Access control techniques Access control techniques Once an









- Slides: 11

Access control techniques

Access control techniques Once an organization decides upon the access control model it will implement(DAC, MAC, or RBAC), then it needs to look at the different possible access control techniques that are available to work within these models and supplement their mechanisms. The following sections explain some of the available access control techniques.

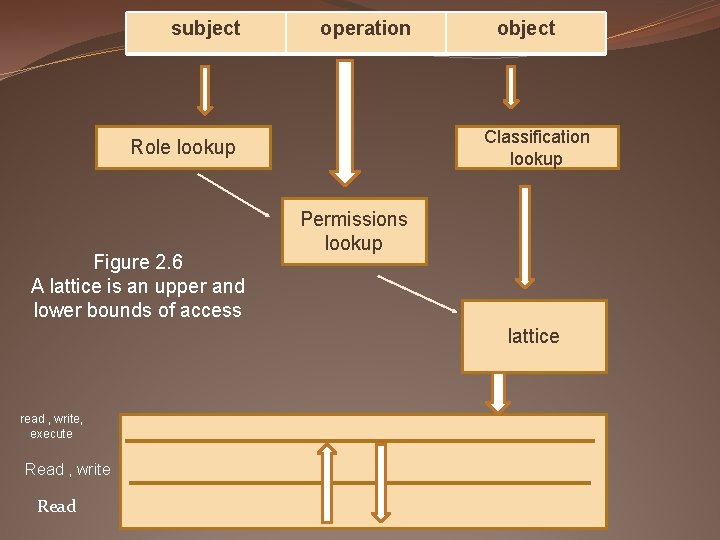
subject operation Classification lookup Role lookup Figure 2. 6 A lattice is an upper and lower bounds of access object Permissions lookup lattice read , write, execute Read , write Read

Restricted Interfaces Users’ environments can be constructed and controlled, which is another approach to controlling the objects they have access to. An administrator can create a user profile that will provide a user’s working environment. This profile allows the administrator to dictate what icons , menus, applications, commands , and functionality is available within that environment. It is considered a restricted interface because the user utilizes the provided environment, desktop , and profile to interface with the operating system, installed applications, and resources. Another example of a restricted interface is a database view. A database administrator can implement database views, which will show only the information within the database that the user has the necessary access rights to view. So the payroll department may be able to view employee salary and commission information, but not individual’s employment records and human resource information

Different department managers may be able to view their employees’ employment records, but not their salary and commission information. Database views are controls that allow the database administrator to logically partition the database and present these specific pieces to different authenticated users. The last restricted interface access control technique we look at is a physically constrained interface. The best example of this type of access control is an automated teller machine (ATM). These systems have operating systems that have many more capabilities than transferring, depositing, and withdrawing funds, but users of these machines are presented only with buttons for these specific functions and no more. Thus, the physically constrained interface provides limited options and only a few buttons so any other functions that the operating system can actually perform are not accessible by regular users.

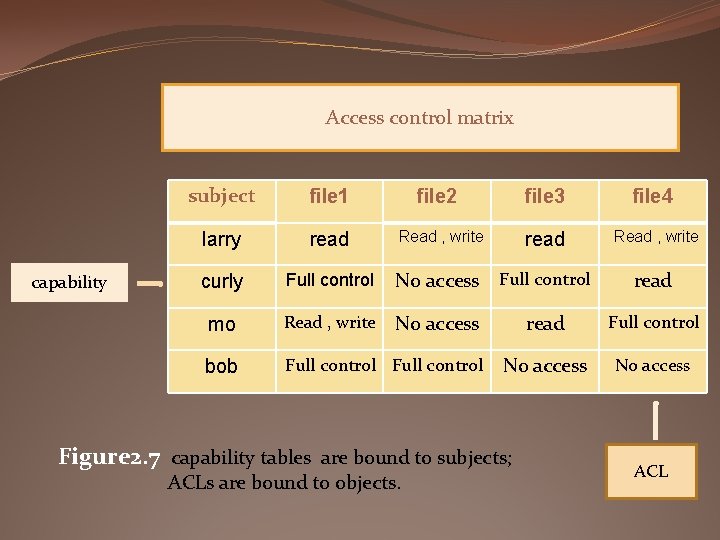
Capability Table and ACLs access control matrix is a mechanism used to associate access permissions of a subject to an object. The actual permissions assigned to a subject , which is a row within the access control matrix, is referred to as a capability table. And the different subjects that can access an object are referred to as an access control list (ACL), which are the columns of the matrix, as shown in Figure 2 -7. When a subject requests to access a specific object, the operating system will refer to this access control matrix to see if the access and An requested operation is allowed

Access control matrix capability subject file 1 file 2 file 3 file 4 larry read Read , write curly Full control No access Full control mo Read , write No access bob Full control read Full control No access Figure 2. 7 capability tables are bound to subjects; ACLs are bound to objects. read ACL

Content-Dependent Access Control Content-dependent control is another technique used, which is based on the object’s content that the subject is trying to access. It is usually implemented in databases. For example, a database may contain sensitive medical information; the more sensitive this data is, the fewer the number of people that will be able to access it. Let’s say the database holds the results of different tests that have been performed on a particular patient. If a lab technician requests to see these results, she may be shown only that the tests were completed successfully, on what date , and by whom. If a nurse requests to see this information, she may be given access to a little bit more of the information than the lab technician, but not sensitive information, as in the patient has positive signs of malaria. And when a physician requests to see the same set of information, she may have access to all test data and results.

Content-dependent access controls require a lot of resources and Overhead because the database will need to scan the object to determine if a particular subject can actually access it. The more granularity that is configured and expected from these types of controls will equate to more resources needed to evaluate requests.

Other Access Techniques The following access control types are more granular in nature and can be used in combination with any of the previously discussed controls and models. The operating system or application would need to provide these types of controls for them to be available to be configured by the administrator or security officer. 1 -Physical location : - A user may be allowed access to a resource only if she has interactively logged in to a computer, meaning that she is physically at a computer and not logged in remotely. 2 -Logical location : - An administrator can restrict access to resources by IP addresses, which is a logical location on a network. 3 -Time of day: - A control mechanism can be configured to only allow access to resources between certain hours of the day and certain days of the week.

4 -Transaction type: - Restrictions based on operations that are requested to be carried out. A bank teller may be able to deposit checks but not cash checks. This would be a type of transaction access restriction.