UNITV Transport Layer Protocol UDP and TCP ATM











- Slides: 155

UNIT-V Transport Layer Protocol UDP and TCP, ATM, Cryptography, Network Security

Role of Transport Layer n Application layer n n n Transport layer n n Communication for specific applications E. g. , Hyper. Text Transfer Protocol (HTTP), File Transfer Protocol (FTP), Network News Transfer Protocol (NNTP) Communication between processes Relies on network layer and serves the application layer E. g. , TCP and UDP Network layer n n n Logical communication between nodes Hides details of the link technology E. g. , IP

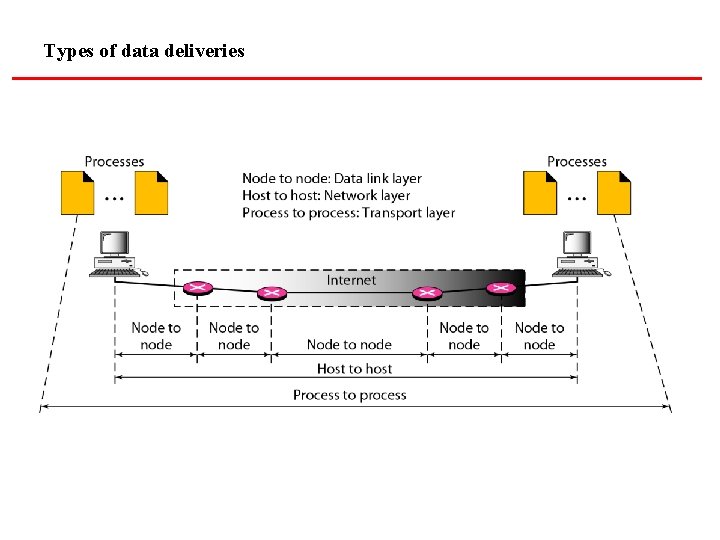
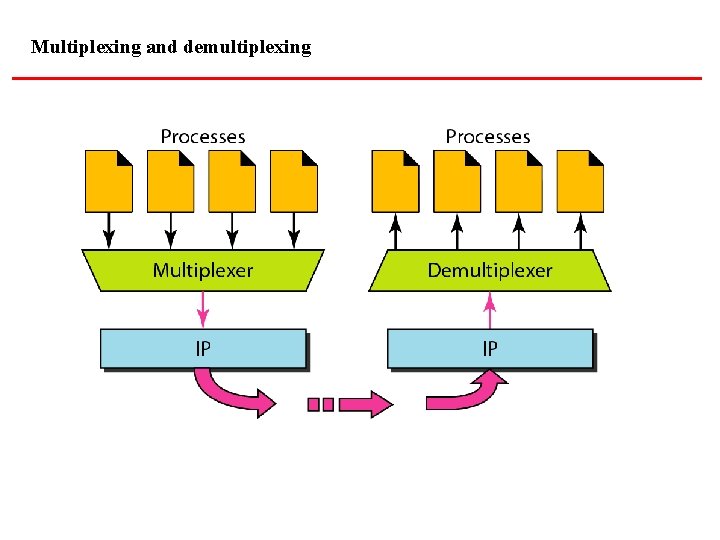
PROCESS-TO-PROCESS DELIVERY The transport layer is responsible for process-toprocess delivery—the delivery of a packet, part of a message, from one process to another. Two processes communicate in a client/server relationship, as we will see later. Topics discussed in this section: Client/Server Paradigm Multiplexing and Demultiplexing Connectionless Versus Connection-Oriented Service Reliable Versus Unreliable Three Protocols

n Principles underlying transport-layer services n n n (De)multiplexing Detecting corruption Reliable delivery Flow control Transport-layer protocols in the Internet n n User Datagram Protocol (UDP) Transmission Control Protocol (TCP)

Note The transport layer is responsible for process-to-process delivery.

Types of data deliveries

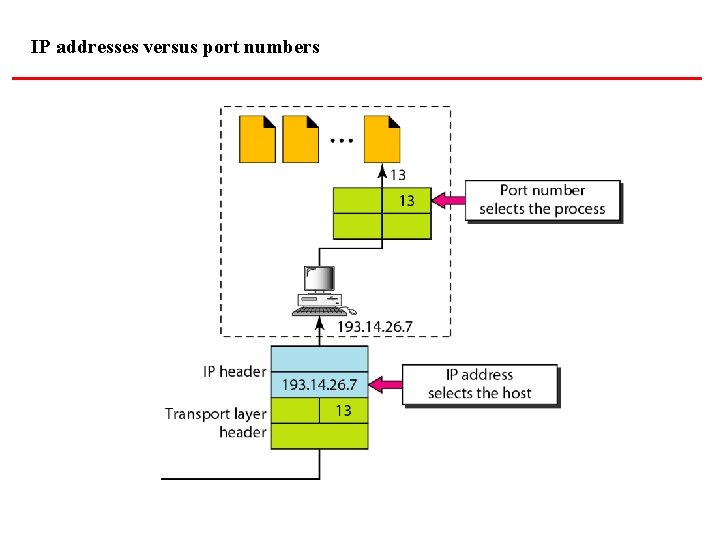
IP addresses versus port numbers

Multiplexing and demultiplexing

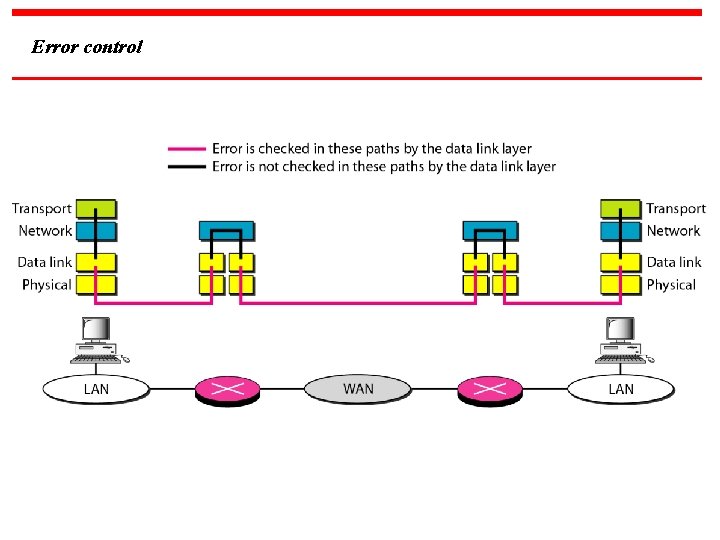
Error control

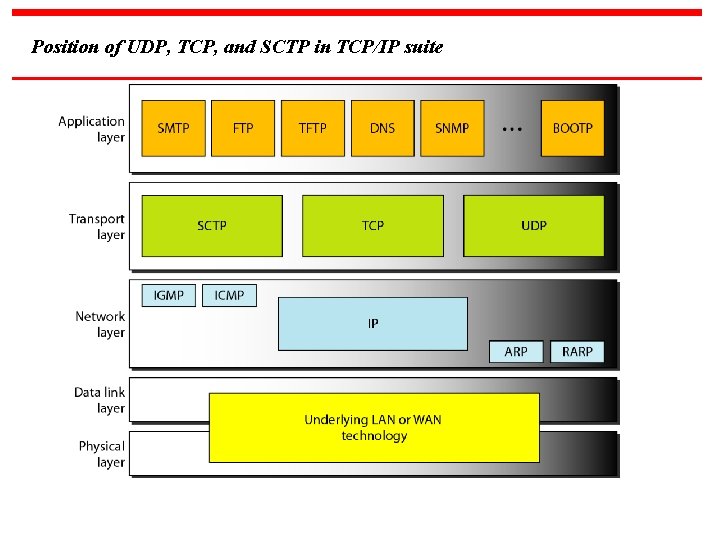
Position of UDP, TCP, and SCTP in TCP/IP suite

USER DATAGRAM PROTOCOL (UDP) The User Datagram Protocol (UDP) is called a connectionless, unreliable transport protocol. It does not add anything to the services of IP except to provide process-to-process communication instead of host-to-host communication. Topics discussed in this section: Well-Known Ports for UDP User Datagram Checksum UDP Operation Use of UDP

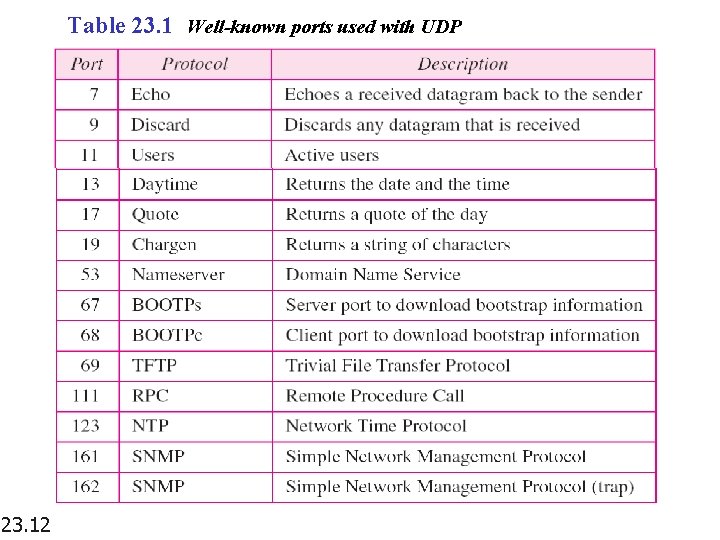
Table 23. 1 Well-known ports used with UDP 23. 12

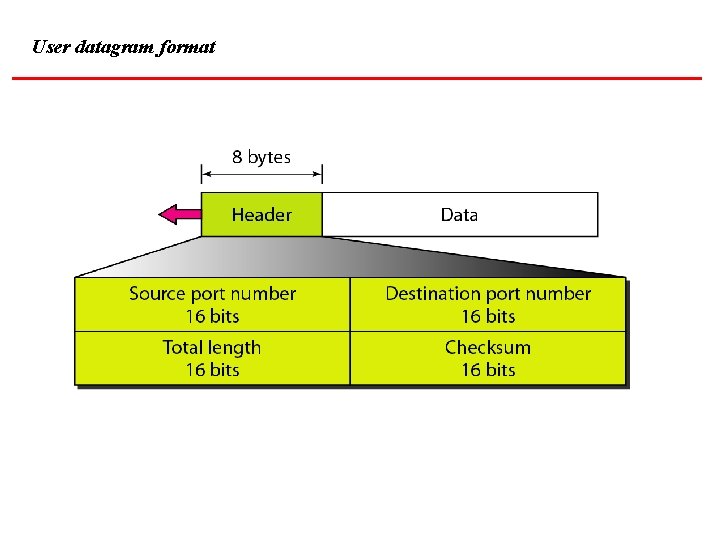
User datagram format

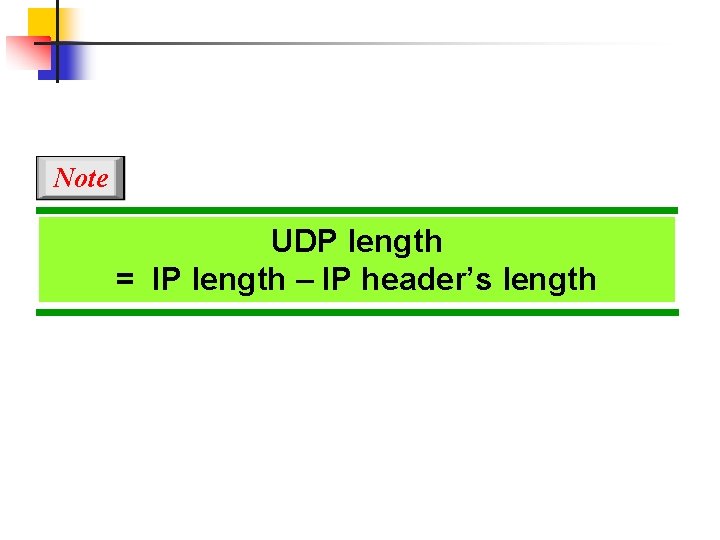
Note UDP length = IP length – IP header’s length

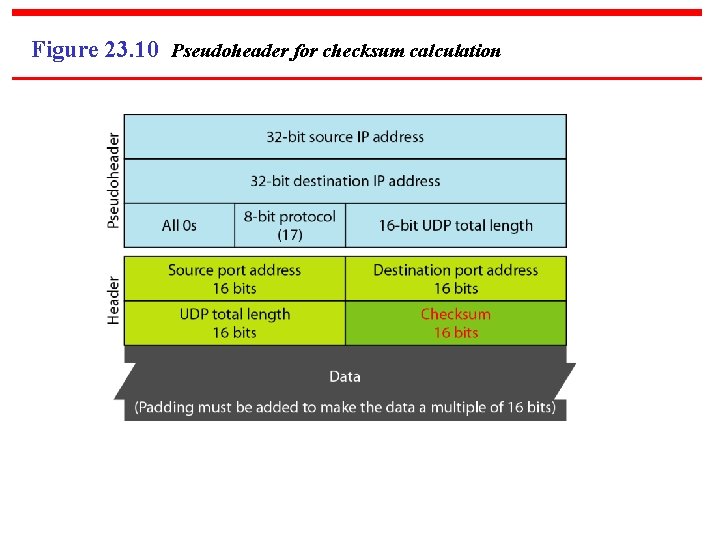
Figure 23. 10 Pseudoheader for checksum calculation

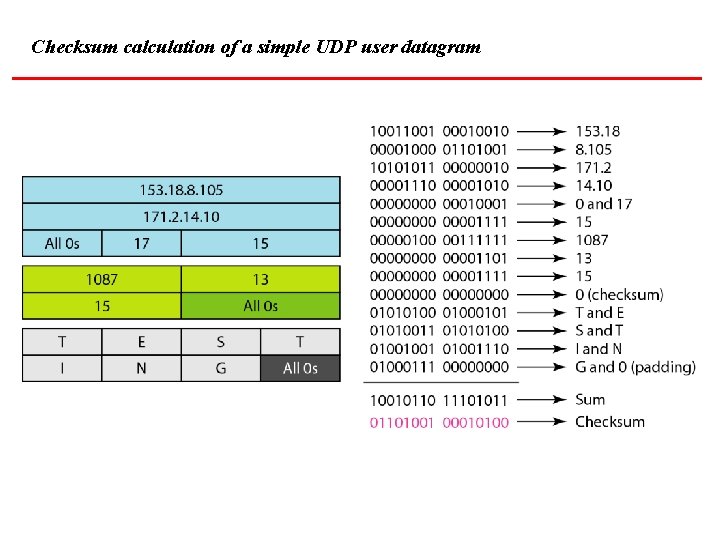
Checksum calculation of a simple UDP user datagram

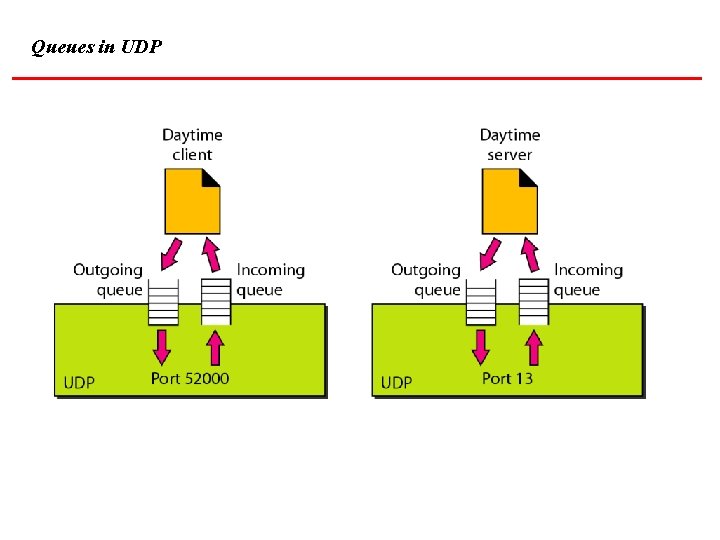
Queues in UDP

TCP is a connection-oriented protocol; it creates a virtual connection between two TCPs to send data. In addition, TCP uses flow and error control mechanisms at the transport level. Topics discussed in this section: TCP Services TCP Features Segment A TCP Connection Flow Control Error Control

Well-known ports used by TCP

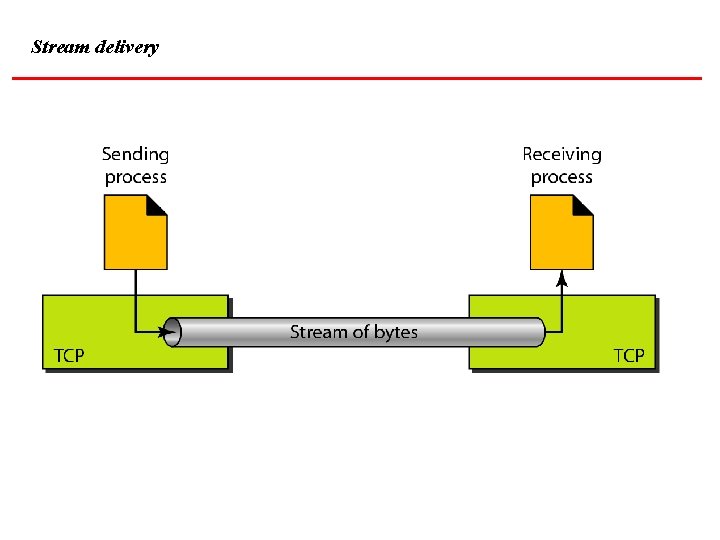
Stream delivery

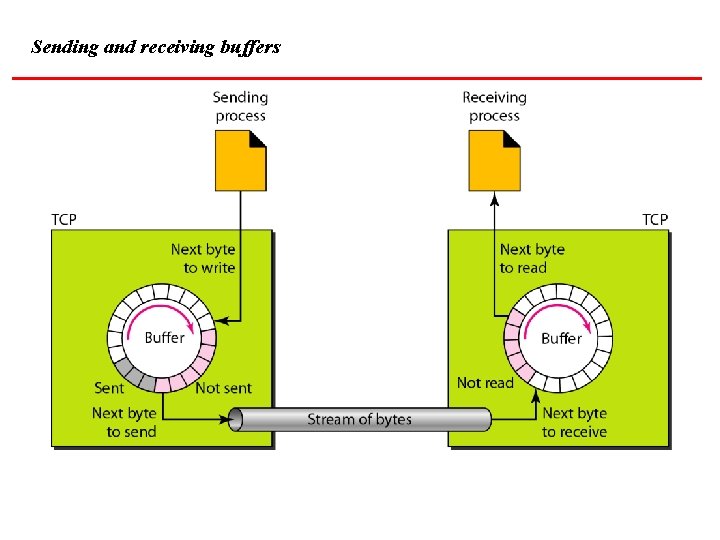
Sending and receiving buffers

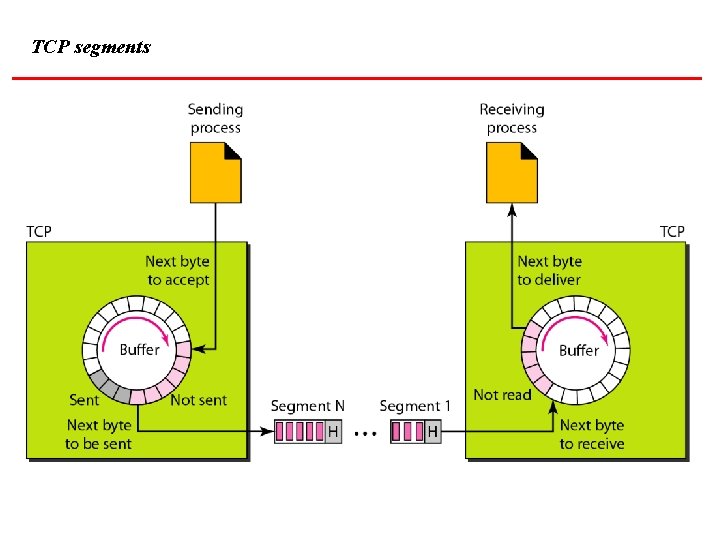
TCP segments

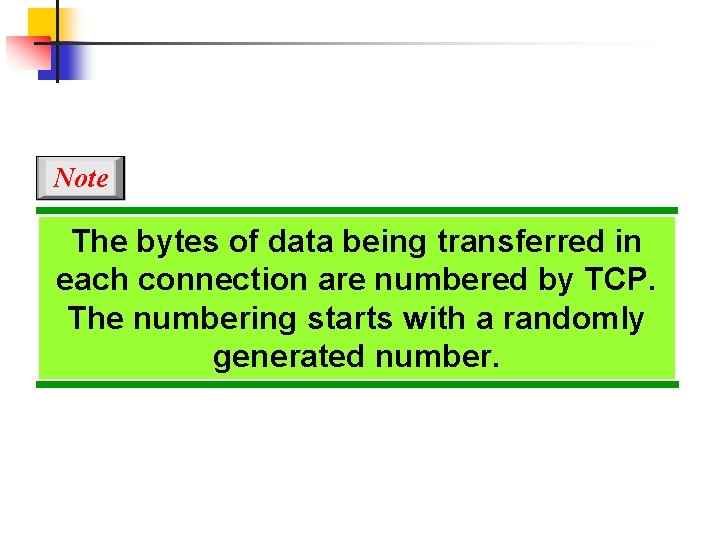
Note The bytes of data being transferred in each connection are numbered by TCP. The numbering starts with a randomly generated number.

