CSC 382 Computer Security Threats CSC 382 Computer

















- Slides: 28

CSC 382: Computer Security Threats CSC 382: Computer Security 1

What are threats? • What threats can you think of to your home? • To your money (including bank accounts, checks, credit and debit cards)? • To your home computer? CSC 382: Computer Security 2

What are threats? • Home: • Computer: – Burglary – Fire – Vandalism • Money (cash/credit): – – Theft. Counterfeiting. Signature forgery. Identity theft. CSC 382: Computer Security – – – Viral/worm infection. Adware/spyware. Denial of service. Data destruction. Physical destruction (overheat, flash “ROM” overwriting) – Use of computer for felonious purposes. 3

Digital Threats: More of the Same • • Theft Vandalism Extortion Con Games Fraud Stalking Voyeurism CSC 382: Computer Security 4

Digital Threats: What’s Different Automation – Salami Attack from Office Space. Action at a Distance – Volodya Levin, from St. Petersburg, Russia, stole over $10 million from US Citibank. Arrested in London. – Operators of CA BBS tried and convicted in TN court because TN had d/led pornography f/ CA. Technique Propagation – Criminals share techniques rapidly and globally. CSC 382: Computer Security 5

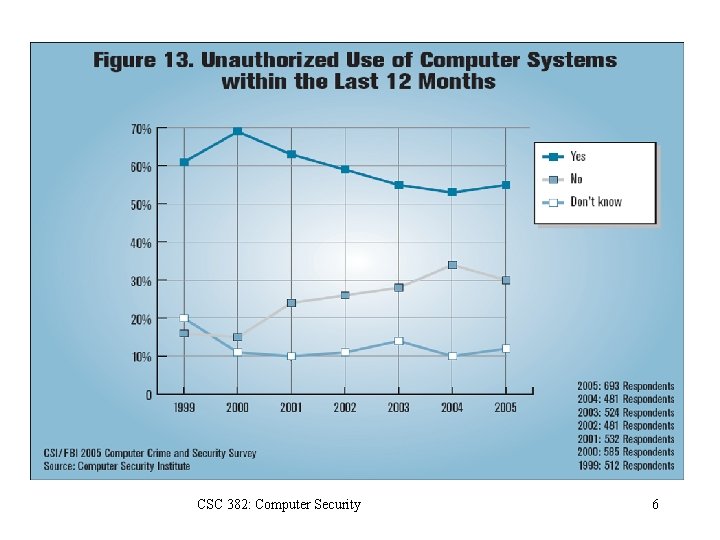
CSC 382: Computer Security 6

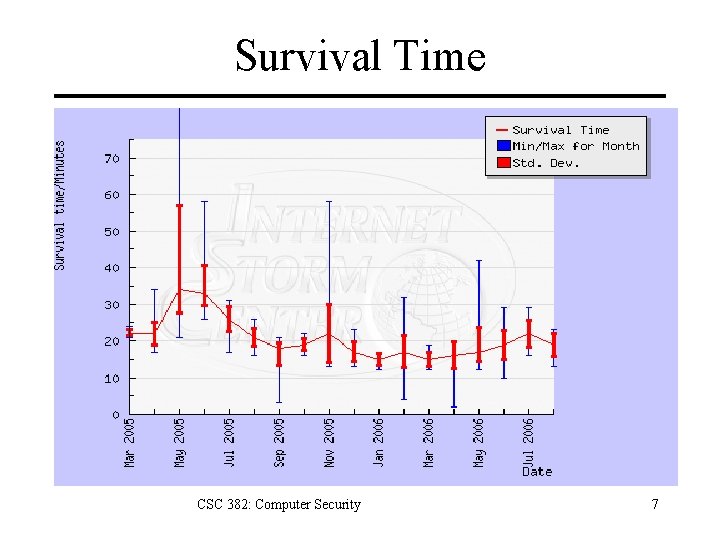
Survival Time CSC 382: Computer Security 7

Current Threat Information • • • SANS Internet Storm Center Bugtraq CERT Packet Storm Risks Digest CSC 382: Computer Security 8

Who are the Attackers? • Hackers vs Crackers • Levels of attackers – Developer • Finds new security vulnerabilities • Writes tools and exploits – User • Understands tools; modifies tools/exploits – Script Kiddie CSC 382: Computer Security 9

