MANAGEMENT of INFORMATION SECURITY Fifth Edition Security Convergence



















- Slides: 23

MANAGEMENT of INFORMATION SECURITY, Fifth Edition

Security Convergence and Security SDLC Management of Information Security, 5 th Edition © Cengage Learning 2

Security Convergence • The convergence of security-related governance in organizations has been observed since the broad deployment of information systems began in the 1970 s and 1980 s • Industry media have discussed the issues surrounding this merging of management accountability in the areas of corporate (physical) security, corporate risk management, computer security, network security, and Info. Sec as such trends waxed and waned over the years Management of Information Security, 5 th Edition © Cengage Learning 3

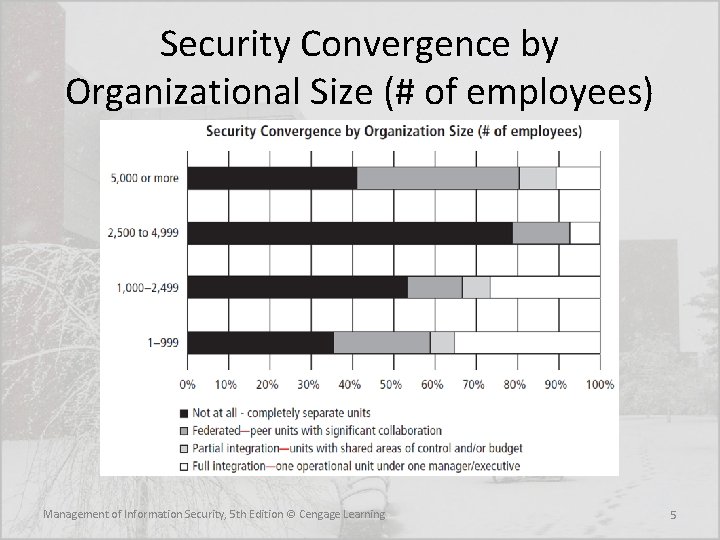
Security Convergence • A 2007 report commissioned by the Alliance for Enterprise Security Risk Management identified the key approaches organizations are using to achieve unified enterprise risk management (ERM): – Combining physical security and Info. Sec under one leader as one business function – Using separate business functions (each with a separate budget and autonomy) that report to a common senior executive – Using a risk council approach to provide a collaborative method for risk management, to set policy about assuming risk to the organization • A 2015 study of Info. Sec management practices found that most larger organizations still keep physical and information security efforts segregate even with significant collaboration, while full integration is much more common in smaller organizations Management of Information Security, 5 th Edition © Cengage Learning 4

Security Convergence by Organizational Size (# of employees) Management of Information Security, 5 th Edition © Cengage Learning 5

Planning For Information Security Implementation • The CIO and CISO play important roles in translating overall strategic planning into tactical and operational information security plans • When the CISO reports directly to the CIO, the CIO charges the CISO and other IT department heads with creating and adopting plans that are consistent with and supportive of the IT strategy as it supports the entire organizational strategy • It falls upon the CISO to go beyond the plans and efforts of the IT group to ensure that the Info. Sec plan also directly supports the entire organization and the strategies of other business units, beyond the scope of the IT plan Management of Information Security, 5 th Edition © Cengage Learning 6

CISO Job Description • Creates a strategic information security plan with a vision for the future of information security at Company X… • Understands the fundamental business activities performed by Company X, and based on this understanding, suggests appropriate information security solutions that uniquely protect these activities… • Develops action plans, schedules, budgets, status reports and other top management communications intended to improve the status of information security at Company X… Management of Information Security, 5 th Edition © Cengage Learning 7

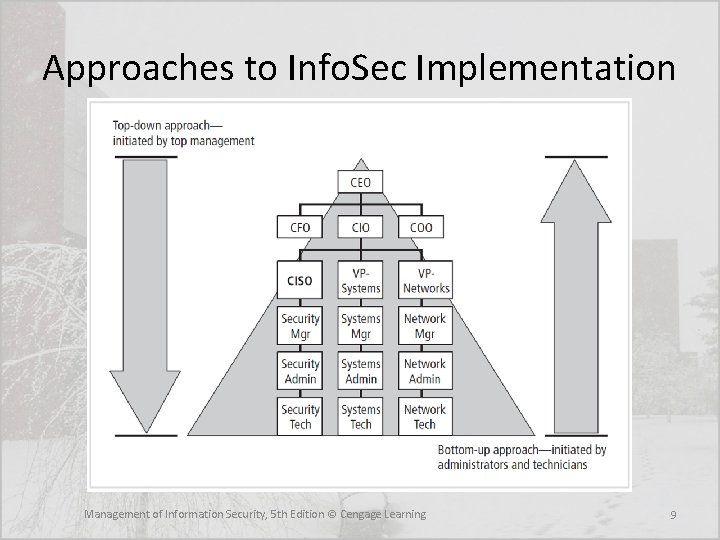
Planning for Info. Sec • Once plan has been translated into IT and information security objectives and tactical and operational plans information security implementation can begin • Implementation of information security can be accomplished in two ways: – bottom-up or – top-down Management of Information Security, 5 th Edition © Cengage Learning 8

