Simplifying Secure Server Access Control Why Upgrade to








- Slides: 20

Simplifying Secure Server Access Control: Why Upgrade to CA Privileged Access Manager Server Control Steve Mc. Cullar Advisor, Solution Strategy Mike Dullea Sr. Director Product Management August 16 th, 2016

Agenda 1 PRIVILEGED ACCOUNT AT RISK: SECURITY AND COMPLIANCE CHALLENGES 2 ADDRESSING SECURITY AND COMPLIANCE RISKS WITH PAM 3 HOW CA TECHNOLOGIES CAN HELP 4 WHAT’S NEW IN CA PRIVILEGED ACCESS MANAGER SERVER CONTROL 5 THE ROAD AHEAD: OUR PRIVILEGED ACCESS MANAGEMENT STRATEGY 6 Q&A 2 © 2016 CA. ALL RIGHTS RESERVED.

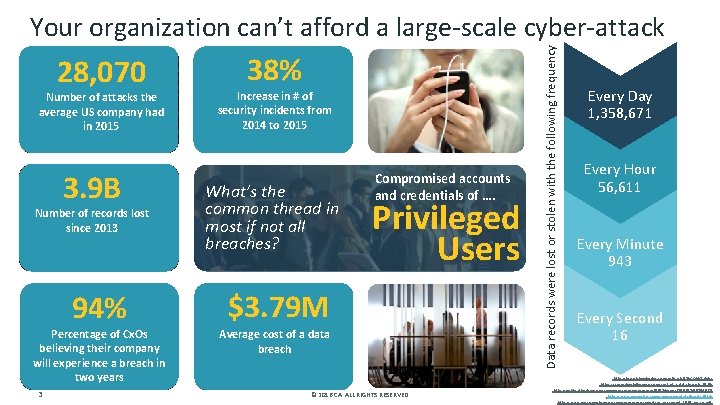
28, 070 Number of attacks the average US company had in 2015 3. 9 B Number of records lost since 2013 94% Percentage of Cx. Os believing their company will experience a breach in two years 3 38% Increase in # of security incidents from 2014 to 2015 What’s the common thread in most if not all breaches? Compromised accounts and credentials of …. Privileged Users $3. 79 M Average cost of a data breach © 2016 CA. ALL RIGHTS RESERVED. Data records were lost or stolen with the following frequency Your organization can’t afford a large-scale cyber-attack Every Day 1, 358, 671 Every Hour 56, 611 Every Minute 943 Every Second 16 http: //breachlevelindex. com/#sthash. RZh. GQk. VZ. dpbs https: //securityintelligence. com/cost-of-a-data-breach-2015/ http: //public. dhe. ibm. com/common/ssi/ecm/se/en/sel 03074 usen/SEL 03074 USEN. PDF http: //www. vormetric. com/campaigns/datathreat/2016/ http: //www. verizonenterprise. com/resources/report/rp_pci-report-2015_en_xg. pdf

But the reality is … The risks are greater than ever CYBERCRIME § Target— 70 million credit cards stolen § Home Depot— 56 million credit cards stolen § JP Morgan Chase— 76 million account records stolen CYBERESPIONAGE § Anthem— 80 million personal records stolen § Forbes. com and unidentified health insurer—targeted (defense contractors, government workers) information gathering of individual data BUSINESS IMPACT § § 4 Code. Spaces—forced out of business Sony Pictures—extensive disruption German Steel Mill—physical damage Saudi Aramco—physical systems damage and business disruption © 2016 CA. ALL RIGHTS RESERVED.

