host A 1. 1. 1. 5: 4444 host B

STUNT n n n Simple Traversal of UDP Through NATs and TCP too (STUNT), which extends STUN to include TCP functionality A JAVA implementation of STUNT is available See http: //nutss. gforge. cis. cornell. edu/stunt. php

Traversing a NAT that collaborates

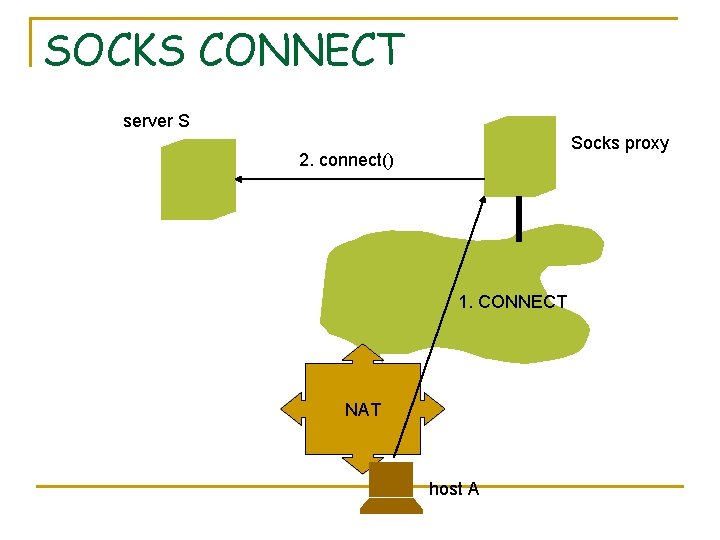
Socks n n SOCKS is a client server protocol that allows a client behind a firewall to use a server in the public Internet to relay traffic Two operations: CONNECT and BIND It is widely adopted, for instance Mozilla can be configured to use SOCKS Two versions. SOCKS 4 and SOCKS 5

SOCKS CONNECT server S Socks proxy 2. connect() 1. CONNECT NAT host A

SOCKS BIND server S 3. connect(33102) Socks proxy 2. Ok. Port=33102 1. BIND (localport=4445, S) NAT host A listening on 4445

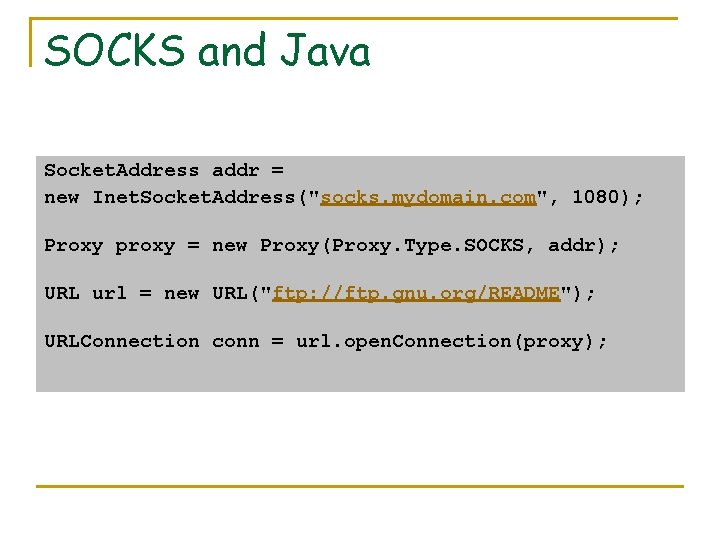
SOCKS and Java Socket. Address addr = new Inet. Socket. Address("socks. mydomain. com", 1080); Proxy proxy = new Proxy(Proxy. Type. SOCKS, addr); URL url = new URL("ftp: //ftp. gnu. org/README"); URLConnection conn = url. open. Connection(proxy);

SOCKS 4 and SOCKS 5 n n n SOCKS 4 doesn't support authentication while SOCKS 5 has the built-in mechanism to support a variety of authentications methods. SOCKS 4 doesn't support UDP proxy while SOCKS 5 does. SOCKS 4 clients require full support of DNS while SOCKS 5 clients can rely on SOCKS 5 server to perform the DNS lookup.
![UPn P NAT Traversal n n Internet Gateway Device IGD protocol1 is defined by UPn. P NAT Traversal n n Internet Gateway Device (IGD) protocol[1] is defined by](https://slidetodoc.com/presentation_image_h/a7d72bb7419350c33a91e48b8019042c/image-43.jpg)
UPn. P NAT Traversal n n Internet Gateway Device (IGD) protocol[1] is defined by UPn. P It is implemented in some internet routers. It allows applications to automatically configure NAT routing. IGD makes it easy to do the following: q q Learn the public (external) IP address Enumerate existing port mappings Add and remove port mappings Assign lease times to mappings

