NAT and NAT Traversal SEng 490 Directed Study








- Slides: 24

NAT and NAT Traversal SEng 490 Directed Study Haoran Song Supervised by Dr. Jianping Pan

Outline • Problems of NAT in the real world • NAT Traversal in our research • Conclusion

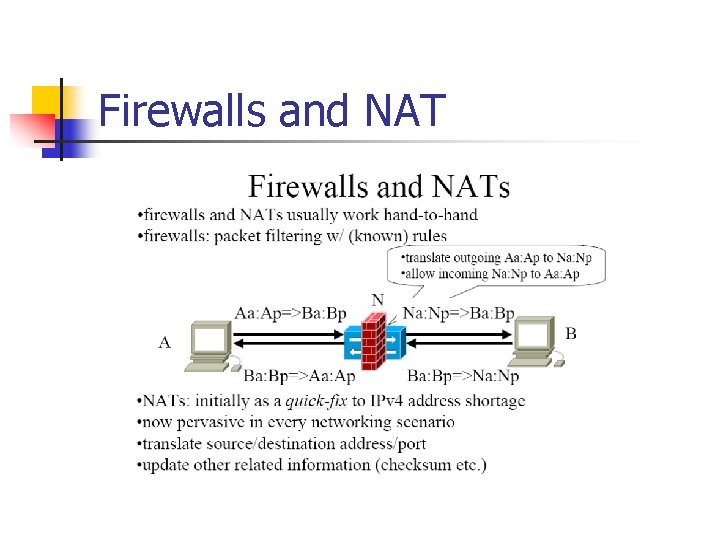
Firewalls and NAT

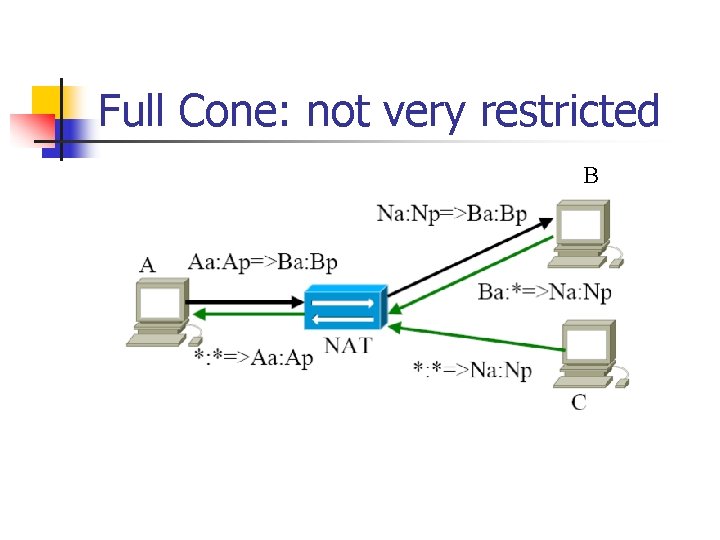
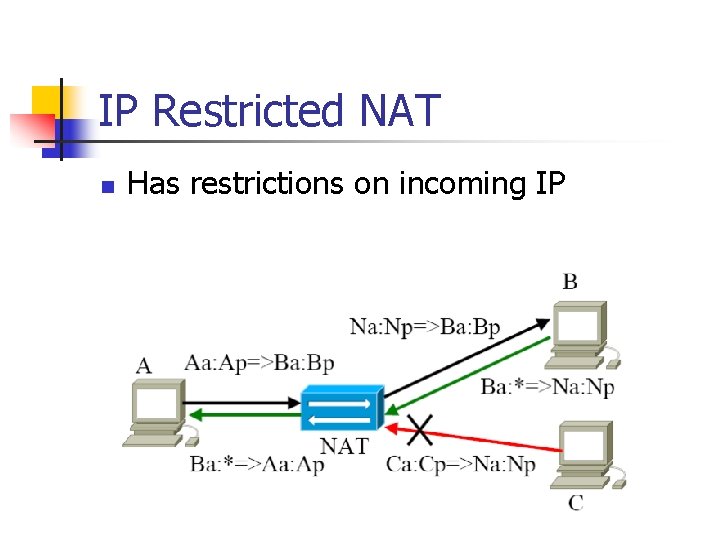
Four Types of NAT Full Cone NAT 2. IP Restricted NAT 3. Port Restricted NAT 4. Symmetric NAT Then let us see how these four NATs work? 1.