Who are the Attackers? • Criminals. – 1993: Thieves installed bogus ATM at Manchester Mall. Saved account#s + PINs. • Organized crime. – 2000: Mafia-led organization members arrested for attempt to steal $680 million from Bank of Sicily. • Malicious insiders. – 2001: Mike Ventimiglia deletes files of his employer, GTE. $200, 000 damage. • Industrial espionage. – 2001: Verdicts in Cadence Design Systems vs. Avant against 7 employees incl CEO. 5 sentenced to jail. CSC 382: Computer Security 10

Who are the Attackers? • Press. – 1998: Cincinnati Enquirer reporter Michael Gallagher breaks into Chiquita Fruits voicemail to expose illegal activities. • Police. – 1997: LAPD illegal wiretapping scandal. • Terrorists. – 1999: DOS attacks and web defacements against NATO country computers during Kosovo bombings. • National Intelligence. – 2000: Former CIA Directory Woolsey admitted to using ECHELON information to help US companies win foreign contracts. CSC 382: Computer Security 11

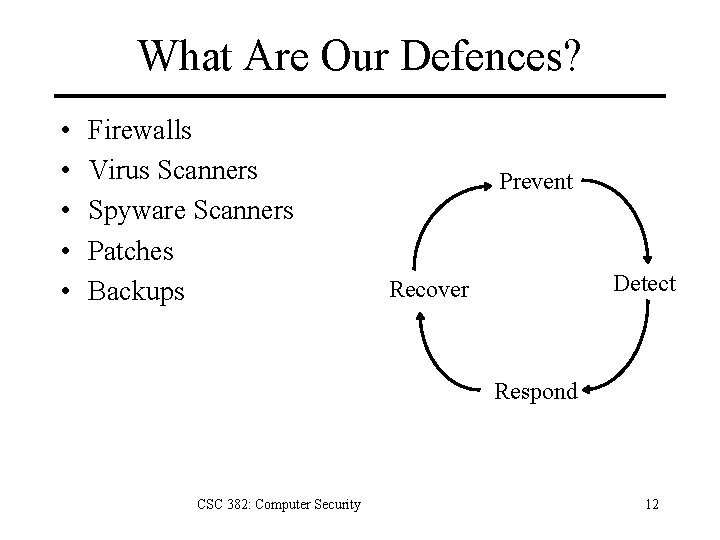
What Are Our Defences? • • • Firewalls Virus Scanners Spyware Scanners Patches Backups Prevent Detect Recover Respond CSC 382: Computer Security 12

What Are The Attacks? • • • Phishing Malware Ransomware Spyware Botnets CSC 382: Computer Security 13

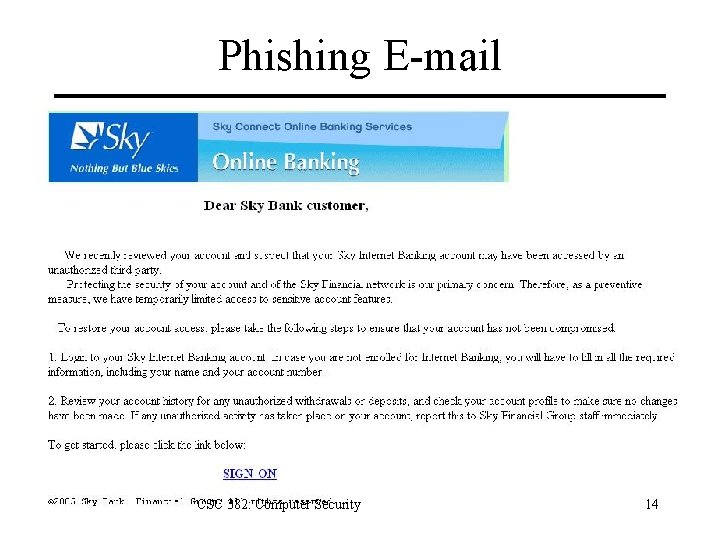
Phishing E-mail CSC 382: Computer Security 14

