CSC 382 Computer Security Incident Response CSC 382

























- Slides: 35

CSC 382: Computer Security Incident Response CSC 382: Computer Security 1

Incident Response What is an Incident? Phases of Incident Response 1. 2. 3. 4. 5. 6. 7. 8. Preparation Identification Containment Damage Assessment Preserve Evidence Eradication Recovery Follow-up CSC 382: Computer Security 2

What is an Incident? Violation of security policy: – Unauthorized access of information – Unauthorized access to machines – Embezzlement – Virus or worm attack – Denial of service attacks – Email spam or harassment CSC 382: Computer Security 3

Detecting an Incident • Catching perpetrator in the act – Unauthorized logins, NIDS alerts. • Noticing unauthorized system changes. • Receiving a message from another site, saying that your site was used to launch an attack on them. • Strange activities on system: – crashes, random reboots, slow performance. CSC 382: Computer Security 4

Incident Response Restoring system to satisfy site security policy Phases: 1. 2. 3. 4. 5. 6. 7. 8. Preparation for attack (before attack detected) Identification of attack Containment of attack (confinement) Damage assessment Preserve evidence (if necessary) Eradication of attack (stop attack) Recovery from attack (restore system to secure state) Follow-up to attack (analysis and other actions) CSC 382: Computer Security 5

Preparation 1. Configure intrusion detection systems. 2. Determine your response goals. 3. Document incident response procedures. – Who to contact? – What to do? 4. Organizing a CSIRT – Finding and training personnel. – Hardware/software necessary for investigation. CSC 382: Computer Security 6

Incident Response Goals 1. 2. 3. 4. 5. 6. Determine if a security breach occurred. Contain intrusion to prevent further damage. Recover systems and data. Prevent future intrusions of same kind. Investigate and/or prosecute intrusion. Prevent public knowledge of incident. CSC 382: Computer Security 7

Identification • Who/what reported incident. • Date and time of the incident. • Nature of the intrusion. – What level of unauthorized access was attained? – Is it known to the public? • Hardware/software involved – How critical are the affected systems? • Assemble CSIRT – Team membership may vary based on nature of incident CSC 382: Computer Security 8

Containment Limit access of attacker to system resources. Containment method depends on criticality of systems and extent of intrusion. – – Monitoring intruder Reducing intruder’s access Deception De-activating the affected account • Need to kill active processes too – Blocking access to system via firewall – Pulling network/phone cable – Powering down system CSC 382: Computer Security 9

Monitoring • Records attacker’s actions; does not interfere with attack: – Idea is to find out what the attacker is after and/or methods the attacker is using. • Problem: attacked system is vulnerable throughout – Attacker can also attack other systems. • Example: type of OS can be derived from settings of TCP and IP packets of incoming connections – Analyst draws conclusions about source of attack. CSC 382: Computer Security 10

Reducing Access • Reduce protection domain of attacker. • Problem: if defenders do not know what attacker is after, reduced protection domain may contain what the attacker is after. – Stoll created document that attacker d/led. – Download took several hours, during which the phone call was traced to Germany. CSC 382: Computer Security 11

Deception Honeypot: system designed for intruders to attack, to waste their time and to allow safe monitoring – ex: The Honeynet Project, honeyd Deception Tool Kit – – Creates false network interface. Can present any network configuration to attackers. When probed, can return wide range of vulnerabilities. Attacker wastes time attacking non-existent systems while analyst collects and analyzes attacks to determine goals and abilities of attacker. Experiments show deception is effective response to keep attackers from targeting real systems. CSC 382: Computer Security 12

Honeynet Project Tool development – Environment simulation: virtual machines. – Data control: firewalling tools to limit attacker activities to avoid damaging other systems. – Data collection: network and keystroke loggers. – Data analysis: tools to extract relevant data from tcpdump logs and more. Research and documentation – Analysis of attacker and honeypot techniques. – Analysis of particular attacks. CSC 382: Computer Security 13

