Introducing NAT and PAT Network Address Translation Inside



- Slides: 22



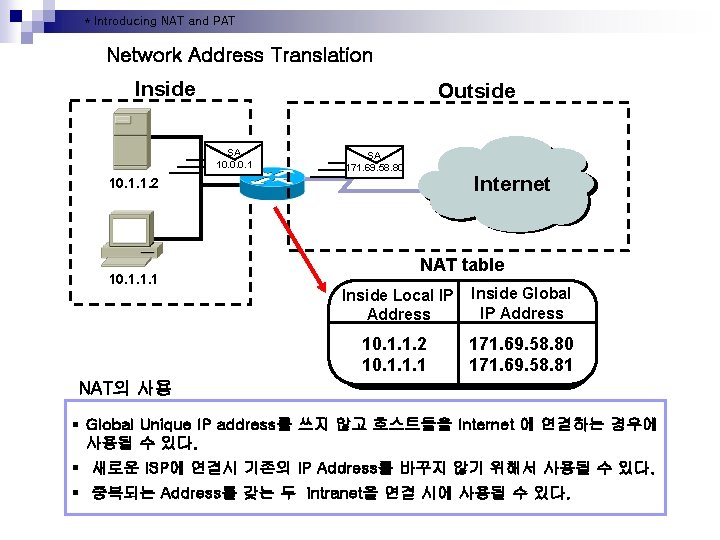
* Introducing NAT and PAT Network Address Translation Inside Outside SA 10. 0. 0. 1 SA 171. 69. 58. 80 Internet 10. 1. 1. 2 10. 1. 1. 1 NAT table Inside Local IP Address Inside Global IP Address 10. 1. 1. 2 10. 1. 1. 1 171. 69. 58. 80 171. 69. 58. 81 NAT의 사용 § Global Unique IP address를 쓰지 않고 호스트들을 Internet 에 연결하는 경우에 사용될 수 있다. § 새로운 ISP에 연결시 기존의 IP Address를 바꾸지 않기 위해서 사용될 수 있다. § 중복되는 Address를 갖는 두 intranet을 연결 시에 사용될 수 있다.

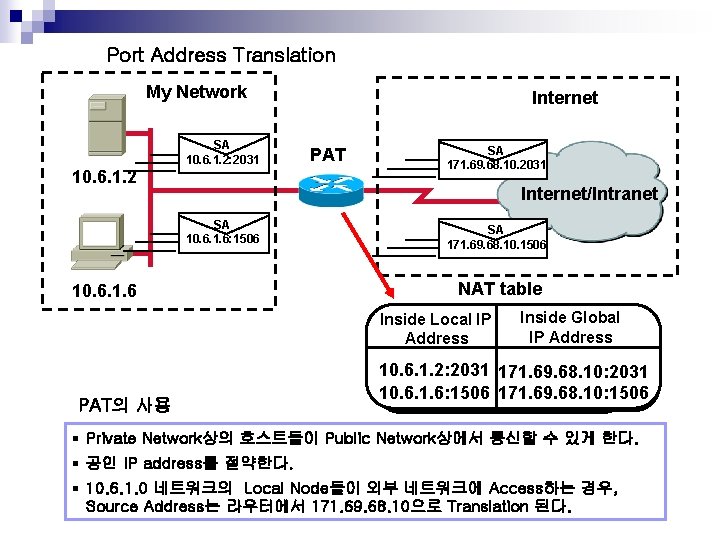
Port Address Translation My Network SA 10. 6. 1. 2: 2031 10. 6. 1. 2 Internet PAT SA 171. 69. 68. 10. 2031 Internet/Intranet SA 10. 6. 1. 6: 1506 10. 6. 1. 6 SA 171. 69. 68. 10. 1506 NAT table Inside Local IP Address PAT의 사용 Inside Global IP Address 10. 6. 1. 2: 2031 171. 69. 68. 10: 2031 10. 6. 1. 6: 1506 171. 69. 68. 10: 1506 § Private Network상의 호스트들이 Public Network상에서 통신할 수 있게 한다. § 공인 IP address를 절약한다. § 10. 6. 1. 0 네트워크의 Local Node들이 외부 네트워크에 Access하는 경우, Source Address는 라우터에서 171. 69. 68. 10으로 Translation 된다.

