Performance Modeling of Anonymity Protocols Carey Williamson Andreas




![Classic Buses Protocol [Beimel and Dolev 2003] n n Metaphor: city bus, with regularly Classic Buses Protocol [Beimel and Dolev 2003] n n Metaphor: city bus, with regularly](https://slidetodoc.com/presentation_image_h/eb9049f91c0a15b1a7f29bc99247abf5/image-11.jpg)


- Slides: 40

Performance Modeling of Anonymity Protocols Carey Williamson Andreas Hirt Niklas Carlsson Michael J. Jacobson, Jr. Department of Computer Science University of Calgary Financial support for this research support was provided by: Natural Sciences and Engineering Research Council (NSERC), Informatics Circle of Research Excellence (i. CORE), Alberta Ingenuity Fund (AIF), and Canada Foundation for Innovation (CFI)

Introduction n Anonymous communication conceals who communicates what, to whom, and when Allows individuals to communicate without fear of embarrassment, ridicule, or retribution Cornerstone for freedom of speech 2

Some Real World Applications n Good: n n n n Freedom of speech in totalitarian regime Crime stoppers On-line counseling Whistle blowing Group evaluations Military communications … Bad: n n n Organized crime Terrorist groups. . . 3

Outline n n n Review of Anonymity Schemes Our Work: Buses, Taxis, Motorcyles Performance Modeling Numerical Results Conclusion 4

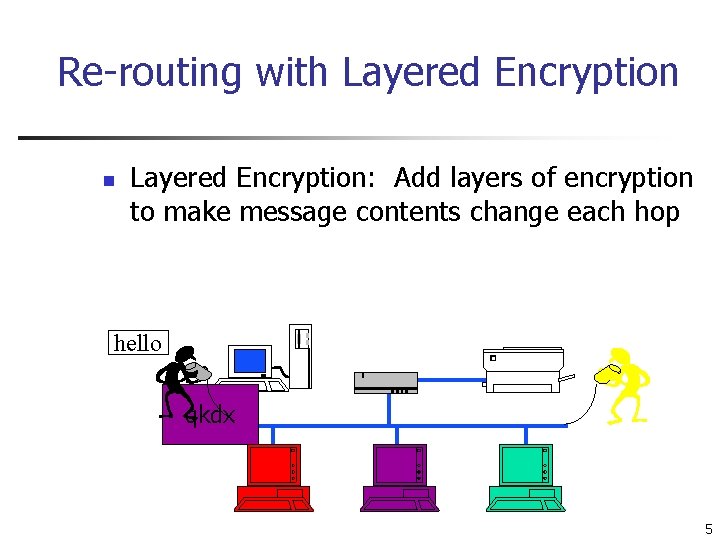
Re-routing with Layered Encryption n Layered Encryption: Add layers of encryption to make message contents change each hop hello xmkz iwqm qkdx ykrz 5

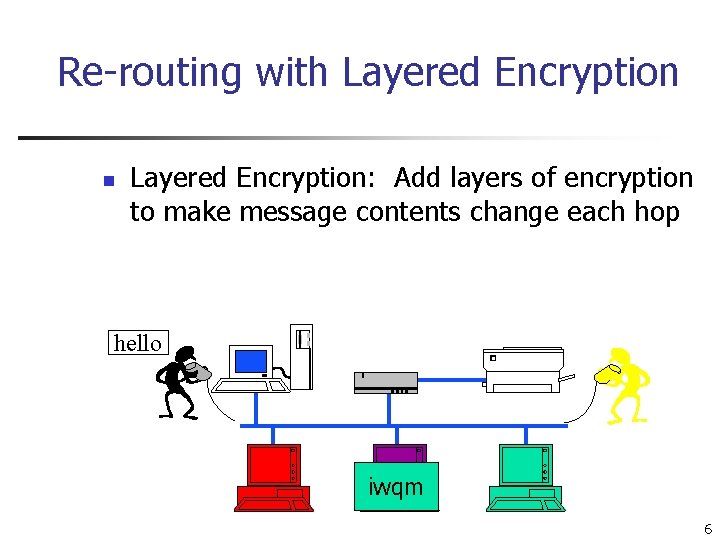
Re-routing with Layered Encryption n Layered Encryption: Add layers of encryption to make message contents change each hop hello xmkz iwqm ykrz 6

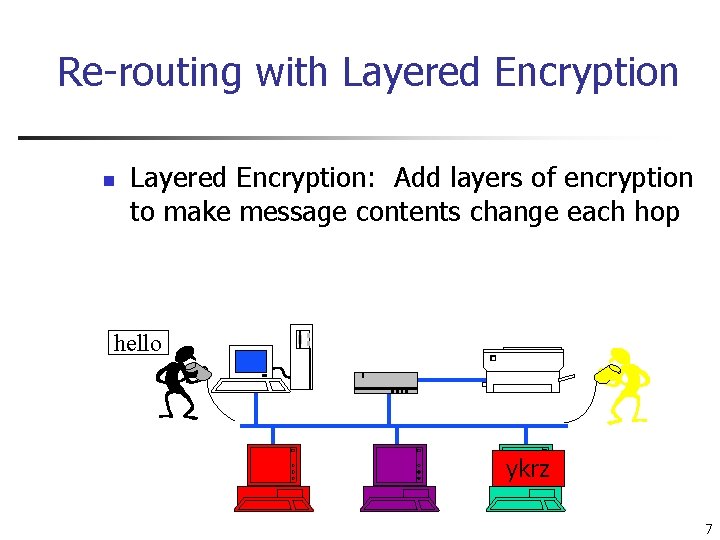
Re-routing with Layered Encryption n Layered Encryption: Add layers of encryption to make message contents change each hop hello xmkz ykrz 7

