Successfully Implementing Information Systems Analysis and Design Learning









































- Slides: 61

Successfully Implementing Information Systems Analysis and Design

Learning Objectives o Comprehend the implementation of a variety of o o distributed systems Design appropriate training programs for users of the new system Recognize the differences in physical conversion strategies and be able to recommend an appropriate one to a client Address security, disaster preparedness, and disaster recovery Understand the importance of evaluating the new system, and be able to recommend a suitable evaluation technique to a client 2

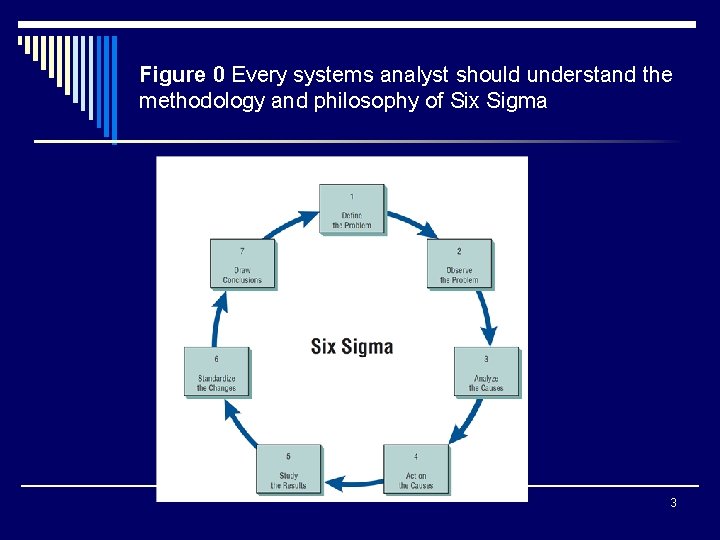
Figure 0 Every systems analyst should understand the methodology and philosophy of Six Sigma 3

Implementation o The process of ensuring that the information system is operational and then allowing users to take over its operation for use and evaluation o Implementation considerations: n n Distributing processing Training users Converting from the old system Evaluating the new system 4

Major Topics o Client/server computing o Network types o Groupware o Training o Security o Organizational metaphors o Evaluation 5

Implementing Distributed Systems o Can be conceived of as an application of telecommunications n n Includes work stations that can communicate with each other and with data processors May have different hierarchical architectural configurations of data processors that communicate with each other 6

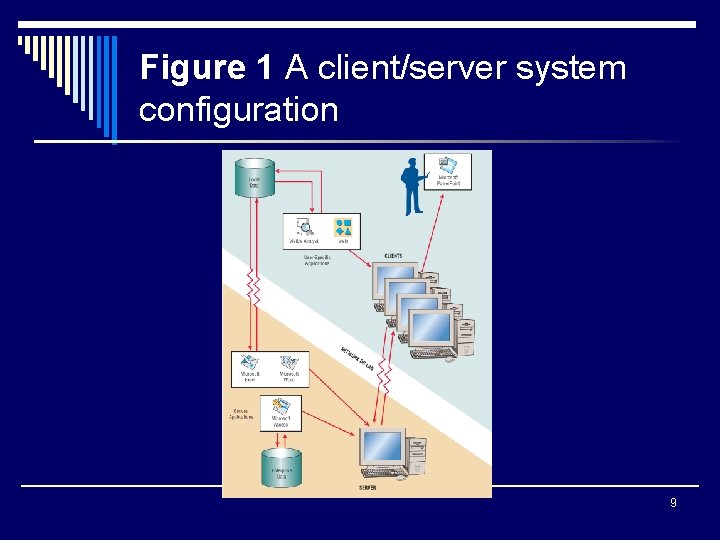
Client/Server Technology o The client/server (C/S) model refers to a design model that can be thought of as applications running on a local area network (LAN) o The client is a networked computer that uses small programs to do front-end processing, including communicating with the user o A file server stores the application programs and data for all the clients on the network o A print server is a PC dedicated to receiving and storing files to be printed 7