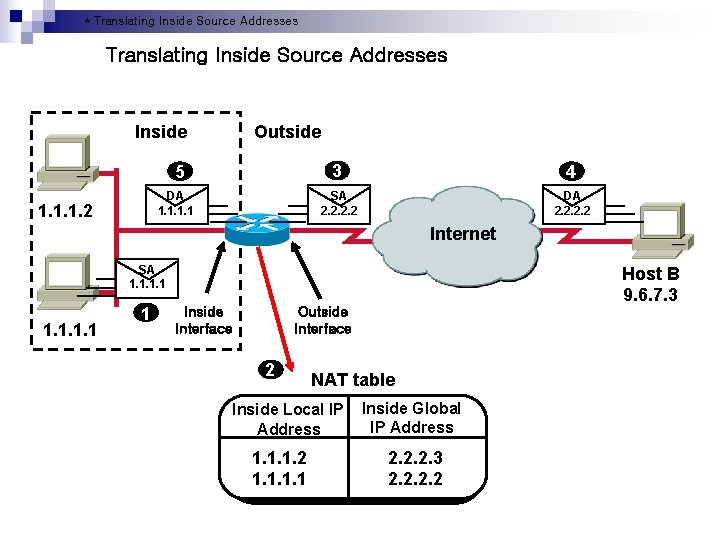
* Translating Inside Source Addresses Inside Outside 5 DA 1. 1. 2 3 4 SA 2. 2 DA 2. 2 Internet SA 1. 1 1 Inside Interface Host B 9. 6. 7. 3 Outside Interface 2 NAT table Inside Local IP Address 1. 1. 1. 2 1. 1 Inside Global IP Address 2. 2. 2. 3 2. 2

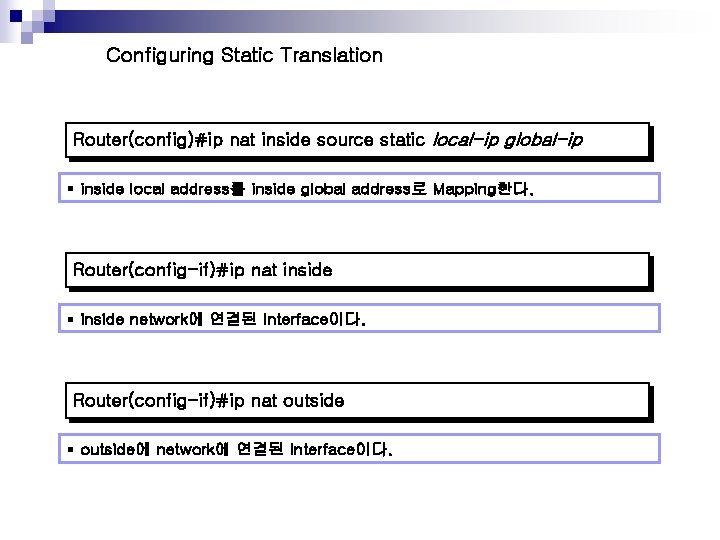
Configuring Static Translation Router(config)#ip nat inside source static local-ip global-ip § inside local address를 inside global address로 Mapping한다. Router(config-if)#ip nat inside § inside network에 연결된 Interface이다. Router(config-if)#ip nat outside § outside에 network에 연결된 Interface이다.

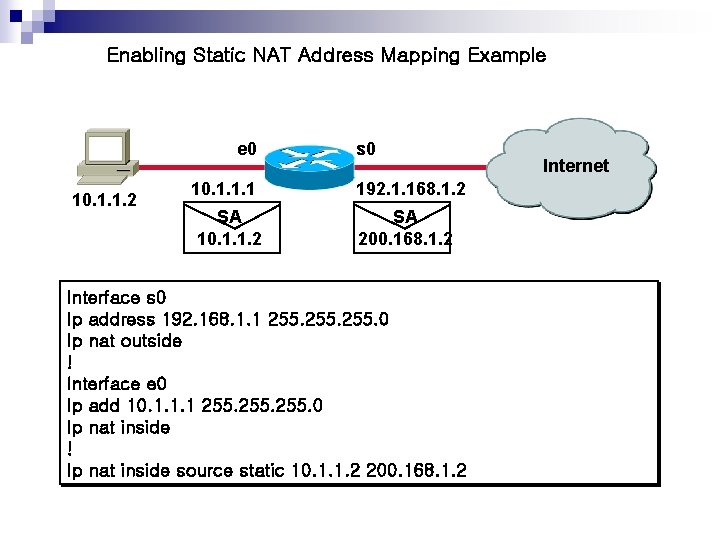
Enabling Static NAT Address Mapping Example 5 10. 1. 1. 2 e 0 s 0 10. 1. 1. 1 192. 1. 168. 1. 2 SA 10. 1. 1. 2 SA 200. 168. 1. 2 Interface s 0 Ip address 192. 168. 1. 1 255. 0 Ip nat outside ! Interface e 0 Ip add 10. 1. 1. 1 255. 0 Ip nat inside ! Ip nat inside source static 10. 1. 1. 2 200. 168. 1. 2 Internet

