Gnutella 2 GNUTELLA A Summary Of The Protocol





























- Slides: 52

Gnutella 2 GNUTELLA A Summary Of The Protocol and it’s Purpose By Fr. Gayatri Tribhuvan University of Freiburg

OUTLINE Introduction n Structure n Functioning Mechanisms n Features n Gnutella 2 n Conclusion n

INTRODUCTION

What is Gnutella ? n Modern and efficient P 2 P network standard and architecture n Provides services such as person to person communication, data location and transfer

History of Gnutella n n Originally conceived of by Justin Frankel, 21 year old founder of Nullsoft. There were multiple open source implementations at http: //sourceforge. net/ including: ¨ Jtella ¨ Gnucleus Software released under the Lesser Gnu Public License (LGPL) The Gnutella protocol was widely analyzed

GOALS: Why is Gnutella n Open architecture n Allows diversity n Integrity. n Good performance. needed?

STRUCTURE

Scope of Gnutella n Consists of two components: 1. Gnutella standard 2. Gnutella network

Gnutella network n Easily recognizable component n Built on a high performance P 2 P architecture n On this a variety of applications can run and also be developed Examples of applications that can be built on this are, file sharing applications, communication tools etc. Any client that joins this network becomes a SERVENT. n n

Gnutella standard n Set of applications for building requirements that run on the Gnutella network n Specifies minimum compliance level required for an application to run on Gnutella. n It recognizes if an application is Gnutella compatible or not. A standard is needed for Gnutella to allow diverse applications to interact with each other. n

Some requirements what applications must have to be compatible with Gnutella : EXAMPLES n Bidirectional TCP stream n Routing maintenance n Reverse connection response n HTTP/ 1. 1 for client server in P 2 P transactions

Gnutella protocol messages n Broadcast Messages ¨ Ping ¨ Query n Back-Propagated Messages ¨ Pong ¨ Query n Hit Node-to-Node Messages ¨ PUSH

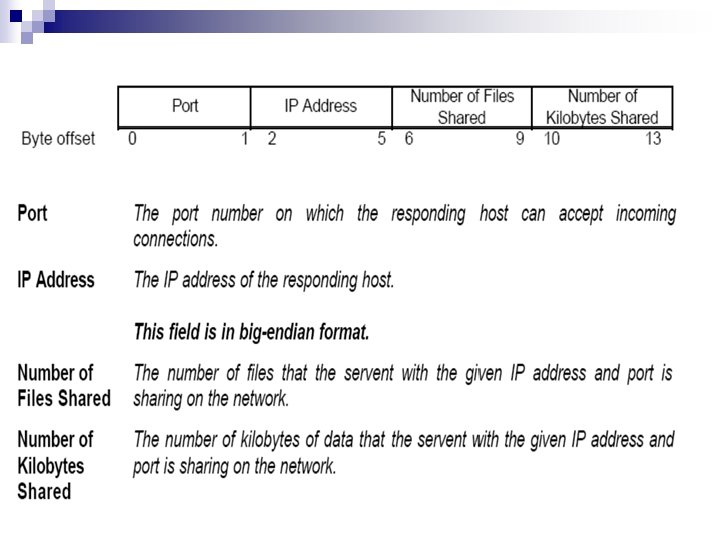
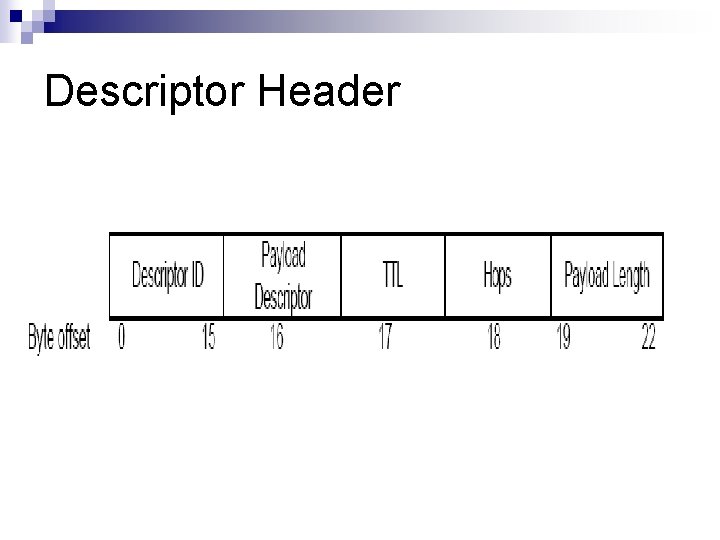
Ping n Discovers hosts on the network actively. n Probes the networks for other Servents. n Represented by descriptor header where: Payload Descriptor field is 0 x 00

Pong n Reply to a Ping message n Contains address of active Gnutella Servent n More than One pong can be sent in reply to one Ping.