Advantages and Disadvantages of C/S Model o Advantage - greater computer power and greater opportunity to customize applications o Disadvantage - more expensive and applications must be written as two separate software components each running on separate machines 8

Figure 1 A client/server system configuration 9

Network Types Wide area network (WAN) Local area network (LAN) 10

Wireless Local Area Network (WLAN) o Called Wi-Fi or 802. 11, wireless fidelity o Can include encryption wired equivalent privacy (WEP) for security purposes o Comparatively cheap to set up o Serve as a flexible technology for supporting work groups 11

Wireless Local Area Network (WLAN) (Continued) o Concerns n n n Security Signal integrity WEP has many flaws, but used in conjunction with traditional LAN security measures is thought to be adequate for many home and business purposes 12

Wi. Max o Worldwide Interoperability for Microwave Access o Also known as “Mobile Wi. Max” o Greater wireless access range (30 miles) 13

Bluetooth o Suitable for personal networks and can include computers, printers, handheld devices, phones, keyboards, mice and household appliances 14

Types of Distributed Systems Networks o Hierarchical o Star o Ring o Bus 15

Hierarchical o The host controls all other nodes o Computers on the same level do not communicate with each other 16

Star o The central node communicates with the lesser nodes o The lesser nodes cannot directly communicate with each other 17

Ring o There is no central computer o All the nodes are of equal computing power o Each node communicates directly with its neighbour 18

Bus o Work well in close quarters o A single central cable is used to connect all the devices o The single central cable serves as the only communication path 19

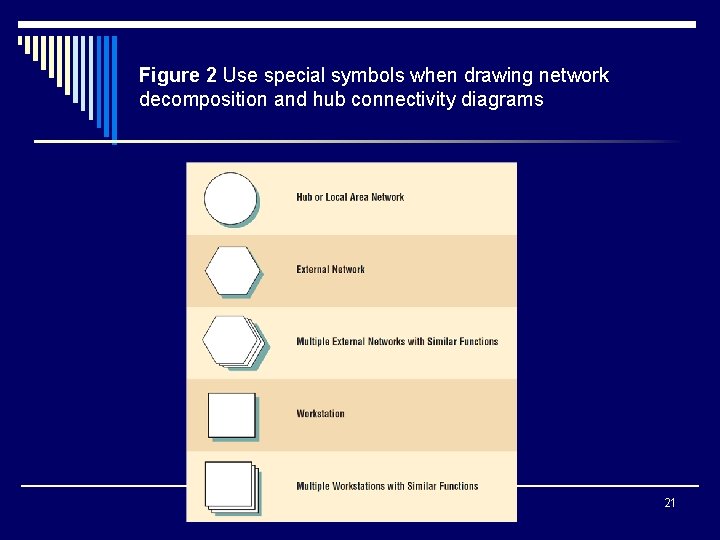
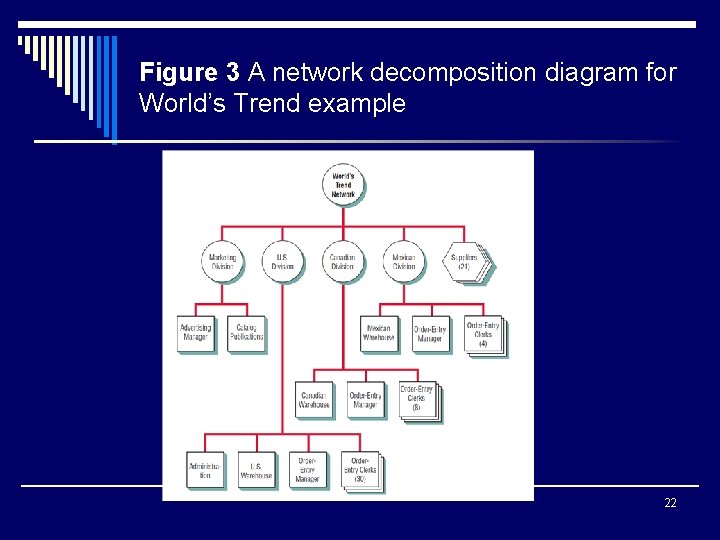
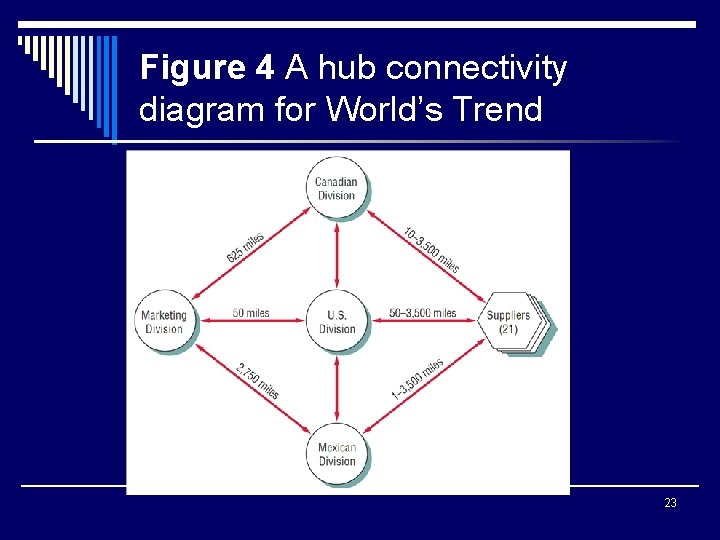
Network Modelling o Draw a network decomposition diagram to provide an overview of the system o Draw a hub connectivity diagram o Explode the hub connectivity diagram to show the various workstations and how they are connected 20