Approaches to Info. Sec Implementation Management of Information Security, 5 th Edition © Cengage Learning 9

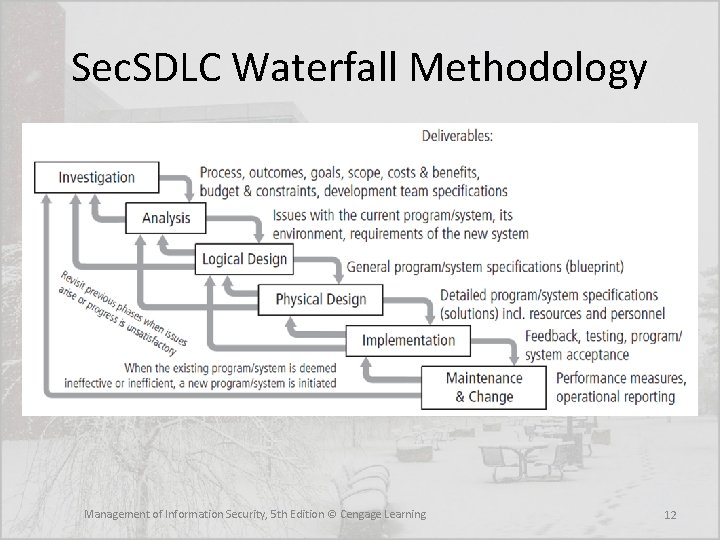
Introduction to the Security Systems Development Life Cycle (Sec. SDLC) • An SDLC is a methodology for the design and implementation of an information system • SDLC-based projects may be initiated by events or planned • At the end of each phase, a review occurs when reviewers determine if the project should be continued, discontinued, outsourced, or postponed Management of Information Security, 5 th Edition © Cengage Learning 10

Introduction to the Security Systems Development Life Cycle (Sec. SDLC) • It may differ in several specifics, but the overall methodology is similar to the SDLC • The Sec. SDLC process involves the identification of specific threats and the risks that they represent as well as the subsequent design and implementation of specific controls to counter those threats and manage the risk Management of Information Security, 5 th Edition © Cengage Learning 11

Sec. SDLC Waterfall Methodology Management of Information Security, 5 th Edition © Cengage Learning 12

Investigation in the Sec. SDLC • Often begins as directive from management specifying the process, outcomes, and goals of the project and its budget • Frequently begins with the affirmation or creation of security policies • Teams assembled to analyze problems, define scope, specify goals and identify constraints • A feasibility analysis determines whether the organization has the resources and commitment to conduct a successful security analysis and design Management of Information Security, 5 th Edition © Cengage Learning 13

Analysis in the Sec. SDLC • A preliminary analysis of existing security policies or programs is prepared along with known threats and associated controls • Includes an analysis of relevant legal issues that could affect the design of the security solution • Risk management begins in this stage Management of Information Security, 5 th Edition © Cengage Learning 14

Design in the Sec. SDLC • The design phase actually consists of two distinct phases: – In the logical design phase, team members create and develop a blueprint for security, and examine and implement key policies – In the physical design phase, team members evaluate the technology needed to support the security blueprint, generate alternative solutions, and agree upon a final design Management of Information Security, 5 th Edition © Cengage Learning 15

Design in the Sec. SDLC • The design phase continues with the formulation of the controls and safeguards used to protect information from attacks by threats. • There are three categories of controls: – Managerial controls cover security processes that are designed by the strategic planners and executed by the security administration of the organization – Operational controls cover management functions and lowerlevel planning, such as disaster recovery and incident response planning (IRP), as well as address personnel security, physical security, and the protection of production inputs and outputs • Technical controls address technical approaches used to implement security in the organization and must be selected, acquired (made or bought), and integrated into the organization’s IT structure Management of Information Security, 5 th Edition © Cengage Learning 16

