CSC 382 Computer Security Authentication CSC 382 Computer





























- Slides: 48

CSC 382: Computer Security Authentication CSC 382: Computer Security 1

Authentication 1. What is Authentication? 2. Passwords 1. Dictionary Attacks 2. UNIX and Windows Passwords 3. Password Selection 3. Challenge-Response 4. Biometrics 5. Location CSC 382: Computer Security 2

What is Authentication? Binding of an identity to a subject Based on: 1. 2. 3. 4. What the entity knows (e. g. , passwords) What the entity has (e. g. , access card) What the entity is (e. g. , fingerprints) Where the entity is (e. g. , local terminal) CSC 382: Computer Security 3

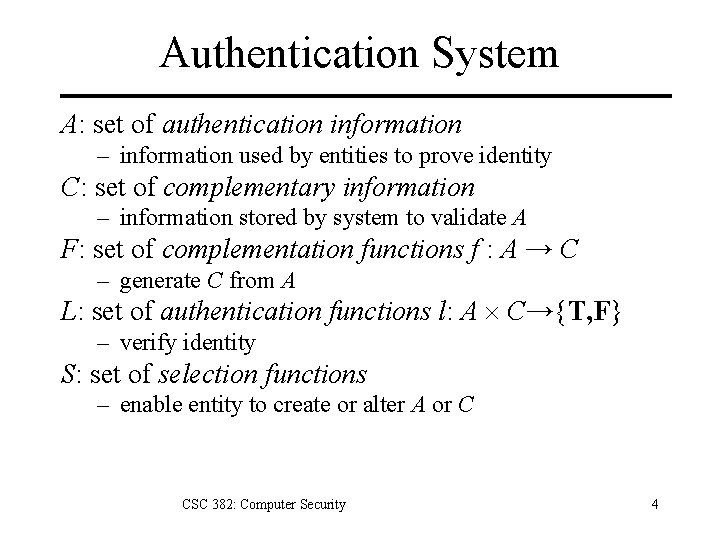
Authentication System A: set of authentication information – information used by entities to prove identity C: set of complementary information – information stored by system to validate A F: set of complementation functions f : A → C – generate C from A L: set of authentication functions l: A C→{T, F} – verify identity S: set of selection functions – enable entity to create or alter A or C CSC 382: Computer Security 4

Password System Example User authenticates with 8 -character alphanumeric password. System compares against stored cleartext password. A = [A-Za-z 0 -9]{8} C=A F={I} L={=} Not a system that anyone should actually use. CSC 382: Computer Security 5

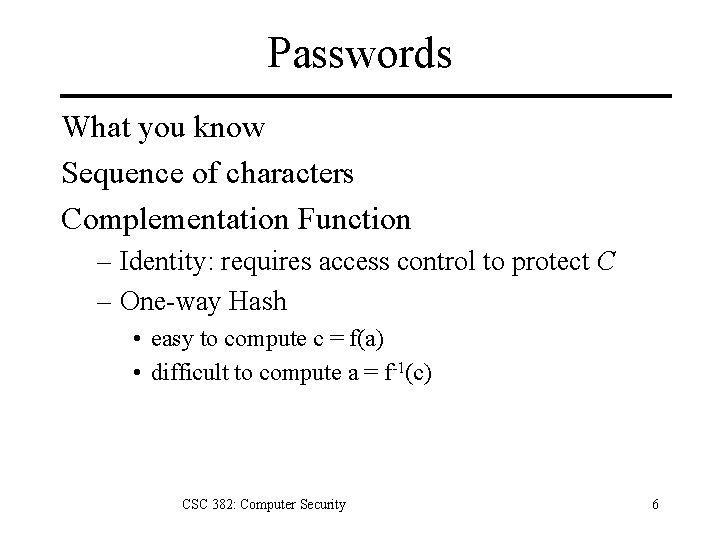
Passwords What you know Sequence of characters Complementation Function – Identity: requires access control to protect C – One-way Hash • easy to compute c = f(a) • difficult to compute a = f-1(c) CSC 382: Computer Security 6

