SY 4003 FP Intrusion Access Control Intrusion Detection














- Slides: 99

SY 4003 FP Intrusion & Access Control Intrusion Detection System Prepared by Sandy Tay Intrusion & Access Control 1 10/7/2020

Content 2 1. Introduction to Intrusion Detection System (IDS) 2. 4 operations of IDS 3. IDS terminologies 4. Features of IDS 5. Type of Detectors Intrusion & Access Control 10/7/2020

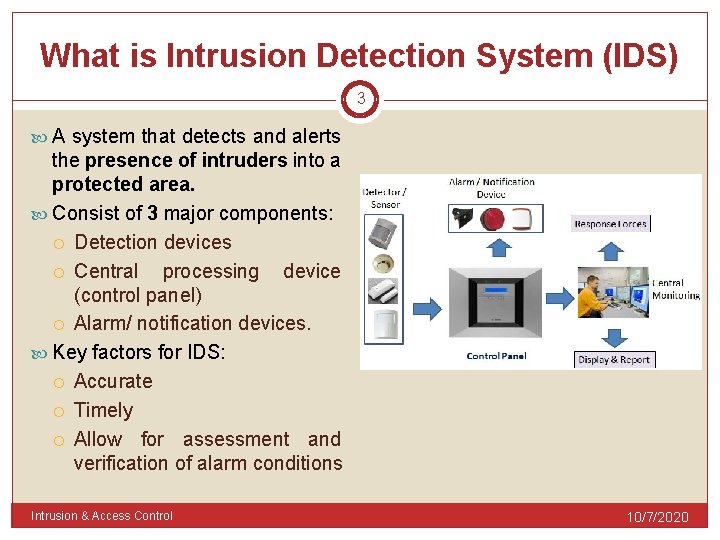
What is Intrusion Detection System (IDS) 3 A system that detects and alerts the presence of intruders into a protected area. Consist of 3 major components: Detection devices Central processing device (control panel) Alarm/ notification devices. Key factors for IDS: Accurate Timely Allow for assessment and verification of alarm conditions Intrusion & Access Control 10/7/2020

Limitations of Electronic Detection (IDS) 4 Can’t provide instant alarm verification. 2. Small area detection 3. Once the detectors are mounted, unable to adjust detection area 4. Relatively high number of false alarms 1. Intrusion & Access Control 10/7/2020

IDS Operations 5 Detection Analysis Report Response Intrusion & Access Control 10/7/2020

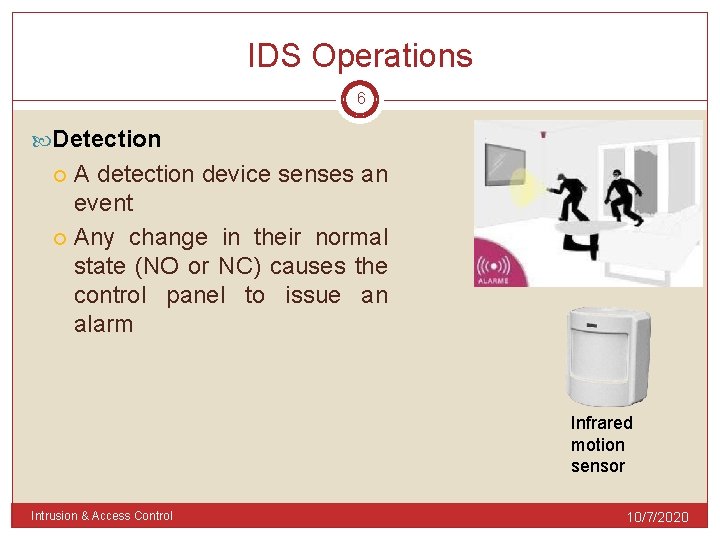
IDS Operations 6 Detection A detection device senses an event Any change in their normal state (NO or NC) causes the control panel to issue an alarm Infrared motion sensor Intrusion & Access Control 10/7/2020

IDS Operations 7 Analysis Control Panel received information from detection device and respond when event occurs. 3 major parts of a control panel § Controller (password protection, history log ) § Alarm unit (drive the notification devices) § Communicator (with central monitoring station) Intrusion & Access Control 10/7/2020

IDS Operations 8 Report Local Visual or Audible reporting devices Visual (Strobe light) Audible (Siren/ buzzer) Local command control center Remote Central Monitoring System User via mobile services (SMS/email) Intrusion & Access Control Local Remote 10/7/2020

IDS Operations 9 Response Security officers Police Fire brigade, Civil Defence Sprinkle system activated Intrusion & Access Control 10/7/2020

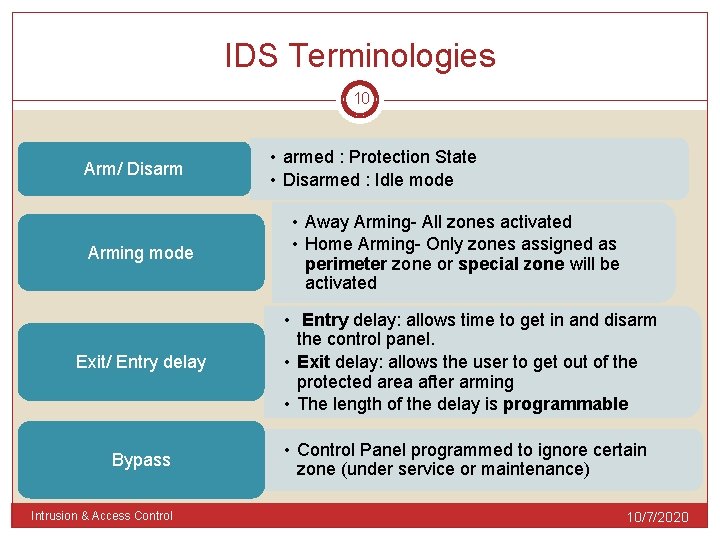
IDS Terminologies 10 Arm/ Disarm Arming mode • armed : Protection State • Disarmed : Idle mode • Away Arming- All zones activated • Home Arming- Only zones assigned as perimeter zone or special zone will be activated Exit/ Entry delay • Entry delay: allows time to get in and disarm the control panel. • Exit delay: allows the user to get out of the protected area after arming • The length of the delay is programmable Bypass • Control Panel programmed to ignore certain zone (under service or maintenance) Intrusion & Access Control 10/7/2020

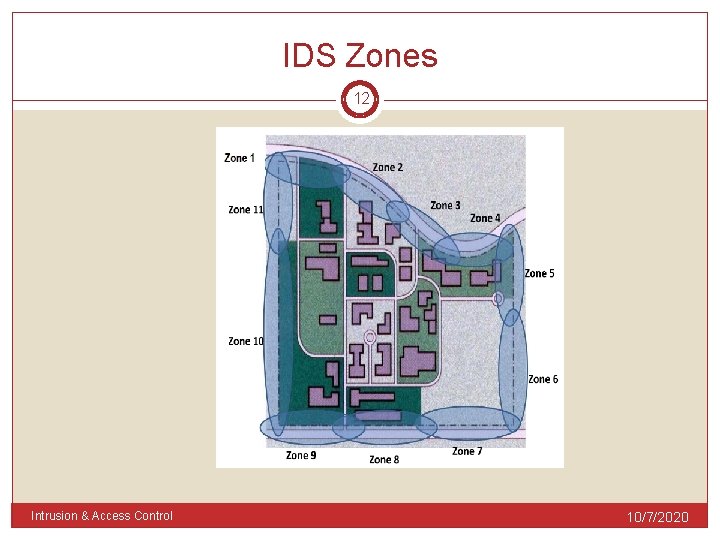
IDS Zones 11 Provides an exact and immediate location of the possible problem/ Danger Zoning is required: 1. To identify the location of the intrusion. 2. To enable different types of action definition or security policy in different areas. 3. To enable partial alarming (of certain Zones). 4. For ease of maintenance and trouble shooting. Intrusion & Access Control 10/7/2020

IDS Zones 12 Intrusion & Access Control 10/7/2020

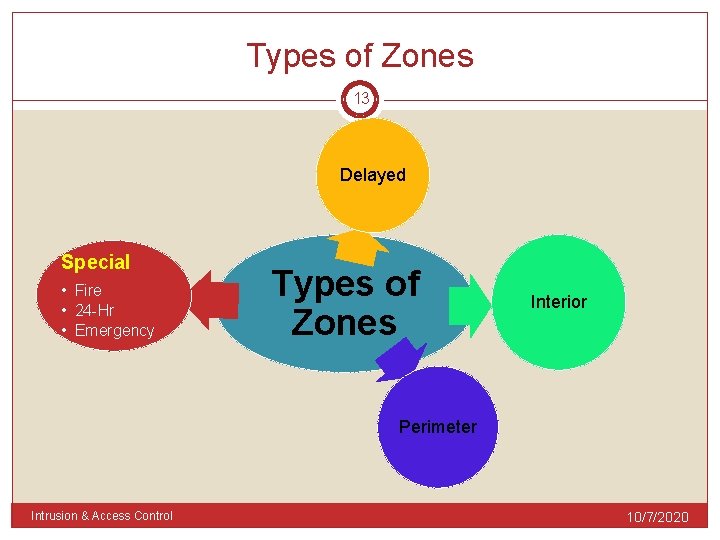
Types of Zones 13 Delayed Special • Fire • 24 -Hr • Emergency Types of Zones Interior Perimeter Intrusion & Access Control 10/7/2020

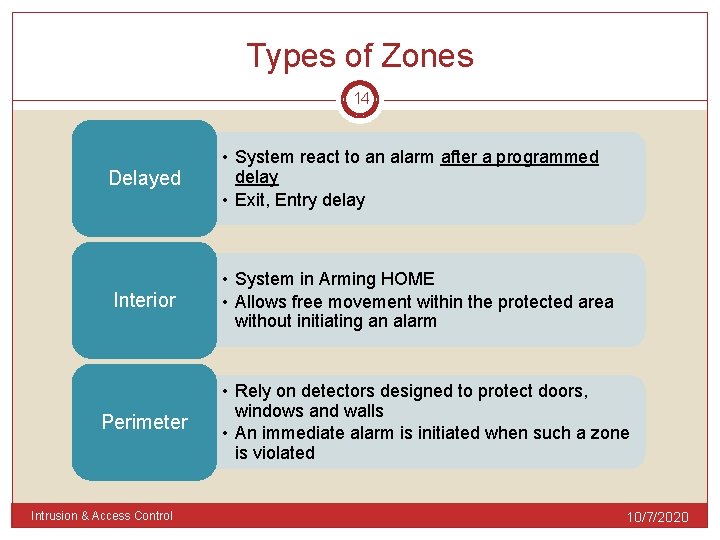
Types of Zones 14 Delayed Interior Perimeter Intrusion & Access Control • System react to an alarm after a programmed delay • Exit, Entry delay • System in Arming HOME • Allows free movement within the protected area without initiating an alarm • Rely on detectors designed to protect doors, windows and walls • An immediate alarm is initiated when such a zone is violated 10/7/2020