Implementation in the Sec. SDLC • The security solutions are acquired, tested, implemented, and tested again • Personnel issues are evaluated and specific training and education programs conducted • Perhaps the most important element of the implementation phase is the management of the project plan: – planning the project – supervising the tasks and action steps within the project – wrapping up the project Management of Information Security, 5 th Edition © Cengage Learning 17

Info. Sec Project Team • Should consist individuals experienced in one or multiple technical and non-technical areas including: – The champion – The team leader – Security policy developers – Risk assessment specialists – Security professionals – Systems administrators – End users Management of Information Security, 5 th Edition © Cengage Learning 18

Staffing the Info. Sec Function • Each organization should examine the options for staffing of the information security function: – First, decide how to position and name the security function – Second, plan for the proper staffing of the information security function – Third, understand the impact of information security across every role in IT – Finally, integrate solid information security concepts into the personnel management practices of the organization Management of Information Security, 5 th Edition © Cengage Learning 19

Info. Sec Professionals • It takes a wide range of professionals to support a diverse information security program: – Chief Information Officer (CIO) – Chief Security Officer (CSO) – Chief Information Security Officer (CISO) – Security Managers – Security Technicians – Data Owners – Data Custodians – Data Users Management of Information Security, 5 th Edition © Cengage Learning 20

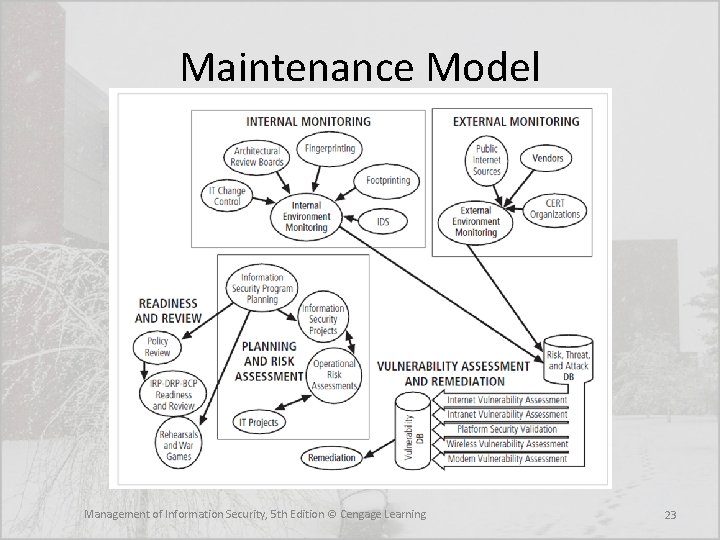
Maintenance in the Sec. SDLC • Once the information security program is implemented, it must be operated, properly managed, and kept up to date by means of established procedures • If the program is not adjusting adequately to the changes in the internal or external environment, it may be necessary to begin the cycle again Management of Information Security, 5 th Edition © Cengage Learning 21

Maintenance Model • While a systems management model is designed to manage and operate systems, a maintenance model is intended to focus organizational effort on system maintenance: – External monitoring – Internal monitoring – Planning and risk assessment – Vulnerability assessment and remediation – Readiness and review – Vulnerability assessment Management of Information Security, 5 th Edition © Cengage Learning 22

Maintenance Model Management of Information Security, 5 th Edition © Cengage Learning 23
 Absolute and conditional convergence
Absolute and conditional convergence Management of information security 5th edition
Management of information security 5th edition Principles of marketing fifth european edition
Principles of marketing fifth european edition Lazarus cognitive appraisal theory
Lazarus cognitive appraisal theory Fundamentals of corporate finance fifth edition
Fundamentals of corporate finance fifth edition Democritus atomic model diagram
Democritus atomic model diagram Molecular biology of the cell
Molecular biology of the cell Molecular biology
Molecular biology Human anatomy fifth edition
Human anatomy fifth edition Human anatomy fifth edition
Human anatomy fifth edition Failure of supporting utilities and structural collapse
Failure of supporting utilities and structural collapse Principles of business information systems
Principles of business information systems Information asset classification worksheet
Information asset classification worksheet Principles of information security 4th edition
Principles of information security 4th edition Information security
Information security Information technology project management 9th edition
Information technology project management 9th edition Information technology project management 9th edition ppt
Information technology project management 9th edition ppt Vertical
Vertical Project management quality control
Project management quality control Information technology project management 9th edition
Information technology project management 9th edition Introduction to management information systems 5th edition
Introduction to management information systems 5th edition Management information systems 13th edition
Management information systems 13th edition Information technology project management 9th edition
Information technology project management 9th edition Mis chapter 6
Mis chapter 6