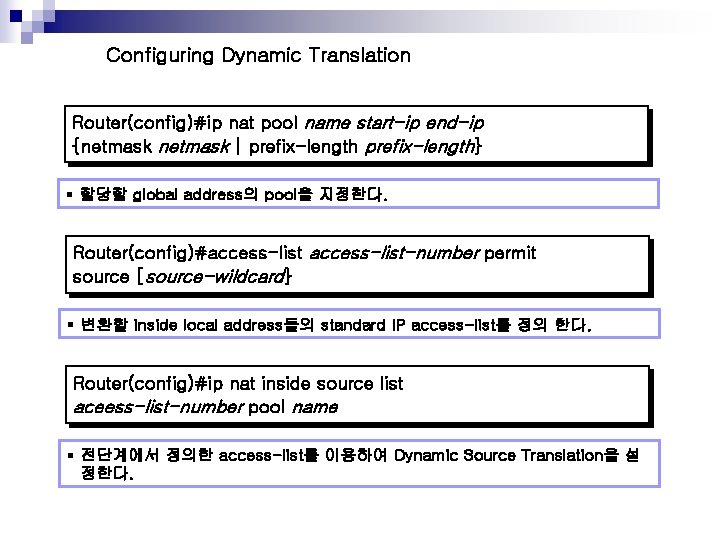
Configuring Dynamic Translation Router(config)#ip nat pool name start-ip end-ip {netmask | prefix-length} § 할당할 global address의 pool을 지정한다. Router(config)#access-list-number permit source [source-wildcard} § 변환할 inside local address들의 standard IP access-list를 정의 한다. Router(config)#ip nat inside source list aceess-list-number pool name § 전단계에서 정의한 access-list를 이용하여 Dynamic Source Translation을 설 정한다.

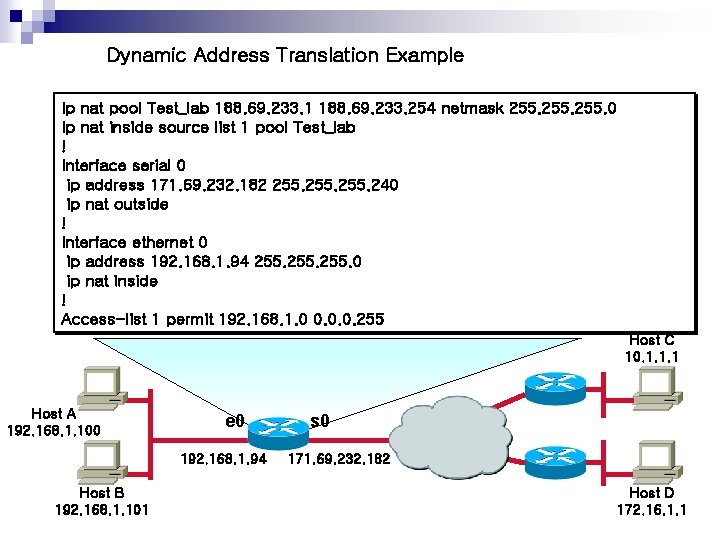
Dynamic Address Translation Example Ip nat pool Test_lab 188. 69. 233. 1 188. 69. 233. 254 netmask 255. 0 Ip nat inside source list 1 pool Test_lab ! Interface serial 0 ip address 171. 69. 232. 182 255. 240 ip nat outside ! Interface ethernet 0 ip address 192. 168. 1. 94 255. 0 ip nat inside ! Access-list 1 permit 192. 168. 1. 0 0. 0. 0. 255 Host C 10. 1. 1. 1 Host A 192. 168. 1. 100 e 0 192. 168. 1. 94 Host B 192. 168. 1. 101 s 0 171. 69. 232. 182 Host D 172. 16. 1. 1

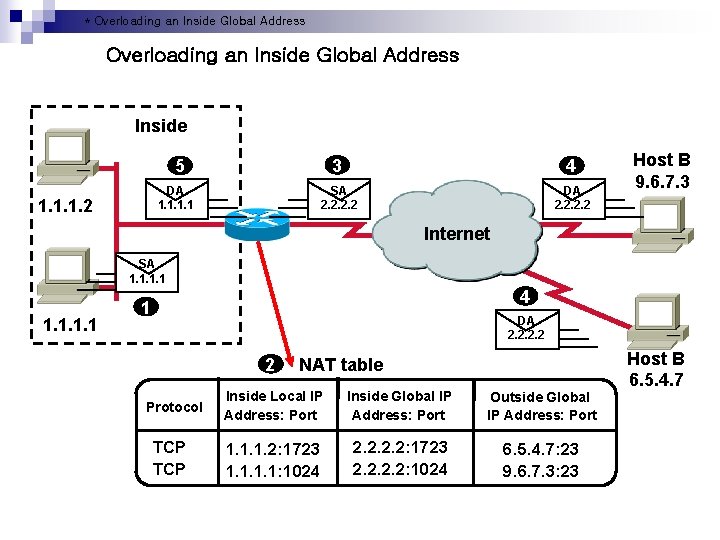
* Overloading an Inside Global Address Inside 3 4 SA 2. 2 DA 2. 2 5 DA 1. 1. 2 Host B 9. 6. 7. 3 Internet SA 1. 1 4 1 DA 2. 2 2 Protocol TCP NAT table Inside Local IP Address: Port Inside Global IP Address: Port Outside Global IP Address: Port 1. 1. 1. 2: 1723 1. 1: 1024 2. 2: 1723 2. 2: 1024 6. 5. 4. 7: 23 9. 6. 7. 3: 23 Host B 6. 5. 4. 7