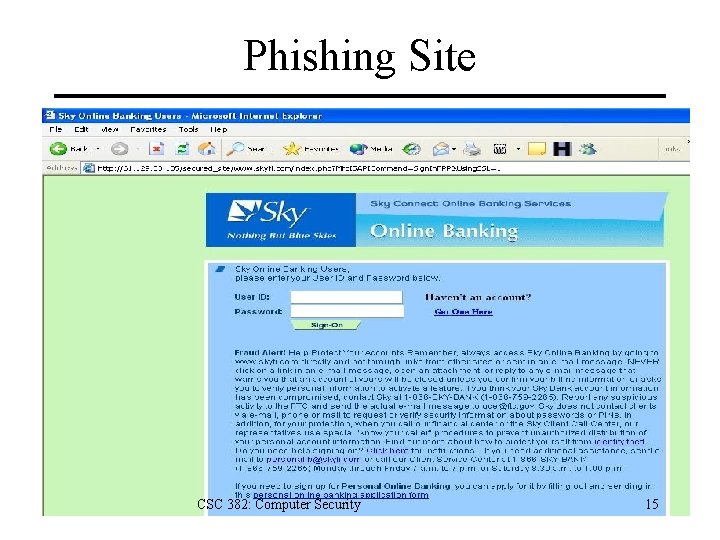
Phishing Site CSC 382: Computer Security 15

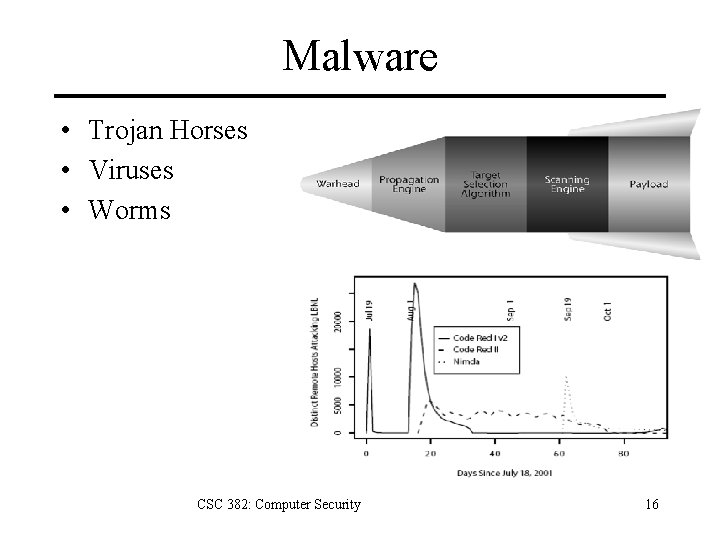
Malware • Trojan Horses • Viruses • Worms CSC 382: Computer Security 16

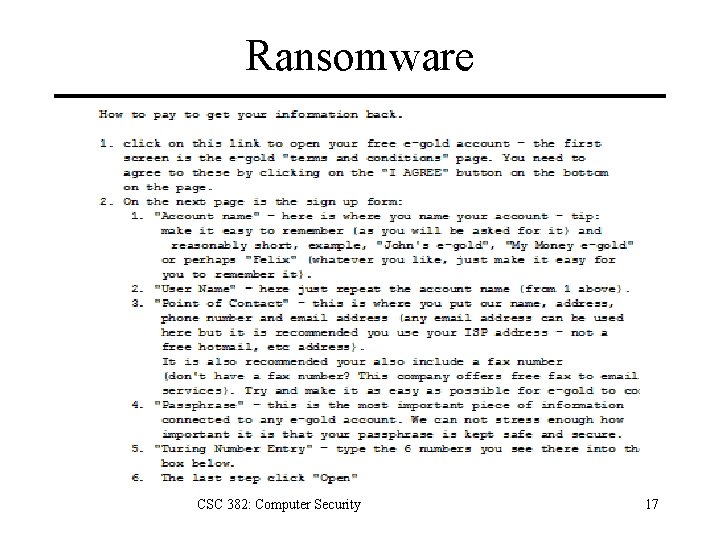
Ransomware CSC 382: Computer Security 17

Spyware and Adware Most Trojan Horses, some infect directly. – Browser hijacking – Pop-up advertisements – Keystroke and network logging – Steal confidential data from email and files 80% of PCs are infected with spyware (Oct 2004 AOL/NCSA survey. ) CSC 382: Computer Security 18