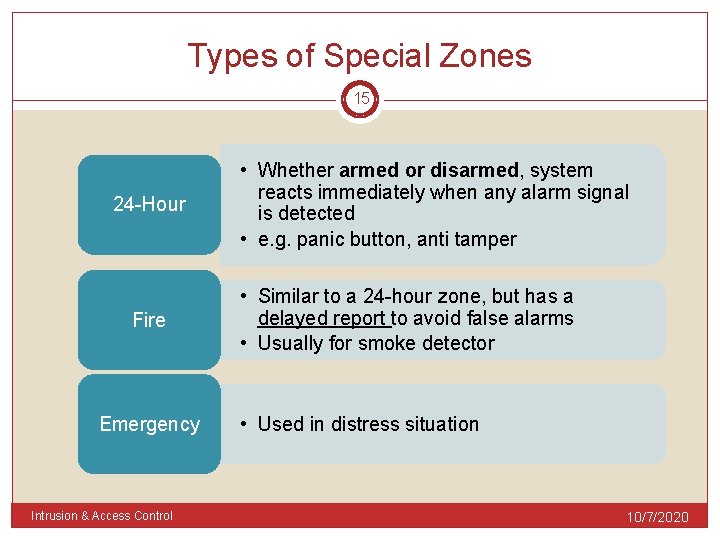
Types of Special Zones 15 24 -Hour Fire Emergency Intrusion & Access Control • Whether armed or disarmed, system reacts immediately when any alarm signal is detected • e. g. panic button, anti tamper • Similar to a 24 -hour zone, but has a delayed report to avoid false alarms • Usually for smoke detector • Used in distress situation 10/7/2020

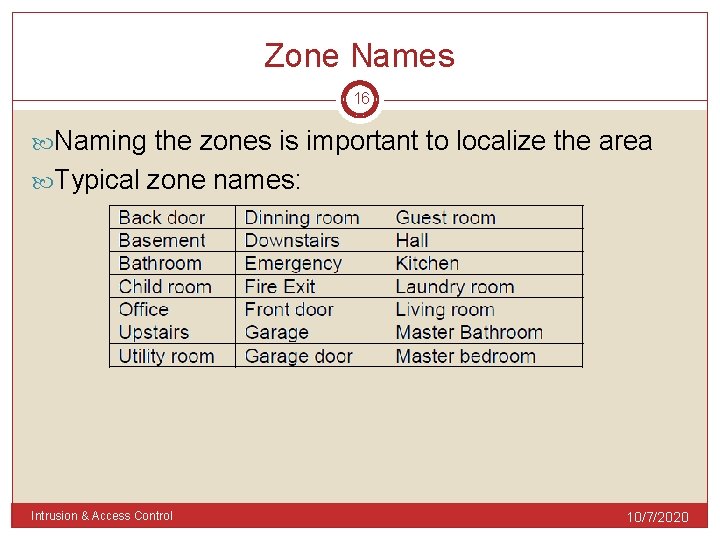
Zone Names 16 Naming the zones is important to localize the area Typical zone names: Intrusion & Access Control 10/7/2020

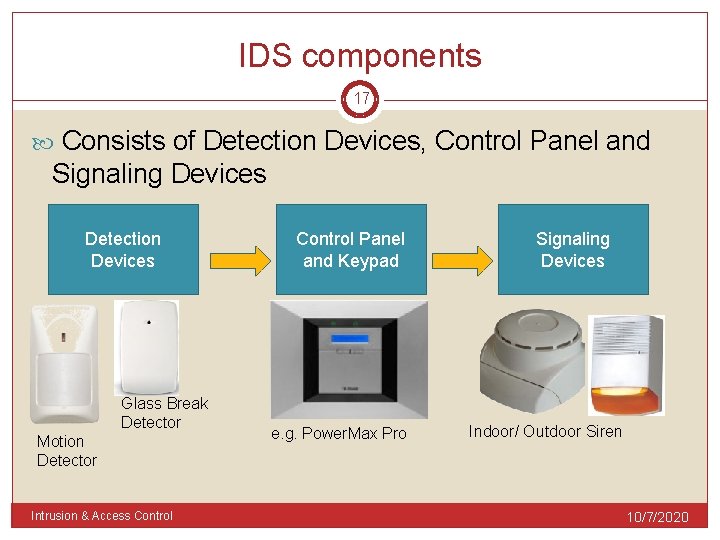
IDS components 17 Consists of Detection Devices, Control Panel and Signaling Devices Detection Devices Glass Break Detector Motion Detector Intrusion & Access Control Panel and Keypad e. g. Power. Max Pro Signaling Devices Indoor/ Outdoor Siren 10/7/2020

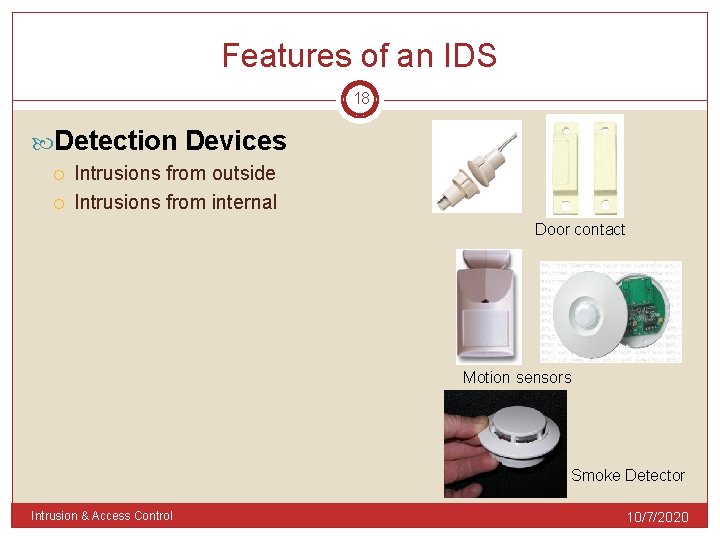
Features of an IDS 18 Detection Devices Intrusions from outside Intrusions from internal Door contact Motion sensors Smoke Detector Intrusion & Access Control 10/7/2020

Features of an IDS 19 Control Panel Function 1. monitor the state of detection devices 2. respond when an event occurs Feature Store history of events Operator control 1. turn the system on or off 2. identify the alarm state of the system 3. locates the zone or specific device causing an alarm condition 4. suspend an alarm condition 5. perform a system reset Intrusion & Access Control 10/7/2020

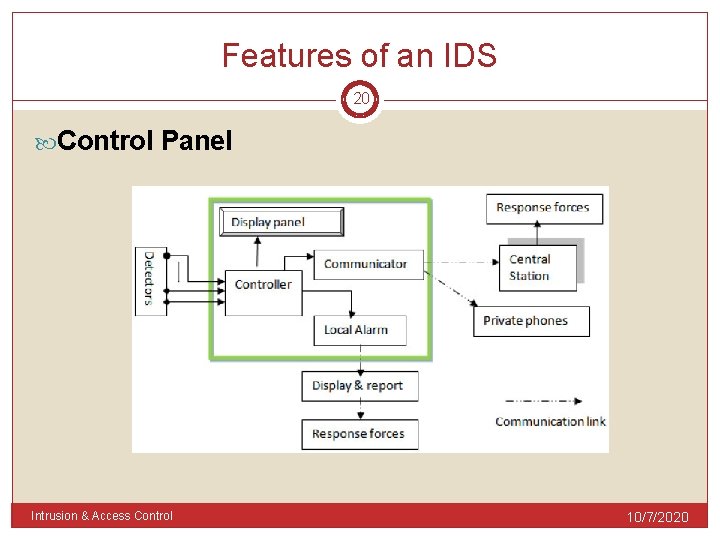
Features of an IDS 20 Control Panel Intrusion & Access Control 10/7/2020

Features of an IDS 21 Control Panel Inputs Controller decides if detector status should be translated into an alarm state. Response Control User can define how every event will be handled. Control panel filters the alarms and transfers only the relevant ones Outputs Local alarm connects to either Siren, strobe light Intrusion & Access Control 10/7/2020

Features of an IDS 22 Modes of Alerting Audio (horn, sirens, bells) Illuminated devices (strobes) Central station monitoring Local directed monitoring through IP PSTN GPRS; GSM Intrusion & Access Control 10/7/2020

Types of IDS 23 1. Wired or Hard-wired (HIDS) 2. Wireless (WIDS) 3. Hybrid (Hy. IDS) 4. IP-enabled (IPIDS) Intrusion & Access Control 10/7/2020

Types of IDS 24 Which type of IDS suitable for a project depends on the customer constraints the environment of building Intrusion & Access Control 10/7/2020

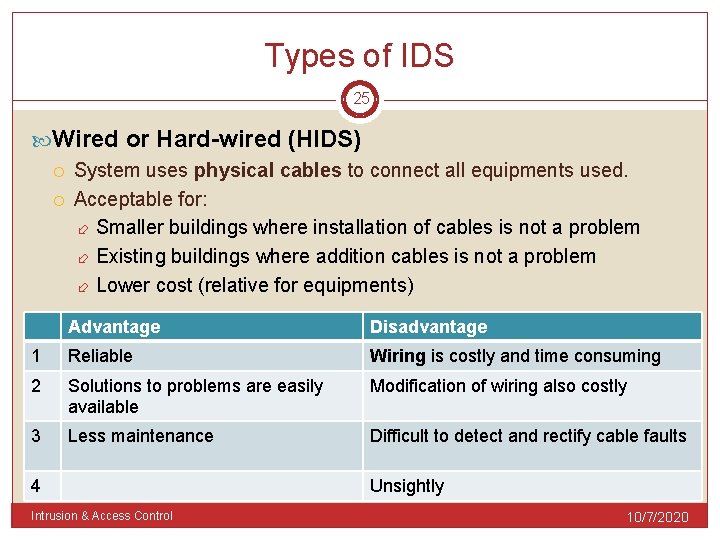
Types of IDS 25 Wired or Hard-wired (HIDS) System uses physical cables to connect all equipments used. Acceptable for: Smaller buildings where installation of cables is not a problem Existing buildings where addition cables is not a problem Lower cost (relative for equipments) Advantage Disadvantage 1 Reliable Wiring is costly and time consuming 2 Solutions to problems are easily available Modification of wiring also costly 3 Less maintenance Difficult to detect and rectify cable faults 4 Intrusion & Access Control Unsightly 10/7/2020

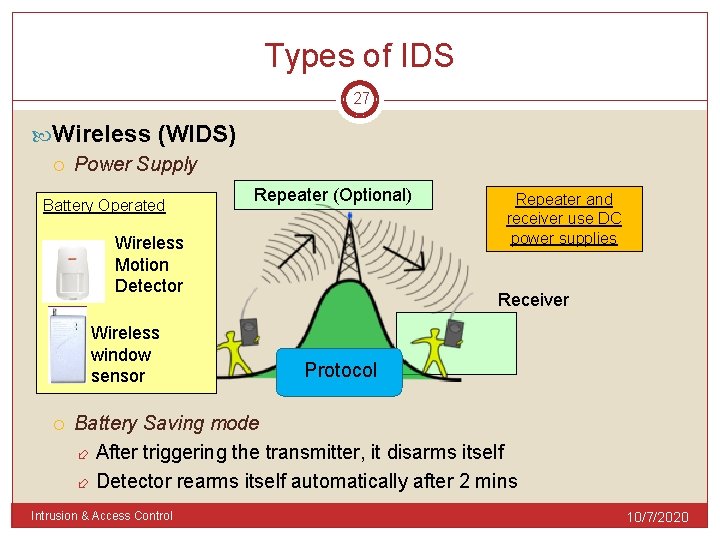
Types of IDS 26 Wireless (WIDS) Uses wireless technology to connect all the detecting devices to radio transmitters. Examples of wireless technology RFID, UHF, microwave, Bluetooth Government of a country needs to regulate the different frequencies used for different purposes Intrusion & Access Control 10/7/2020

Types of IDS 27 Wireless (WIDS) Power Supply Battery Operated Repeater (Optional) Wireless Motion Detector Wireless window sensor Repeater and receiver use DC power supplies Receiver Protocol Battery Saving mode After triggering the transmitter, it disarms itself Detector rearms itself automatically after 2 mins Intrusion & Access Control 10/7/2020

