TEL 382 Information Assurance Policies and Disaster Recovery






















































































- Slides: 107

TEL 382 Information Assurance Policies and Disaster Recovery Week 2

Outline • • • 9/9/2021 Risk Analysis Background Risk Analysis Benefits and Goals Risk Analysis Team Quantitative vs. Qualitative Steps Assets Threat Analysis/Risk Assessment Controls/Risk Management Example 2

Risk Management Objectives • Maintain customer, constituent, stockholder, or taxpayer confidence in organization • Protect confidentiality of sensitive information (personal, financial, trade secret, etc. ) • Protect sensitive operational data from inappropriate disclosure • Avoid third-party liability for illegal or malicious acts committed with organization’s systems • Ensure that organization computer, network, and data are not misused or wasted • Avoid fraud • Avoid expensive and disruptive incidents • Comply with pertinent laws and regulations • Avoid a hostile workplace atmosphere 9/9/2021 3

Risk Analysis/Policy Development Team • • Information Security Telecommunications Network Administration System Users System Administrator Systems Analysis Systems Programming Applications Programming • Database Administration 9/9/2021 • • • Physical Security Functional Owner Service Provider Executive Management Business/Project Management Auditing Legal HRM Labor Relations 4

Introduction to Risk Analysis • Security in any system should be commensurate with its risks. • Process to determine which security controls are appropriate and cost effective is quite often complex and subjective • Several distinct approaches to risk analysis that can be broken down into two types: quantitative and qualitative. 9/9/2021 5

Two Types of Risk Analysis • Quantitative: Assigns independently objective numeric values (e. g. , monetary values) to the components of the risk analysis and to the level of potential losses. When all elements (asset value, threat frequency, safeguard effectiveness, safeguard costs, uncertainty, and probability) are quantified, the process is considered to be fully quantitative • Qualitative: Is subjective in nature. Does not attempt to assign numeric values to all components. Relies on scenarios or ‘what if” questions 9/9/2021 6

Standard Risk Analysis Methodology • Identify asset to be reviewed • Ascertain threats, risks, concerns or issues to asset • Prioritize risk or determine vulnerability of threat to asset • Implement corrective measures, controls, safeguards, or accept risk • Monitor effectiveness of controls and assess effectiveness 9/9/2021 7

Risk Assessment Steps • • Set parameters for risk analysis Define system’s assets Determine relevant threat profiles Survey all system users to discover vulnerabilities • Analyze all data • Write the report 9/9/2021 8

Qualitative Steps • Develop a Scope Statement • Assemble a Competent Team • Identify Threats • Prioritize Threats • Calculate Impact Priority • Calculate Total Threat Impact • Identify Safeguards • Cost-Benefit Analysis • Rank Safeguards in Priority Order 9/9/2021 • Write Risk Analysis Report 9

Risk Analysis Process Steps • • • Assign responsibilities for risk assessment Identify information assets that are at risk Identify threats to information assets Assess vulnerabilities to information assets Determine probable loss or consequences, based upon quantitative/qualitative evaluation, threat and likelihood of such occurrence • Identify and estimate cost of protective measures that could eliminate or reduce vulnerability to an acceptable level • Select cost-effective security management measures to be implemented • Prepare report for submittal to executive or senior management that documents findings and recommendations 9/9/2021 10

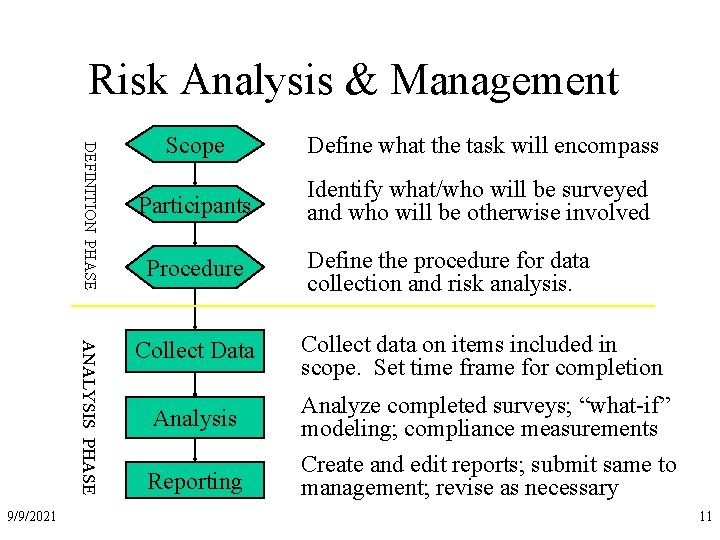
Risk Analysis & Management DEFINITION PHASE ANALYSIS PHASE 9/9/2021 Scope Define what the task will encompass Participants Identify what/who will be surveyed and who will be otherwise involved Procedure Collect Data Analysis Reporting Define the procedure for data collection and risk analysis. Collect data on items included in scope. Set time frame for completion Analyze completed surveys; “what-if” modeling; compliance measurements Create and edit reports; submit same to management; revise as necessary 11

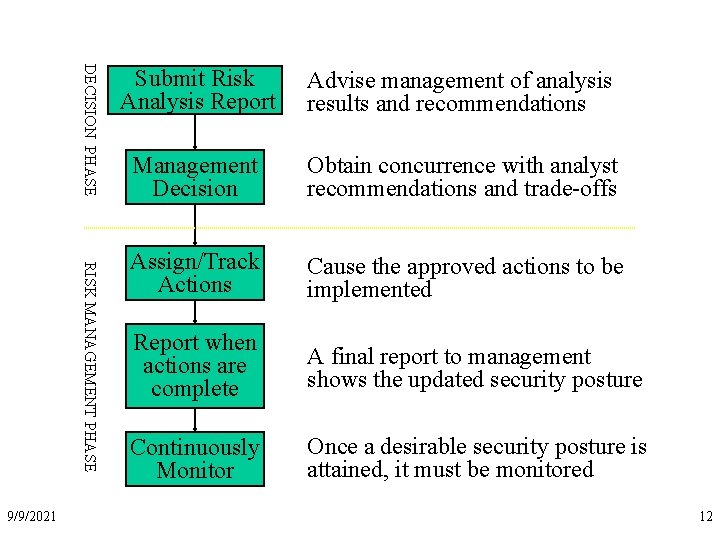
DECISION PHASE RISK MANAGEMENT PHASE 9/9/2021 Submit Risk Analysis Report Advise management of analysis results and recommendations Management Decision Obtain concurrence with analyst recommendations and trade-offs Assign/Track Actions Cause the approved actions to be implemented Report when actions are complete A final report to management shows the updated security posture Continuously Monitor Once a desirable security posture is attained, it must be monitored 12