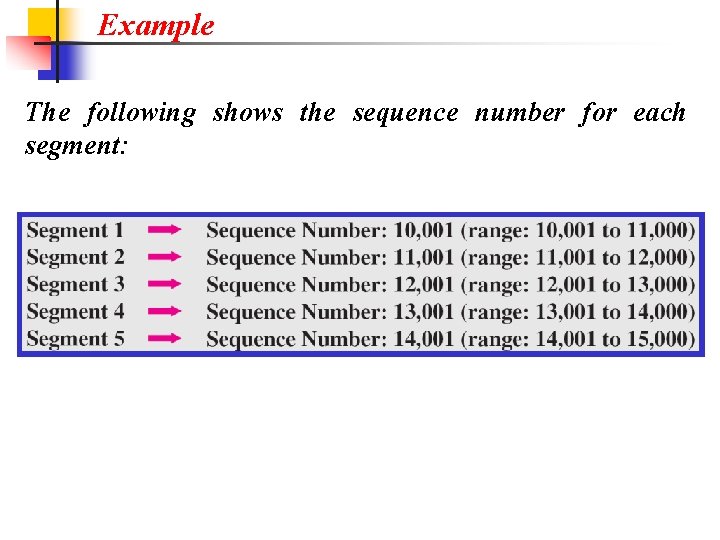
Example The following shows the sequence number for each segment:

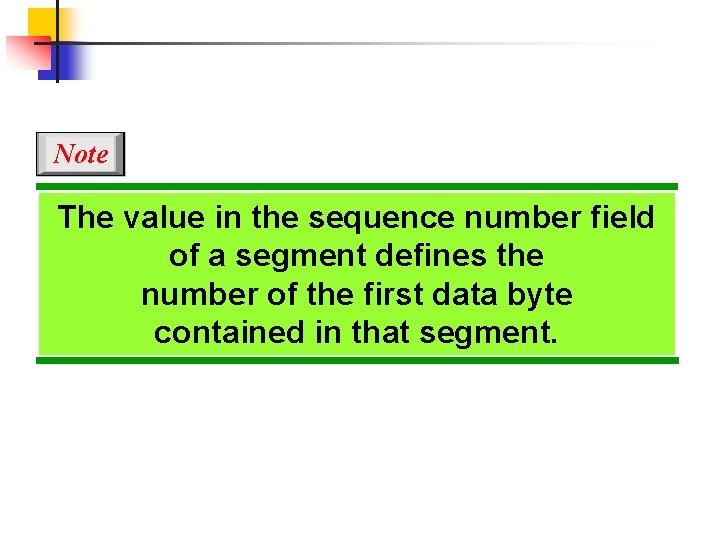
Note The value in the sequence number field of a segment defines the number of the first data byte contained in that segment.

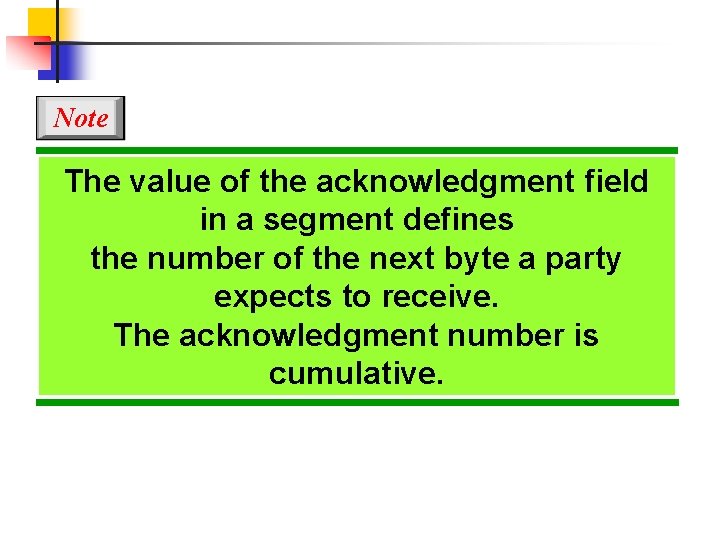
Note The value of the acknowledgment field in a segment defines the number of the next byte a party expects to receive. The acknowledgment number is cumulative.

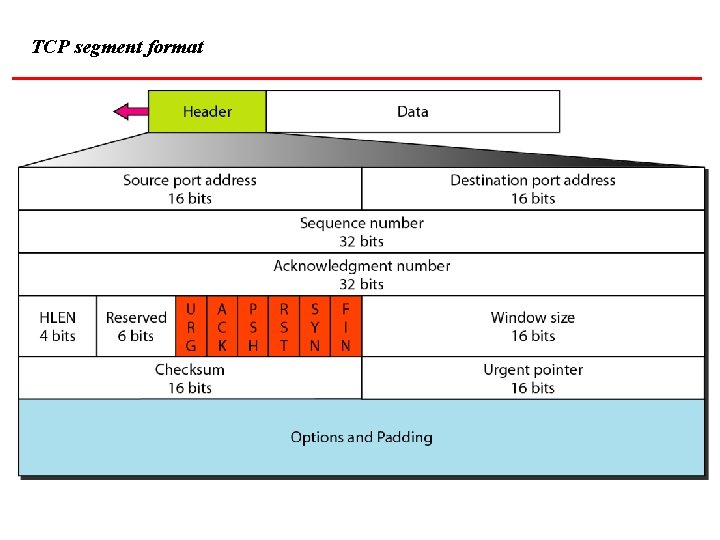
TCP segment format

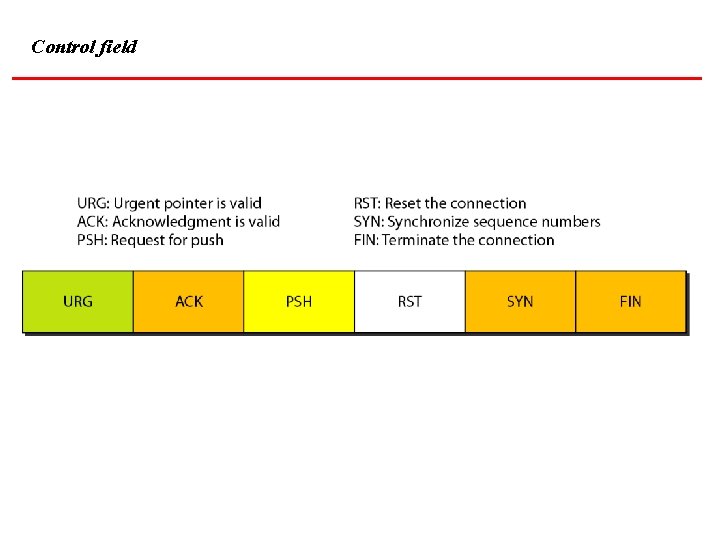
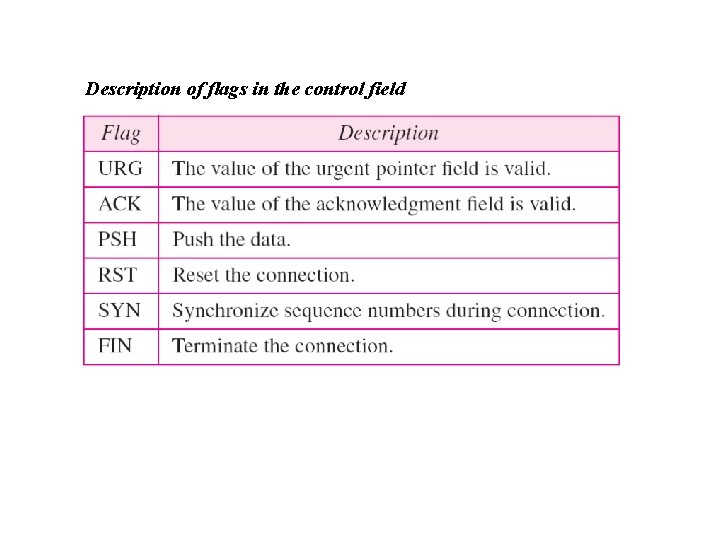
Control field

Description of flags in the control field

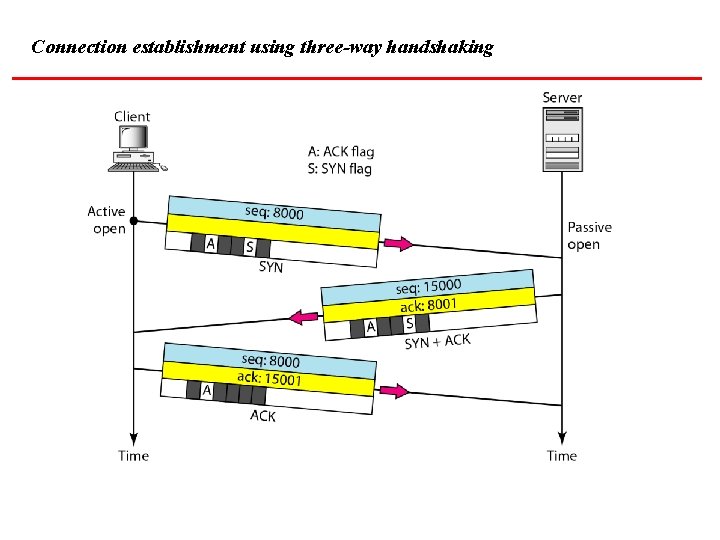
Connection establishment using three-way handshaking

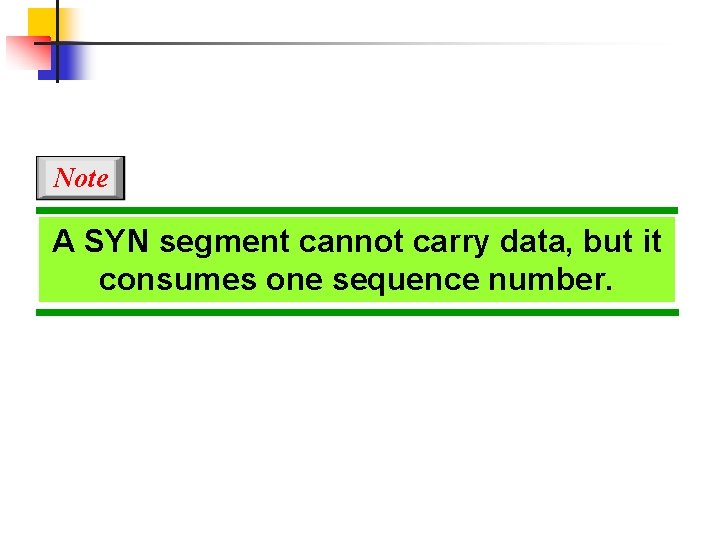
Note A SYN segment cannot carry data, but it consumes one sequence number.

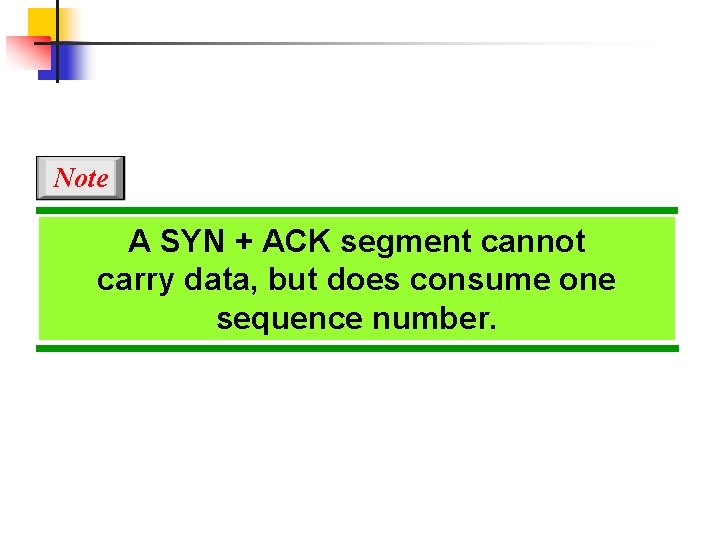
Note A SYN + ACK segment cannot carry data, but does consume one sequence number.

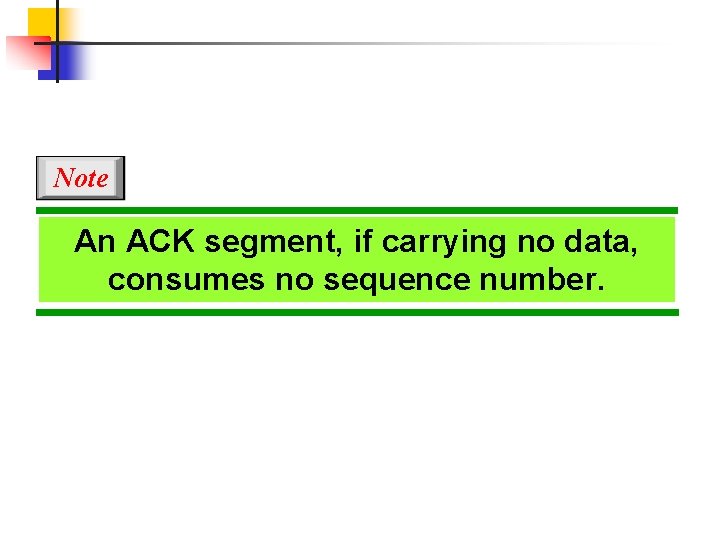
Note An ACK segment, if carrying no data, consumes no sequence number.

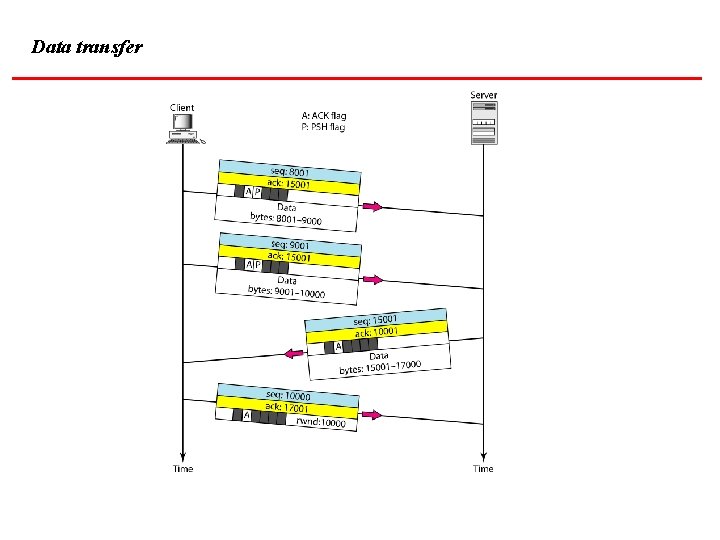
Data transfer

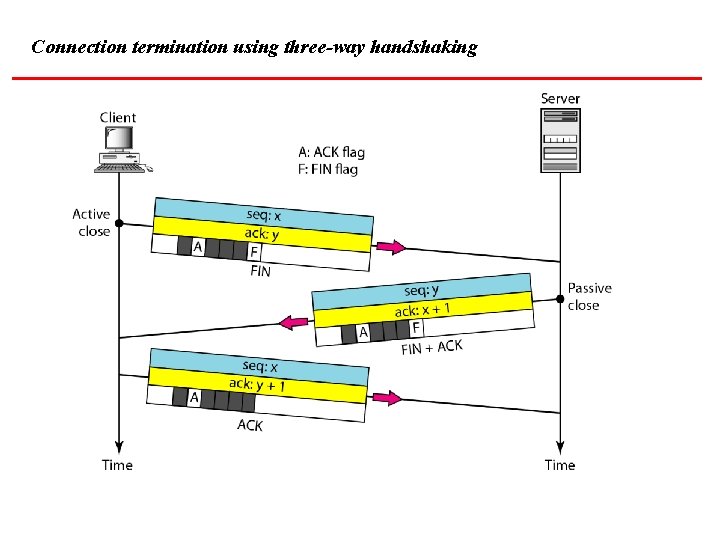
Connection termination using three-way handshaking

Note The FIN segment consumes one sequence number if it does not carry data. 23. 36

Note The FIN + ACK segment consumes one sequence number if it does not carry data. 23. 37

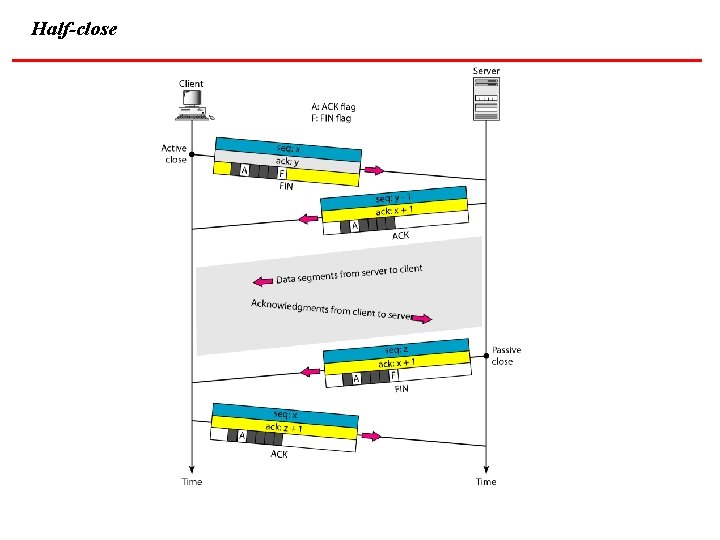
Half-close

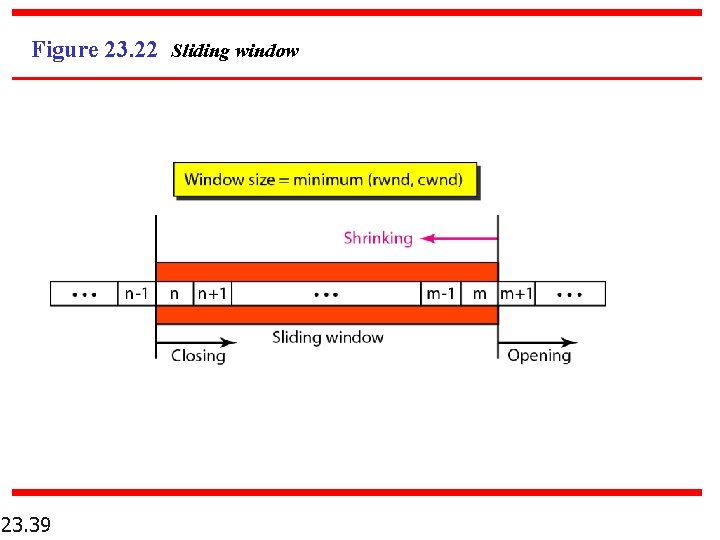
Figure 23. 22 Sliding window 23. 39

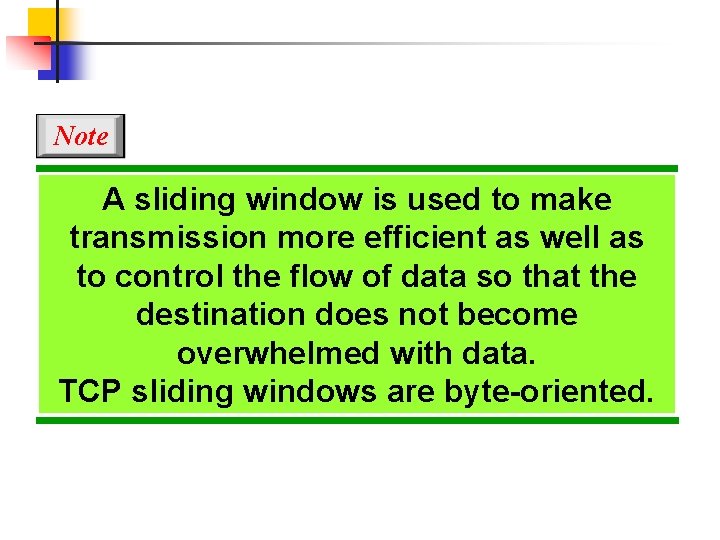
Note A sliding window is used to make transmission more efficient as well as to control the flow of data so that the destination does not become overwhelmed with data. TCP sliding windows are byte-oriented.