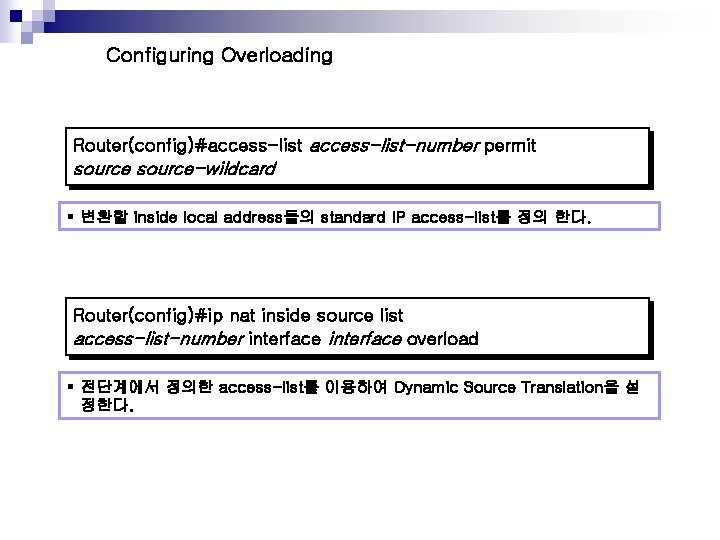
Configuring Overloading Router(config)#access-list-number permit source-wildcard § 변환할 inside local address들의 standard IP access-list를 정의 한다. Router(config)#ip nat inside source list access-list-number interface overload § 전단계에서 정의한 access-list를 이용하여 Dynamic Source Translation을 설 정한다.

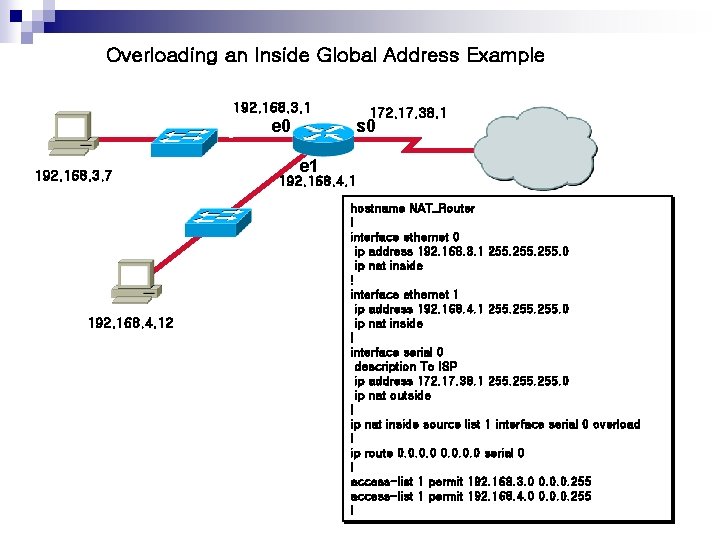
Overloading an Inside Global Address Example 192. 168. 3. 1 5 192. 168. 3. 7 192. 168. 4. 12 e 0 172. 17. 38. 1 s 0 e 1 192. 168. 4. 1 hostname NAT_Router ! interface ethernet 0 ip address 192. 168. 3. 1 255. 0 ip nat inside ! interface ethernet 1 ip address 192. 168. 4. 1 255. 0 ip nat inside ! interface serial 0 description To ISP ip address 172. 17. 38. 1 255. 0 ip nat outside ! ip nat inside source list 1 interface serial 0 overload ! ip route 0. 0 serial 0 ! access-list 1 permit 192. 168. 3. 0 0. 0. 0. 255 access-list 1 permit 192. 168. 4. 0 0. 0. 0. 255 !