Types of IDS 28 Wireless (WIDS) Data Protocol 12 - Bit Code Enables sending of only the identify of the transmitter. (system code + channel code) Only information is : alarm or low battery Battery require to check every 6 months 36 -bit code 24 -bit for identify + 12 -bit for supervision (alarm, battery status, tampering, inactivity, periodical test) Note: Selected system code ensures that the central control receiver can only respond to transmitters set to the same code Intrusion & Access Control 10/7/2020

Types of IDS 29 Wireless (WIDS) Installation of Wireless IDS Points to consider 1. Direct data transfer path among the equipment 2. Area should be free from disturbances. 3. Perform walk test with receiver and watch the red LED for reception. Flickers-> Constant disturbance. Remedy: Look for another area to install the receiver Light constantly Remedy: Do not install a wireless system. Propose alternative solution. 4. Avoid direct sunlight on detectors and receivers 5. Batteries in transmitters have to be changed periodically. 6. Frequency of wireless devices must match the manufacturer of the control panel. Intrusion & Access Control 10/7/2020

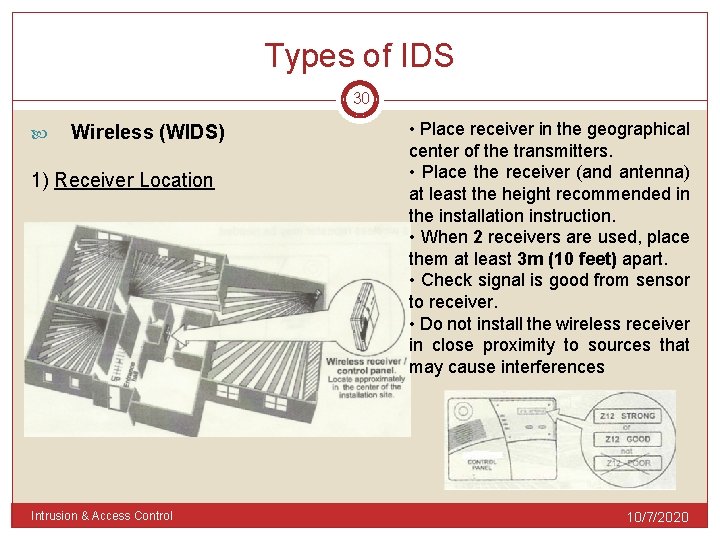
Types of IDS 30 Wireless (WIDS) 1) Receiver Location Intrusion & Access Control • Place receiver in the geographical center of the transmitters. • Place the receiver (and antenna) at least the height recommended in the installation instruction. • When 2 receivers are used, place them at least 3 m (10 feet) apart. • Check signal is good from sensor to receiver. • Do not install the wireless receiver in close proximity to sources that may cause interferences 10/7/2020

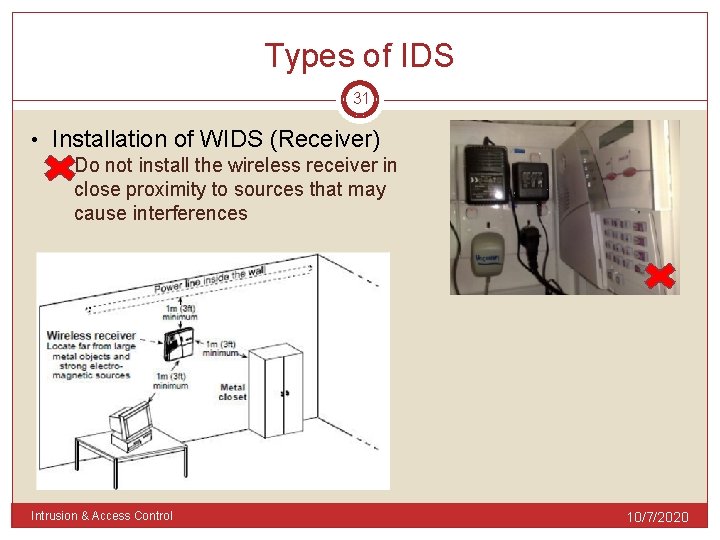
Types of IDS 31 • Installation of WIDS (Receiver) • Do not install the wireless receiver in close proximity to sources that may cause interferences Intrusion & Access Control 10/7/2020

Types of IDS 32 Wireless (WIDS) 2) Repeater Location • Install a repeater where there is good communication between the transmitters and the receiver or other repeaters. • Mount repeater and antenna at least the height recommended in the instructor manual. • Install it near a 230 VAC source (for the chargeable battery). Intrusion & Access Control 10/7/2020

Types of IDS 33 Wireless (WIDS) 3) Transmitter Location • Perform the walk test to select best location for detection • if metal object is present, install transmitter at least 1 m away from it. Intrusion & Access Control 10/7/2020

Types of IDS 34 Wireless (WIDS) No Advantage Disadvantage 1 No installation of cables needed Limitations of range and frequencies due to regulations 2 Easy to install Disturbance and Interference from other radio signals. § Lesser time § Don’t need skill people to hide wires. 3 Using latest technology Intrusion & Access Control Equipment may be more costly than hard wired. 10/7/2020

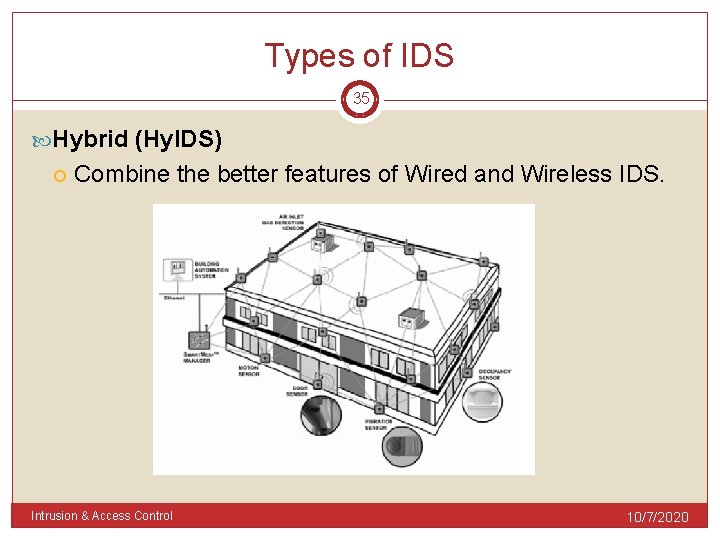
Types of IDS 35 Hybrid (Hy. IDS) Combine the better features of Wired and Wireless IDS. Intrusion & Access Control 10/7/2020

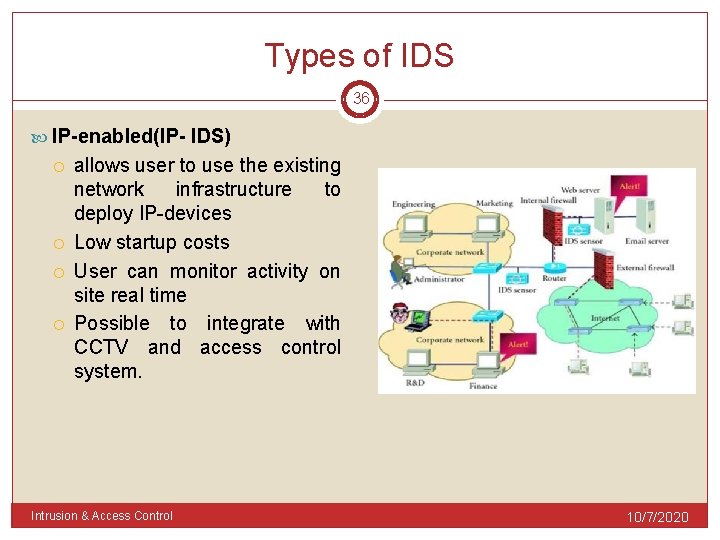
Types of IDS 36 IP-enabled(IP- IDS) allows user to use the existing network infrastructure to deploy IP-devices Low startup costs User can monitor activity on site real time Possible to integrate with CCTV and access control system. Intrusion & Access Control 10/7/2020

Types of IDS 37 IP-enabled(IP- IDS) Benefits 1. Cost efficient 2. Flexible and scalable 3. Easy to integrate with other systems 4. Greater verification and response efficiency Intrusion & Access Control 10/7/2020

Alarm Monitoring Center 38 2 types Centralized Decentralized Intrusion & Access Control 10/7/2020

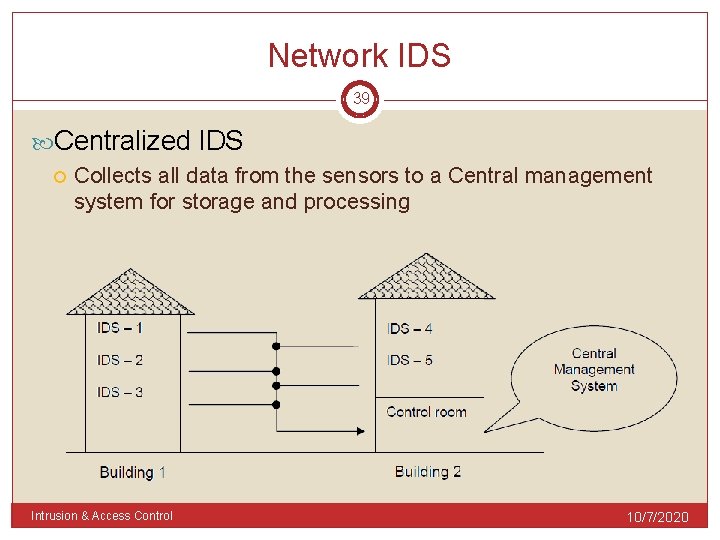
Network IDS 39 Centralized IDS Collects all data from the sensors to a Central management system for storage and processing Intrusion & Access Control 10/7/2020

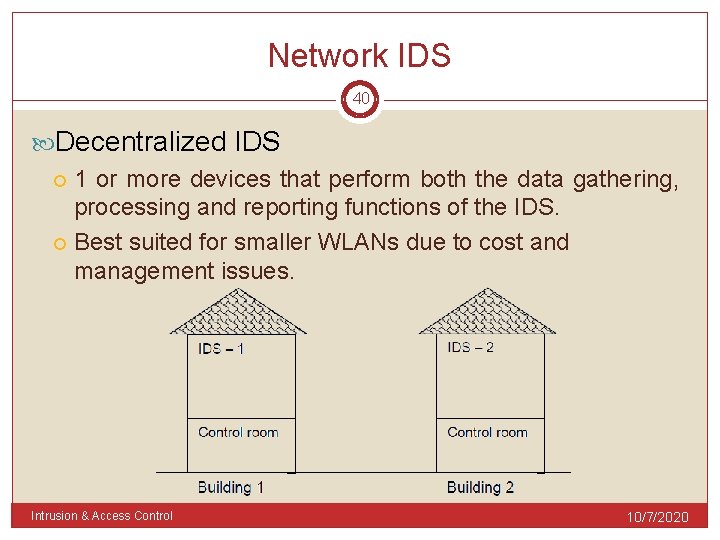
Network IDS 40 Decentralized IDS 1 or more devices that perform both the data gathering, processing and reporting functions of the IDS. Best suited for smaller WLANs due to cost and management issues. Intrusion & Access Control 10/7/2020