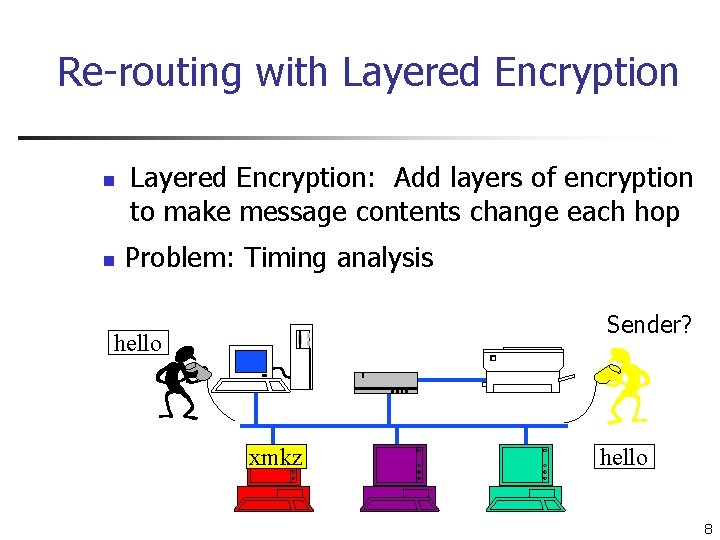
Re-routing with Layered Encryption n n Layered Encryption: Add layers of encryption to make message contents change each hop Problem: Timing analysis Sender? hello xmkz hello 8

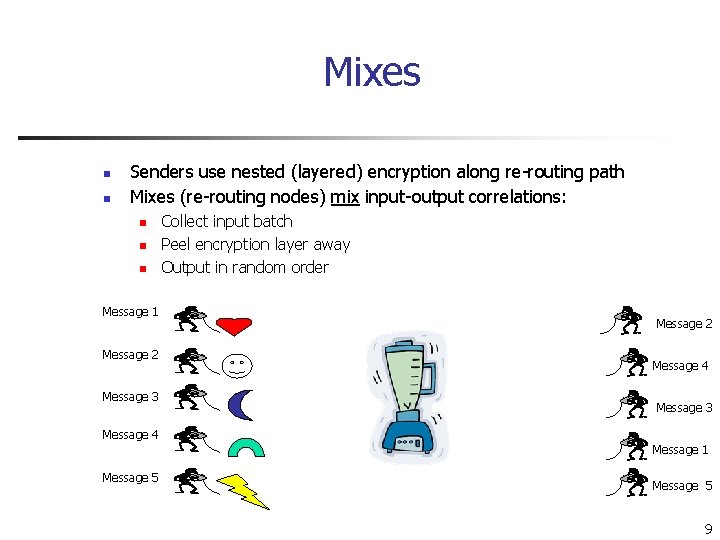
Mixes n n Senders use nested (layered) encryption along re-routing path Mixes (re-routing nodes) mix input-output correlations: n n n Message 1 Message 2 Message 3 Message 4 Message 5 Collect input batch Peel encryption layer away Output in random order Message 2 Message 4 Message 3 Message 1 Message 5 9

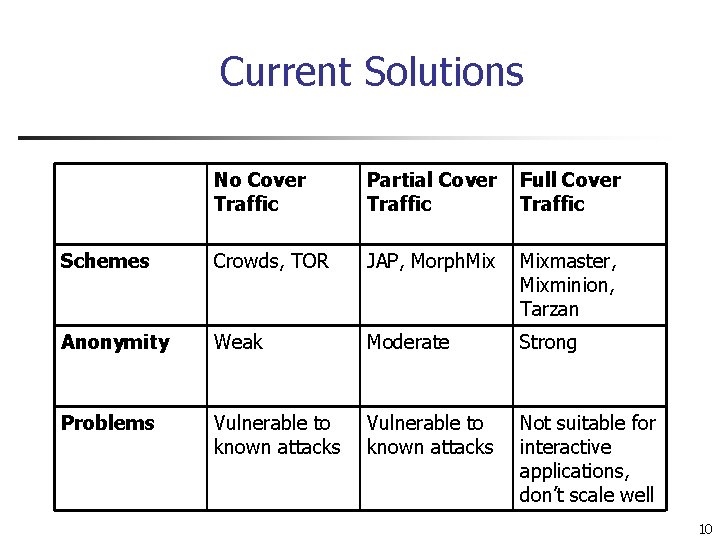
Current Solutions No Cover Traffic Partial Cover Traffic Full Cover Traffic Schemes Crowds, TOR JAP, Morph. Mixmaster, Mixminion, Tarzan Anonymity Weak Moderate Strong Problems Vulnerable to known attacks Not suitable for interactive applications, don’t scale well 10
![Classic Buses Protocol Beimel and Dolev 2003 n n Metaphor city bus with regularly Classic Buses Protocol [Beimel and Dolev 2003] n n Metaphor: city bus, with regularly](https://slidetodoc.com/presentation_image_h/eb9049f91c0a15b1a7f29bc99247abf5/image-11.jpg)
Classic Buses Protocol [Beimel and Dolev 2003] n n Metaphor: city bus, with regularly scheduled route, which obscures the movements of its messengers Assume dark windows, and enclosed garages at each stop hello 11

Anonymity in Buses n n Sender Anonymity: Suspected sender can claim they are forwarding a message on behalf of any other participant on the bus path Receiver Anonymity: Suspected receiver can claim they forwarded a message to any other participant on the bus path 12

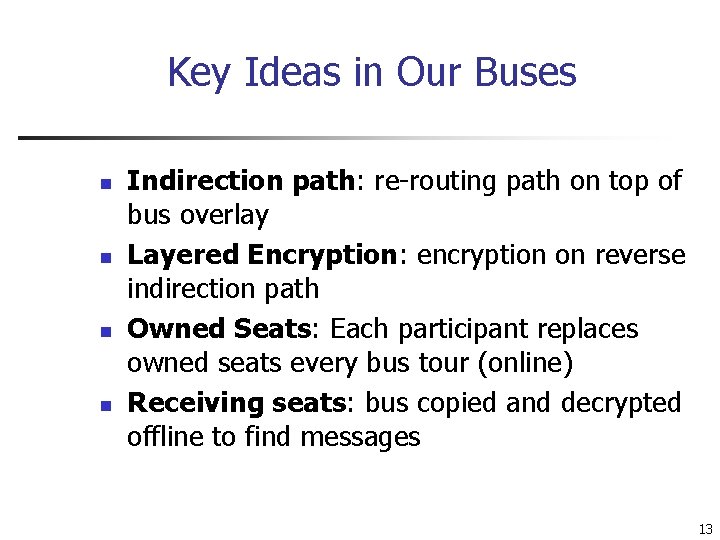
Key Ideas in Our Buses n n Indirection path: re-routing path on top of bus overlay Layered Encryption: encryption on reverse indirection path Owned Seats: Each participant replaces owned seats every bus tour (online) Receiving seats: bus copied and decrypted offline to find messages 13