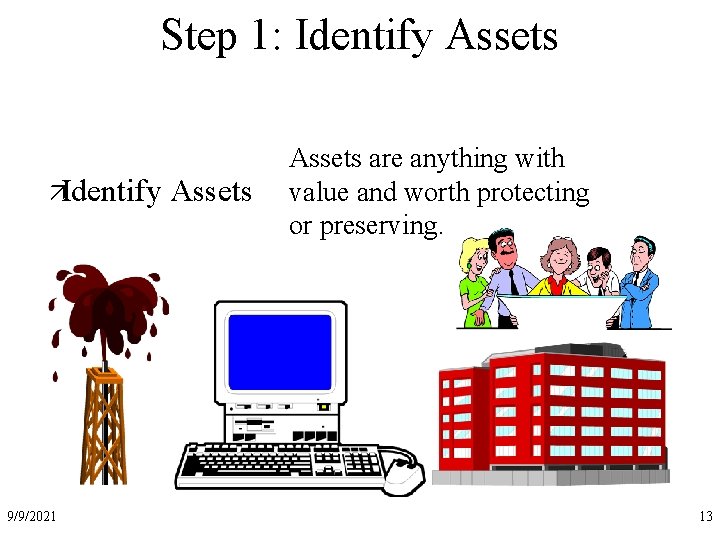
Step 1: Identify Assets äIdentify 9/9/2021 Assets are anything with value and worth protecting or preserving. 13

Asset Details • Determine value • If shared with other resources • If critical to the organization or function • Ownership • Physical location • Part of inventory? 9/9/2021 14

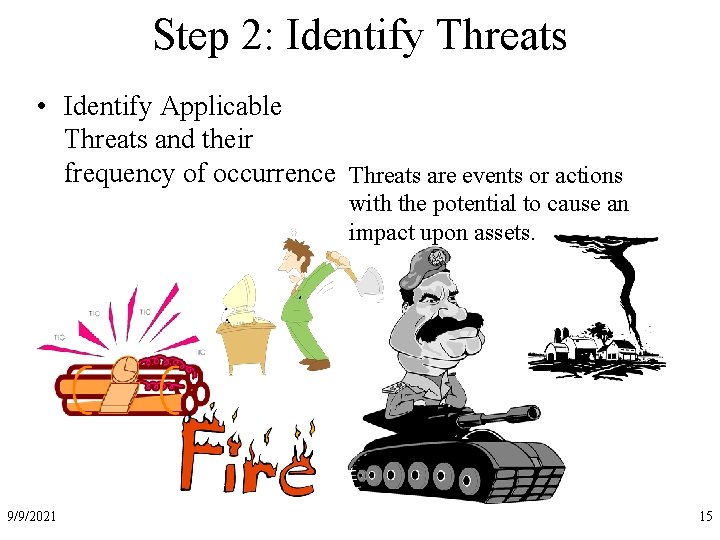
Step 2: Identify Threats • Identify Applicable Threats and their frequency of occurrence Threats are events or actions with the potential to cause an impact upon assets. 9/9/2021 15

Threat Examples • • Natural hazards Human error Fire Theft ä ä 9/9/2021 Unstable power Hardware failure Software failure Masquerading as authorized employee 16

Threat Details • Justification – Why applicable – Why the frequency • Frequency of occurrence – historical records – empirical knowledge 9/9/2021 17

Step 3: In-place Countermeasures • Identify In-Place Countermeasures are devices, processes, actions and/or procedures which have the propensity to reduce vulnerability They only count if they’re in-place! 9/9/2021 18

Countermeasure Examples • Procedures • Management support • Contingency plan • Metal Detector • Virus software • Perimeter Fences 9/9/2021 ä Training ä Power conditioning ä Backup procedures ä Access controls ä CCTV ä Guards 19

Step 4: Vulnerabilities ä Determine Vulnerabilities are a condition of weakness. A weakness might allow threats to have an impact on assets. 9/9/2021 20

Vulnerability Examples Susceptibility to: • • 9/9/2021 Unauthorized access Natural hazards Unstable power Terrorist Activity äKey person dependency äUser or operator errors äFire äTheft of Resources 21

Quantify Vulnerabilities ä Vulnerability levels are calculated ä Based on in-place countermeasures A risk analysis process must identify areas of vulnerabilities and their levels. 9/9/2021 22

Step 5: Calculate Loss ä Calculate Estimated Loss: (VL*Asset Cost * TV) = SLE And, SLE * Threat Multiplier = ALE Where: VL= Vulnerability level Tv= Threat Value SLE= Single Loss Expectancy ALE= Annual Loss Expectancy Loss is a measure of the impact upon assets by one or more manifested threats. Impact is a calculated value. 9/9/2021 23