Figure 2 Use special symbols when drawing network decomposition and hub connectivity diagrams 21

Figure 3 A network decomposition diagram for World’s Trend example 22

Figure 4 A hub connectivity diagram for World’s Trend 23

Figure 5 A workstation connectivity diagram for World’s Trend 24

Groupware o Software that supports people working together in an organization o Can help group members to schedule and attend meetings, share data, create and analyze documents, communicate in unstructured ways, hold group conferences, do image management, manage and monitor workflow 25

Figure 8 There are five main advantages to creating distributed systems 26

Figure 9 There are four main disadvantages to creating distributed systems 27

Training o Who to train o People who train users o Training objectives o Training methods o Training sites o Training materials 28

Who to Train o All people who will have primary or secondary use of the system o Ensure that users of different skill levels and job interests are separated 29

People Who Train Users o Vendors o Systems analysts o External paid trainers o In-house trainers o Other system users 30

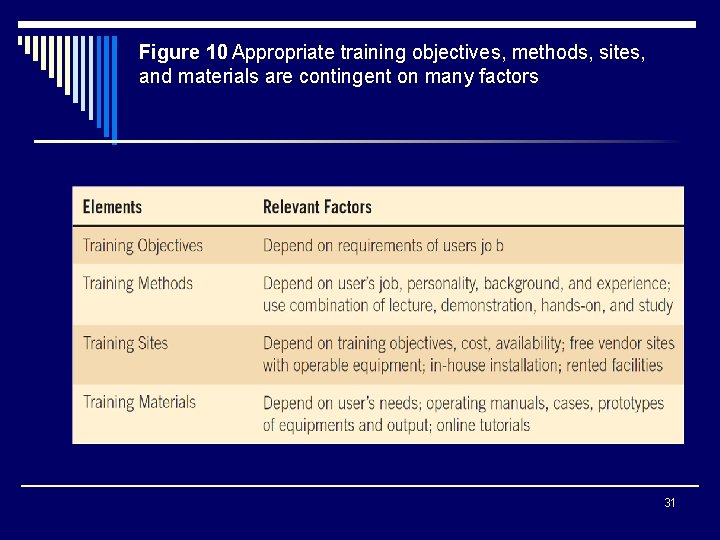
Figure 10 Appropriate training objectives, methods, sites, and materials are contingent on many factors 31

