OWASP Top 10 All rights reserved www keepcoding















- Slides: 87

OWASP Top 10 © All rights reserved. www. keepcoding. io

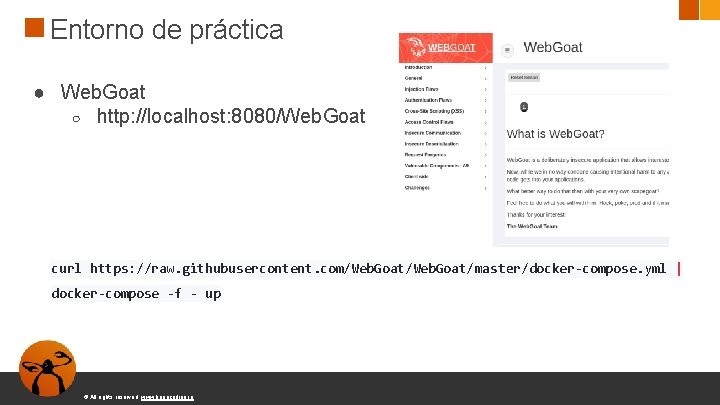
Entorno de práctica ● Web. Goat ○ http: //localhost: 8080/Web. Goat curl https: //raw. githubusercontent. com/Web. Goat/master/docker-compose. yml | docker-compose -f - up © All rights reserved. www. keepcoding. io

HTTP Proxies ● ● Burp Proxy Owasp ZAP Postman Insomnia © All rights reserved. www. keepcoding. io

Burp Suite © All rights reserved. www. keepcoding. io

Burp Suite © All rights reserved. www. keepcoding. io

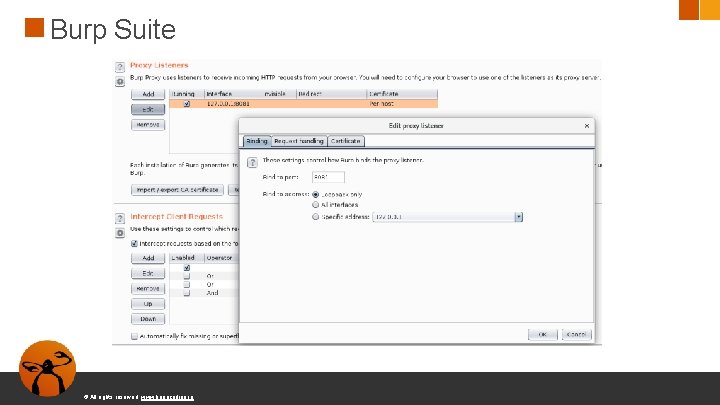
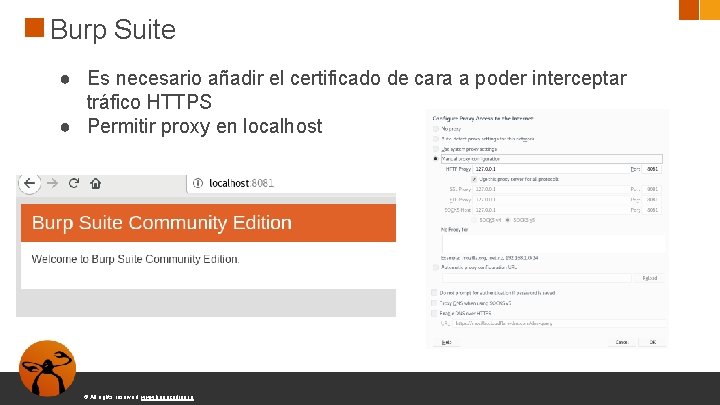
Burp Suite ● Es necesario añadir el certificado de cara a poder interceptar tráfico HTTPS ● Permitir proxy en localhost © All rights reserved. www. keepcoding. io

A 1: 2017 - Injection ● Fallos que permiten inyección, como SQL, No. SQL, OS y LDAP ● Ocurren cuando un atacante consigue enviar datos que modifican una query o comando © All rights reserved. www. keepcoding. io

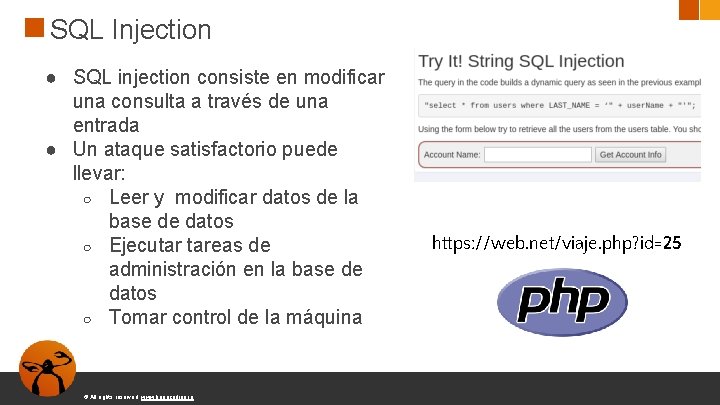
SQL Injection ● SQL injection consiste en modificar una consulta a través de una entrada ● Un ataque satisfactorio puede llevar: ○ Leer y modificar datos de la base de datos ○ Ejecutar tareas de administración en la base de datos ○ Tomar control de la máquina © All rights reserved. www. keepcoding. io https: //web. net/viaje. php? id=25

SQL Injection ● Forzar a True la consulta ● ‘ or ‘ 1’=’ 1 © All rights reserved. www. keepcoding. io

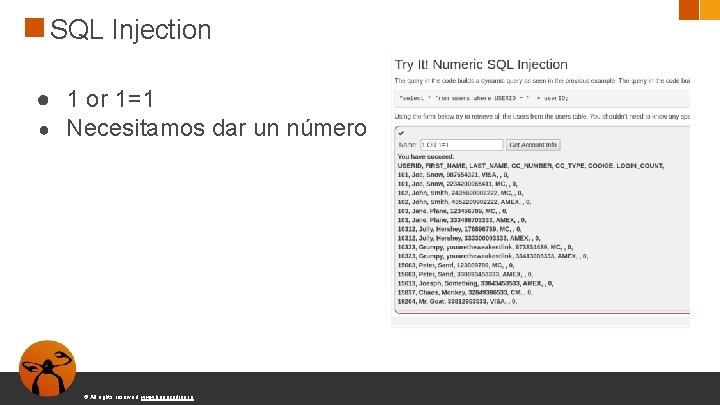
SQL Injection ● 1 or 1=1 ● Necesitamos dar un número © All rights reserved. www. keepcoding. io

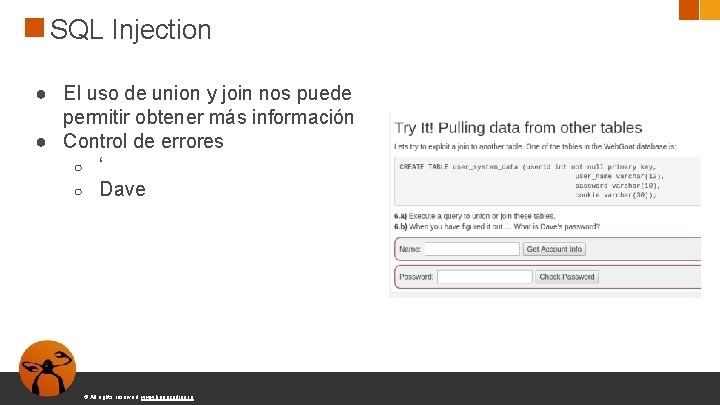
SQL Injection ● El uso de union y join nos puede permitir obtener más información ● Control de errores ○ ‘ ○ Dave © All rights reserved. www. keepcoding. io

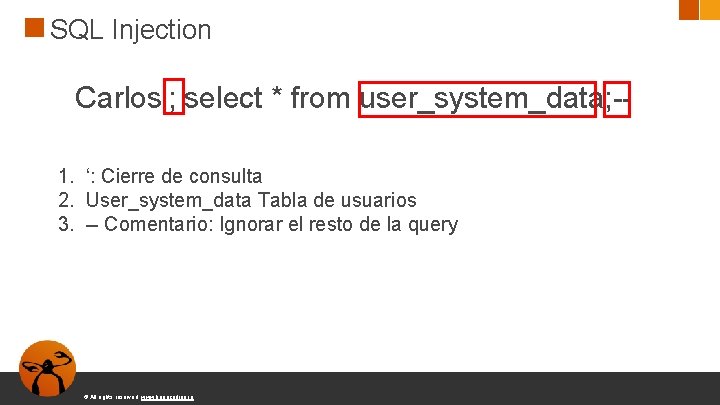
SQL Injection Carlos'; select * from user_system_data; -1. ‘: Cierre de consulta 2. User_system_data Tabla de usuarios 3. -- Comentario: Ignorar el resto de la query © All rights reserved. www. keepcoding. io

Blind SQL Injection ● El control de errores dificulta el ataque pero no lo hace inviable ● Se utilizan consultas con un resultado booleano ○ https: //my-shop. com? article=4 AND 1=1 ○ https: //my-shop. com? article=4 AND 1=2 ● Consultas basadas en tiempo ○ article = 4; sleep(10) -- © All rights reserved. www. keepcoding. io

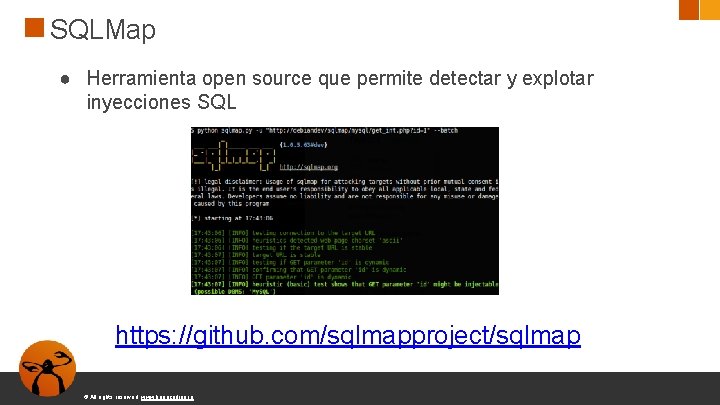
SQLMap ● Herramienta open source que permite detectar y explotar inyecciones SQL https: //github. com/sqlmapproject/sqlmap © All rights reserved. www. keepcoding. io