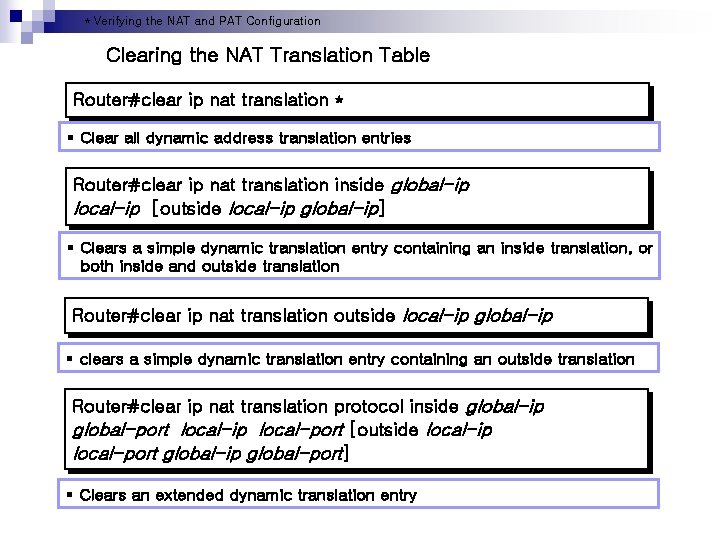
* Verifying the NAT and PAT Configuration Clearing the NAT Translation Table Router#clear ip nat translation * § Clear all dynamic address translation entries Router#clear ip nat translation inside global-ip local-ip [outside local-ip global-ip] § Clears a simple dynamic translation entry containing an inside translation, or both inside and outside translation Router#clear ip nat translation outside local-ip global-ip § clears a simple dynamic translation entry containing an outside translation Router#clear ip nat translation protocol inside global-ip global-port local-ip local-port [outside local-ip local-port global-ip global-port] § Clears an extended dynamic translation entry

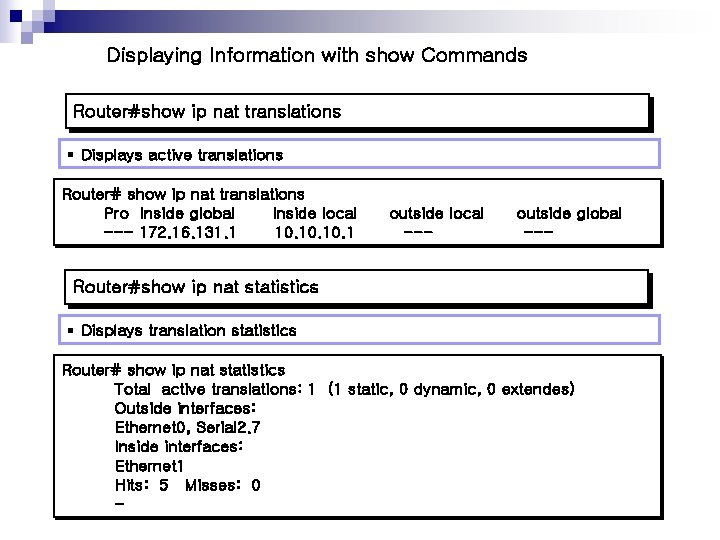
Displaying Information with show Commands Router#show ip nat translations § Displays active translations Router# show ip nat translations Pro Inside global Inside local --- 172. 16. 131. 1 10. 10. 1 outside local --- outside global --- Router#show ip nat statistics § Displays translation statistics Router# show ip nat statistics Total active translations: 1 (1 static, 0 dynamic, 0 extendes) Outside interfaces: Ethernet 0, Serial 2. 7 Inside interfaces: Ethernet 1 Hits: 5 Misses: 0 -

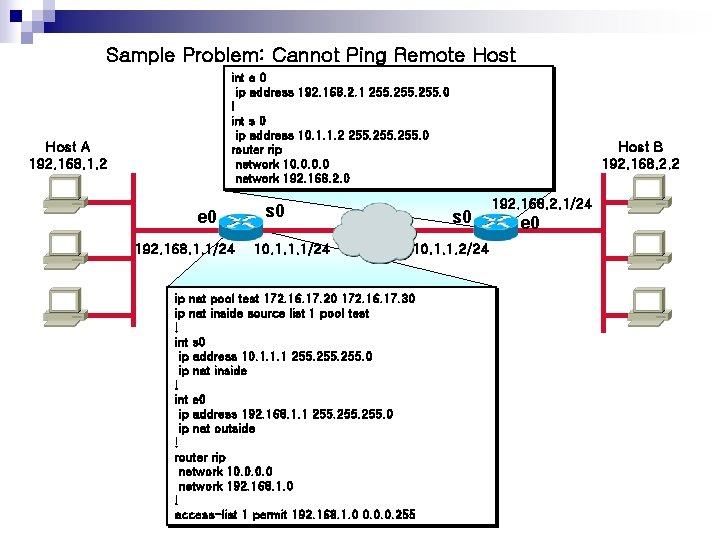
Sample Problem: Cannot Ping Remote Host int e 0 ip address 192. 168. 2. 1 255. 0 ! int s 0 ip address 10. 1. 1. 2 255. 0 router rip network 10. 0 network 192. 168. 2. 0 Host A 192. 168. 1. 2 e 0 192. 168. 1. 1/24 s 0 10. 1. 1. 1/24 Host B 192. 168. 2. 2 s 0 10. 1. 1. 2/24 ip nat pool test 172. 16. 17. 20 172. 16. 17. 30 ip nat inside source list 1 pool test ! int s 0 ip address 10. 1. 1. 1 255. 0 ip nat inside ! int e 0 ip address 192. 168. 1. 1 255. 0 ip nat outside ! router rip network 10. 0 network 192. 168. 1. 0 ! access-list 1 permit 192. 168. 1. 0 0. 0. 0. 255 192. 168. 2. 1/24 e 0

