CSC 382 Computer Security TCPIP CSC 382 Computer

























- Slides: 67

CSC 382: Computer Security TCP/IP CSC 382: Computer Security 1

Topics 1. 2. 3. 4. 5. 6. 7. 8. TCP/IP Layering Encapsulation Internet Addresses Link Layer Protocols IP Routing TCP and UDP Application Layer Protocols CSC 382: Computer Security 2

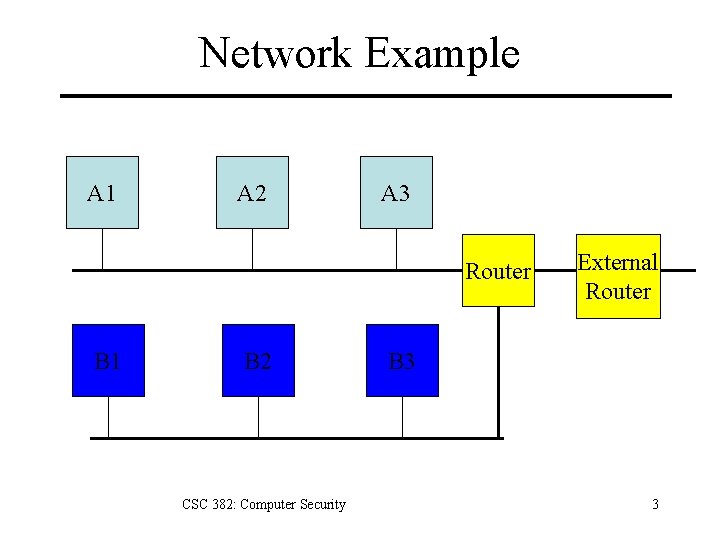
Network Example A 1 A 2 A 3 Router B 1 B 2 CSC 382: Computer Security External Router B 3 3

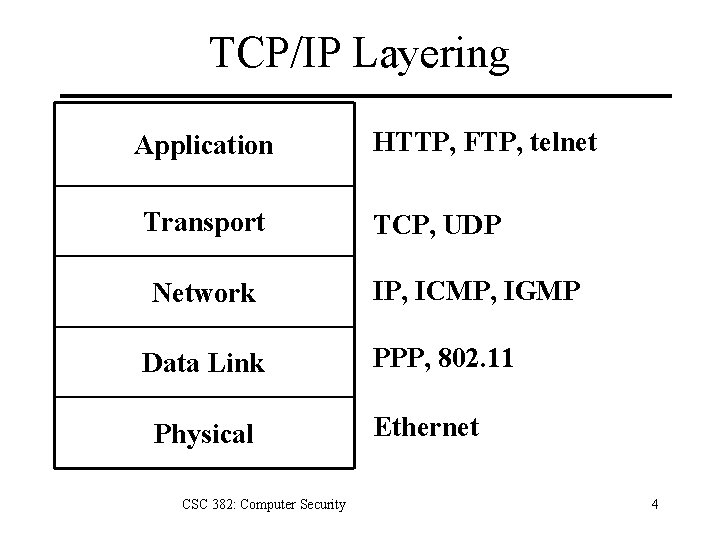
TCP/IP Layering Application Transport Network Data Link Physical CSC 382: Computer Security HTTP, FTP, telnet TCP, UDP IP, ICMP, IGMP PPP, 802. 11 Ethernet 4

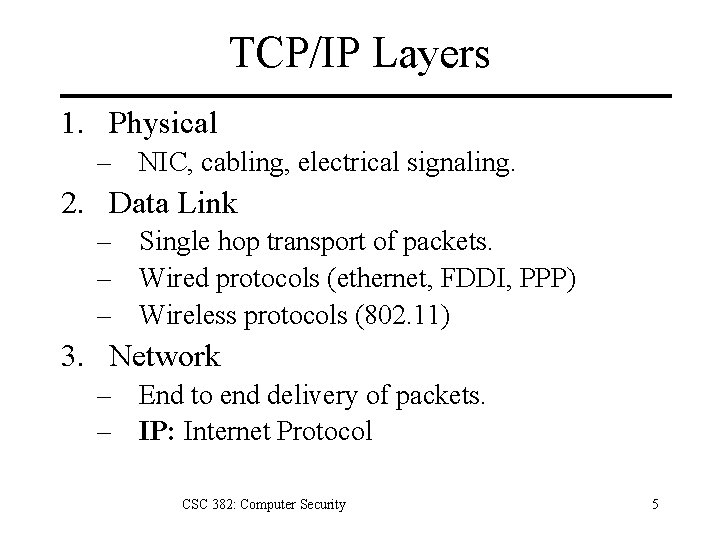
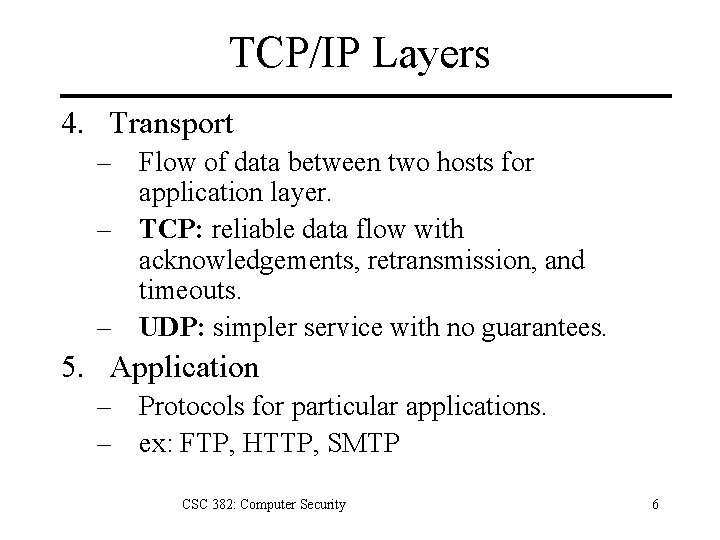
TCP/IP Layers 1. Physical – NIC, cabling, electrical signaling. 2. Data Link – Single hop transport of packets. – Wired protocols (ethernet, FDDI, PPP) – Wireless protocols (802. 11) 3. Network – End to end delivery of packets. – IP: Internet Protocol CSC 382: Computer Security 5

TCP/IP Layers 4. Transport – Flow of data between two hosts for application layer. – TCP: reliable data flow with acknowledgements, retransmission, and timeouts. – UDP: simpler service with no guarantees. 5. Application – Protocols for particular applications. – ex: FTP, HTTP, SMTP CSC 382: Computer Security 6

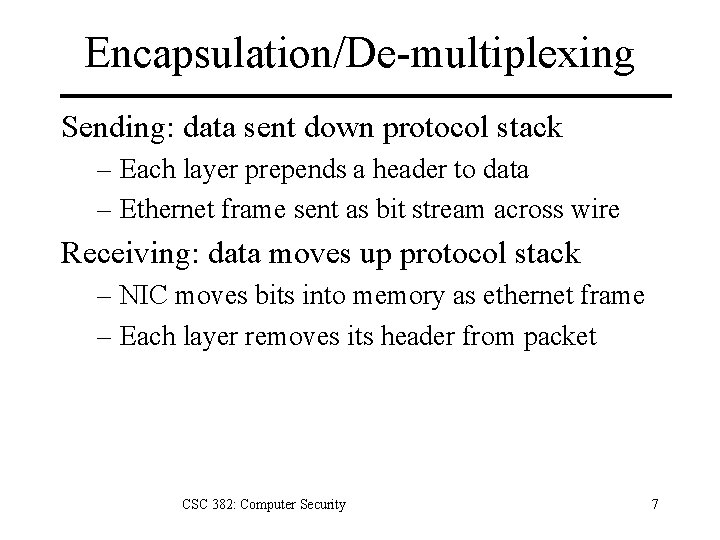
Encapsulation/De-multiplexing Sending: data sent down protocol stack – Each layer prepends a header to data – Ethernet frame sent as bit stream across wire Receiving: data moves up protocol stack – NIC moves bits into memory as ethernet frame – Each layer removes its header from packet CSC 382: Computer Security 7

Encapsulation CSC 382: Computer Security 8

De-multiplexing CSC 382: Computer Security 9

TCP/IP Security TCP/IP has no built-in strong security. – No confidentiality features. – Minimal availability features (To. S options). – Insecure CRC checksums for integrity. – IPsec protocol extension adds security. CSC 382: Computer Security 10

Data Link Layer IEEE Standards – Ethernet (802. 3) – Token Ring (802. 5) – Wireless (802. 11) Serial Protocols – SLIP and CSLIP – PPP CSC 382: Computer Security 11