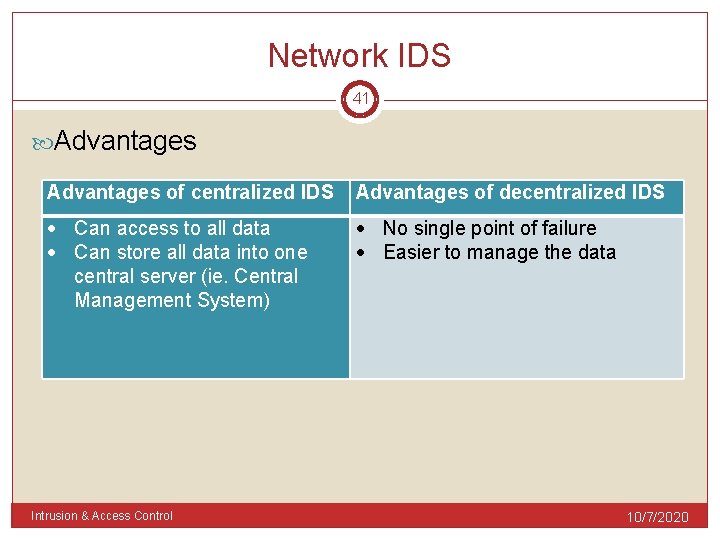
Network IDS 41 Advantages of centralized IDS Advantages of decentralized IDS Can access to all data Can store all data into one central server (ie. Central Management System) No single point of failure Easier to manage the data Intrusion & Access Control 10/7/2020

IDS Detectors 42 designed to generate an alarm condition in response to a deliberate action by the users detects intrusion, equipment malfunction, rate of temperature change smoke fire Intrusion & Access Control 10/7/2020

IDS Detectors 43 1. Interior detectors Detect intrusion into a building or facility Indoor use. Less susceptible to false and nuisance alarms 2. Perimeter detectors respond to outside intruders crossing a boundary higher false alarm rate often require the use of two or more sensors for effective detect Intrusion & Access Control 10/7/2020

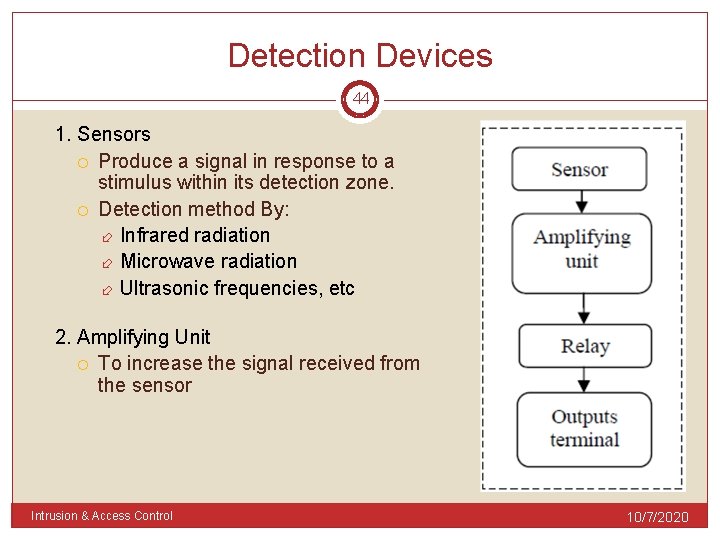
Detection Devices 44 1. Sensors Produce a signal in response to a stimulus within its detection zone. Detection method By: Infrared radiation Microwave radiation Ultrasonic frequencies, etc 2. Amplifying Unit To increase the signal received from the sensor Intrusion & Access Control 10/7/2020

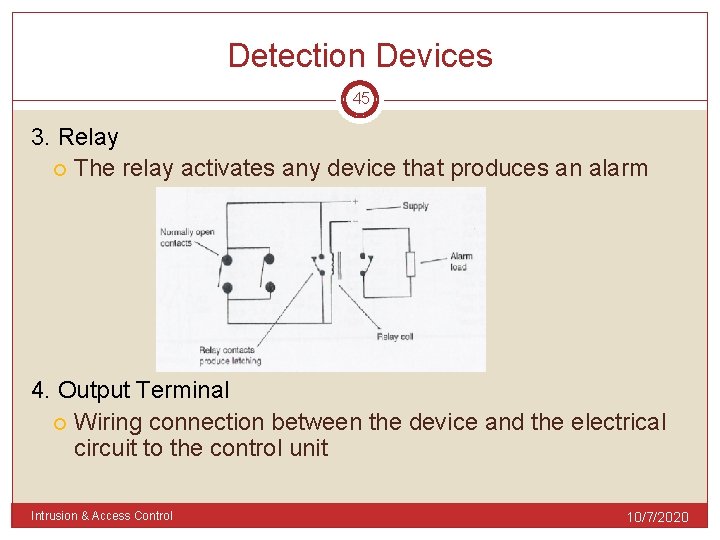
Detection Devices 45 3. Relay The relay activates any device that produces an alarm 4. Output Terminal Wiring connection between the device and the electrical circuit to the control unit Intrusion & Access Control 10/7/2020

Detector Devices 46 Features Light Emitting Diodes (LEDs) indicator 2. The Tamper Switch 3. Timer 4. Anti Masking feature 1. Intrusion & Access Control 10/7/2020

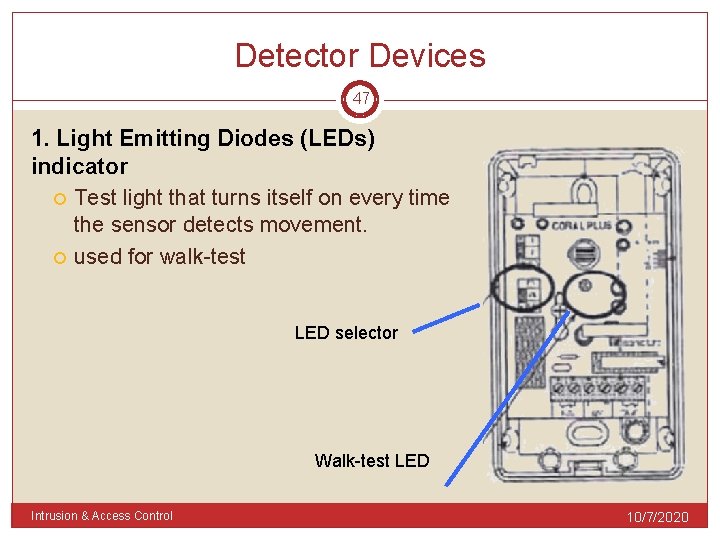
Detector Devices 47 1. Light Emitting Diodes (LEDs) indicator Test light that turns itself on every time the sensor detects movement. used for walk-test LED selector Walk-test LED Intrusion & Access Control 10/7/2020

Detector Devices 48 2. The Tamper Switch Detect attempts to remove some alarm components such as detector covers, switch covers 2 types of tamper switch: Internal tamper switch – detects cover removal 2. External tamper switch – detects whole unit removal from the wall. 1. Intrusion & Access Control 10/7/2020

Detector Devices 49 3. Timer Controls the amount of time an element will remain activated before turning itself OFF. Examples: The timing for the LED light remains ON. The amount of time an alarm sounds. The amount of time a light-controller alarm remains activated. Intrusion & Access Control 10/7/2020

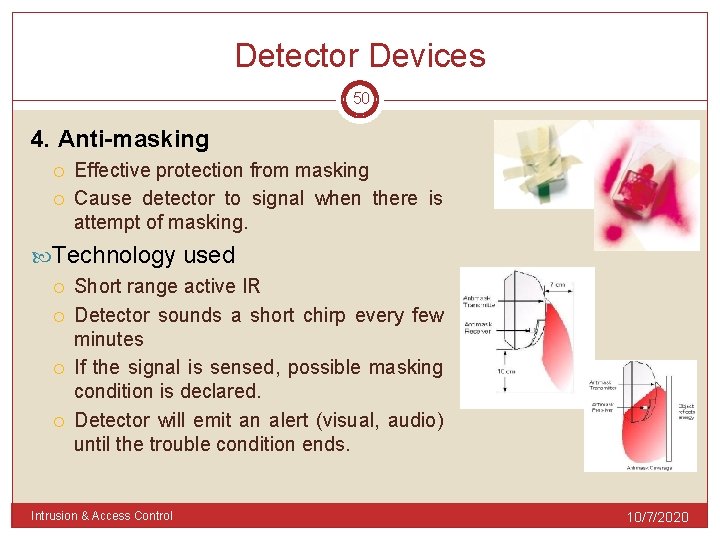
Detector Devices 50 4. Anti-masking Effective protection from masking Cause detector to signal when there is attempt of masking. Technology used Short range active IR Detector sounds a short chirp every few minutes If the signal is sensed, possible masking condition is declared. Detector will emit an alert (visual, audio) until the trouble condition ends. Intrusion & Access Control 10/7/2020

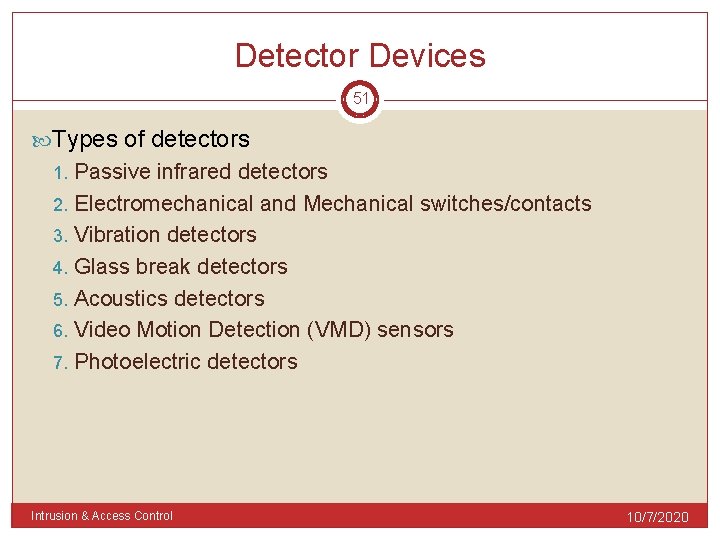
Detector Devices 51 Types of detectors Passive infrared detectors 2. Electromechanical and Mechanical switches/contacts 3. Vibration detectors 4. Glass break detectors 5. Acoustics detectors 6. Video Motion Detection (VMD) sensors 7. Photoelectric detectors 1. Intrusion & Access Control 10/7/2020

