Access Control Access Control Example n Access Control










![Grant and Revoke GRANT <privilege> ON <relation> To <user> [WITH GRANT OPTION] ------------------------------------------------------------------ n Grant and Revoke GRANT <privilege> ON <relation> To <user> [WITH GRANT OPTION] ------------------------------------------------------------------ n](https://slidetodoc.com/presentation_image_h/c8b5e0c98052203e1ee4fa031926ca7d/image-25.jpg)
![Grant and Revoke REVOKE <privileges> [ON <relation>] FROM <user> ------------------------------------------------------------- n n n REVOKE Grant and Revoke REVOKE <privileges> [ON <relation>] FROM <user> ------------------------------------------------------------- n n n REVOKE](https://slidetodoc.com/presentation_image_h/c8b5e0c98052203e1ee4fa031926ca7d/image-26.jpg)
- Slides: 32

Access Control

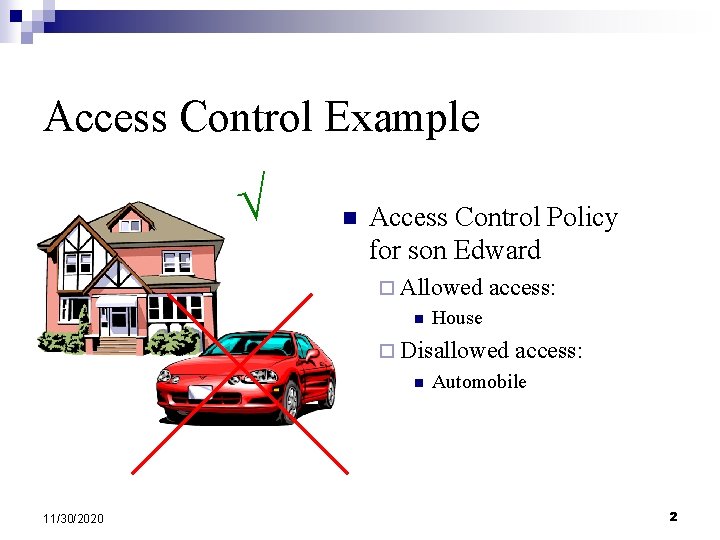
Access Control Example n Access Control Policy for son Edward ¨ Allowed n access: House ¨ Disallowed n 11/30/2020 access: Automobile 2

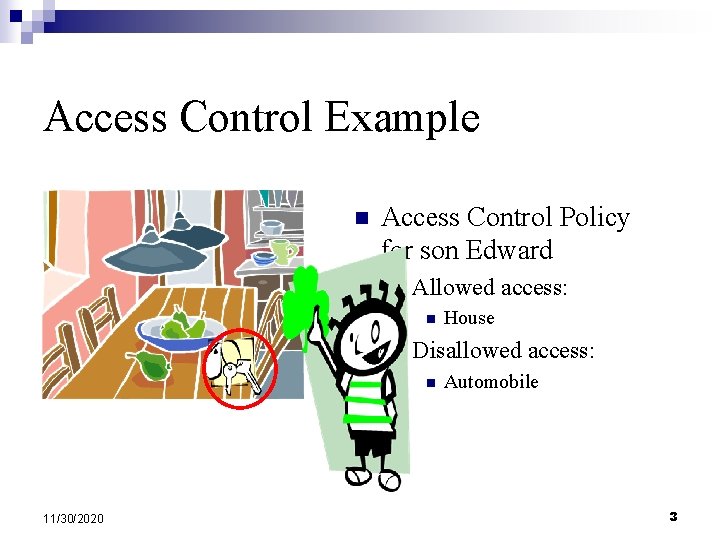
Access Control Example n Access Control Policy for son Edward ¨ Allowed n access: House ¨ Disallowed n 11/30/2020 access: Automobile 3

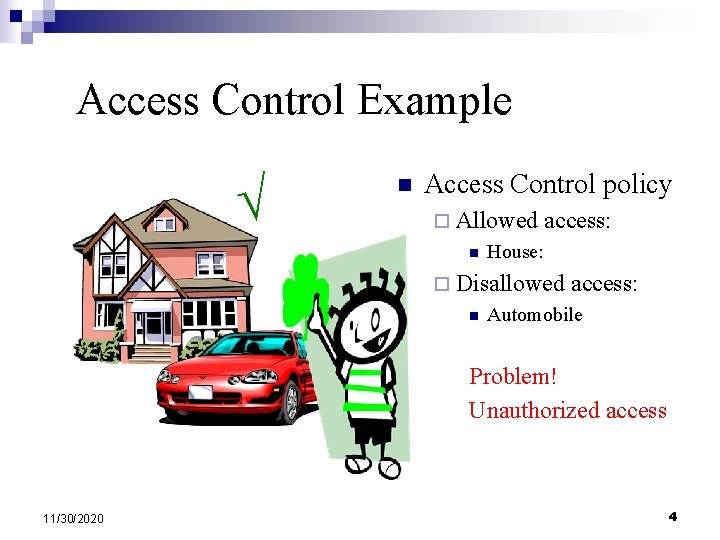
Access Control Example n Access Control policy ¨ Allowed n access: House: ¨ Disallowed n access: Automobile Problem! Unauthorized access 11/30/2020 4