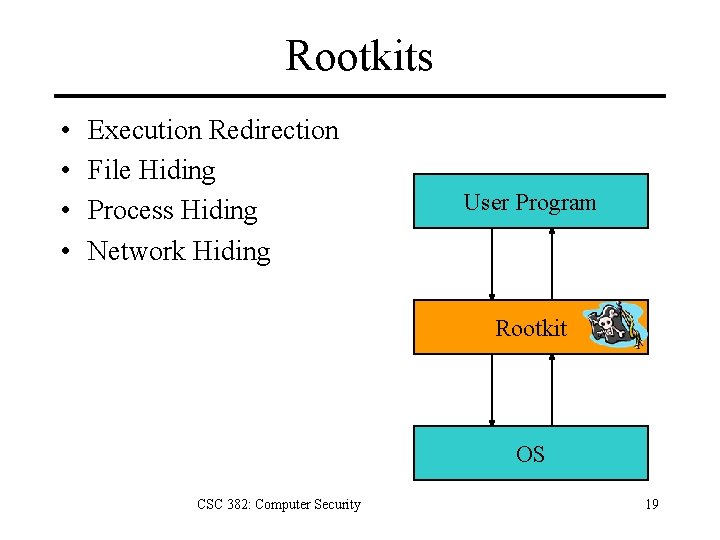
Rootkits • • Execution Redirection File Hiding Process Hiding Network Hiding User Program Rootkit OS CSC 382: Computer Security 19

Botnets Worm or direct attack usurps control of PC, then installs control software to listen for instructions. Instructions can include: • • • Attempt to infect other PCs Send spam message Launch DOS attack Upgrade attack and control software Virus writers sell botnets to spammers for $0. 10/compromised PC CSC 382: Computer Security 20

Future of Attacks • • • VM Rootkits Mobile Malware Gone in 20 Minutes RFID Viruses Virtual Property Theft CSC 382: Computer Security 21

Key Points • Computer crimes same as pre-computer crimes. • Differences in digital threats – Automation – Action at a distance – Technique propagation • Digital threats – – – Phishing Malware Ransomware Spyware Botnets CSC 382: Computer Security 22

References 1. 2. 3. 4. 5. 6. 7. 8. 9. 10. 11. Alexander Gostev et. al. , “Malware Evolution: January – March 2006, ” Virus List, http: //www. viruslist. com/en/analysis? pubid=184012401, April 12, 2006. The Honeynet Project, Know Your Enemy, 2 nd edition, Addison-Wesley, 2004. John Leyden, "The illicit trade in compromised PCs, " The Register, Apr 30 2004. Stuart Mc. Clure, Joel Scambray, and George Kurtz, Hacking Exposed, 5 th edition, Mc. Graw-Hill, 2005. Rachna Dhamija and J. D. Tygar, "The Battle Against Phishing: Dynamic Security Skins, " Proceedings of the Symposium on Usable Privacy and Security (SOUPS), July 2005. SANS Internet Storm Center, http: //isc. sans. org/survivalhistory. php Schneier, Bruce, Beyond Fear, Copernicus Books, 2003. Ed Skoudis, Counter Hack Reloaded, Prentice Hall, 2006 Stuart Staniford, Vern Paxson, and Nicholas Weaver, "How to 0 wn the Internet in Your Spare Time, " Proceedings of the 11 th USENIX Security Symposium, 2002. Richard Stiennon, "Spyware: 2004 Was Only the Beginning, " CIO Update, Jan 26 2005. Thompson, Ken, “Reflections on Trusting Trust”, Communication of the ACM, Vol. 27, No. 8, August 1984, pp. 761 -763 (http: //www. acm. org/classics/sep 95/) CSC 382: Computer Security 23

Extra Slides CSC 382: Computer Security 24

Classes of Threats • Disclosure – unauthorized access to data – Examples • copyright infringement • unauthorized CC use • Deception – acceptance of false data – Examples • Anti-spam filter techniques • “Social engineering” CSC 382: Computer Security 25

Classes of Threats • Disruption – interruption of correct system operation – Examples: • DDOS attacks • Usurpation – unauthorized control of system component – Example: Nicholas Jacobsen • Controlled T-mobile’s systems in 2004 • Monitored e-mail, downloaded web-cam photos • Sold customer records (incl SSN, voicemail pw, etc) CSC 382: Computer Security 26

Types of Threats • Snooping – interception of data – Examples: • Reading email, or intercepting cleartext passwords. • ECHELON. • Modification – Examples: • Changing student grades in War Games. • Web site defacing (>1500/month recorded at attrition. org in 2001) • Spoofing – impersonation – Examples: • Spam emails almost always spoof source address. • The many Citibank phishing scams. CSC 382: Computer Security 27

Types of Threats • Repudiation of Origin – Deny ordering goods. • Denial of Receipt – Deny receipt of payment or goods. – Examples • e. Bay • Credit card payments. • Denial of Service – Examples: • 2000: “Mafiaboy” DDOS takes down Amazon, e. Bay, Yahoo. • Filling up disk with spam, unauthorized copies of files. CSC 382: Computer Security 28