Access Control Mechanisms all access control approaches rely




























- Slides: 64

Access Control Mechanisms • all access control approaches rely on the following four mechanisms -fundamental functions of access control systems: • ● Identification: I am a user of the system. • ● Authentication: I can prove I’m a user of the system. • ● Authorization: Here’s what I can do with the system. • ● Accountability: You can verify my use of the system.

Identification • mechanism - unverified entities called supplicants who seek access to a resource provide a label by which they are known to the system. • label - an identifier (ID) - must be mapped to one and only one entity within the security domain. • composite identifiers by concatenating elements - department codes, random numbers, or special characters to make unique identifiers within the security domain • Random IDs to protect resources from potential attackers

Authentication • process of validating a supplicant’s purported identity. • three widely used authentication mechanisms, or authentication factors – Something a supplicant knows – Something a supplicant has – Something a supplicant is

Authentication • Something a supplicant knows - what the supplicant knows and can recall—for example, a password, passphrase, or other unique authentication code, such as a personal identification number (PIN) • password is a private word or combination of characters that only the user should know. • passphrase is a series of characters that is typically longer than a password and can be used to derive a virtual password. • typical password - “ 23 skedoo, ”, typical passphrase “May. The. Force. Be. With. You. Always, ” represented as the virtual password “MTFBWYA.

Authentication • Something a Supplicant Has - relies on something a supplicant has and can produce when necessary. • example - dumb cards, such as ID cards or ATM cards with magnetic stripes that contain the digital (and often encrypted) user PIN, which is compared against the number the user enters. • smart card contains a computer chip that can verify and validate several pieces of information instead of just a PIN. • Another example- token - a card or key fob with a computer chip and a liquid crystal display that shows a computer-generated number for remote login authentication. – Tokens - synchronous or asynchronous. – synchronous tokens - synchronized with a server, both the server and token use the same time or a time-based database to generate a number that must be entered during the user login phase. – Asynchronous tokens - don’t require that the server and tokens maintain the same time setting, use a challenge/ response system, in which the server challenges the supplicant during login with a numerical sequence, supplicant places this sequence into the token and receives a response.

Authentication • Something a Supplicant Is (or Can Produce) - relies on individual characteristics - fingerprints, palm prints, hand topography, hand geometry, or retina and iris scans • something a supplicant can produce on demand - voice patterns, signatures, or keyboard kinetic measurements. • known collectively as biometrics • certain critical logical or physical areas - use of strong authentication—at least two authentication mechanisms drawn from two different factors - something you have and something you know. • Example - access to a bank’s ATM services requires a banking card plus a PIN - two-factor authentication • Strong authentication requires - at least one of the mechanisms be something other than what you know.

Authorization • matching of an authenticated entity to a list of information assets and corresponding access levels - an ACL or access control matrix. • 3 ways of handling authorization – authentication process to verify each entity - grants access to resources for only that entity - quickly becomes complex and resource-intensive in a computer system. – Authorization for members of a group - system matches authenticated entities to a list of group memberships - grants access to resources based on the group’s access rights, common authorization method. – Authorization across multiple systems - central authentication and authorization system - verifies an entity’s identity and grants it a set of credentials

Accountability • Auditability • ensures that all actions on a system - authorized or unauthorized - attributed to an authenticated identity. • accomplished by - system logs, database journals, auditing of these records. • Systems logs - failed access attempts and systems modifications. • Logs – uses - intrusion detection, determining the root cause of a system failure, or simply tracking the use of a particular resource.

Biometric access control • • • • relies on recognition Biometric authentication technologies ● Fingerprint comparison of the supplicant’s actual fingerprint to a stored fingerprint ● Palm print comparison ● Hand geometry comparison of the supplicant’s actual hand to a stored measurement ● Facial recognition using a photographic ID card, in which a human security guard compares the supplicant’s face to a photo ● Facial recognition using a digital camera, in which a supplicant’s face is compared to a stored image ● Retinal print comparison of the supplicant’s actual retina to a stored image ● Iris pattern comparison of the supplicant’s actual iris to a stored image three unique human characteristics are usually considered: ● Fingerprints ● Retina of the eye (blood vessel pattern) ● Iris of the eye (random pattern of features found in the iris, including freckles, pits, striations, vasculature, coronas, and crypts)

Biometric access control • scan human characteristics - convert these images to some form of minutiae, subsequent access attempt - compared with an encoded value - verify the user’s identity. • problem with this method - some human characteristics - change over time due to normal development, injury, or illness - must create fall back or failsafe authentication mechanisms. • Signature and voice recognition technologies - biometric access control measures. • Signature recognition - signature capture, for authentication during a purchase, customer signs a digital pad with a special stylus that captures the signature, digitized signature saved for future reference or compared with a signature in a database for validation. • Voice recognition - captures and stores an initial voiceprint of the user reciting a phrase, authentication process requires the user to speak the same phrase - technology can compare the current voiceprint against the stored value

Effectiveness of Biometrics • evaluated on three basic criteria: • the false reject rate - percentage of authorized users who are denied access – Type I error • the false accept rate - percentage of unauthorized users who are granted access – Type II error • the crossover error rate - the level at which the number of false rejections equals the false acceptances.

Firewalls • information security program - prevents specific types of information from moving between two different levels of networks - (an untrusted network like the Internet and a trusted network like the organization’s internal network) • different levels of trust between portions of their network environment - to add extra security for the most important applications and data. • firewall - a separate computer system, a software service running on an existing router or server, or a separate network that contains several supporting devices. • Firewalls - categorized by processing mode, development era, or structure.