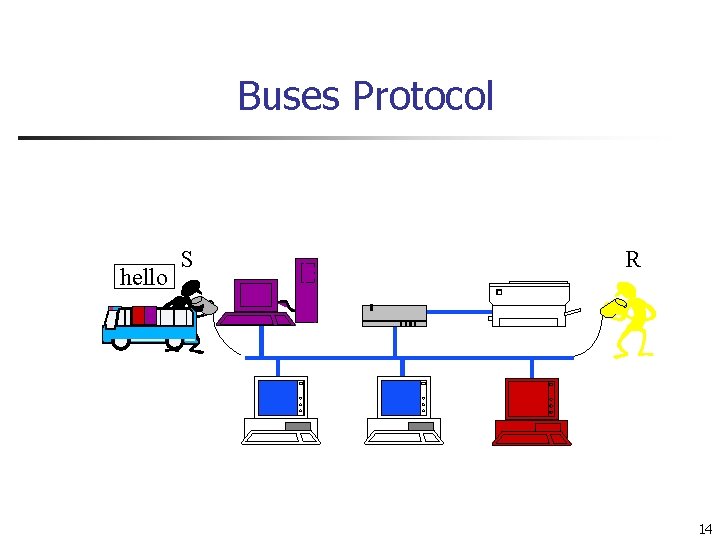
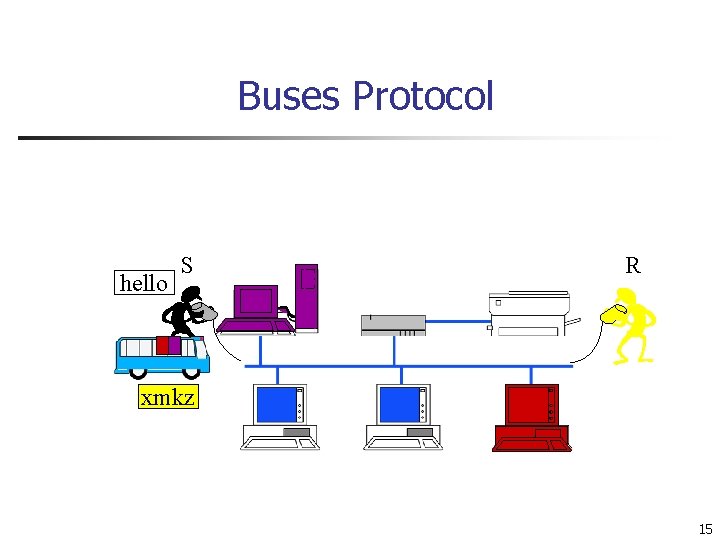
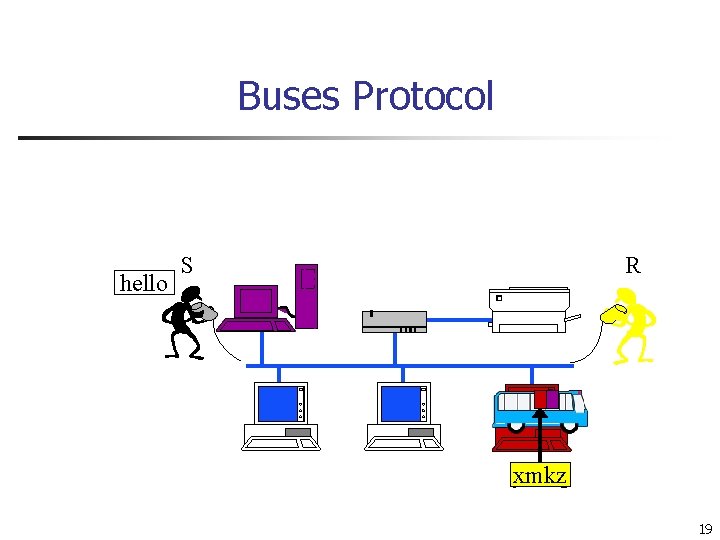
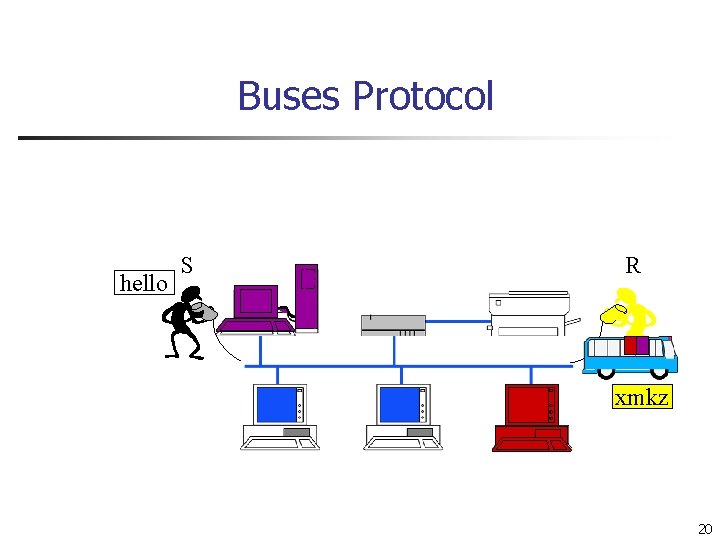
Buses Protocol hello S R 14