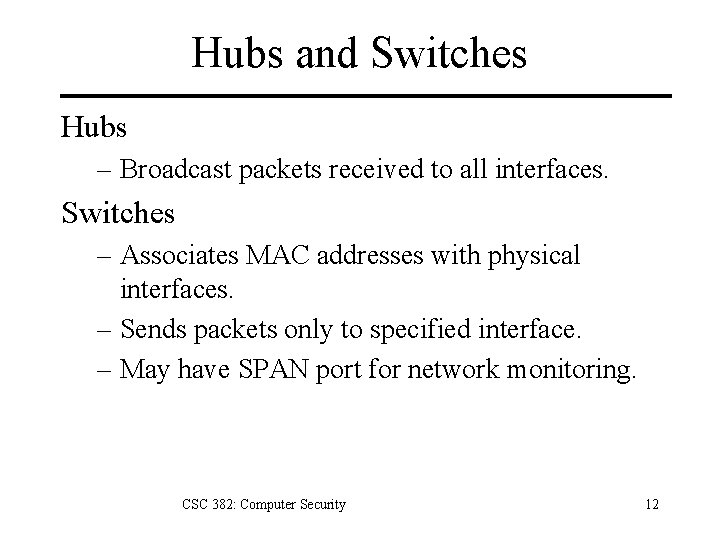
Hubs and Switches Hubs – Broadcast packets received to all interfaces. Switches – Associates MAC addresses with physical interfaces. – Sends packets only to specified interface. – May have SPAN port for network monitoring. CSC 382: Computer Security 12

Data Link Layer Loopback – Looks like any other link layer device. – Full network processing is performed. – Sends packets to localhost for testing. 48 -bit MAC address Maximum Transmission Unit (MTU) – 1492 or 1500 bytes, depending on ethernet std CSC 382: Computer Security 13

Promiscuous Mode • All ethernet frames to or from any locally connected host are seen by all hosts. • NIC normally filters out frames that are not addressed to its MAC address. • In promiscuous mode, NIC processes all ethernet frames, not just ones addressed to it. – Requires administrative access on most OSes. CSC 382: Computer Security 14

Packet Sniffers: – wiretap: ntercept network traffic – analysis: network protocol analysis/decoding Applications: – Network troubleshooting and education – Network intrusion detection – Security attacks (password interception) CSC 382: Computer Security 15

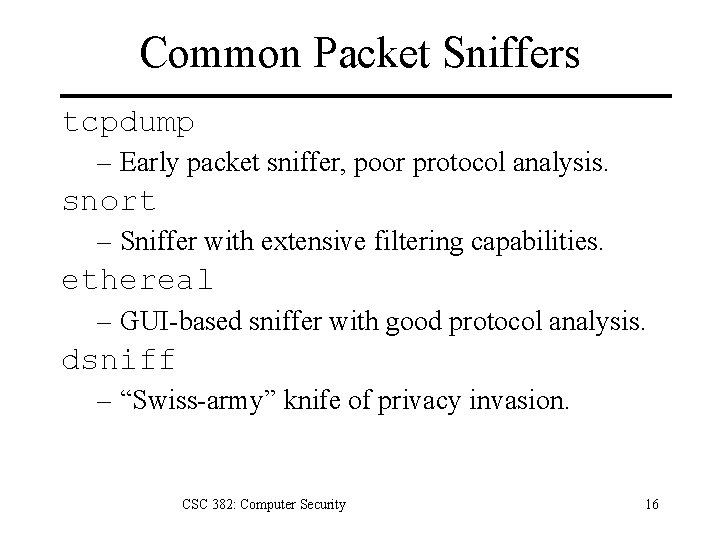
Common Packet Sniffers tcpdump – Early packet sniffer, poor protocol analysis. snort – Sniffer with extensive filtering capabilities. ethereal – GUI-based sniffer with good protocol analysis. dsniff – “Swiss-army” knife of privacy invasion. CSC 382: Computer Security 16

IP: Internet Protocol Unreliable, connectionless datagram service – Packets may arrived damaged, out of order, duplicated or not at all. – Transport/Application layers provide reliability. IPv 4 underlies Internet. – 32 -bit addresses in dotted-quad: 10. 17. 0. 90. – IPv 6 is successor with 128 -bit addresses. Complexities: addressing, routing CSC 382: Computer Security 17

IP Header CSC 382: Computer Security 18

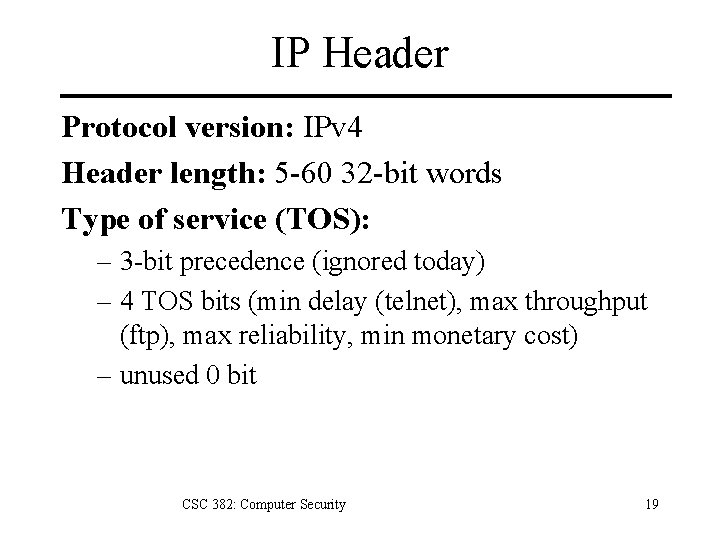
IP Header Protocol version: IPv 4 Header length: 5 -60 32 -bit words Type of service (TOS): – 3 -bit precedence (ignored today) – 4 TOS bits (min delay (telnet), max throughput (ftp), max reliability, min monetary cost) – unused 0 bit CSC 382: Computer Security 19

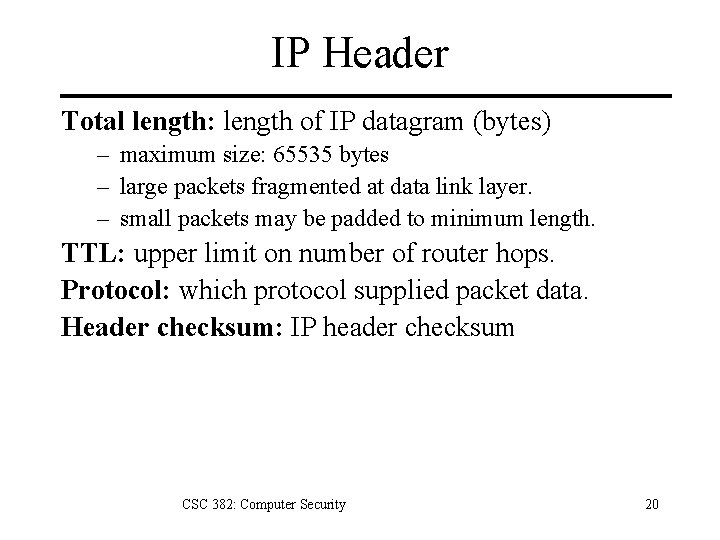
IP Header Total length: length of IP datagram (bytes) – maximum size: 65535 bytes – large packets fragmented at data link layer. – small packets may be padded to minimum length. TTL: upper limit on number of router hops. Protocol: which protocol supplied packet data. Header checksum: IP header checksum CSC 382: Computer Security 20

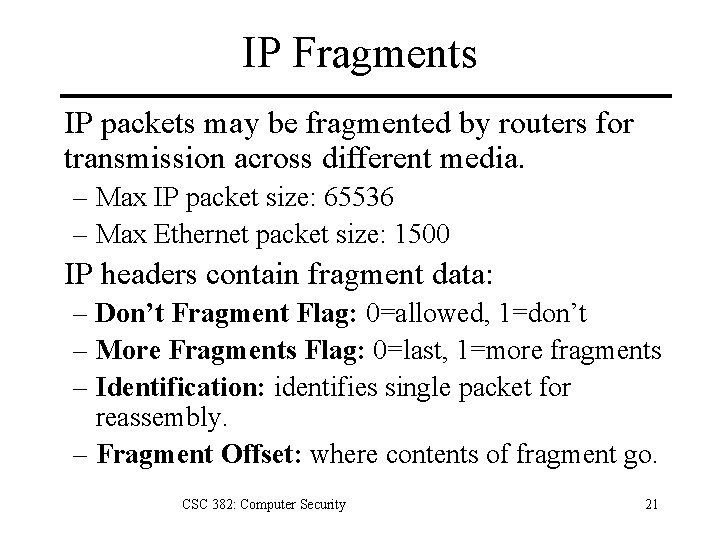
IP Fragments IP packets may be fragmented by routers for transmission across different media. – Max IP packet size: 65536 – Max Ethernet packet size: 1500 IP headers contain fragment data: – Don’t Fragment Flag: 0=allowed, 1=don’t – More Fragments Flag: 0=last, 1=more fragments – Identification: identifies single packet for reassembly. – Fragment Offset: where contents of fragment go. CSC 382: Computer Security 21

