WTLS Wireless Transport Layer Security Youngho Choung Yhchoungcs










![WTLS Specifications Optimized full handshaking Server. Hello Certificate [Change. Cipher. Spec] Finished [Chang. Cipher. WTLS Specifications Optimized full handshaking Server. Hello Certificate [Change. Cipher. Spec] Finished [Chang. Cipher.](https://slidetodoc.com/presentation_image_h/8a6934ea3e90a9c89fec0d58577e90ff/image-19.jpg)


- Slides: 22

WTLS (Wireless Transport Layer Security) Youngho Choung Yhchoung@cs. uh. edu Youngho Choung

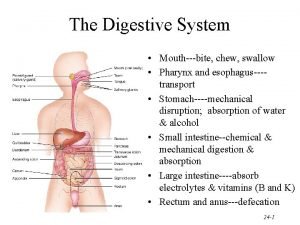
Contents Why we need WTLS? What is TLS (SSL 3. 0) ? WTLS Functions Security Algorithm WTLS specifications Other Technologies Youngho Choung

Why we need WTLS ? (1/2) What can we do through the Cell Phone? ¾ Communication ¾ Using Internet ¾ E-commerce ¾ On-line banking ¾ Trading Stock ¾ Electric Cash ¾ Electric ID ¾ Watching movie, take a picture… etc… Youngho Choung

Why we need WTLS ? (2/2) Environment problems We need Security Solutions Youngho Choung

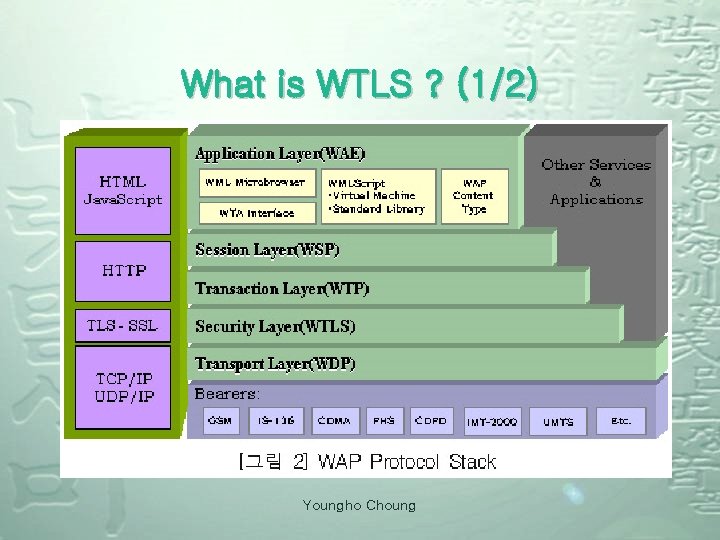
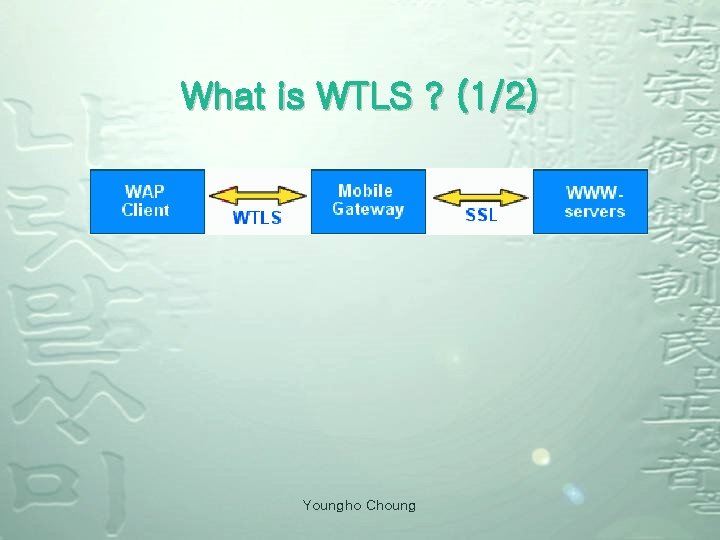
What is WTLS ? (1/2) Youngho Choung

