Chapter 4 Security Policies 4 1 Security Policies










- Slides: 15

Chapter 4: Security Policies 4. 1 Security Policies 4. 2 Types of Security Policies 4. 3 The Role of Trust 4. 4 Types of Access Control Introduction to Computer Security © 2004 Matt Bishop Slide #4 -1

Security Policy Definition: a security policy is a statement that partitions system states into: Authorized (secure) These are states the system can enter Unauthorized (nonsecure) If the system enters any of these states, it’s a security violation Slide #4 -2

Secure System Definition: a secure system is a system Starts in authorized state Never enters unauthorized state http: //www. blog. transmac. eu/wp-content/uploads/2015/06/secure-system-3 -big. jpg Slide #4 -3

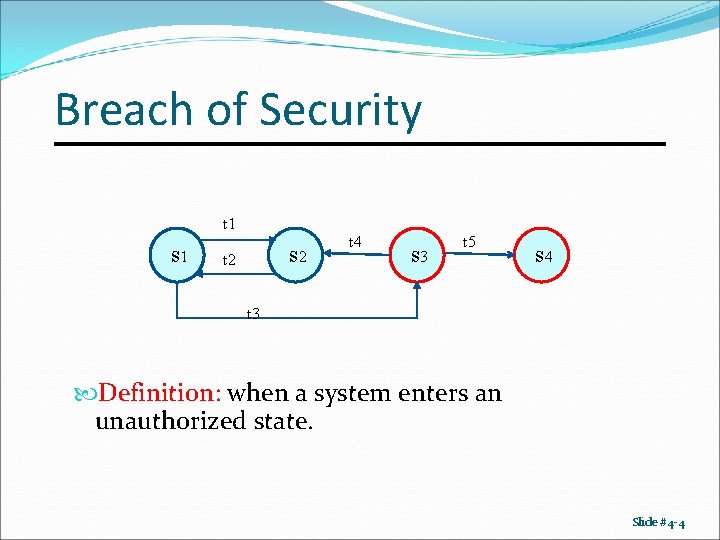
Breach of Security t 1 s 2 t 4 s 3 t 5 s 4 t 3 Definition: when a system enters an unauthorized state. Slide #4 -4

Definition 4 -4: Confidentiality X set of entities, I information I has confidentiality property with respect to X if no x X can obtain information from I I can be disclosed to others Example: X set of students I final exam answer key I is confidential with respect to X if students cannot obtain final exam answer key Slide #4 -5

Definition 4 -5: Integrity X set of entities, I information I has integrity property with respect to X if all x X trust information in I Types of integrity: trust I, its conveyance and protection (data integrity) I information about origin of something or an identity (origin integrity, authentication) I resource: means resource functions as it should (assurance) Slide #4 -6

Definition 4 -6: Availability X set of entities, I resource I has availability property with respect to X if all x X can access I Types of availability: traditional: x gets access or not quality of service: promised a level of access (for example, a specific level of bandwidth) and not meet it, even though some access is achieved, e. g. service is not provided in a timely manner; Slide #4 -7

Definition 4 -7: Mechanism A security mechanism is an entity or procedure that enforces some part of the security policy; Example: Policy: the statement that no student may copy another student’s homework; Mechanism: file access control; set permission to prevent access to a particular file; Slide #4 -8

Types of Security Policies Definition 4 -9: Military (governmental) security policy Policy primarily protecting confidentiality; Example: information about a military mission; Definition 4 -10: Commercial security policy Policy primarily protecting integrity Confidentiality: leak of customer account information; Integrity: modification of customer account balance; Slide #4 -9

Types of Security Policies Definition 4 -11: Confidentiality policy Policy protecting only confidentiality Definition 4 -12: Integrity policy Policy protecting only integrity Slide #4 -10