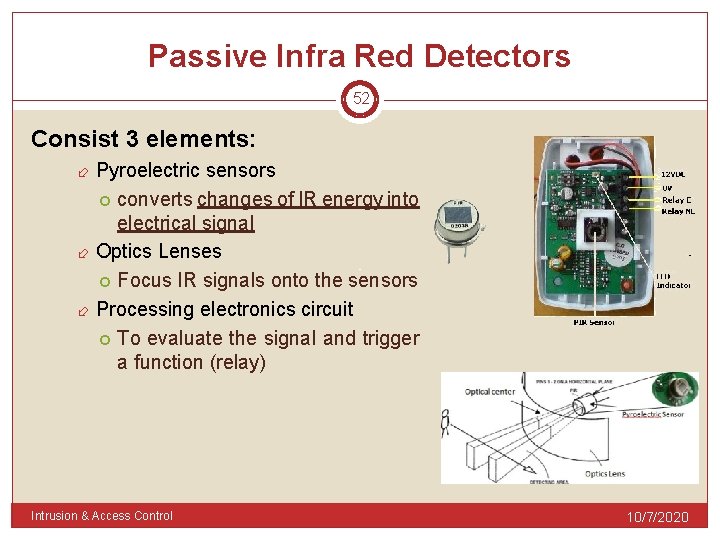
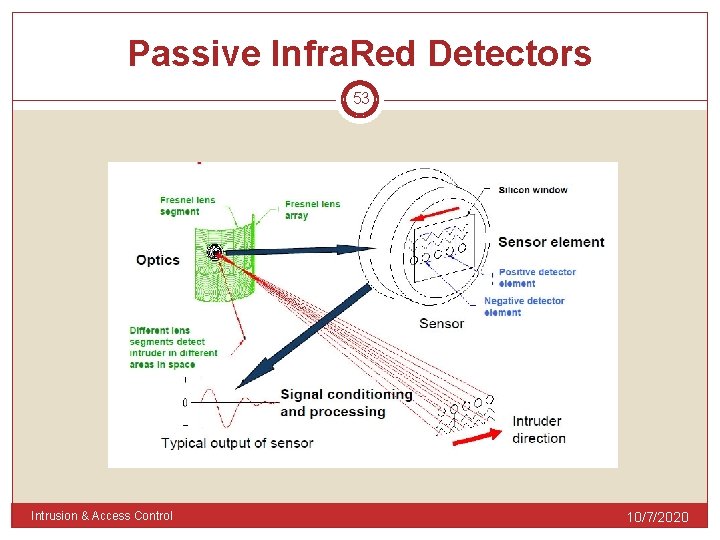
Passive Infra Red Detectors 52 Consist 3 elements: Pyroelectric sensors converts changes of IR energy into electrical signal Optics Lenses Focus IR signals onto the sensors Processing electronics circuit To evaluate the signal and trigger a function (relay) Intrusion & Access Control 10/7/2020

Passive Infra. Red Detectors 53 Intrusion & Access Control 10/7/2020

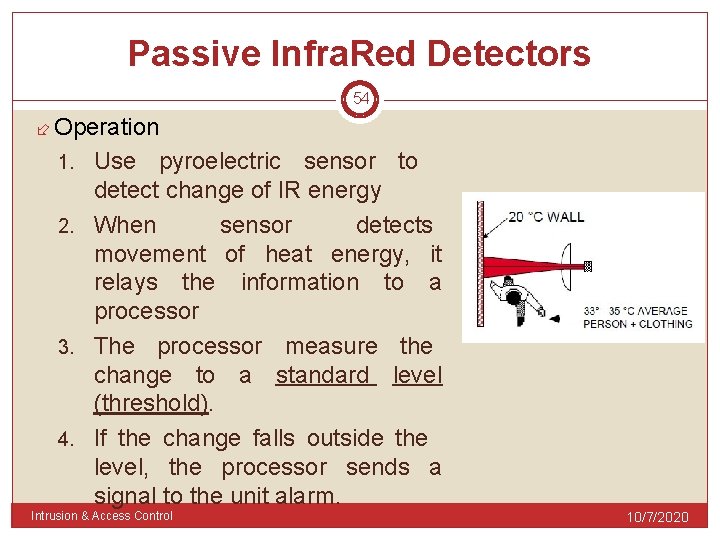
Passive Infra. Red Detectors 54 Operation Use pyroelectric sensor to detect change of IR energy 2. When sensor detects movement of heat energy, it relays the information to a processor 3. The processor measure the change to a standard level (threshold). 4. If the change falls outside the level, the processor sends a signal to the unit alarm. 1. Intrusion & Access Control 10/7/2020

Passive Infra. Red Detectors 55 Dual or Quad PIR opposed sensor elements Develop to reduce the frequency of false alarms. A dual element produce opposite charges An IR source must appear in an active zone on one section and than appear on the other section within a given time -scale When both sensor elements sense IR energy at the same time, the positive and negative charges cancel, i. e. no signal is generated. Intrusion & Access Control 10/7/2020

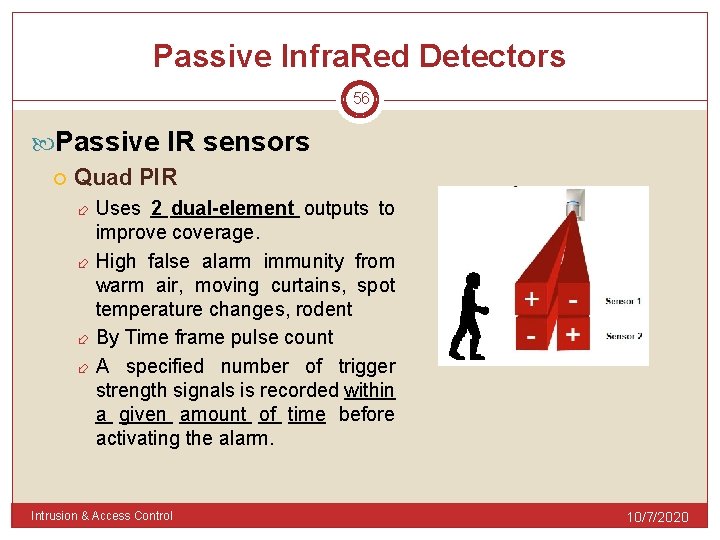
Passive Infra. Red Detectors 56 Passive IR sensors Quad PIR Uses 2 dual-element outputs to improve coverage. High false alarm immunity from warm air, moving curtains, spot temperature changes, rodent By Time frame pulse count A specified number of trigger strength signals is recorded within a given amount of time before activating the alarm. Intrusion & Access Control 10/7/2020

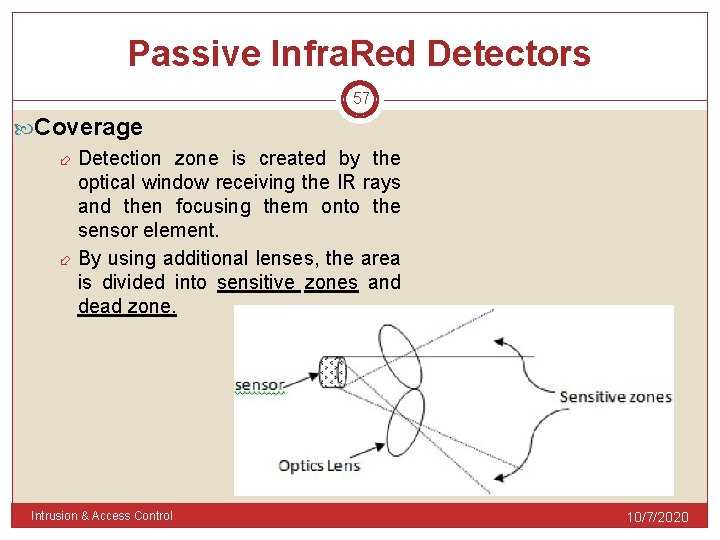
Passive Infra. Red Detectors 57 Coverage Detection zone is created by the optical window receiving the IR rays and then focusing them onto the sensor element. By using additional lenses, the area is divided into sensitive zones and dead zone. Intrusion & Access Control 10/7/2020

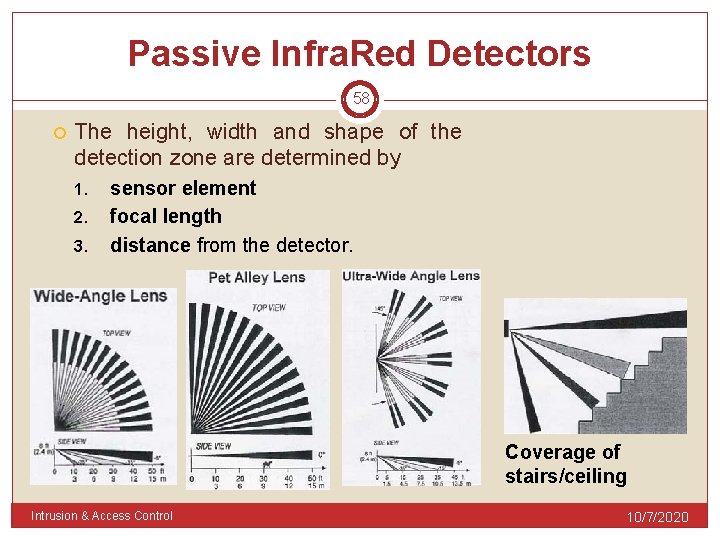
Passive Infra. Red Detectors 58 The height, width and shape of the detection zone are determined by 1. 2. 3. sensor element focal length distance from the detector. Coverage of stairs/ceiling Intrusion & Access Control 10/7/2020

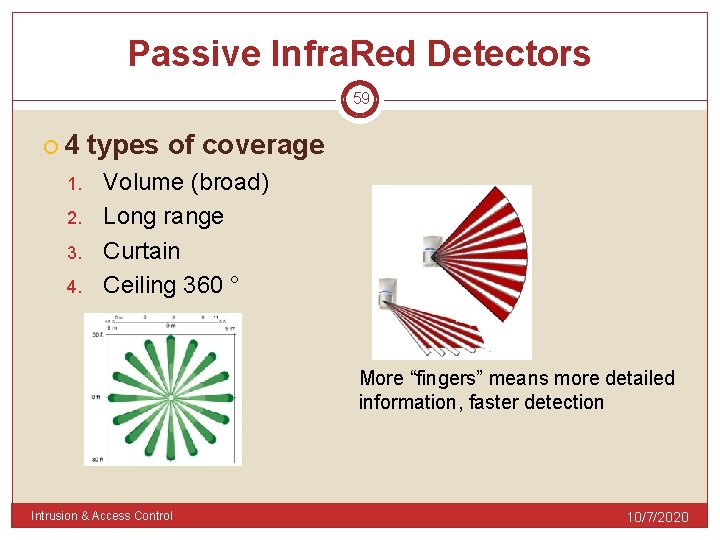
Passive Infra. Red Detectors 59 4 1. 2. 3. 4. types of coverage Volume (broad) Long range Curtain Ceiling 360 ° More “fingers” means more detailed information, faster detection Intrusion & Access Control 10/7/2020

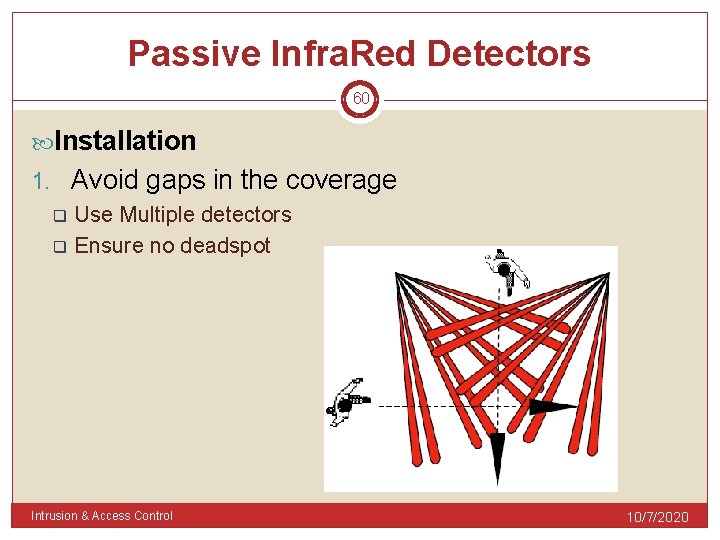
Passive Infra. Red Detectors 60 Installation 1. Avoid gaps in the coverage q q Use Multiple detectors Ensure no deadspot Intrusion & Access Control 10/7/2020