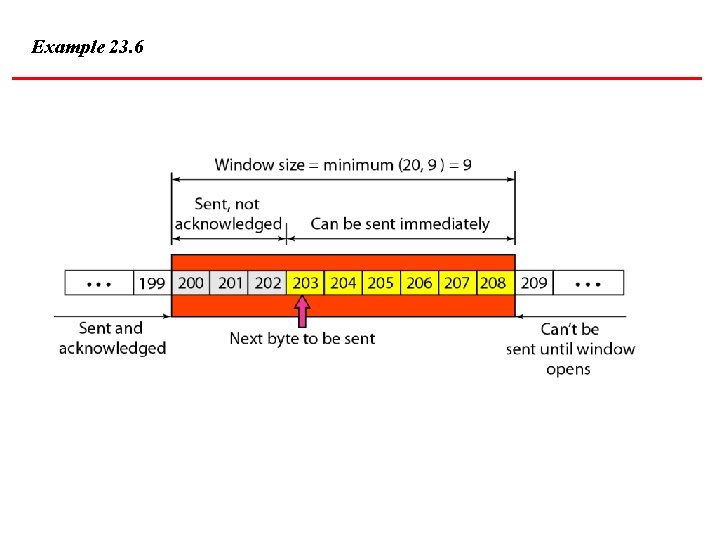
Example 23. 6

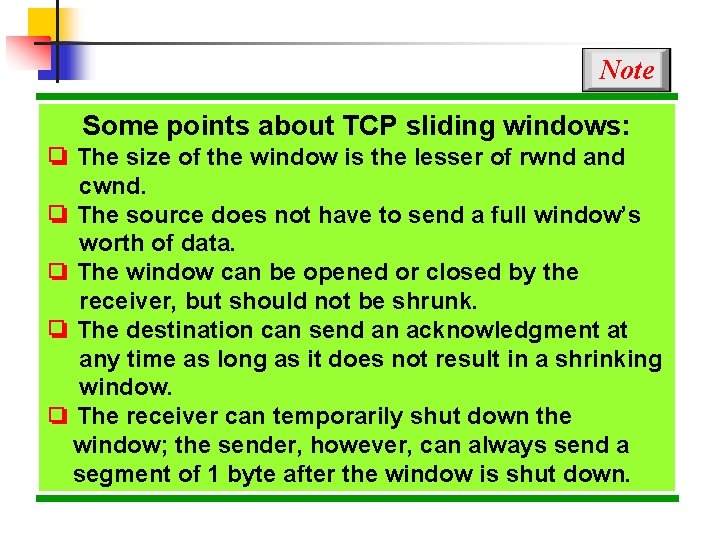
Note Some points about TCP sliding windows: ❏ The size of the window is the lesser of rwnd and cwnd. ❏ The source does not have to send a full window’s worth of data. ❏ The window can be opened or closed by the receiver, but should not be shrunk. ❏ The destination can send an acknowledgment at any time as long as it does not result in a shrinking window. ❏ The receiver can temporarily shut down the window; the sender, however, can always send a segment of 1 byte after the window is shut down.

Note ACK segments do not consume sequence numbers and are not acknowledged.

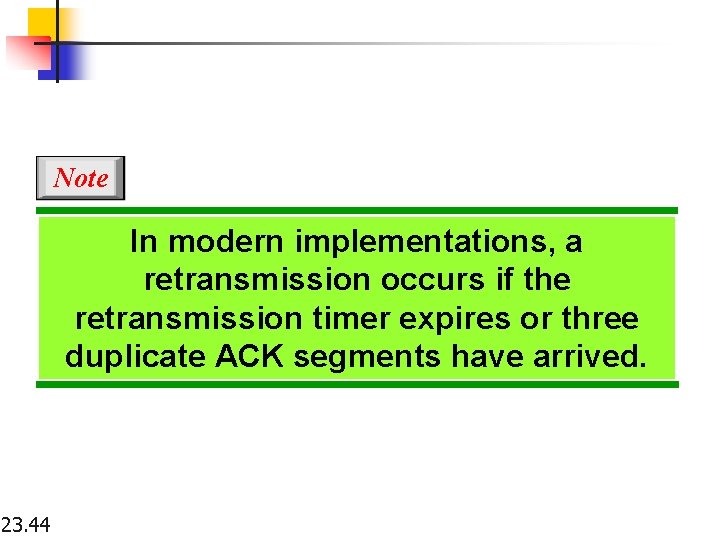
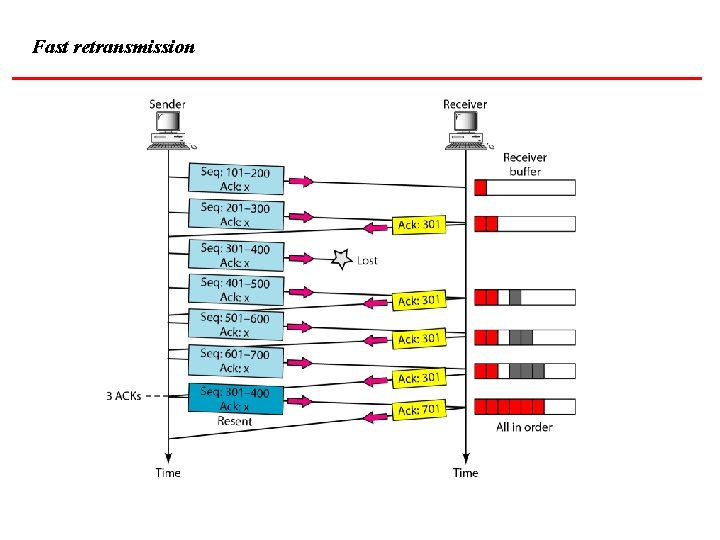
Note In modern implementations, a retransmission occurs if the retransmission timer expires or three duplicate ACK segments have arrived. 23. 44

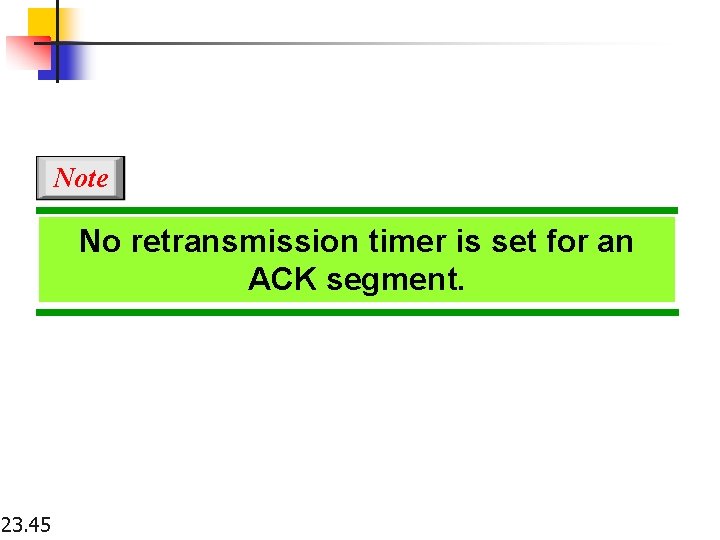
Note No retransmission timer is set for an ACK segment. 23. 45

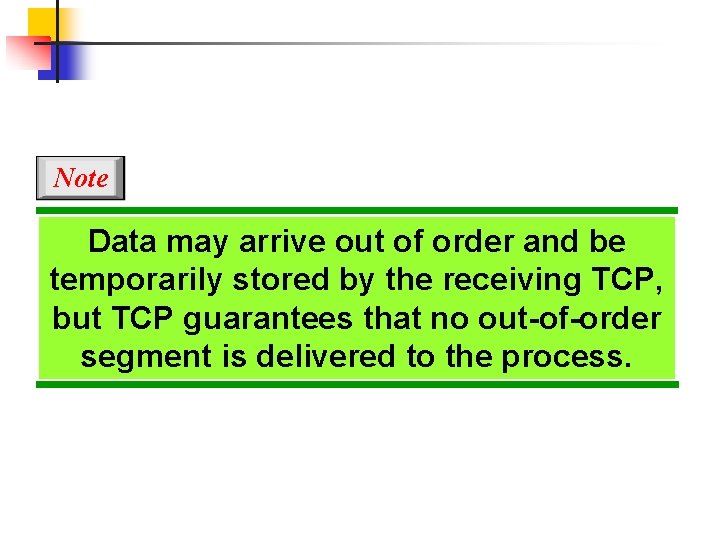
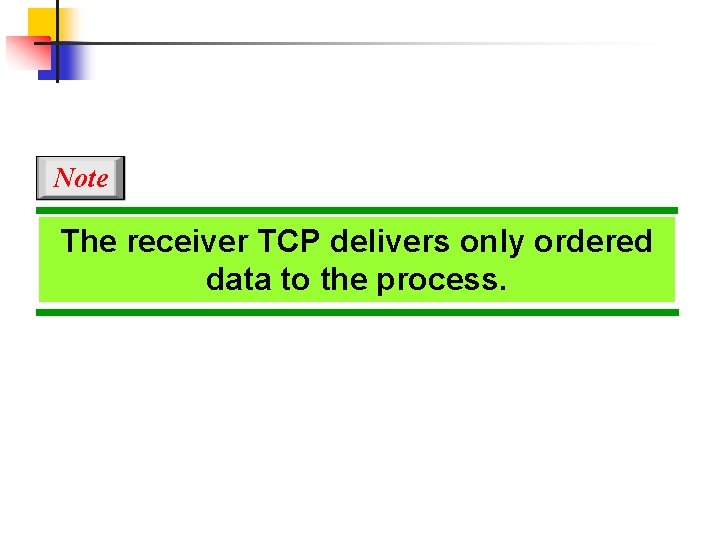
Note Data may arrive out of order and be temporarily stored by the receiving TCP, but TCP guarantees that no out-of-order segment is delivered to the process.

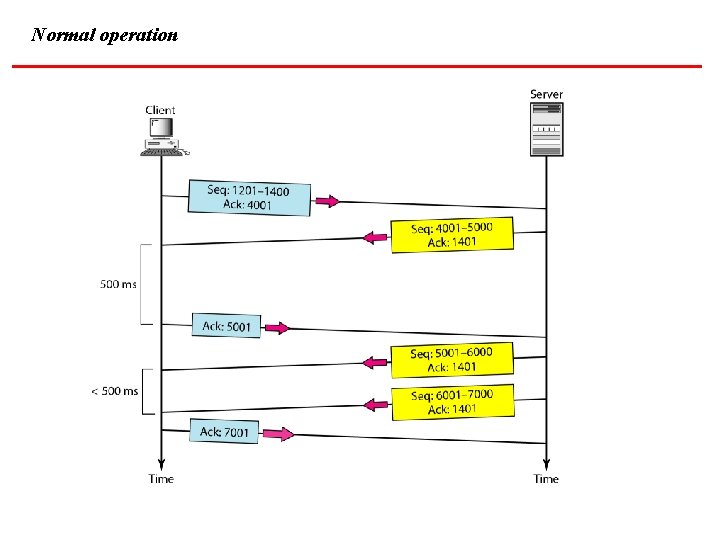
Normal operation

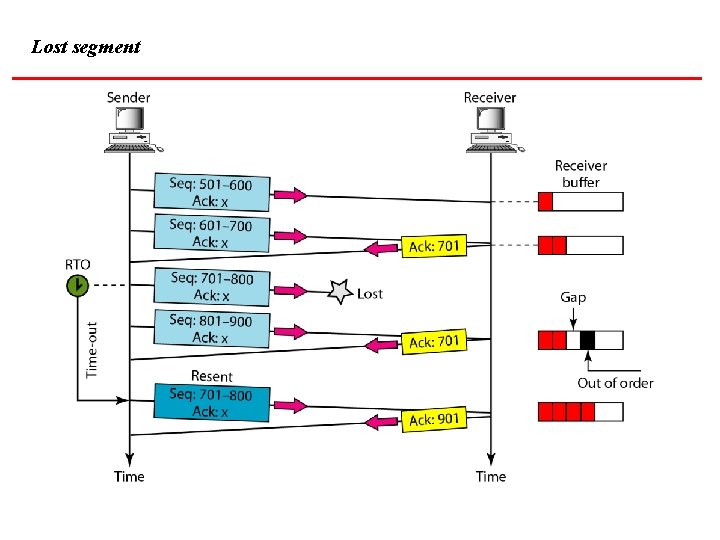
Lost segment

Note The receiver TCP delivers only ordered data to the process.

Fast retransmission

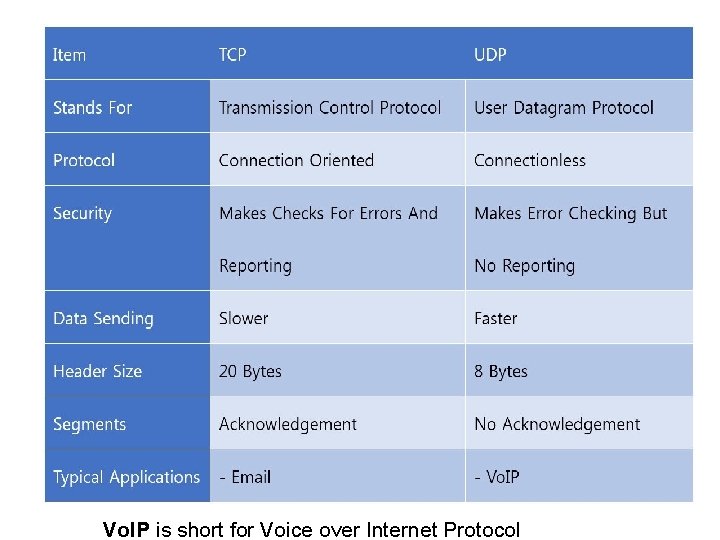
Vo. IP is short for Voice over Internet Protocol

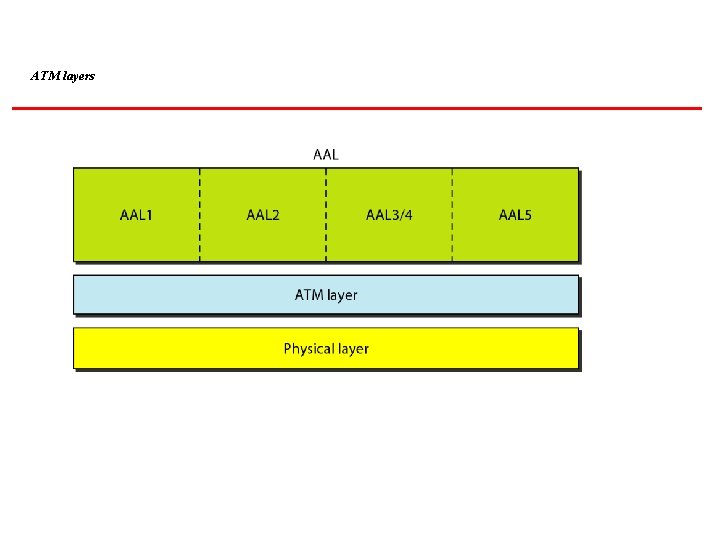
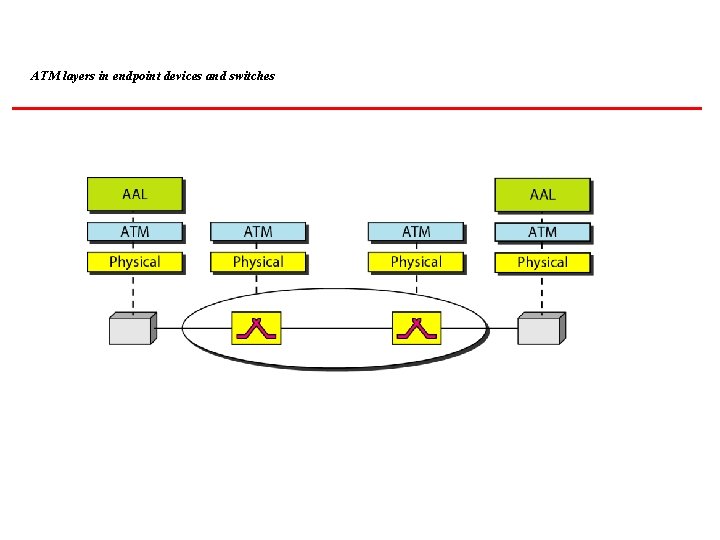
ATM Asynchronous Transfer Mode (ATM) is the cell relay protocol designed by the ATM Forum and adopted by the ITU-T. Topics discussed in this section: Design Goals Problems Architecture Switching ATM Layers

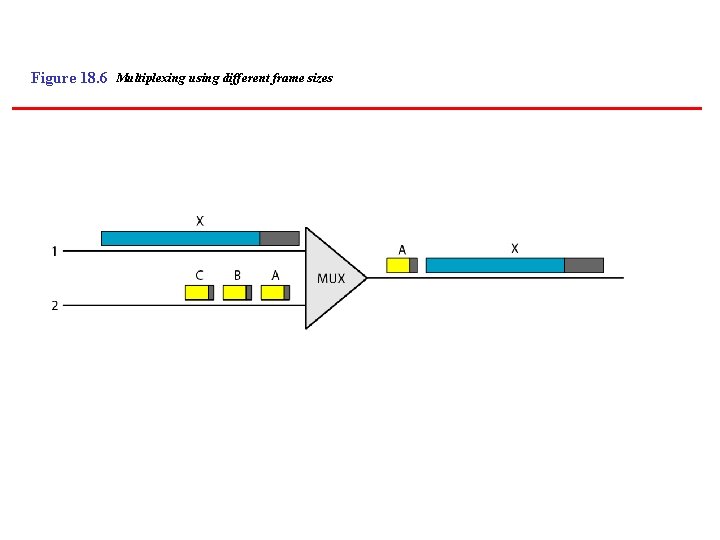
Figure 18. 6 Multiplexing using different frame sizes

Note A cell network uses the cell as the basic unit of data exchange. A cell is defined as a small, fixed-size block of information.

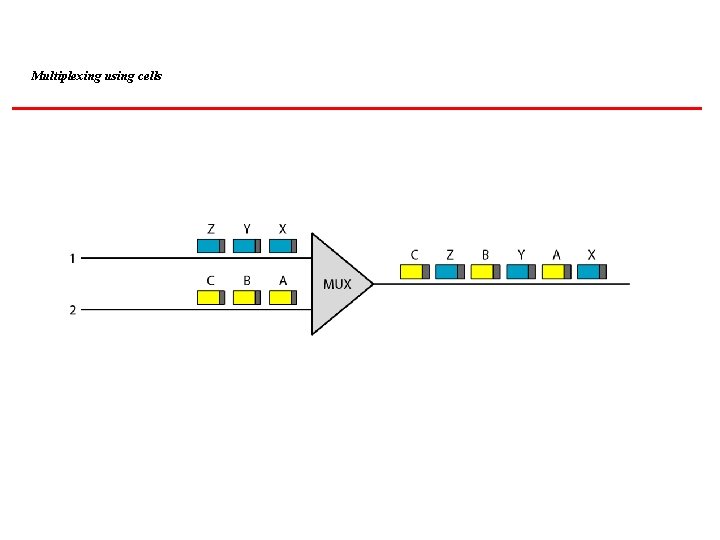
Multiplexing using cells

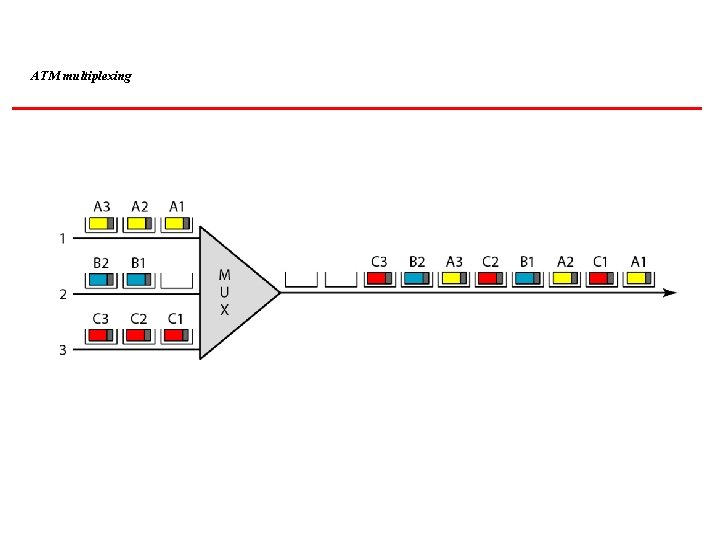
ATM multiplexing

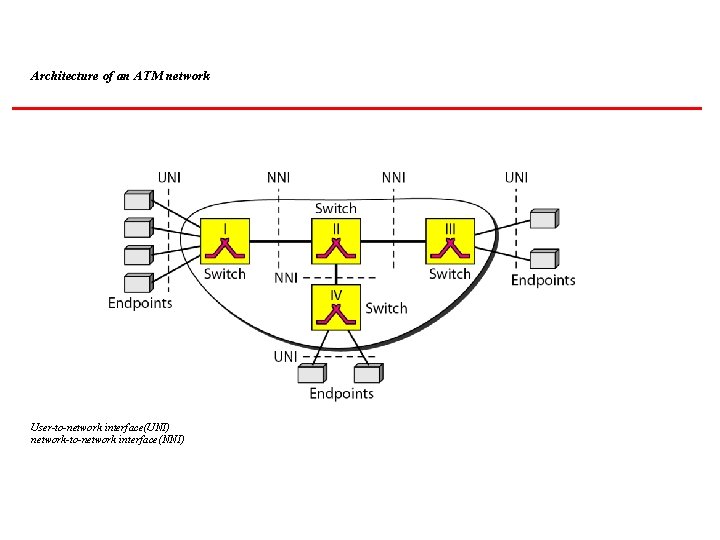
Architecture of an ATM network User-to-network interface(UNI) network-to-network interface(NNI)