Firewall Processing Modes • five major categories – packet-filtering firewalls – Application gateways – circuit gateways – MAC layer firewalls – hybrids

Packet-Filtering Firewalls • examines the header information of data packets • installed on a TCP/IP-based network • functions at the IP level and determines whether to deny (drop) a packet or allow (forward) it to the next network connection • examine every incoming packet header, selectively filter packets based on header information – destination address, source address, packet type, and other key information.

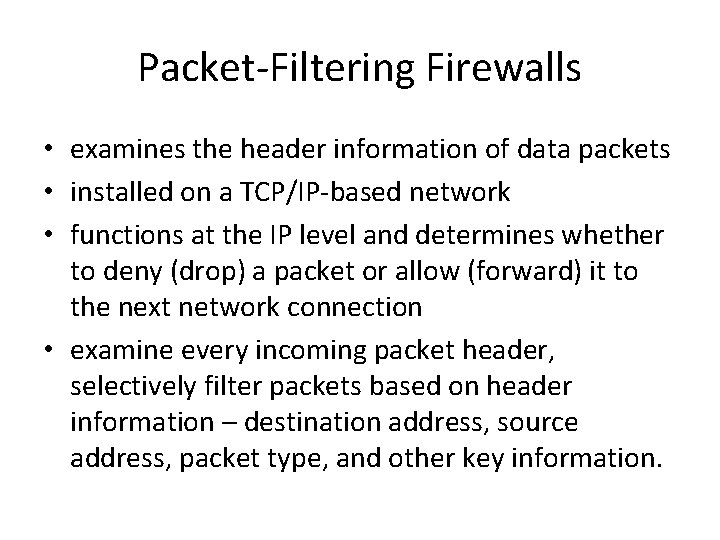
IP Packet Structure

Packet-Filtering Firewalls • If the device finds a packet that matches a restriction - stops the packet from traveling • restrictions are based on, • ● IP source and destination address • ● Direction (inbound or outbound) • ● Protocol, for firewalls capable of examining the IP protocol layer • ●TCP or UDP source and destination port requests

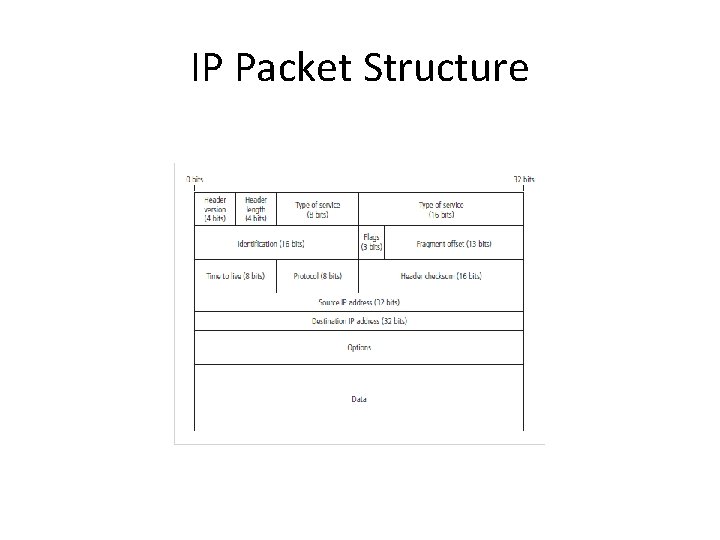
TCP Packet Structure

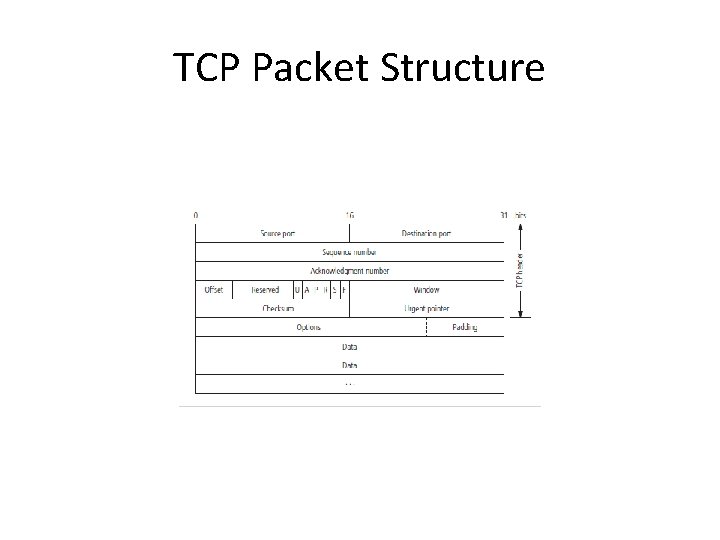
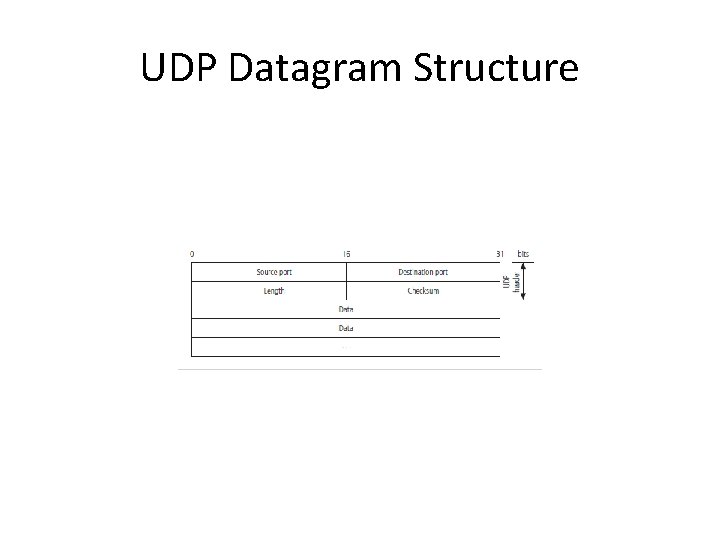
UDP Datagram Structure

Packet Filtering Router

Subset of Packet Filtering Firewall • • static filtering dynamic filtering stateful packet inspection (SPI). enforce address restrictions, rules designed to prohibit packets with certain addresses or partial addresses from passing through the device.