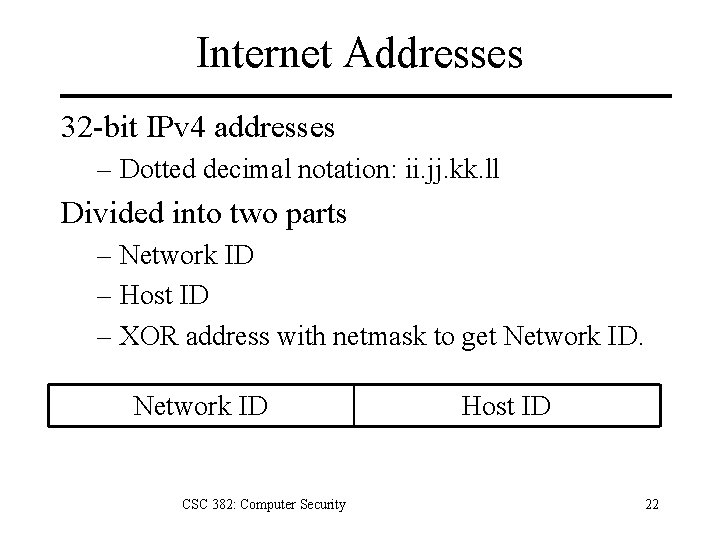
Internet Addresses 32 -bit IPv 4 addresses – Dotted decimal notation: ii. jj. kk. ll Divided into two parts – Network ID – Host ID – XOR address with netmask to get Network ID CSC 382: Computer Security Host ID 22

Address Classes Class A: 0. 0 -127. 255 8 -bit net ID, 24 -bit host ID Class B: 128. 0. 0. 0 -191. 255 16 -bit net ID, 16 -bit host ID Class C: 192. 0. 0. 0 -223. 255 24 -bit net ID, 8 -bit host ID Class D: 224. 0. 0. 0 -239. 255 28 -bit multicast group ID Class E: 240. 0 -255. 255 Reserved for future use CSC 382: Computer Security 23

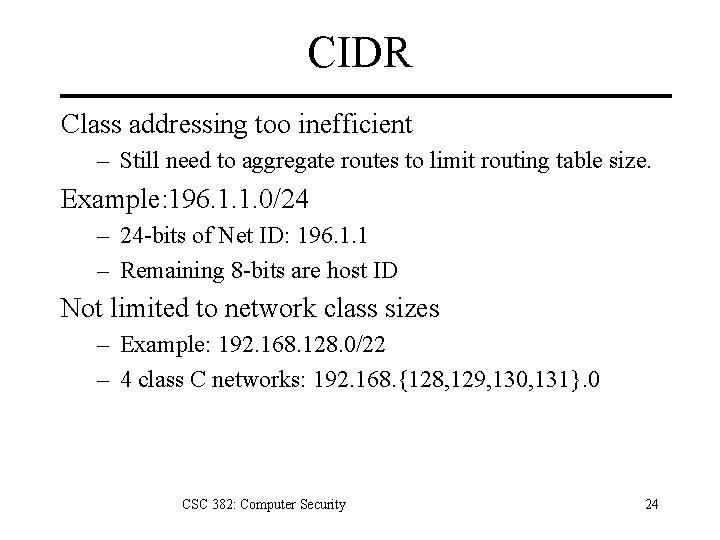
CIDR Class addressing too inefficient – Still need to aggregate routes to limit routing table size. Example: 196. 1. 1. 0/24 – 24 -bits of Net ID: 196. 1. 1 – Remaining 8 -bits are host ID Not limited to network class sizes – Example: 192. 168. 128. 0/22 – 4 class C networks: 192. 168. {128, 129, 130, 131}. 0 CSC 382: Computer Security 24

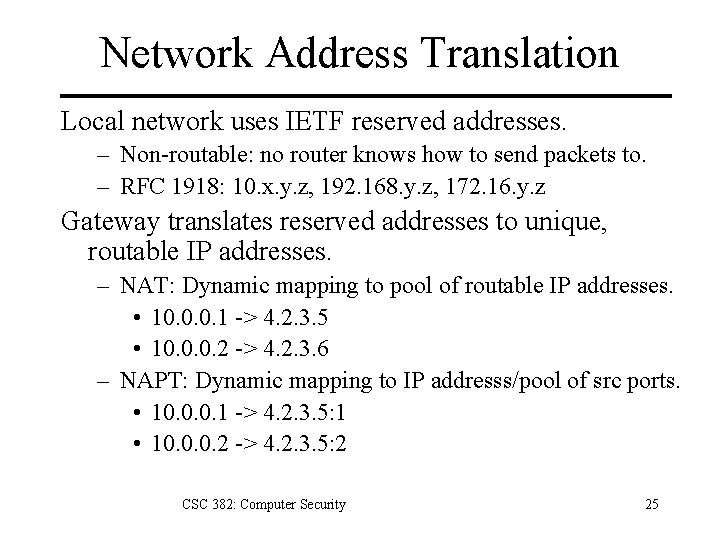
Network Address Translation Local network uses IETF reserved addresses. – Non-routable: no router knows how to send packets to. – RFC 1918: 10. x. y. z, 192. 168. y. z, 172. 16. y. z Gateway translates reserved addresses to unique, routable IP addresses. – NAT: Dynamic mapping to pool of routable IP addresses. • 10. 0. 0. 1 -> 4. 2. 3. 5 • 10. 0. 0. 2 -> 4. 2. 3. 6 – NAPT: Dynamic mapping to IP addresss/pool of src ports. • 10. 0. 0. 1 -> 4. 2. 3. 5: 1 • 10. 0. 0. 2 -> 4. 2. 3. 5: 2 CSC 382: Computer Security 25

ARP: Address Resolution Protocol MAC address determines packet destination. How does network layer supply the link layer with a MAC address? ARP: Address Resolution Protocol – Maps 32 -bit IP addresses to 48 -bit MAC addrs – Data link layer protocol above ethernet – RARP: Reverse ARP CSC 382: Computer Security 26

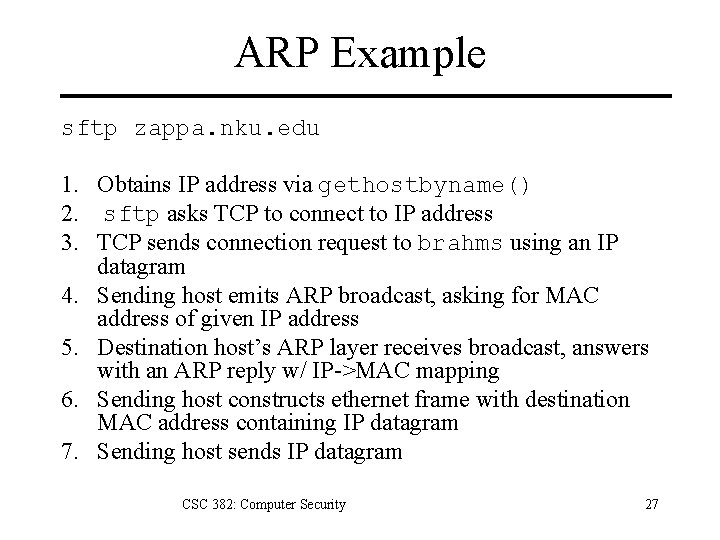
ARP Example sftp zappa. nku. edu 1. Obtains IP address via gethostbyname() 2. sftp asks TCP to connect to IP address 3. TCP sends connection request to brahms using an IP datagram 4. Sending host emits ARP broadcast, asking for MAC address of given IP address 5. Destination host’s ARP layer receives broadcast, answers with an ARP reply w/ IP->MAC mapping 6. Sending host constructs ethernet frame with destination MAC address containing IP datagram 7. Sending host sends IP datagram CSC 382: Computer Security 27