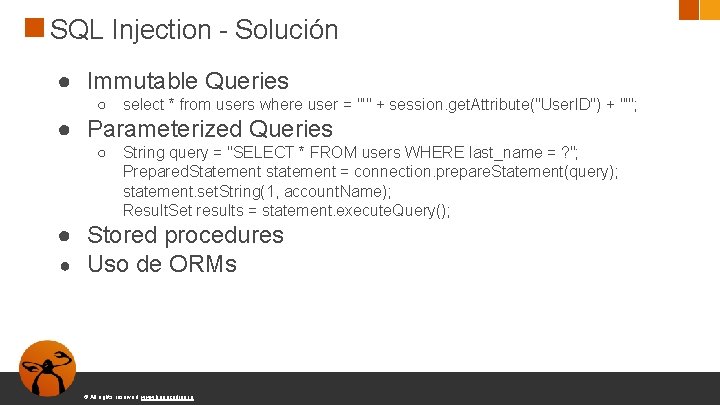
SQL Injection - Solución ● Immutable Queries ○ select * from users where user = "'" + session. get. Attribute("User. ID") + "'"; ● Parameterized Queries ○ String query = "SELECT * FROM users WHERE last_name = ? "; Prepared. Statement statement = connection. prepare. Statement(query); statement. set. String(1, account. Name); Result. Set results = statement. execute. Query(); ● Stored procedures ● Uso de ORMs © All rights reserved. www. keepcoding. io

SQL Injection - Solución ● Validación de la entrada del usuario ○ Nunca debemos confiar en los datos proporcionados por el usuario ● Conectarse con los menores privilegios ○ Permisos de lectura/escritura ○ Limitar acceso a tablas © All rights reserved. www. keepcoding. io

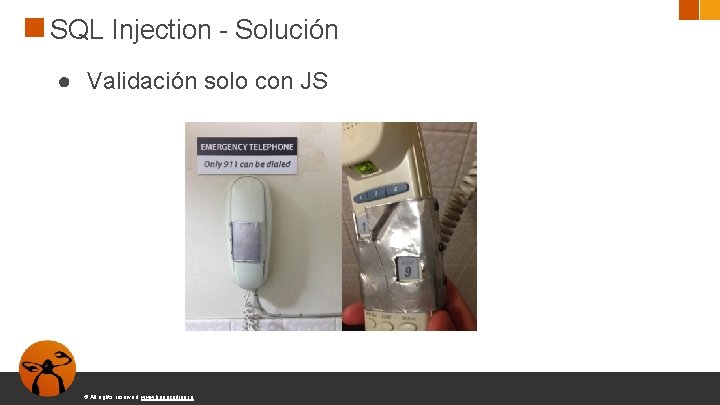
SQL Injection - Solución ● Validación solo con JS © All rights reserved. www. keepcoding. io

A 2: 2017 - Broken Authentication Las funciones de autenticación y manejo de sesiones no están implementadas correctamente. Permiten a atacantes robar contraseñas, claves, tokens de sesión o explotar otros fallos ● Permite ataques de fuerza bruta ● Contraseñas débiles o conocidas © All rights reserved. www. keepcoding. io

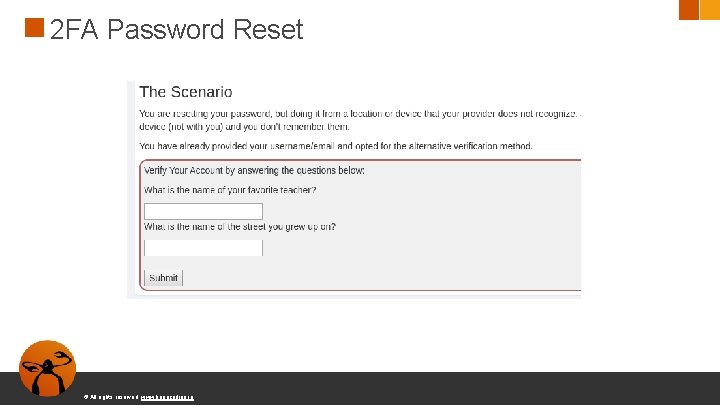
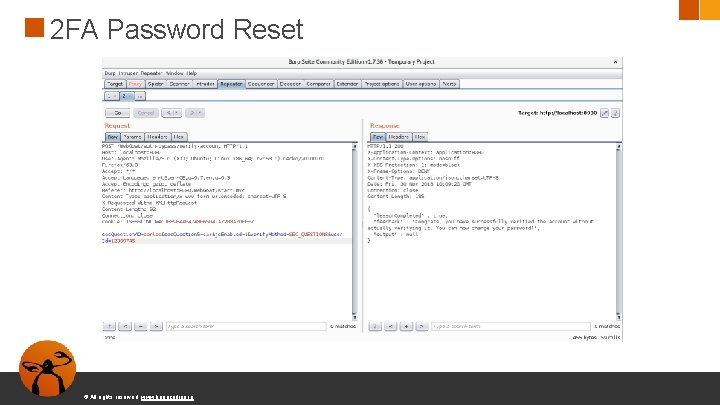
2 FA Password Reset © All rights reserved. www. keepcoding. io

2 FA Password Reset © All rights reserved. www. keepcoding. io

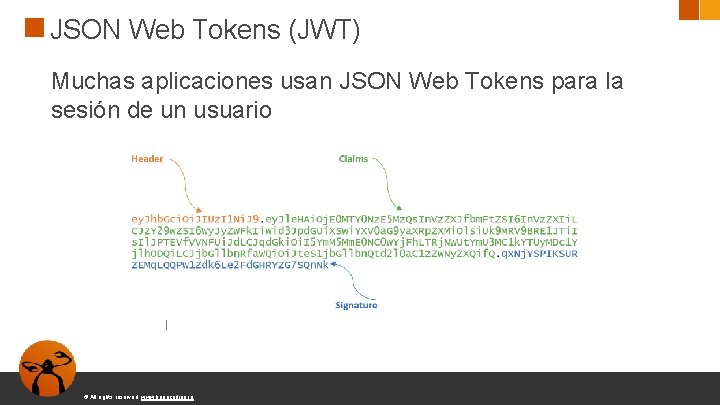
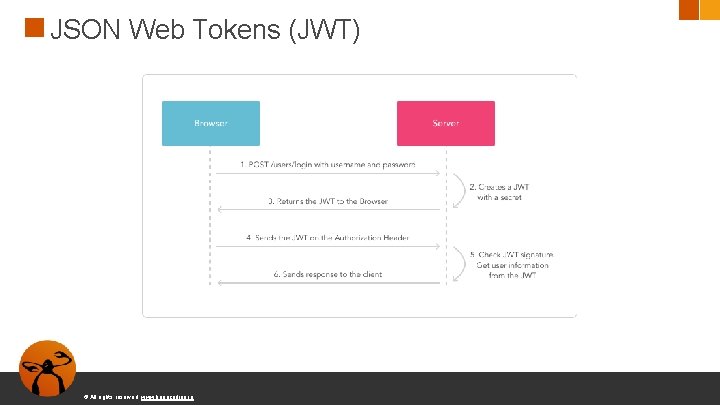
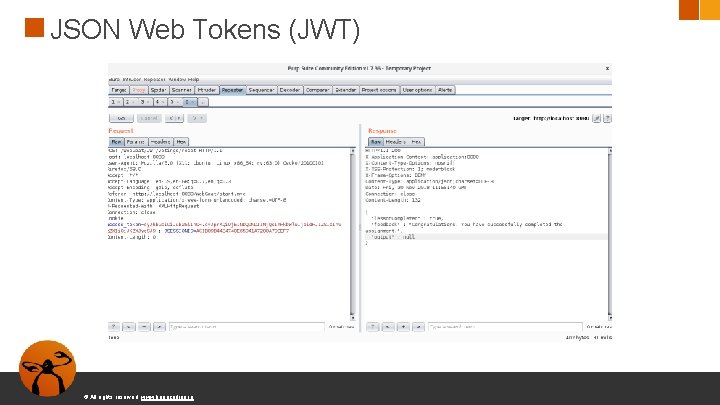
JSON Web Tokens (JWT) Muchas aplicaciones usan JSON Web Tokens para la sesión de un usuario © All rights reserved. www. keepcoding. io

JSON Web Tokens (JWT) © All rights reserved. www. keepcoding. io

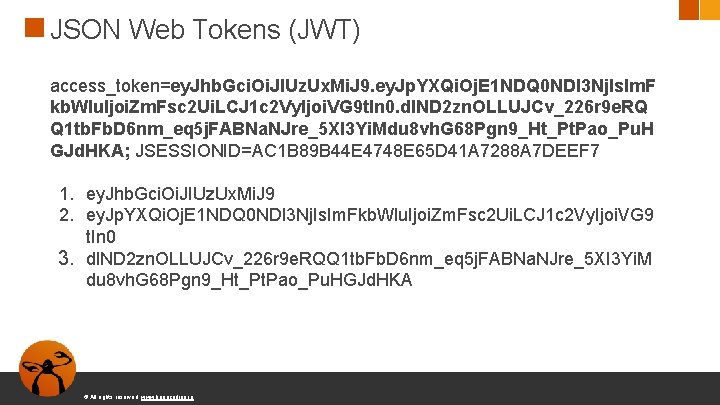
JSON Web Tokens (JWT) access_token=ey. Jhb. Gci. Oi. JIUz. Ux. Mi. J 9. ey. Jp. YXQi. Oj. E 1 NDQ 0 NDI 3 Nj. Is. Im. F kb. Wlu. Ijoi. Zm. Fsc 2 Ui. LCJ 1 c 2 Vy. Ijoi. VG 9 t. In 0. dl. ND 2 zn. OLLUJCv_226 r 9 e. RQ Q 1 tb. Fb. D 6 nm_eq 5 j. FABNa. NJre_5 XI 3 Yi. Mdu 8 vh. G 68 Pgn 9_Ht_Pt. Pao_Pu. H GJd. HKA; JSESSIONID=AC 1 B 89 B 44 E 4748 E 65 D 41 A 7288 A 7 DEEF 7 1. ey. Jhb. Gci. Oi. JIUz. Ux. Mi. J 9 2. ey. Jp. YXQi. Oj. E 1 NDQ 0 NDI 3 Nj. Is. Im. Fkb. Wlu. Ijoi. Zm. Fsc 2 Ui. LCJ 1 c 2 Vy. Ijoi. VG 9 t. In 0 3. dl. ND 2 zn. OLLUJCv_226 r 9 e. RQQ 1 tb. Fb. D 6 nm_eq 5 j. FABNa. NJre_5 XI 3 Yi. M du 8 vh. G 68 Pgn 9_Ht_Pt. Pao_Pu. HGJd. HKA © All rights reserved. www. keepcoding. io