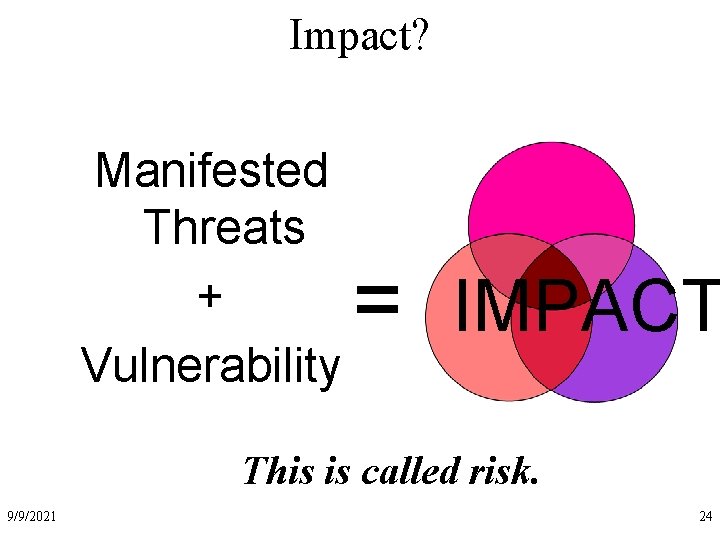
Impact? Manifested Threats + Vulnerability = IMPACT This is called risk. 9/9/2021 24

Impact Categories • Disclosure (Confidentiality lost) • Destruction (Complete loss) • Distrust (Available but questionable) • Denial of Service (Not available) Which category(ies) should be avoided? 9/9/2021 25

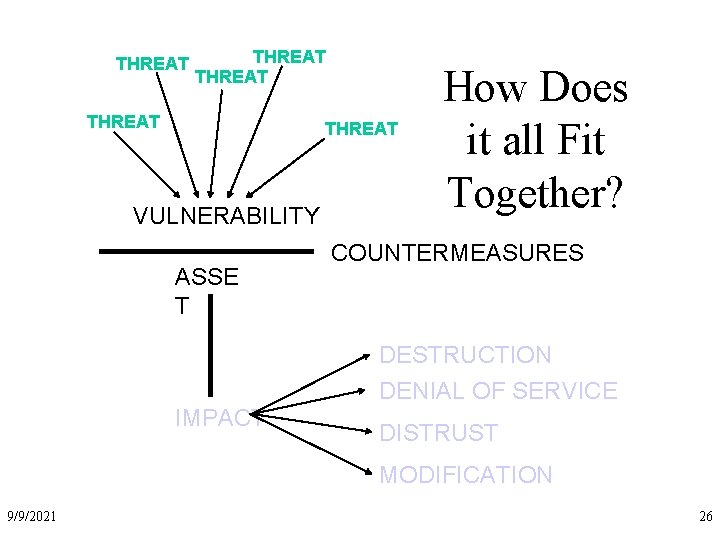
THREAT THREAT VULNERABILITY ASSE T How Does it all Fit Together? COUNTERMEASURES DESTRUCTION DENIAL OF SERVICE IMPACT DISTRUST MODIFICATION 9/9/2021 26

Step 6: Recommendations ä Recommend Corrective Action There are many ways to reduce expected loss from threat activity. Each corrective action is a countermeasure. 9/9/2021 27

Types of Action • Operational trade-off • Some countermeasures required by regulation – contingency plan – security training • Discretionary countermeasures 9/9/2021 28

Reports Should. . . • • 9/9/2021 Show procedures used Be management oriented Be concise Contain no jargon Show conclusions Include recommendations Show appropriate references Provide trade-off justification 29

Critical Asset Examples • • • 9/9/2021 Information People Software Hardware Facilities etc. 30

Asset Categories • Physical • Logical – Critical Applications or Data – Confidential Information – Sensitive Information – Public Information 9/9/2021 31

Value of an Information Asset • • • 9/9/2021 Cost to produce Value of info on open market cost of reproducing if destroyed benefit info brings to enterprise repercussion if info not available advantage to competitor if used, changed or destroyed cost if released, altered or destroyed loss of client or customer confidence if info not held loss of public credibility and embarrassment if info not secure 32

Assets: Networks and Software • Networks – – – – 9/9/2021 FEPs Workstations Modems Comm Lines Data Encryption Tools SAT Links Remote Access Security • Software – – – OS Utilities Compilers Database SW Application SW Procedure Libraries 33

Assets: Physical and Other • Physical – – – 9/9/2021 Buildings HVAC Furniture Supplies Machinery Fire Control Systems • Other – – Employees Policies Procedures Customer Confidence 34

Threat Analysis/Risk Assessment

The Variable Nature of the Elements of Risk 9/9/2021 36

Risk is Commonplace 9/9/2021 37

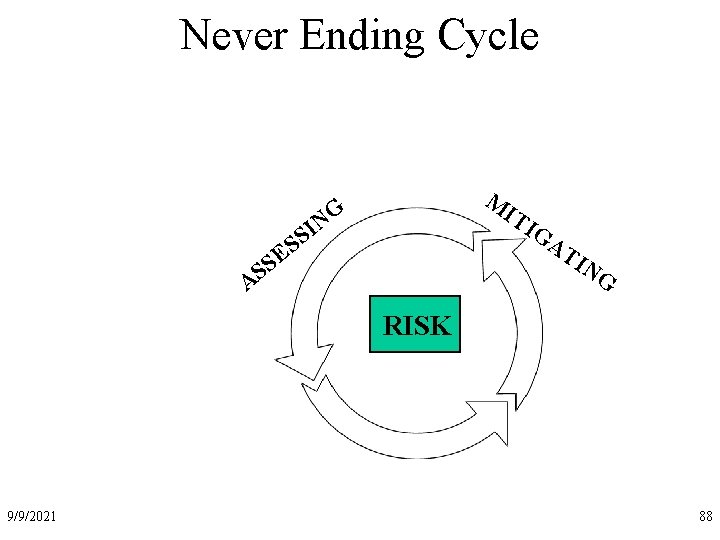
Never Ending Cycle M IT G N I IG SS E S S A AT IN G RISK 9/9/2021 38

Evaluate the Risks as to Consequences & Likelihoods • A risk consists of a likelihood and consequences. • Derived from mathematical concept of “expectation” • Expectation for some event is defined as the product of its probability of occurrence and its value if it occurs. – Thus, a one-in-forty million lottery ticket for a prize of $20, 000 has an expectation of fifty cents. • Our work is more fuzzy than the lottery example, and there is usually very little precision in either the metrics for probability of occurrence or consequences • Therefore, possibility expressed as a combination of probability and consequences is subject to debate • Use whatever tools are available and meaningful in a given situation, but do not get hung up on mathematics that do not really have any more precision than a judgment • There may be situations in which effectiveness analyses, engineering analyses, bean counting of interfaces, etc. may be desirable, but these are sideline issues to the exercising of judgment about the risks 9/9/2021 39