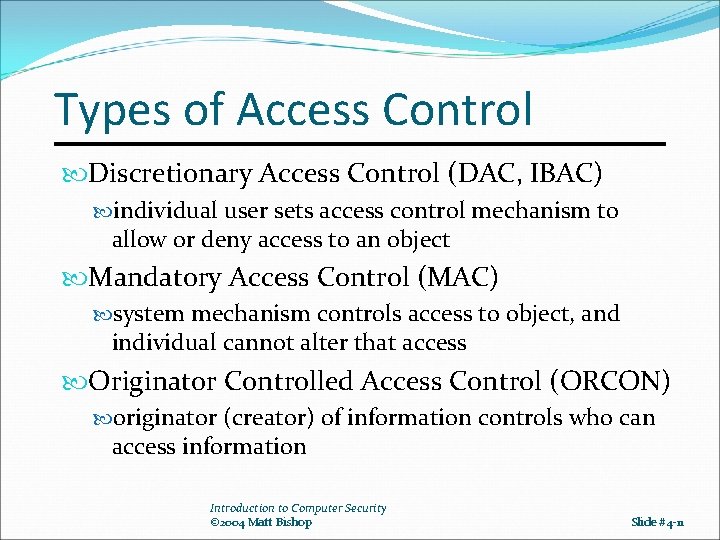
Types of Access Control Discretionary Access Control (DAC, IBAC) individual user sets access control mechanism to allow or deny access to an object Mandatory Access Control (MAC) system mechanism controls access to object, and individual cannot alter that access Originator Controlled Access Control (ORCON) originator (creator) of information controls who can access information Introduction to Computer Security © 2004 Matt Bishop Slide #4 -11

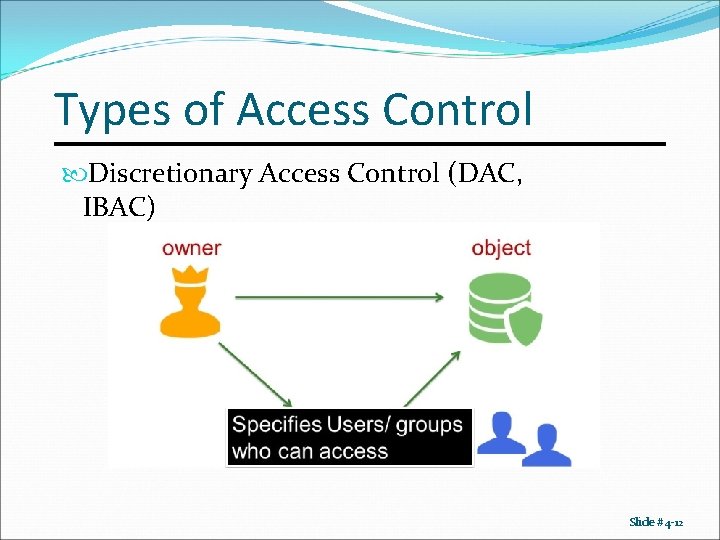
Types of Access Control Discretionary Access Control (DAC, IBAC) Slide #4 -12

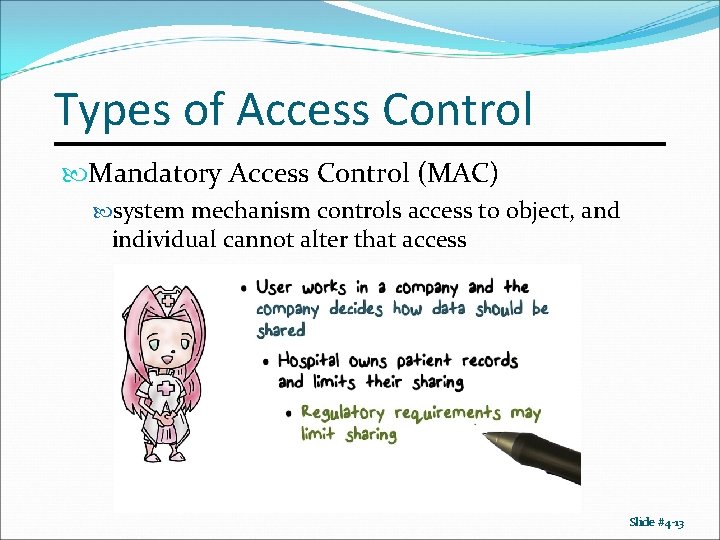
Types of Access Control Mandatory Access Control (MAC) system mechanism controls access to object, and individual cannot alter that access Slide #4 -13

Types of Access Control Originator Controlled Access Control (ORCON) originator (creator) of information controls who can access information; Micro. Soft sold you a software: now you are the owner and Micro. Soft is the Originator; You, as the owner, can not distribute the software to others; Micro. Soft, the originator, decides who can access the software; Slide #4 -14

DAC vs ORCON Is the Owner the same as the Originator? If yes, then it is DAC; If no, then it is ORCON; In other words, has the originator passed the data to another person? If the originator still owns the data, then it is DAC; otherwise, it is ORCON; Slide #4 -15