“For digital businesses, privileged identity management becomes both incredibly important and challenging. It’s important because one administrator with malicious intent or theft of administrator credentials can have a disastrous effect on your customers, revenues and long-term reputation. ” - Forrester Research “Critical Questions To Ask Your Privileged Identity Management Solution Provider", Forrester Research, September 9, 2014. http: //www. informationisbeautiful. net/visualizations/worlds-biggest-data-breaches-hacks/ The frequency and severity of breaches are increasing ‘Privilege exploits’ as a common attack vector 5 © 2016 CA. ALL RIGHTS RESERVED. http: //www. informationisbeautiful. net/visualizations/worlds-biggest-data-breaches-hacks/

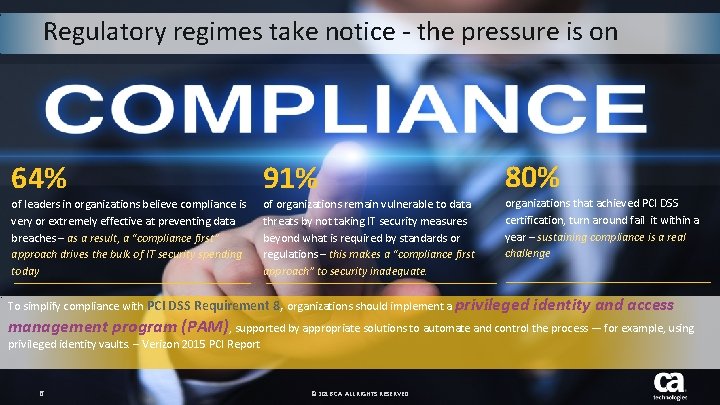
Regulatory regimes take notice - the pressure is on 64% of leaders in organizations believe compliance is very or extremely effective at preventing data breaches – as a result, a “compliance first” approach drives the bulk of IT security spending today 91% of organizations remain vulnerable to data threats by not taking IT security measures beyond what is required by standards or regulations – this makes a “compliance first approach” to security inadequate. 80% organizations that achieved PCI DSS certification, turn around fail it within a year – sustaining compliance is a real challenge To simplify compliance with PCI DSS Requirement 8, organizations should implement a privileged identity and access management program (PAM), supported by appropriate solutions to automate and control the process — for example, using privileged identity vaults. – Verizon 2015 PCI Report 6 © 2016 CA. ALL RIGHTS RESERVED.

Addressing security and compliance risks With Privileged Access Management STOP TARGETED ATTACKS 7 MITIGATE INSIDER THREATS ACHIEVE & SUSTAIN COMPLIANCE © 2016 CA. ALL RIGHTS RESERVED. IMPROVE EFFICIENCIES SECURE THE HYBRID ENTERPRISE

How CA Technologies can help CA Privileged Access Manager § Access requests § Certification § Risk analytics CA IDENTITY GOVERNANCE Delivering comprehensive Privileged Access Management solutions § § § § CA Privileged Access Manager Server Control Strong authentication, including MFA Credential management Policy-based, least privilege access control Command filtering Session recording, auditing, attribution Application password management Comprehensive, hybrid enterprise protection Self-contained, hardened appliance In-depth protection for critical servers Highly-granular access controls Segregated duties of super-users Controlled access to system resources such as files, folders, processes and registries § Secured Task Delegation (sudo) § Enforce Trusted Computing Base § Unix Authentication Bridge § § NETWORK-BASED SECURITY § HOST-BASED SECURITY DEFENSE IN DEPTH 8 © 2016 CA. ALL RIGHTS RESERVED.

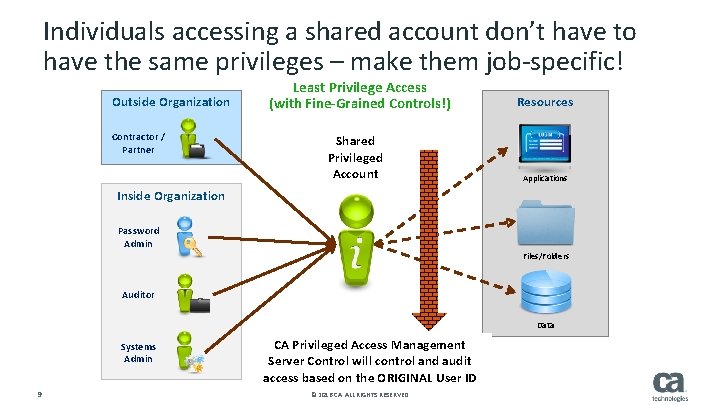
Individuals accessing a shared account don’t have to have the same privileges – make them job-specific! Outside Organization Contractor / Partner Least Privilege Access (with Fine-Grained Controls!) Shared Privileged Account Resources Applications Inside Organization Password Admin Files/Folders Auditor Data Systems Admin 9 CA Privileged Access Management Server Control will control and audit access based on the ORIGINAL User ID © 2016 CA. ALL RIGHTS RESERVED.

