MANAGEMENT of INFORMATION SECURITY Fifth Edition DISASTER RECOVERY























- Slides: 29

MANAGEMENT of INFORMATION SECURITY, Fifth Edition

DISASTER RECOVERY Management of Information Security, 5 th Edition, © Cengage Learning 2

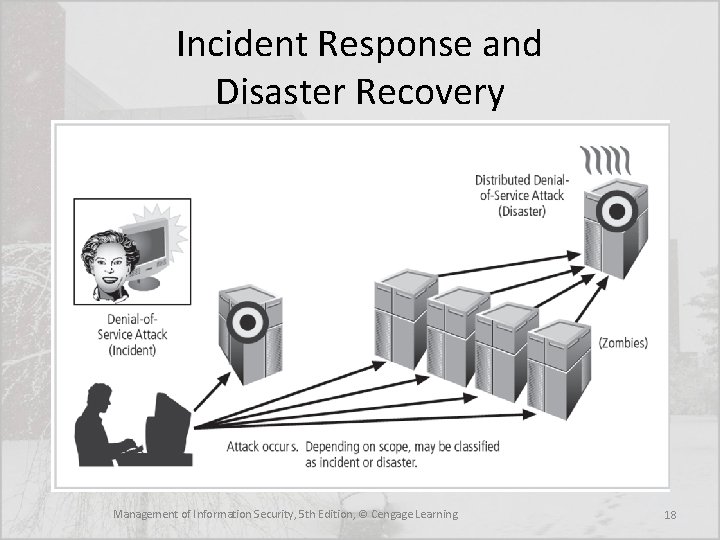
Disaster Recovery • Disaster recovery planning (DRP) entails preparation for and recovery from a disaster, whether natural or man-made • In general, an incident is a disaster when: – the organization is unable to contain or control the impact of an incident, or – the level of damage or destruction from an incident is so severe the organization is unable to quickly recover. • The key role of a DR Plan is defining how to reestablish operations at the location where the organization is usually located (primary site) Management of Information Security, 5 th Edition, © Cengage Learning 3

Disaster Recovery • As you learned earlier, the CP team creates the DR planning team (DRPT) • The DRPT in turn organizes and prepares the DR response teams (DRRTs) to actually implement the DR plan in the event of a disaster • These teams may have multiple responsibilities in the recovery of the primary site and the reestablishment of operations: – Recover information assets that are salvageable from the primary facility after the disaster – Purchase or otherwise acquire replacement information assets from appropriate sources – Reestablish functional information assets at the primary site if possible or at a new primary site, if necessary Management of Information Security, 5 th Edition, © Cengage Learning 4

Disaster Recovery Response Teams • DR Management • Communications • Computer Recovery (Hardware) Team • Systems Recovery (OS) • Network Recovery Team • Storage Recovery • Applications Recovery • Data Management • Vendor Contact • Damage Assessment and Salvage • Business Interface • Logistics • Others as needed. Management of Information Security, 5 th Edition, © Cengage Learning 5

Disaster Recovery Process • The NIST methodology can be adapted for DRP: 1. 2. 3. 4. 5. 6. 7. 8. Organize the DR team Develop the DR planning policy statement Review the BIA Identify preventive controls Create DR strategies Develop the DR plan document Ensure DR Plan testing, training, and exercises Ensure DR Plan maintenance Management of Information Security, 5 th Edition, © Cengage Learning 6

Disaster Recovery Policy • The DR team, led by the manager designated as the DR team leader, begins with the development of the DR policy soon after the team is formed • The policy presents an overview of the organization’s philosophy on the conduct of DR operations and serves as the guide for the development of the DR plan • The DR policy itself may have been created by the organization’s CP team or the DR team may be assigned the role of developing the DR policy Management of Information Security, 5 th Edition, © Cengage Learning 7

Disaster Recovery Policy (cont. ) • In either case, the DR policy contains the following key elements: – Purpose – Scope – Roles and responsibilities – Resource requirements – Training requirements – Exercise and testing schedules – Plan maintenance schedule – Special considerations Management of Information Security, 5 th Edition, © Cengage Learning 8

Disaster Classifications • A DR Plan classify disasters in a number of ways: – Natural disasters – Man-made disasters • By speed of development – Rapid onset disasters – Slow onset disasters Management of Information Security, 5 th Edition, © Cengage Learning 9