Damage Assessment: Data • • • System date and time when assessment began. List of users currently logged in. Time/date stamps for filesystem. List of processes List of open network sockets – Associated applications – Associated systems • System configuration files. • Log and accounting files. • System date and time when assessment complete. CSC 382: Computer Security 14

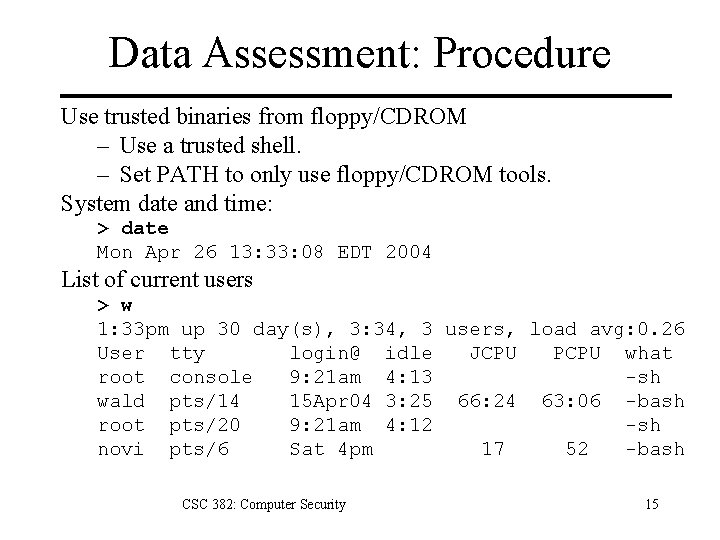
Data Assessment: Procedure Use trusted binaries from floppy/CDROM – Use a trusted shell. – Set PATH to only use floppy/CDROM tools. System date and time: > date Mon Apr 26 13: 33: 08 EDT 2004 List of current users > w 1: 33 pm up 30 day(s), 3: 34, 3 users, load avg: 0. 26 User tty login@ idle JCPU PCPU what root console 9: 21 am 4: 13 -sh wald pts/14 15 Apr 04 3: 25 66: 24 63: 06 -bash root pts/20 9: 21 am 4: 12 -sh novi pts/6 Sat 4 pm 17 52 -bash CSC 382: Computer Security 15

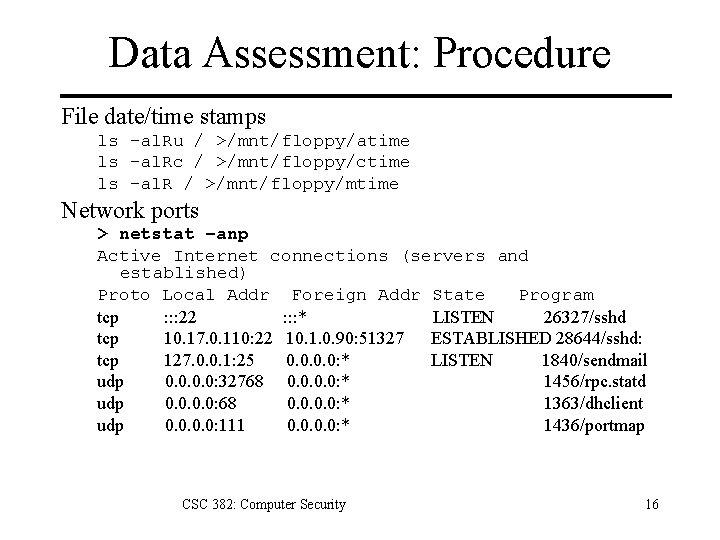
Data Assessment: Procedure File date/time stamps ls –al. Ru / >/mnt/floppy/atime ls –al. Rc / >/mnt/floppy/ctime ls –al. R / >/mnt/floppy/mtime Network ports > netstat –anp Active Internet connections (servers and established) Proto Local Addr Foreign Addr State Program tcp : : : 22 : : : * LISTEN 26327/sshd tcp 10. 17. 0. 110: 22 10. 1. 0. 90: 51327 ESTABLISHED 28644/sshd: tcp 127. 0. 0. 1: 25 0. 0: * LISTEN 1840/sendmail udp 0. 0: 32768 0. 0: * 1456/rpc. statd udp 0. 0: 68 0. 0: * 1363/dhclient udp 0. 0: 111 0. 0: * 1436/portmap CSC 382: Computer Security 16