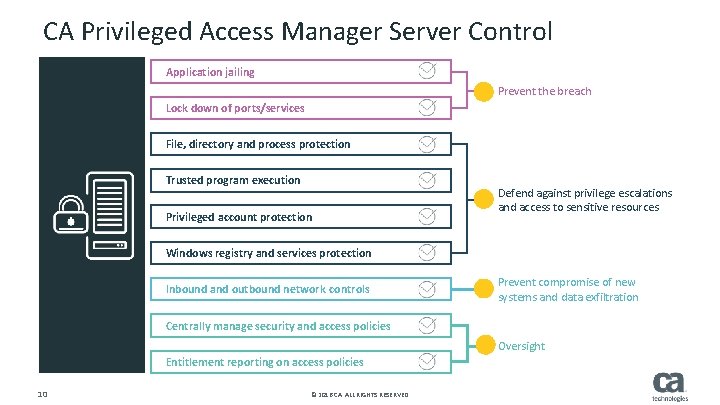
CA Privileged Access Manager Server Control Application jailing Prevent the breach Lock down of ports/services File, directory and process protection Trusted program execution Privileged account protection Defend against privilege escalations and access to sensitive resources Windows registry and services protection Inbound and outbound network controls Prevent compromise of new systems and data exfiltration Centrally manage security and access policies Oversight Entitlement reporting on access policies 10 © 2016 CA. ALL RIGHTS RESERVED.

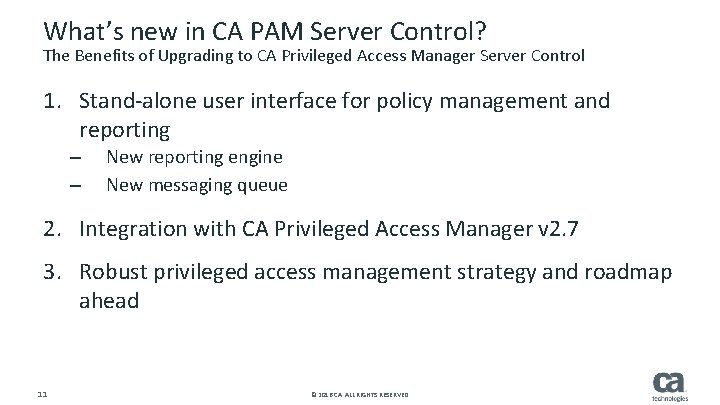
What’s new in CA PAM Server Control? The Benefits of Upgrading to CA Privileged Access Manager Server Control 1. Stand-alone user interface for policy management and reporting – – New reporting engine New messaging queue 2. Integration with CA Privileged Access Manager v 2. 7 3. Robust privileged access management strategy and roadmap ahead 11 © 2016 CA. ALL RIGHTS RESERVED.