Static Filtering • filtering rules be developed and installed with the firewall. • rules are created and sequenced by a person who either directly edits the rule set or uses a programmable interface to specify the rules and the sequence. • Any changes to the rules require human intervention. • common in network routers and gateways.

Dynamic filtering firewall • react to an emergent event and update or create rules to deal with that event. • reaction – positive - allowing an internal user to engage in a specific activity upon request • Reaction – negative - dropping all packets from a particular address when an increased presence of a particular type of malformed packet is detected. • allows only a particular packet with a particular source, destination, and port address to enter. (static-filtering firewalls allow entire sets of one type of packet to enter in response to authorized requests) • works by opening and closing “doors” in the firewall based on the information contained in the packet header • dynamic packet filters an intermediate form between traditional static packet filters and application proxies.

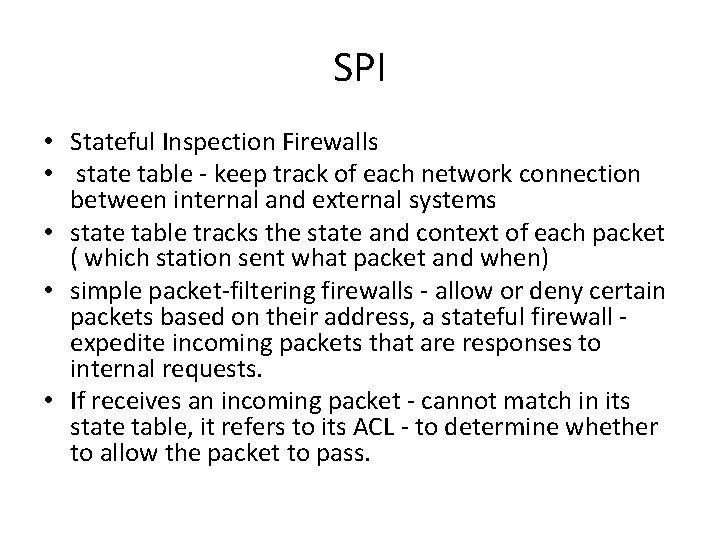
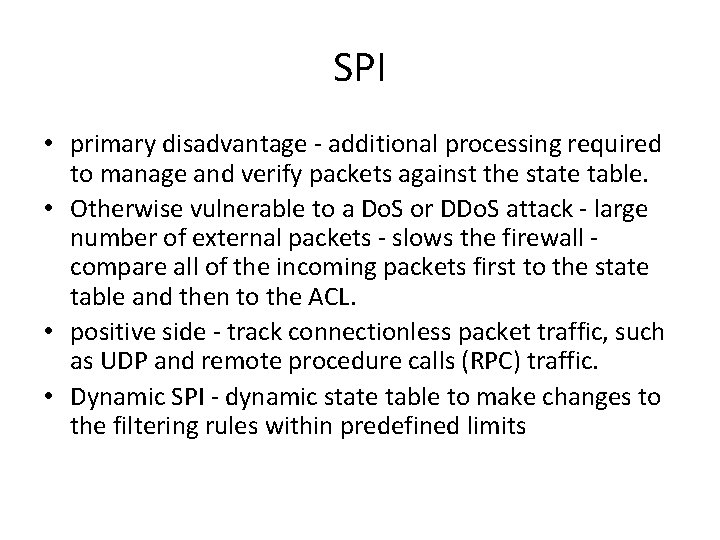
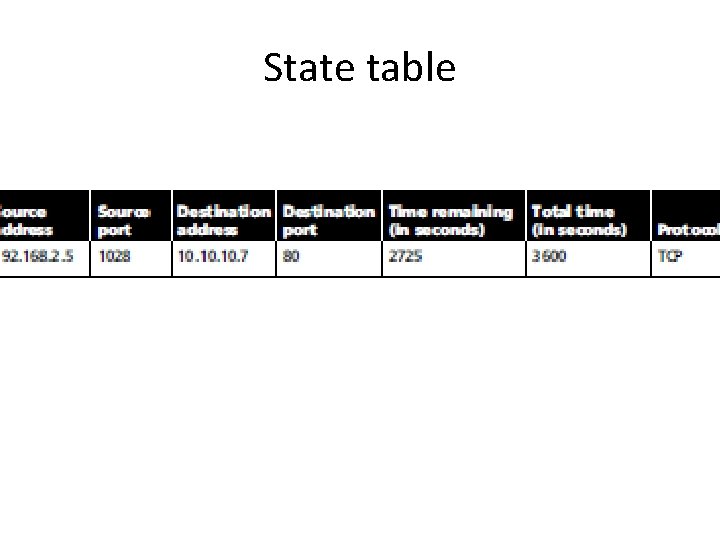
SPI • Stateful Inspection Firewalls • state table - keep track of each network connection between internal and external systems • state table tracks the state and context of each packet ( which station sent what packet and when) • simple packet-filtering firewalls - allow or deny certain packets based on their address, a stateful firewall expedite incoming packets that are responses to internal requests. • If receives an incoming packet - cannot match in its state table, it refers to its ACL - to determine whether to allow the packet to pass.