Conversion Strategies o Direct changeover o Parallel conversion o Gradual or Phased conversion o Modular prototype conversion o Distributed conversion 32

Figure 11 Five conversion strategies for information systems 33

Direct Changeover o Advantage n Users have no possibility of using the old system rather than the new one o Disadvantage n Long delays might ensue if errors occur n Users resent being forced into using an unfamiliar system without recourse n No adequate way to compare new results to old 34

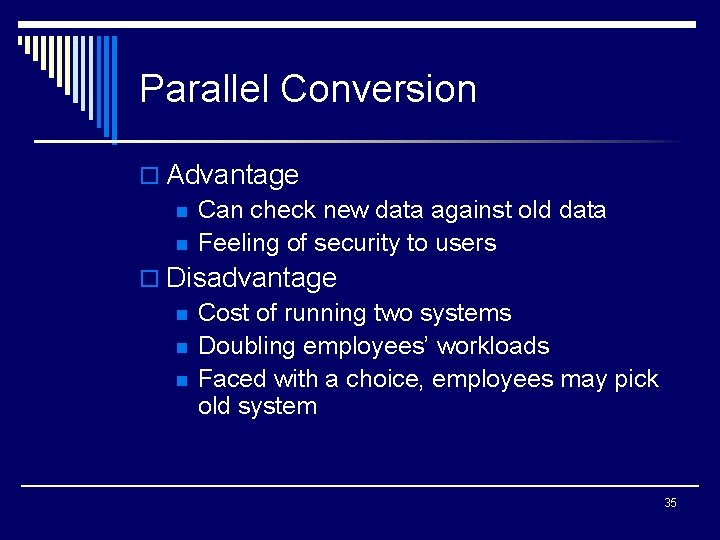
Parallel Conversion o Advantage n Can check new data against old data n Feeling of security to users o Disadvantage n Cost of running two systems n Doubling employees’ workloads n Faced with a choice, employees may pick old system 35

Gradual Conversion o Advantage n Allows users to get involved with the system gradually o Disadvantage n n Taking too long to get the new system in place Inappropriateness for conversion of small, uncomplicated systems 36

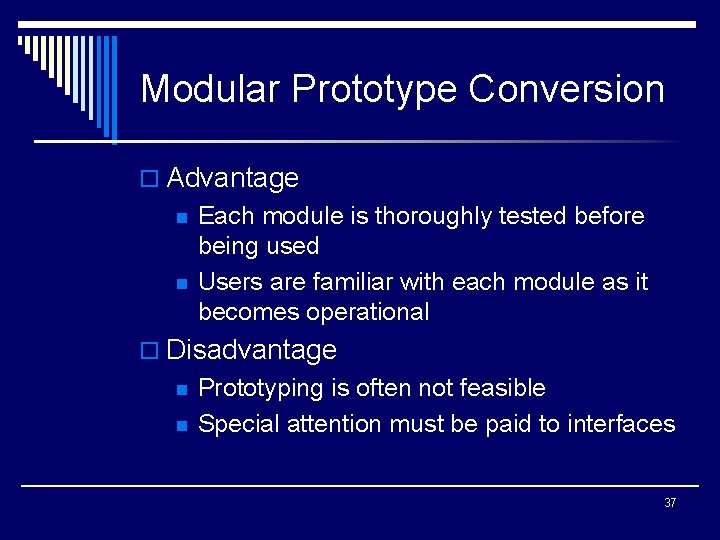
Modular Prototype Conversion o Advantage n n Each module is thoroughly tested before being used Users are familiar with each module as it becomes operational o Disadvantage n n Prototyping is often not feasible Special attention must be paid to interfaces 37