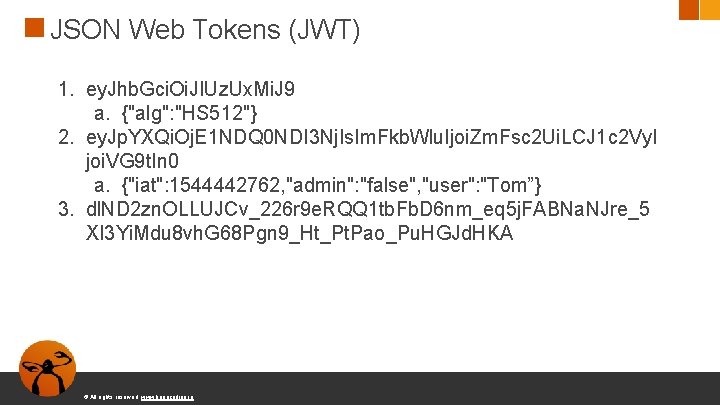
JSON Web Tokens (JWT) 1. ey. Jhb. Gci. Oi. JIUz. Ux. Mi. J 9 a. {"alg": "HS 512"} 2. ey. Jp. YXQi. Oj. E 1 NDQ 0 NDI 3 Nj. Is. Im. Fkb. Wlu. Ijoi. Zm. Fsc 2 Ui. LCJ 1 c 2 Vy. I joi. VG 9 t. In 0 a. {"iat": 1544442762, "admin": "false", "user": "Tom”} 3. dl. ND 2 zn. OLLUJCv_226 r 9 e. RQQ 1 tb. Fb. D 6 nm_eq 5 j. FABNa. NJre_5 XI 3 Yi. Mdu 8 vh. G 68 Pgn 9_Ht_Pt. Pao_Pu. HGJd. HKA © All rights reserved. www. keepcoding. io

JSON Web Tokens (JWT) © All rights reserved. www. keepcoding. io

JSON Web Tokens (JWT) © All rights reserved. www. keepcoding. io

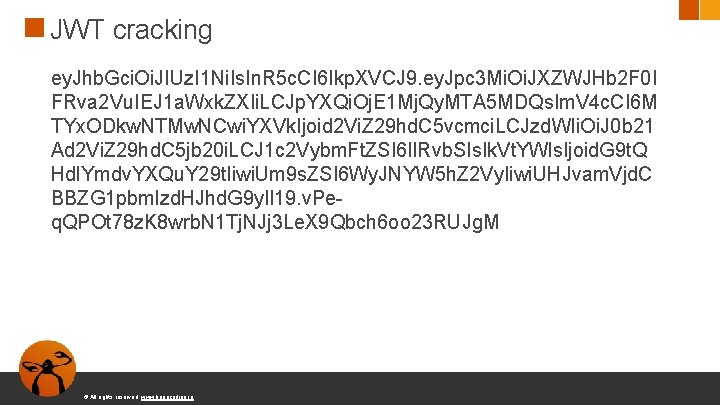
JWT cracking ey. Jhb. Gci. Oi. JIUz. I 1 Ni. Is. In. R 5 c. CI 6 Ikp. XVCJ 9. ey. Jpc 3 Mi. Oi. JXZWJHb 2 F 0 I FRva 2 Vu. IEJ 1 a. Wxk. ZXIi. LCJp. YXQi. Oj. E 1 Mj. Qy. MTA 5 MDQs. Im. V 4 c. CI 6 M TYx. ODkw. NTMw. NCwi. YXVk. Ijoid 2 Vi. Z 29 hd. C 5 vcmci. LCJzd. WIi. Oi. J 0 b 21 Ad 2 Vi. Z 29 hd. C 5 jb 20 i. LCJ 1 c 2 Vybm. Ft. ZSI 6 Il. Rvb. SIs. Ik. Vt. YWls. Ijoid. G 9 t. Q Hdl. Ymdv. YXQu. Y 29 t. Iiwi. Um 9 s. ZSI 6 Wy. JNYW 5 h. Z 2 Vy. Iiwi. UHJvam. Vjd. C BBZG 1 pbmlzd. HJhd. G 9 y. Il 19. v. Peq. QPOt 78 z. K 8 wrb. N 1 Tj. NJj 3 Le. X 9 Qbch 6 oo 23 RUJg. M © All rights reserved. www. keepcoding. io

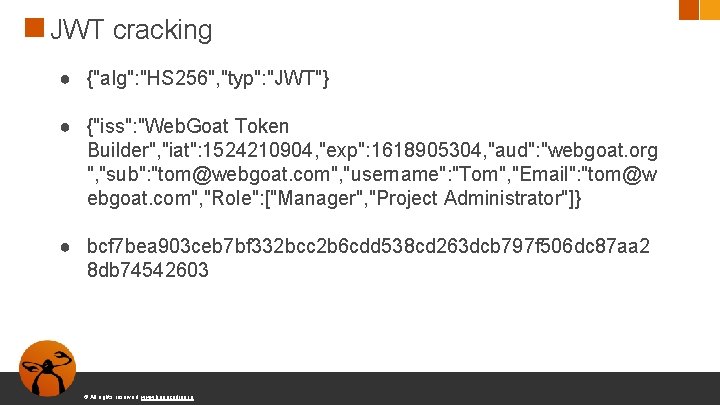
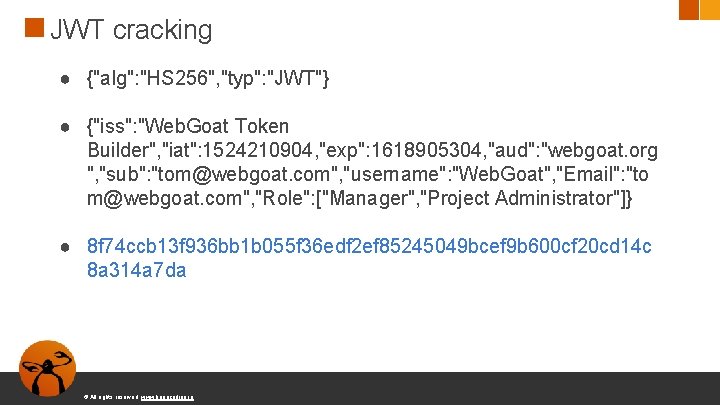
JWT cracking ● {"alg": "HS 256", "typ": "JWT"} ● {"iss": "Web. Goat Token Builder", "iat": 1524210904, "exp": 1618905304, "aud": "webgoat. org ", "sub": "tom@webgoat. com", "username": "Tom", "Email": "tom@w ebgoat. com", "Role": ["Manager", "Project Administrator"]} ● bcf 7 bea 903 ceb 7 bf 332 bcc 2 b 6 cdd 538 cd 263 dcb 797 f 506 dc 87 aa 2 8 db 74542603 © All rights reserved. www. keepcoding. io

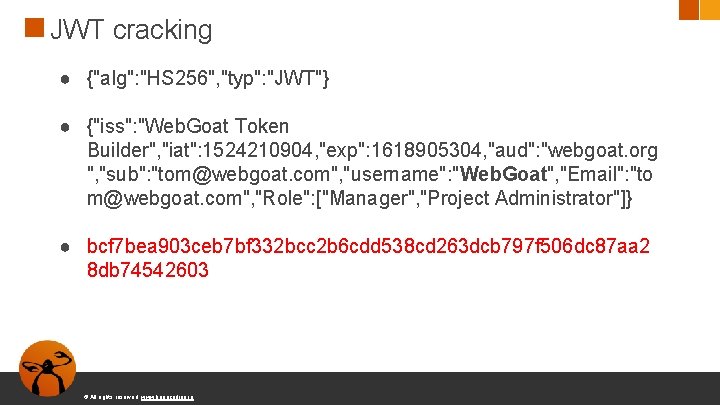
JWT cracking ● {"alg": "HS 256", "typ": "JWT"} ● {"iss": "Web. Goat Token Builder", "iat": 1524210904, "exp": 1618905304, "aud": "webgoat. org ", "sub": "tom@webgoat. com", "username": "Web. Goat", "Email": "to m@webgoat. com", "Role": ["Manager", "Project Administrator"]} ● bcf 7 bea 903 ceb 7 bf 332 bcc 2 b 6 cdd 538 cd 263 dcb 797 f 506 dc 87 aa 2 8 db 74542603 © All rights reserved. www. keepcoding. io

JWT cracking ● {"alg": "HS 256", "typ": "JWT"} ● {"iss": "Web. Goat Token Builder", "iat": 1524210904, "exp": 1618905304, "aud": "webgoat. org ", "sub": "tom@webgoat. com", "username": "Web. Goat", "Email": "to m@webgoat. com", "Role": ["Manager", "Project Administrator"]} ● 8 f 74 ccb 13 f 936 bb 1 b 055 f 36 edf 2 ef 85245049 bcef 9 b 600 cf 20 cd 14 c 8 a 314 a 7 da © All rights reserved. www. keepcoding. io

¿Usar JWT? ● Su uso es muy cuestionado a la hora de establecer sesiones de usuario ● Sin embargo, bien implementado, es un buen protocolo para comunicación entre servidores © All rights reserved. www. keepcoding. io