SPI • primary disadvantage - additional processing required to manage and verify packets against the state table. • Otherwise vulnerable to a Do. S or DDo. S attack - large number of external packets - slows the firewall compare all of the incoming packets first to the state table and then to the ACL. • positive side - track connectionless packet traffic, such as UDP and remote procedure calls (RPC) traffic. • Dynamic SPI - dynamic state table to make changes to the filtering rules within predefined limits

State table

Application Layer Firewall • Installed on a dedicated computer separate from the filtering router • commonly used in conjunction with a filtering router. • Also known as application firewall, a proxy server or reverse proxy

Application Firewall • Example - Web server - avoid exposure to users, installs a proxy server-registered domain URL. • receives requests for Web pages - accesses the Web server on behalf of the external client, returns the requested pages to the users. • Stores the most recently accessed pages internal cache - cache servers.

Application Firewall • Benefit - the proxy server - placed in an unsecured area of the network or in the demilitarized zone (DMZ) - exposed to the higher levels of risk from less trusted networks - than exposing the Web server to such risks. • Additional filtering routers - implemented behind the proxy server - limiting access to the more secure internal system, provides further protection

Application Firewall • Disadvantage - designed for specific protocols, not easy to reconfigure to protect against attacks • work at the application layer by definition restricted to a single application such as FTP, Telnet, HTTP, SMTP, or SNMP – due to processing time and resources - to read each packet down to the application layer

MAC Layer Firewalls • filtering decisions based on the specific host computer’s identity - represented by its MAC or NIC address. • link the addresses of specific host computers to ACL entries - identify the specific types of packets that can be sent to each host and block all other traffic.

Hybrid Firewall • combine the elements of other types of firewalls — elements of packet filtering and proxy services or of packet filtering and circuit gateways • consist of two separate firewall devices; each is a separate firewall system, connected so that they work in tandem. • Unified Threat Management (UTM) - devices are categorized by their ability to perform the work of an SPI firewall, network intrusion detection and prevention system, content filter, spam filter, and malware scanner and filter.

Hybrid firewall • UTM systems - advantage - increasing memory capacity and processor capability and reduce the complexity associated with deploying, configuring, and integrating multiple networking devices. • proper configuration - down to protocol layers and examine application-specific data, encrypted data, compressed data, and encoded data. • primary disadvantage of UTM systems - creation of a single point of failure if the device has technical problems.

Firewall Architecture • Configuration - mutually exclusive or combined • Factors - objectives of the network, organization’s ability to develop and implement the architectures and the budget available • four common architectural implementations: – packet-filtering routers – dual homed firewalls (bastion hosts) – screened host firewalls – screened subnet firewalls.

Packet filtering routers • Some form of router • Boundary between internal n/w and external service provider • Many packets- rejected – to lower the risk of attack • Drawback- lack of auditing and strong authentication

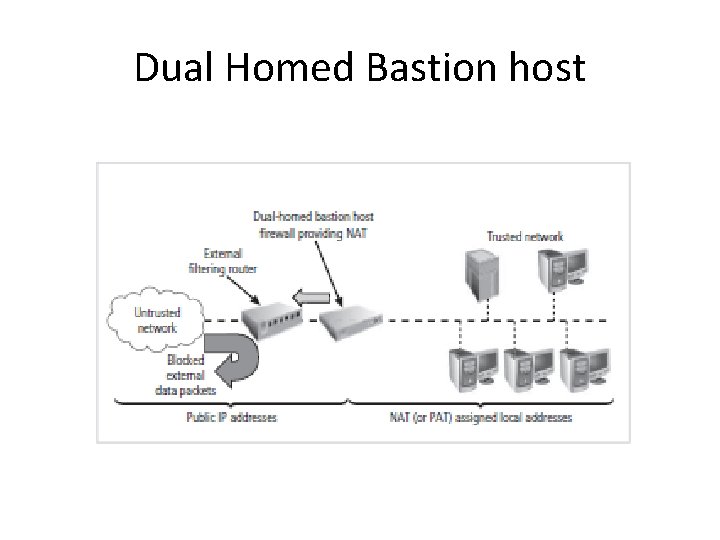
Bastion Host • Single firewall – protection behind router – sole defender on n/w perimeter-also called sacrificial host • Configuration – as a switch or as in-line between router and inside n/w – hence called dual homed firewall • 2 NIC – external and internal n/w

Dual Homed Bastion host

Bastion Host • For implementation – NAT or PAT , (NAPT) - map valid external address to internal IPv 4 address, IPv 6 – Unique local address(ULA) • NAT address- 3 ranges – Class A, B, C - 24, 20, 16 bits respectively • Internal address – message not routed externally, direct connection to external n/w , avoid NAT server – prevents external attacks • PAT- map many internal hosts to single external IP address • For integrity of communication – assigns unique port address to ext. IP and socket (port+address) to internal IP