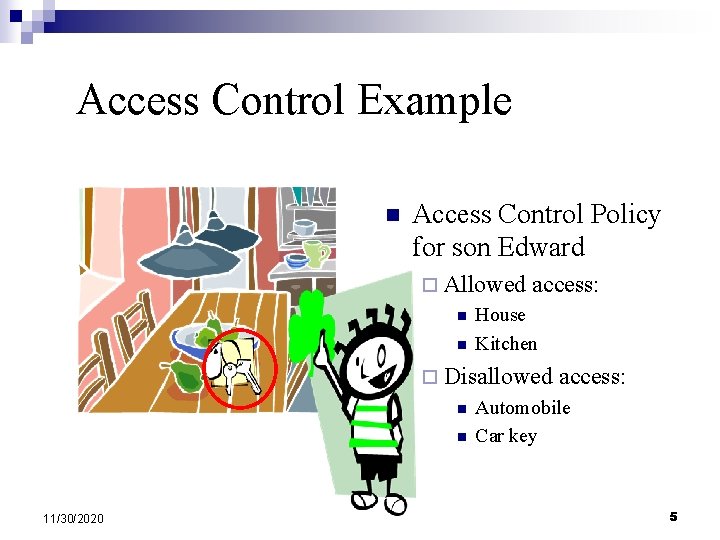
Access Control Example n Access Control Policy for son Edward ¨ Allowed n n access: House Kitchen ¨ Disallowed n n 11/30/2020 access: Automobile Car key 5

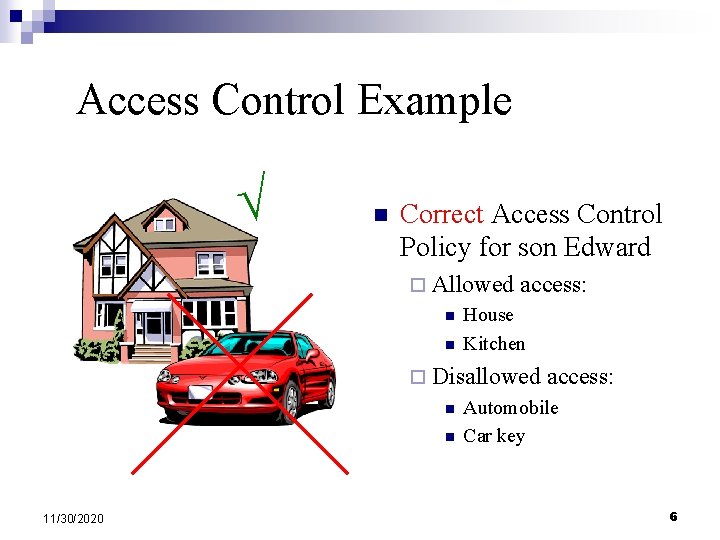
Access Control Example n Correct Access Control Policy for son Edward ¨ Allowed n n access: House Kitchen ¨ Disallowed n n 11/30/2020 access: Automobile Car key 6

Access Control n Protection objects: system resources for which protection is desirable ¨ Memory, file, directory, hardware resource, software resources, etc. n Subjects: active entities requesting accesses to resources ¨ User, n owner, program, etc. Access mode: type of access ¨ Read, 11/30/2020 write, execute 7

Access Control Requirement Cannot be bypassed n Enforce least-privilege and need-to-know restrictions n Enforce organizational policy n 11/30/2020 8

Access Control n n n Access control: ensures that all direct accesses to object are authorized Protects against accidental and malicious threats by regulating the reading, writing and execution of data and programs Need: ¨ Proper user identification and authentication ¨ Information specifying the access rights is protected form modification 11/30/2020 9

Access Control n Access control components: ¨ Access control policy: specifies the authorized accesses of a system ¨ Access control mechanism: implements and enforces the policy n Separation of components allows to: ¨ Define access requirements independently from implementation ¨ Compare different policies ¨ Implement mechanisms that can enforce a wide range of policies 11/30/2020 10