Buses Protocol hello S R xmkz 15

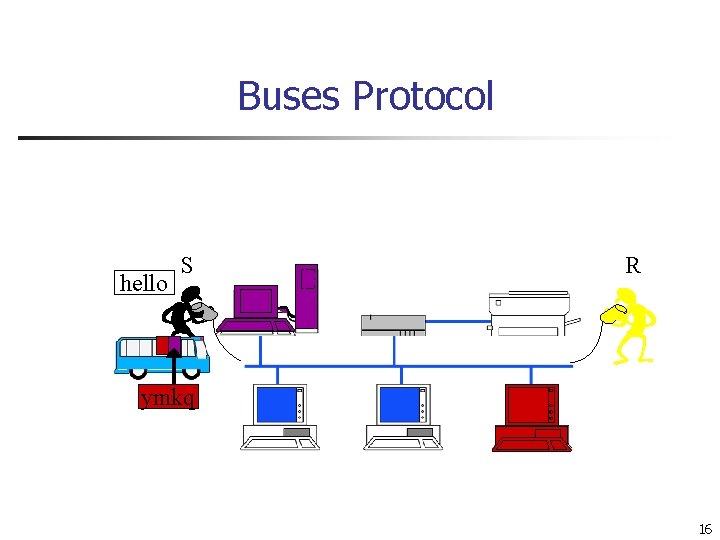
Buses Protocol hello S R ymkq 16

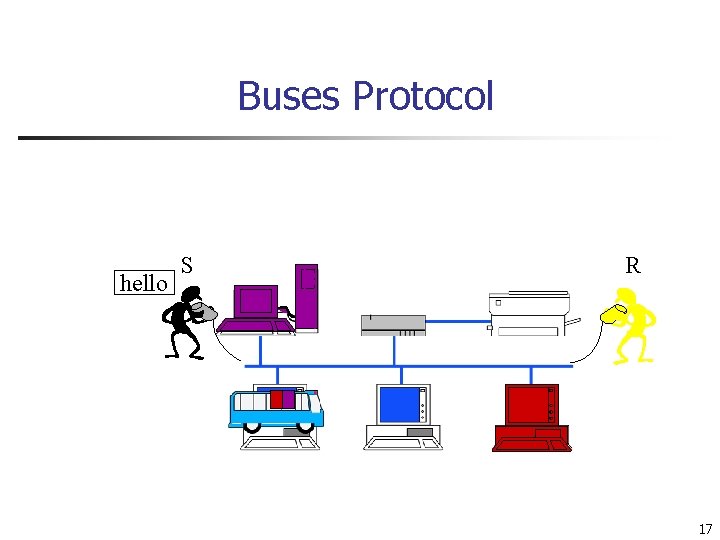
Buses Protocol hello S R 17

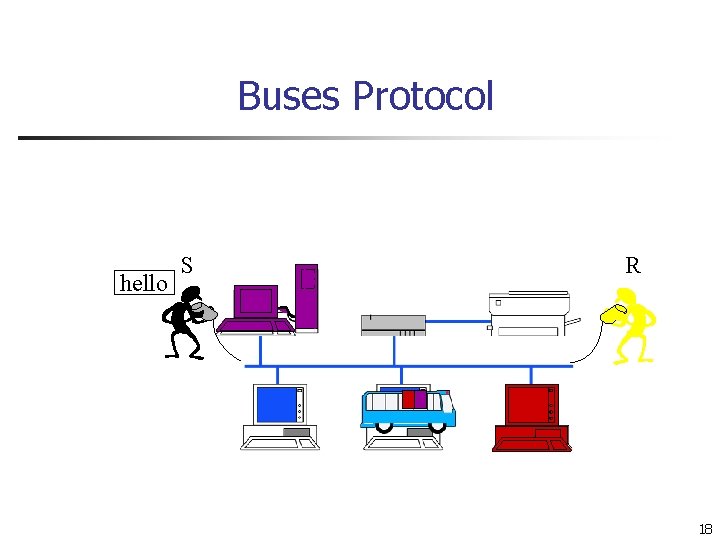
Buses Protocol hello S R 18

Buses Protocol hello S R ymkq xmkz 19

Buses Protocol hello S R xmkz hello 20

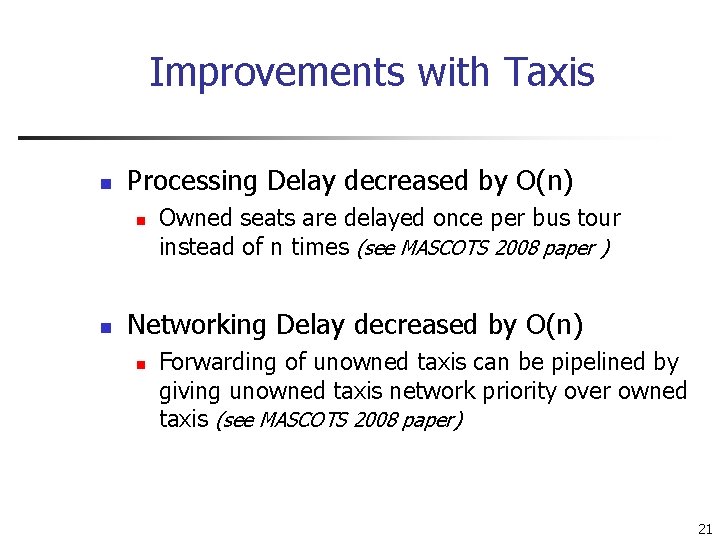
Improvements with Taxis n Processing Delay decreased by O(n) n n Owned seats are delayed once per bus tour instead of n times (see MASCOTS 2008 paper ) Networking Delay decreased by O(n) n Forwarding of unowned taxis can be pipelined by giving unowned taxis network priority over owned taxis (see MASCOTS 2008 paper) 21

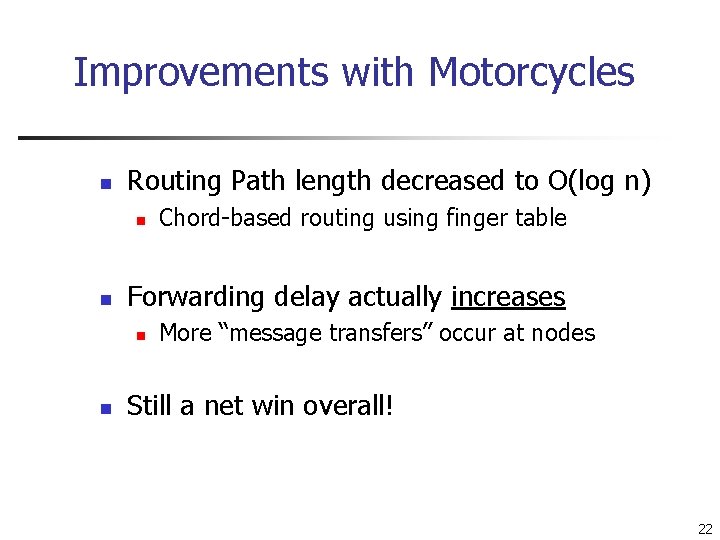
Improvements with Motorcycles n Routing Path length decreased to O(log n) n n Forwarding delay actually increases n n Chord-based routing using finger table More “message transfers” occur at nodes Still a net win overall! 22