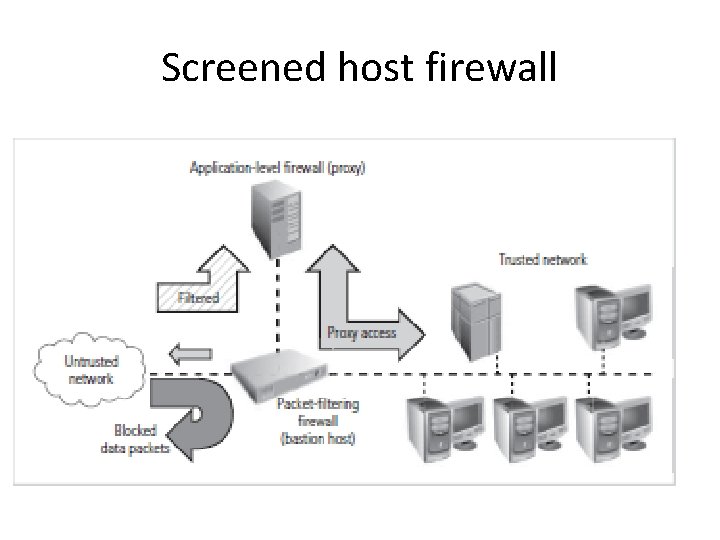
Screened host firewall • Packet filtering router + dedicated firewall (application proxy server) • Prescreen packets to n/w traffic and put all load on internal proxy server • Application proxy server – stores the web documents – unexpected loss of information when system is compromised • Compromise of bastion host – attack on proxy server – n/w and all internal information obtained • External attack – 2 separate systems – should be compromised before accessing data.

Screened host firewall

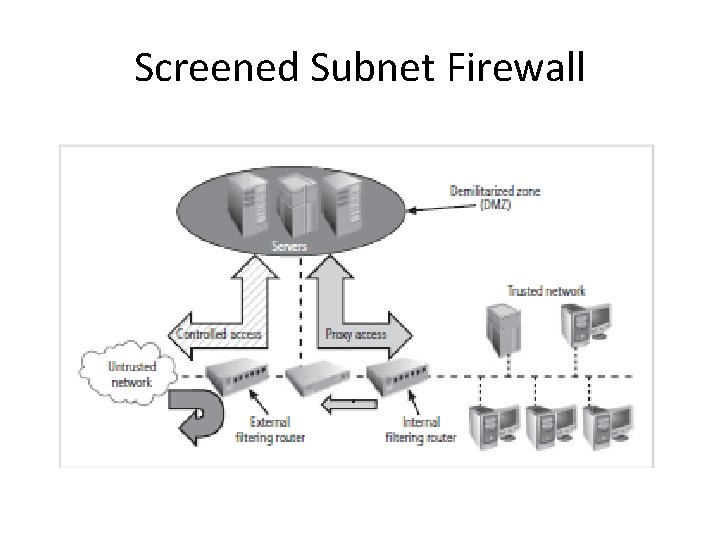
Screened Subnet Firewall(with DMZ) • Dominant architecture • DMZ-dedicated port on firewall device – connects to single BH or to screened subnet • DMZ- servers of untrusted n/w (FTP server, Web Server or some database server) • Common arrangement – 2 or more internal bastion hosts behind a packet-filtering router, with each host protecting the trusted network • 2 variations – (i) 2 filtering routers with 1 or more BHs, (ii)connections from outside - external filter , routing firewall , then to DMZ, connections inside internal n/w –only from DMZ BH server

Screened Subnet Firewall

Screened Subnet Firewall • Main functions – protection of DMZ system and information , more secure than general public networks but less secure than the internal network • Protection of internal network (limit the access to external connections) • Extremely secure, expensive and complex to configure and manage • DMZ – creation of Extranet – additional authentication and authorization controls, example – online retailer

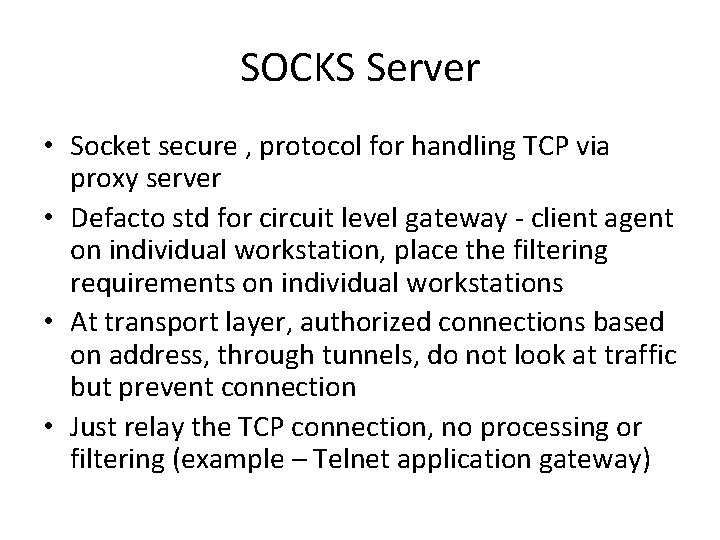
SOCKS Server • Socket secure , protocol for handling TCP via proxy server • Defacto std for circuit level gateway - client agent on individual workstation, place the filtering requirements on individual workstations • At transport layer, authorized connections based on address, through tunnels, do not look at traffic but prevent connection • Just relay the TCP connection, no processing or filtering (example – Telnet application gateway)

Selecting the Right Firewall • Firewall technology – – right balance between protection and cost – features for base price and extra cost for additional features – are all these cost factors known? – setup and configuration – easy or not – adapt to growing network

Firewall Rules and Managing Firewalls • Good policy and practice – configuration rule instructions a system administrator codes into a server, networking device, or security device to specify how it operates • Syntax error – easy to identify, alert to system administrator, • Logic error – allow instead of deny, wrong port or service, wrong switch etc • Novice administrator - virus screening firewall – blocks all emails instead of preventing malicious code in emails

Best practices • All traffic from the trusted network is allowed out. • The firewall device is never directly accessible from the public network for configuration or management purposes. • SMTP data is allowed to enter through the firewall, but is routed to a well-configured SMTP gateway to filter and route messaging traffic securely • ICMP data should be denied • Telnet (terminal emulation) access should be blocked to all internal servers from the public networks • When Web services are offered outside the firewall, HTTP traffic should be blocked from internal networks through the use of some form of proxy access or DMZ architecture. • All data that is not verifiably authentic should be denied

Firewall Rules • determining whether to allow or deny a packet – predetermined set of specific rules – firewall administrator or dynamic creation based on request • logical set – firewall rules, a rule base, or firewall logic. • Principle - “that which is not permitted is prohibited, ” also known as expressly permitted rules.