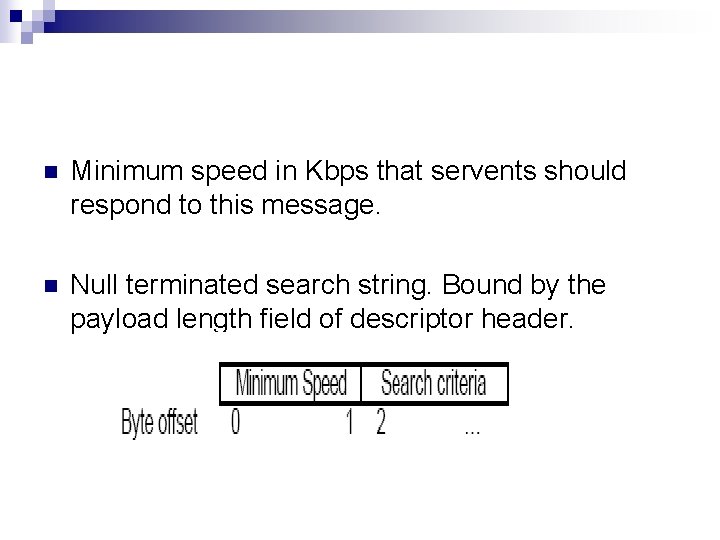
Query n Primary mechanism for searching the distributed network n Responds with query hit after searching its local data set.

n Minimum speed in Kbps that servents should respond to this message. n Null terminated search string. Bound by the payload length field of descriptor header.

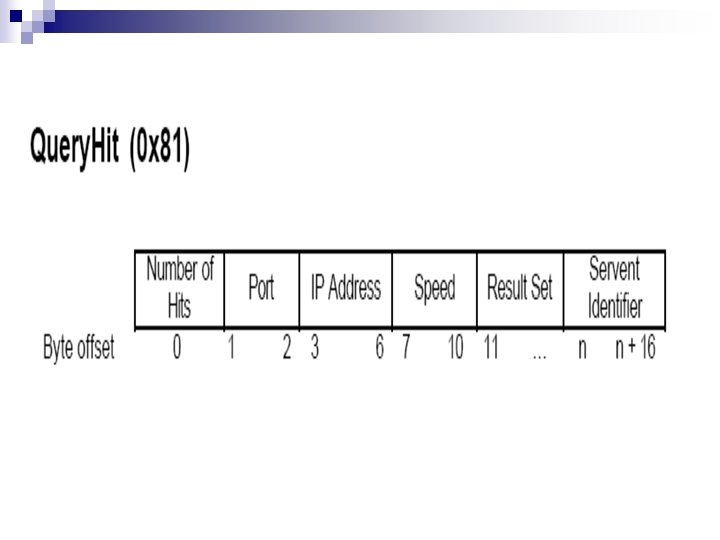
Query Hit n Reply to Query. n Must be generated only if the search criteria is accurately met. n Has the same descriptor identifier as Query.