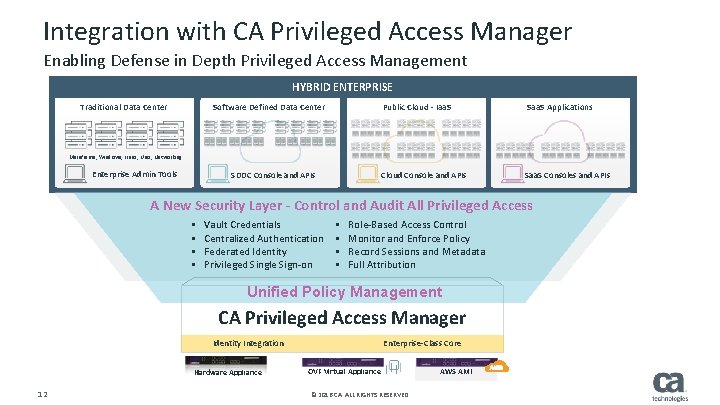
Integration with CA Privileged Access Manager Enabling Defense in Depth Privileged Access Management HYBRID ENTERPRISE Traditional Data Center Software Defined Data Center Public Cloud - Iaa. S Saa. S Applications Cloud Console and APIs Saa. S Consoles and APIs Mainframe, Windows, Linux, Unix, Networking Enterprise Admin Tools SDDC Console and APIs A New Security Layer - Control and Audit All Privileged Access § § Vault Credentials Centralized Authentication Federated Identity Privileged Single Sign-on § § Role-Based Access Control Monitor and Enforce Policy Record Sessions and Metadata Full Attribution Unified Policy Management CA Privileged Access Manager Identity Integration Hardware Appliance 12 Enterprise-Class Core OVF Virtual Appliance © 2016 CA. ALL RIGHTS RESERVED. AWS AMI

A Peek Into the Future 13 © 2016 CA. ALL RIGHTS RESERVED.

Strategic Themes Data Breach Prevention 14 Hybrid Enterprise Protection © 2016 CA. ALL RIGHTS RESERVED. Security Ecosystem Integration

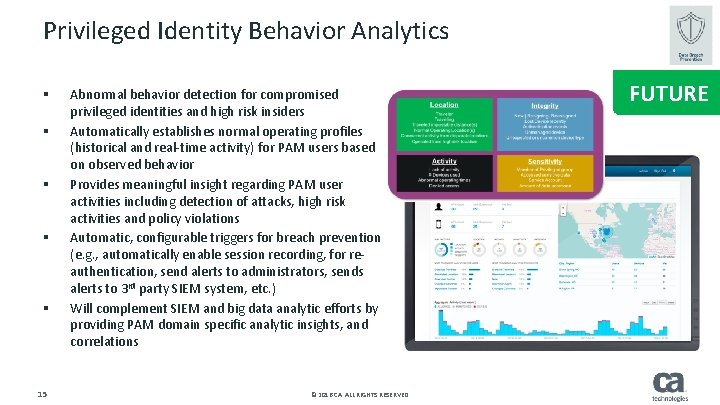
Privileged Identity Behavior Analytics § § § 15 Abnormal behavior detection for compromised privileged identities and high risk insiders Automatically establishes normal operating profiles (historical and real-time activity) for PAM users based on observed behavior Provides meaningful insight regarding PAM user activities including detection of attacks, high risk activities and policy violations Automatic, configurable triggers for breach prevention (e. g. , automatically enable session recording, for reauthentication, send alerts to administrators, sends alerts to 3 rd party SIEM system, etc. ) Will complement SIEM and big data analytic efforts by providing PAM domain specific analytic insights, and correlations © 2016 CA. ALL RIGHTS RESERVED. FUTURE

Additional agent capabilities and platform coverage § Enhanced Policy Management Capabilities – Wizard-based approach – Simplified management of access control policies § Additional platform support – Support for Docker Containers § Enhanced access control capability – Intercepting system calls for Unix (Ptrace Interception) 16 © 2016 CA. ALL RIGHTS RESERVED. FUTURE

Deep Integration with Microsoft Azure § Extend deep integration of PAM to Azure, similar to the current capabilities with PAM and Amazon Web Services § Some capabilities may include: – CA PAM running in Azure and Azure. Gov as a Virtual Machine – Azure Credentials Management (vaulting of Azure credentials in PAM) – Azure Portal Auto-Login, Session Recording, and DVR-like Playback – Azure VM Discovery, Sync, and Dynamic Policy – Azure VM Auto-Login, Session Recording, and DVR-like Playback – Azure Active Directory Authentication (via SAML) 17 © 2016 CA. ALL RIGHTS RESERVED. FUTURE