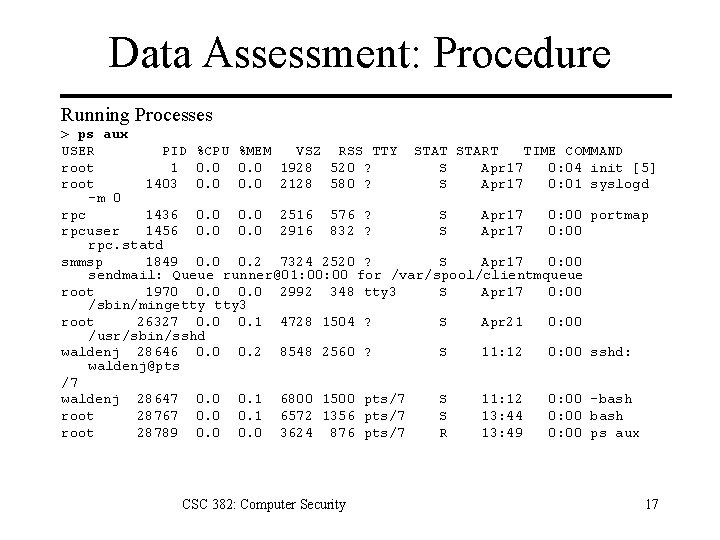
Data Assessment: Procedure Running Processes > ps aux USER PID %CPU %MEM VSZ RSS TTY STAT START TIME COMMAND root 1 0. 0 1928 520 ? S Apr 17 0: 04 init [5] root 1403 0. 0 2128 580 ? S Apr 17 0: 01 syslogd -m 0 rpc 1436 0. 0 2516 576 ? S Apr 17 0: 00 portmap rpcuser 1456 0. 0 2916 832 ? S Apr 17 0: 00 rpc. statd smmsp 1849 0. 0 0. 2 7324 2520 ? S Apr 17 0: 00 sendmail: Queue runner@01: 00 for /var/spool/clientmqueue root 1970 0. 0 2992 348 tty 3 S Apr 17 0: 00 /sbin/mingetty 3 root 26327 0. 0 0. 1 4728 1504 ? S Apr 21 0: 00 /usr/sbin/sshd waldenj 28646 0. 0 0. 2 8548 2560 ? S 11: 12 0: 00 sshd: waldenj@pts /7 waldenj 28647 0. 0 0. 1 6800 1500 pts/7 S 11: 12 0: 00 -bash root 28767 0. 0 0. 1 6572 1356 pts/7 S 13: 44 0: 00 bash root 28789 0. 0 3624 876 pts/7 R 13: 49 0: 00 ps aux CSC 382: Computer Security 17

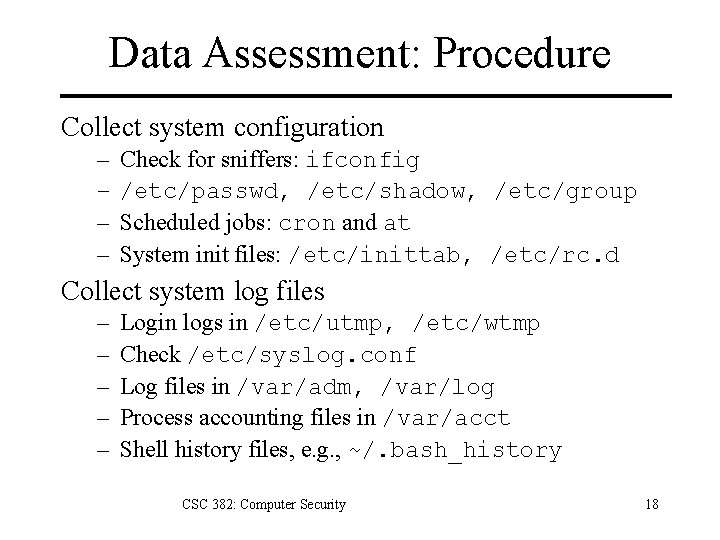
Data Assessment: Procedure Collect system configuration – – Check for sniffers: ifconfig /etc/passwd, /etc/shadow, /etc/group Scheduled jobs: cron and at System init files: /etc/inittab, /etc/rc. d Collect system log files – – – Login logs in /etc/utmp, /etc/wtmp Check /etc/syslog. conf Log files in /var/adm, /var/log Process accounting files in /var/acct Shell history files, e. g. , ~/. bash_history CSC 382: Computer Security 18