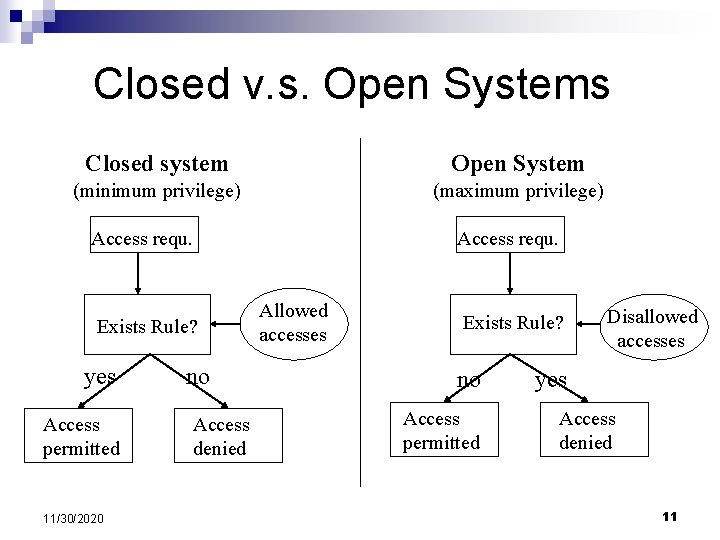
Closed v. s. Open Systems Closed system Open System (minimum privilege) (maximum privilege) Access requ. Exists Rule? yes Access permitted 11/30/2020 no Access denied Access requ. Allowed accesses Exists Rule? no Access permitted Disallowed accesses yes Access denied 11

Authorization Management n n n Who can grant and revoke access rights? Centralized administration: security officer Decentralized administration: locally autonomous systems Hierarchical decentralization: security officer > departmental system administrator > Windows NT administrator Ownership based: owner of data may grant access to other to his/her data (possibly with grant option) Cooperative authorization: predefined groups of users or predefined number of users may access data 11/30/2020 12

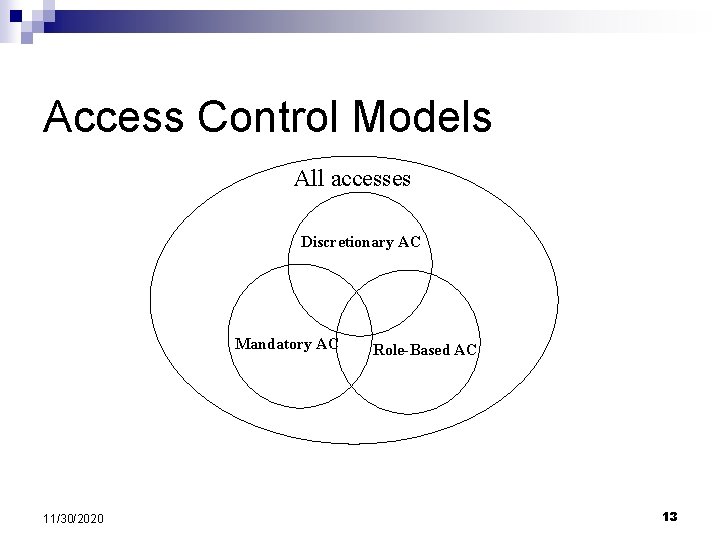
Access Control Models All accesses Discretionary AC Mandatory AC 11/30/2020 Role-Based AC 13

Discretionary Access Control n Access control is based on ¨ User’s identity and ¨ Access control rules n Most common administration: owner based ¨ Users can protect what they own ¨ Owner may grant access to others ¨ Owner may define the type of access given to others 11/30/2020 14

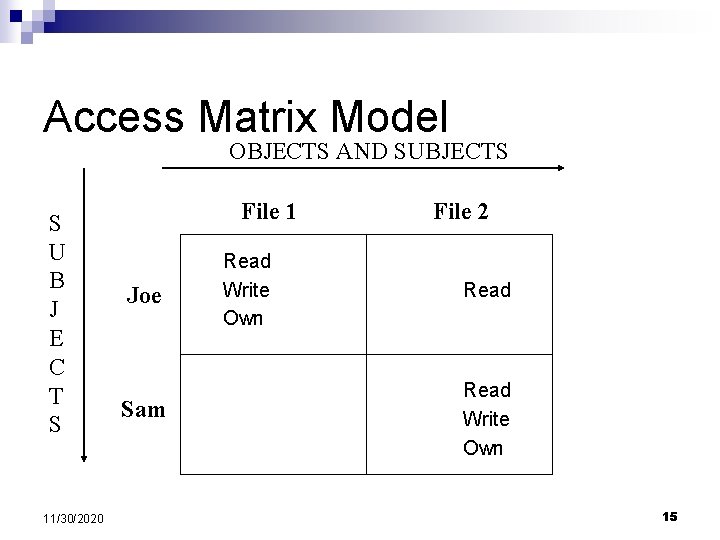
Access Matrix Model OBJECTS AND SUBJECTS S U B J E C T S 11/30/2020 File 1 Joe Sam Read Write Own File 2 Read Write Own 15