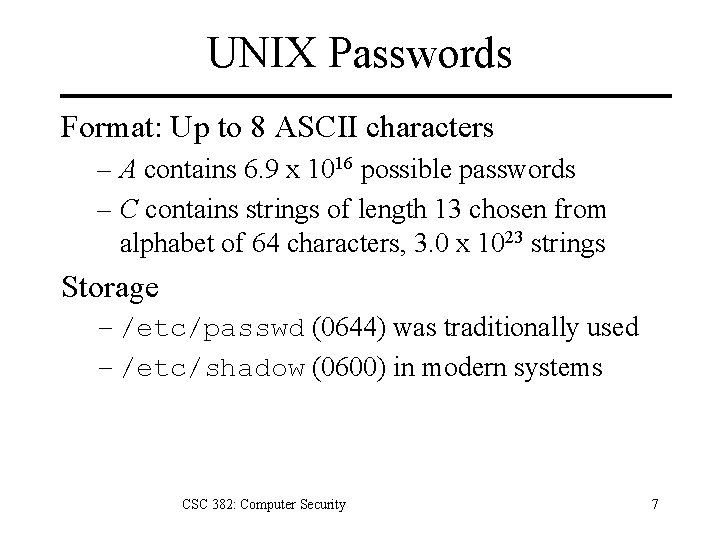
UNIX Passwords Format: Up to 8 ASCII characters – A contains 6. 9 x 1016 possible passwords – C contains strings of length 13 chosen from alphabet of 64 characters, 3. 0 x 1023 strings Storage – /etc/passwd (0644) was traditionally used – /etc/shadow (0600) in modern systems CSC 382: Computer Security 7

Password Cracking Find a A, such that, for f F, f(a) = c C and c is associated with a particular entity. Methods of determining whether a is associated with an entity: 1. Compute f(a) – Defend by hiding info so a, c, or f unknown. 2. Authenticate via l(a) – Defend by preventing access to auth functions L. CSC 382: Computer Security 8

Dictionary Attack Guess password by repeated trial and error. Types of Dictionary Attacks: 1. Compute f(g), requires password hashes. 1. Compute f(g) for each guess g and each f F. 2. Success if f(g) matches complementary info for any entity E. 2. Compute l(g) 1. Attempt l(g) for each guess g. 2. Success if l(g) true. CSC 382: Computer Security 9

Types of Dictionary Attacks 1. Common passwords 2. English/foreign words 3. Permutation rules – Substitute numbers/symbols for letters – Change case, pluralize, reverse words, character shifts, digit/symbol prefix/postfix, joining words 4. Brute force – All possible strings CSC 382: Computer Security 10

Making Password Guessing Easier Web sites will e-mail you password if you answer a simple “secret” question: 1. What is your favorite color? 2. What is your pet’s name? 3. What is your mother’s maiden name? Violation of fail-safe defaults Failover to less secure protocol. How many favorite colors are there? CSC 382: Computer Security 11

Countering Password Guessing Choose a, c, and f to select suitably low probability of successful guessing P(T) >= TG / N – G is number of guess per time unit T – T is number of time units in attack – N is number of possible passwords CSC 382: Computer Security 12

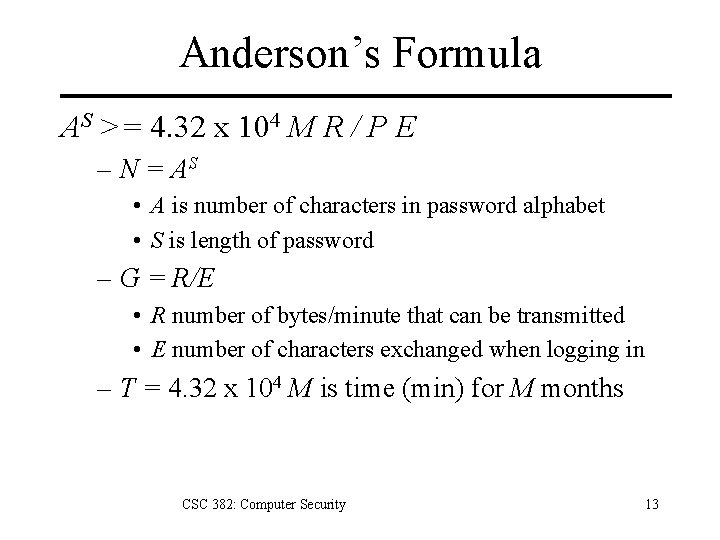
Anderson’s Formula AS >= 4. 32 x 104 M R / P E – N = AS • A is number of characters in password alphabet • S is length of password – G = R/E • R number of bytes/minute that can be transmitted • E number of characters exchanged when logging in – T = 4. 32 x 104 M is time (min) for M months CSC 382: Computer Security 13