A 3 -Sensitive Data Exposure Muchas aplicaciones y APIs no tratan correctamente datos sensibles, como datos financieros o contraseñas. Comunicación de datos sensibles sin cifrado ● ¿Hay datos transmitidos en claro? HTTP, SMTP, FTP ● Uso de algoritmos criptográficos antiguos como MD 5 ● No se fuerza el uso de comunicación cifrada © All rights reserved. www. keepcoding. io

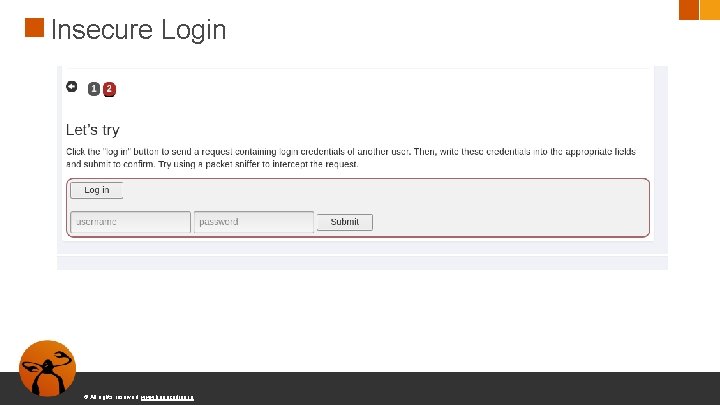
Insecure Login © All rights reserved. www. keepcoding. io

A 4 -XML External Entities (XXE) ● Muchos parseadores de XML antiguos o mal configurados permiten utilizar entidad externas en documentos XML ● Esto puede ser utilizado para mostrar archivos internos, escanear puertos, ejecutar código remotamente y denegación de servicio © All rights reserved. www. keepcoding. io

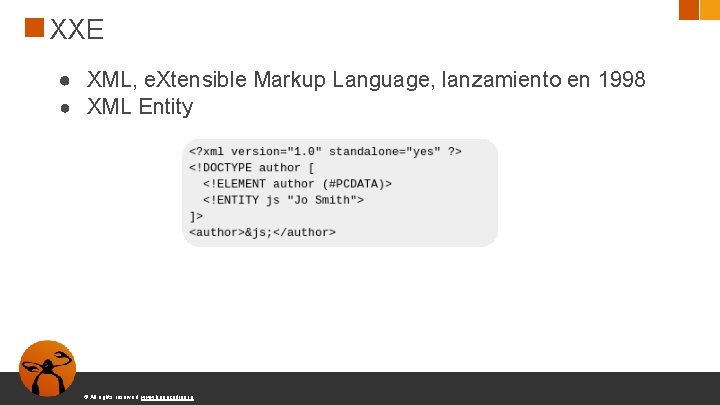
XXE ● XML, e. Xtensible Markup Language, lanzamiento en 1998 ● XML Entity © All rights reserved. www. keepcoding. io

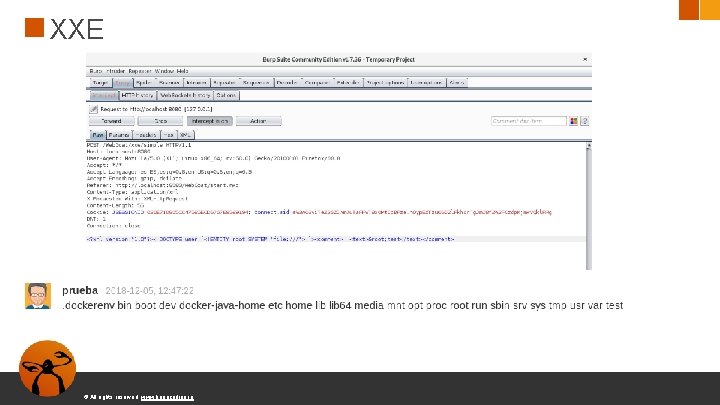
XXE © All rights reserved. www. keepcoding. io

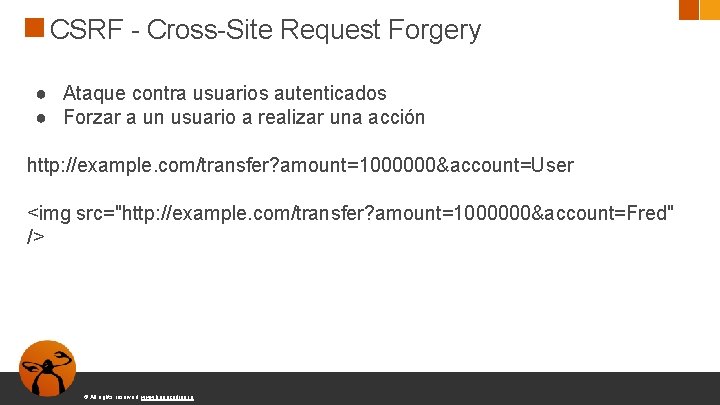
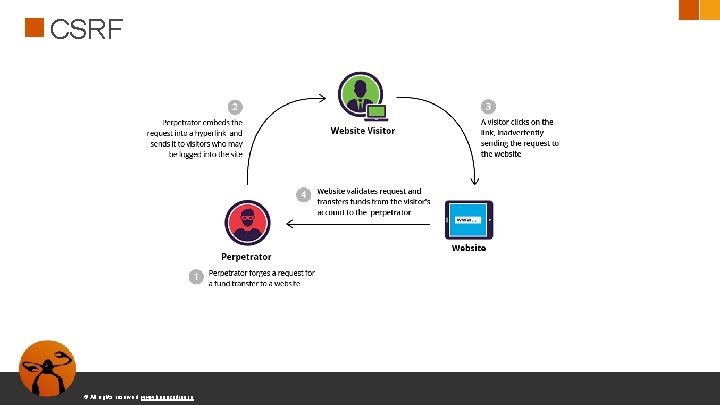
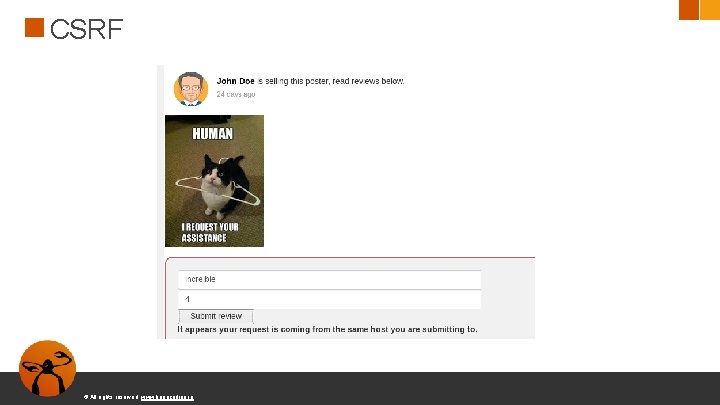
CSRF - Cross-Site Request Forgery ● Ataque contra usuarios autenticados ● Forzar a un usuario a realizar una acción http: //example. com/transfer? amount=1000000&account=User <img src="http: //example. com/transfer? amount=1000000&account=Fred" /> © All rights reserved. www. keepcoding. io

CSRF © All rights reserved. www. keepcoding. io

CSRF © All rights reserved. www. keepcoding. io

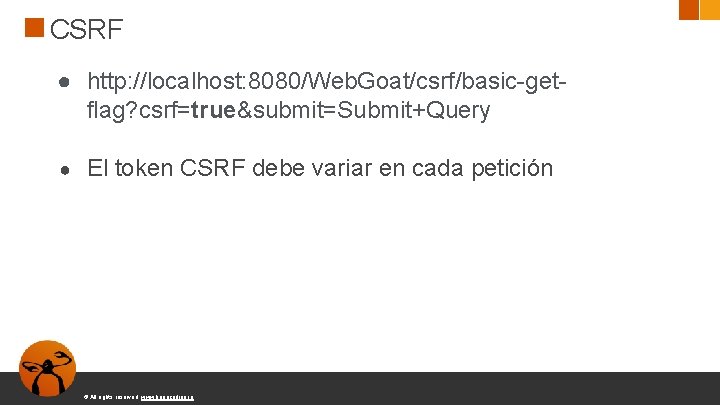
CSRF ● http: //localhost: 8080/Web. Goat/csrf/basic-getflag? csrf=true&submit=Submit+Query ● El token CSRF debe variar en cada petición © All rights reserved. www. keepcoding. io

CSRF © All rights reserved. www. keepcoding. io

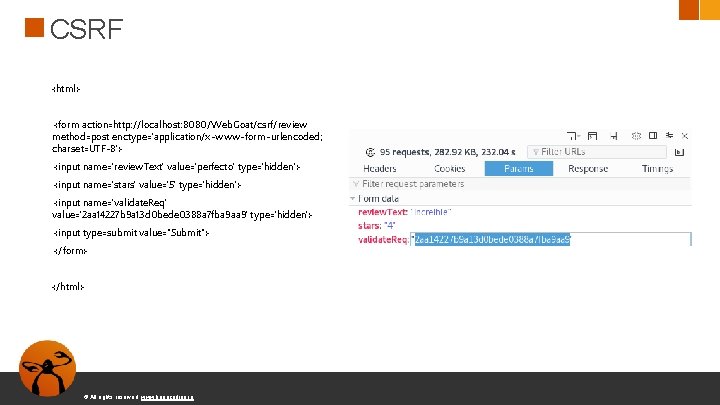
CSRF <html> <form action=http: //localhost: 8080/Web. Goat/csrf/review method=post enctype='application/x-www-form-urlencoded; charset=UTF-8'> <input name='review. Text' value='perfecto' type='hidden'> <input name='stars' value='5' type='hidden'> <input name='validate. Req' value='2 aa 14227 b 9 a 13 d 0 bede 0388 a 7 fba 9 aa 9' type='hidden'> <input type=submit value="Submit"> </form> </html> © All rights reserved. www. keepcoding. io