Firewall Rules • separate access control lists are created for each interface • creates a set of unidirectional flow checks for dual-homed hosts • filter packets by protocol name as opposed to protocol port number - Telnet protocol packets usually go to TCP port 23, redirected to another much higher port number in an attempt to conceal the activity

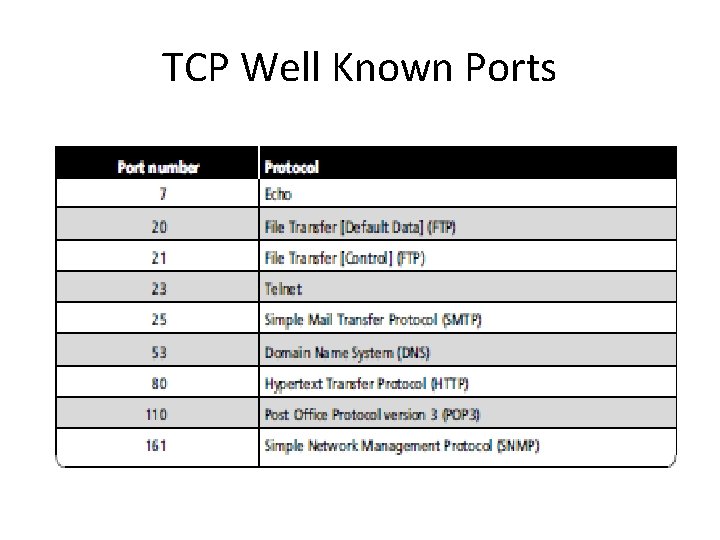
TCP Well Known Ports

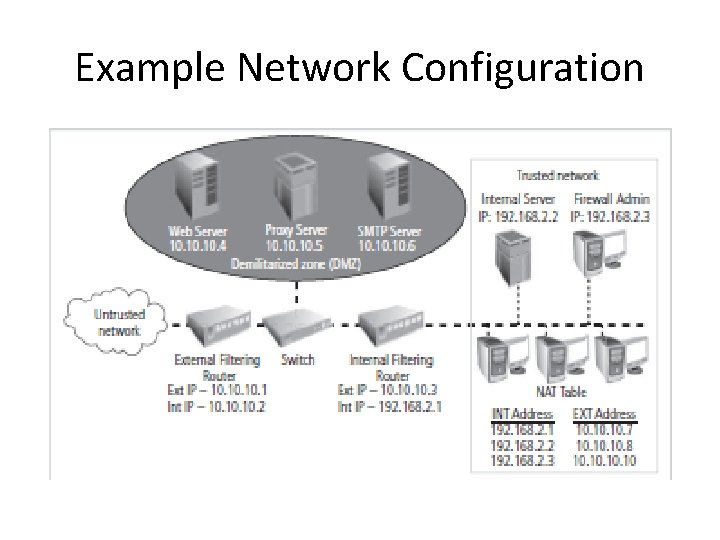
Example Network Configuration

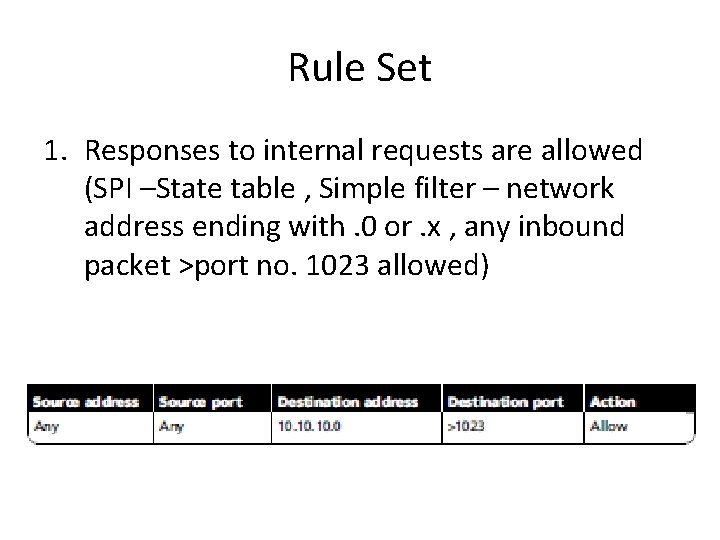
Rule Set 1. Responses to internal requests are allowed (SPI –State table , Simple filter – network address ending with. 0 or. x , any inbound packet >port no. 1023 allowed)

RULE SET 2. The firewall device is never accessible directly from the public network – attackers access firewall – modify or delete rules and allow unwanted traffic rule for external filtering and firewall only