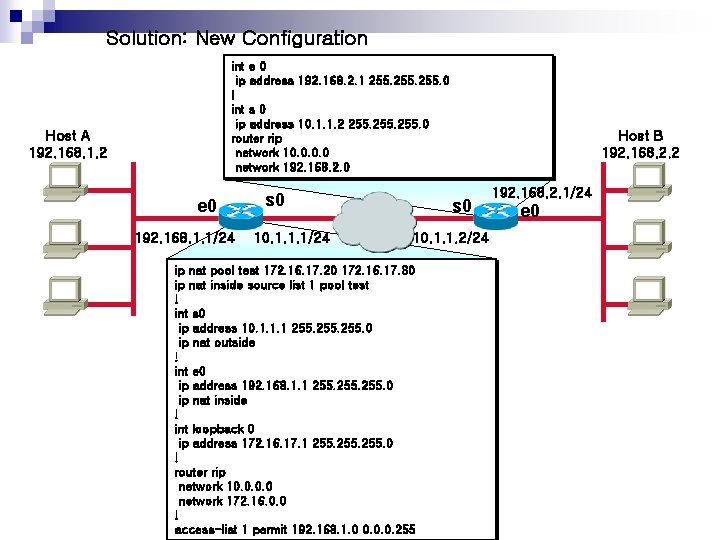
Solution: New Configuration int e 0 ip address 192. 168. 2. 1 255. 0 ! int s 0 ip address 10. 1. 1. 2 255. 0 router rip network 10. 0 network 192. 168. 2. 0 Host A 192. 168. 1. 2 e 0 192. 168. 1. 1/24 s 0 10. 1. 1. 1/24 Host B 192. 168. 2. 2 s 0 10. 1. 1. 2/24 ip nat pool test 172. 16. 17. 20 172. 16. 17. 30 ip nat inside source list 1 pool test ! int s 0 ip address 10. 1. 1. 1 255. 0 ip nat outside ! int e 0 ip address 192. 168. 1. 1 255. 0 ip nat inside ! int loopback 0 ip address 172. 16. 17. 1 255. 0 ! router rip network 10. 0 network 172. 16. 0. 0 ! access-list 1 permit 192. 168. 1. 0 0. 0. 0. 255 192. 168. 2. 1/24 e 0

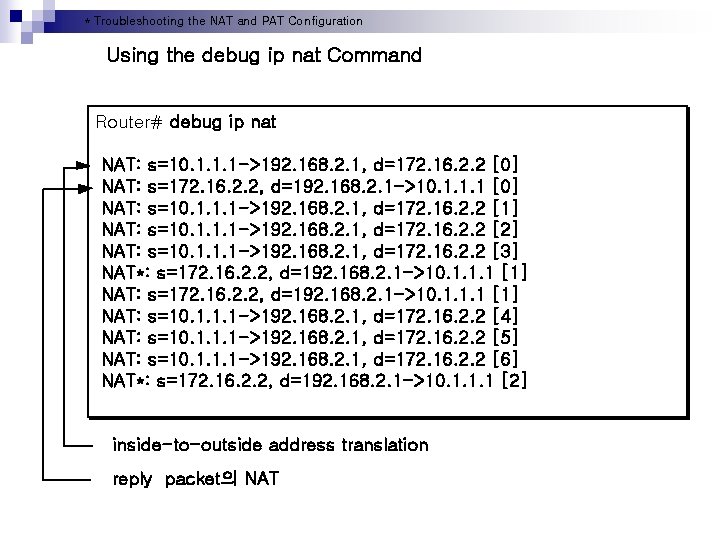
* Troubleshooting the NAT and PAT Configuration Using the debug ip nat Command Router# debug ip nat NAT: s=10. 1. 1. 1 ->192. 168. 2. 1, d=172. 16. 2. 2 [0] NAT: s=172. 16. 2. 2, d=192. 168. 2. 1 ->10. 1. 1. 1 [0] NAT: s=10. 1. 1. 1 ->192. 168. 2. 1, d=172. 16. 2. 2 [1] NAT: s=10. 1. 1. 1 ->192. 168. 2. 1, d=172. 16. 2. 2 [2] NAT: s=10. 1. 1. 1 ->192. 168. 2. 1, d=172. 16. 2. 2 [3] NAT*: s=172. 16. 2. 2, d=192. 168. 2. 1 ->10. 1. 1. 1 [1] NAT: s=10. 1. 1. 1 ->192. 168. 2. 1, d=172. 16. 2. 2 [4] NAT: s=10. 1. 1. 1 ->192. 168. 2. 1, d=172. 16. 2. 2 [5] NAT: s=10. 1. 1. 1 ->192. 168. 2. 1, d=172. 16. 2. 2 [6] NAT*: s=172. 16. 2. 2, d=192. 168. 2. 1 ->10. 1. 1. 1 [2] inside-to-outside address translation reply packet의 NAT