Distributed Conversion o Advantage n Problems can be detected and contained o Disadvantage n Even when one conversion is successful, each site will have its own peculiarities to work through 38

Security Concerns o Physical security o Logical security o Behavioural security 39

Security Concerns (Continued) o Physical security is securing the computer facility, its equipment, and software through physical means o Logical security refers to logical controls in the software itself o Behavioural security is building and enforcing procedures to prevent the misusing of computer hardware and software 40

Special Security Considerations for Ecommerce o Virus protection software o Email filtering products o URL filtering products o Firewalls, gateways, and virtual private networks o Intrusion detection products 41

Special Security Considerations for Ecommerce (Continued) o Vulnerability management products o Security technologies such as secure socket layering (SSL) for authentication o Encryption technologies o Public key infrastructure (PKI) use and obtaining a digital certificate 42

Privacy Considerations for Ecommerce o Start with a corporate policy on privacy o Only ask for information required to complete the transaction o Make it optional for customers to fill out personal information on the Web site 43

Privacy Considerations for Ecommerce (Continued) o Use sources that allow you to obtain anonymous information about classes of customers o Be ethical 44

Disaster Recovery Planning o Identify teams responsible for managing a crisis o Eliminate single points of failure o Determine data replication technologies that match the organization’s timetable o Create detailed relocation and transportation plans 45

Disaster Recovery Planning (Continued) o Provide recovery solutions that include an off-site location o Ensure the physical and psychological well-being of employees and others 46

Identify Who Is Responsible o Whether business operations will continue o How to support communications o Where people will be sent if the business is uninhabitable o Where personnel will go in an emergency o Seeing to the personal and psychological needs o Restoring the main computing and working environments 47

Single Points of Failure and Data Replication Technologies o Redundancy of data provides the key for servers running Web applications o SNAs and data mirroring 48

Relocation and Transportation Plans o Send employees home o Remain on site o Relocate to a recovery facility 49

Communication Channels o Email o Emergency information Web page o Emergency hotline o Emergency response agencies 50

Recovery Solutions and Support for the Well-Being of Employees o Recovery involves an off-site location and converting paper documents to digital formats o Well-being of employees might include providing water or safety kits 51

Other Conversion Considerations o Ordering equipment o Ordering any external materials supplied to the information system o Appointing a manager to supervise the preparation of the installation site o Planning, scheduling, and supervising programmers and data entry personnel 52

Figure 12 Organizational metaphors may contribute to the success or failure of an information system 53

Evaluation Techniques o Cost-benefit analysis o Revised decision evaluation approach o User involvement evaluations o The information system utility approach 54

Information System Utility Approach o Possession o Form o Place o Time o Actualization o Goal 55

Information System Utility Approach (Continued) o Possession utility answers the question of who should receive output o Goal utility answers the why of information systems by asking whether the output has value in helping the organization achieve its objectives o Place utility answers the question of where information is distributed 56

Information System Utility Approach (Continued) o Form utility answers the question of what kind of output is distributed to the decision maker o Time utility answers the question of when information is delivered o Actualization utility involves how the information is introduced and used by the decision maker 57

Web Site Evaluation o Know how often the Web site is visited o Learn details about specific pages on the site o Find out more about the Web site’s visitors 58

Web Site Evaluation (Continued) o Discover if visitors can properly fill out the forms you designed o Find out who is referring Web site visitors to the client’s site o Determine what browsers visitors are using o Find out if the client’s Web site visitors are interested in advertising 59

Summary o Implementation o Distributed systems n Client/server o Training users and personnel o Conversion n Direct changeover n Parallel n Phased n Gradual n Modular prototype 60

Summary (Continued) o Security n n n Physical Logical Behavioural o Organizational metaphors o Evaluation 61