Example Password System – A = 96 characters – System allows 104 guesses/second – Requirement: probablility of success guess should be 0. 5 over 365 -day period What should the minimum password length be? – N >= TG/P – N >= (365 x 24 x 60) x 104 / 0. 5 = 6. 31 x 1011 S – 96 i >= N = 6. 31 x 1011 is true when S >= 6 – The minimum required password length is 6. CSC 382: Computer Security 14

Assumptions 1. Time to test password is constant • • Reasonable for f F Choose minimum time if variable. 2. All passwords are equally likely to be selected. • Dependent on password selection mechanism CSC 382: Computer Security 15

UNIX Password Hashing crypt() function used for hashing – DES encrypts 64 -bit block of 0 s (25 rounds) using your password for the key. • Modified DES incompatible with DES hardware cracking tools. – Limited to 8 characters or less. – If limited to 95 printable characters, only 253 possible passwords. – How to resist dictionary attacks? Salting CSC 382: Computer Security 16

Salting Adds a 2 -character (12 -bit) random, public data to password to create key. Any word may be encrypted in 4096 possible ways (i. e. , there are 4096 f F). – Your password always uses same salt. – Someone else with same password (a) probably has different salt, and thus different c = f(a). Number of possible keys increased to 266 – Too small for today; modern UNIX uses MD 5/SHA-1. CSC 382: Computer Security 17

Salting (cont. ) Prevents pre-calculated dictionary attack – 266 passwords requires millions of terabytes crypt() 218 passwords/second – Brute force would require 8000 machines for 48 days. CSC 382: Computer Security 18

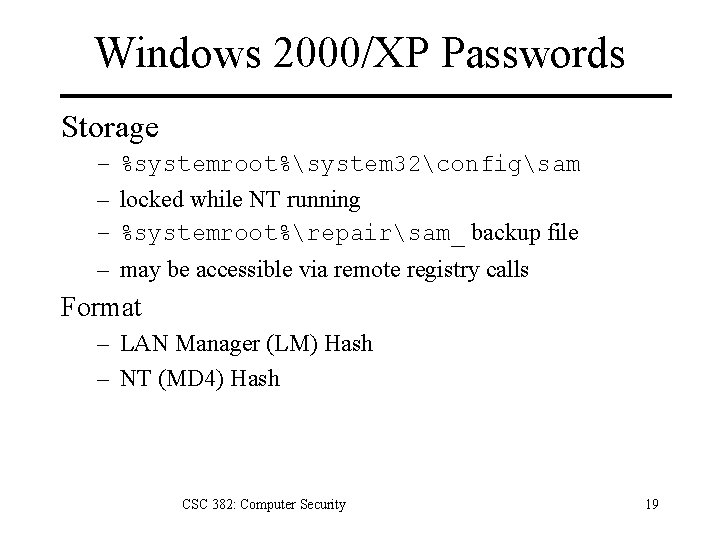
Windows 2000/XP Passwords Storage – – %systemroot%system 32configsam locked while NT running %systemroot%repairsam_ backup file may be accessible via remote registry calls Format – LAN Manager (LM) Hash – NT (MD 4) Hash CSC 382: Computer Security 19