ARP Cache at 204 m 02 (10. 1. 0. 90) > arp -a Net to Device -----hme 0 hme 0 Media Table: IPv 4 IP Address ----------at_elan. lc 3 net 10. 1. 0. 79 at 204 m 02 10. 1. 7. 103 10. 139 CSC 382: Computer Security Phys Addr ---------00: a 2: cb: 28: 5 e 00: e 0: cf: 00: 0 e: 92 08: 00: 20: d 8: e 0: 07 00: 90: 27: b 6: b 5: e 5 00: e 0: cf: 00: 15: bd 28

ARP Features Proxy ARP – Router can answer ARP requests on network B for a host on network A that doesn’t see broadcast. Gratuitous ARP – Host sends ARP for own IP address at boot. – No reply should be received. – Network misconfiguration if reply received. CSC 382: Computer Security 29

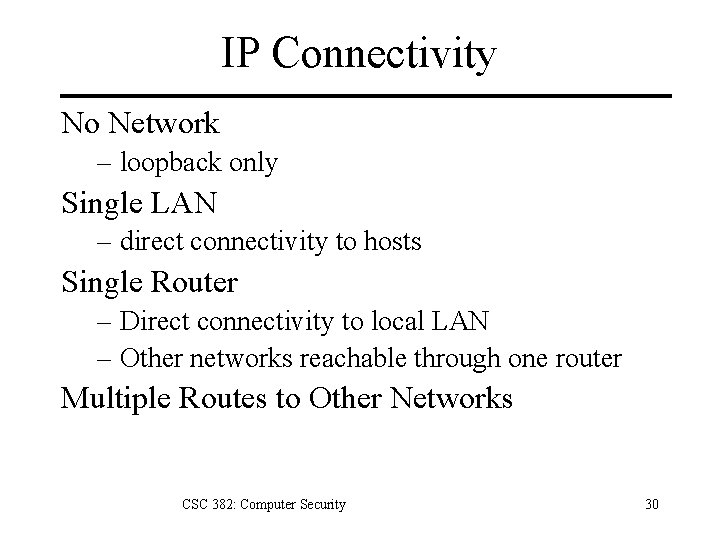
IP Connectivity No Network – loopback only Single LAN – direct connectivity to hosts Single Router – Direct connectivity to local LAN – Other networks reachable through one router Multiple Routes to Other Networks CSC 382: Computer Security 30

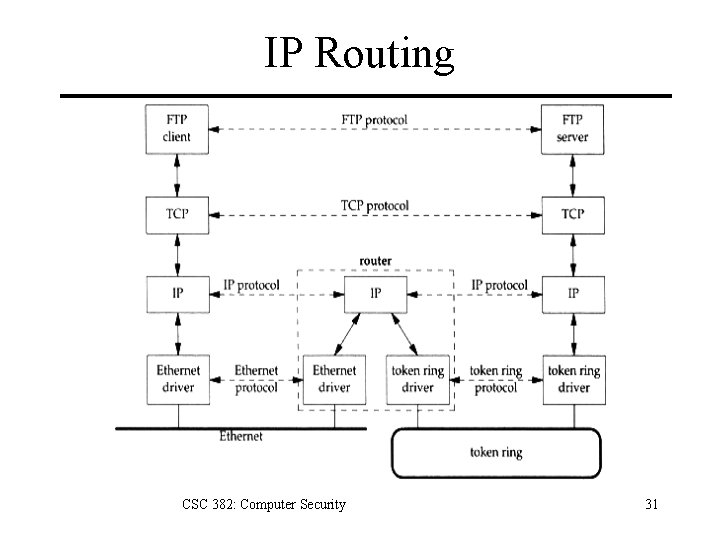
IP Routing CSC 382: Computer Security 31

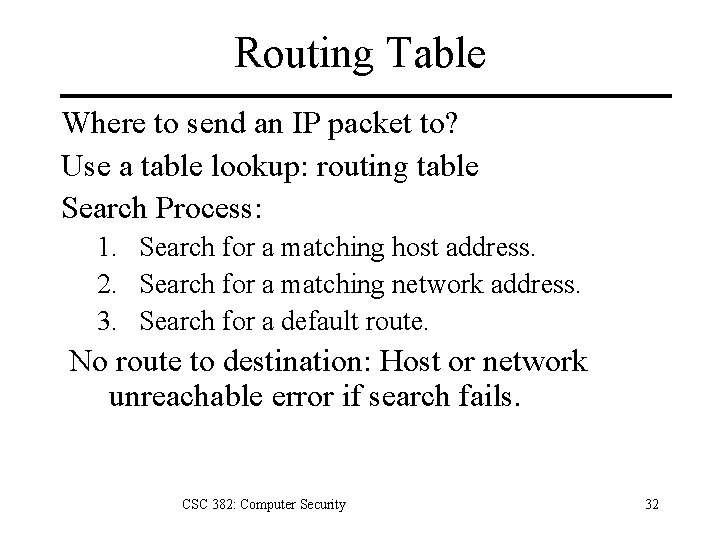
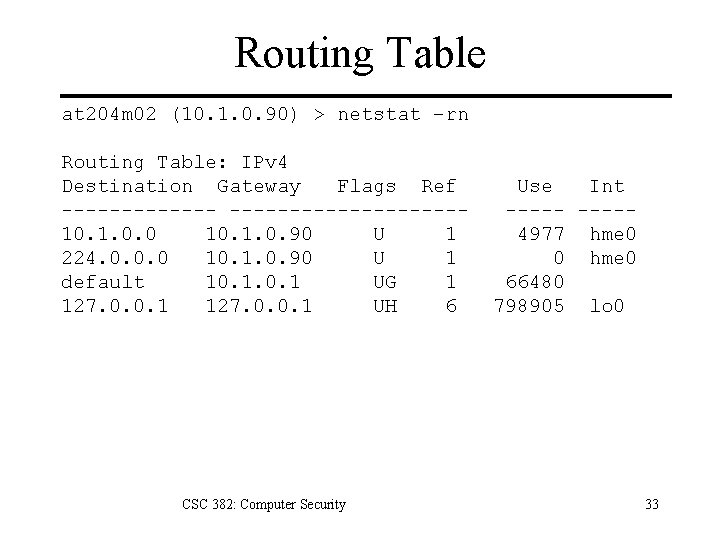
Routing Table Where to send an IP packet to? Use a table lookup: routing table Search Process: 1. Search for a matching host address. 2. Search for a matching network address. 3. Search for a default route. No route to destination: Host or network unreachable error if search fails. CSC 382: Computer Security 32

Routing Table at 204 m 02 (10. 1. 0. 90) > netstat –rn Routing Table: IPv 4 Destination Gateway Flags Ref -------------------10. 1. 0. 0 10. 1. 0. 90 U 1 224. 0. 0. 0 10. 1. 0. 90 U 1 default 10. 1 UG 1 127. 0. 0. 1 UH 6 CSC 382: Computer Security Use Int -----4977 hme 0 0 hme 0 66480 798905 lo 0 33

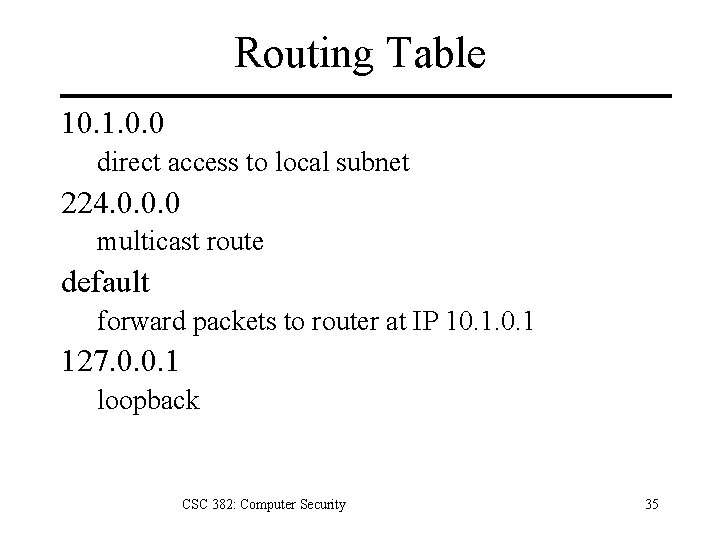
Routing Table Destination: final destination host/network Gateway: next host in route to destination Flags U: Route is up G: Route is to a gateway (router) H: Route destination is a host (not a network) D: Route created by a redirect M: Route modified by a redirect CSC 382: Computer Security 34

Routing Table 10. 1. 0. 0 direct access to local subnet 224. 0. 0. 0 multicast route default forward packets to router at IP 10. 1 127. 0. 0. 1 loopback CSC 382: Computer Security 35