What is WTLS ? (1/2) Youngho Choung

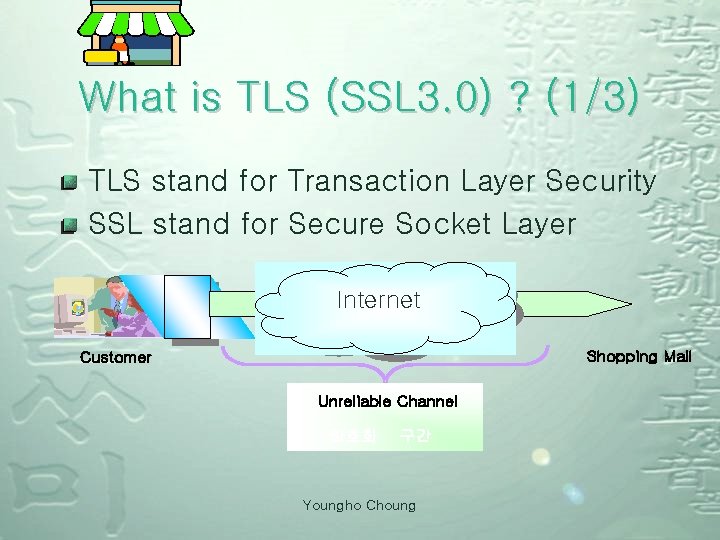
What is TLS (SSL 3. 0) ? (1/3) TLS stand for Transaction Layer Security SSL stand for Secure Socket Layer 웹 브 라 우 저 인터넷 Internet 인터넷 Shopping Mall Customer Unreliable 불안전한 Channel 암호화 구간 Youngho Choung

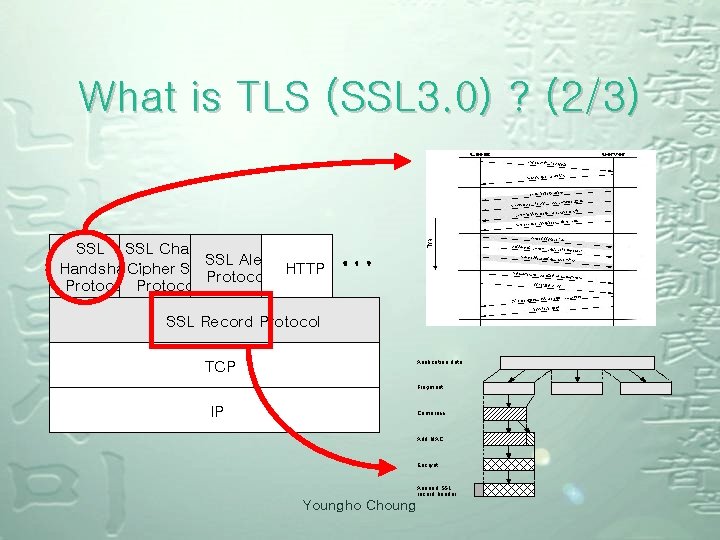
What is TLS (SSL 3. 0) ? (2/3) SSL Change SSL Alert Handshake Cipher Spec HTTP Protocol SSL Record Protocol TCP Application data Fragment IP Compress Add MAC Encrypt Append SSL record header Youngho Choung

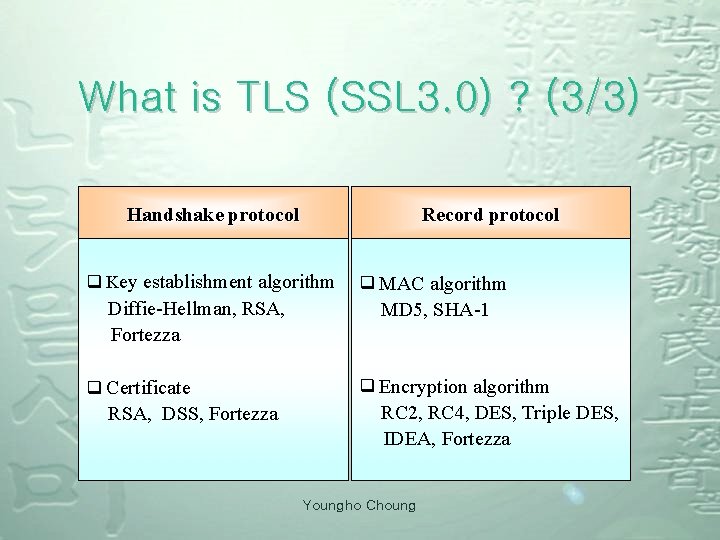
What is TLS (SSL 3. 0) ? (3/3) Handshake protocol Record protocol q Key establishment algorithm Diffie-Hellman, RSA, Fortezza q Certificate RSA, DSS, Fortezza q MAC algorithm MD 5, SHA-1 q Encryption algorithm RC 2, RC 4, DES, Triple DES, IDEA, Fortezza Youngho Choung