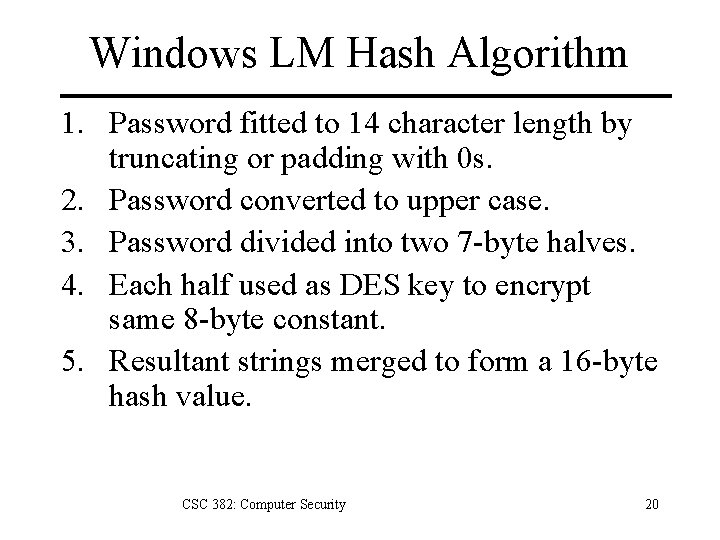
Windows LM Hash Algorithm 1. Password fitted to 14 character length by truncating or padding with 0 s. 2. Password converted to upper case. 3. Password divided into two 7 -byte halves. 4. Each half used as DES key to encrypt same 8 -byte constant. 5. Resultant strings merged to form a 16 -byte hash value. CSC 382: Computer Security 20

Windows LM Hash Problems Last 8 bytes of c known if password < 7 chars. Dividing password into halves reducing problem of breaking 14 -character password to breaking two 7 character passwords. Conversion to upper case reduces character set. Dictionary of password hashes can be prebuilt – Number of possible passwords much smaller than DES space. – No salt is used. CSC 382: Computer Security 21

Windows NT Hash Converts to Unicode, MD 4 hashes result Caveat: Often used in conjunction with LM hash, which is required for backwards compatibility. No salt: identical passwords generate identical hashes. CSC 382: Computer Security 22

Password Selection 1. Random Selection 2. Pronounceable Passwords 3. User Selection CSC 382: Computer Security 23

Random Selection Yields equal distribution of passwords for maximum difficulty in cracking – What about short passwords? Random passwords aren’t easy to remember – Short term memory holds 7 +/- 2 items – People have multiple passwords – Principle of Psychological Acceptability Requires a good PRNG CSC 382: Computer Security 24

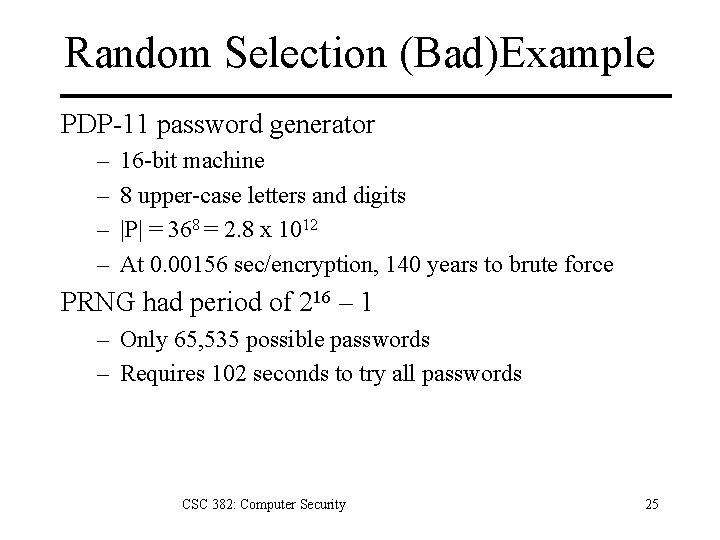
Random Selection (Bad)Example PDP-11 password generator – – 16 -bit machine 8 upper-case letters and digits |P| = 368 = 2. 8 x 1012 At 0. 00156 sec/encryption, 140 years to brute force PRNG had period of 216 – 1 – Only 65, 535 possible passwords – Requires 102 seconds to try all passwords CSC 382: Computer Security 25