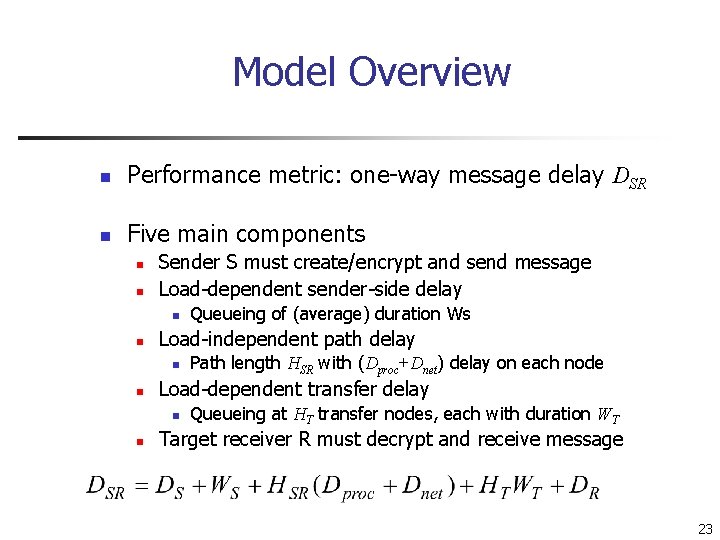
Model Overview n Performance metric: one-way message delay DSR n Five main components n n Sender S must create/encrypt and send message Load-dependent sender-side delay n n Load-independent path delay n n Path length HSR with (Dproc+Dnet) delay on each node Load-dependent transfer delay n n Queueing of (average) duration Ws Queueing at HT transfer nodes, each with duration WT Target receiver R must decrypt and receive message 23

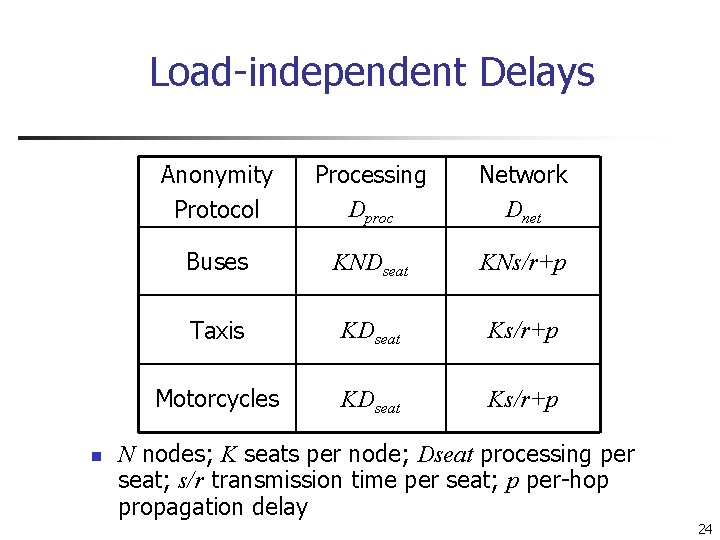
Load-independent Delays n Anonymity Protocol Processing Dproc Network Dnet Buses KNDseat KNs/r+p Taxis KDseat Ks/r+p Motorcycles KDseat Ks/r+p N nodes; K seats per node; Dseat processing per seat; s/r transmission time per seat; p per-hop propagation delay 24

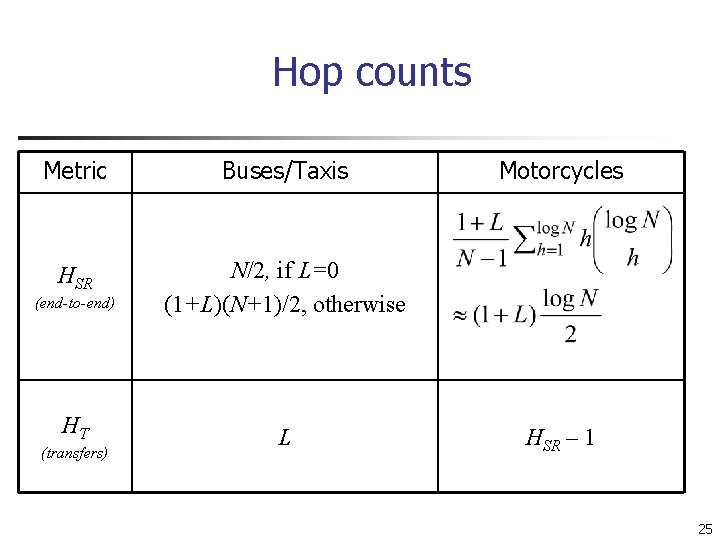
Hop counts Metric Buses/Taxis HSR (end-to-end) N/2, if L=0 (1+L)(N+1)/2, otherwise HT L (transfers) Motorcycles HSR – 1 25

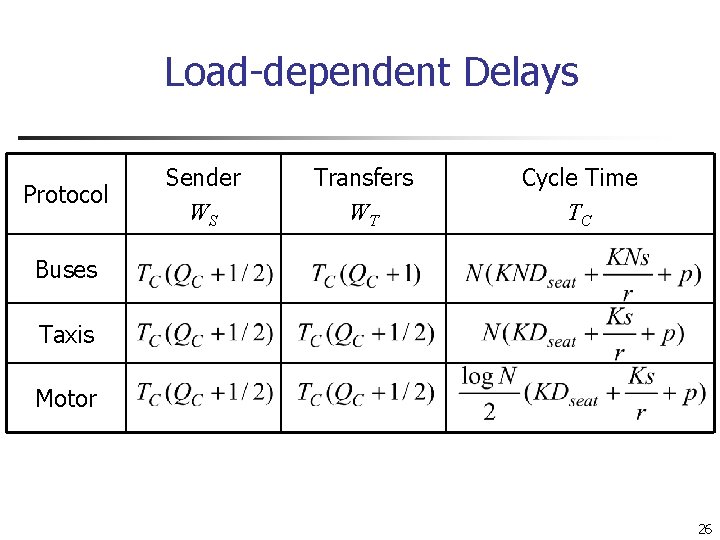
Load-dependent Delays Protocol Sender WS Transfers WT Cycle Time TC Buses Taxis Motor 26