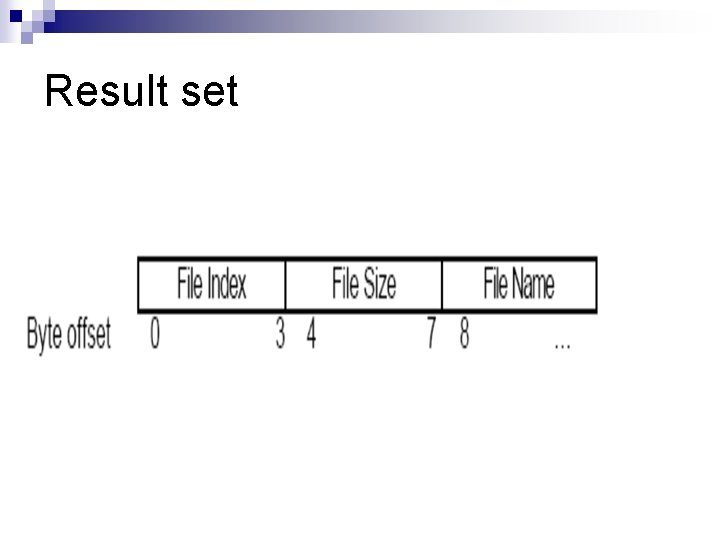
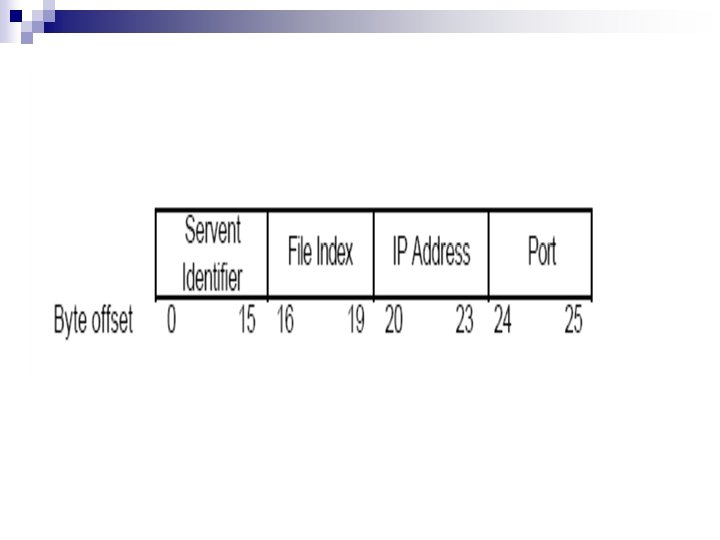
Result set

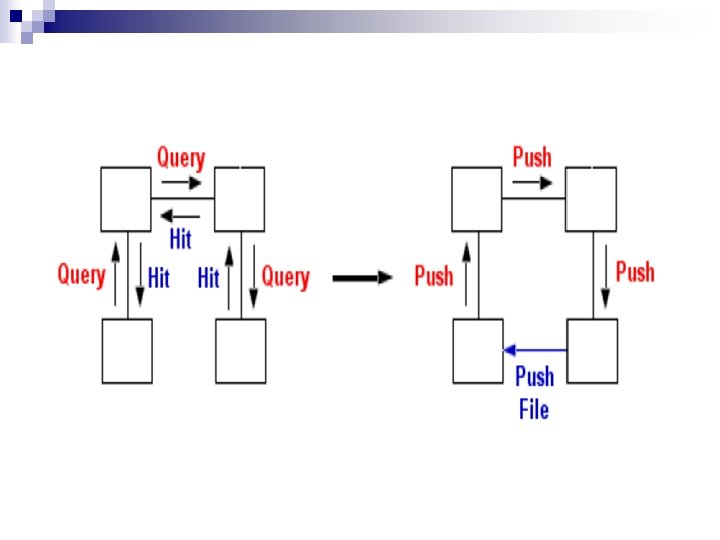
Push n Allows for data access from firewalled servent n Servent sending Query hit is behind a firewall.


FUNCTIONING MECHANISMS

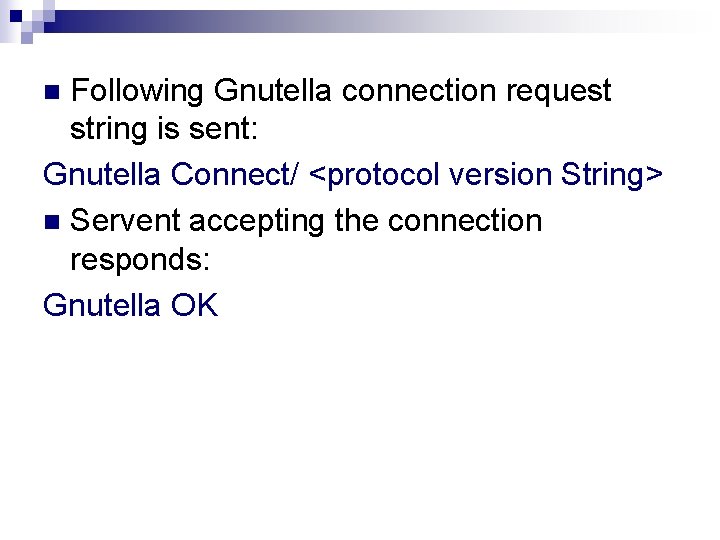
How does a servent join Gnutella? n Tries to establish connection with a fellow servent. n TCP connection established once address of the other servent is obtained.