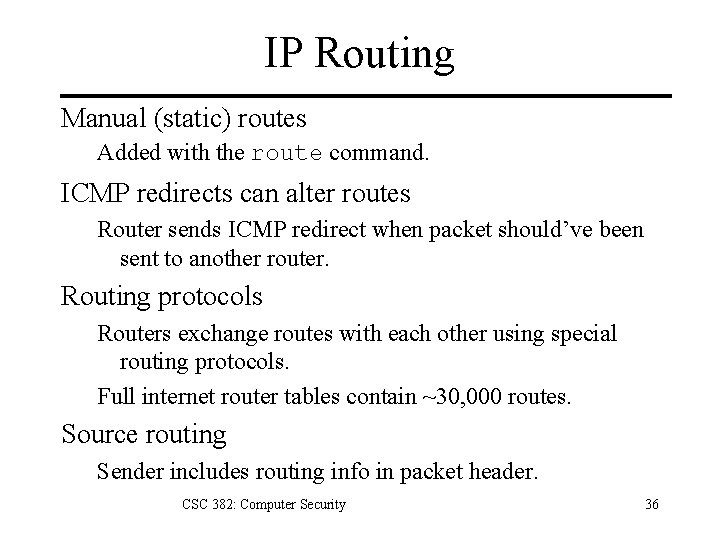
IP Routing Manual (static) routes Added with the route command. ICMP redirects can alter routes Router sends ICMP redirect when packet should’ve been sent to another router. Routing protocols Routers exchange routes with each other using special routing protocols. Full internet router tables contain ~30, 000 routes. Source routing Sender includes routing info in packet header. CSC 382: Computer Security 36

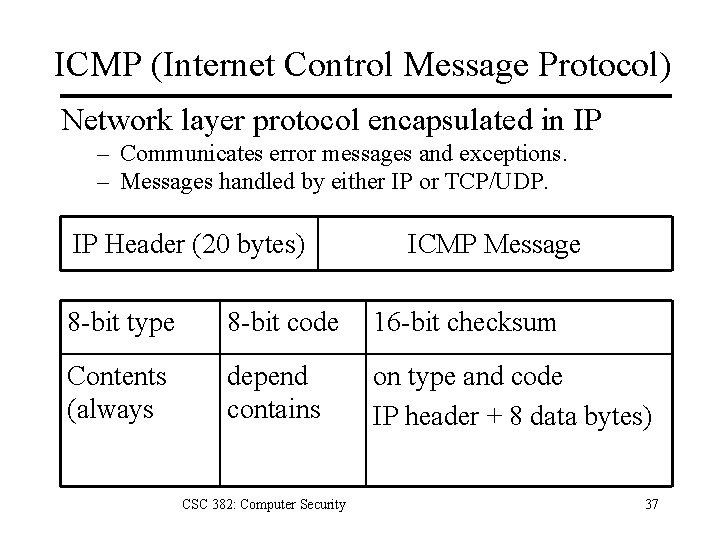
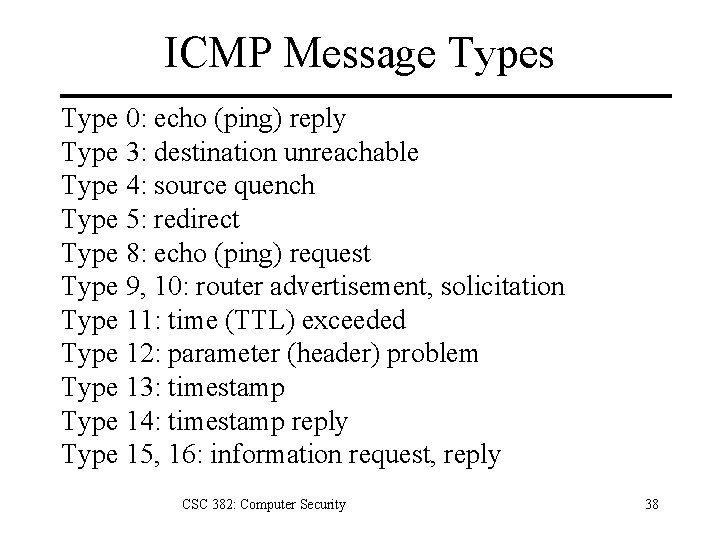
ICMP (Internet Control Message Protocol) Network layer protocol encapsulated in IP – Communicates error messages and exceptions. – Messages handled by either IP or TCP/UDP. IP Header (20 bytes) ICMP Message 8 -bit type 8 -bit code 16 -bit checksum Contents (always depend contains on type and code IP header + 8 data bytes) CSC 382: Computer Security 37

ICMP Message Types Type 0: echo (ping) reply Type 3: destination unreachable Type 4: source quench Type 5: redirect Type 8: echo (ping) request Type 9, 10: router advertisement, solicitation Type 11: time (TTL) exceeded Type 12: parameter (header) problem Type 13: timestamp Type 14: timestamp reply Type 15, 16: information request, reply CSC 382: Computer Security 38

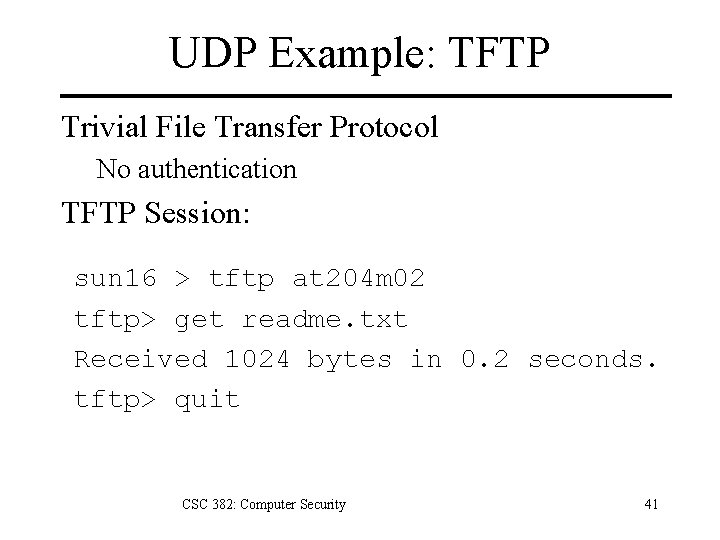
UDP: User Datagram Protocol Simple datagram transport layer protocol. Each application output generates one UDP datagram, which produces one IP datagram. Trades reliability for speed Sends datagrams directly to unreliable IP layer. 16 -bit port numbers Identify sending and receiving processes. Applications DNS, SNMP, TFTP, streaming audio/video CSC 382: Computer Security 39

UDP Header CSC 382: Computer Security 40

UDP Example: TFTP Trivial File Transfer Protocol No authentication TFTP Session: sun 16 > tftp at 204 m 02 tftp> get readme. txt Received 1024 bytes in 0. 2 seconds. tftp> quit CSC 382: Computer Security 41

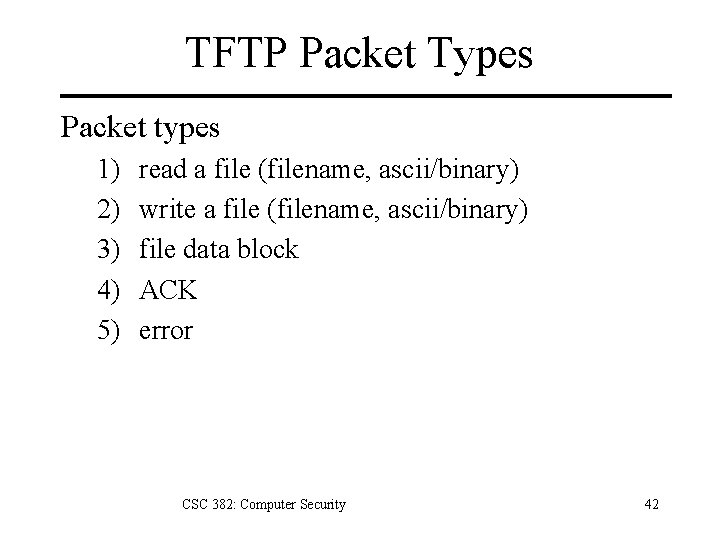
TFTP Packet Types Packet types 1) 2) 3) 4) 5) read a file (filename, ascii/binary) write a file (filename, ascii/binary) file data block ACK error CSC 382: Computer Security 42