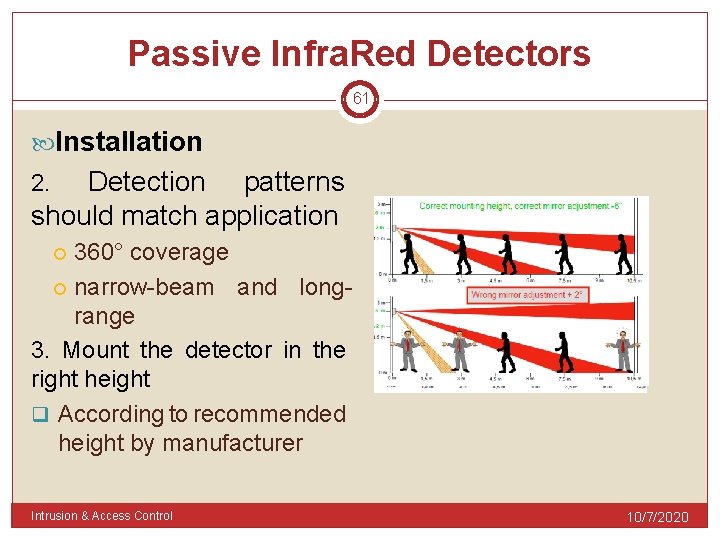
Passive Infra. Red Detectors 61 Installation Detection patterns should match application 2. 360° coverage narrow-beam and longrange 3. Mount the detector in the right height q According to recommended height by manufacturer Intrusion & Access Control 10/7/2020

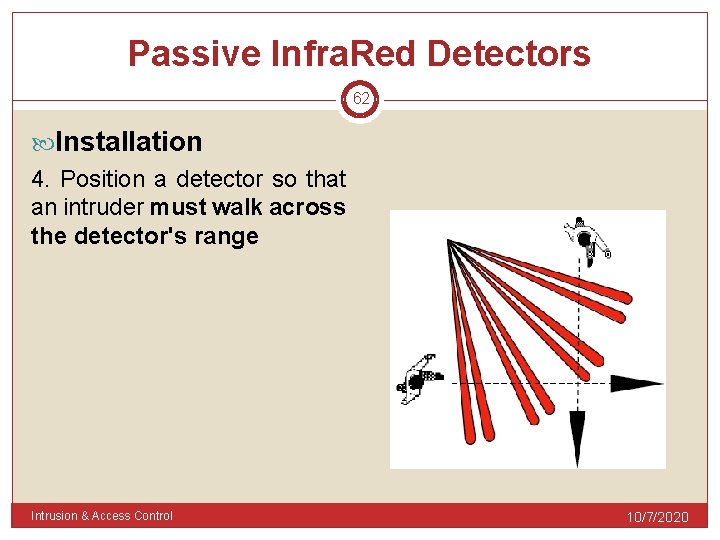
Passive Infra. Red Detectors 62 Installation 4. Position a detector so that an intruder must walk across the detector's range Intrusion & Access Control 10/7/2020

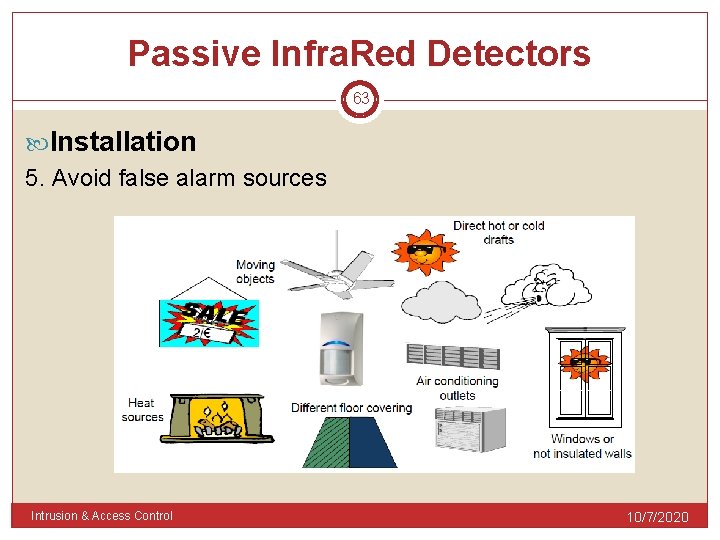
Passive Infra. Red Detectors 63 Installation 5. Avoid false alarm sources Intrusion & Access Control 10/7/2020

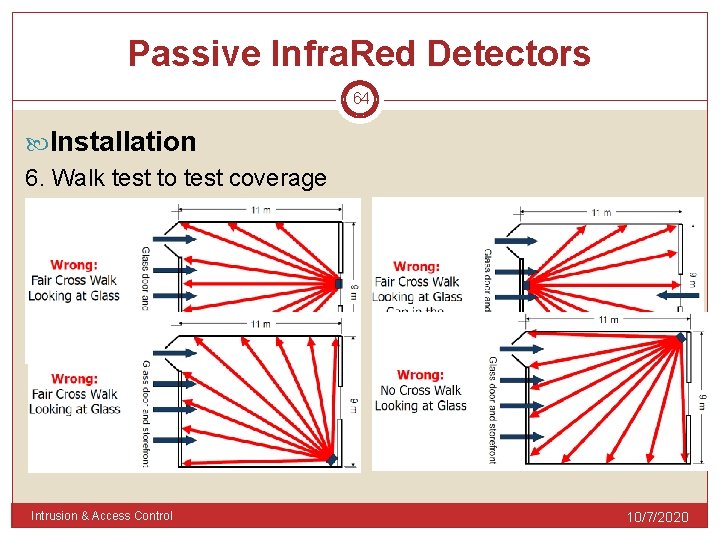
Passive Infra. Red Detectors 64 Installation 6. Walk test to test coverage Intrusion & Access Control 10/7/2020

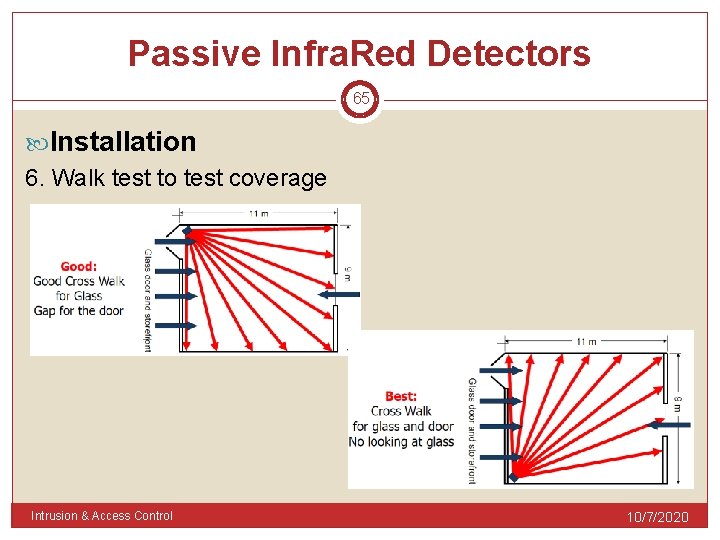
Passive Infra. Red Detectors 65 Installation 6. Walk test to test coverage Intrusion & Access Control 10/7/2020

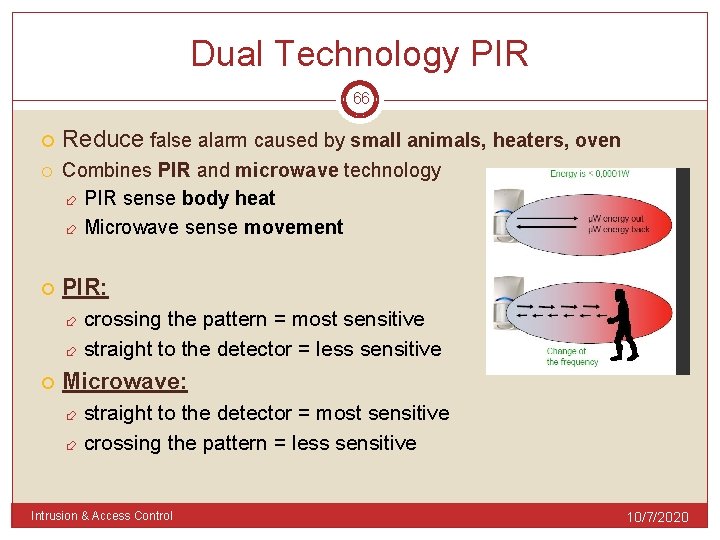
Dual Technology PIR 66 Reduce false alarm caused by small animals, heaters, oven Combines PIR and microwave technology PIR sense body heat Microwave sense movement PIR: crossing the pattern = most sensitive straight to the detector = less sensitive Microwave: straight to the detector = most sensitive crossing the pattern = less sensitive Intrusion & Access Control 10/7/2020

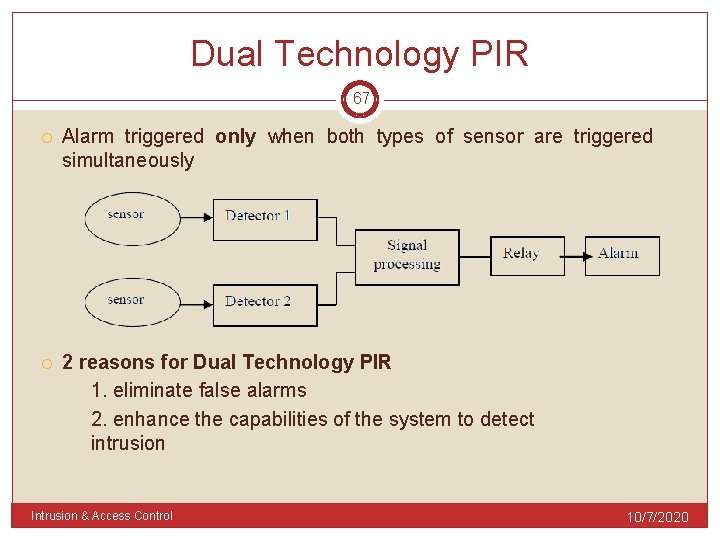
Dual Technology PIR 67 Alarm triggered only when both types of sensor are triggered simultaneously 2 reasons for Dual Technology PIR 1. eliminate false alarms 2. enhance the capabilities of the system to detect intrusion Intrusion & Access Control 10/7/2020

Detector Devices 68 Types of detectors Passive infrared detectors 2. Electromechanical and Mechanical switches/contacts 3. Vibration detectors 4. Glass break detectors 5. Acoustics detectors 6. Video Motion Detection (VMD) sensors 7. Photoelectric detectors 1. Intrusion & Access Control 10/7/2020

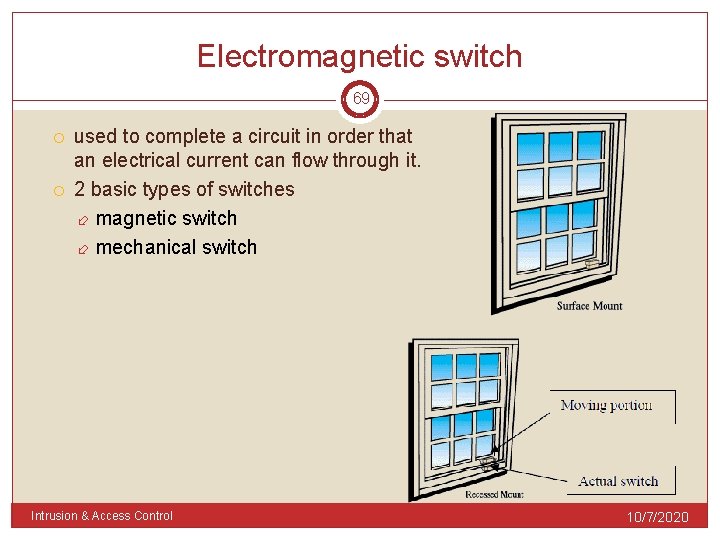
Electromagnetic switch 69 used to complete a circuit in order that an electrical current can flow through it. 2 basic types of switches magnetic switch mechanical switch Intrusion & Access Control 10/7/2020