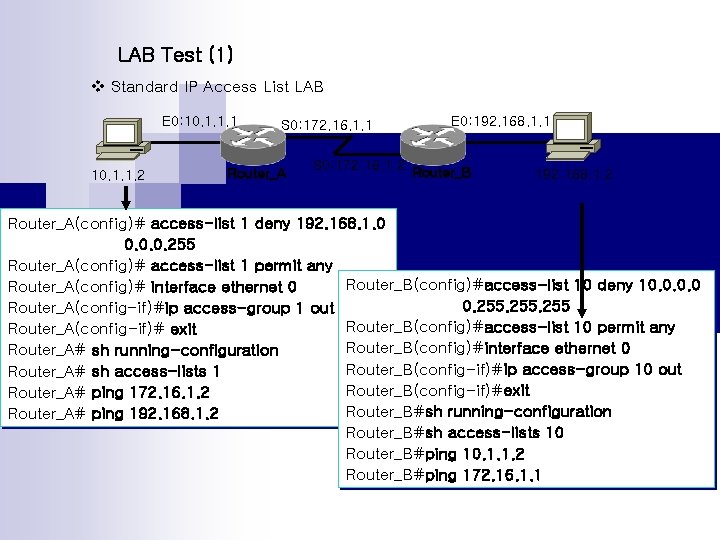
LAB Test (1) v Standard IP Access List LAB E 0: 10. 1. 1. 1 10. 1. 1. 2 S 0: 172. 16. 1. 1 Router_A E 0: 192. 168. 1. 1 S 0: 172. 16. 1. 2 Router_B 192. 168. 1. 2 Router_A(config)# access-list 1 deny 192. 168. 1. 0 0. 0. 0. 255 Router_A(config)# access-list 1 permit any Router_B(config)#access-list 10 deny 10. 0 Router_A(config)# interface ethernet 0 0. 255 Router_A(config-if)#ip access-group 1 out Router_B(config)#access-list 10 permit any Router_A(config-if)# exit Router_B(config)#interface ethernet 0 Router_A# sh running-configuration Router_B(config-if)#ip access-group 10 out Router_A# sh access-lists 1 Router_B(config-if)#exit Router_A# ping 172. 16. 1. 2 Router_B#sh running-configuration Router_A# ping 192. 168. 1. 2 Router_B#sh access-lists 10 Router_B#ping 10. 1. 1. 2 Router_B#ping 172. 16. 1. 1

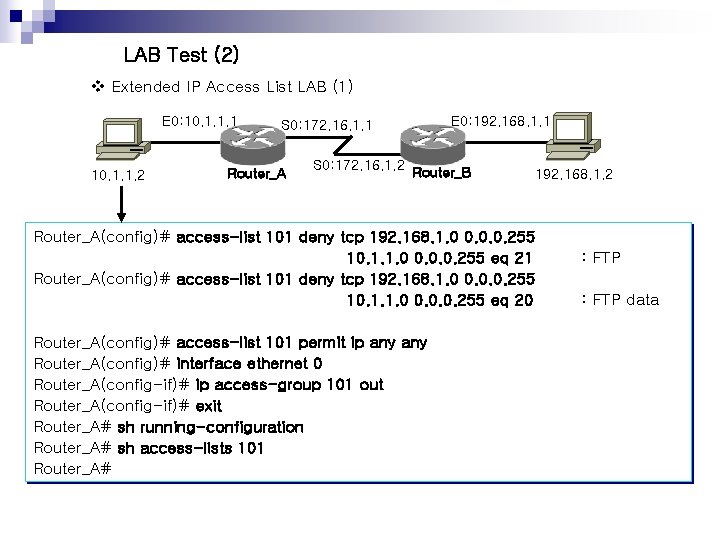
LAB Test (2) v Extended IP Access List LAB (1) E 0: 10. 1. 1. 1 10. 1. 1. 2 S 0: 172. 16. 1. 1 Router_A E 0: 192. 168. 1. 1 S 0: 172. 16. 1. 2 Router_B 192. 168. 1. 2 Router_A(config)# access-list 101 deny tcp 192. 168. 1. 0 0. 0. 0. 255 10. 1. 1. 0 0. 0. 0. 255 eq 21 Router_A(config)# access-list 101 deny tcp 192. 168. 1. 0 0. 0. 0. 255 10. 1. 1. 0 0. 0. 0. 255 eq 20 Router_A(config)# access-list 101 permit ip any Router_A(config)# interface ethernet 0 Router_A(config-if)# ip access-group 101 out Router_A(config-if)# exit Router_A# sh running-configuration Router_A# sh access-lists 101 Router_A# : FTP data