TFTP Packet Diagram CSC 382: Computer Security 43

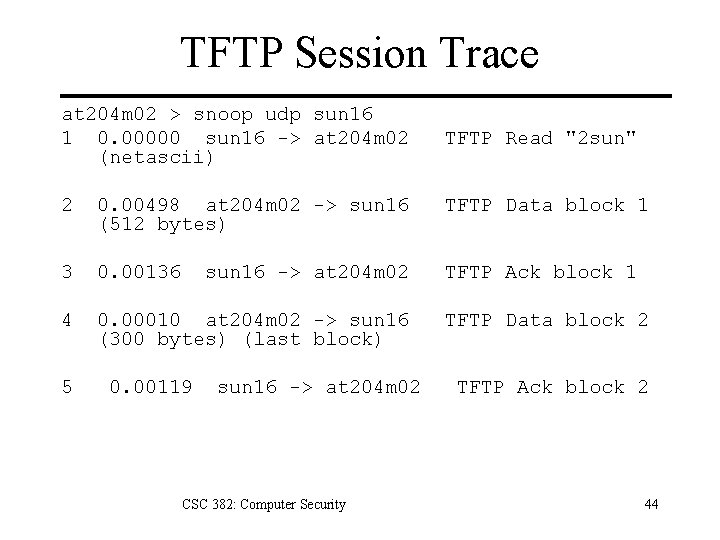
TFTP Session Trace at 204 m 02 > snoop udp sun 16 1 0. 00000 sun 16 -> at 204 m 02 (netascii) TFTP Read "2 sun" 2 0. 00498 at 204 m 02 -> sun 16 (512 bytes) TFTP Data block 1 3 0. 00136 TFTP Ack block 1 4 0. 00010 at 204 m 02 -> sun 16 (300 bytes) (last block) 5 sun 16 -> at 204 m 02 0. 00119 sun 16 -> at 204 m 02 CSC 382: Computer Security TFTP Data block 2 TFTP Ack block 2 44

TFTP Security Feature: no username/password required TFTP used for diskless hosts to boot. How to protect /etc/passwd? Limit TFTP server filesystem access. Generally only can access /tftpboot directory. CSC 382: Computer Security 45

TCP: Transmission Control Protocol Connection-oriented Must establish connection before sending data. 3 -way handshake. Reliable byte-stream TCP decides how to divide stream into packets. ACK, timeout, retransmit, reordering. 16 -bit source and destination ports. FTP(21), HTTP(80), POP(110), SMTP(25) CSC 382: Computer Security 46

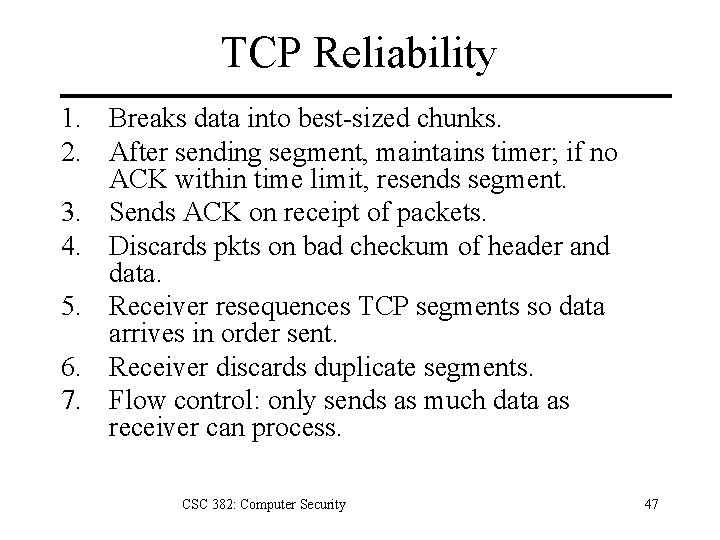
TCP Reliability 1. Breaks data into best-sized chunks. 2. After sending segment, maintains timer; if no ACK within time limit, resends segment. 3. Sends ACK on receipt of packets. 4. Discards pkts on bad checkum of header and data. 5. Receiver resequences TCP segments so data arrives in order sent. 6. Receiver discards duplicate segments. 7. Flow control: only sends as much data as receiver can process. CSC 382: Computer Security 47

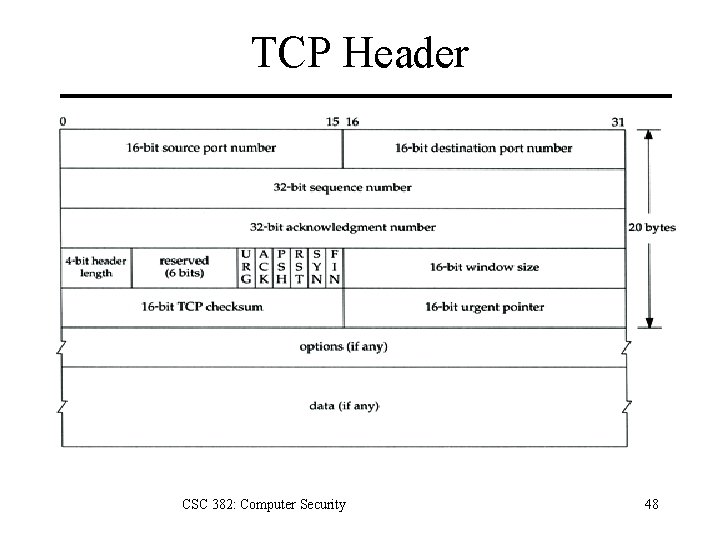
TCP Header CSC 382: Computer Security 48

TCP Header • Sequence Number: 32 -bit segment identifier. • Acknowledgment: next sequence number expected by sender of ACK – TCP is full duplex so both sides of connection have own set of sequence numbers • Header length: length of header in 32 -bit words (20 bytes default– 60 bytes w/ options) • Window size: number of bytes receiver is willing to accept (flow control) CSC 382: Computer Security 49

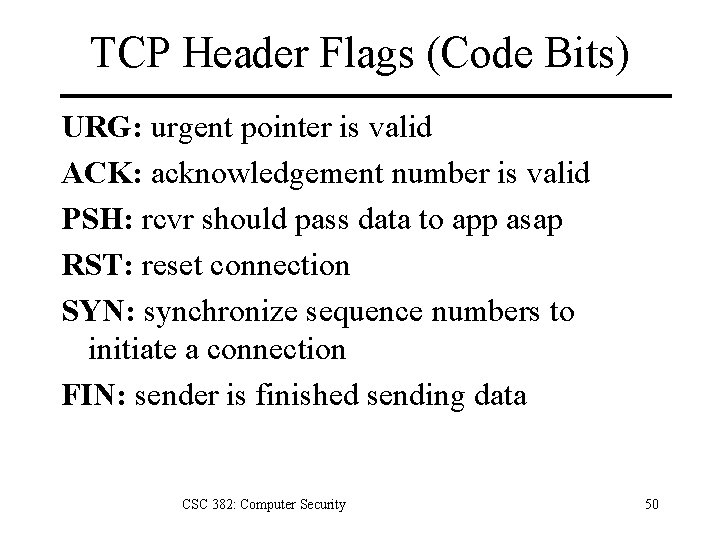
TCP Header Flags (Code Bits) URG: urgent pointer is valid ACK: acknowledgement number is valid PSH: rcvr should pass data to app asap RST: reset connection SYN: synchronize sequence numbers to initiate a connection FIN: sender is finished sending data CSC 382: Computer Security 50

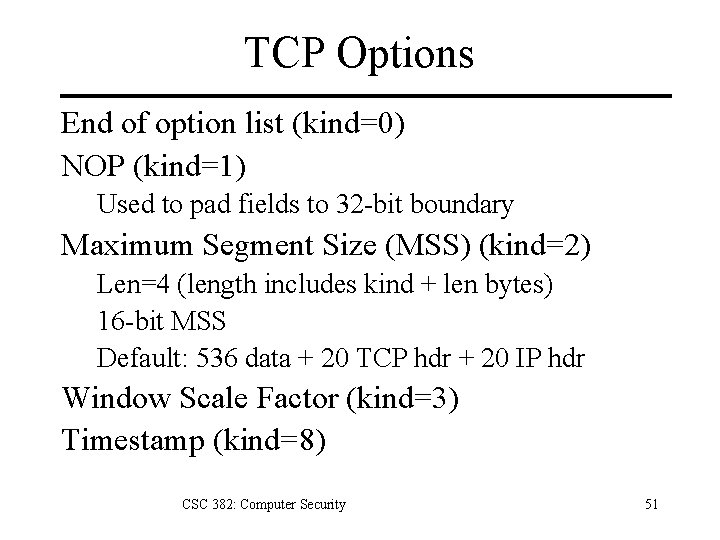
TCP Options End of option list (kind=0) NOP (kind=1) Used to pad fields to 32 -bit boundary Maximum Segment Size (MSS) (kind=2) Len=4 (length includes kind + len bytes) 16 -bit MSS Default: 536 data + 20 TCP hdr + 20 IP hdr Window Scale Factor (kind=3) Timestamp (kind=8) CSC 382: Computer Security 51