Full Cone: not very restricted B

IP Restricted NAT n Has restrictions on incoming IP

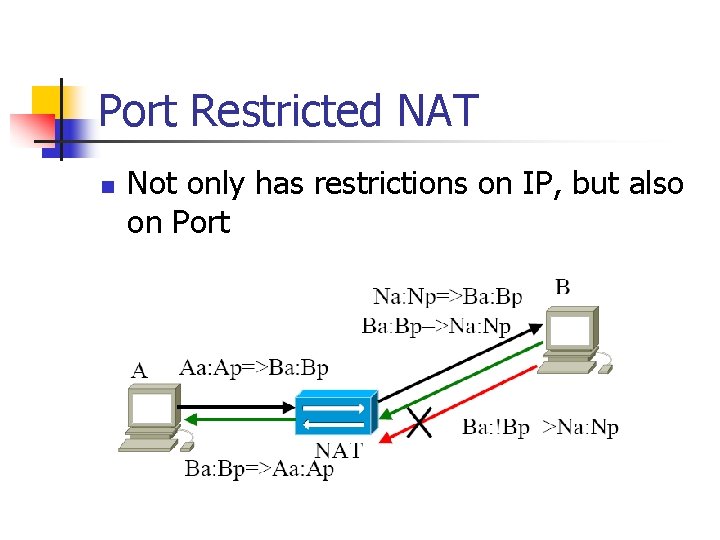
Port Restricted NAT n Not only has restrictions on IP, but also on Port

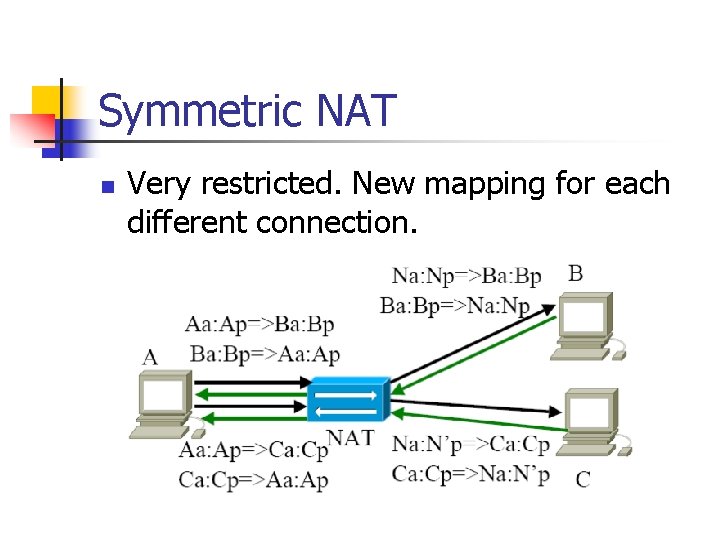
Symmetric NAT n Very restricted. New mapping for each different connection.

Problems caused by NAT n n So, When we do communication with NAT, outside packets can not come in until inside packets go out first. We need to find a way to overcome this problem and this technique is called NAT Traversal.

NAT Traversal n 1. 2. n 1. 2. Our plan We need to know what NAT we are behind Do NAT traversal according to the identified NAT Therefore, two main parts in our research NAT Detection NAT Traversal

NAT Detection We get the Poly. NAT from Dr. Hoffman. It can emulates four different NATs. Thanks to Dr. Hoffman and his students.