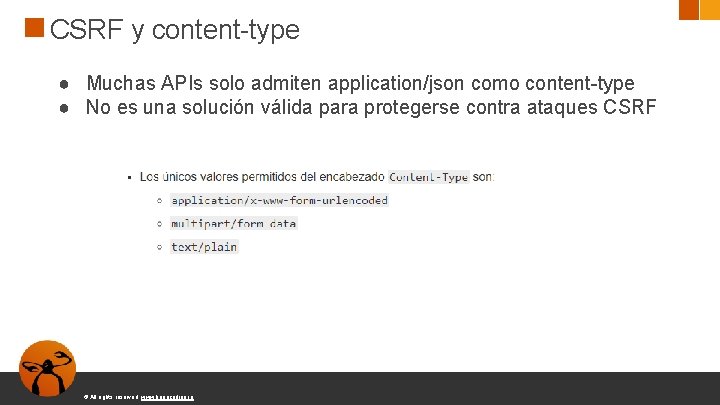
CSRF y content-type ● Muchas APIs solo admiten application/json como content-type ● No es una solución válida para protegerse contra ataques CSRF © All rights reserved. www. keepcoding. io

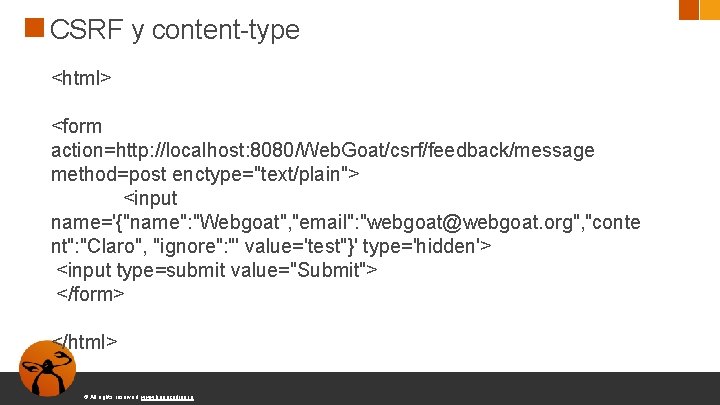
CSRF y content-type <html> <form action=http: //localhost: 8080/Web. Goat/csrf/feedback/message method=post enctype="text/plain"> <input name='{"name": "Webgoat", "email": "webgoat@webgoat. org", "conte nt": "Claro", "ignore": "' value='test"}' type='hidden'> <input type=submit value="Submit"> </form> </html> © All rights reserved. www. keepcoding. io

A 5: 2017 -Broken Access Control ● Las restricciones acerca de lo que puede hacer y no hacer un usuario autenticado muchas veces no se encuentran bien configuradas ● Un atacante puede acceder a sitios o funciones a las que no está autorizado: acceder cuentas de otros usuarios, ver archivos privados, modificar datos, cambiar permisos, etc © All rights reserved. www. keepcoding. io

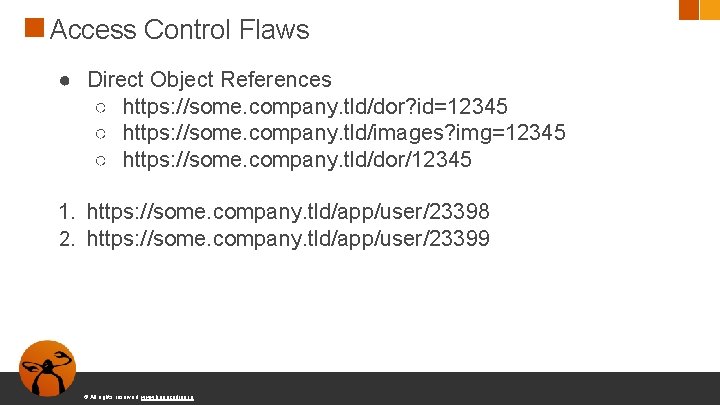
Access Control Flaws ● Direct Object References ○ https: //some. company. tld/dor? id=12345 ○ https: //some. company. tld/images? img=12345 ○ https: //some. company. tld/dor/12345 1. https: //some. company. tld/app/user/23398 2. https: //some. company. tld/app/user/23399 © All rights reserved. www. keepcoding. io

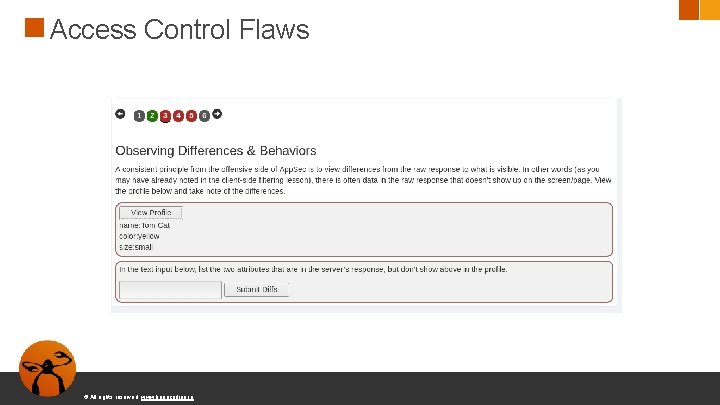
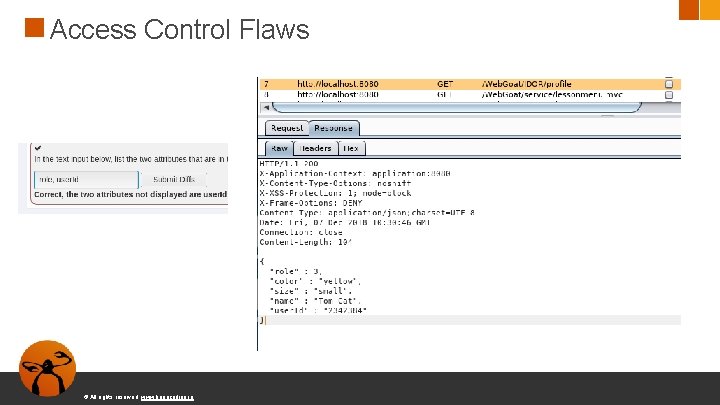
Access Control Flaws © All rights reserved. www. keepcoding. io

Access Control Flaws © All rights reserved. www. keepcoding. io

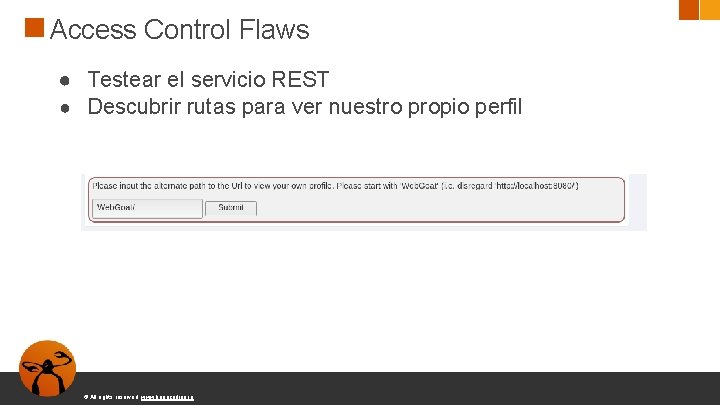
Access Control Flaws ● Testear el servicio REST ● Descubrir rutas para ver nuestro propio perfil © All rights reserved. www. keepcoding. io

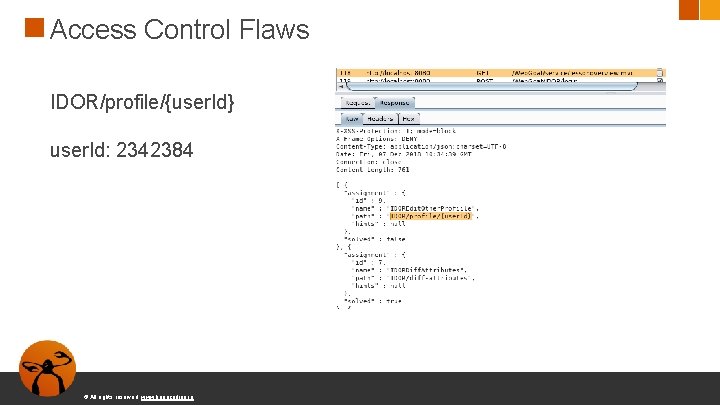
Access Control Flaws IDOR/profile/{user. Id} user. Id: 2342384 © All rights reserved. www. keepcoding. io

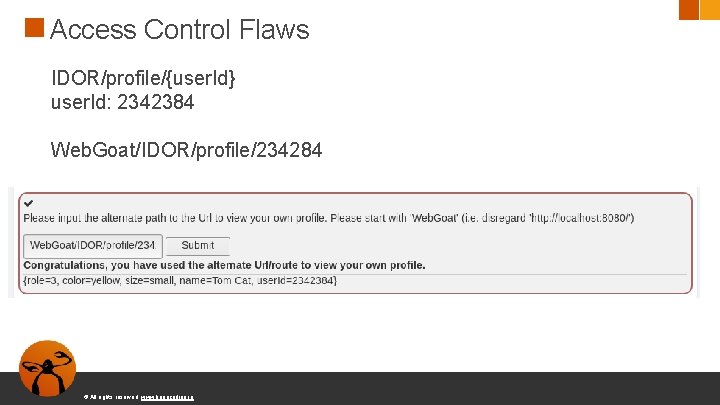
Access Control Flaws IDOR/profile/{user. Id} user. Id: 2342384 Web. Goat/IDOR/profile/234284 © All rights reserved. www. keepcoding. io

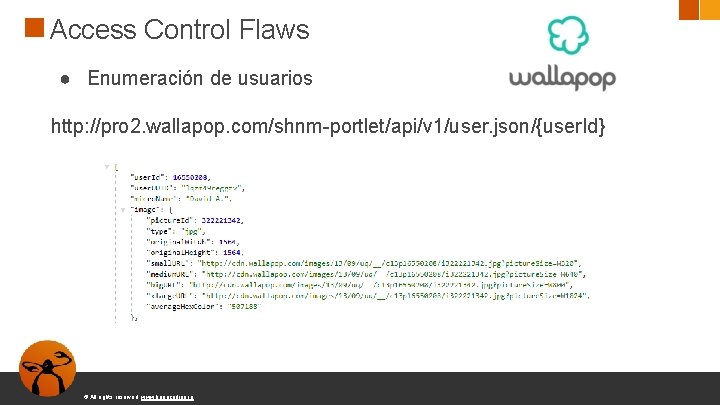
Access Control Flaws ● Enumeración de usuarios © All rights reserved. www. keepcoding. io