TCP Connections Establishment 3 -way handshake Connection Trace Termination Normal Termination Connection Trace Reset CSC 382: Computer Security 52

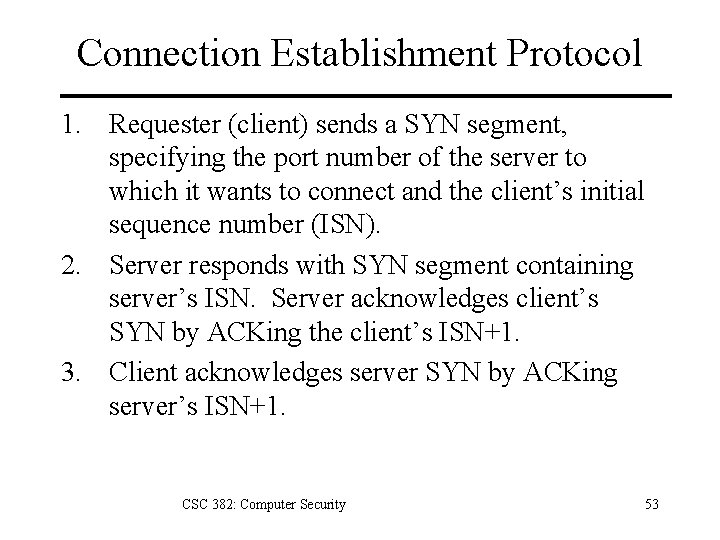
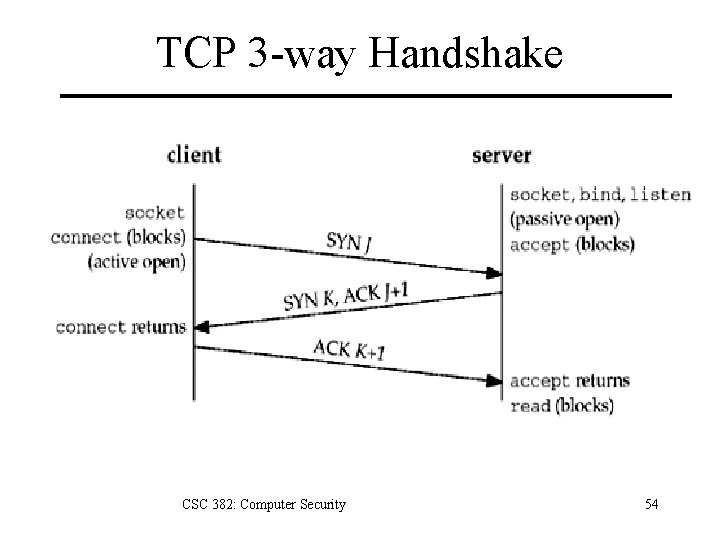
Connection Establishment Protocol 1. Requester (client) sends a SYN segment, specifying the port number of the server to which it wants to connect and the client’s initial sequence number (ISN). 2. Server responds with SYN segment containing server’s ISN. Server acknowledges client’s SYN by ACKing the client’s ISN+1. 3. Client acknowledges server SYN by ACKing server’s ISN+1. CSC 382: Computer Security 53

TCP 3 -way Handshake CSC 382: Computer Security 54

Connection Establishment Test at 204 m 02> /usr/sbin/snoop sun 09 at 204 m 02> nc sun 09 22 SSH-1. 99 -Open. SSH_3. 7. 1 p 2 ^C If no services running, start your own: at 204 m 02> nc -l -p 8192 CSC 382: Computer Security 55

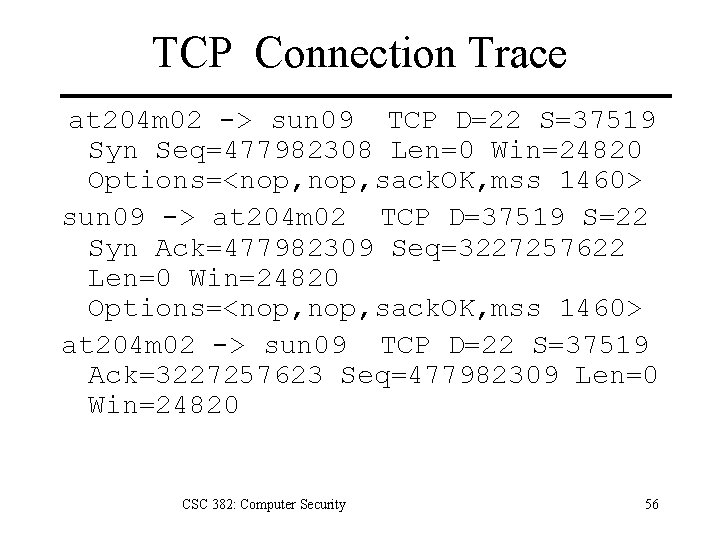
TCP Connection Trace at 204 m 02 -> sun 09 TCP D=22 S=37519 Syn Seq=477982308 Len=0 Win=24820 Options=<nop, sack. OK, mss 1460> sun 09 -> at 204 m 02 TCP D=37519 S=22 Syn Ack=477982309 Seq=3227257622 Len=0 Win=24820 Options=<nop, sack. OK, mss 1460> at 204 m 02 -> sun 09 TCP D=22 S=37519 Ack=3227257623 Seq=477982309 Len=0 Win=24820 CSC 382: Computer Security 56

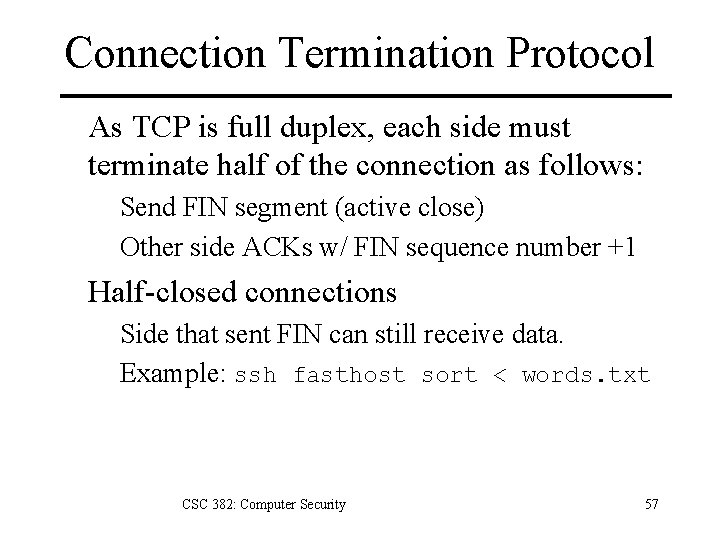
Connection Termination Protocol As TCP is full duplex, each side must terminate half of the connection as follows: Send FIN segment (active close) Other side ACKs w/ FIN sequence number +1 Half-closed connections Side that sent FIN can still receive data. Example: ssh fasthost sort < words. txt CSC 382: Computer Security 57

TCP Disconnection CSC 382: Computer Security 58

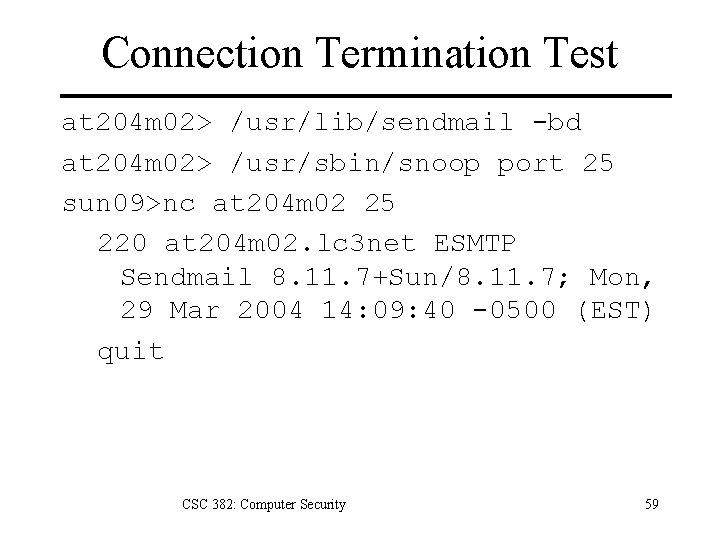
Connection Termination Test at 204 m 02> /usr/lib/sendmail -bd at 204 m 02> /usr/sbin/snoop port 25 sun 09>nc at 204 m 02 25 220 at 204 m 02. lc 3 net ESMTP Sendmail 8. 11. 7+Sun/8. 11. 7; Mon, 29 Mar 2004 14: 09: 40 -0500 (EST) quit CSC 382: Computer Security 59