WTLS Functions Data Integrity Privacy Authentication Do. S (Denial of Service) protection Optional Youngho Choung

Security Algorithm Hash Function Any Length Plain Text Hash Function MD 5, MD 4, Hash, SHA-1, etc Dyejsmldmnf Fix length Encrypted Text mdfnmd fnfnfnlkfekkfe ekfkjefjefelfee -------- Youngho Choung , sdd

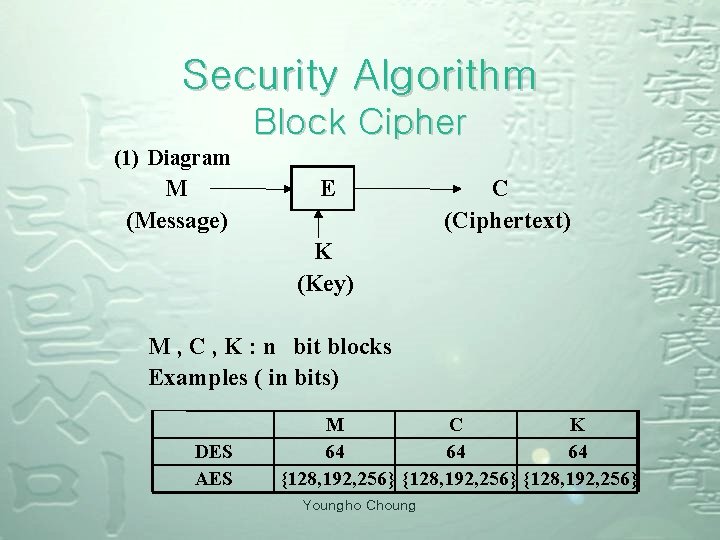
Security Algorithm Block Cipher (1) Diagram M (Message) E C (Ciphertext) K (Key) M , C , K : n bit blocks Examples ( in bits) DES AES M C K 64 64 64 {128, 192, 256} Youngho Choung

Security Algorithm Block Cipher (2) Encryption : Combination of Substitution & Permutation Decryption : Inverse of Encryption (3) Classical ciphers a. Permutation Ciphers b. Substitution Cipher : Caesar Cipher Youngho Choung

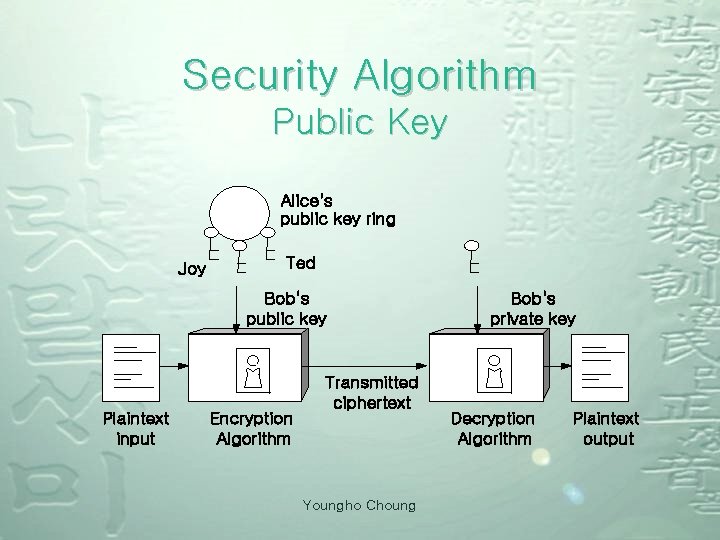
Security Algorithm Public Key distribution is difficult ¾ Tow Communicants already share a key or have the use of a key distribution center Characteristic ¾ (public) encryption key ≠ (private) decryption key Youngho Choung

Security Algorithm Public Key Alice's public key ring Joy Ted Bob's public key Plaintext input Encryption Algorithm Transmitted ciphertext Youngho Choung Bob's private key Decryption Algorithm Plaintext output

WTLS Specifications (1/5) Handshaking protocol ¾ Full handshaking protocol ¾ Abbreviated handshaking protocol ¾ Optimized handshaking protocol Alert protocol Change Cipher spec protocol Record protocol Youngho Choung