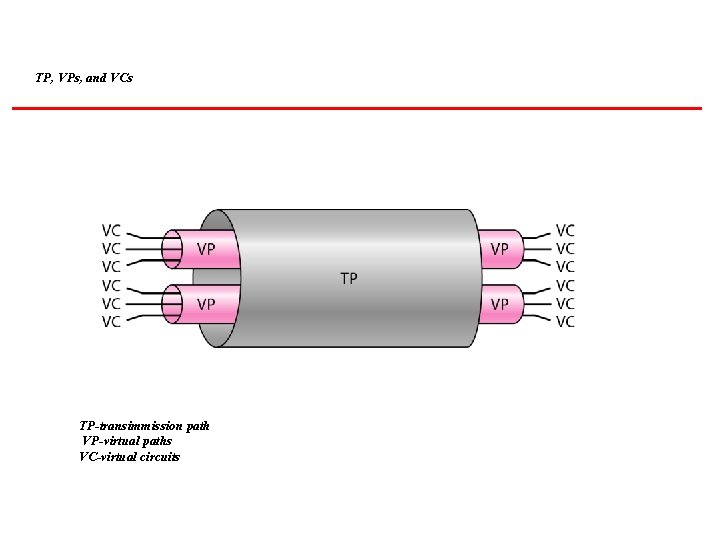
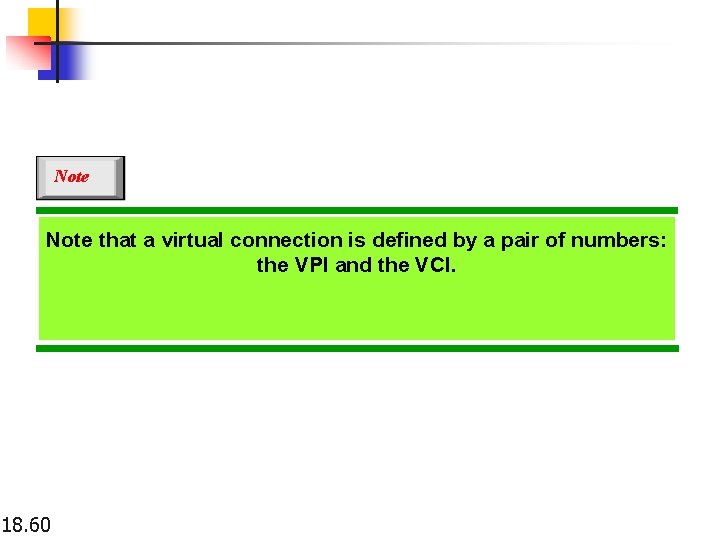
TP, VPs, and VCs TP-transimmission path VP-virtual paths VC-virtual circuits

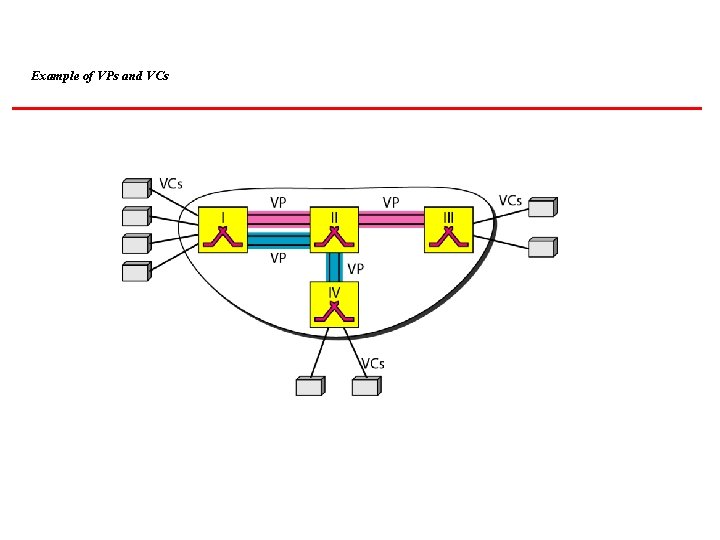
Example of VPs and VCs

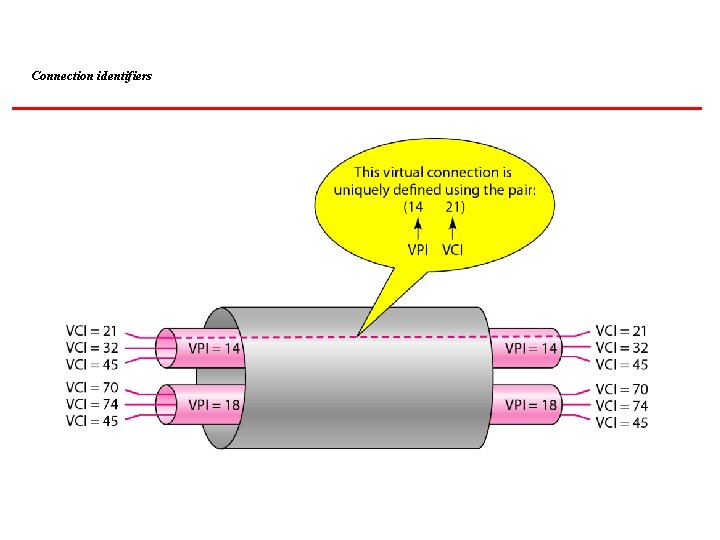
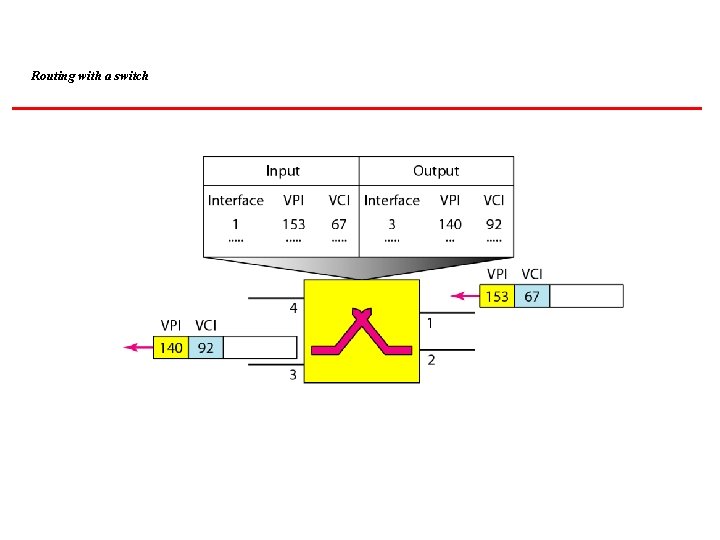
Note that a virtual connection is defined by a pair of numbers: the VPI and the VCI. 18. 60

Connection identifiers

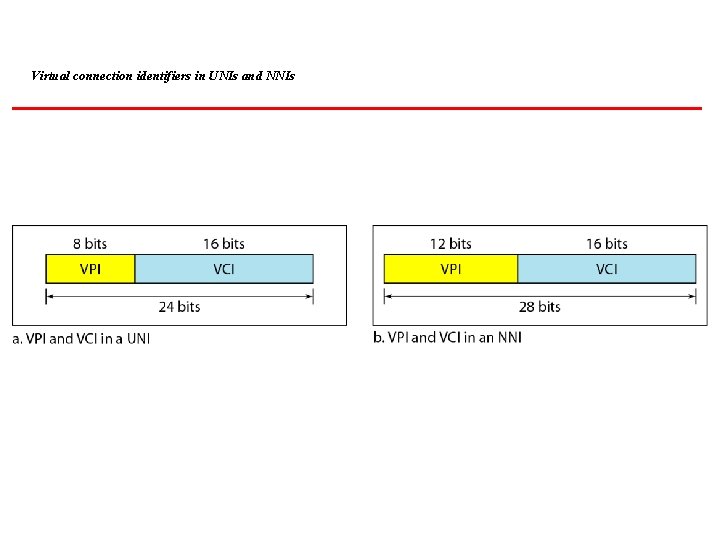
Virtual connection identifiers in UNIs and NNIs

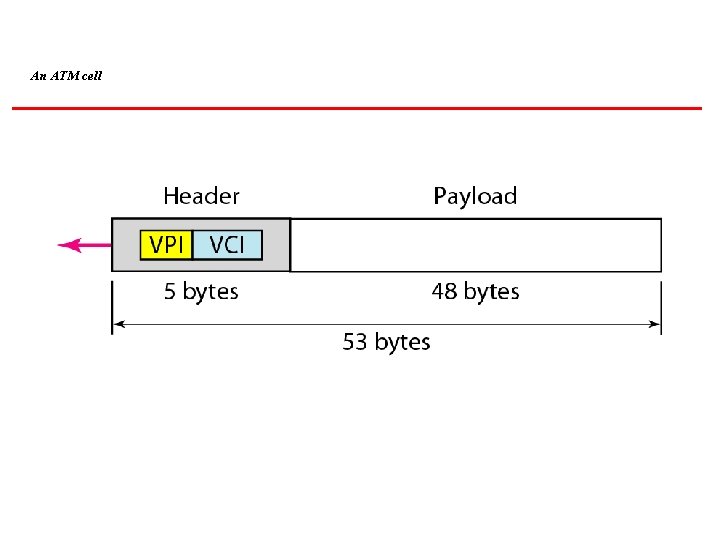
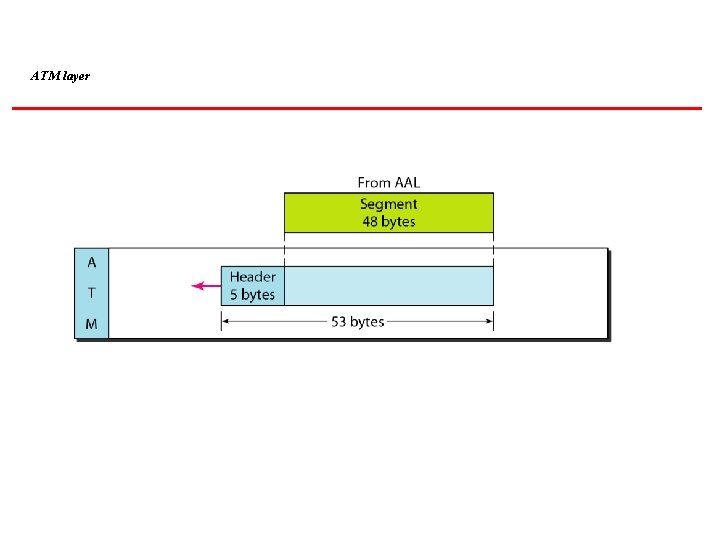
An ATM cell

Routing with a switch

ATM layers

ATM layers in endpoint devices and switches

ATM layer

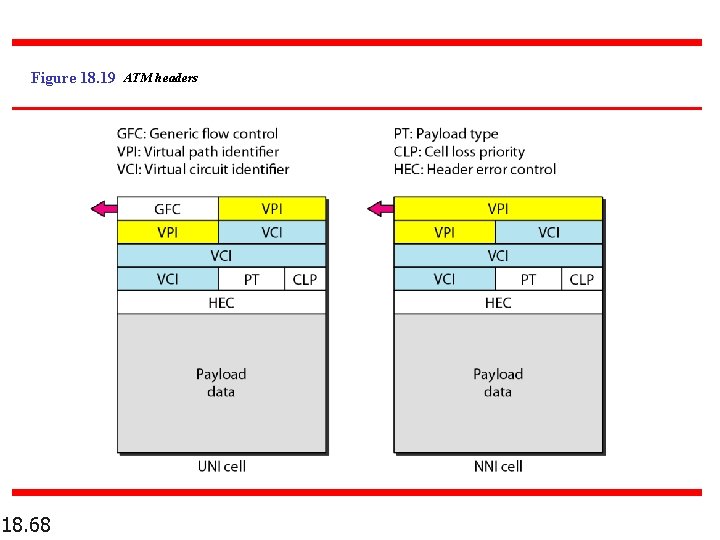
Figure 18. 19 ATM headers 18. 68

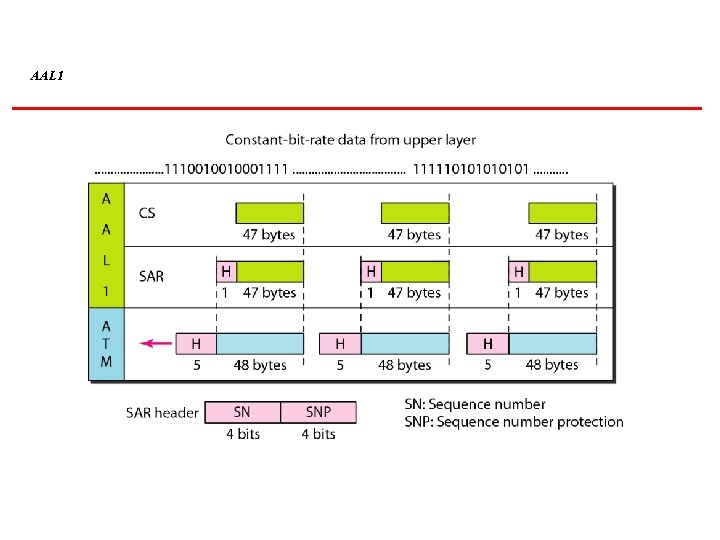
AAL 1

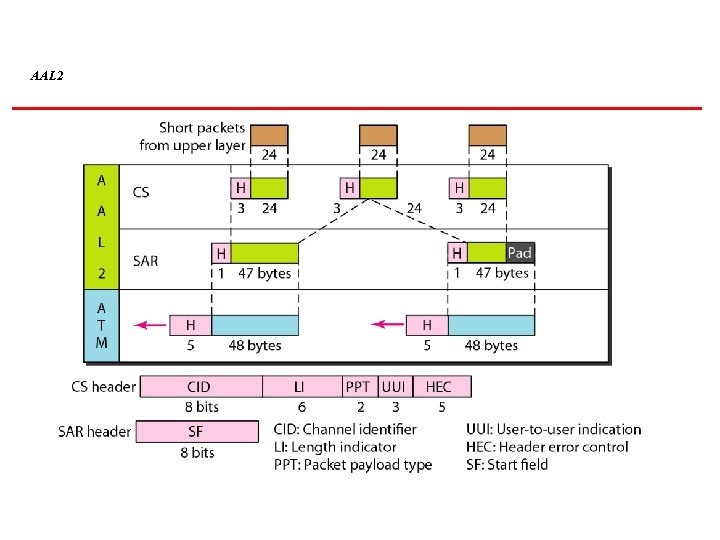
AAL 2

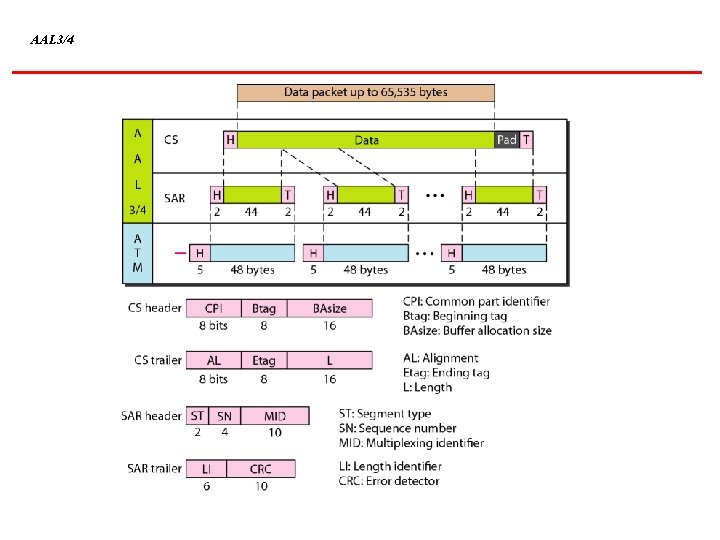
AAL 3/4

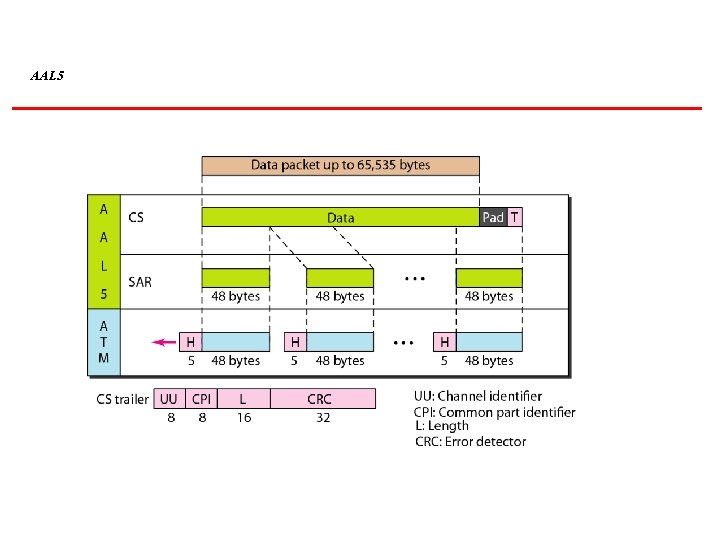
AAL 5

Cryptography

30 -1 INTRODUCTION Let us introduce the issues involved in cryptography. First, we need to define some terms; then we give some taxonomies. Topics discussed in this section: Definitions Two Categories 30. 74

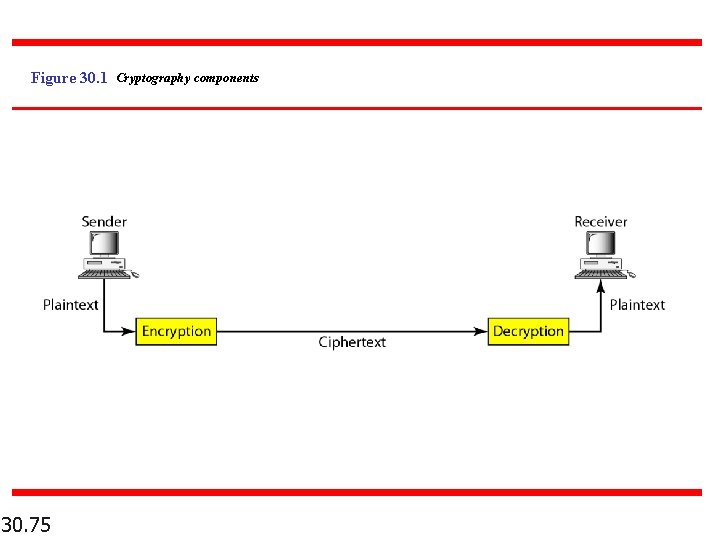
Figure 30. 1 Cryptography components 30. 75

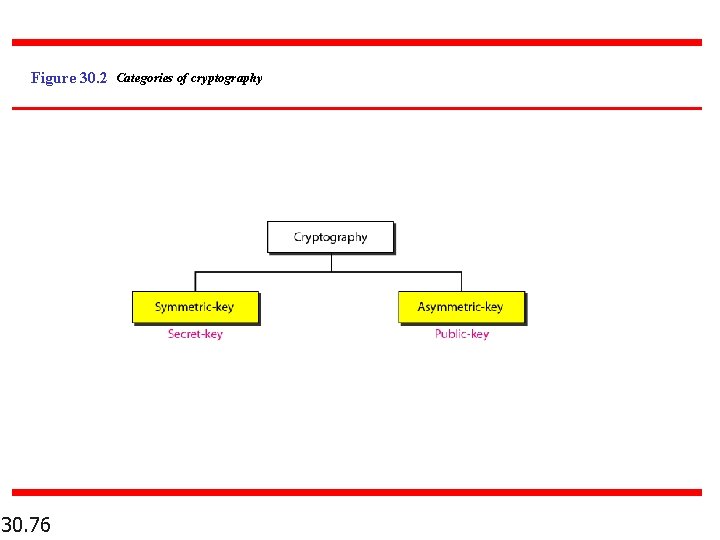
Figure 30. 2 Categories of cryptography 30. 76

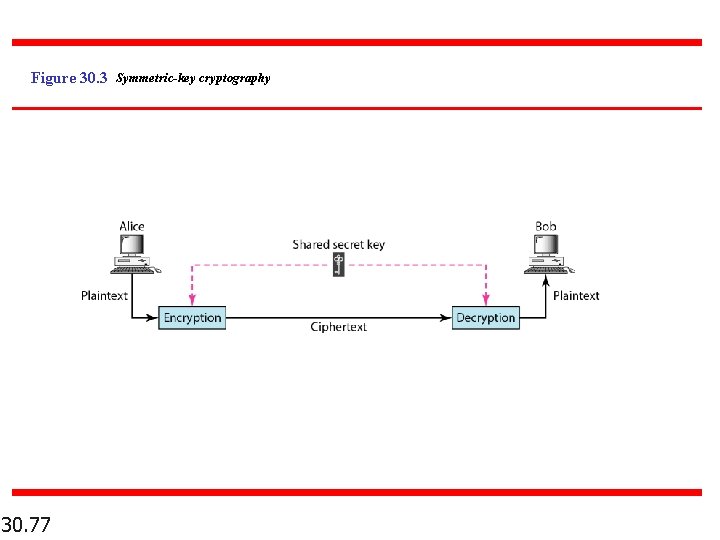
Figure 30. 3 Symmetric-key cryptography 30. 77