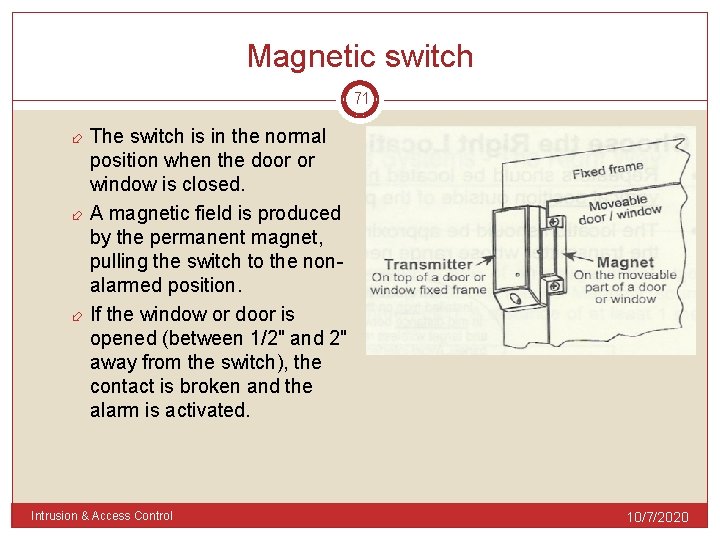
Magnetic switch 70 used to detect the opening of a door or window. Consist of 2 components: 1) a permanent magnet placed in the moving portion of the door or window 2) actual switch, is mounted on the fixed frame or within the frame. Intrusion & Access Control 10/7/2020

Magnetic switch 71 The switch is in the normal position when the door or window is closed. A magnetic field is produced by the permanent magnet, pulling the switch to the nonalarmed position. If the window or door is opened (between 1/2" and 2" away from the switch), the contact is broken and the alarm is activated. Intrusion & Access Control 10/7/2020

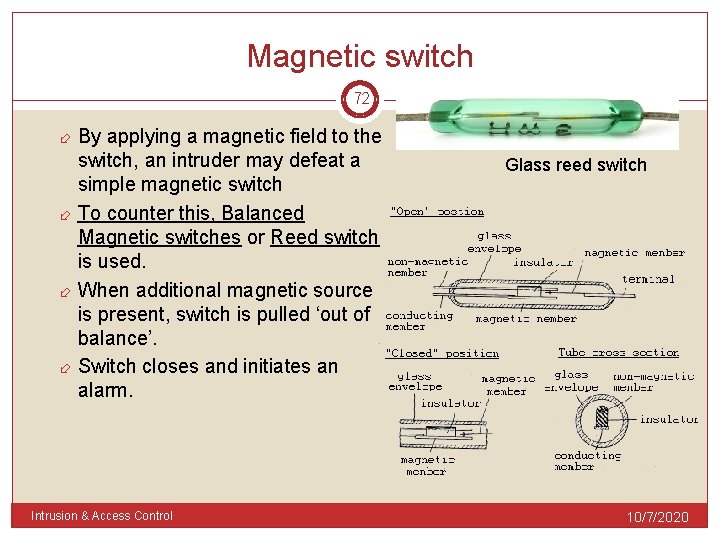
Magnetic switch 72 By applying a magnetic field to the switch, an intruder may defeat a simple magnetic switch To counter this, Balanced Magnetic switches or Reed switch is used. When additional magnetic source is present, switch is pulled ‘out of balance’. Switch closes and initiates an alarm. Intrusion & Access Control Glass reed switch 10/7/2020

Magnetic switch 73 Types of Mountings Surface mount Intrusion & Access Control Recessed mount 10/7/2020

Magnetic switch 74 Avoidance of False Alarms 1. Excessive door or window movement 2. Improper alignment of the switch on door or window 3. Seasonal conditions (heat or cold) Intrusion & Access Control 10/7/2020

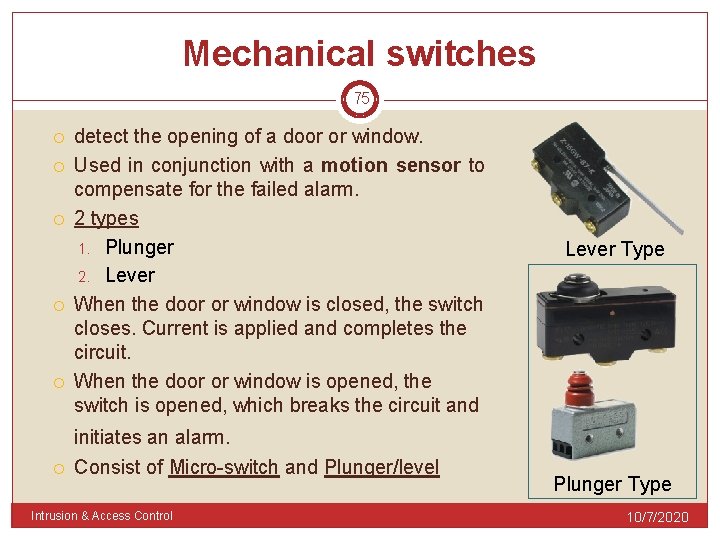
Mechanical switches 75 detect the opening of a door or window. Used in conjunction with a motion sensor to compensate for the failed alarm. 2 types 1. Plunger 2. Lever When the door or window is closed, the switch closes. Current is applied and completes the circuit. When the door or window is opened, the switch is opened, which breaks the circuit and Lever Type initiates an alarm. Consist of Micro-switch and Plunger/level Intrusion & Access Control Plunger Type 10/7/2020

Mechanical switches 76 Operations Micro-switch is connected to an electric circuit to an alarm. When the door/window is closed, the plunger is forced against the microswitch to keep it in a Normally Closed (NC) position. The alarm is set to off. When the window/door is opened, the spring causes the plunger to release. The micro-switch opens the electric circuit and the alarm is turned on. Intrusion & Access Control 10/7/2020

Types of detectors 77 Mechanical switches Applications 1. Perimeter devices 2. Windows/doors/roller shutters 3. Anti-tamper switches protecting enclosures and housings 4. Pressure mats Intrusion & Access Control 10/7/2020

Detector Devices 78 Types of detectors Passive infrared detectors 2. Electromechanical and Mechanical switches/contacts 3. Vibration detectors 4. Glass break detectors 5. Acoustics detectors 6. Video Motion Detection (VMD) sensors 7. Photoelectric detectors 1. Intrusion & Access Control 10/7/2020

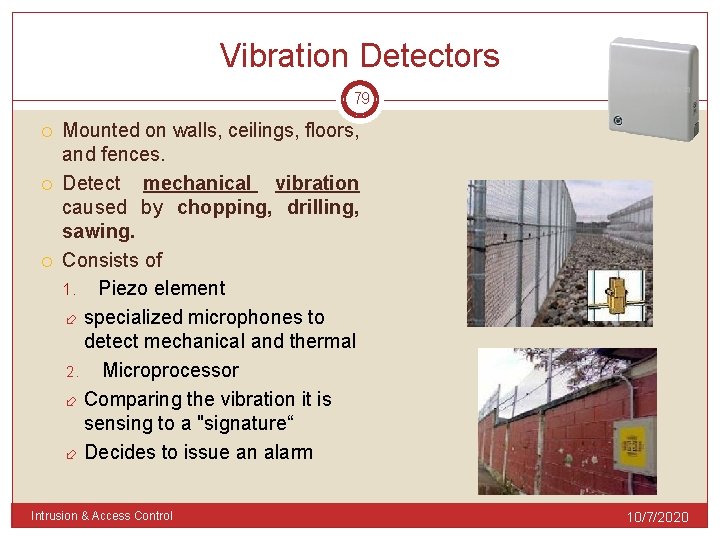
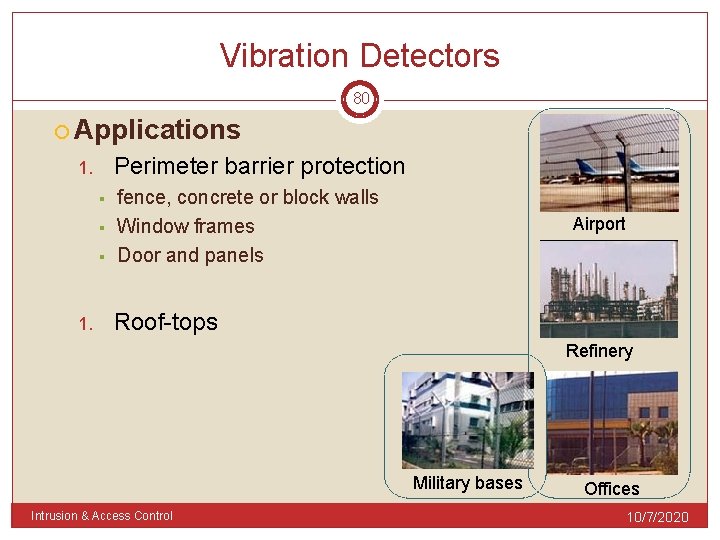
Vibration Detectors 79 Mounted on walls, ceilings, floors, and fences. Detect mechanical vibration caused by chopping, drilling, sawing. Consists of 1. Piezo element specialized microphones to detect mechanical and thermal 2. Microprocessor Comparing the vibration it is sensing to a "signature“ Decides to issue an alarm Intrusion & Access Control 10/7/2020

Vibration Detectors 80 Applications Perimeter barrier protection 1. § § § 1. fence, concrete or block walls Window frames Door and panels Airport Roof-tops Refinery Military bases Intrusion & Access Control Offices 10/7/2020

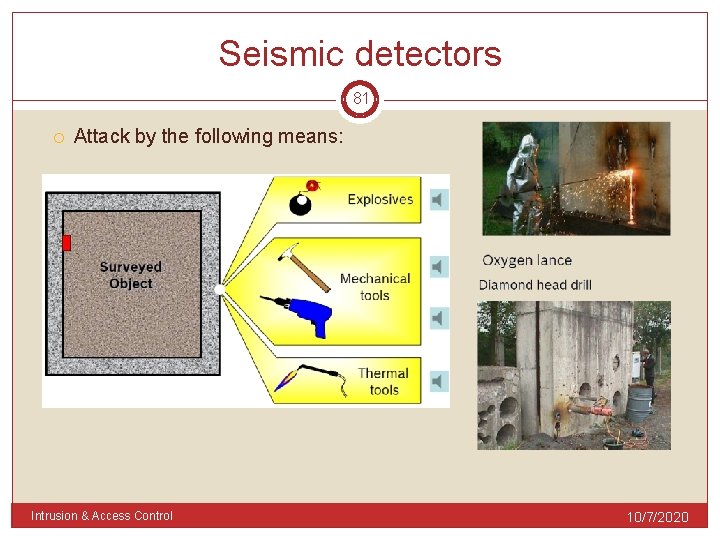
Seismic detectors 81 Attack by the following means: Intrusion & Access Control 10/7/2020