Following Gnutella connection request string is sent: Gnutella Connect/ <protocol version String> n Servent accepting the connection responds: Gnutella OK n

Descriptor Header

Payload Descriptor tkes the following values: 0 x 00 Ping 0 x 01 Pong 0 x 40 Push 0 x 80 Query 0 x 81 Query hit n

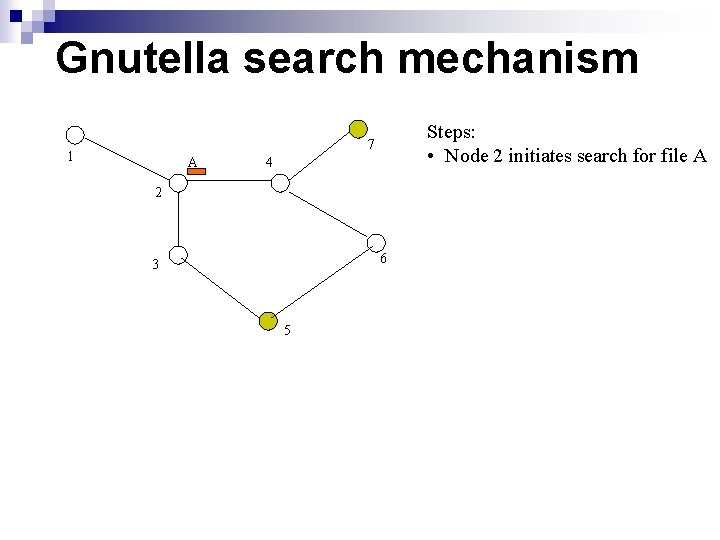
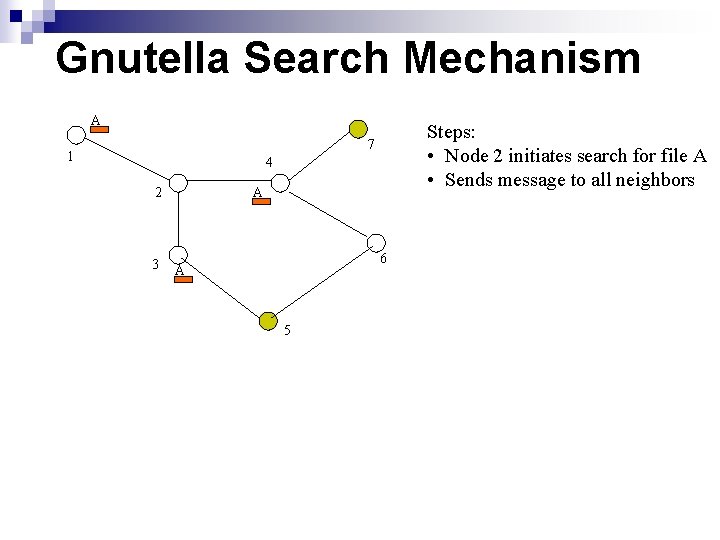
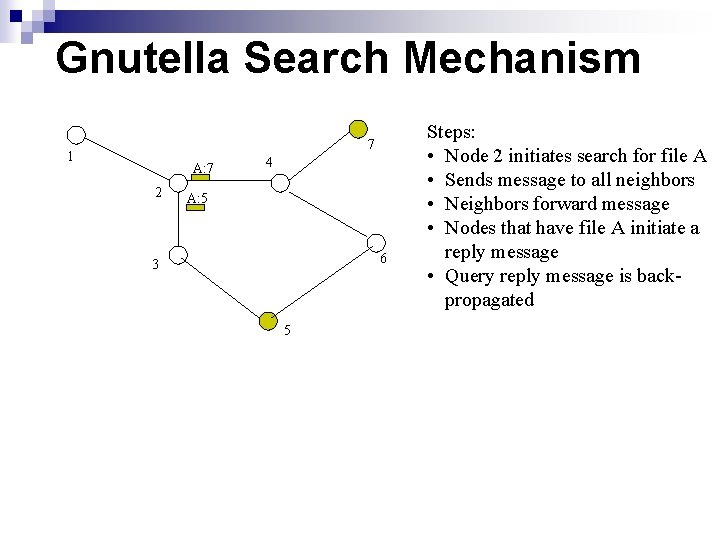
Gnutella search mechanism Steps: • Node 2 initiates search for file A 7 1 A 4 2 6 3 5