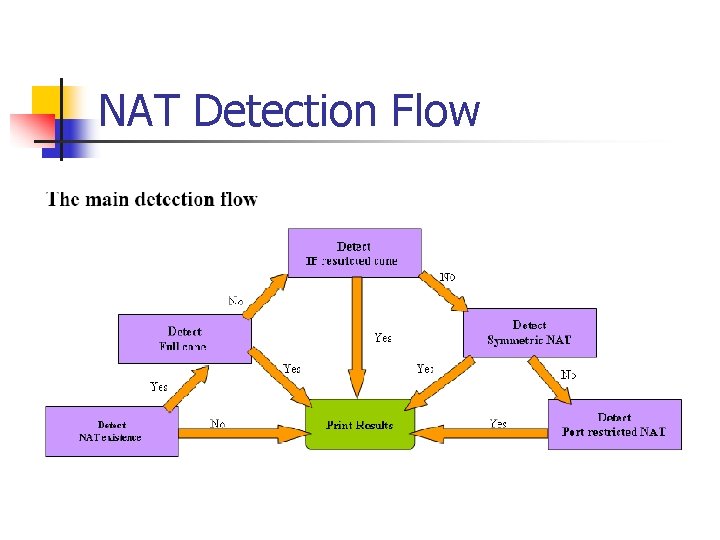
NAT Detection Flow

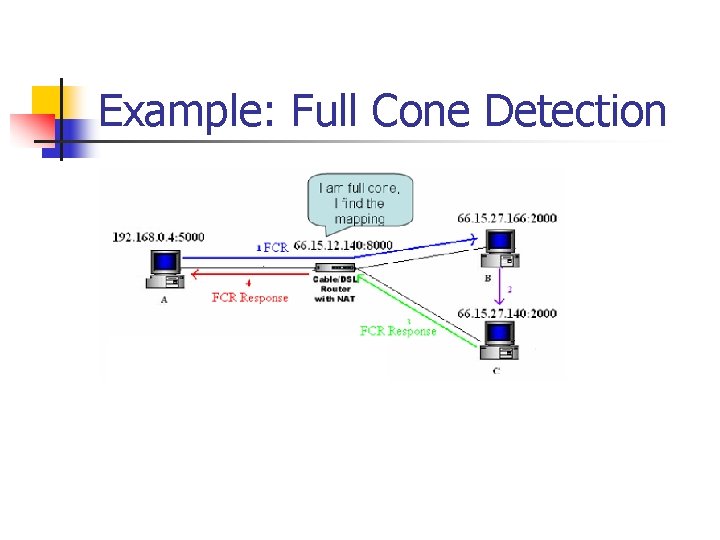
Example: Full Cone Detection

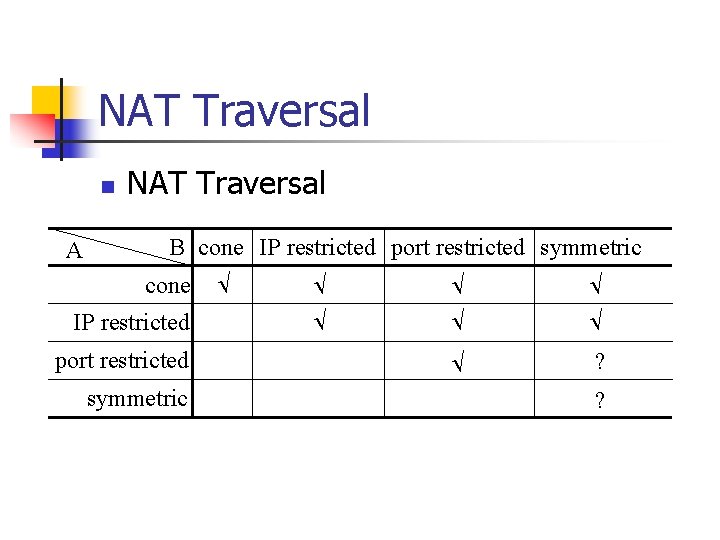
NAT Traversal n A NAT Traversal B cone IP restricted port restricted symmetric ? ?