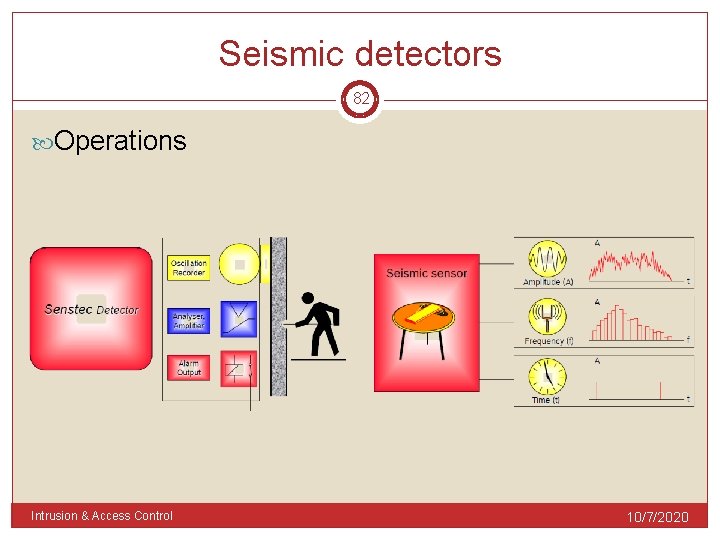
Seismic detectors 82 Operations Intrusion & Access Control 10/7/2020

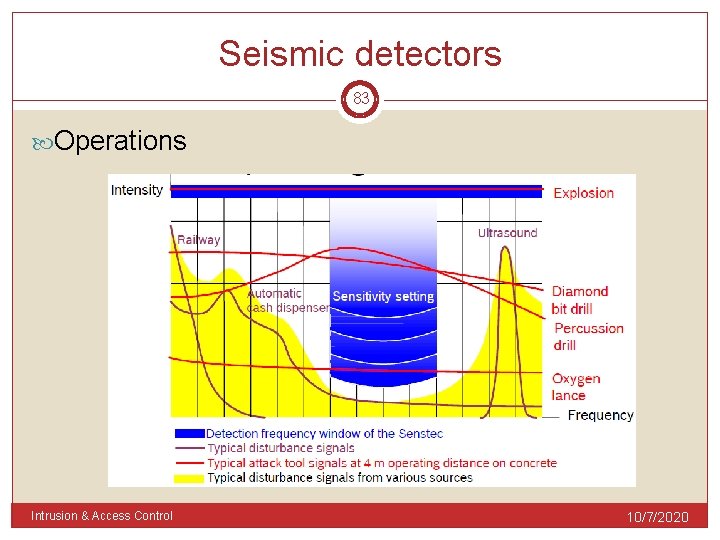
Seismic detectors 83 Operations Intrusion & Access Control 10/7/2020

Seismic detectors 84 Applications 1. 2. 3. 4. 5. Monitoring of safes, cash boxes Ticketing machines Night deposits Automatic teller machines(ATMs) Strong rooms Intrusion & Access Control 10/7/2020

Seismic detectors 85 Installation wall, ceiling or floor, or surfacemounted e. g. to the door of a safe Multi-level sensitivity adjustment Easily fine-tuned to the environmental conditions Intrusion & Access Control 10/7/2020

Detector Devices 86 Types of detectors Passive infrared detectors 2. Electromechanical and Mechanical switches/contacts 3. Vibration detectors 4. Glass break detectors 5. Acoustics detectors 6. Video Motion Detection (VMD) sensors 7. Photoelectric detectors 1. Intrusion & Access Control 10/7/2020

Glassbreak Detectors 87 Monitor glass broken during an intrusion entry. A microphone is used to listen for frequencies associated with breaking glass. A processor is used to filter frequencies not associated with glass breaking and allow only a certain range of frequencies to be analyzed. Intrusion & Access Control 10/7/2020

Glassbreak Detectors 88 3 types of glassbreak detectors 1. Acoustic sensors Detects acoustic sound wave that matches the frequency of broken glass. Shock sensors 2. Detects shock wave when glass is broken Dual-technology sensors 3. Detects acoustic and shock vibrations Intrusion & Access Control 10/7/2020

Glassbreak Detectors 89 Glass Break Detectors Plate glass Tempered glass Laminated glass The 3 different glass types look similar when installed. Each of these present different breakage "sound signature, “ An effective audio glass breakage detector system must be able to recognize all of these signatures. Intrusion & Access Control Plate Glass Shattered tempered glass Laminated Glass 10/7/2020

Glassbreak Detectors 90 Installation 1. According to specifications determined by the manufacturer. 2. Detector should be located inside the protected area 3. Testing done for Glass break Simulate “household” sounds (rattling keys or knocking with keys on glass) § Use a commercial glass break simulator § Adjust the coverage range and sensitivity § Verify the room is suitable for protection by the selected sensor § Intrusion & Access Control 10/7/2020

Glassbreak Detectors 91 Glassbreak detector (Courtesy of Honeywell) Intrusion & Access Control demonstration 10/7/2020

Detector Devices 92 Types of detectors Passive infrared detectors 2. Electromechanical and Mechanical switches/contacts 3. Vibration detectors 4. Glass break detectors 5. Acoustics detectors 6. Video Motion Detection (VMD) detectors 7. Photoelectric detectors 1. Intrusion & Access Control 10/7/2020

Acoustic Detectors 93 High-security device used in quiet area. activated by audible sound energy as a result of intrusion changes sound energy into electrical energy Trigger the alarm state Applications 1. bank vaults 2. strong-rooms Intrusion & Access Control 10/7/2020

Detector Devices 94 Types of detectors Active & Passive infrared detection units 2. Electromechanical and Mechanical switches/contacts 3. Vibration sensors 4. Glass break detectors 5. Acoustics detectors 6. Video Motion Detection (VMD) sensors 1. Intrusion & Access Control 10/7/2020

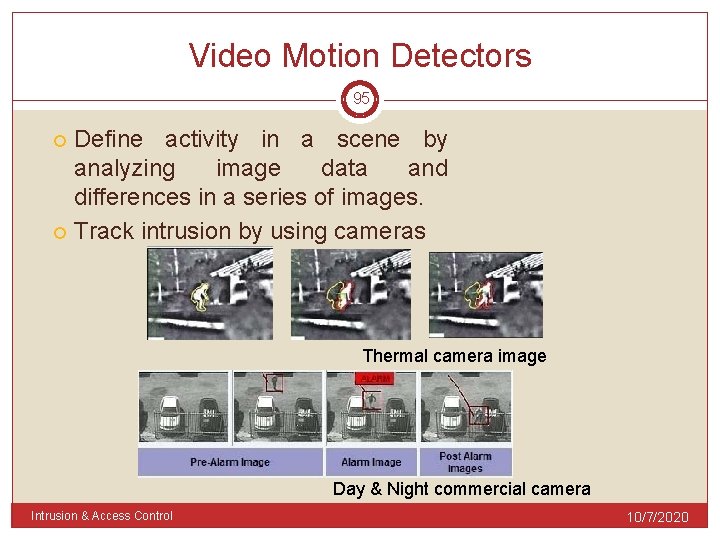
Video Motion Detectors 95 Define activity in a scene by analyzing image data and differences in a series of images. Track intrusion by using cameras Thermal camera image Day & Night commercial camera Intrusion & Access Control 10/7/2020

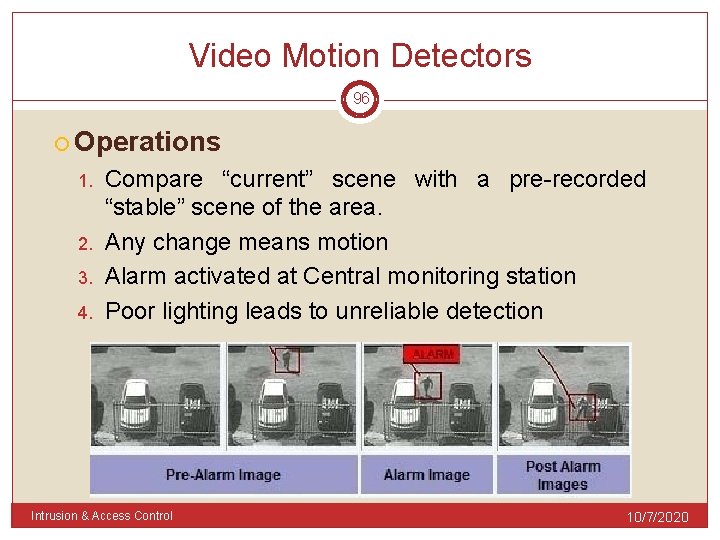
Video Motion Detectors 96 Operations 1. 2. 3. 4. Compare “current” scene with a pre-recorded “stable” scene of the area. Any change means motion Alarm activated at Central monitoring station Poor lighting leads to unreliable detection Intrusion & Access Control 10/7/2020

Video Motion Detectors 97 Applications 1. Physical barrier in perimeter protection 2. Outdoor use Military compounds Airports Object tracking Prisons Borders Detection of removed of left objects 3. Art in museums Intrusion & Access Control 10/7/2020

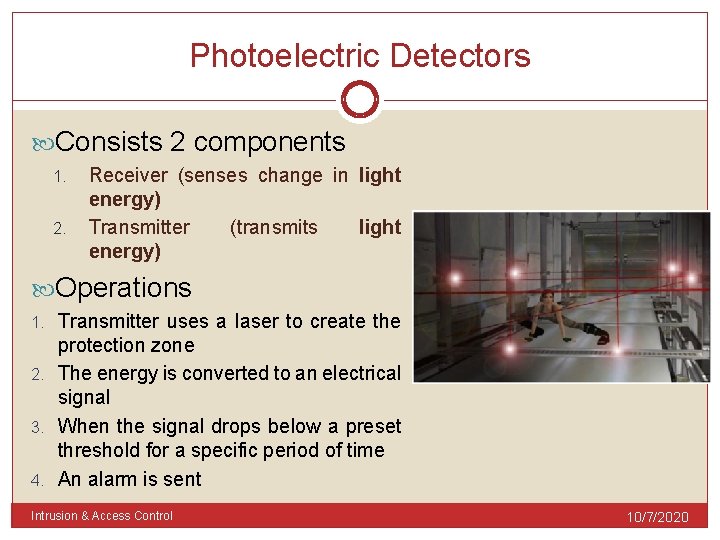
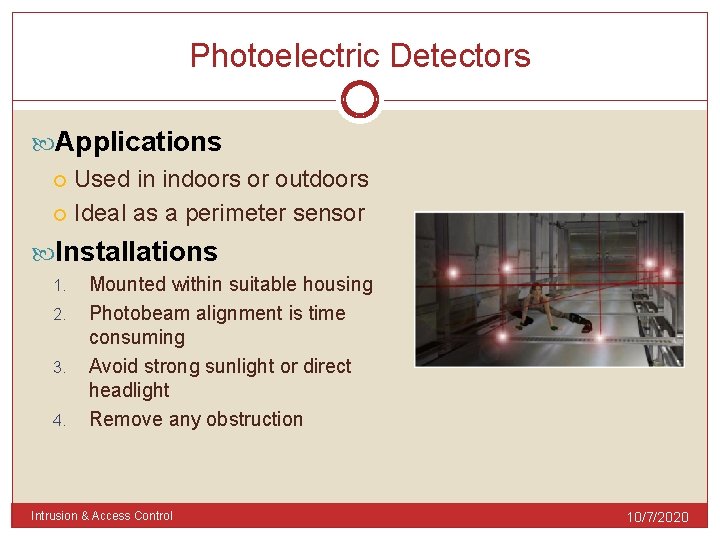
Photoelectric Detectors Consists 2 components 1. 2. Receiver (senses change in light energy) Transmitter (transmits light energy) Operations Transmitter uses a laser to create the protection zone 2. The energy is converted to an electrical signal 3. When the signal drops below a preset threshold for a specific period of time 4. An alarm is sent 1. Intrusion & Access Control 10/7/2020

Photoelectric Detectors Applications Used in indoors or outdoors Ideal as a perimeter sensor Installations 1. 2. 3. 4. Mounted within suitable housing Photobeam alignment is time consuming Avoid strong sunlight or direct headlight Remove any obstruction Intrusion & Access Control 10/7/2020