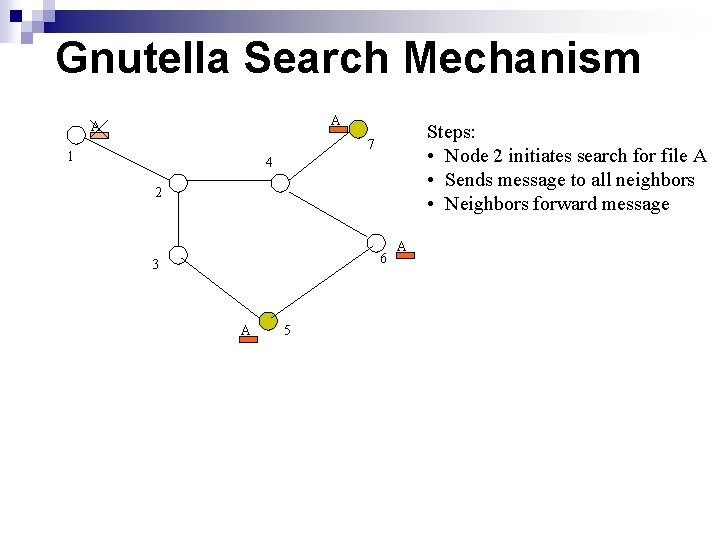
Gnutella Search Mechanism A Steps: • Node 2 initiates search for file A • Sends message to all neighbors 7 1 4 2 3 A 6 A 5

Gnutella Search Mechanism A A Steps: • Node 2 initiates search for file A • Sends message to all neighbors • Neighbors forward message 7 1 4 2 6 3 A 5 A

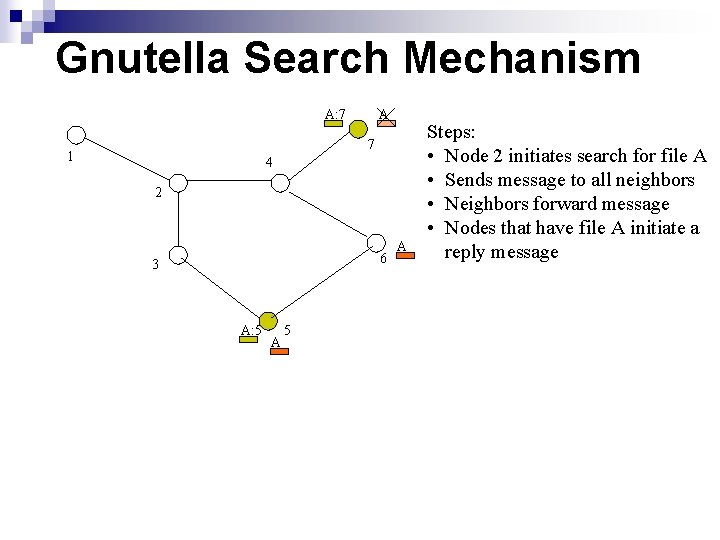
Gnutella Search Mechanism A: 7 A 7 1 4 2 6 3 A: 5 A Steps: • Node 2 initiates search for file A • Sends message to all neighbors • Neighbors forward message • Nodes that have file A initiate a reply message

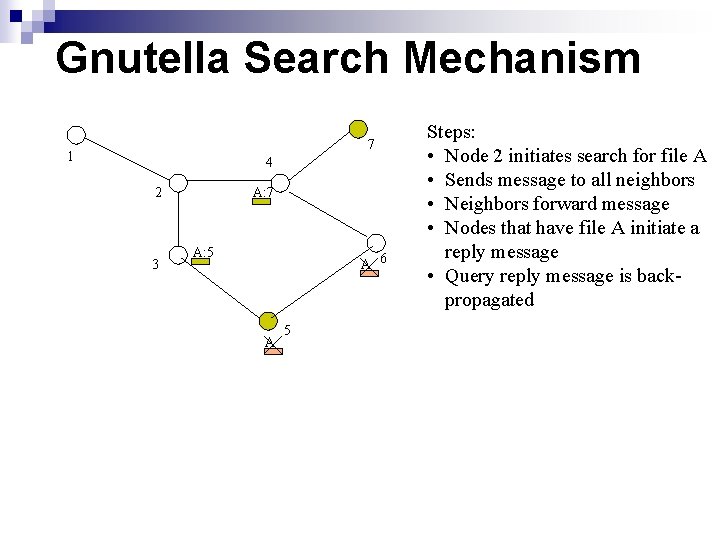
Gnutella Search Mechanism 7 1 4 2 3 A: 7 A: 5 A 6 A 5 Steps: • Node 2 initiates search for file A • Sends message to all neighbors • Neighbors forward message • Nodes that have file A initiate a reply message • Query reply message is backpropagated