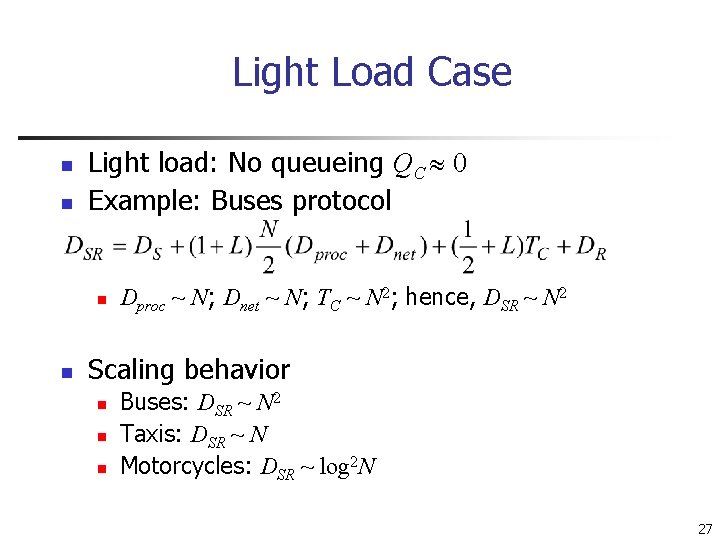
Light Load Case n n Light load: No queueing QC 0 Example: Buses protocol n n Dproc ~ N; Dnet ~ N; TC ~ N 2; hence, DSR ~ N 2 Scaling behavior n n n Buses: DSR ~ N 2 Taxis: DSR ~ N Motorcycles: DSR ~ log 2 N 27

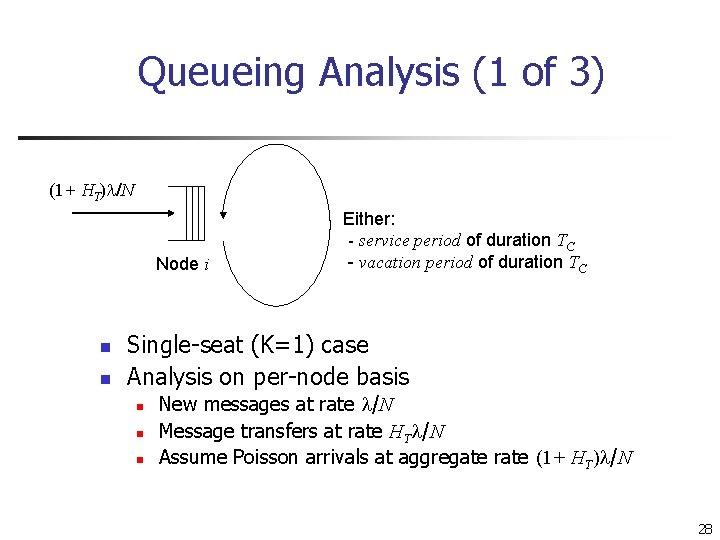
Queueing Analysis (1 of 3) (1+ HT) /N Node i n n Either: - service period of duration TC - vacation period of duration TC Single-seat (K=1) case Analysis on per-node basis n n n New messages at rate /N Message transfers at rate HT /N Assume Poisson arrivals at aggregate rate (1+ HT) /N 28

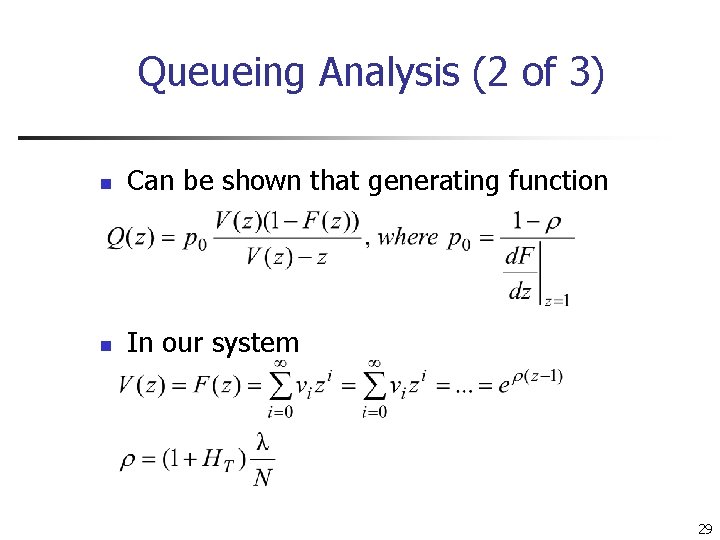
Queueing Analysis (2 of 3) n Can be shown that generating function n In our system 29

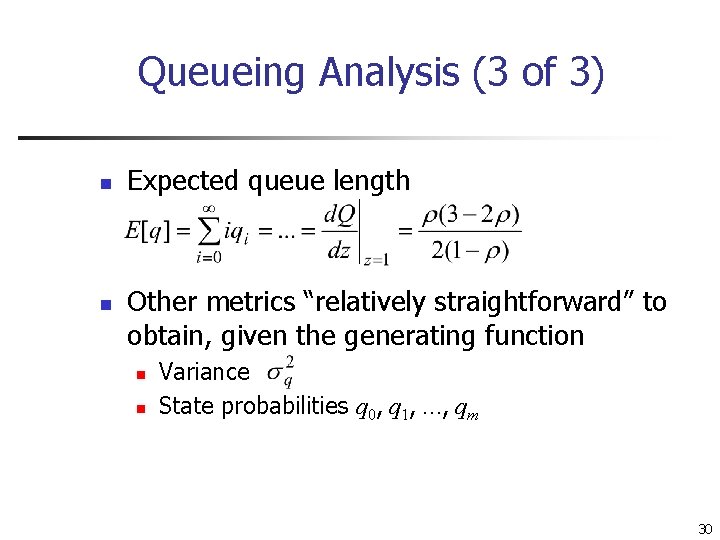
Queueing Analysis (3 of 3) n n Expected queue length Other metrics “relatively straightforward” to obtain, given the generating function n n Variance State probabilities q 0, q 1, …, qm 30