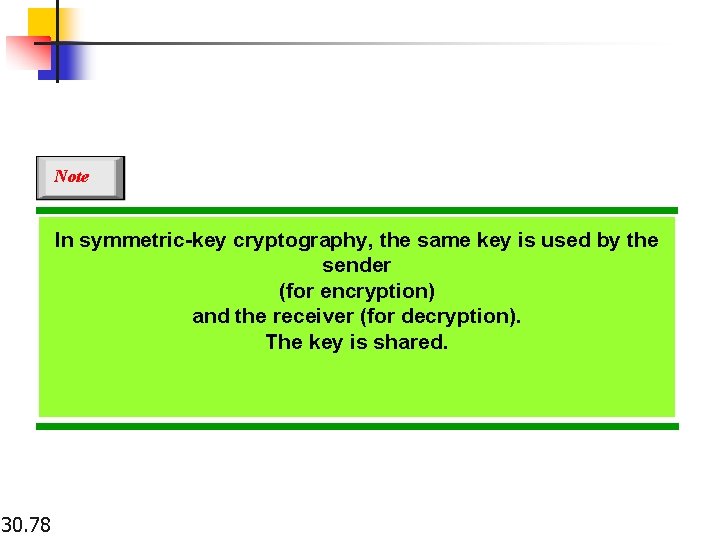
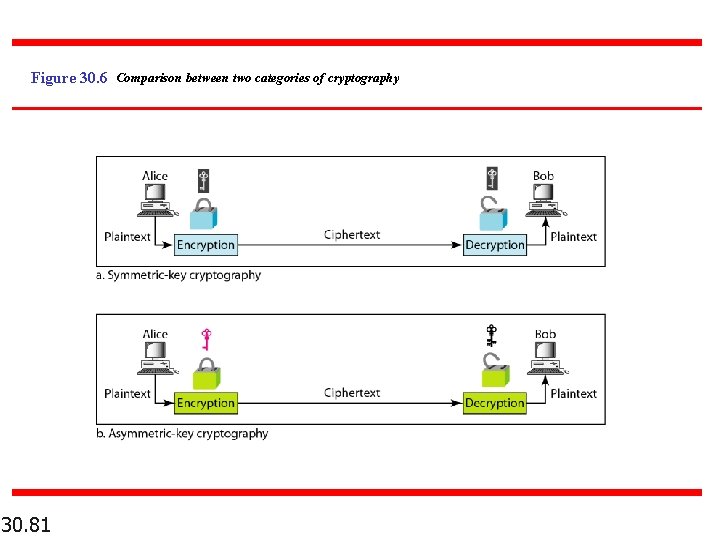
Note In symmetric-key cryptography, the same key is used by the sender (for encryption) and the receiver (for decryption). The key is shared. 30. 78

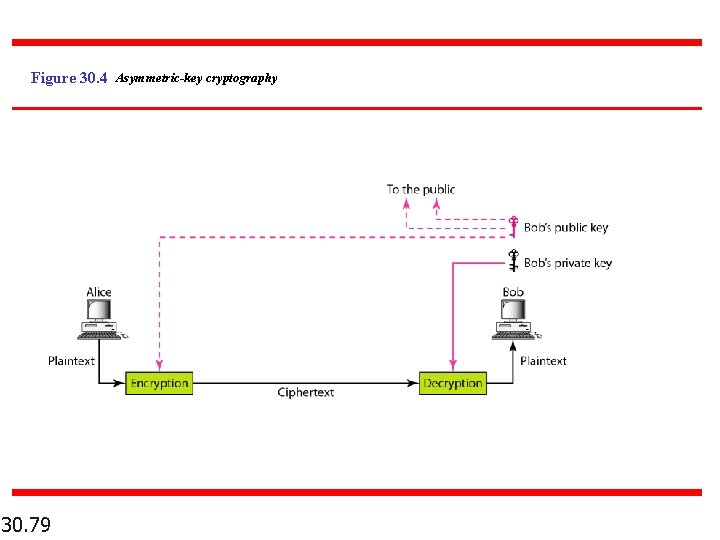
Figure 30. 4 Asymmetric-key cryptography 30. 79

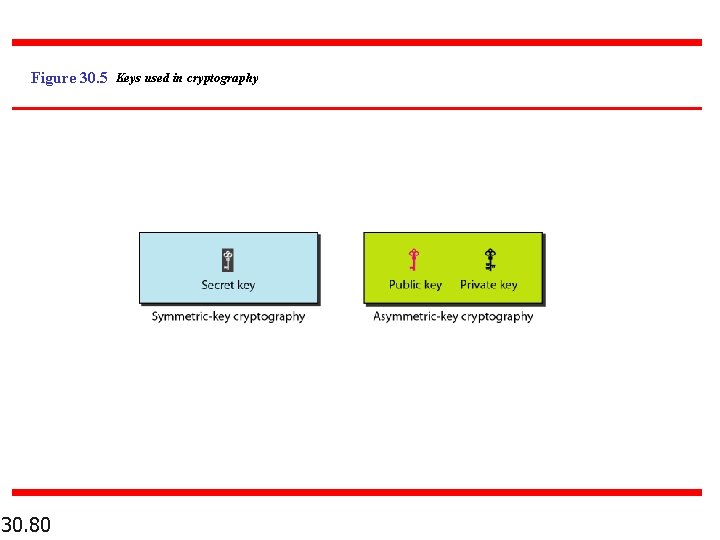
Figure 30. 5 Keys used in cryptography 30. 80

Figure 30. 6 Comparison between two categories of cryptography 30. 81

SYMMETRIC-KEY CRYPTOGRAPHY Symmetric-key cryptography started thousands of years ago when people needed to exchange secrets (for example, in a war). We still mainly use symmetric-key cryptography in our network security. Topics discussed in this section: Traditional Ciphers Simple Modern Ciphers Modern Round Ciphers Mode of Operation 30. 82

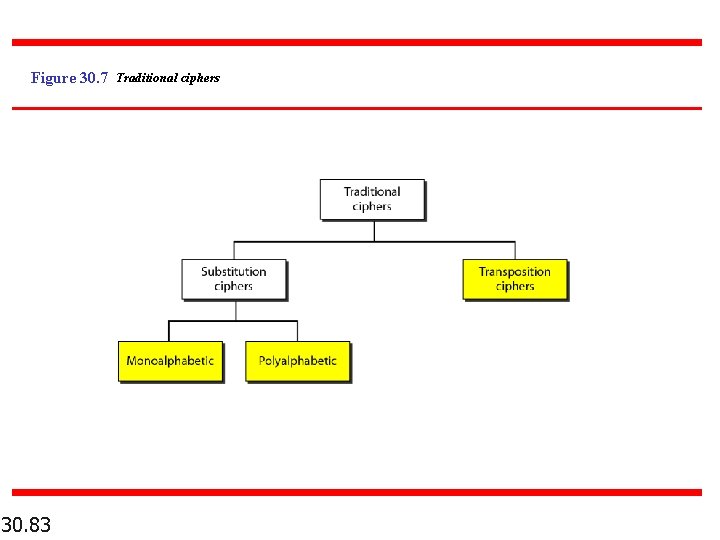
Figure 30. 7 Traditional ciphers 30. 83

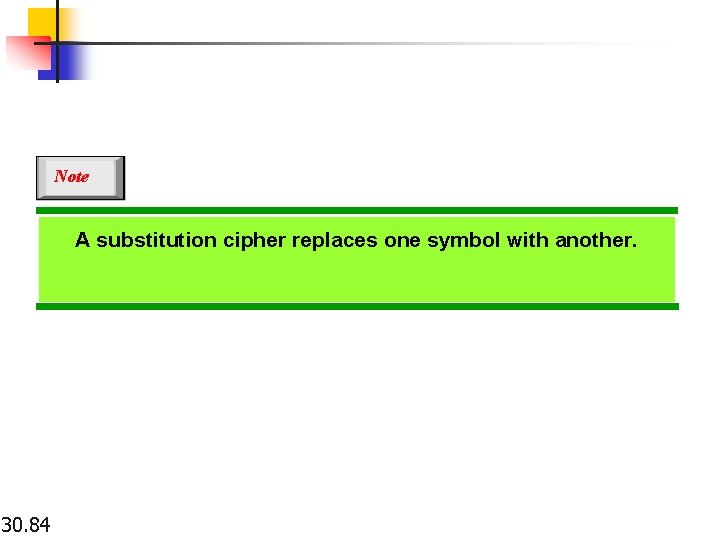
Note A substitution cipher replaces one symbol with another. 30. 84

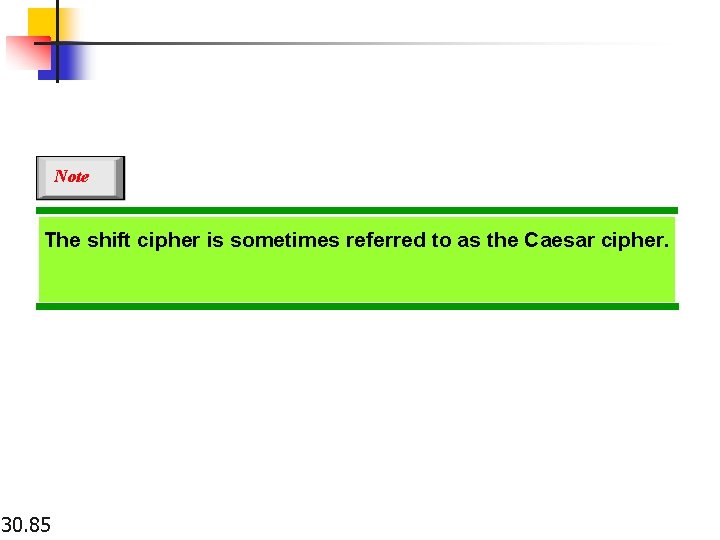
Note The shift cipher is sometimes referred to as the Caesar cipher. 30. 85

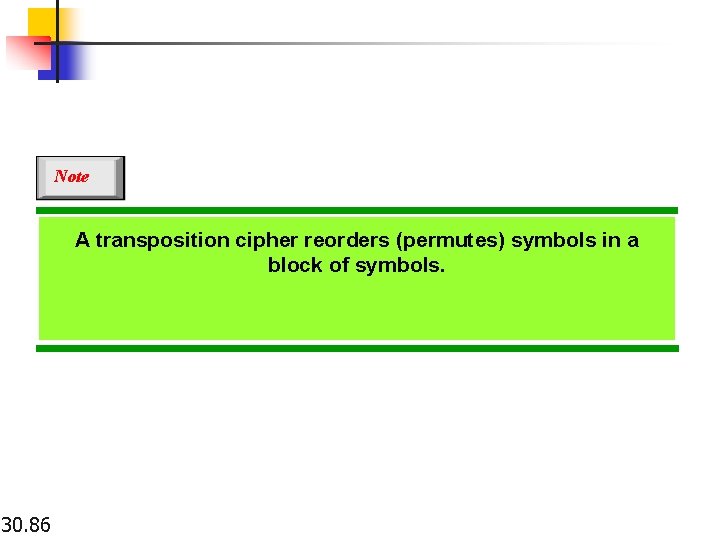
Note A transposition cipher reorders (permutes) symbols in a block of symbols. 30. 86

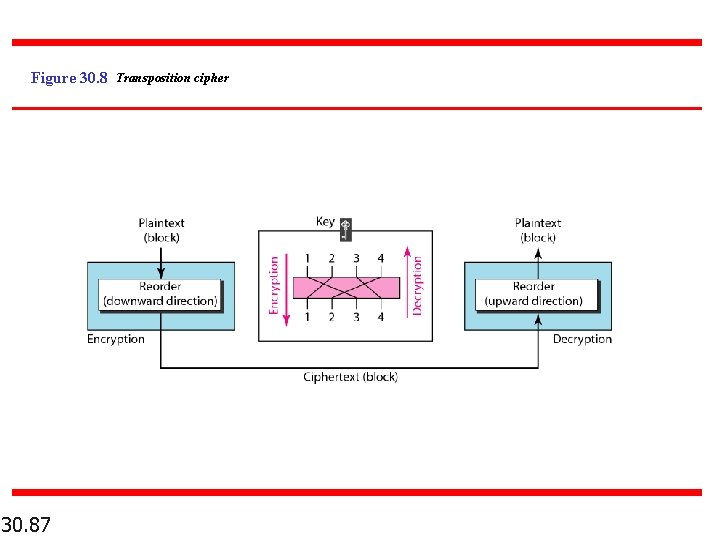
Figure 30. 8 Transposition cipher 30. 87

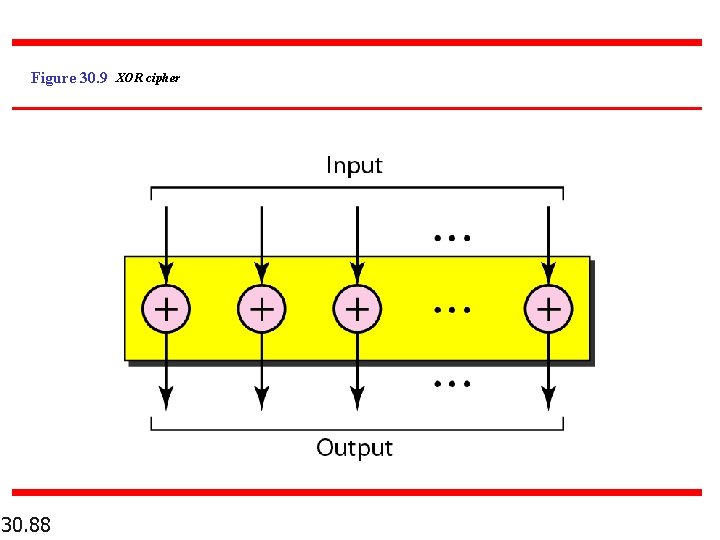
Figure 30. 9 XOR cipher 30. 88

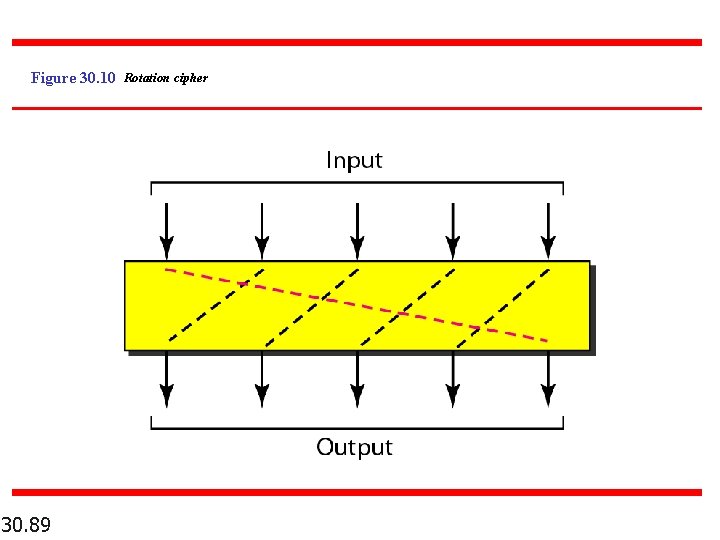
Figure 30. 10 Rotation cipher 30. 89

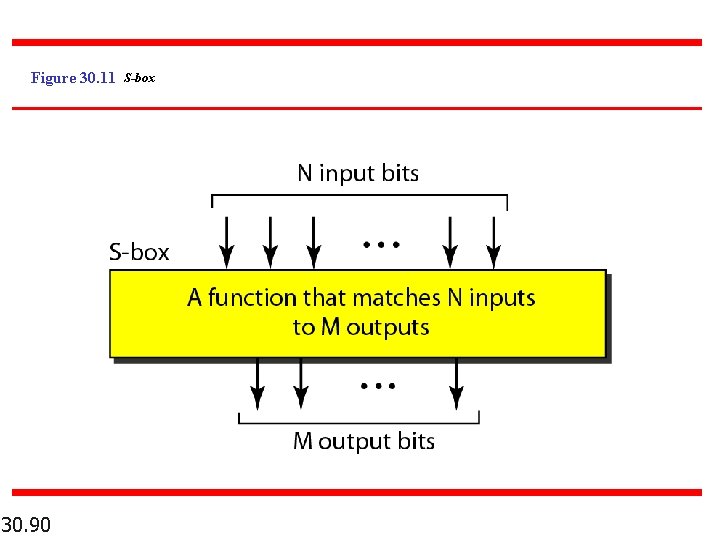
Figure 30. 11 S-box 30. 90

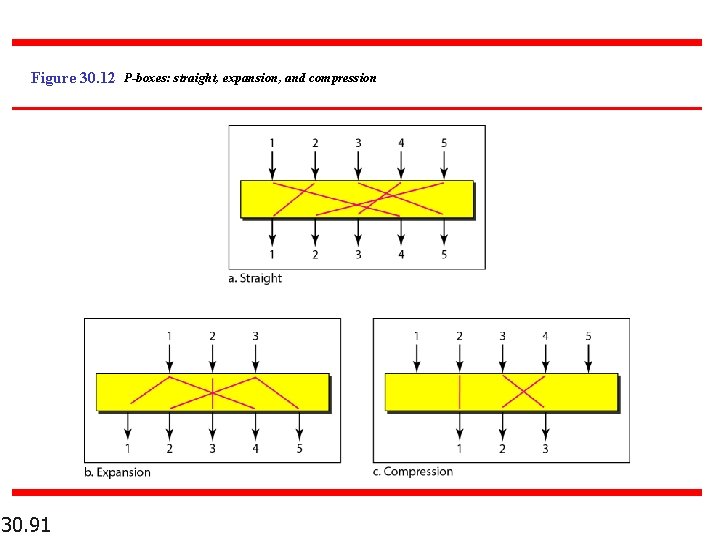
Figure 30. 12 P-boxes: straight, expansion, and compression 30. 91

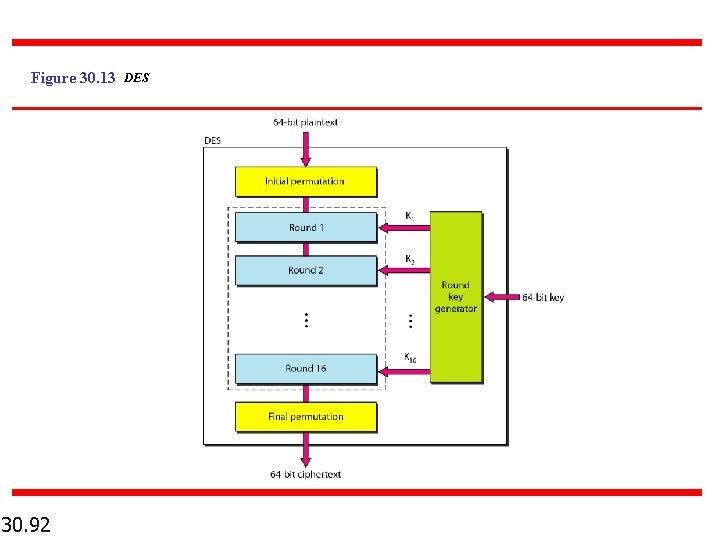
Figure 30. 13 DES 30. 92

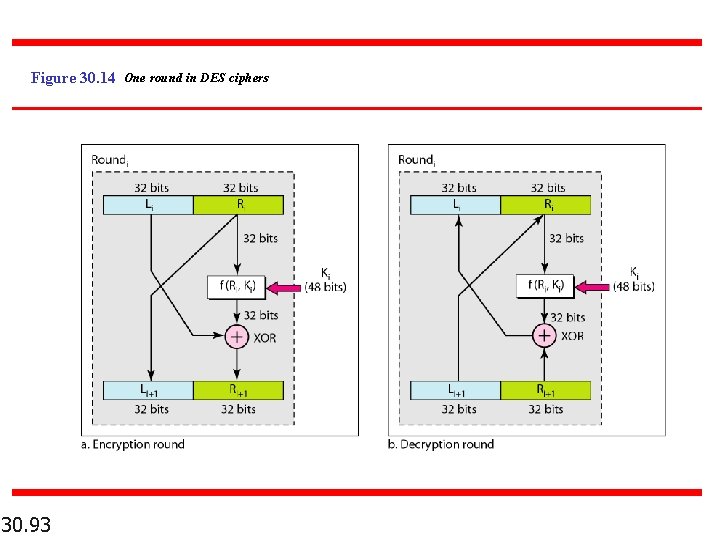
Figure 30. 14 One round in DES ciphers 30. 93