Preserve Evidence In-depth live system investigation. Construct a bit-level copy of entire hard disk or partition forensic examination. – Create image in single-user mode md 5 sum /dev/hda dd if=/dev/hda conv=noerror, sync | ssh desthost “cat >disk. img” desthost> md 5 sum disk. img CSC 382: Computer Security 19

Eradication 1. 2. 3. 4. Do nothing. Kill attacker’s processes and/or accounts. Block attacker’s network access to system. Patch and repair what you think was changed, then resume operation. 5. Investigate until root cause discovered, then restore system from backups and patch security holes. 6. Call law enforcement before proceeding further. CSC 382: Computer Security 20

Follow-Up 1. File reports with law enforcement, vendor, or regulatory agency. 2. File insurance claims if relevant. 3. Notify administrators of other affected systems. 4. Disciplinary actions against employees for internal attacks. 5. Update security of computer networks/systems. 6. Review handling of the incident. 7. Update incident handling policy/training. CSC 382: Computer Security 21

Follow-Up Tracking/Counter-attacking – Thumbprinting: traceback at connection level. – IP header marking: traceback at the packet level. – Counterattacking CSC 382: Computer Security 22

Thumbprinting Compares contents of connections to determine which are in a chain of connections. Characteristic of a good thumbprint: 1. Takes as little space as possible. 2. Connections with different contents have low probability of having same thumbprint. 3. Thumbprint minimally affected by common transmission errors. 4. Thumbprints additive, so two thumbprints over successive intervals can be combined. 5. Thumbprints cost little to compute, compare. CSC 382: Computer Security 23

Example: Foxhound • Thumbprints are linear combinations of character frequencies. – Experiment used telnet, rlogin connections. • Computed over normal network traffic. • Control experiment – Out of 4000 pairings, 1 match reported • So thumbprints unlikely to match if connections paired randomly. • Matched pair had identical contents. CSC 382: Computer Security 24

IP Header Marking Router inserts header data indicating path taken. When do you mark it? Deterministic: always marked. Probabilistic: marked with some probability. How do you mark it? Internal: marking placed in existing header. Expansive: header expanded to include space for marking. CSC 382: Computer Security 25

Example 1 Expand header to have n slots for router addresses. Router address placed in slot s with probability sp. Use: suppose SYN flood occurs in network. CSC 382: Computer Security 26

Use D B A C E E SYN flooded; 3150 packets could be result of flood 600 (A, B, D); 200 (A, D); 150 (B, D); 1500 (D); 400 (A, C); 300 (C) A: 1200; B: 750; C: 700; D: 2450 Note traffic increases between B and D; so B probable culprit. CSC 382: Computer Security 27