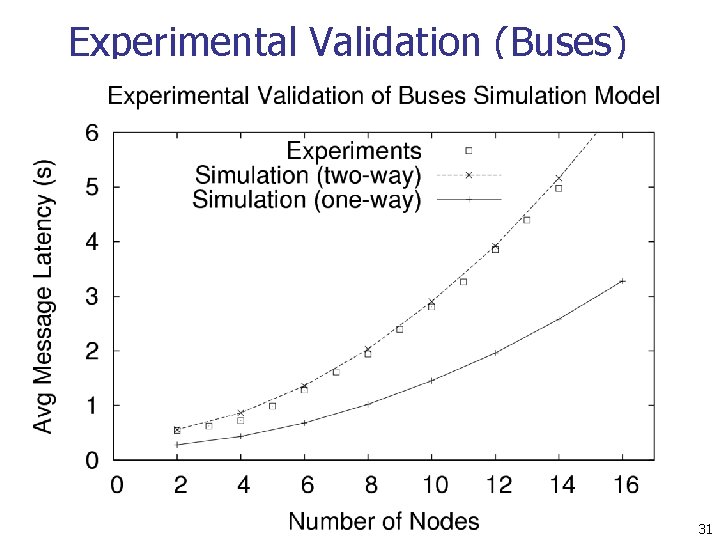
Experimental Validation (Buses) 31

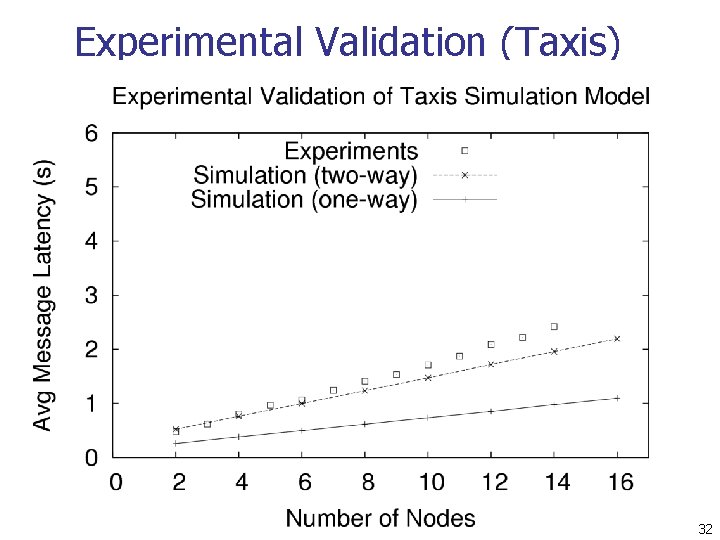
Experimental Validation (Taxis) 32

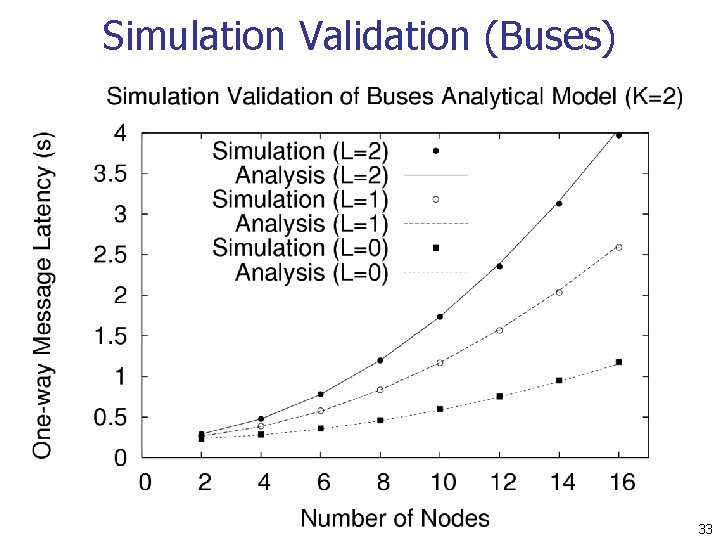
Simulation Validation (Buses) 33

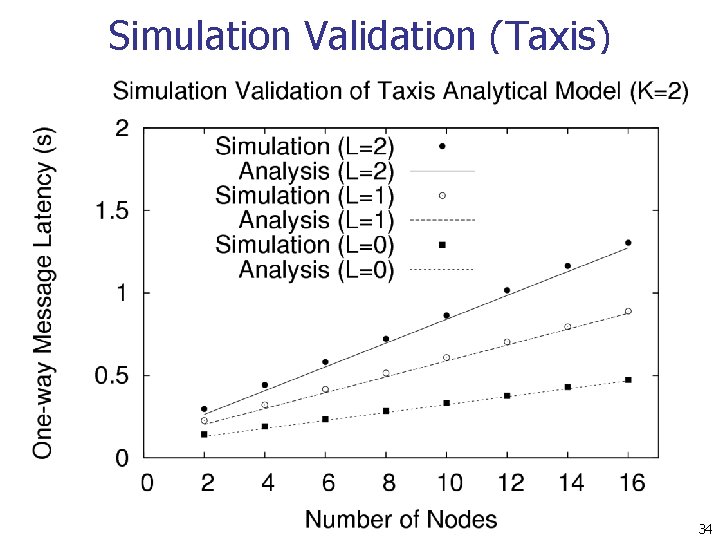
Simulation Validation (Taxis) 34

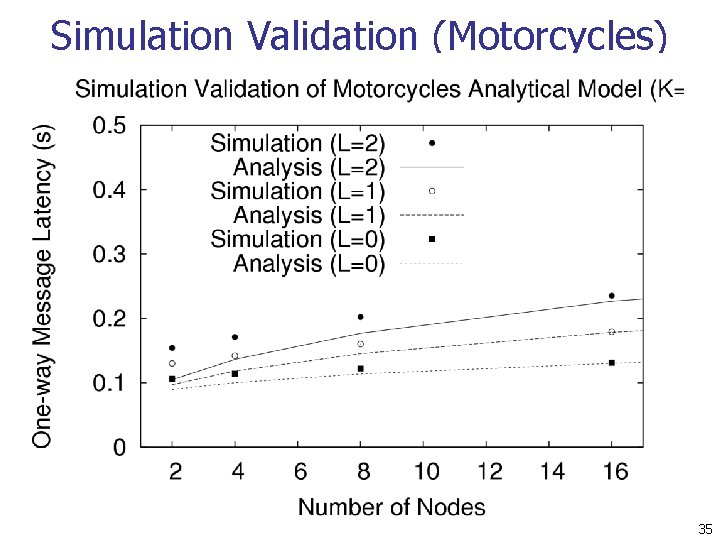
Simulation Validation (Motorcycles) 35

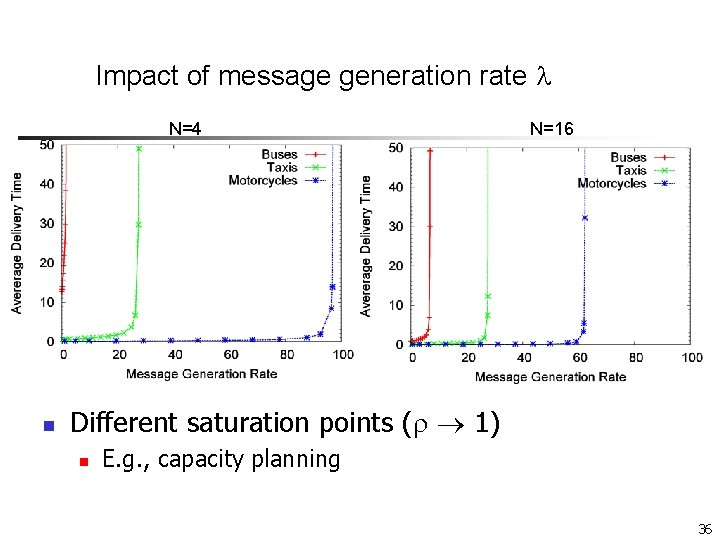
Impact of message generation rate N=4 n N=16 Different saturation points ( 1) n E. g. , capacity planning 36

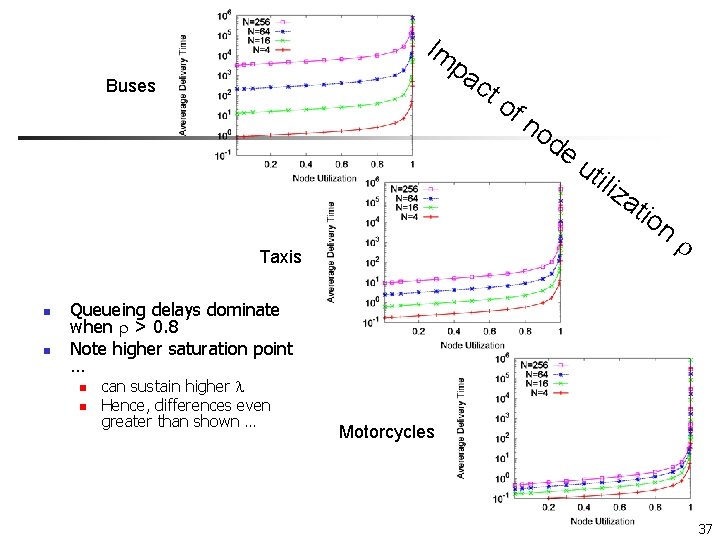
Im pa ct Buses of no d e ut iliz at ion Taxis n n Queueing delays dominate when > 0. 8 Note higher saturation point … n n can sustain higher Hence, differences even greater than shown … Motorcycles 37

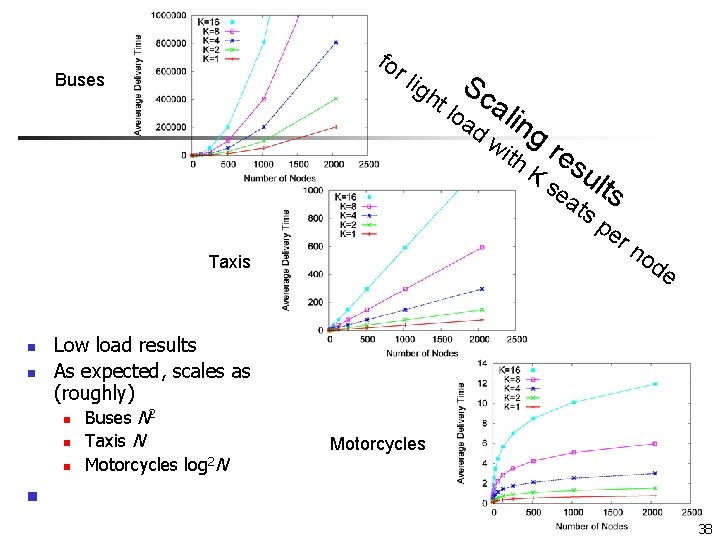