Threat • Webster: “an indication of an impending undesirable event” or “an expression of intention to inflict evil, injury or damage” 9/9/2021 40

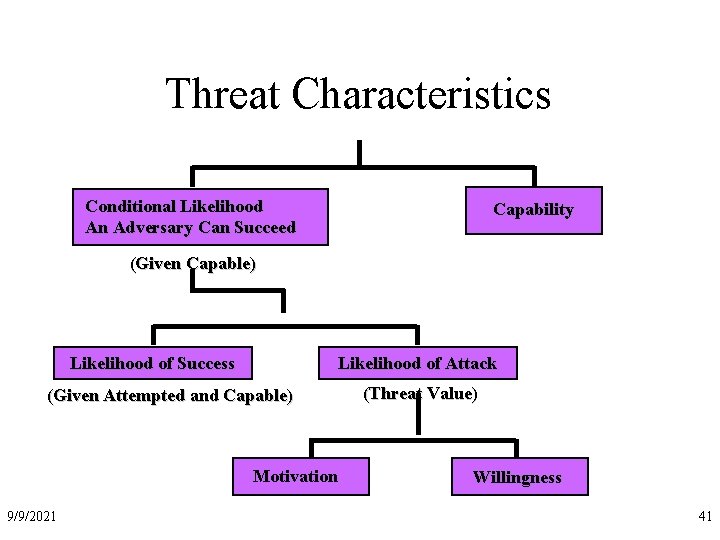
Threat Characteristics Conditional Likelihood An Adversary Can Succeed Capability (Given Capable) Likelihood of Success Likelihood of Attack (Given Attempted and Capable) Motivation 9/9/2021 (Threat Value) Willingness 41

Threat Sources • • 9/9/2021 Nature - Historical Unintentional human error - Historical Technological failure - Historical Adversarial - Threat Assessment 42

Adversarial Threat Characteristics • • 9/9/2021 Objectives - As opposed to ours Intentions Motivation to act Willingness to accept risk Willingness to accept cost Technical capability Resources 43

Threat • The capabilities and intentions of adversaries to exploit an information system; or any natural or unintentional event with the potential to cause harm to an information system, resulting in a degradation of an organization’s ability to fully perform its mission 9/9/2021 44

Threat Examples • Adversarial – Terrorists – Foreign States – Disgruntled Employees – Criminals – Recreational Hackers – Commercial Competitors 9/9/2021 • Non-Adversarial – Nature – Unintentional Human Acts 45

Attack • A well-defined set of actions by the threat (an active agent) that, if successful, would damage a critical asset -- cause an undesirable state of affairs -- resulting in harm to an organization’s ability to perform its mission 9/9/2021 46

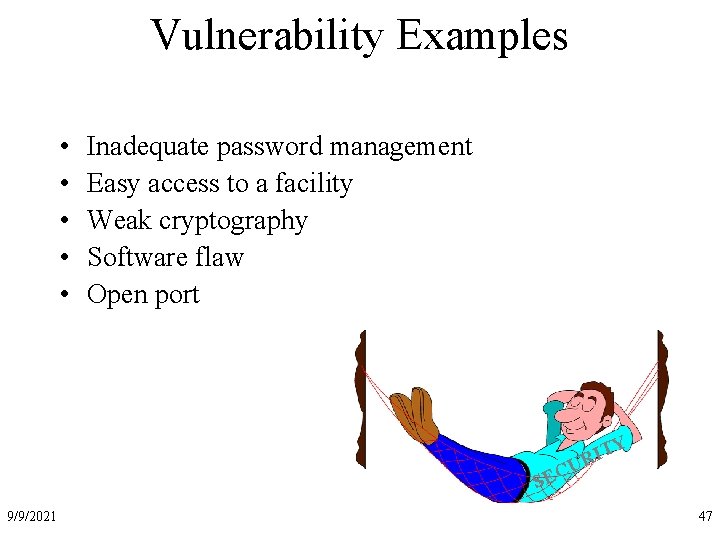
Vulnerability Examples • • • Inadequate password management Easy access to a facility Weak cryptography Software flaw Open port U C SE 9/9/2021 Y T I R 47

Consequence/Impact • The harmful result of a successful attack, degrading an organization’s ability to perform its mission 9/9/2021 48

Consequence Examples • Harm to organization mission – – – 9/9/2021 Loss of information confidentiality Loss of information integrity Loss of availability of information or system functions Inability to correctly authenticate sender of information Inability to verify receipt of information by the intended recipient 49

Threat Elements • Agent: catalyst that performs the threat. May be human, machine, or nature • Motive: something causing agent to act. May be either accidental or intentional. • Results: Outcome of applied threat. May lead to loss of access, unauthorized access, modification, disclosure, or destruction of the information asset. 9/9/2021 50

Risk assessment • Identify and value – data assets – software assets – physical assets (e. g. hardware) • Identify threats (hazards) to groups of assets – assessment of level of threat may be High/Medium/Low • Identify vulnerabilities of groups of assets – assessment of level of vulnerability may be High/Medium/Low • Assess level of risk from asset values and levels of threats and vulnerabilities 9/9/2021 51

Natural Threats • • • • • 9/9/2021 Acid Rain Alberta Clipper Air Pollution Beach Erosion Black Blizzard Cold Air Funnel Cyclone Downburst Earthquake Erosion Flash Flood Funnel Cloud Gale Haze • • • • • Humidity Hurricane Ice Storm Lake Effect Snow Lightning Monsoon Precipitation Rain Sandstorm Snow Storm Surge Thunder Tornado Tropical Storm Tsunami Typhoon Yellow Snow 52

Accidental Threats • • • 9/9/2021 Disclosure Electrical Disturbance Electrical Disruption Emanation Environmental Failure • • • Fire Hardware Failure Liquid Leakage Operator/user Error Software Error Telecommunication Interruption 53