Pronounceable Passwords Generate passwords from random phonemes instead of random characters. – People can remember password as sequence of audible phonemes instead of characters, allowing easy recall of longer passwords. – Fewer pronounceable passwords exist than random passwords. CSC 382: Computer Security 26

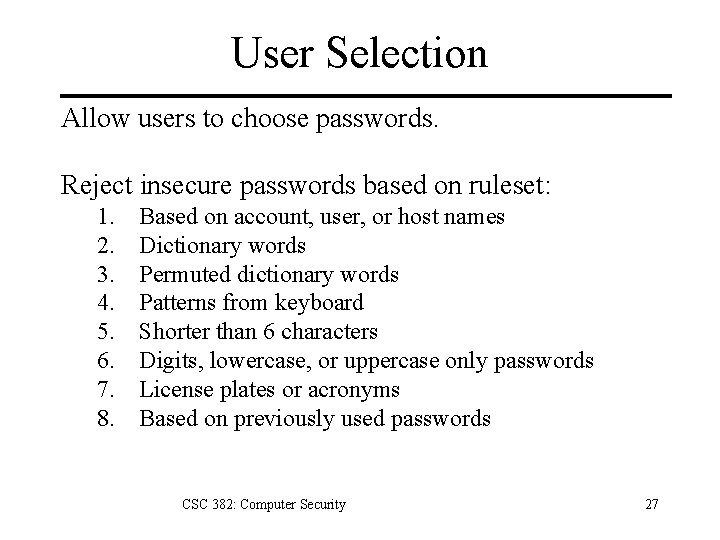
User Selection Allow users to choose passwords. Reject insecure passwords based on ruleset: 1. 2. 3. 4. 5. 6. 7. 8. Based on account, user, or host names Dictionary words Permuted dictionary words Patterns from keyboard Shorter than 6 characters Digits, lowercase, or uppercase only passwords License plates or acronyms Based on previously used passwords CSC 382: Computer Security 27

How to Select Good Passwords 1. 2. 3. 4. 5. Use a long password (at least 8 chars). Avoid dictionary words and permutations. Avoid using passwords based on old ones. Incorporate numbers and/or punctuation. Use a pass phrase – Use nth letter of each word if phrase too long. 6. Manual random generation – Roll dice to select word from list. CSC 382: Computer Security 28

Guessing via Authentication Fns If complements not accessible, attacker must use authentication functions. Cannot be prevented. Increase difficulty of auth function attack: Backoff: increasing wait before reprompting. Disconnection: disconnect after n failures. Disabling: disable account after n failures. Jailing: permit access to limited system, so admins can observe attacker. CSC 382: Computer Security 29

Password Aging Requirement that password be changed after a period of time or after an event has occurred If expected time to guess is 180 days, should change password more frequently than 180 days 1. If change time too short, users have difficulty recalling passwords. 2. Cannot allow users to change password to current one. 3. Also prevent users from changing passwords too soon. 4. Give notice of impending password change requirement. CSC 382: Computer Security 30

Challenge-Response Problem: passwords are reusable, and thus subject to replay attacks. Solution: authenticate in such a way that the transmitted password changes each time. CSC 382: Computer Security 31

One-Time Passwords A password that’s invalidated once used. Challenge: number of auth attempt Response: one-time password Problems – Generation of one-time passwords • Use hash or crytographic function – Synchronization of the user and the system • Number or timestamp passwords CSC 382: Computer Security 32

S/Key One-time password system based on a hash function h (MD 4 or MD 5). User initializes with random seed k. Key generator calculates: h(k) = k 1, h(k 1) = k 2, …, h(kn-1) = kn Passwords, in order used, are p 1 = kn, p 2 = kn-1, …, pn-1= k 2, pn= k 1 CSC 382: Computer Security 33

S/Key Attacker cannot derive pi+1 from pi since pi = kn-i+1, pi+1 = kn-i, and h(kn-i) = kn-i+1 which would require inverting h. Once user has used all passwords, S/Key must be re-initialized with a new seed. CSC 382: Computer Security 34