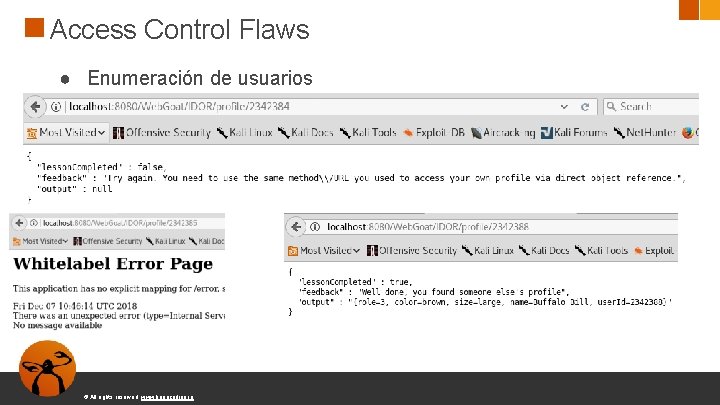
Access Control Flaws ● Enumeración de usuarios © All rights reserved. www. keepcoding. io

Access Control Flaws ● Enumeración de usuarios http: //pro 2. wallapop. com/shnm-portlet/api/v 1/user. json/{user. Id} © All rights reserved. www. keepcoding. io

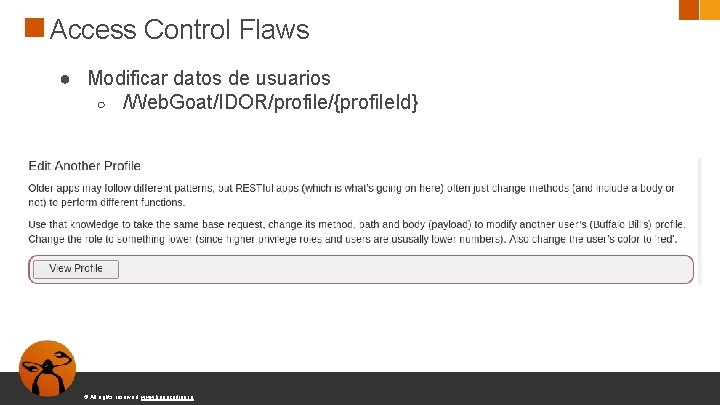
Access Control Flaws ● Modificar datos de usuarios ○ /Web. Goat/IDOR/profile/{profile. Id} © All rights reserved. www. keepcoding. io

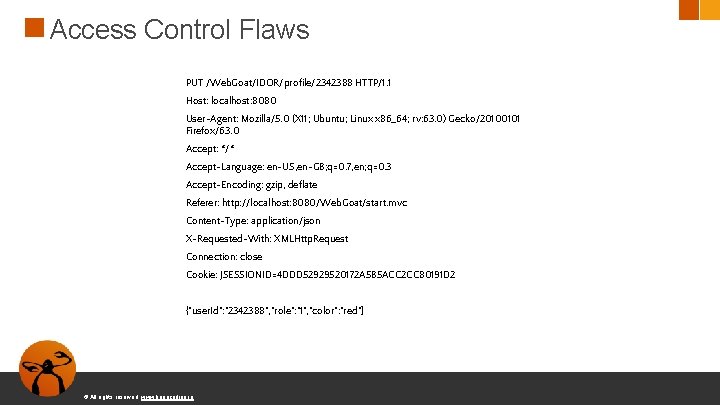
Access Control Flaws PUT /Web. Goat/IDOR/profile/2342388 HTTP/1. 1 Host: localhost: 8080 User-Agent: Mozilla/5. 0 (X 11; Ubuntu; Linux x 86_64; rv: 63. 0) Gecko/20100101 Firefox/63. 0 Accept: */* Accept-Language: en-US, en-GB; q=0. 7, en; q=0. 3 Accept-Encoding: gzip, deflate Referer: http: //localhost: 8080/Web. Goat/start. mvc Content-Type: application/json X-Requested-With: XMLHttp. Request Connection: close Cookie: JSESSIONID=4 DDD 52929520172 A 5 B 5 ACC 2 CC 80191 D 2 {"user. Id": "2342388", "role": "1", "color": "red"} © All rights reserved. www. keepcoding. io

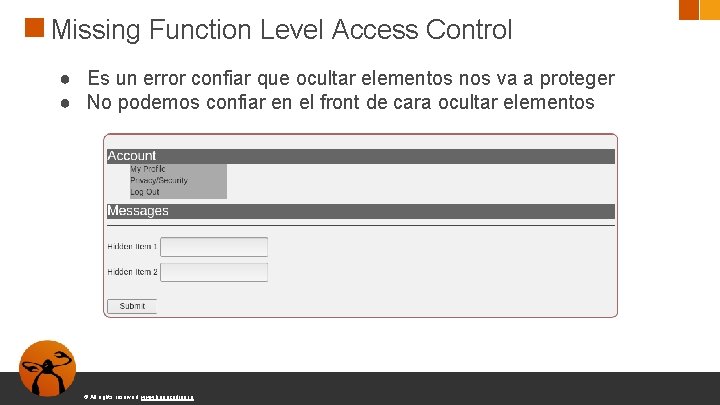
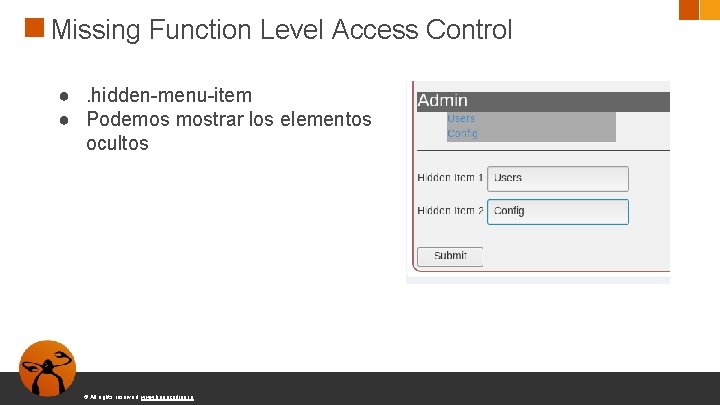
Missing Function Level Access Control ● Es un error confiar que ocultar elementos nos va a proteger ● No podemos confiar en el front de cara ocultar elementos © All rights reserved. www. keepcoding. io

Missing Function Level Access Control ●. hidden-menu-item ● Podemos mostrar los elementos ocultos © All rights reserved. www. keepcoding. io

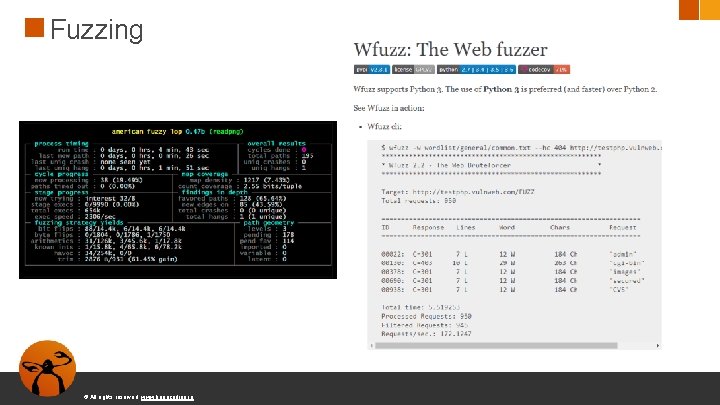
Fuzzing ● Fuzzing es una técnica de pruebas de software, a menudo automatizado o semiautomatizado, que implica proporcionar datos inválidos, inesperados o aleatorios a las entradas de un programa © All rights reserved. www. keepcoding. io

Fuzzing © All rights reserved. www. keepcoding. io

Missing Function Level Access Control ● Testear control de usuarios ● http: //localhost: 8080/Web. Goat/users © All rights reserved. www. keepcoding. io

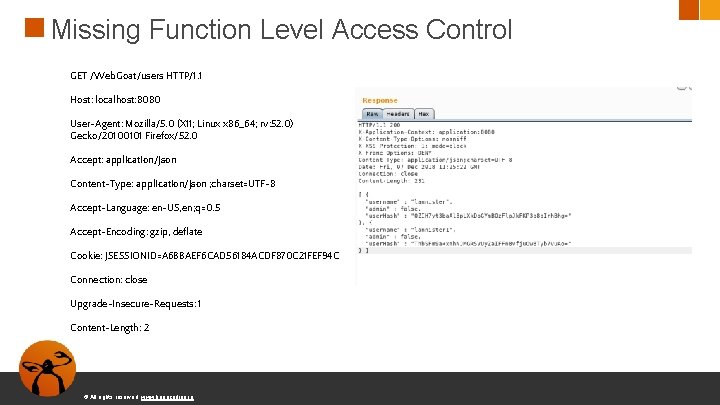
Missing Function Level Access Control GET /Web. Goat/users HTTP/1. 1 Host: localhost: 8080 User-Agent: Mozilla/5. 0 (X 11; Linux x 86_64; rv: 52. 0) Gecko/20100101 Firefox/52. 0 Accept: application/json Content-Type: application/json ; charset=UTF-8 Accept-Language: en-US, en; q=0. 5 Accept-Encoding: gzip, deflate Cookie: JSESSIONID=A 6 BBAEF 6 CAD 56184 ACDF 870 C 21 FEF 94 C Connection: close Upgrade-Insecure-Requests: 1 Content-Length: 2 © All rights reserved. www. keepcoding. io

A 6 -Security Misconfiguration Configuración errónea es la causa más común. Configuraciones inseguras por defecto, incompletas, almacenamientos en la nube abiertos, configuración errónea de cabeceras HTTP y mensajes de error con información sensible. Aparte de configurar adecuadamente cada pieza de software es necesario mantenerlo actualizado. © All rights reserved. www. keepcoding. io