Natural Disasters • • • Fire Flood Earthquake Lightning Landslide or mudslide Tornado or severe windstorm • Hurricane or typhoon • Tsunami • Electrostatic discharge (ESD) • Dust contamination Management of Information Security, 5 th Edition, © Cengage Learning 10

Planning to Recover • Scenario development and impact analysis are used to categorize the level of threat of each potential disaster • When generating a DR scenario, start with the most important asset: people • Key points in the DR plan: – Clear delegation of roles and responsibilities – Execution of the alert roster and notification of key personnel – Clear establishment of priorities – Documentation of the disaster – Action steps to mitigate the impact – Alternative implementations for the various systems components Management of Information Security, 5 th Edition, © Cengage Learning 11

Simple DR Plan Elements 1. Name of agency 2. Date of completion or update of the plan and the date of the most recent test. 3. Agency staff to be called in the event of a disaster 4. Emergency services to be called (if needed) in event of a disaster 5. Locations of in-house emergency equipment and supplies 6. Sources of off-site equipment and supplies 7. Salvage priority list 8. Agency disaster recovery procedures 9. Follow-up assessment Management of Information Security, 5 th Edition, © Cengage Learning 12

BUSINESS CONTINUITY Management of Information Security, 5 th Edition, © Cengage Learning 13

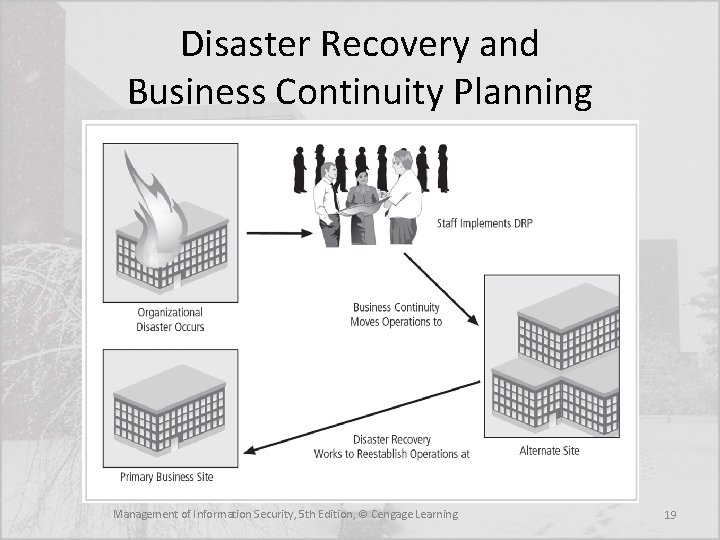
Business Continuity Planning (BCP) • Sometimes, disasters have such a profound effect on the organization that it cannot continue operations at its primary site until it fully completes all DR efforts, which requires business continuity (BC) strategies • BCP ensures critical business functions can continue in a disaster, and is most likely managed by the CEO or COO of the organization • BCP is activated and executed concurrently with the DRP when needed • While BCP reestablishes critical functions at alternate site, DRP focuses on reestablishment at the primary site Management of Information Security, 5 th Edition, © Cengage Learning 14

Business Continuity • The NIST methodology can also be adapted to BC: 1. 2. 3. 4. 5. 6. 7. 8. Form the BC Team Develop the BC planning policy statement Review the BIA Identify preventive controls Create relocation strategies Develop the BC plan Ensure BC plan testing, training and exercises Ensure BC plan Maintenance Management of Information Security, 5 th Edition, © Cengage Learning 15

Business Continuity Policy • • Purpose Scope Roles and responsibilities Resource requirements Training requirements Exercise and testing schedules Plan maintenance schedule Special considerations Management of Information Security, 5 th Edition, © Cengage Learning 16

Continuity Strategies • Several continuity strategies for business continuity, determining factor is usually cost • Three exclusive-use options: – hot sites – warm sites – cold sites • Three shared-use options: – timeshare – service bureaus – mutual agreements • Specialized options: – Rolling mobile site – Externally stored (prepositioned) resources Management of Information Security, 5 th Edition, © Cengage Learning 17

Incident Response and Disaster Recovery Management of Information Security, 5 th Edition, © Cengage Learning 18

Disaster Recovery and Business Continuity Planning Management of Information Security, 5 th Edition, © Cengage Learning 19