Intentional Threats • • Alteration of data Alteration of software Bomb threat Disclosure Employee Sabotage Enemy Overrun Misappropriation of Services • Denial of Service • Unauthorized Access 9/9/2021 • • • Theft Fraud Embezzlement Extortion Riot/civil disorder Strike Theft Unauthorized Use Vandalism 54

Other Factors Affecting Impact of Threats • • • 9/9/2021 Geographical Location Operation Facilities Kind of info Organization uses/processes Visibility of organization Emergency Training Employee Morale 55

Vulnerabilities • Definitions • Vulnerability • A weakness in a system that leads to unexpected, undesired, or unauthorized results. An obvious violation of any security policy • Taxonomy • Division in to ordered groups or categories. • Classification • A distribution into groups, as classes, orders, families, etc. , according to some common relations or affinities. 9/9/2021 56

Vulnerabilities • Definitions (Continued) • Exposure • A state in system that is not a universal vulnerability. A violation of only some security policies. • Attack • An attempt to exploit a vulnerability or exposure. • Incident • A series of attacks that share some commonality. (e. g. attacker, method, time, result) • Threat • The means through which an attacker can affect a system 9/9/2021 57

Controls/Risk Management

Risk Mitigation Actions or countermeasures we can take to lessen risk – Affect threat agent or their capabilities – Eliminate or limit our vulnerabilities 9/9/2021 59

Assess Options for Risk Management • Risk management options usually cited as risk handling options subdivided as avoidance, control, assumption, risk transfer, and knowledge and research – Avoidance: Use alternate approach that does not have the risk. This mode is not always an option. – Control: Involves development of a risk reduction plan and then tracking the plan – Assumption: Simply accepting the risk and proceeding. A word of caution: There appears to be a tendency within organizations to gradually let the assumption of a risk take on the aura of a controlled risk. This mental evolution is the kind of wrongly conditioned thinking that led to the Challenger failure. – Risk Transfer: Attempt to pass risk to another element. What is done is, at best, a CYA exercise. – Knowledge & Research: Intensive study associated with specialized testing, developing intellectual ownership of problem in all of its aspects: theoretical, empirical and practical 9/9/2021 60

Prioritize the Risk Management Efforts • Once risks have been evaluated in terms of likelihood of occurrence and consequences, and when options for risk management have been reviewed, it is then meaningful to rank the risks to assign priorities. • Prioritizing risks is performed at the senior staff level to assure that all political, business and programmatic factors are weighted in the priority assessment. • Management must exercise judgment to prioritize resources for risk management purposes. The ranked risks are reviewed in terms of combined likelihoods and consequences and in terms of concerns with missions, functions, business objectives and political aspects. 9/9/2021 61

Develop Risk Management Plans • Allow for multiple risk plans for risks that may have significantly different characteristics. • Therefore, the recommendation is that the risk management program encompass a two-tier approach to risk management plans: – a risk management program plan (RMPP) captures all aspects of risk management at a high level and those aspects common to all risks (Policy) – risk-specific risk management plans (RMPs) (Guide or Procedures) 9/9/2021 62

Track the risk management efforts and manage accordingly • After planning is accomplished and RMPP is underway, the risk manager should review the status of all risks • A part of this effort may be implementation of a risk management board – Do not have to be risk owners although they may be. – Convened routinely to provide high-level visibility to the risk management process 9/9/2021 63

Risk Management • From this exercise, risks identified and managed. • Codes of Practice for IS Security BS 7799 – Covers how IS security should be managed and what support should be provided. • • • 9/9/2021 • • • Development of written information security policy Development of management structures and responsibilities Development of authorization processes for installing IT facilities Arranging independent audits of security Identifying risks from third party connections Identifying and classifying assets - information, software and physical. Addressing security at the recruitment stage and including it in job description Developing information security training Management of physical and environmental security Managing the security operation of networking facilities. Planning capacity requirements, systems acceptance, change control to minimize risk of failure. Virus detection and prevention Back up management User access management - registration, password management, user authentication Data and software access control. Audit trails, monitoring system use Business continuity planning. 64

Security Policy • The purpose of a security policy is to provide management direction and support for information security in the organization. • Security is an issue of corporate culture and, as such, must be led and driven from the top of the organization. The security policy, with appropriate actions to formally adopt it at CEO/Board level, is the starting point for the introduction of a security culture. The document should contain a definition of the overall objectives of the policy as well as an explanation of specific points, including compliance with legislative and contractual requirements; security education requirements; virus prevention and detection; and business continuity planning. The policy should define specific responsibilities for all aspects of information security and a documented process for reviewing the policy and reporting on suspected security incidents. 9/9/2021 65

Security Organization • BS 7799 tells how to coordinate throughout an organization by: – establishing suitable management forums; – consultation with external experts; – independent reviews of security considering the security implications when third parties have access to information assets and guidance on security clauses in contracts with third parties. – Board level adoption of security policy – Implementation of security policy – Regular reporting on security issues at CEO level · – Identification of security manager – Set up of procedures to implement the policy • The roles of the security organization are; 1. To manage information security within the Company 2. To maintain the security of organizational information processing facilities and information assets accessed by third parties 3. To maintain the security of information when the responsibility for information processing has been outsourced to another organization. 9/9/2021 66

Assets Classification and Control Maintain appropriate protection of corporate assets and ensure that information assets receive an appropriate level of protection. BS 7799 provides guidance how to classify assets which need to be protected in a way that is useful for defining appropriate security countermeasures. Guidance is given on identifying the objective of a threat to a particular asset (disclosure, loss or modification). In most organizations there will be a number of assets with different owners and different sets of access privileges. Examples are; the customer databases, personnel data, financial data, and authorized user data. To fulfil the above objective requires; 1. Register of data assets. 2. Designated owner for each data asset. 3. Set of access permissions for each data asset. 4. Management processes to ensure that access permissions are 9/9/2021 maintained and enforced. 67