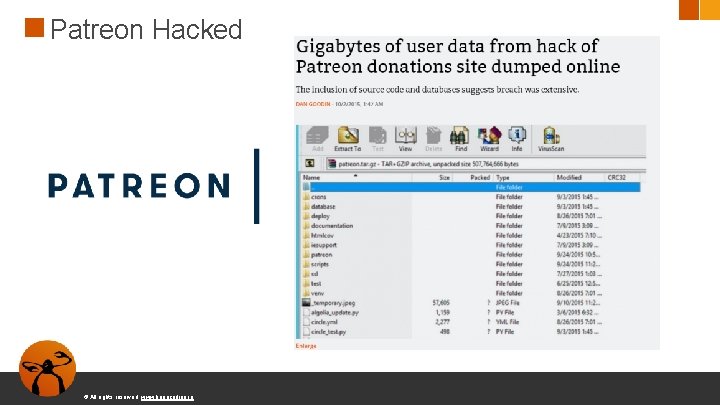
Patreon Hacked © All rights reserved. www. keepcoding. io

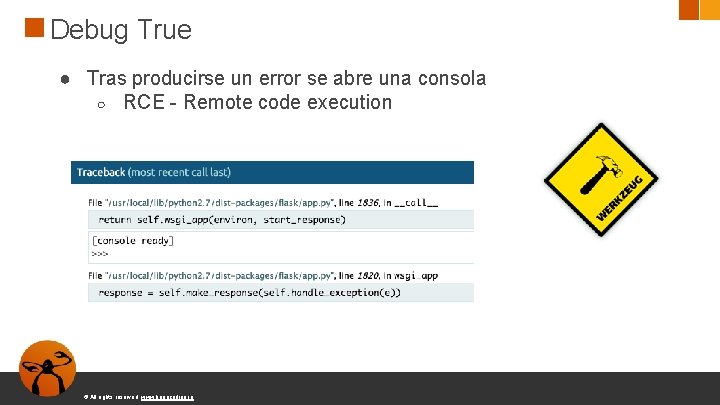
Debug True ● Tras producirse un error se abre una consola ○ RCE - Remote code execution © All rights reserved. www. keepcoding. io

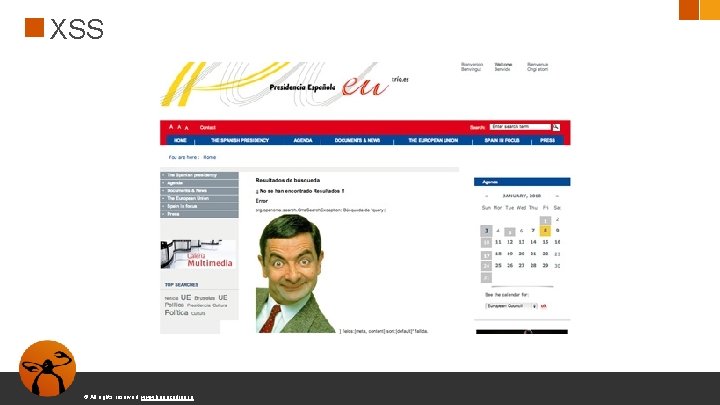
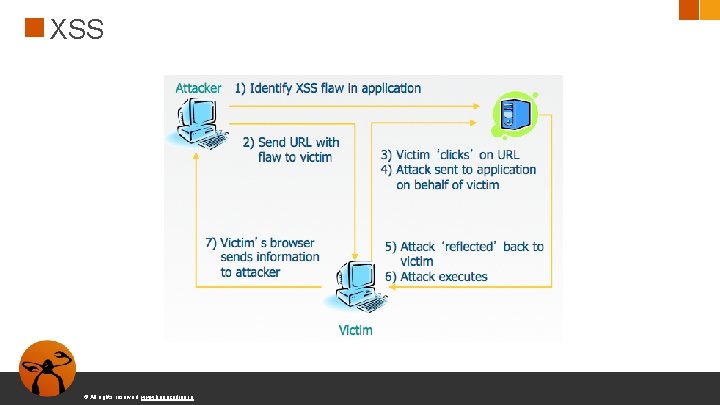
A 7: 2017 -Cross-Site Scripting (XSS) ● XSS ocurre cuando una aplicación incluye datos en una web sin validación o escape ● XSS permite a los atacantes inyectar HTML o Java. Script en una página web ● Robar sesiones ● Deface de webs ● Redirigir a una web maliciosa © All rights reserved. www. keepcoding. io

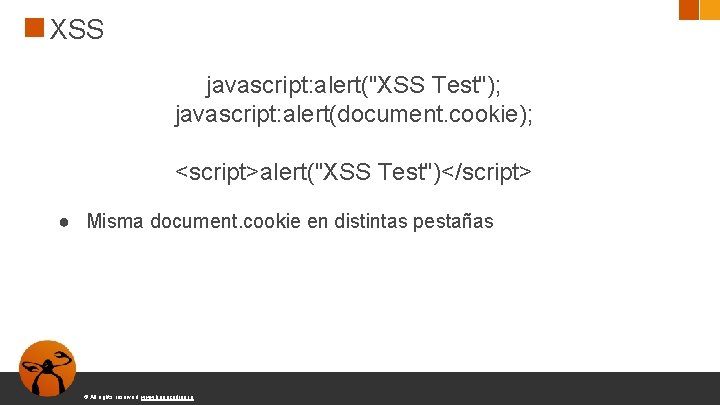
XSS javascript: alert("XSS Test"); javascript: alert(document. cookie); <script>alert("XSS Test")</script> ● Misma document. cookie en distintas pestañas © All rights reserved. www. keepcoding. io

XSS © All rights reserved. www. keepcoding. io

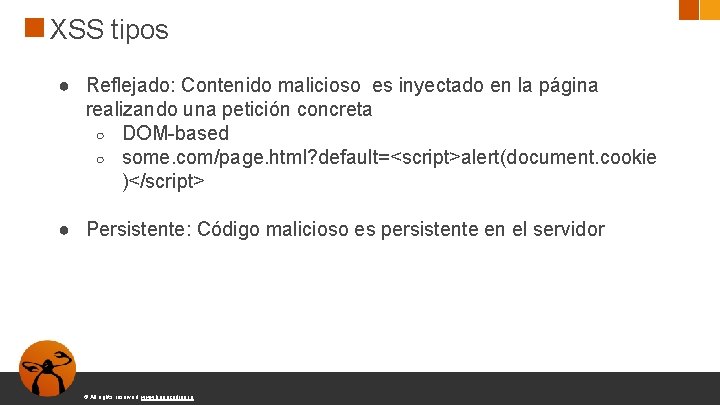
XSS tipos ● Reflejado: Contenido malicioso es inyectado en la página realizando una petición concreta ○ DOM-based ○ some. com/page. html? default=<script>alert(document. cookie )</script> ● Persistente: Código malicioso es persistente en el servidor © All rights reserved. www. keepcoding. io

XSS © All rights reserved. www. keepcoding. io

XSS © All rights reserved. www. keepcoding. io

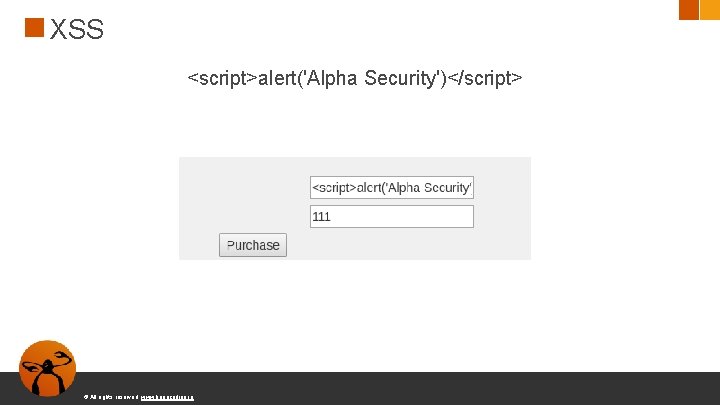
XSS <script>alert('Alpha Security')</script> © All rights reserved. www. keepcoding. io

XSS © All rights reserved. www. keepcoding. io

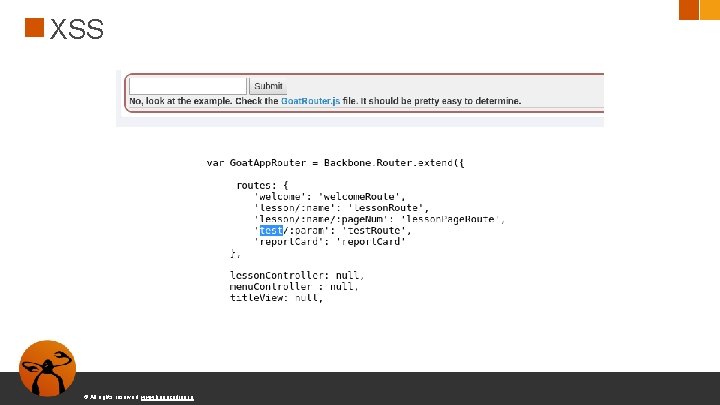
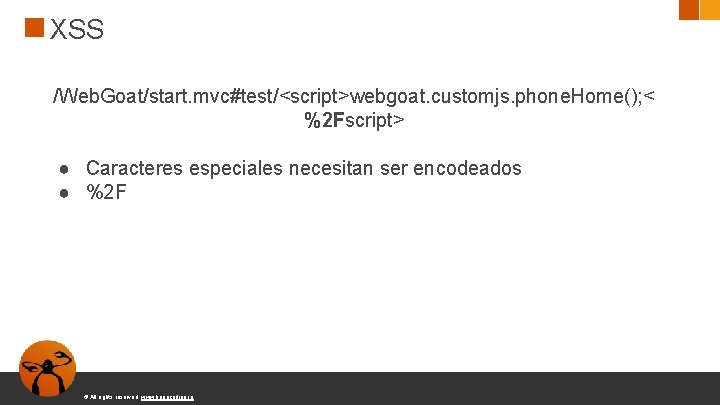
XSS /Web. Goat/start. mvc#test/<script>webgoat. customjs. phone. Home(); < %2 Fscript> ● Caracteres especiales necesitan ser encodeados ● %2 F © All rights reserved. www. keepcoding. io