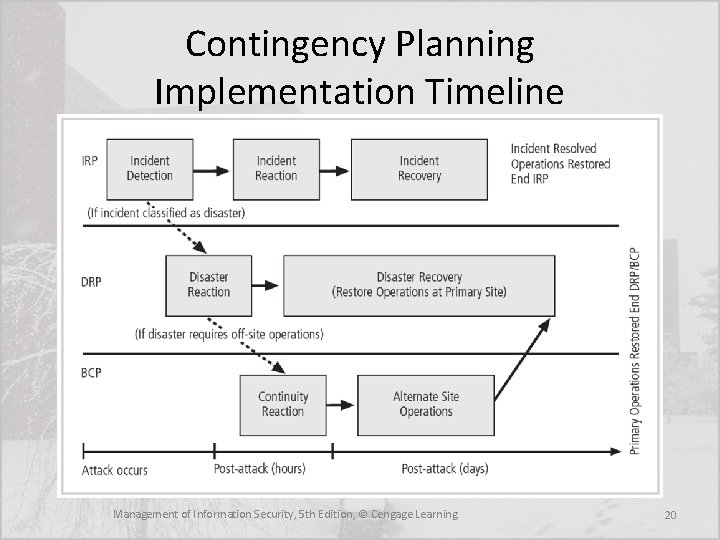
Contingency Planning Implementation Timeline Management of Information Security, 5 th Edition, © Cengage Learning 20

CRISIS MANAGEMENT Management of Information Security, 5 th Edition, © Cengage Learning 21

Crisis Management • Another process that many organizations plan for separately is crisis management (CM), which focuses more on the effects that a disaster has on people than its effects on information assets • While some organizations include crisis management as a subset of the DR plan, the protection of human life and the organization’s image is such a high priority that it may deserve its own committee, policy, and plan Management of Information Security, 5 th Edition, © Cengage Learning 22

Crisis Management • According to Gartner Research, the crisis management team is responsible for managing the event from an enterprise perspective and performs the following roles: – Supporting personnel and their loved ones during the crisis – Keeping the public informed about the event and the actions being taken to ensure the recovery of personnel and the enterprise – Communicating with major customers, suppliers, partners, regulatory agencies, industry organizations, the media, and other interested parties Management of Information Security, 5 th Edition, © Cengage Learning 23

Crisis Management • The crisis management planning team (CMPT) should establish a base of operations or command center near the site of the disaster as soon as possible • The CMPT should include individuals from all functional areas of the organization in order to facilitate communications and cooperation • The CMPT is charged with three primary responsibilities: 1. Verifying personnel status 2. Activating the alert roster 3. Coordinating with emergency services Management of Information Security, 5 th Edition, © Cengage Learning 24

BUSINESS RESUMPTION Management of Information Security, 5 th Edition, © Cengage Learning 25

Business Resumption Planning • Because the DR and BC plans are closely related, most organizations merge the two functions into a single function called business resumption planning (BRP) • Such a comprehensive plan must be able to support the reestablishment of operations at two different locations—one immediately at an alternate site and one eventually back at the primary site Management of Information Security, 5 th Edition, © Cengage Learning 26

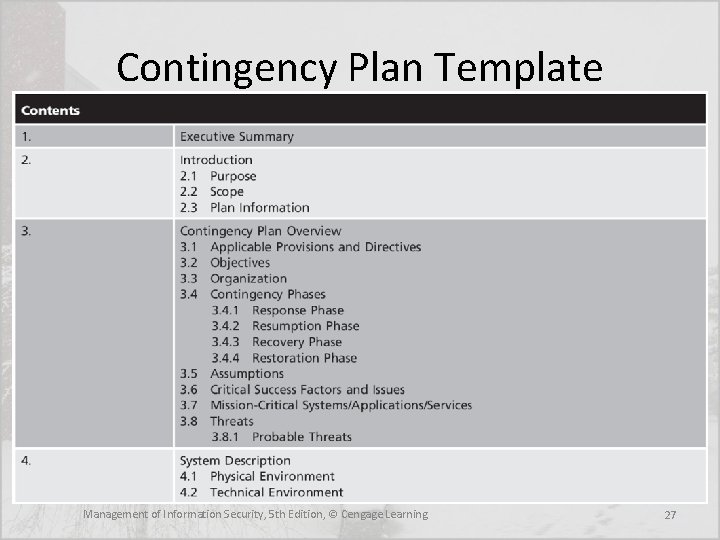
Contingency Plan Template Management of Information Security, 5 th Edition, © Cengage Learning 27