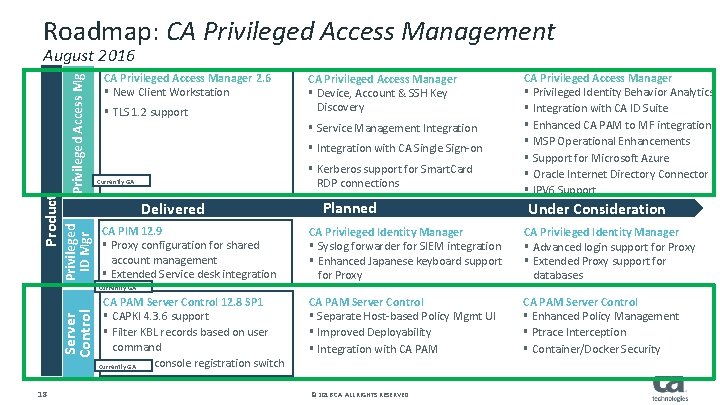
Roadmap: CA Privileged Access Management Privileged Access Mgr CA Privileged Access Manager 2. 6 § New Client Workstation § TLS 1. 2 support CA Privileged Access Manager § Device, Account & SSH Key Discovery § Service Management Integration § Integration with CA Single Sign-on § Kerberos support for Smart. Card RDP connections Currently GA Delivered Privileged ID Mgr Product August 2016 CA PIM 12. 9 § Proxy configuration for shared account management § Extended Service desk integration Planned CA Privileged Access Manager § Privileged Identity Behavior Analytics § Integration with CA ID Suite § Enhanced CA PAM to MF integration § MSP Operational Enhancements § Support for Microsoft Azure § Oracle Internet Directory Connector § IPV 6 Support Under Consideration CA Privileged Identity Manager § Syslog forwarder for SIEM integration § Enhanced Japanese keyboard support for Proxy CA Privileged Identity Manager § Advanced login support for Proxy § Extended Proxy support for databases CA PAM Server Control § Separate Host-based Policy Mgmt UI § Improved Deployability § Integration with CA PAM Server Control § Enhanced Policy Management § Ptrace Interception § Container/Docker Security Server Control Currently GA 18 CA PAM Server Control 12. 8 SP 1 § CAPKI 4. 3. 6 support § Filter KBL records based on user command § New UX console registration switch Currently GA © 2016 CA. ALL RIGHTS RESERVED.

Disclaimer Certain information in this presentation may outline CA’s general product direction. This presentation shall not serve to (i) affect the rights and/or obligations of CA or its licensees under any existing or future license agreement or services agreement relating to any CA software product; or (ii) amend any product documentation or specifications for any CA software product. This presentation is based on current information and resource allocations as of July 1, 2016 and is subject to change or withdrawal by CA at any time without notice. The development, release and timing of any features or functionality described in this presentation remain at CA’s sole discretion. Notwithstanding anything in this presentation to the contrary, upon the general availability of any future CA product release referenced in this presentation, CA may make such release available to new licensees in the form of a regularly scheduled major product release. Such release may be made available to licensees of the product who are active subscribers to CA maintenance and support, on a when and ifavailable basis. The information in this presentation is not deemed to be incorporated into any contract. Copyright © 2016 CA. All rights reserved. All trademarks, trade names, service marks and logos referenced herein belong to their respective companies. THIS PRESENTATION IS FOR YOUR INFORMATIONAL PURPOSES ONLY. CA assumes no responsibility for the accuracy or completeness of the information. TO THE EXTENT PERMITTED BY APPLICABLE LAW, CA PROVIDES THIS DOCUMENT “AS IS” WITHOUT WARRANTY OF ANY KIND, INCLUDING, WITHOUT LIMITATION, ANY IMPLIED WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, OR NONINFRINGEMENT. In no event will CA be liable for any loss or damage, direct or indirect, in connection with this presentation, including, without limitation, lost profits, lost investment, business interruption, goodwill, or lost data, even if CA is expressly advised in advance of the possibility of such damages. 19 © 2016 CA. ALL RIGHTS RESERVED.