TCP Disconnection Trace at 204 m 02 -> sun 09 TCP D=33042 S=25 Fin Ack=3597541820 Seq=872479258 Len=0 Win=24820 sun 09 -> at 204 m 02 TCP D=25 S=33042 Ack=872479259 Seq=3597541820 Len=0 Win=24820 sun 09 -> at 204 m 02 TCP D=25 S=33042 Fin Ack=872479259 Seq=3597541820 Len=0 Win=24820 at 204 m 02 -> sun 09 TCP D=33042 S=25 Ack=3597541821 Seq=872479259 Len=0 Win=24820 CSC 382: Computer Security 60

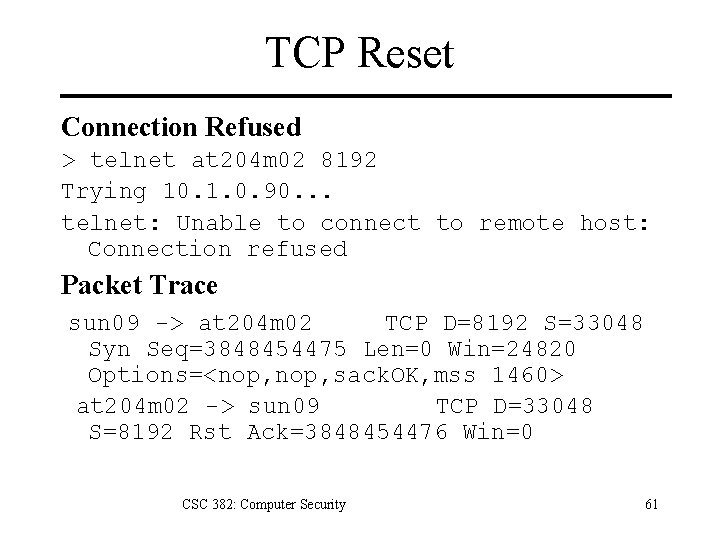
TCP Reset Connection Refused > telnet at 204 m 02 8192 Trying 10. 1. 0. 90. . . telnet: Unable to connect to remote host: Connection refused Packet Trace sun 09 -> at 204 m 02 TCP D=8192 S=33048 Syn Seq=3848454475 Len=0 Win=24820 Options=<nop, sack. OK, mss 1460> at 204 m 02 -> sun 09 TCP D=33048 S=8192 Rst Ack=3848454476 Win=0 CSC 382: Computer Security 61

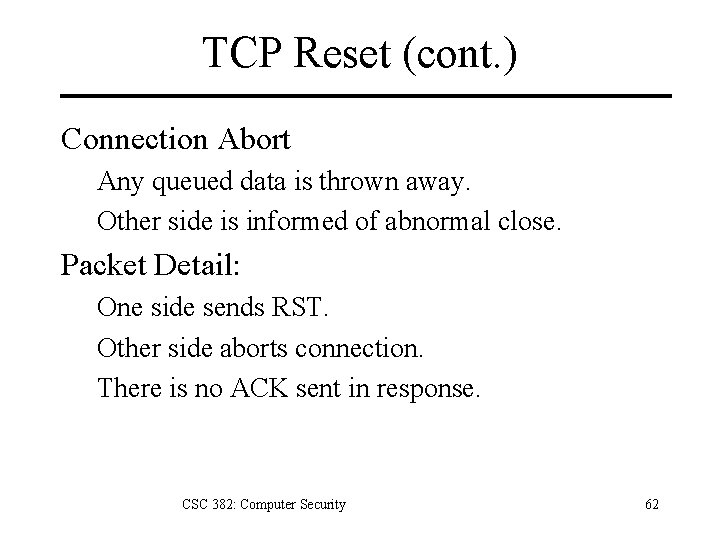
TCP Reset (cont. ) Connection Abort Any queued data is thrown away. Other side is informed of abnormal close. Packet Detail: One side sends RST. Other side aborts connection. There is no ACK sent in response. CSC 382: Computer Security 62

Half-Open Connections where one side has aborted or closed connection w/o knowledge of other. – Client or server host has crashed. – DOS attack: requester sends SYN, doesn’t respond to SYN+ACK. CSC 382: Computer Security 63

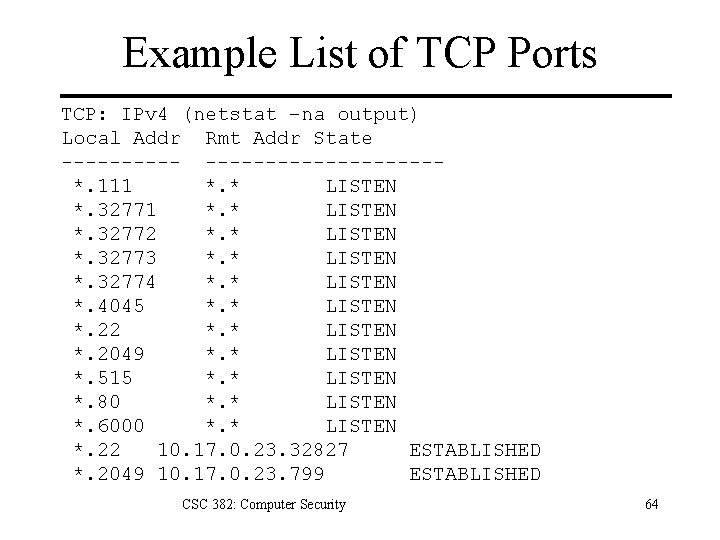
Example List of TCP Ports TCP: IPv 4 (netstat –na output) Local Addr Rmt Addr State ---------------*. 111 *. * LISTEN *. 32772 *. * LISTEN *. 32773 *. * LISTEN *. 32774 *. * LISTEN *. 4045 *. * LISTEN *. 22 *. * LISTEN *. 2049 *. * LISTEN *. 515 *. * LISTEN *. 80 *. * LISTEN *. 6000 *. * LISTEN *. 22 10. 17. 0. 23. 32827 ESTABLISHED *. 2049 10. 17. 0. 23. 799 ESTABLISHED CSC 382: Computer Security 64

TCP Servers Local Address *. 80 means that it will accept connections on any network interface on TCP port 80. Foreign Address *. * means that the server will accept connections from any source host and port. Conn=(src IP, src port, dst IP, dst port) All connections to same server will have same dst IP and port, but will have different source IPs and ports Kernel maintains queue of ~5 incoming connections for each server. CSC 382: Computer Security 65

Key Points 1. TCP/IP Layers: encapsulation/de-multiplexing 1. 2. 3. 4. Physical/Data Link: ethernet, PPP Network: IP, ICMP Transport: UDP, TCP Application: ftp, http, smtp, telnet, etc. 2. IP 1. Addressing: DNS/IP/MAC, netmasks, CIDR, NAT. 2. Routing: tables, hubs/switches/routers. 3. TCP 1. Connection and Termination: 3 -way handshake 2. Addressing: source and destination ports. CSC 382: Computer Security 66

References 1. 2. 3. 4. 5. 6. 7. 8. K. Egevang and P. Francis, “The IP Network Address Translator (NAT), ” RFC 1631, http: //www. ietf. org/rfc 1631. txt, 1994. J. B. Postel, “Internet Protocol, ” RFC 791, “http: //www. ietf. org/rfc 0791. txt, 1981. J. B. Postel, “Internet Control Message Protocol, ” RFC 792, “http: //www. ietf. org/rfc 0792. txt, 1981. J. B. Postel, “Transmission Control Protocol, ” RFC 793, http: //www. ietf. org/rfc 0793. txt, 1981. Ed Skoudis, Counter Hack, Prentice Hall, 2002. Richard Stevens, TCP/IP Illustrated, Vol. 1, Addison-Wesley, 1994. Richard Stevens, UNIX Network Programming, Vol. 1, Prentice. Hall, 1998. Andrew Tannenbaum, Computer Networks, 4 th edition, Prentice. Hall, 2002. CSC 382: Computer Security 67