fo rl Buses igh Sc t lo a ad lin w g ith K re se su at s Taxis n n Low load results As expected, scales as (roughly) 2 n Buses N n Taxis N 2 n Motorcycles log N lts pe r no de Motorcycles n 38

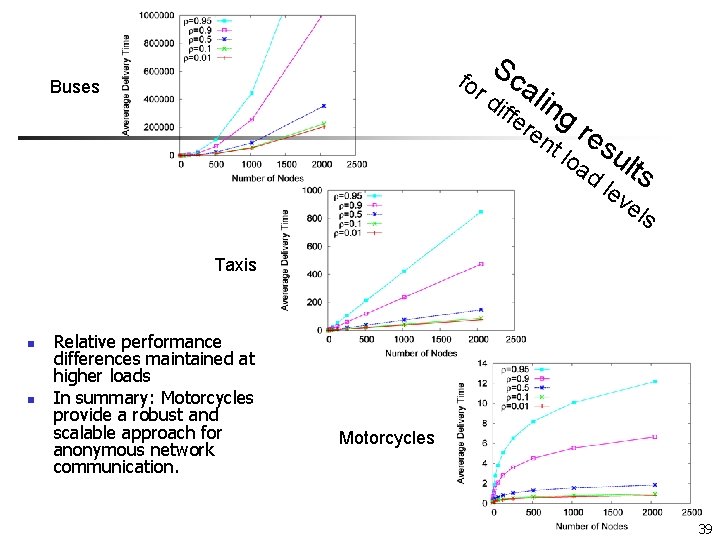
fo Sc rd Buses ali iffe ng re nt re loa sul d ts lev els Taxis n n Relative performance differences maintained at higher loads In summary: Motorcycles provide a robust and scalable approach for anonymous network communication. Motorcycles 39

Conclusions n The average message latency of Practical Buses scales quadratically with number of participants n n The average message latency of Taxis scales linearly with the number of participants n n Analysis, simulation, and experimental results The average message latency of Motorcycles scales logarithmically with the number of participants n Analysis and simulation results 40