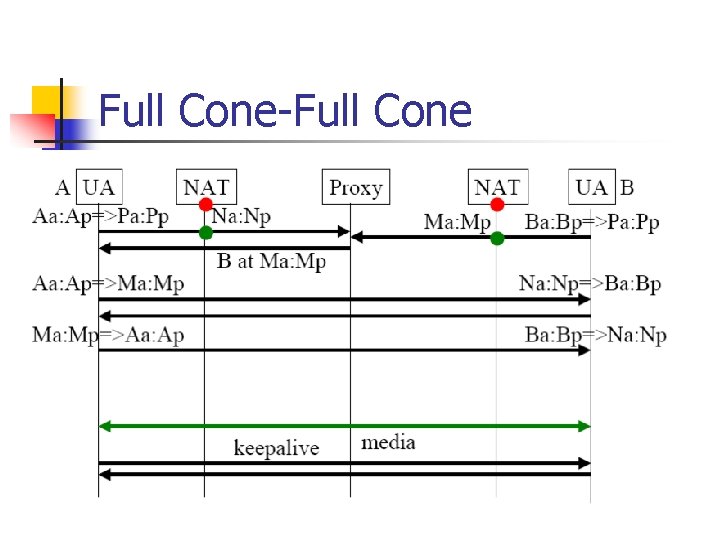
Full Cone-Full Cone

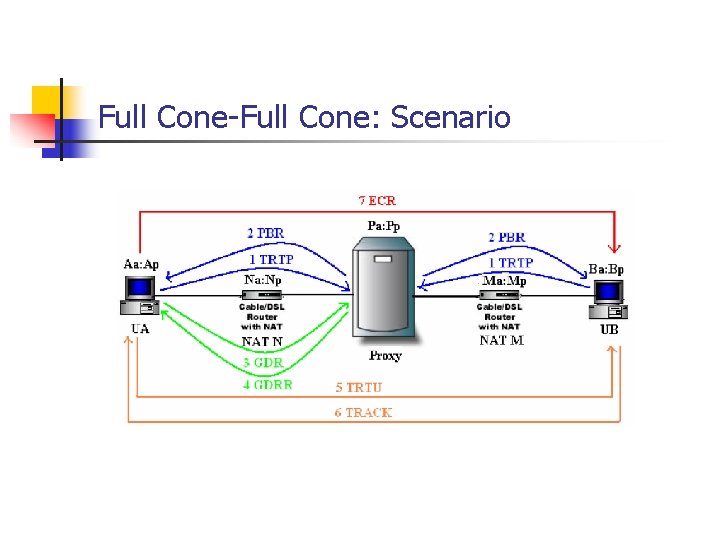
Full Cone-Full Cone: Scenario

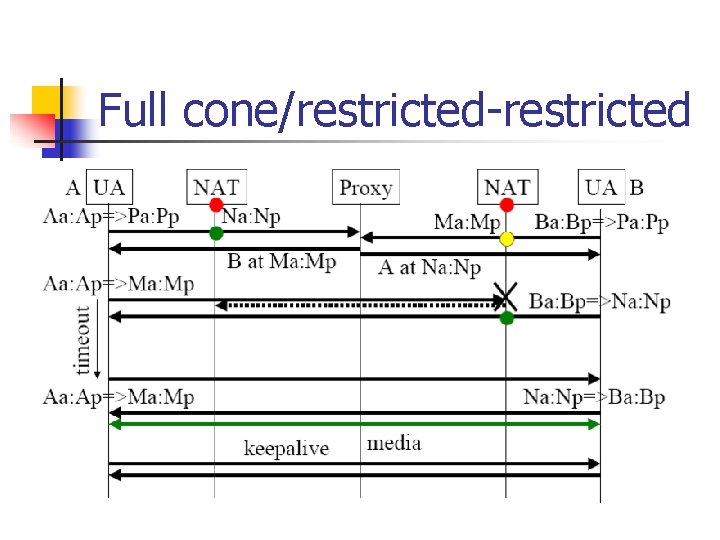
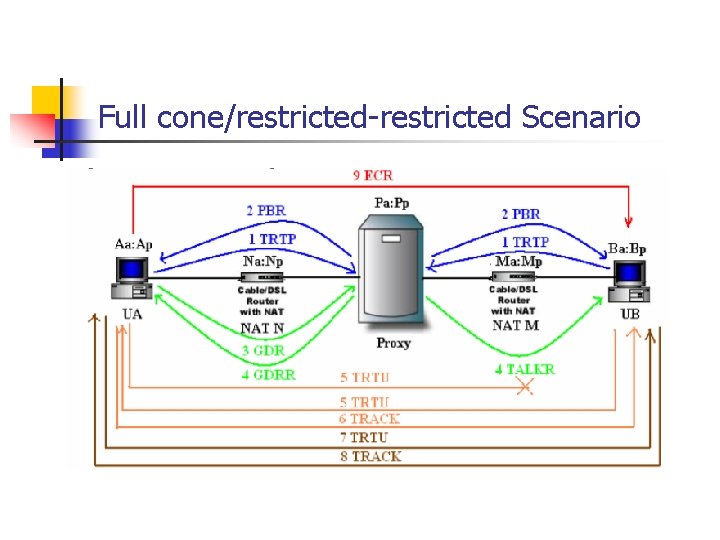
Full cone/restricted-restricted