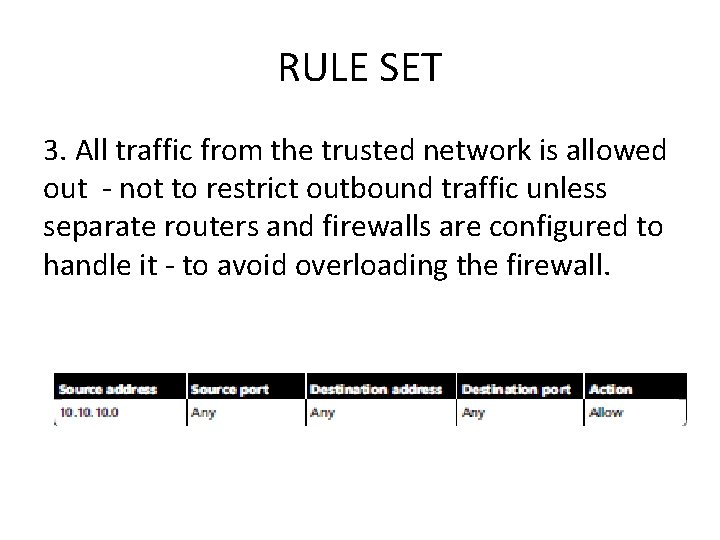
RULE SET 3. All traffic from the trusted network is allowed out - not to restrict outbound traffic unless separate routers and firewalls are configured to handle it - to avoid overloading the firewall.

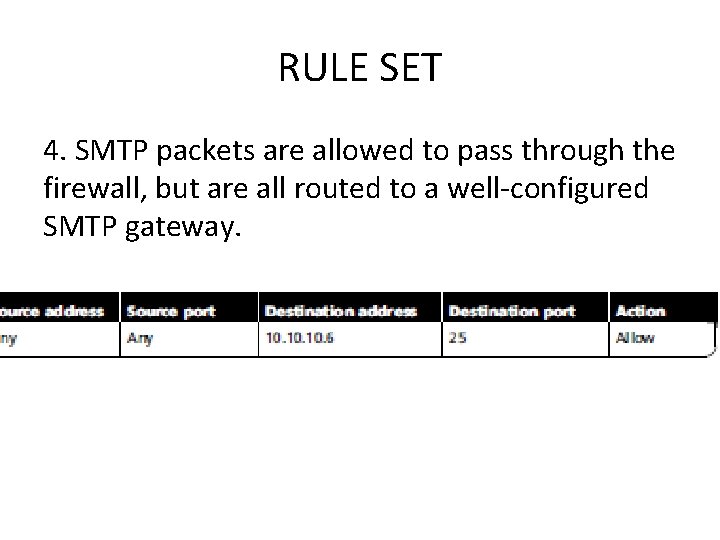
RULE SET 4. SMTP packets are allowed to pass through the firewall, but are all routed to a well-configured SMTP gateway.

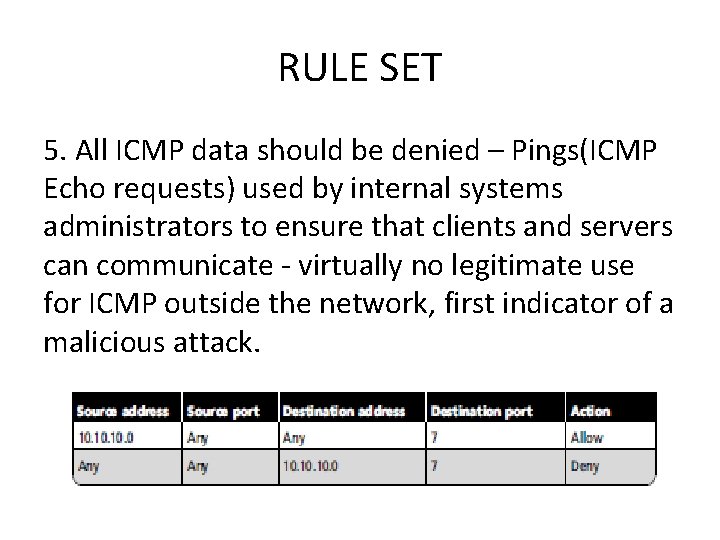
RULE SET 5. All ICMP data should be denied – Pings(ICMP Echo requests) used by internal systems administrators to ensure that clients and servers can communicate - virtually no legitimate use for ICMP outside the network, first indicator of a malicious attack.

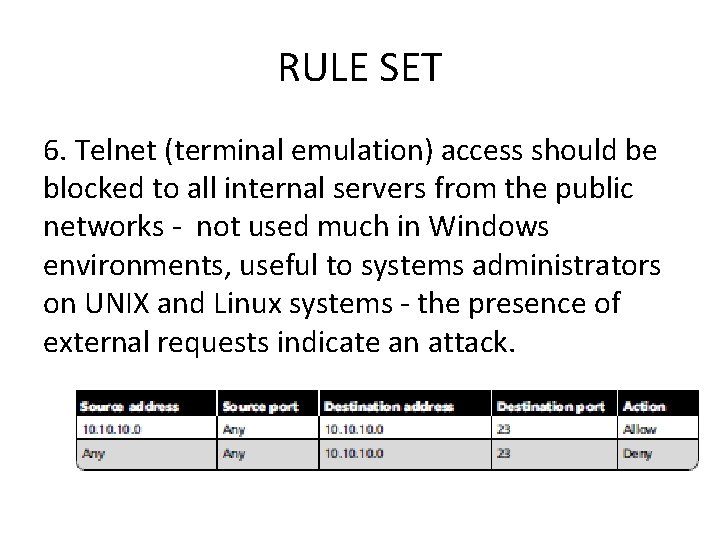
RULE SET 6. Telnet (terminal emulation) access should be blocked to all internal servers from the public networks - not used much in Windows environments, useful to systems administrators on UNIX and Linux systems - the presence of external requests indicate an attack.