XSS Stored ● Buscamos crear un comentario que ejecute webgoat. customjs. phone. Home © All rights reserved. www. keepcoding. io

XSS Stored <embed src="javascript: webgoat. customjs. phone. Home(); "> ● Chrome incorpora protecciones frente a XSS © All rights reserved. www. keepcoding. io

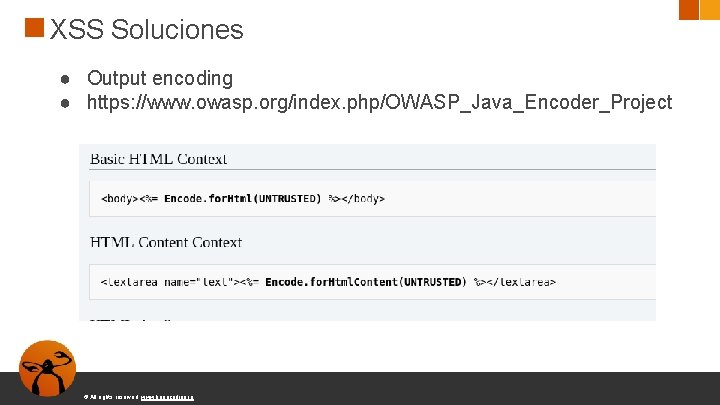
XSS Soluciones ● Output encoding ● https: //www. owasp. org/index. php/OWASP_Java_Encoder_Project © All rights reserved. www. keepcoding. io

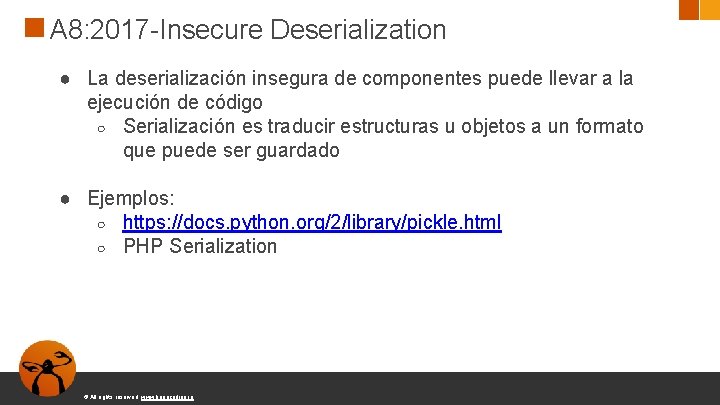
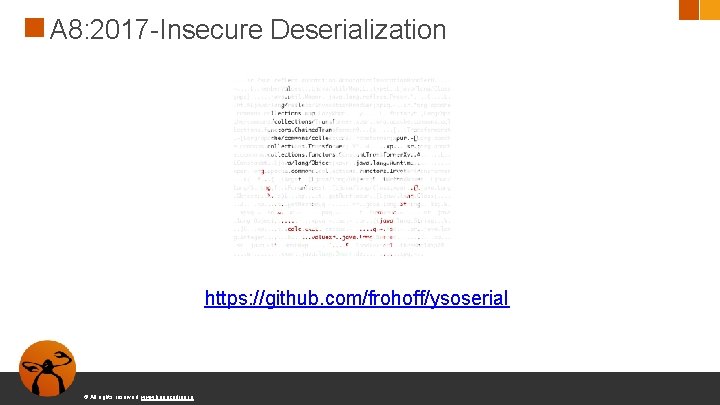
A 8: 2017 -Insecure Deserialization ● La deserialización insegura de componentes puede llevar a la ejecución de código ○ Serialización es traducir estructuras u objetos a un formato que puede ser guardado ● Ejemplos: ○ https: //docs. python. org/2/library/pickle. html ○ PHP Serialization © All rights reserved. www. keepcoding. io

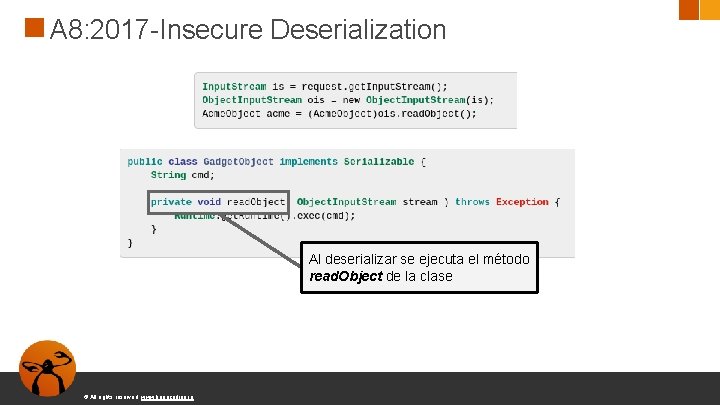
A 8: 2017 -Insecure Deserialization Al deserializar se ejecuta el método read. Object de la clase © All rights reserved. www. keepcoding. io

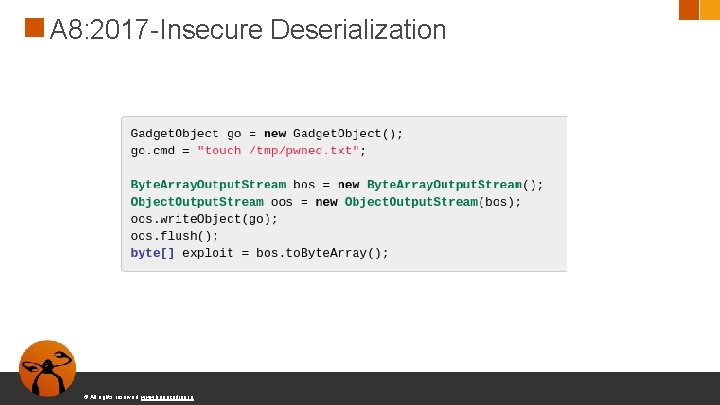
A 8: 2017 -Insecure Deserialization © All rights reserved. www. keepcoding. io

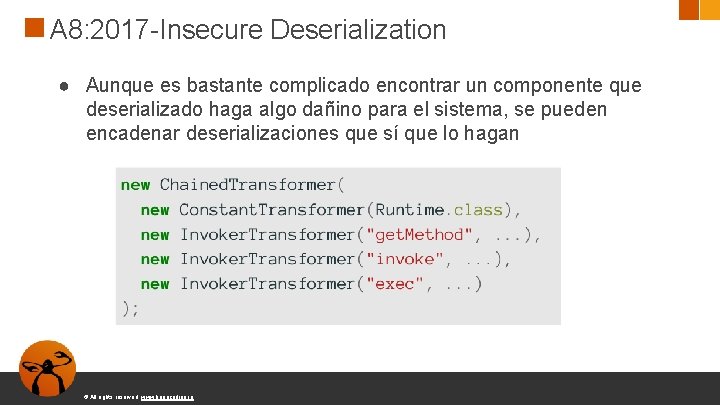
A 8: 2017 -Insecure Deserialization ● Aunque es bastante complicado encontrar un componente que deserializado haga algo dañino para el sistema, se pueden encadenar deserializaciones que sí que lo hagan © All rights reserved. www. keepcoding. io

A 8: 2017 -Insecure Deserialization https: //github. com/frohoff/ysoserial © All rights reserved. www. keepcoding. io

A 8: 2017 -Insecure Deserialization ● Usar serializador sólo si es imprescindible ● Sólo deserializar datos de fuentes confiables ○ La mayor parte de las veces, sólo nosotros somos una fuente confiable © All rights reserved. www. keepcoding. io

A 9: 2017 -Using Components with Known Vulnerabilities ● Utilizar componentes con vulnerabilidades conocidas ● Recomendable mirar siempre ○ https: //www. cvedetails. com/ ● Ejemplos: ○ Apache Struts 2 ■ https: //cve. mitre. org/cgi-bin/cvename. cgi? name=CVE 2017 -5638 ○ Wordpress 4. 9. 2 ■ https: //cve. mitre. org/cgi-bin/cvename. cgi? name=CVE 2018 -6389 © All rights reserved. www. keepcoding. io

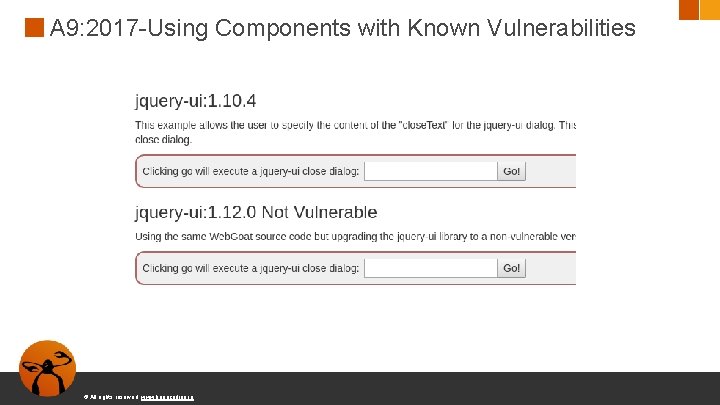
A 9: 2017 -Using Components with Known Vulnerabilities © All rights reserved. www. keepcoding. io

A 9: 2017 -Using Components with Known Vulnerabilities ● CVE-2013 -7285 ○ https: //github. com/Web. Goat/blob/4 d 7 d 0058 c 3 ba 0 b 4 e 542 ed 7 e 964 ee 1056207 b 7 a 08/webgoatlessons/vulnerablecomponents/src/main/java/org/owasp/webgoat/plugin/Vulner able. Components. Lesson. java © All rights reserved. www. keepcoding. io

A 10: 2017 -Insufficient Logging & Monitoring ● ● Es necesario mantener logs y que estén monitorizados Permiten una respuesta a incidentes (DFIR) Digital Forensics and Incident Response Detectar ataques de forma temprana © All rights reserved. www. keepcoding. io