Full cone/restricted-restricted Scenario

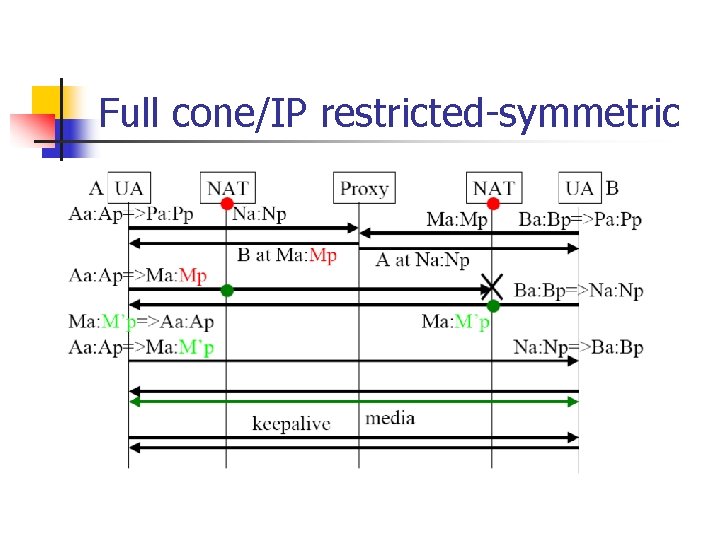
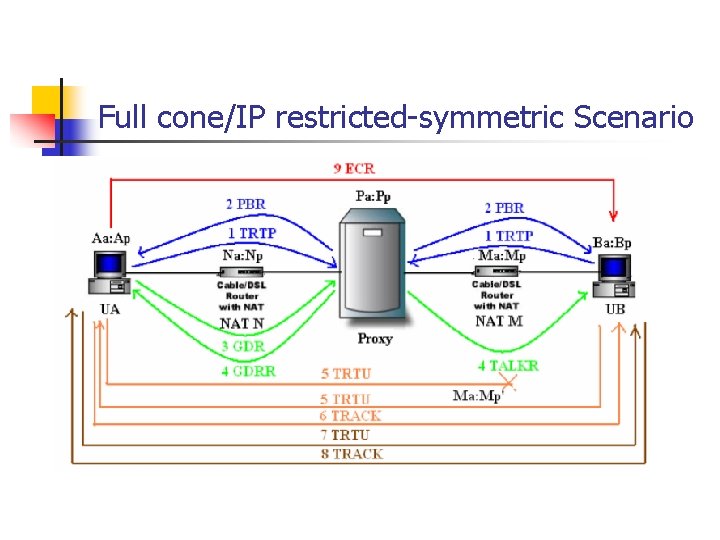
Full cone/IP restricted-symmetric

Full cone/IP restricted-symmetric Scenario

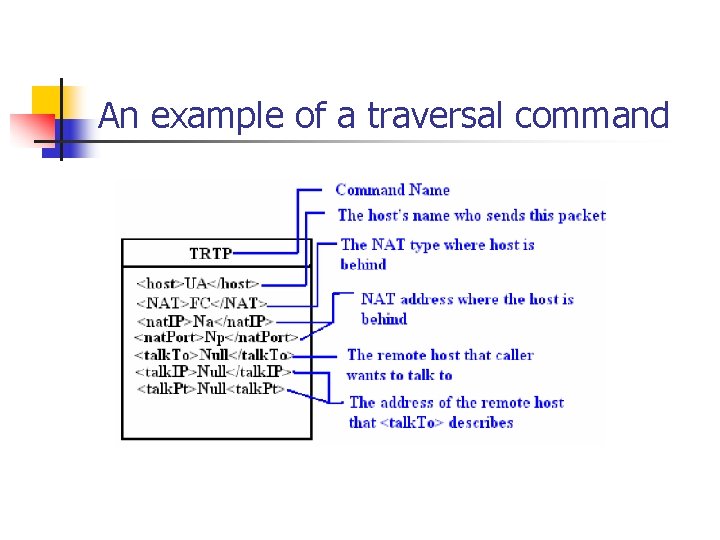
How does clients describe who they are n n n We build our own traversal commands We use XML to describe necessary information and embed these descriptions in our traversal commands. So, other clients get specified information about their peers by learning these XML contents.

An example of a traversal command

Conclusion n We have implemented 3. Full Cone – Full Cone Full/Restricted Cone – Restricted Cone Full/IP Restricted Cone – Symmetric n The things we will do in the future 1. 2. Port Restricted Cone – Symmetric

NAT and NAT Traversal n Questions?