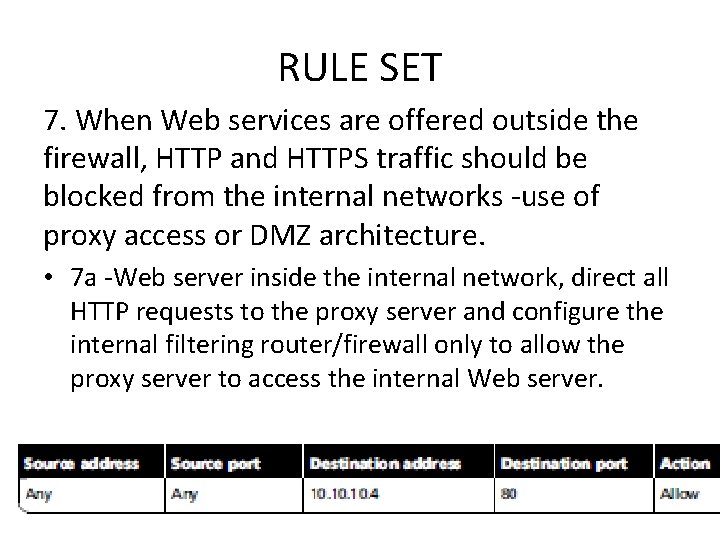
RULE SET 7. When Web services are offered outside the firewall, HTTP and HTTPS traffic should be blocked from the internal networks -use of proxy access or DMZ architecture. • 7 a -Web server inside the internal network, direct all HTTP requests to the proxy server and configure the internal filtering router/firewall only to allow the proxy server to access the internal Web server.

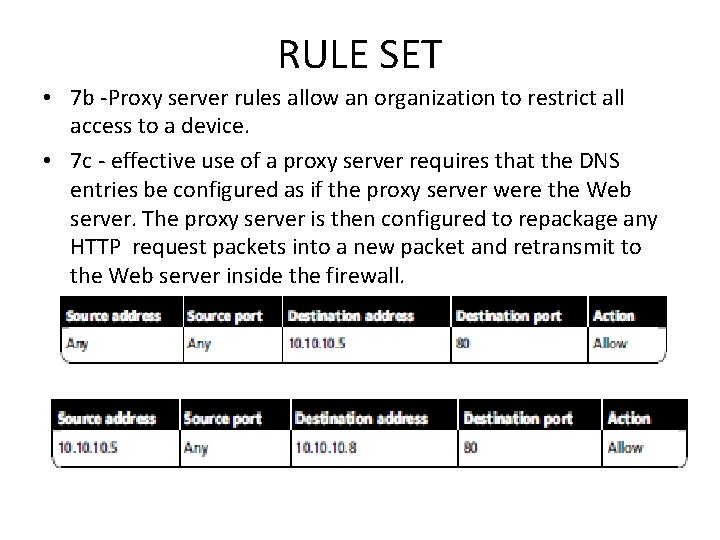
RULE SET • 7 b -Proxy server rules allow an organization to restrict all access to a device. • 7 c - effective use of a proxy server requires that the DNS entries be configured as if the proxy server were the Web server. The proxy server is then configured to repackage any HTTP request packets into a new packet and retransmit to the Web server inside the firewall.

RULE SET • 8. The clean up rule. As a general practice in firewall rule construction, if a request for a service is not explicitly allowed by policy, that request should be denied by a rule.

Virtual Private Networks • Implementation of cryptographic technology • Private data network – use public telecommunication infrastructure and security procedure – privacy through tunneling • Secure extension of internal network connection to remote locations • 3 technologies – Trusted, Secure and hybrid – Trusted – legacy n/w, leased circuit packet switching, must trust service provider, properly maintained and protected – Secured – use security protocols (IPSec), encrypt data over unsecured public network – Hybrid – combination, encrypted transmissions over some or all of trusted VPN

VPN • For security and reliability – ensure o Encapsulation –incoming and outgoing data , native protocol –embedded – routed through public n/w and used by server environment o Encryption – privacy of data contents o Authentication – remote computer and user • Common implementation-turn into private n/w • User – tunneling points across internet – send encrypted data back and forth – IP packet within IP packet – safety and security

VPN • Server support – Microsoft s/w, 2012 • Client support - Windows 7&8 • Less costly compared to true pvt n/w configuration • IPSec-dominant protocol, either stand alone or coupled with layer 2 tunneling protocol (L 2 TP) – Transport and Tunnel Mode operation

Transport Mode VPN • Data encrypted , not header • Secure link to remote host • Eavesdropper –identify destination system, compromise anyone end node and packet information, no need of specific servers and tunneling software • Useful for traveling and telecommuting employees • 2 Uses – end to end transport of encrypted data, each machine acts as end node VPN server and client – remote access workers connect to office n/w through VPN server on perimeter of n/w, VPN server intermediate node , acts as if part of LAN

Tunnel Mode VPN • 2 perimeter tunnel servers, encrypt all traffic to unsecured n/w • Entire packet encryption, added to data part of packet address to tunneling server • Primary benefit-intermediate packet – no information about true destination system • Example-Internet Security & Acceleration Server (ISA)-gateway to gateway tunnel-point to point tunneling protocol, L 2 TP, IPSec • Client side-Windows 7 or 8 , user-Internet through ISP or direct n/w connection, establishes link to remote VPN server