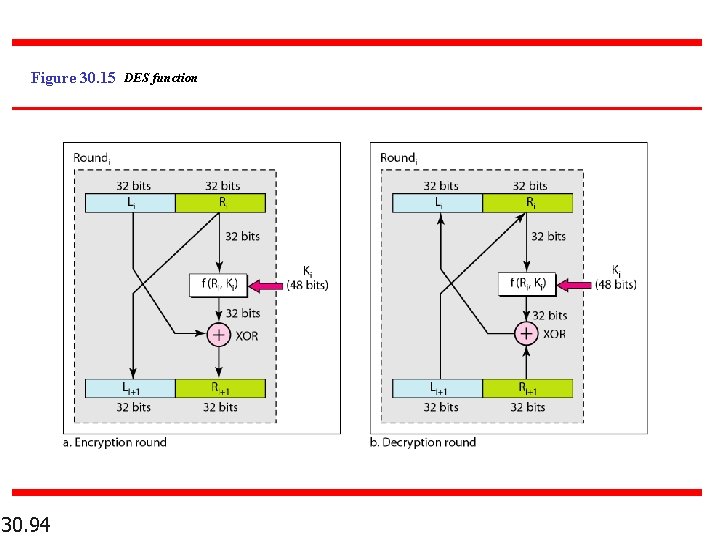
Figure 30. 15 DES function 30. 94

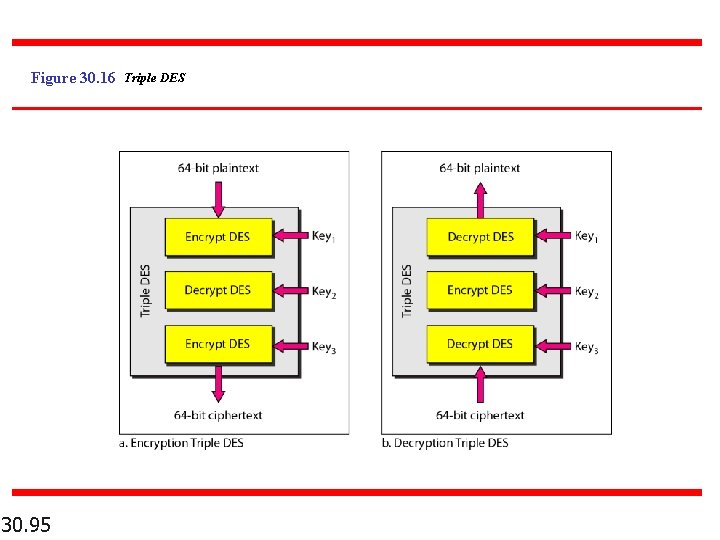
Figure 30. 16 Triple DES 30. 95

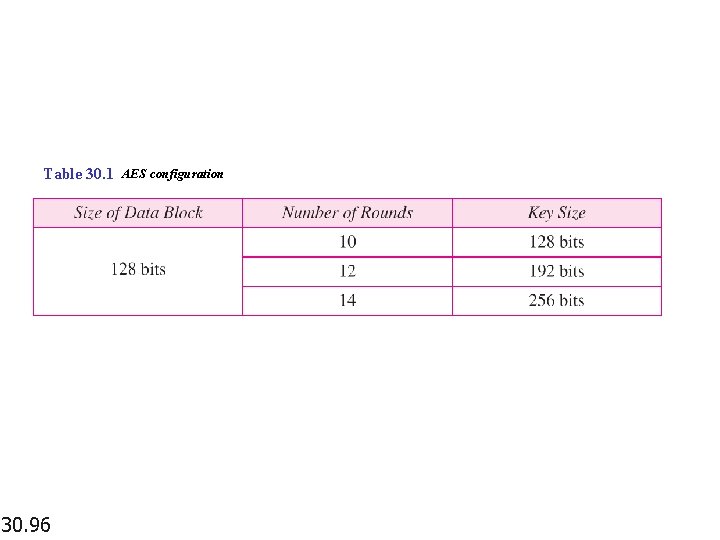
Table 30. 1 AES configuration 30. 96

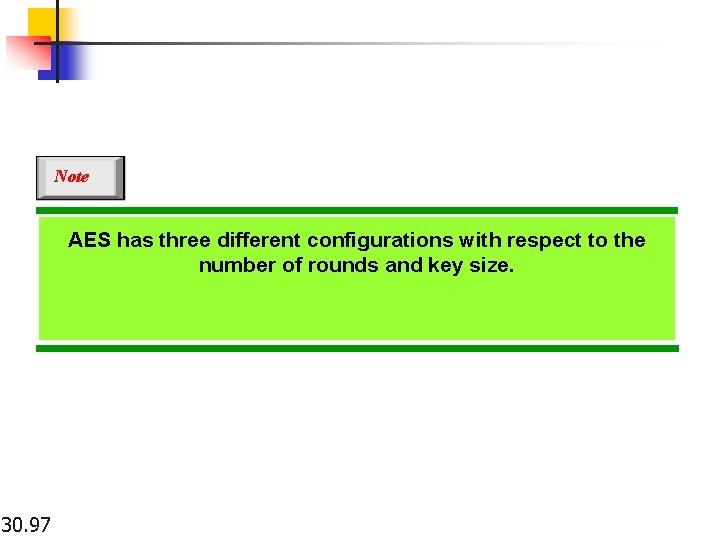
Note AES has three different configurations with respect to the number of rounds and key size. 30. 97

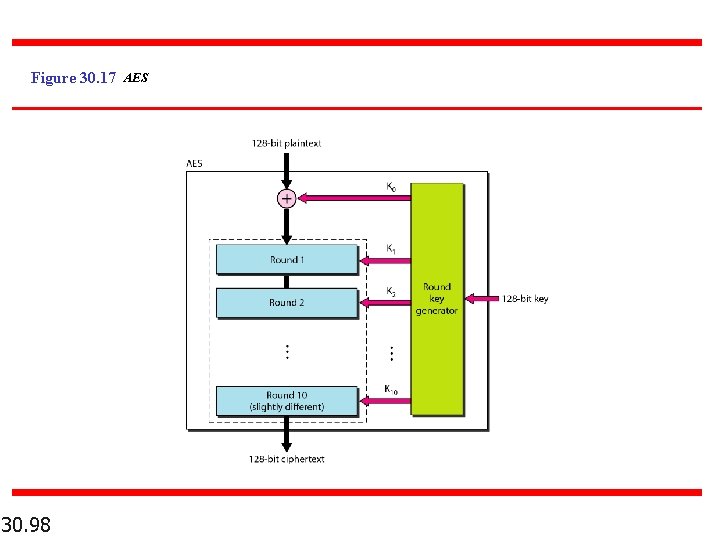
Figure 30. 17 AES 30. 98

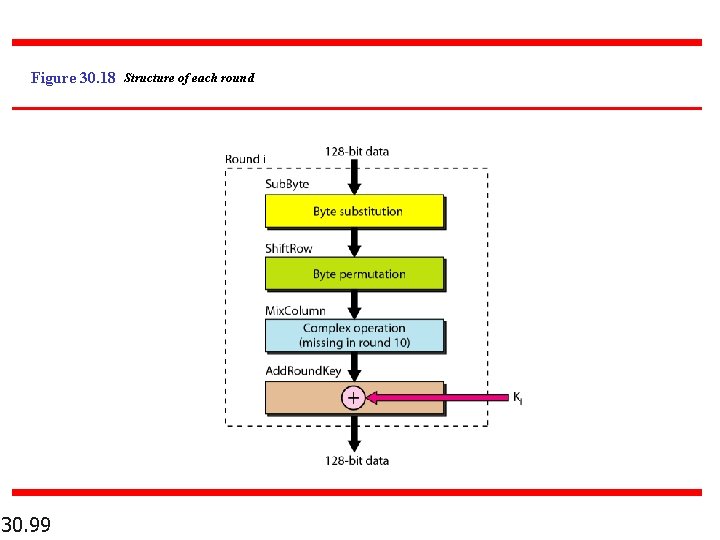
Figure 30. 18 Structure of each round 30. 99

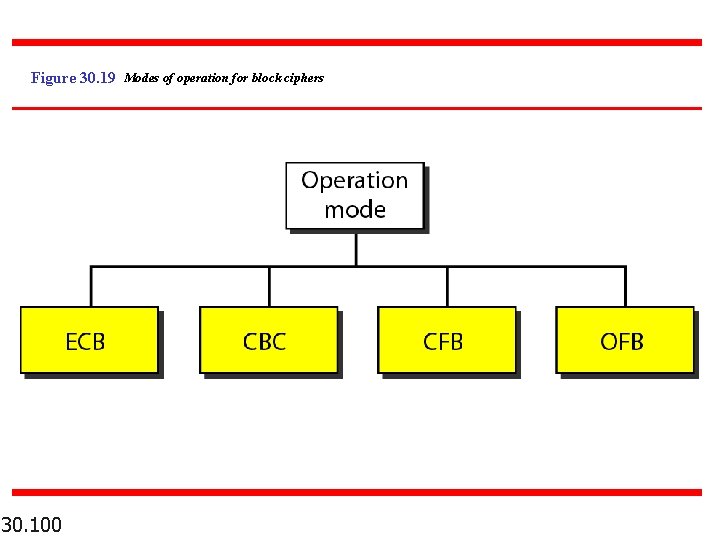
Figure 30. 19 Modes of operation for block ciphers 30. 100

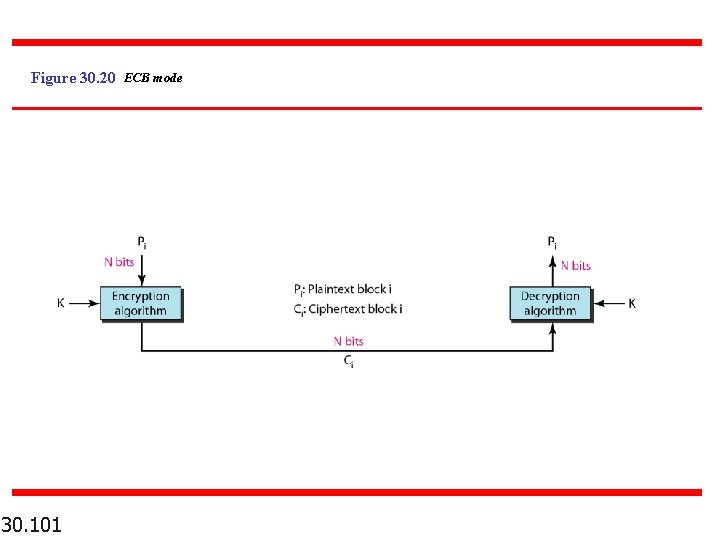
Figure 30. 20 ECB mode 30. 101

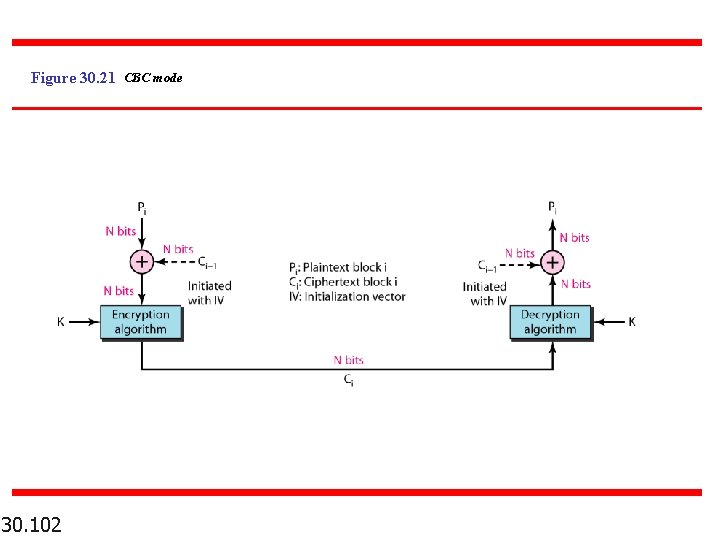
Figure 30. 21 CBC mode 30. 102

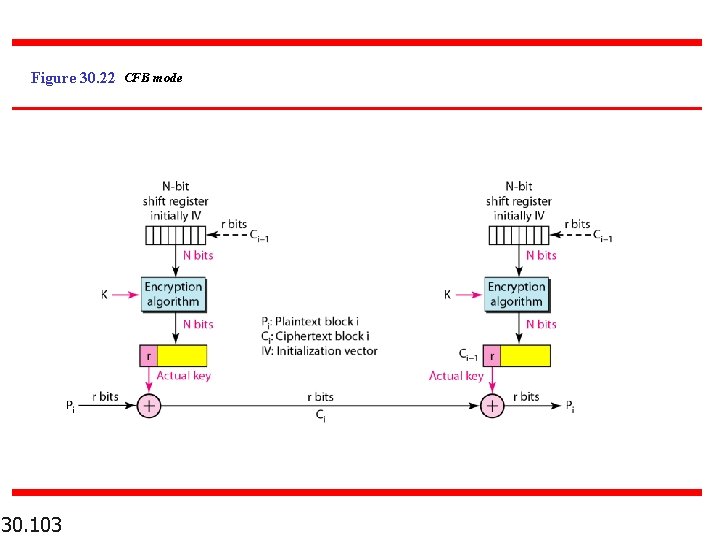
Figure 30. 22 CFB mode 30. 103

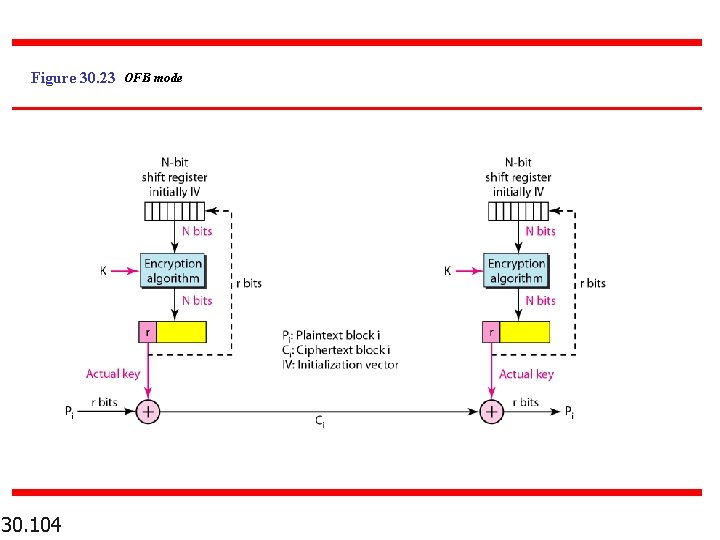
Figure 30. 23 OFB mode 30. 104

ASYMMETRIC-KEY CRYPTOGRAPHY An asymmetric-key (or public-key) cipher uses two keys: one private and one public. We discuss two algorithms: RSA and Diffie-Hellman. Topics discussed in this section: RSA Diffie-Hellman 30. 105

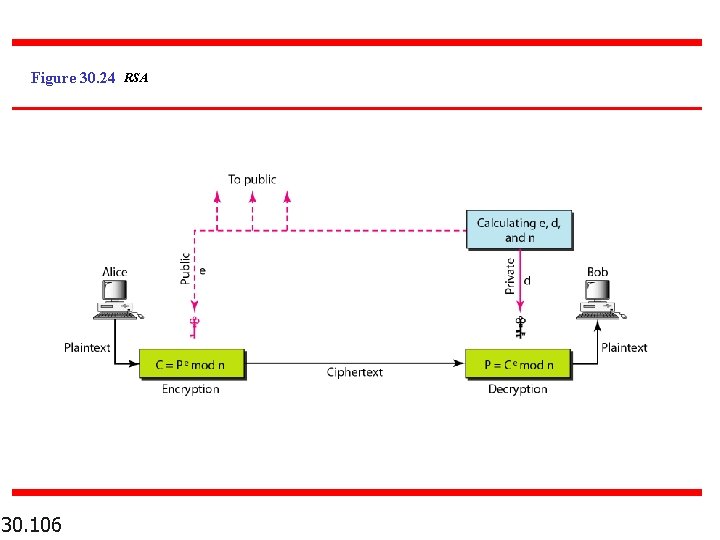
Figure 30. 24 RSA 30. 106

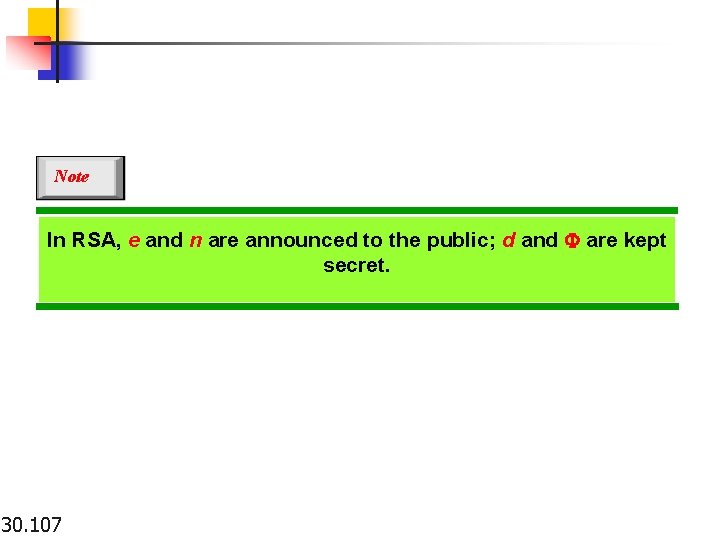
Note In RSA, e and n are announced to the public; d and F are kept secret. 30. 107

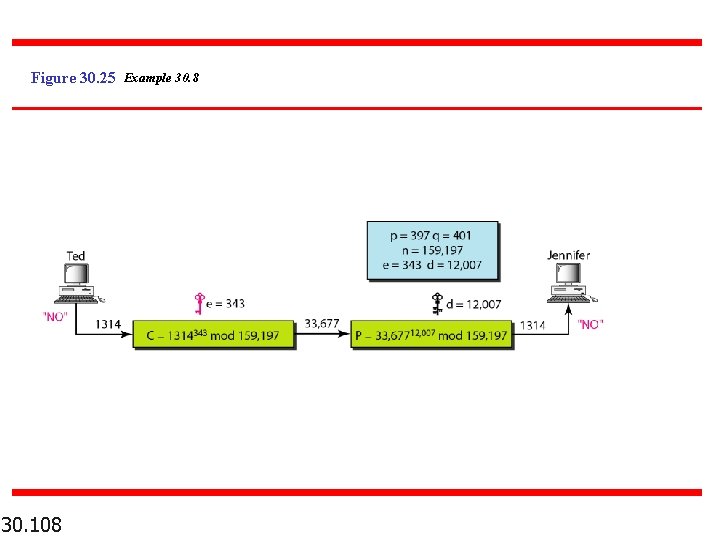
Figure 30. 25 Example 30. 8 30. 108

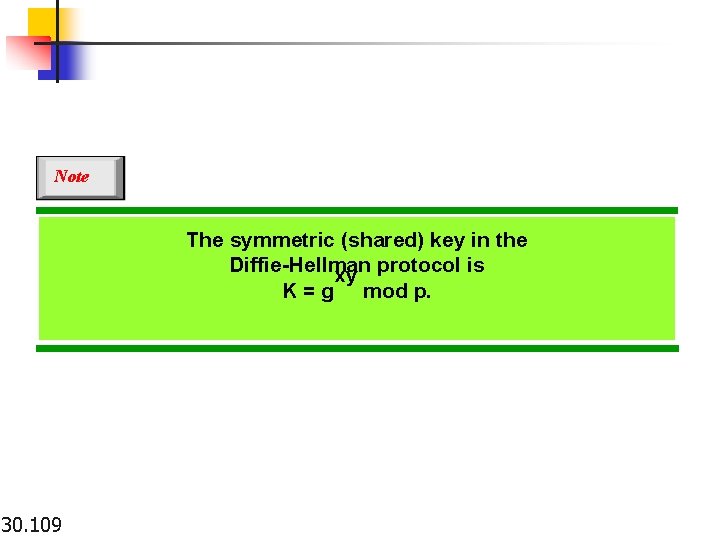
Note The symmetric (shared) key in the Diffie-Hellman xy protocol is K = g mod p. 30. 109

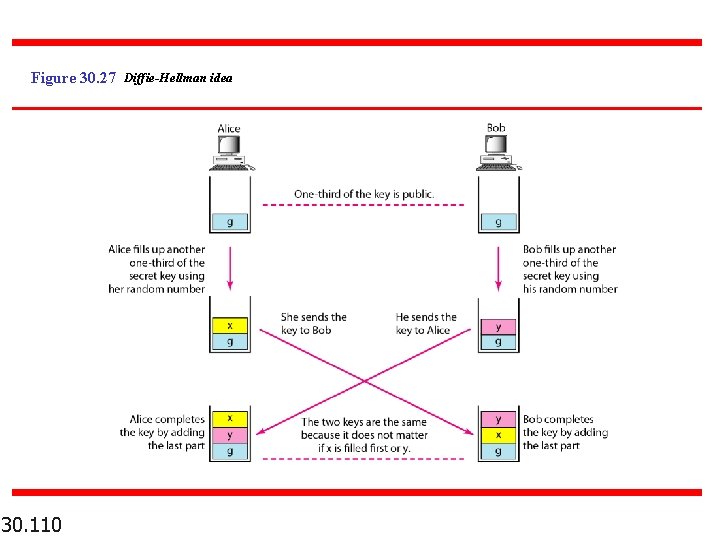
Figure 30. 27 Diffie-Hellman idea 30. 110

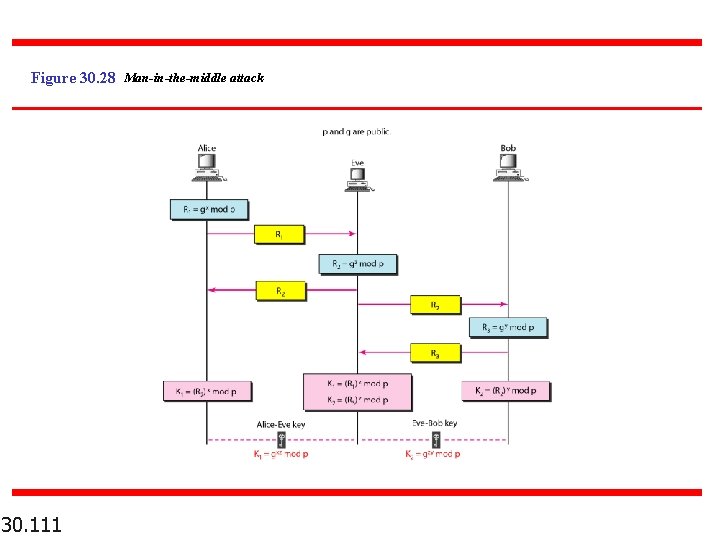
Figure 30. 28 Man-in-the-middle attack 30. 111

Network Security

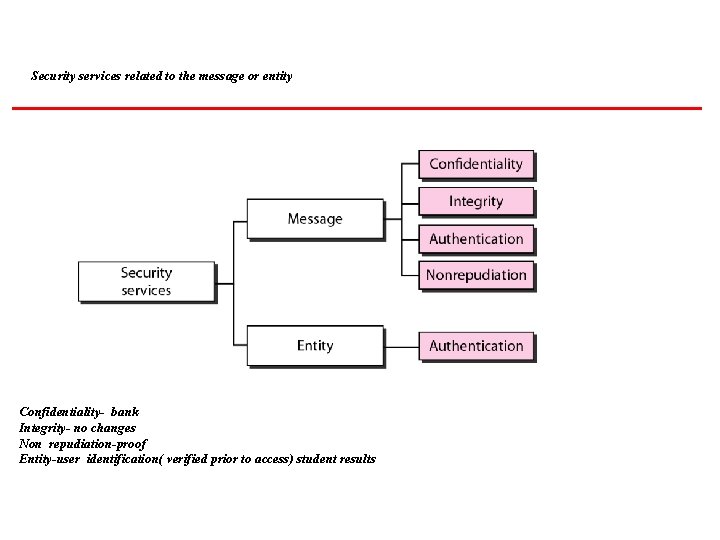
SECURITY SERVICES Network security can provide five services. Four of these services are related to the message exchanged using the network. The fifth service provides entity authentication or identification.