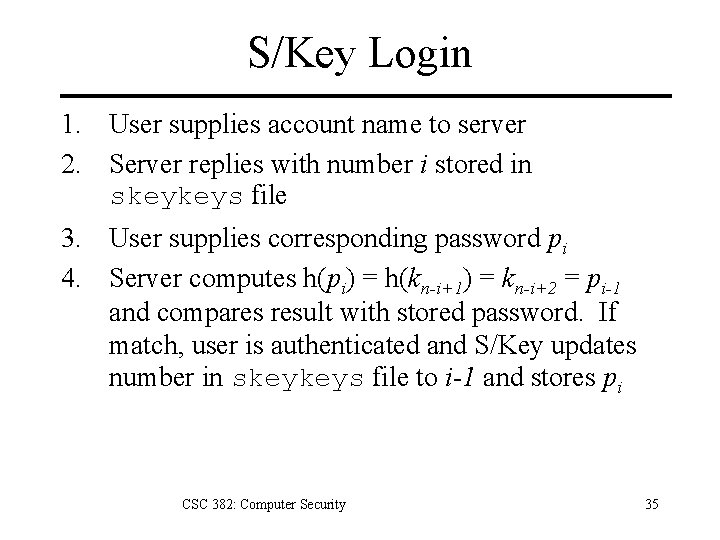
S/Key Login 1. User supplies account name to server 2. Server replies with number i stored in skeykeys file 3. User supplies corresponding password pi 4. Server computes h(pi) = h(kn-i+1) = kn-i+2 = pi-1 and compares result with stored password. If match, user is authenticated and S/Key updates number in skeykeys file to i-1 and stores pi CSC 382: Computer Security 35

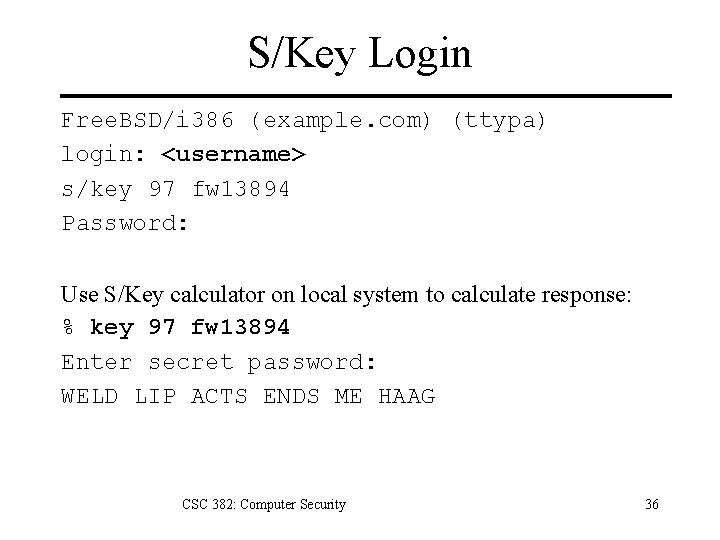
S/Key Login Free. BSD/i 386 (example. com) (ttypa) login: <username> s/key 97 fw 13894 Password: Use S/Key calculator on local system to calculate response: % key 97 fw 13894 Enter secret password: WELD LIP ACTS ENDS ME HAAG CSC 382: Computer Security 36

Other One Time Password Systems Software: OPIE – Backwards compatible with S/Key (if same hash used). Hardware: RSA Secur. ID card – Displayed password changes every 60 sec. – Password = constant password + Secur. ID CSC 382: Computer Security 37

Biometrics Identification by human anatomic or behavioral characteristics. A biometric characteristic should be: 1. 2. 3. 4. universal: everyone should have it unique: not two people should share it permanent: it should not change with time quantifiable: it must be practically measurable CSC 382: Computer Security 38

Biometric Measurement Possible Outcomes: 1. 2. 3. 4. Correct person accepted Imposter rejected Correct person rejected (False Rejection) Imposter accepted (False Acceptance) Tradeoff exists between False Accept Rate and False Reject Rate CSC 382: Computer Security 39