Gnutella Search Mechanism 7 1 A: 7 2 4 A: 5 6 3 5 Steps: • Node 2 initiates search for file A • Sends message to all neighbors • Neighbors forward message • Nodes that have file A initiate a reply message • Query reply message is backpropagated

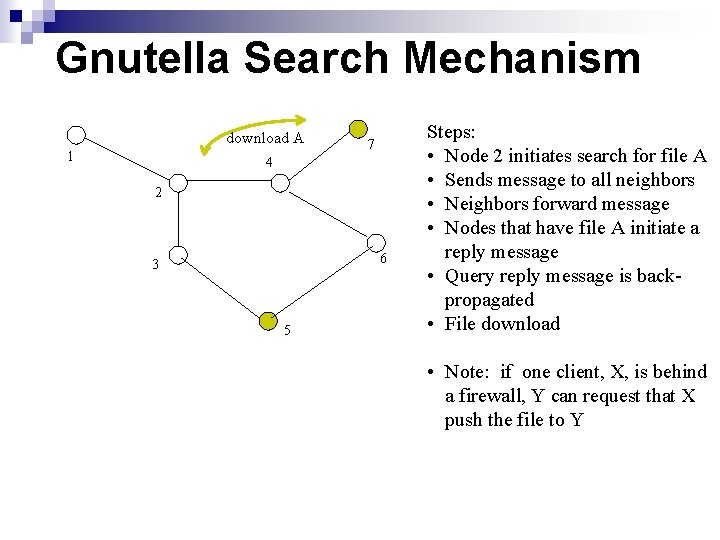
Gnutella Search Mechanism download A 1 7 4 2 6 3 5 Steps: • Node 2 initiates search for file A • Sends message to all neighbors • Neighbors forward message • Nodes that have file A initiate a reply message • Query reply message is backpropagated • File download • Note: if one client, X, is behind a firewall, Y can request that X push the file to Y

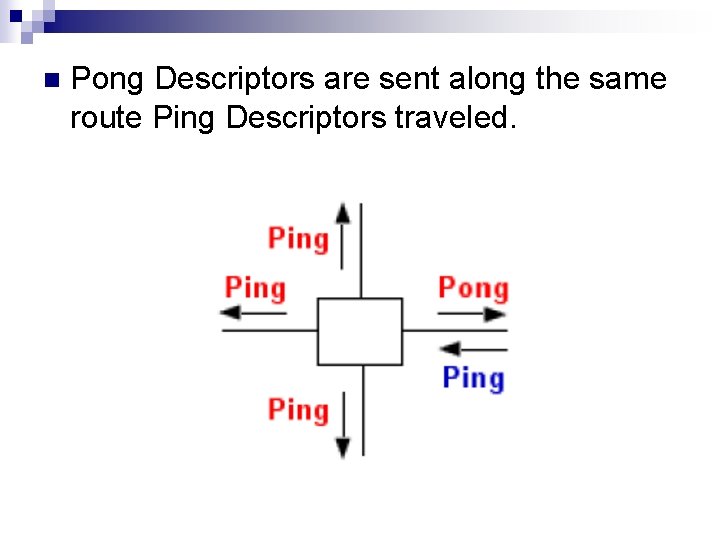
Descriptor Routing Necessary to control traffic in Gnutella network. n Well behaved Gnutella servent routes descriptors in the following manner n

n Pong Descriptors are sent along the same route Ping Descriptors traveled.

n Query hits are sent long the same path Query descriptors traveled. n Push descriptors are sent along the same path of the incoming query hit descriptors.


n Servent sends incoming ping and query messages to all directly connected servents, except the servent that initiated the message. n TTL decremented, and Hops field incremented , before descriptors are forwarded. If TTL is 0, descriptors are stopped being forwarded.

n If the payload descriptor and descriptor ID is the same as received before, these descriptors should not be forwarded.

File Downloads n Direct connection between source and target n File is never transferred over the Gnutella network.