Personnel Security • It is commonplace to note that people are the biggest security risk in any organization. People can be careless, error-prone and, tragically, downright dishonest at times. Any effective security policy must therefore deal adequately with personnel issues. • The objective of personnel security is to reduce risks of human error, theft, fraud or misuse of facilities; to ensure that users are aware of information security threats and concerns, and are equipped to support the corporate security policy in the course of their normal work; to minimize the damage from security incidents and malfunctions and learn from such incidents. • This can be achieved by: – addressing security issues at the recruitment stage; – during the development of job descriptions and contracts; – in the monitoring of an individual's employment. 9/9/2021 68

Personnel Security • In general BS 7799 recommends; 1. An employee handbook which sets out clearly the policies for information security and acceptable use and the rules which employees must observe. 2. Staff presentations on the security policy, its implementation, and their behavior in a security culture. The presentations would include training on how to recognize and respond to a security incident. 3. A contract of employment which is appropriate for an environment where information security is a major issue. 4. A new employee induction program which includes briefing on the security and acceptable use policies. 9/9/2021 69

Physical and Environmental Security • The purpose is to prevent unauthorized access, damage and interference to business premises and information; to prevent loss, damage or compromise of assets and interruption to business activities; to prevent compromise or theft of information and information processing facilities. • The level of physical security at most business premises is inadequate. BS 7799 recommends that the following areas be considered and appropriate action taken; 1. The introduction with an employee ID scheme using swipe cards. These cards to be worn visibly by employees at all times when they are in the premises. 2. That all visitors be issued with a temporary ID and be accompanied while on the premises. • 3. That all visitors bringing portable computing equipment or removable media into the premises be requested to complete a formal permission to do so and that any media intended to be used on the Company’s network be submitted to a virus scanning process. • 4. That the removal of computer equipment and media from the Company’s premises be subject to formal controls. • 5. The use of an electronic time control system to record when employees are present in the building. This log can be compared with the security access logs 9/9/2021 to identify impersonation incidents. 70

System Access Control System access control aims to; 1. To control access to information 2. To prevent unauthorized access to information systems 3. To ensure the protection of networked services 4. To prevent unauthorized computer access 5. To detect unauthorized activities 6. To ensure information security when using mobile computing and tele-networking facilities 9/9/2021 71

Systems Development and Maintenance Security in this area comprises techniques: 1. To ensure security is built into operational systems 2. To prevent loss, modification or misuse of user data in application systems 3. To protect the confidentiality, authenticity and integrity of information 4. To ensure IT projects and support activities are conducted in a secure manner 5. To maintain the security of application system software and data. An organization's test and acceptance procedures should be reviewed to ensure that the security attributes of new software components are adequately validated. 9/9/2021 72

Business Continuity Planning BCP exists to mitigate interruptions to business activities and to critical business processes from the effects of major failures or disasters. Frequently one finds that while there is a procedure for offsite backup of data there is no overall continuity plan to deal with catastrophic loss of premises or computing facilities. We recommend that a business continuity plan be put in place. 9/9/2021 73

Compliance The purpose of compliance is to: 1. Avoid breaches of criminal/civil law, statutory, regulatory or contractual obligations 2. Ensure compliance of systems with organizational security policies and standards 3. Maximize the effectiveness of and to minimize interference to/from the system audit process In general it is recommended that: 1. Procedures be established to ensure that contractual obligations to trading partners are complied with 2. HR procedures be established to deal with breaches of security policy or acceptable use 3. Regular internal audits be performed in order to check compliance and make improvements 4. Regular external audits be performed in order to verify compliance with the security policy and procedures 5. A review of applicable law is undertaken with particular reference to financial regulation and legislation dealing with electronic 9/9/2021 transactions, encryption, competition and e-commerce 74

Security Mechanisms • • 9/9/2021 Private keys Public keys Digital Certificates Secure Socket Layer (SSL) 75

Potential Controls • Backup • Recovery Plan • Access Control Mechanism • Authentication • Encryption • Application Controls • Acceptance Testing • Change Management • Anti-virus 9/9/2021 • • • Policy Training Auditing/Monitoring Interface Dependencies Maintenance Service Level Agreements • Physical Security • Management Support 76

Countermeasure Examples • • 9/9/2021 Fix known exploitable software flaws Enforce operational procedures Provide encryption capability Improve physical security Disconnect unreliable networks Train system administrators Install virus scanning software 77

Risk Analysis Success • Depends upon: – commitment of management – skills and expertise of risk management team identifying risks and controls – risk management team and business unit working together to identify and manage information asset risks – on-going risk analysis – use of consistent process – reporting of safeguard performance 9/9/2021 78

Asset Value Analysis • Confidentiality: Information has not undergone unauthorized or undesirable disclosure • Integrity: Information is as intended, without unauthorized or undesirable modification or corruption • Availability: Availability of an application or system, and its information is protected 9/9/2021 79

Example Risks • Threats to Confidentiality – Access without authorization – Disclosure without authorization – Observation or monitoring of transactions – Copying without authorization – Packet Sniffing – Contractor accessing confidential information 9/9/2021 80

Risk Management Decision • Determination by management or command to – take specific actions that will mitigate risk to mission, or – reject countermeasure recommendations and accept risk to mission 9/9/2021 81

Countermeasure Considerations • What is the cost Vs. benefit? • Are we creating another vulnerability? • Are people involved? If so, will they participate? • How long is the countermeasure needed? • How long will the countermeasure be effective? 9/9/2021 82

Cost Vs. . Benefit • Cost in – dollars – time to implement – impact on operations Results 9/9/2021 83

People Considerations • Are people involved? Will they participate in the solution? COUNTERMEASURE USER 9/9/2021 84

Time Consideration • How long is the countermeasure needed? 9/9/2021 85

Time Consideration • How long will the countermeasure be effective? 9/9/2021 86

Risk Assessment Reality • • • 9/9/2021 Are we sure of the threat? Have we identified all vulnerabilities? Have we considered all possible attacks? Is our estimate of consequence correct? Is all of this art or science? 87