Security services related to the message or entity Confidentiality- bank Integrity- no changes Non repudiation-proof Entity-user identification( verified prior to access) student results

MESSAGE CONFIDENTIALITY The concept of how to achieve message confidentiality or privacy has not changed for thousands of years. The message must be encrypted at the sender site and decrypted at the receiver site. This can be done using either symmetric-key cryptography or asymmetric-key cryptography. Topics discussed in this section: Confidentiality with Symmetric-Key Cryptography Confidentiality with Asymmetric-Key Cryptography 31. 115

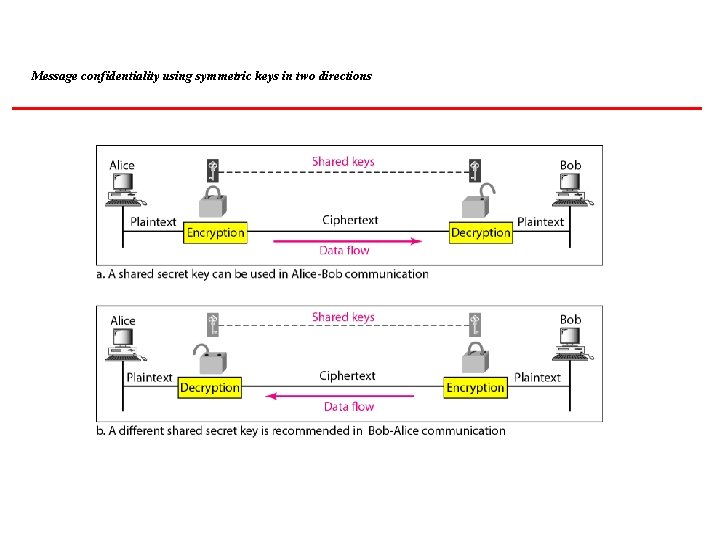
Message confidentiality using symmetric keys in two directions

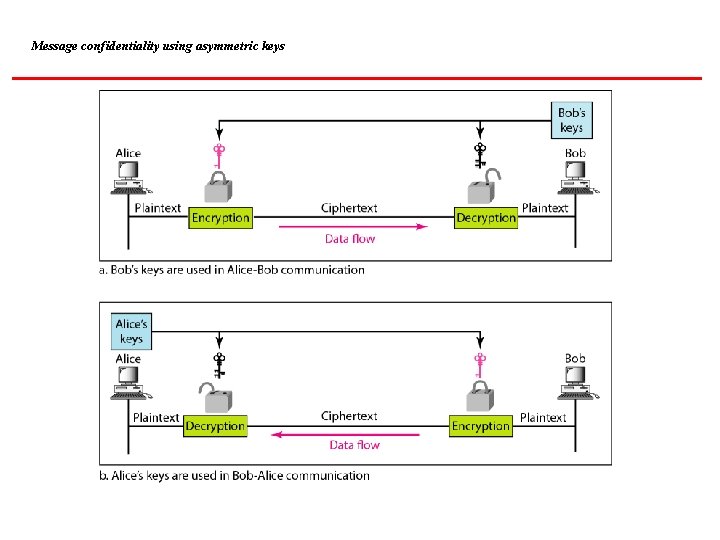
Message confidentiality using asymmetric keys

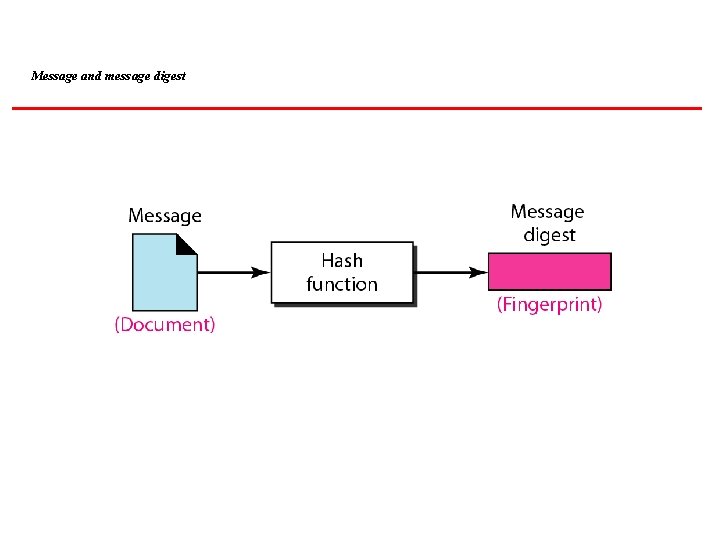
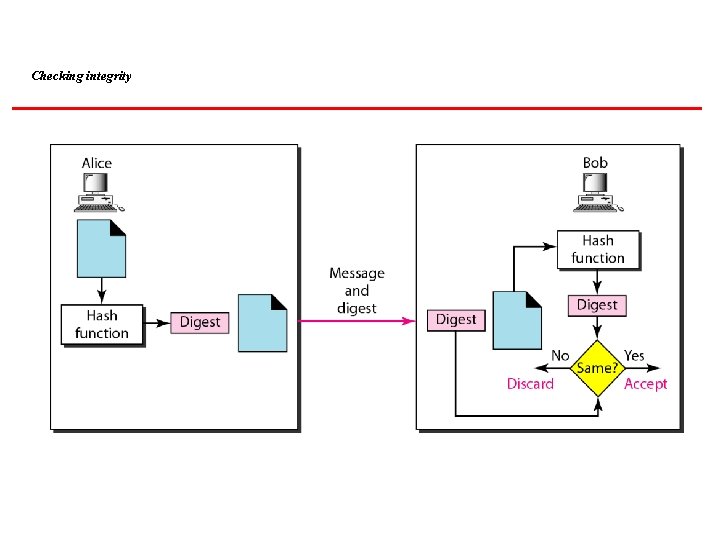
MESSAGE INTEGRITY Encryption and decryption provide secrecy, or confidentiality, but not integrity. However, on occasion we may not even need secrecy, but instead must have integrity. Topics discussed in this section: Document and Fingerprint Message and Message Digest Creating and Checking the Digest Hash Function Criteria Hash Algorithms: SHA-1

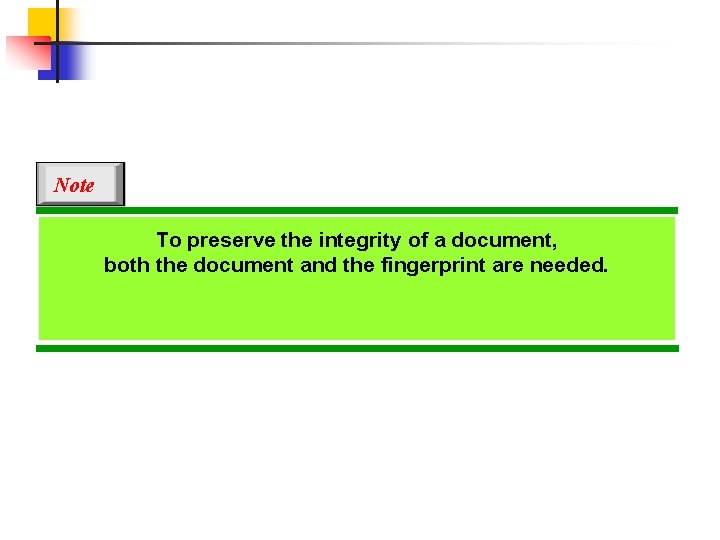
Note To preserve the integrity of a document, both the document and the fingerprint are needed.

Message and message digest

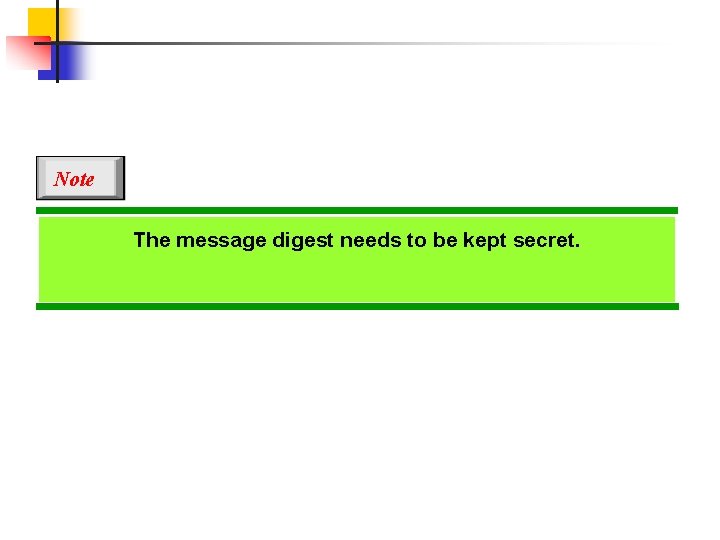
Note The message digest needs to be kept secret.

Checking integrity

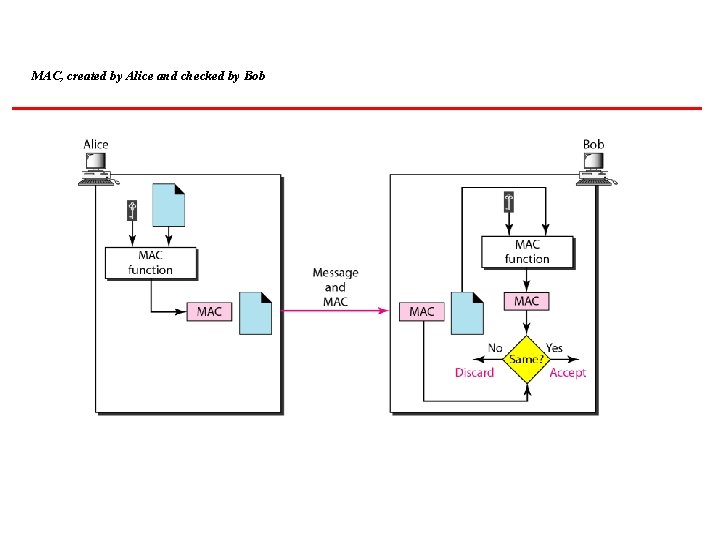
MESSAGE AUTHENTICATION A hash function per se cannot provide authentication. The digest created by a hash function can detect any modification in the message, but not authentication. Topics discussed in this section: MAC (Message authentication code)

MAC, created by Alice and checked by Bob

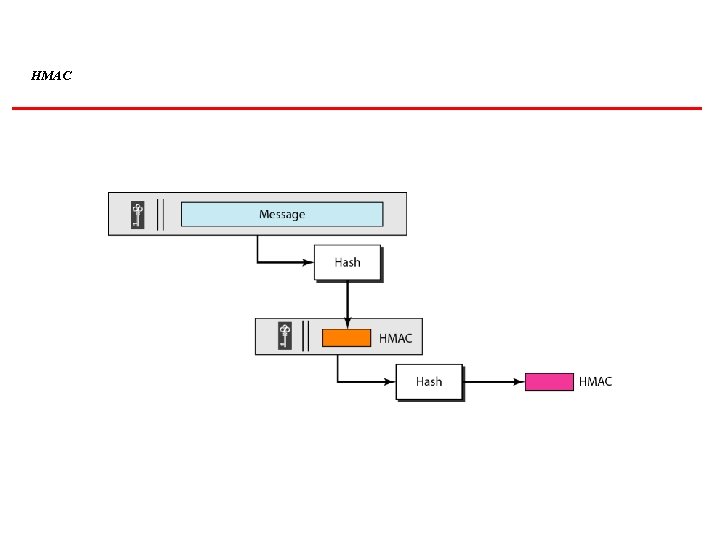
HMAC

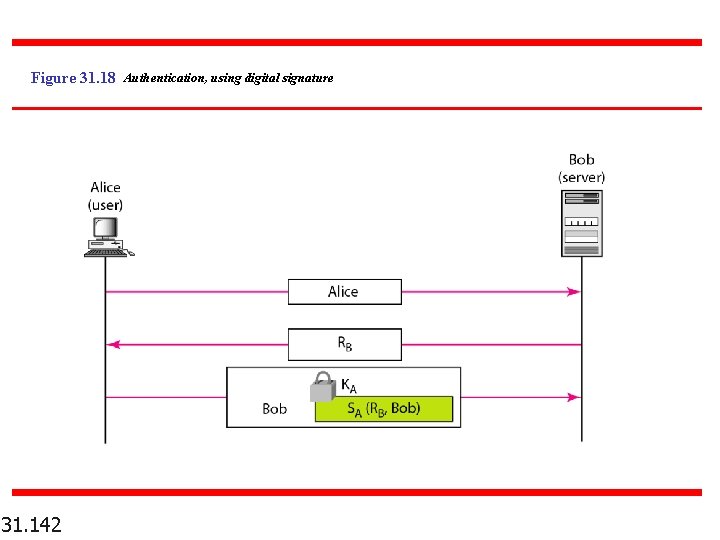
MESSAGE NONREPUDIATION or DIGITAL SIGNATURE When Alice sends a message to Bob, Bob needs to check the authenticity of the sender; he needs to be sure that the message comes from Alice and not Eve. Bob can ask Alice to sign the message electronically. In other words, an electronic signature can prove the authenticity of Alice as the sender of the message. We refer to this type of signature as a digital signature. Topics discussed in this section: Comparison Need for Keys Process

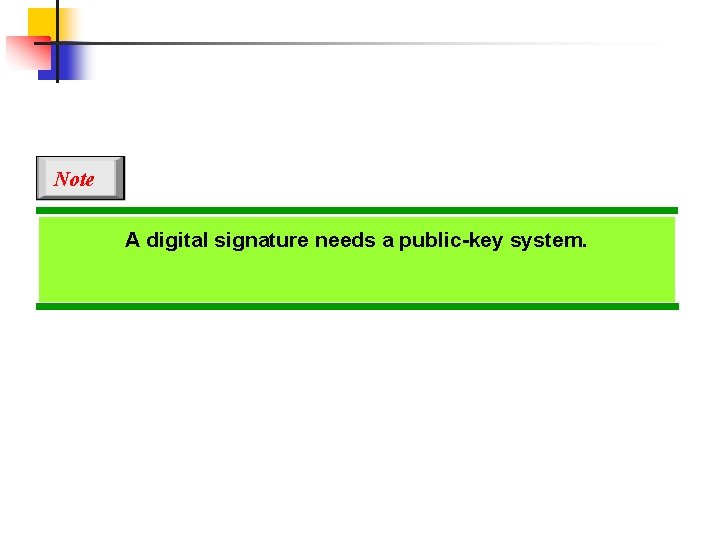
Note A digital signature needs a public-key system.

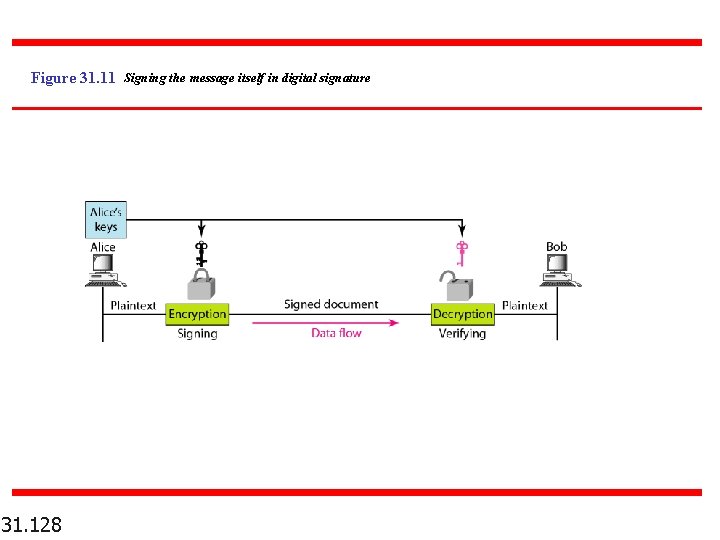
Figure 31. 11 Signing the message itself in digital signature 31. 128

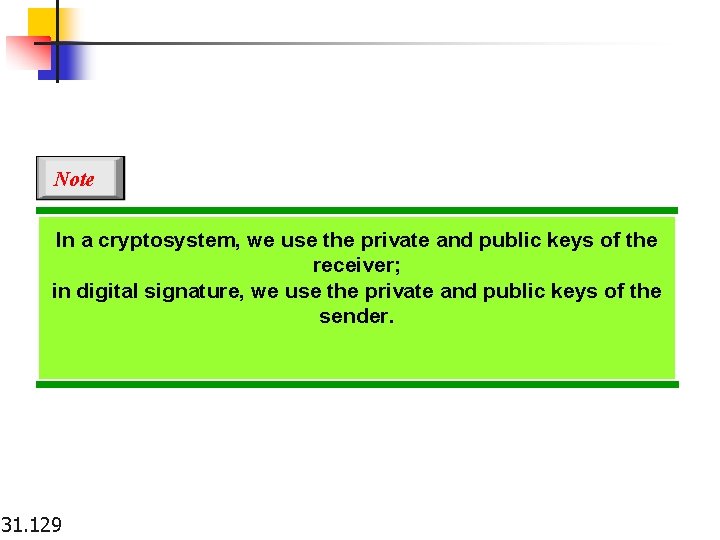
Note In a cryptosystem, we use the private and public keys of the receiver; in digital signature, we use the private and public keys of the sender. 31. 129

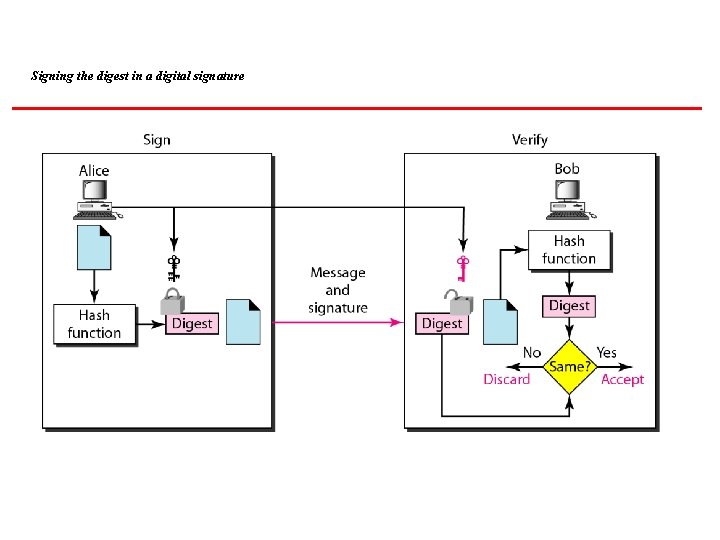
Signing the digest in a digital signature

Note A digital signature today provides message integrity.

Note Digital signature provides message authentication.

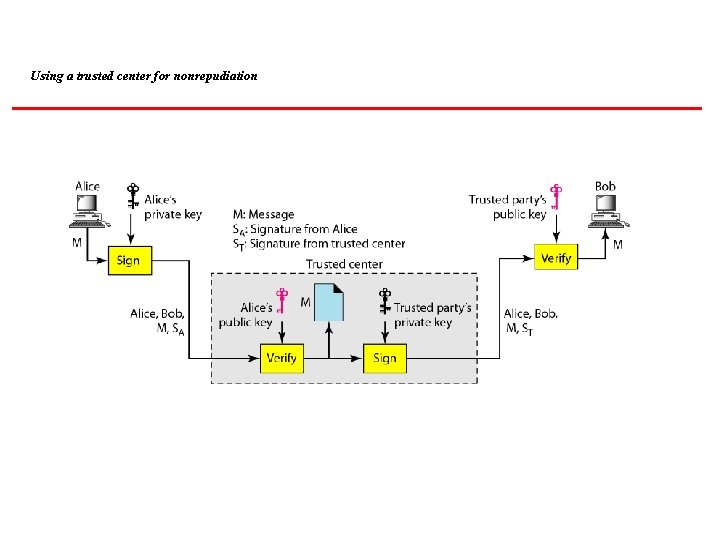
Using a trusted center for nonrepudiation

Note Nonrepudiation can be provided using a trusted party.