WTLS Specifications Full handshaking Youngho Choung

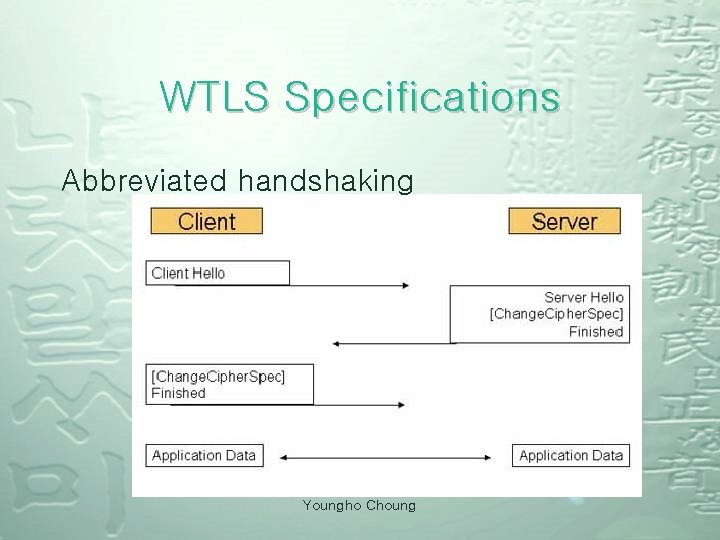
WTLS Specifications Abbreviated handshaking Youngho Choung
![WTLS Specifications Optimized full handshaking Server Hello Certificate Change Cipher Spec Finished Chang Cipher WTLS Specifications Optimized full handshaking Server. Hello Certificate [Change. Cipher. Spec] Finished [Chang. Cipher.](https://slidetodoc.com/presentation_image_h/8a6934ea3e90a9c89fec0d58577e90ff/image-19.jpg)
WTLS Specifications Optimized full handshaking Server. Hello Certificate [Change. Cipher. Spec] Finished [Chang. Cipher. Spec] Finished Application Data Youngho Choung

WTLS Specifications (4/5) Alert protocol Change Cipher spec protocol Youngho Choung

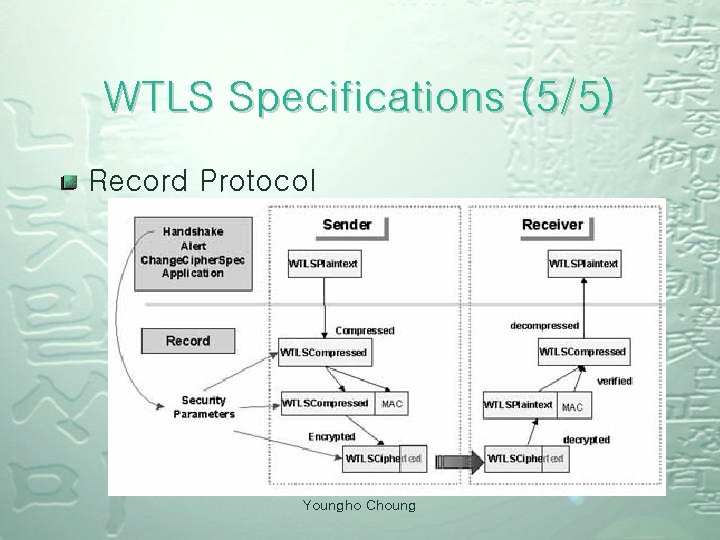
WTLS Specifications (5/5) Record Protocol Youngho Choung

Let’s talk about……later. . WALS(Wireless Application Layer Security) WPKI(Wireless Public-Key Infrastructure) WIM(WAP Identity Module References Youngho Choung
 Wireless transport layer security
Wireless transport layer security Secure socket layer and transport layer security
Secure socket layer and transport layer security Secure socket layer and transport layer security
Secure socket layer and transport layer security Secure socket layer and transport layer security
Secure socket layer and transport layer security Secure socket layer and transport layer security
Secure socket layer and transport layer security Youngho chang
Youngho chang Wtp in mobile computing
Wtp in mobile computing Session mobility in mobile computing
Session mobility in mobile computing Wireless security in cryptography and network security
Wireless security in cryptography and network security Multiplexed transport layer security
Multiplexed transport layer security Multiplexed transport layer security
Multiplexed transport layer security Telecommunications, the internet, and wireless technology
Telecommunications, the internet, and wireless technology Privat security
Privat security Wireless network security definition
Wireless network security definition Wireless security threats and vulnerabilities
Wireless security threats and vulnerabilities 802-11-wireless-security
802-11-wireless-security Border security using wireless integrated network sensors
Border security using wireless integrated network sensors Wireless security training
Wireless security training Wireless security threats
Wireless security threats Fig 19
Fig 19 How are glands classified
How are glands classified Layer 6 presentation layer
Layer 6 presentation layer Layer 2 e layer 3
Layer 2 e layer 3