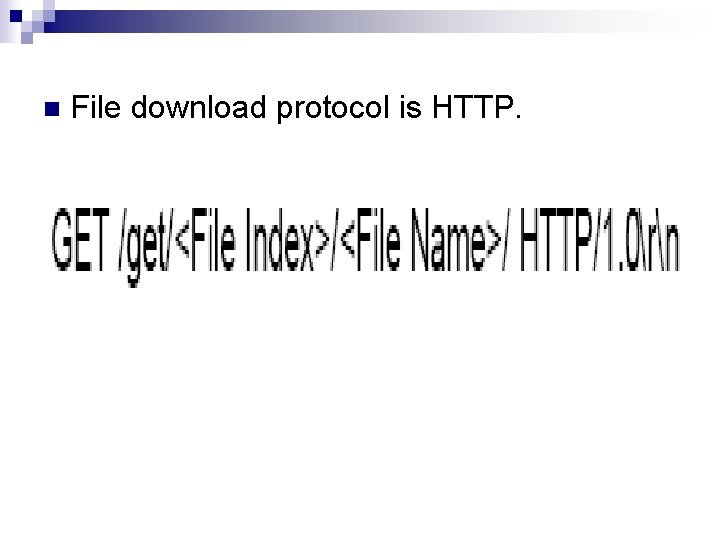
n File download protocol is HTTP.

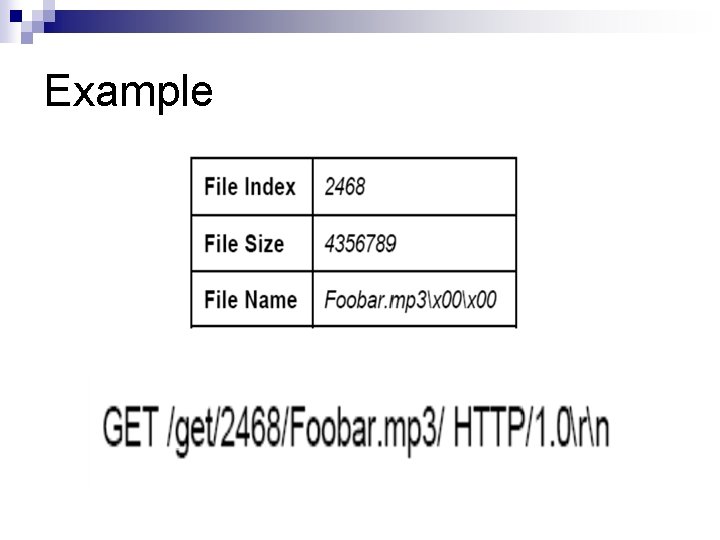
Example

Features of Gnutella Scalability When a node receives a ping/query message, it forwards it to the other nodes. n Existing mechanisms to reduce traffic ¨ TTL counter ¨ Cache information about messages they received, so that they don't forward duplicated messages. n Anonymity Gnutella provides for anonymity by masking the identity of the peer n that generated a query.

Disadvantages Limited number of hosts being searched leads to a limited number of hits n The search result is not accurate due to the search by filename n An inefficient use of computer resource spending too much resource on handling other peers' queries. n

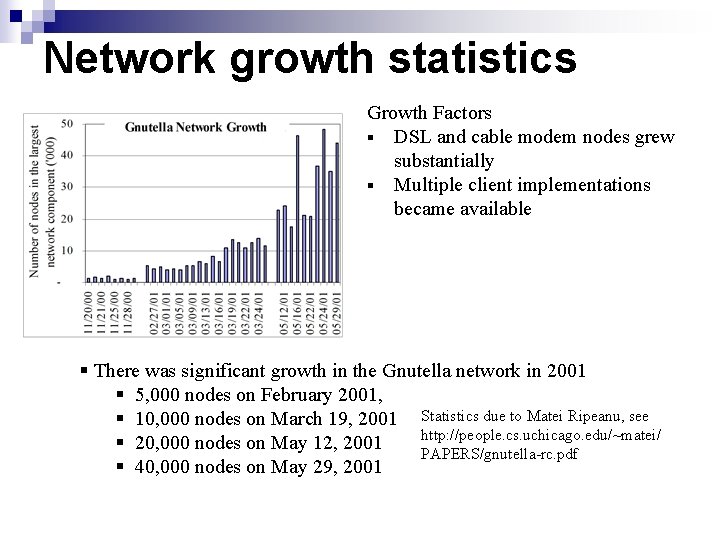
Network growth statistics Growth Factors § DSL and cable modem nodes grew substantially § Multiple client implementations became available § There was significant growth in the Gnutella network in 2001 § 5, 000 nodes on February 2001, § 10, 000 nodes on March 19, 2001 Statistics due to Matei Ripeanu, see http: //people. cs. uchicago. edu/~matei/ § 20, 000 nodes on May 12, 2001 PAPERS/gnutella-rc. pdf § 40, 000 nodes on May 29, 2001