ENTITY AUTHENTICATION Entity authentication is a technique designed to let one party prove the identity of another party. An entity can be a person, a process, a client, or a server. The entity whose identity needs to be proved is called the claimant; the party that tries to prove the identity of the claimant is called the verifier. Topics discussed in this section: Passwords Challenge-Response

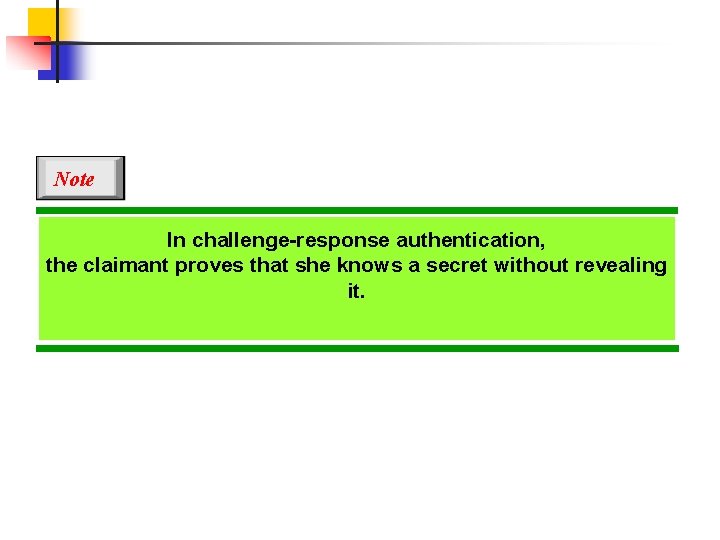
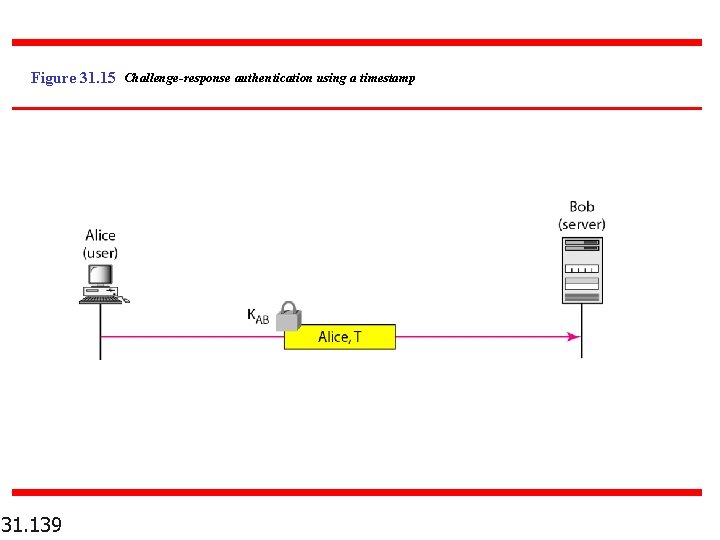
Note In challenge-response authentication, the claimant proves that she knows a secret without revealing it.

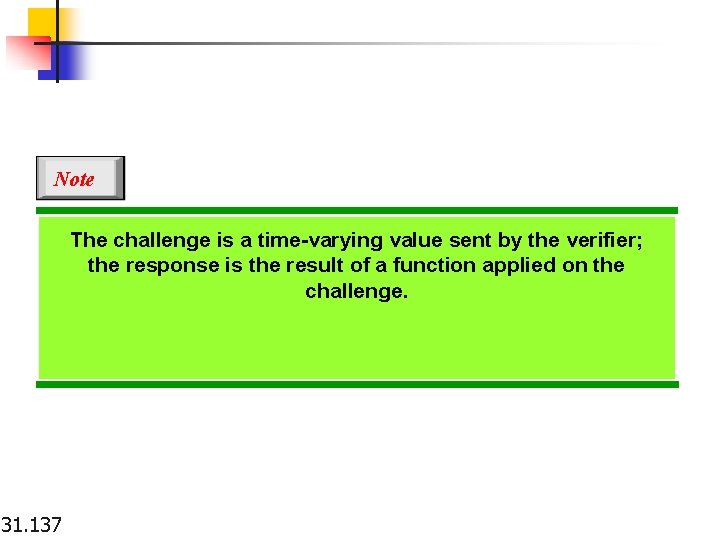
Note The challenge is a time-varying value sent by the verifier; the response is the result of a function applied on the challenge. 31. 137

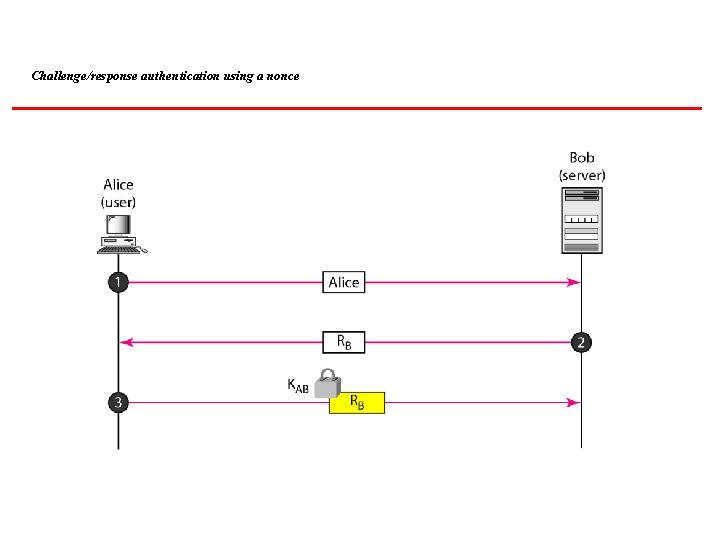
Challenge/response authentication using a nonce

Figure 31. 15 Challenge-response authentication using a timestamp 31. 139

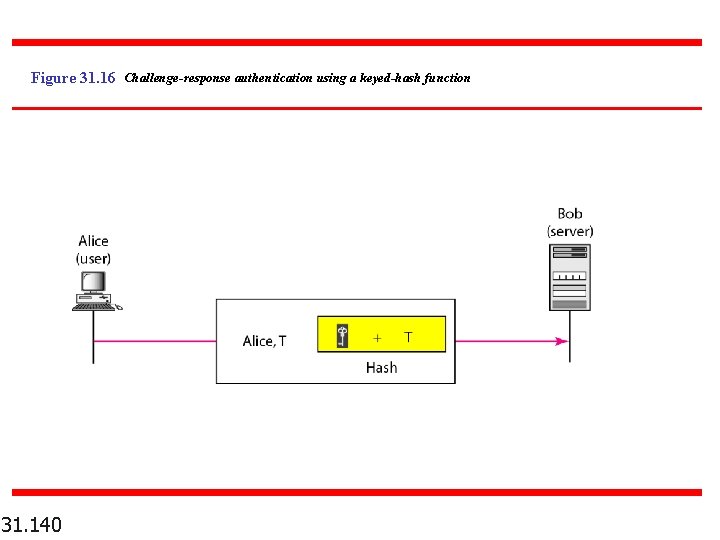
Figure 31. 16 Challenge-response authentication using a keyed-hash function 31. 140

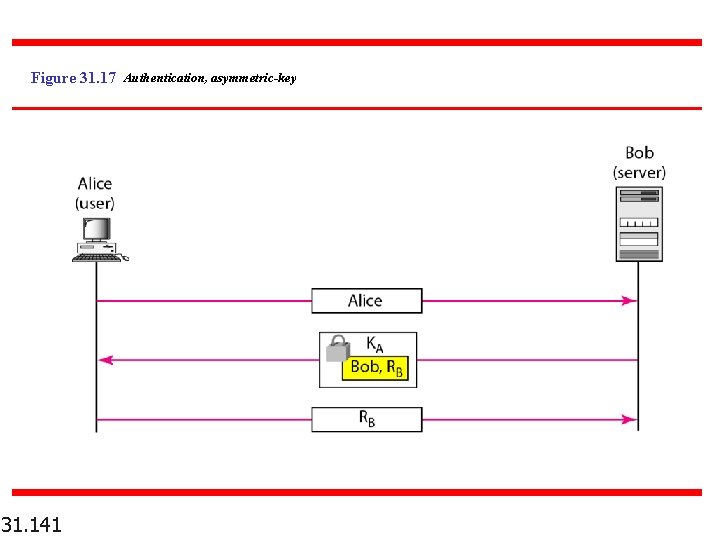
Figure 31. 17 Authentication, asymmetric-key 31. 141

Figure 31. 18 Authentication, using digital signature 31. 142

31 -7 KEY MANAGEMENT We never discussed how secret keys in symmetric-key cryptography and how public keys in asymmetric-key cryptography are distributed and maintained. In this section, we touch on these two issues. We first discuss the distribution of symmetric keys; we then discuss the distribution of asymmetric keys. Topics discussed in this section: Symmetric-Key Distribution Public-Key Distribution 31. 143

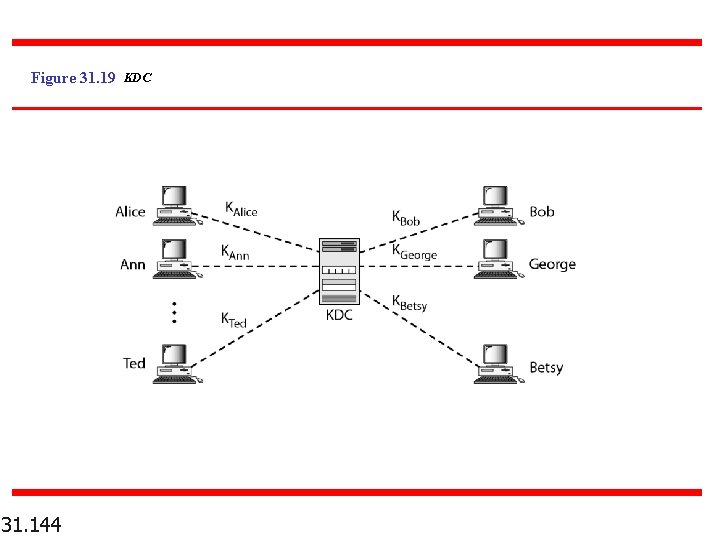
Figure 31. 19 KDC 31. 144

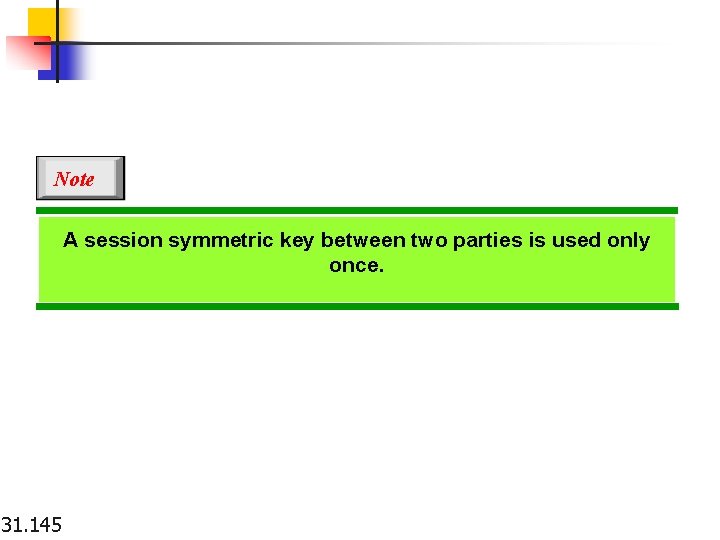
Note A session symmetric key between two parties is used only once. 31. 145

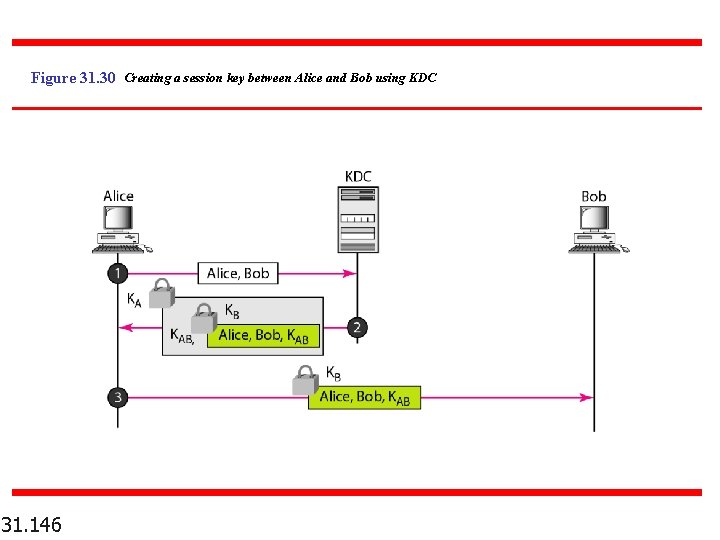
Figure 31. 30 Creating a session key between Alice and Bob using KDC 31. 146

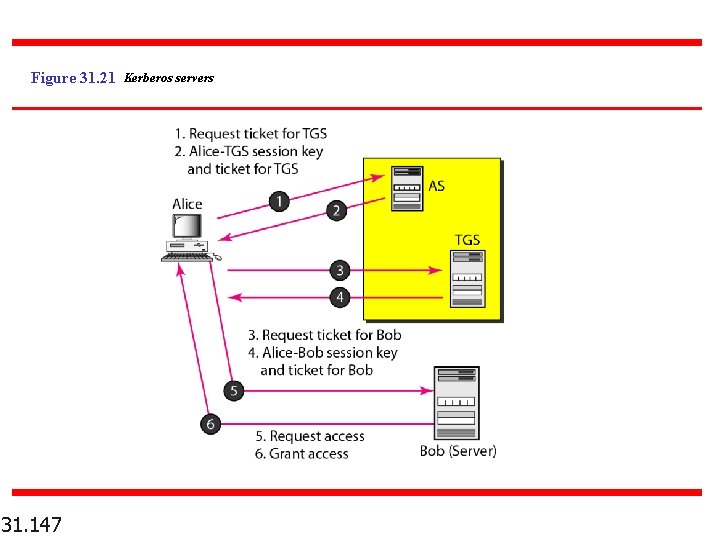
Figure 31. 21 Kerberos servers 31. 147

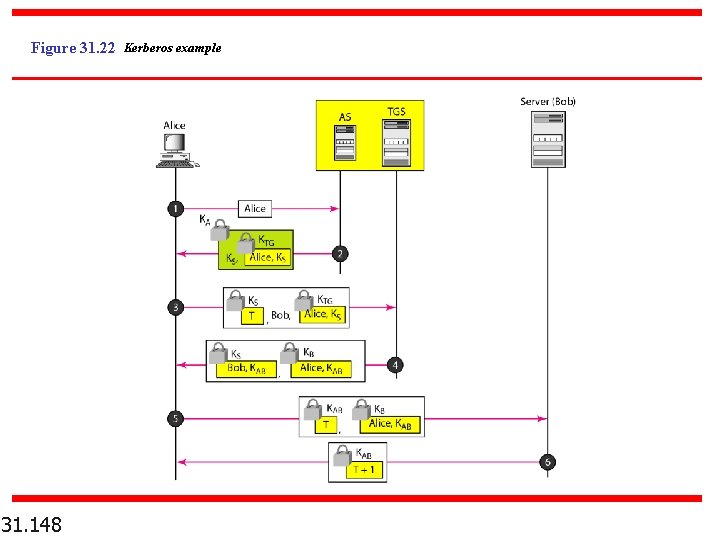
Figure 31. 22 Kerberos example 31. 148

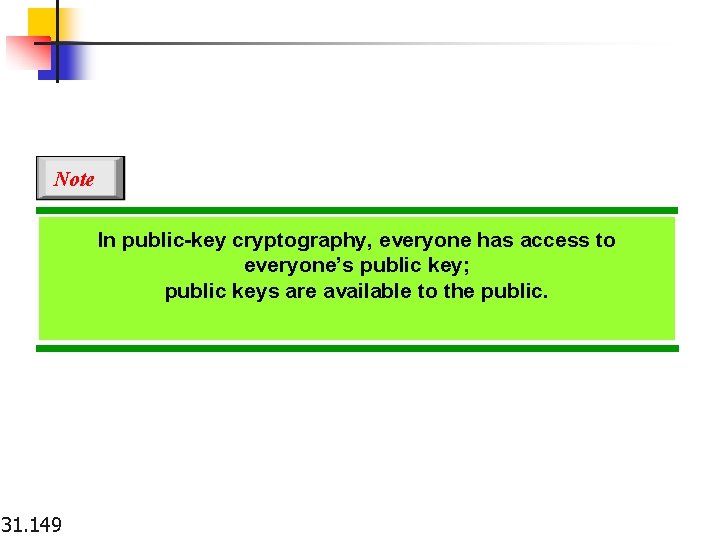
Note In public-key cryptography, everyone has access to everyone’s public key; public keys are available to the public. 31. 149

Figure 31. 23 Announcing a public key 31. 150

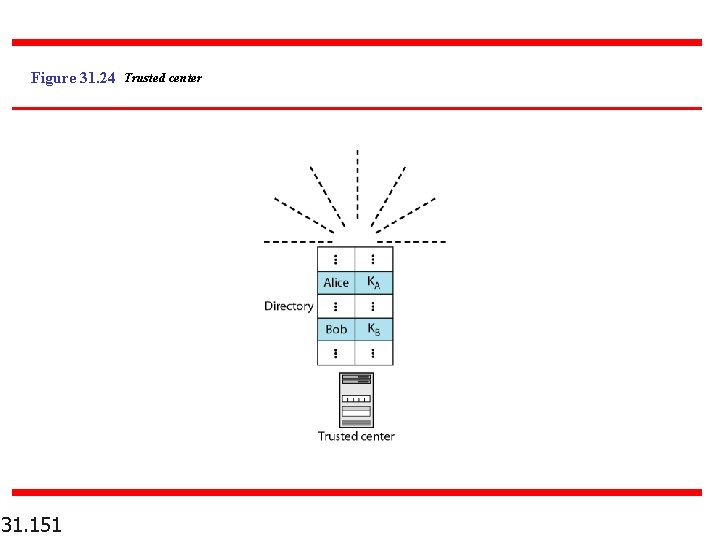
Figure 31. 24 Trusted center 31. 151

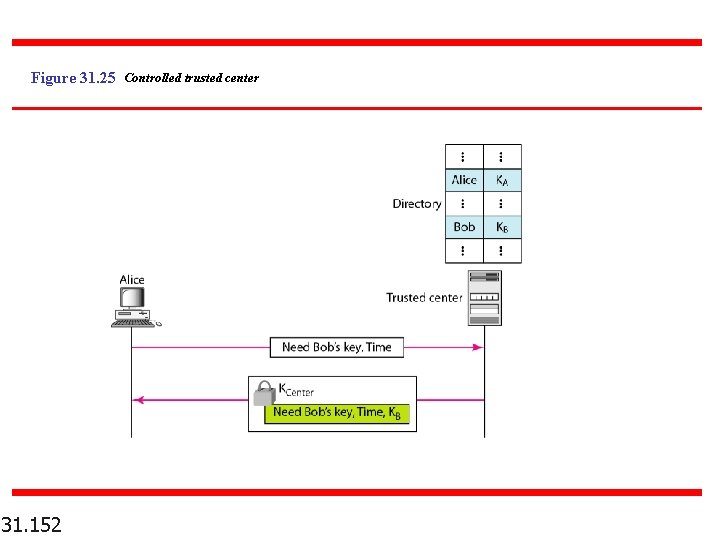
Figure 31. 25 Controlled trusted center 31. 152

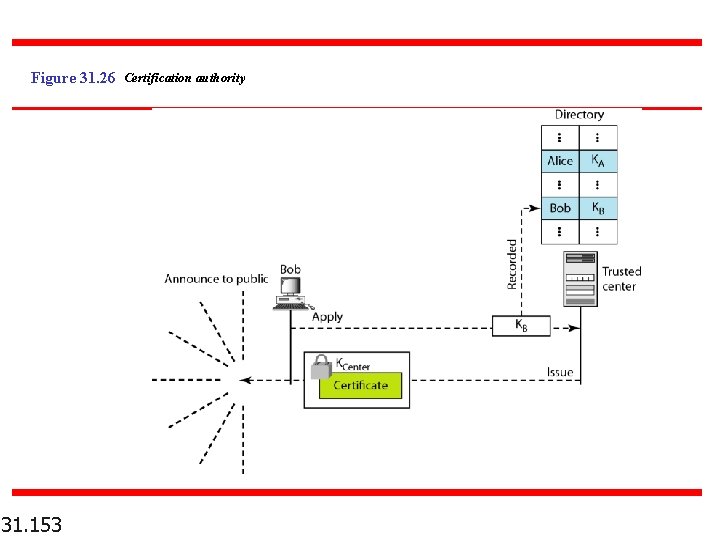
Figure 31. 26 Certification authority 31. 153

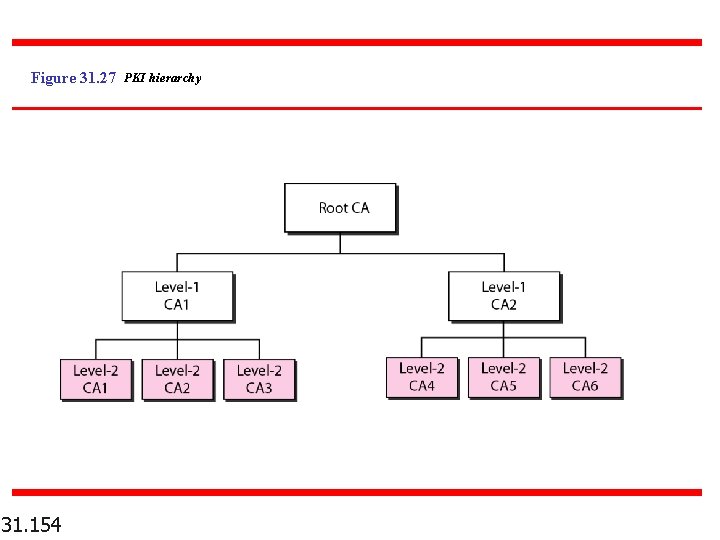
Figure 31. 27 PKI hierarchy 31. 154

23. 155