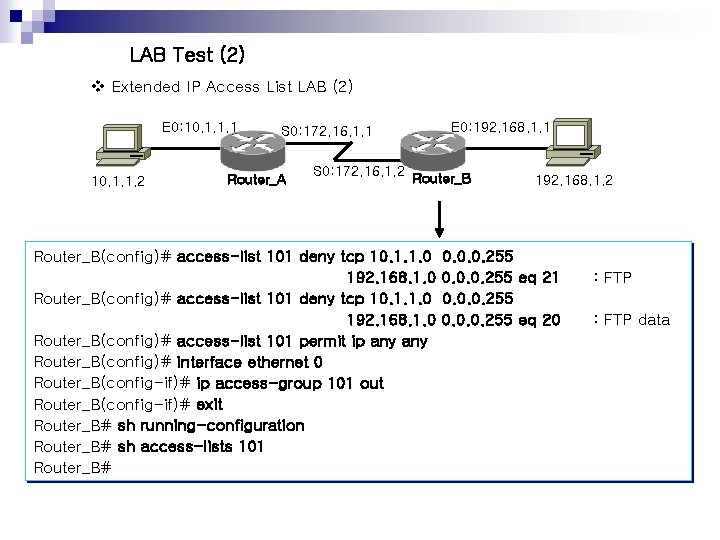
LAB Test (2) v Extended IP Access List LAB (2) E 0: 10. 1. 1. 1 10. 1. 1. 2 S 0: 172. 16. 1. 1 Router_A E 0: 192. 168. 1. 1 S 0: 172. 16. 1. 2 Router_B(config)# access-list 101 deny tcp 10. 1. 1. 0 192. 168. 1. 0 Router_B(config)# access-list 101 permit ip any Router_B(config)# interface ethernet 0 Router_B(config-if)# ip access-group 101 out Router_B(config-if)# exit Router_B# sh running-configuration Router_B# sh access-lists 101 Router_B# 192. 168. 1. 2 0. 0. 0. 255 eq 21 0. 0. 0. 255 eq 20 : FTP data

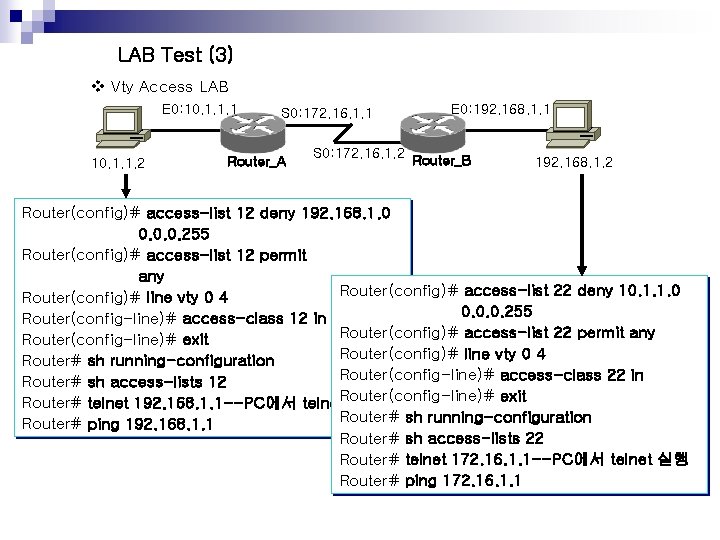
LAB Test (3) v Vty Access LAB E 0: 10. 1. 1. 1 10. 1. 1. 2 S 0: 172. 16. 1. 1 Router_A E 0: 192. 168. 1. 1 S 0: 172. 16. 1. 2 Router_B 192. 168. 1. 2 Router(config)# access-list 12 deny 192. 168. 1. 0 0. 0. 0. 255 Router(config)# access-list 12 permit any Router(config)# access-list 22 deny 10. 1. 1. 0 Router(config)# line vty 0 4 0. 0. 0. 255 Router(config-line)# access-class 12 in Router(config)# access-list 22 permit any Router(config-line)# exit Router(config)# line vty 0 4 Router# sh running-configuration Router(config-line)# access-class 22 in Router# sh access-lists 12 exit Router# telnet 192. 168. 1. 1 --PC에서 telnet. Router(config-line)# 실행 Router# sh running-configuration Router# ping 192. 168. 1. 1 Router# sh access-lists 22 Router# telnet 172. 16. 1. 1 --PC에서 telnet 실행 Router# ping 172. 16. 1. 1