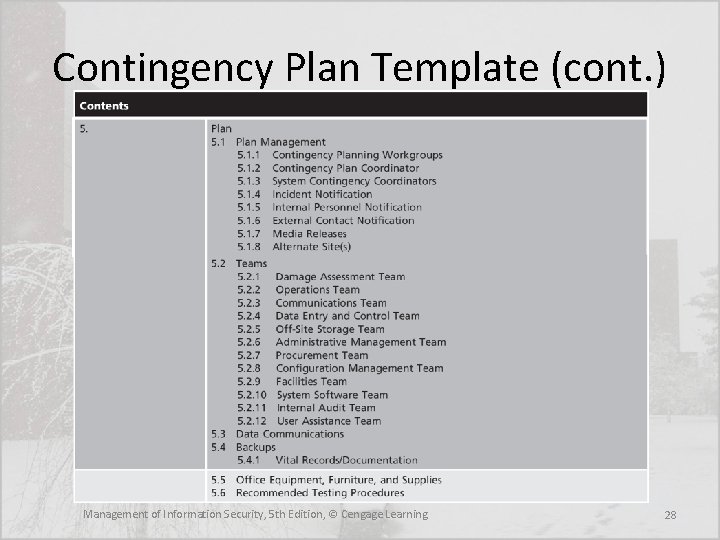
Contingency Plan Template (cont. ) Management of Information Security, 5 th Edition, © Cengage Learning 28

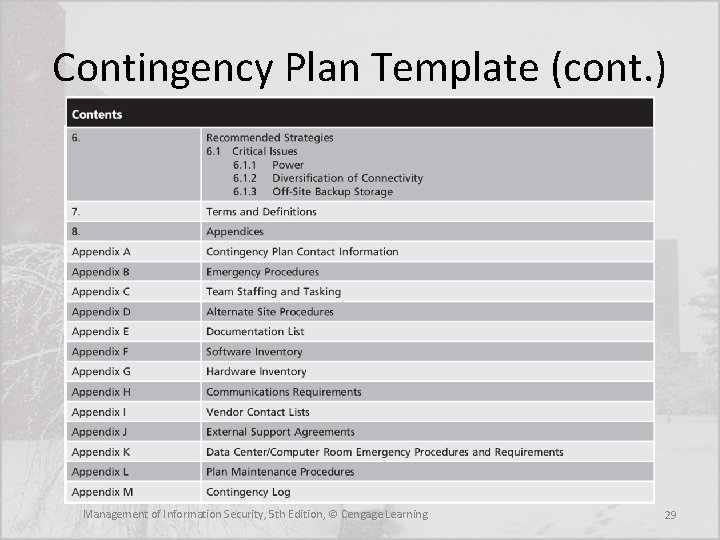
Contingency Plan Template (cont. ) Management of Information Security, 5 th Edition, © Cengage Learning 29
 Management of information security 5th edition
Management of information security 5th edition Records management disaster recovery plan
Records management disaster recovery plan Principles of marketing fifth european edition
Principles of marketing fifth european edition Appraisals in lazarus's theory of emotion
Appraisals in lazarus's theory of emotion Fundamentals of corporate finance fifth edition
Fundamentals of corporate finance fifth edition Fifth edition chemistry a molecular approach
Fifth edition chemistry a molecular approach Mitosis
Mitosis Molecular biology
Molecular biology Human anatomy fifth edition
Human anatomy fifth edition Human anatomy fifth edition
Human anatomy fifth edition Principles of information security 5th edition pdf
Principles of information security 5th edition pdf Principles of information security, 7th edition
Principles of information security, 7th edition Principles of information security 4th edition
Principles of information security 4th edition Principles of information security 4th edition
Principles of information security 4th edition Principles of information security 4th edition
Principles of information security 4th edition Privat security
Privat security Verizon 140 west street
Verizon 140 west street Principles of incident response and disaster recovery
Principles of incident response and disaster recovery Payroll disaster recovery plan
Payroll disaster recovery plan Backup and disaster recovery mississippi
Backup and disaster recovery mississippi Disaster recovery plan for manufacturing company
Disaster recovery plan for manufacturing company Mainframe disaster recovery services
Mainframe disaster recovery services Law firm disaster recovery plan
Law firm disaster recovery plan Always on disaster recovery
Always on disaster recovery Emc business continuity
Emc business continuity Oracle disaster recovery plan
Oracle disaster recovery plan Cissp business continuity and disaster recovery planning
Cissp business continuity and disaster recovery planning Ad disaster recovery planning scenario
Ad disaster recovery planning scenario Disaster recovery audit program isaca
Disaster recovery audit program isaca Vmware offsite disaster recovery
Vmware offsite disaster recovery