Never Ending Cycle M IT G N I IG SS E S S A AT IN G RISK 9/9/2021 88

Residual Risk • That portion of risk that remains – Management decides to accept risk – Unconsidered threat factors – Unconsidered vulnerabilities – Incorrect conclusions 9/9/2021 89

TEL 382 Week 02 Risk Peltier Text

Outline • • • 9/9/2021 Risk Analysis RA Methodology Asset Identification Threat Impact Factors Threat Occurrence Rates Risk Management Objectives Risk Management Cycle Quantitative and Qualitative Analysis 91

Risk • “someone or something that creates or suggests a hazard” • Management must perform “due diligence” in the enterprise • Formal Risk Analysis (RA) Process proves that due diligence is performed 9/9/2021 92

Risk Analysis (RA) • Should be performed whenever money or resources are to be spent, any project or task initiated • Should be done using internal experts (and outside experts, as needed) • Should be capable of being performed in a few days or weeks or less • Results indicate whether or not to proceed – – Identify concerns Prioritize level of vulnerability Select appropriate level of control OR Accept Risk • Should have a management sponsor 9/9/2021 93

RA Methodology • Identify asset • Determine threats, risks, concerns, or issues with that asset • Prioritize the risk or determine the vulnerability of the threat to the asset • Implement corrective measures, controls, safeguards, or accept the risk • Monitor the effectiveness of the controls and assess their effectiveness 9/9/2021 94

Asset Identification • Physical • Logical • • 9/9/2021 People Physical Environmental Telecommunications Hardware Software Data Information 95

Intangible Assets • • • Cost of Producing Information Value of information on open market Cost of reproducing information if it is destroyed Benefit of information to the organization Repercussion if it is not available Advantage to a competitor if they could use, change or destroy information • Cost if information was released, altered, or destroyed • Loss of client or customer confidence if information was not held and processed securely • Loss of public credibility and embarrassment if information is not secure 9/9/2021 96

Threat Identification • “Intent to something bad to someone or something” • 3 Elements of a Threat – Agent: Catalyst that performs threat – Motive: Something that causes an agent to act – Results: Outcome of applied threat • Natural Threats • Accidental Threats • Intentional Threats 9/9/2021 97

Threat Impact Factors • • • 9/9/2021 Information Sensitivity Employee Emergency Training Protection and Detection Features Employee Morale Local Economic Conditions Visibility Redundancies Employee Proficiency Level Written Procedures Employee Security Awareness Past Prosecutions Etc. 98

Threat Occurrence Rates • Annual Loss Exposure (ALE) – Asset Value in $ (V) x Threat Occurrence Likelihood in terms of 1 year (L) – V x L = ALE • EXAMPLE: – V = $3 Million – L = Once every 100 years (1/100 or 0. 01) – V x L = $3 Million x 0. 01 = $30, 000 9/9/2021 99

Risk Management Objectives • Maintain customer, constituent, stockholder, or taxpayer confidence in organization • Protect confidentiality of sensitive information (personal, financial, trade secret, etc. ) • Protect sensitive operational data from inappropriate disclosure • Avoid third-party liability for illegal or malicious acts committed with organization’s systems • Ensure that organization computer, network, and data are not misused or wasted • Avoid fraud • Avoid expensive and disruptive incidents • Comply with pertinent laws and regulations • Avoid a hostile workplace atmosphere 9/9/2021 100

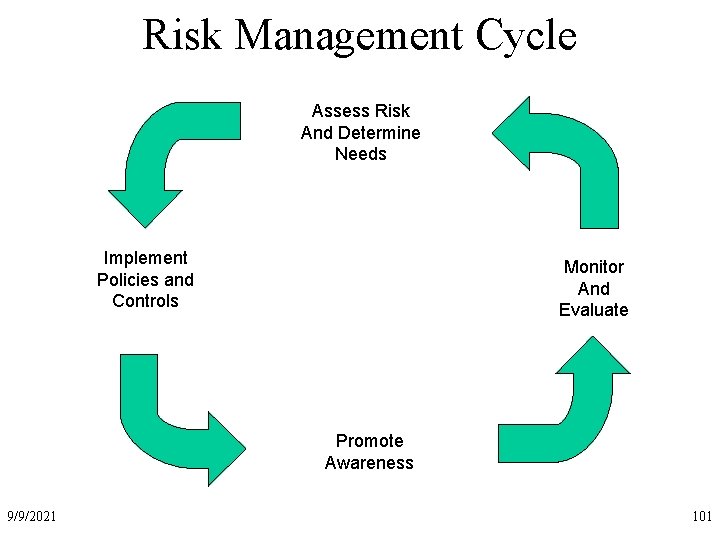
Risk Management Cycle Assess Risk And Determine Needs Implement Policies and Controls Monitor And Evaluate Promote Awareness 9/9/2021 101

Risk Management Cycle • Assess Risk and Determine Needs – Recognize info resources as enterprise asset – Develop RA process linking controls to business needs – Hold managers accountable to protect info resources • Implement Appropriate Policies and Related Controls – Link policies to business risks – Implement standards to support policies – Distinguish between standards and guidelines – Make policy support a management review issue 9/9/2021 102

Risk Management Cycle • Promote Awareness – Continually educate users and others on the risks and related policies and controls – Report to management, on an annual basis, the state of business-related risks • Monitor and Evaluate Policy and Control Effectiveness – Monitor factors that effect risk and indicate security effectiveness – Use results to direct future efforts and hold managers accountable – Be alert to new monitoring tools and techniques 9/9/2021 103

Quantitative & Qualitative Analysis • Quantitative – Assigns independently objective numeric values (i. e. , $) to RA components • Qualitative – Subjective – Relies on “what-if” scenarios 9/9/2021 104

Quantitative • Pros – – Results based upon independently objective processes and metrics Great effort is put into asset value determination and risk mitigation Cost/benefit assessment effort is essential Results can be expressed in management-specific language ($, %, probabilities) • Cons – Calculations can be complex – Historically, works best with a recognized automated tool and associated knowledge base – Requires large amounts of preliminary work – Generally not presented on a personal level – Participants cannot easily be coached through the process – Difficult to change directions 9/9/2021 105