Gnutella 2 Developed by Michael Stokes in 2002. n Uses extendible XML packet format n Uses SHA-1 hashes for file identification and secure integrity check of files. n Uses a metadata system to ensure a quality search of files than merely searching based on file name. n

How it Works Divides network into hubs and leaves n Hubs are connected to each other and can have as many leaves as possible n Searches only the required hubs mentioned in the list n Doesn’t overload the network n

Details of files at leaves are maintained by query routing tables in the hub, and forwarded to other hubs. n Reduces unnecessary flooding. n

Gnutella 2 versus Gnutella 2 relies on UDP n Search Mechanism Gnutella- Query flooding Gnutella 2 - Walk mechanism n Searching node collects information only from the necessary hubs. n

Conclusion n Gnutella is a self-organizing, large-scale, P 2 P application that produces an overlay network on top of the Internet n Since there is no central authority the open source community must commit to making any changes

THANK YOU
 Napster and gnutella
Napster and gnutella Gnutella clients
Gnutella clients What is gnutella
What is gnutella Gnutella
Gnutella Gnutella 2
Gnutella 2 Hình ảnh bộ gõ cơ thể búng tay
Hình ảnh bộ gõ cơ thể búng tay Lp html
Lp html Bổ thể
Bổ thể Tỉ lệ cơ thể trẻ em
Tỉ lệ cơ thể trẻ em Gấu đi như thế nào
Gấu đi như thế nào Glasgow thang điểm
Glasgow thang điểm Hát lên người ơi
Hát lên người ơi Các môn thể thao bắt đầu bằng tiếng bóng
Các môn thể thao bắt đầu bằng tiếng bóng Thế nào là hệ số cao nhất
Thế nào là hệ số cao nhất Các châu lục và đại dương trên thế giới
Các châu lục và đại dương trên thế giới Công thức tính thế năng
Công thức tính thế năng Trời xanh đây là của chúng ta thể thơ
Trời xanh đây là của chúng ta thể thơ Mật thư tọa độ 5x5
Mật thư tọa độ 5x5 Phép trừ bù
Phép trừ bù Phản ứng thế ankan
Phản ứng thế ankan Các châu lục và đại dương trên thế giới
Các châu lục và đại dương trên thế giới Thể thơ truyền thống
Thể thơ truyền thống Quá trình desamine hóa có thể tạo ra
Quá trình desamine hóa có thể tạo ra Một số thể thơ truyền thống
Một số thể thơ truyền thống Cái miệng nó xinh thế
Cái miệng nó xinh thế Vẽ hình chiếu vuông góc của vật thể sau
Vẽ hình chiếu vuông góc của vật thể sau Biện pháp chống mỏi cơ
Biện pháp chống mỏi cơ đặc điểm cơ thể của người tối cổ
đặc điểm cơ thể của người tối cổ Ví dụ giọng cùng tên
Ví dụ giọng cùng tên Vẽ hình chiếu đứng bằng cạnh của vật thể
Vẽ hình chiếu đứng bằng cạnh của vật thể Vẽ hình chiếu vuông góc của vật thể sau
Vẽ hình chiếu vuông góc của vật thể sau Thẻ vin
Thẻ vin đại từ thay thế
đại từ thay thế điện thế nghỉ
điện thế nghỉ Tư thế ngồi viết
Tư thế ngồi viết Diễn thế sinh thái là
Diễn thế sinh thái là Các loại đột biến cấu trúc nhiễm sắc thể
Các loại đột biến cấu trúc nhiễm sắc thể Bảng số nguyên tố lớn hơn 1000
Bảng số nguyên tố lớn hơn 1000 Tư thế ngồi viết
Tư thế ngồi viết Lời thề hippocrates
Lời thề hippocrates Thiếu nhi thế giới liên hoan
Thiếu nhi thế giới liên hoan ưu thế lai là gì
ưu thế lai là gì Sự nuôi và dạy con của hổ
Sự nuôi và dạy con của hổ Sự nuôi và dạy con của hươu
Sự nuôi và dạy con của hươu Hệ hô hấp
Hệ hô hấp Từ ngữ thể hiện lòng nhân hậu
Từ ngữ thể hiện lòng nhân hậu Thế nào là mạng điện lắp đặt kiểu nổi
Thế nào là mạng điện lắp đặt kiểu nổi Drcr.net protocol summary
Drcr.net protocol summary Sism9
Sism9 Wtp pathfinder
Wtp pathfinder Wa anticoagulation chart
Wa anticoagulation chart Rogers score dvt
Rogers score dvt Vdp protocol
Vdp protocol