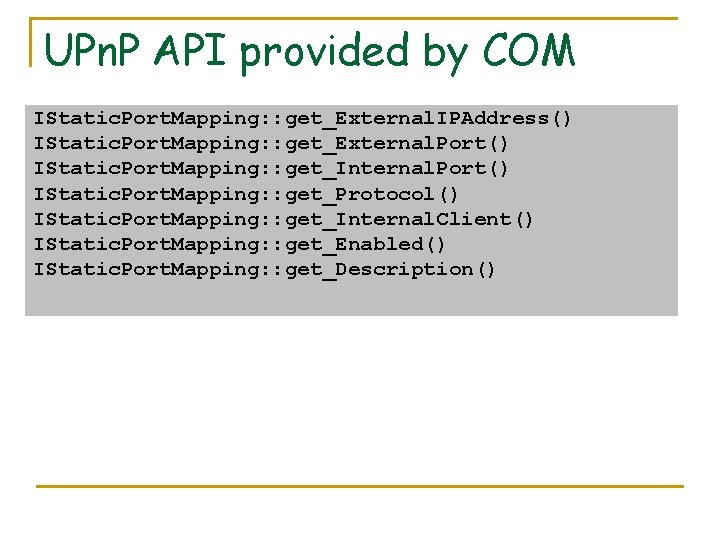
UPn. P API provided by COM IStatic. Port. Mapping: : get_External. IPAddress() IStatic. Port. Mapping: : get_External. Port() IStatic. Port. Mapping: : get_Internal. Port() IStatic. Port. Mapping: : get_Protocol() IStatic. Port. Mapping: : get_Internal. Client() IStatic. Port. Mapping: : get_Enabled() IStatic. Port. Mapping: : get_Description()

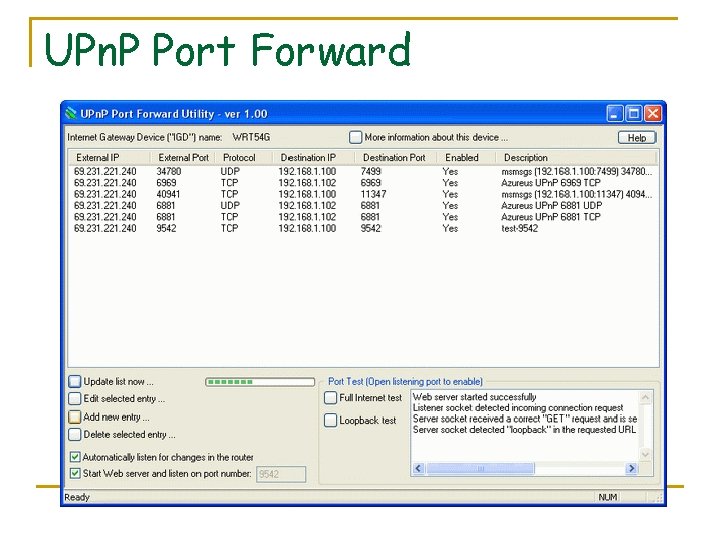
UPn. P Port Forward

Issues with UPn. P n n n Oppents to IGD see a significant security risk UPn. P allows any program, even malicious programs, to create a port mapping through the router. with UPn. P, the port mapping can be created even without any knowledge of the administrative password to the router

References n n Peer-to-Peer Communication Across NAT http: //www. brynosaurus. com/pub/net/p 2 pnat/ STUN Protocol RFC. http: //www. ietf. org/rfc 3489. txt TCP NAT traversal. http: //nutss. gforge. cis. cornell. edu//stunt. php Traversal Using Relay NAT (TURN) IETF RFC

References (2) n n SOCKS 5 IETF RFC http: //www. ietf. org/rfc 1928. txt SOCKS 4 http: //archive. socks. permeo. com/protocol/socks 4. protocol n Java Networking and Proxies http: //java. sun. com/j 2 se/1. 5. 0/docs/guide/net/proxies. html n Using UPn. P for Programmatic Port Forwardings and NAT Traversal http: //www. codeproject. com/internet/Port. Forward. asp

License Attribution-Share. Alike 2. 5 You are free: to copy, distribute, display, and perform the work to make derivative works to make commercial use of the work Under the following conditions: Attribution. You must give the original author credit. Share Alike. If you alter, transform, or build upon this work, you may distribute the resulting work only under a licence identical to this one. For any reuse or distribution, you must make clear to others the licence terms of this work. Any of these conditions can be waived if you get permission from the copyright holder. Your fair use and other rights are in no way affected by the above. This is a human-readable summary of the Legal Code (the full licence). Disclaimer