Qualitative • Pro – – – Calculations are simple Not necessary to determine monetary value of assets Not necessary to quantify threat frequency Easier to involve non-security and non-technical staff Provides flexibility in process and reporting • Con – Subjective in nature – Rests solely with quality of risk management team assembled – Limited effort is required to develop monetary value for targeted assets – No basis for cost-benefit analysis of risk mitigation 9/9/2021 106

Example https: //people. sunyit. edu/~climekd/TEL 382/Qual. RAMeth. FINAL. xls 9/9/2021 107
 Principles of incident response and disaster recovery
Principles of incident response and disaster recovery Backup and disaster recovery mississippi
Backup and disaster recovery mississippi Bcp vs drp cissp
Bcp vs drp cissp Global facility for disaster reduction and recovery
Global facility for disaster reduction and recovery Sql server high availability and disaster recovery
Sql server high availability and disaster recovery Read-scale availability groups
Read-scale availability groups Principles of incident response and disaster recovery
Principles of incident response and disaster recovery Disaster recovery planning in system analysis and design
Disaster recovery planning in system analysis and design Verizon coop
Verizon coop Payroll disaster recovery plan
Payroll disaster recovery plan Manufacturing disaster recovery plan
Manufacturing disaster recovery plan Mainframe disaster recovery
Mainframe disaster recovery Law firm disaster recovery plan
Law firm disaster recovery plan Emc disaster recovery
Emc disaster recovery Records management disaster recovery plan
Records management disaster recovery plan Oracle business continuity plan
Oracle business continuity plan Ad disaster recovery
Ad disaster recovery Isaca business continuity
Isaca business continuity Vmware offsite disaster recovery
Vmware offsite disaster recovery Hot site cold site warm site disaster recovery
Hot site cold site warm site disaster recovery Disaster recovery for dummies
Disaster recovery for dummies Disaster recovery call tree template
Disaster recovery call tree template Disaster recovery plan presentation
Disaster recovery plan presentation School disaster recovery plan
School disaster recovery plan Database disaster recovery plan
Database disaster recovery plan Oracle disaster recovery best practices
Oracle disaster recovery best practices Open source disaster recovery
Open source disaster recovery Disaster recovery telecommunications
Disaster recovery telecommunications National disaster recovery framework 2016
National disaster recovery framework 2016 Ict disaster recovery plan
Ict disaster recovery plan Disaster recovery techniques
Disaster recovery techniques Disaster recovery case study examples
Disaster recovery case study examples Coop disaster recovery
Coop disaster recovery Aws disaster recovery warm standby
Aws disaster recovery warm standby Disaster recovery cost curve
Disaster recovery cost curve Bcp metrics
Bcp metrics Bia bcp drp
Bia bcp drp Disaster recovery process flow diagram
Disaster recovery process flow diagram Share data
Share data Disaster recovery plan voorbeeld
Disaster recovery plan voorbeeld National disaster recovery framework
National disaster recovery framework National disaster recovery framework
National disaster recovery framework Disaster recovery plan template nist
Disaster recovery plan template nist International recovery platform
International recovery platform Disaster recovery lombardia
Disaster recovery lombardia Disaster recovery plan adalah
Disaster recovery plan adalah Disaster recovery plan adalah
Disaster recovery plan adalah Desoto disaster recovery
Desoto disaster recovery Ibm zerto disaster recovery
Ibm zerto disaster recovery Kj 382
Kj 382 49 cfr 382
49 cfr 382 Ramsedo
Ramsedo Btm 382
Btm 382 Ce 382
Ce 382 Cmput 429
Cmput 429 Btm 382
Btm 382 Btm 382
Btm 382 Btm 382
Btm 382 Hai mari sembah
Hai mari sembah Comp 382
Comp 382 Ce 382
Ce 382 Emu information assurance and cyber defense
Emu information assurance and cyber defense According to the weather forecast there is no typhoon
According to the weather forecast there is no typhoon Disaster management in libraries and information centres
Disaster management in libraries and information centres Maconachy-schou-ragsdale model
Maconachy-schou-ragsdale model Primaros
Primaros Tel mixto
Tel mixto Tel aviv university electrical engineering
Tel aviv university electrical engineering Tel mixto
Tel mixto Mammoth oil company 1920
Mammoth oil company 1920 Tel ve levha haline getirilebilen elementler
Tel ve levha haline getirilebilen elementler 123 12345678
123 12345678 A sok kincsnek a tél metafora
A sok kincsnek a tél metafora Tel 104
Tel 104 Picture tel
Picture tel Gerard tel
Gerard tel Tel laminar 37m
Tel laminar 37m Tel aviv university mechanical engineering
Tel aviv university mechanical engineering Tel aviv university electrical engineering
Tel aviv university electrical engineering Tel 971
Tel 971 Tel
Tel Tel 044
Tel 044 Tel
Tel Sharengen
Sharengen Tel / tokyo electron sccm shin
Tel / tokyo electron sccm shin Logo tel
Logo tel Baby tel
Baby tel Tel 972
Tel 972 Midland utilities 1920s
Midland utilities 1920s Tel 31
Tel 31 çemberin manyetik alanı
çemberin manyetik alanı Tel.krgi
Tel.krgi 2 tel
2 tel Tel hashomer kriterleri
Tel hashomer kriterleri Yarı metaller tel ve levha haline getirilebilir mi
Yarı metaller tel ve levha haline getirilebilir mi 2120
2120 Fernando mieli
Fernando mieli Robert boyle element tanımı
Robert boyle element tanımı Gerard tel
Gerard tel Tel. fax
Tel. fax Shore tel
Shore tel The suffixes ic, -ous, -al, and oid are found in:
The suffixes ic, -ous, -al, and oid are found in: Gdb tel aviv
Gdb tel aviv Unsteady flow
Unsteady flow Tel 016
Tel 016 Dizabilitate locomotorie
Dizabilitate locomotorie Nivkit
Nivkit Tel. fax
Tel. fax