Fingerprints Capacitive measurement, using differences in electrical charges of whorls on finger to detect those parts touching chip and those raised. Attacks: – Forcing authorized user to grant access. – Recover latent fingerprint impression. – Artificial gummy fingers made from molding plastic/gelatin 68 -100% successful when tested against 11 types of fingerprint auth systems. CSC 382: Computer Security 40

Types of Biometrics Voice Characteristic Recognition – statistical analysis of voice characteristics Eyes – iris patterns – retina patterns • pattern of blood vessels observed by laser Face Recognition – Can it distinguish a face from a picture of that face? CSC 382: Computer Security 41

Types of Biometrics (cont. ) Keystroke Dynamics – Signature based on keystroke intervals, pressure, duration, and where key is struck. – Belived to be unique as written signatures. – Dynamic detection constantly observes user. Combinations – Combine multiple biometric techniques. – Not necessarily an improvement: typically can reduce either False Accept Rate or False Reject Rate, not both. CSC 382: Computer Security 42

Biometrics are not infallible What are False Accept and Reject Rates? Do the characteristics change over time? – Retina changes during pregnancy. – Fingerprint damage due to work/pipe smoking. – Young and old people have fainter fingerprints. Is it accurate in the installed environment? – Is someone observing fingerprint or voiceprint checks? – i. e. , did you collect biometric from the person? CSC 382: Computer Security 43

Biometrics can be compromised. Unique identifiers, not secrets. – You can change a password. – You can’t change your iris scan. Examples: – You leave your fingerprints every place. – It’s easy to take a picture of your face. Other compromises. – Use faux ATM-style devices to collect biometrics. – Obtain all biometric templates from server. CSC 382: Computer Security 44

Use and Misuse of Biometrics Employee identification. – Employee enters login name. – System uses fingerprint to verify employee is who he claims to be. – Problem: Does biometric match the employee? Criminal search (Superbowl 2001) – System uses face recognition to search for criminals in public places. – Problem: Does any biometric in database match anyone in a crowd of people? – Assume system is 99. 99% accurate and 1 in 10 million people is a terrorist. Result: 1000 false positives for each terrorist. CSC 382: Computer Security 45

Location Classic: only allow access from a particular terminal or a particular set of remote hosts. Modern: GPS-based – Location Signature Sensor (LSS) for host and user. – Access rules permit user only to access host with specific LSS values. – Cell-phones track location, and some states use them to track drivers’ speed and locations. CSC 382: Computer Security 46

Key Points 1. Authentication consists of an entity, the user, attempting to convince another entity, the verifier, of the user’s identity – something you know, something you have, something you are, somewhere you are located 2. Passwords are the most common and basic type of authentication – – Dictionary Attacks Challenge Response: One-Time Passwords 3. Biometrics verify identity based on measured physical characteristics of the user CSC 382: Computer Security 47

References 1. 2. 3. 4. 5. 6. 7. 8. Phil Agre. “Your Face is not a Bar Code, ” http: //polaris. gseis. ucla. edu/pagre/bar-code. html, 2003. Ross Anderson, Security Engineering, Wiley, 2001. Matt Bishop, Introduction to Computer Security, Addison-Wesley, 2005. Ben Mook, “Md. pilot program tracks drivers’ speed, location via cell phones, ” The Daily Record, October 21, 2005, http: //www. mddailyrecord. com/pub/5_398_friday/businessnews/172883 -1. html Bruce Schneier, “Biometrics: Truths and Fictions, ” Cryptogram, http: //www. schneier. com/crypto-gram-9808. html#biometrics, 1998. Bruce Schneier, “The Curse of the Secret Question, ” http: //www. schneier. com/essay-081. html, 2005. John Viega and Gary Mc. Graw, Building Secure Software, Addison. Wesley, 2002. David Wheeler, Secure Programming for UNIX and Linux HOWTO, http: //www. dwheeler. com/secure-programs/Secure-Programs. HOWTO/index. html, 2003. CSC 382: Computer Security 48