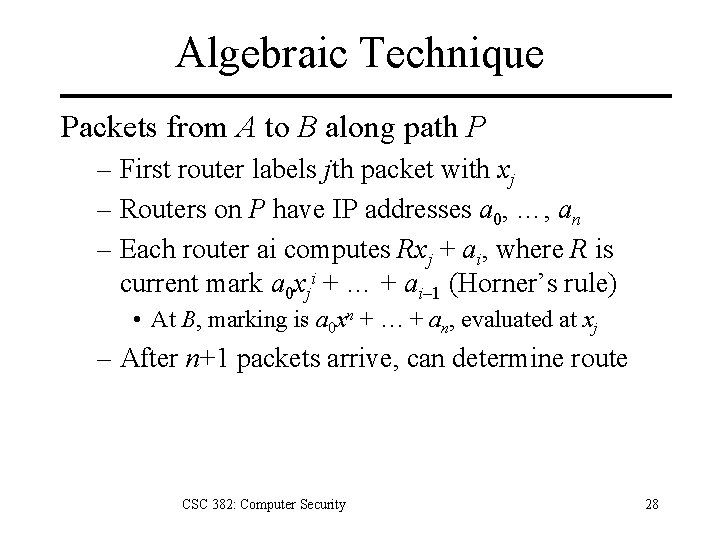
Algebraic Technique Packets from A to B along path P – First router labels jth packet with xj – Routers on P have IP addresses a 0, …, an – Each router ai computes Rxj + ai, where R is current mark a 0 xji + … + ai– 1 (Horner’s rule) • At B, marking is a 0 xn + … + an, evaluated at xj – After n+1 packets arrive, can determine route CSC 382: Computer Security 28

Alternative Alternate approach: at most l routers mark packet this way – l set by first router – Marking routers decrement it – Experiment analyzed 20, 000 packets marked by this scheme; recovered paths of length 25 about 98% of time CSC 382: Computer Security 29

Problem Who assigns xj? – Infeasible for a router to know it is first on path – Can use weighting scheme to determine if router is first Attacker can place arbitrary info into marking – If router does not select packet for marking, bogus information passed on – Destination cannot tell if packet has had bogus information put in it CSC 382: Computer Security 30

Counterattacking Use legal procedures – Collect chain of evidence so legal authorities can establish attack was real. – Check with lawyers for this • Rules of evidence very specific and detailed. • If you don’t follow them, expect case to be dropped. Technical attack – Goal is to damage attacker seriously enough to stop current attack and deter future attacks. CSC 382: Computer Security 31

Consequences 1. Counterattack may harm innocent party. • Attacker may have broken into source of attack or may be impersonating innocent party. 2. Counterattack may have side effects. • If counterattack is flooding, may block legitimate use of network. 3. Counterattack antithetical to shared use of network. • Counterattack absorbs network resources and makes threats more immediate. 4. Counterattack may be legally actionable. CSC 382: Computer Security 32

Example: Counterworm • Counterworm given signature of worm. • Counterworm spreads rapidly, deleting all occurrences of original worm. – ex: Welchia/Nachi hunts Blaster/My. Doom worms. • Issues – Can counterworm delete only targeted worm? – What if infected system gathering worms for research? – How do originators of counterworm know it will not cause problems for any system? • And are they legally liable if it does? CSC 382: Computer Security 33

Key Points • • Security incidents come in many forms. Prepare for an incident before one occurs. Understand your response goals. Don’t trust the affected system in any way. Contain the problem, then prepare detailed response. Save data offline for later analysis. Legal issues of counterattacks. CSC 382: Computer Security 34

References 1. 2. 3. 4. 5. 6. 7. Matt Bishop, Introduction to Computer Security, Addison-Wesley, 2005. N. Brownlee and E. Guttman, , “RFC 2350 - Expectations for Computer Security Incident Response, ” http: //www. faqs. org/rfcs/rfc 2350. html, 1998. CERT, “Computer Security Incident Response Team (CSIRT) FAQ, ” http: //www. cert. org/csirts/csirt_faq. html William Cheswick, Steven Bellovin, Steven, and Avriel Rubin, Firewalls and Internet Security, 2 nd edition, Addison-Wesley, 2003. Fraser (ed. ), “RFC 2196 - Site Security Handbook, ” http: //www. faqs. org/rfcs/rfc 2196. html, 1997. Garfinkel, Simson, Spafford, Gene, and Schartz, Alan, Practical UNIX and Internet Security, 3 rd edition, O’Reilly & Associates, 2003. Kevin Mandia, Chris Prosise, and Matt Pepe, Incident Response & Computer Forensics, 2 nd edition, Mc. Graw-Hill, 2003. CSC 382: Computer Security 35