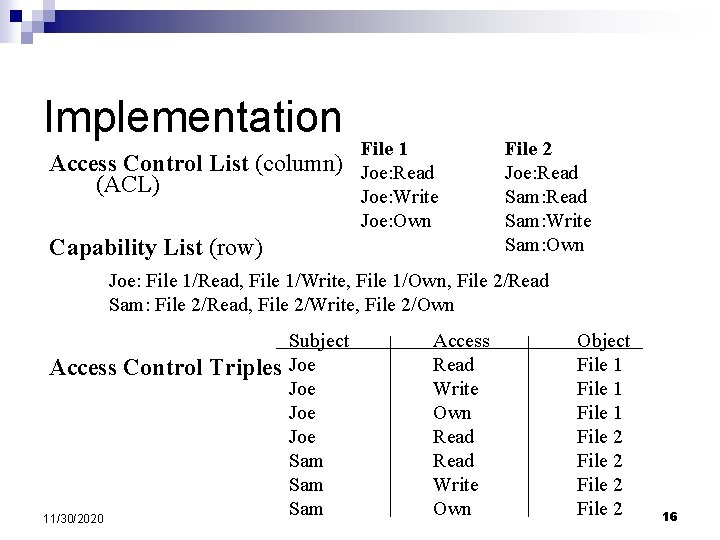
Implementation Access Control List (column) (ACL) File 1 Joe: Read Joe: Write Joe: Own Capability List (row) File 2 Joe: Read Sam: Write Sam: Own Joe: File 1/Read, File 1/Write, File 1/Own, File 2/Read Sam: File 2/Read, File 2/Write, File 2/Own Access Control Triples 11/30/2020 Subject Joe Joe Sam Sam Access Read Write Own Object File 1 File 2 16

ACL v. s. Capabilities n ACL: ¨ Per object based ¨ Good for file systems n Capabilities: ¨ Per subject based ¨ Good for environment with dynamic, short-lived subjects 11/30/2020 17

Access Control Conditions n n Data-dependent conditions: access constraints based on the value of the accessed data Time-dependent: access constraints based on the time of the data access Context-dependent: access constraints based on combinations on data which can be accessed History-dependent: access constraints based on previously accessed data 11/30/2020 18

Access Control Mechanisms Security through Views n Stored Procedures n Grant and Revoke n Query modification n 11/30/2020 19

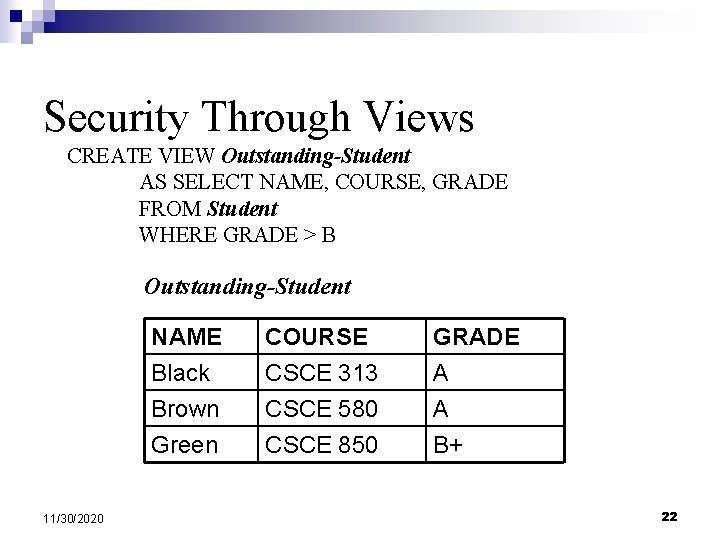
Security Through Views n Assign rights to access predefined views CREATE VIEW Outstanding-Student AS SELECT NAME, COURSE, GRADE FROM Student WHERE GRADE > B Problem: Difficult to maintain updates. 11/30/2020 20

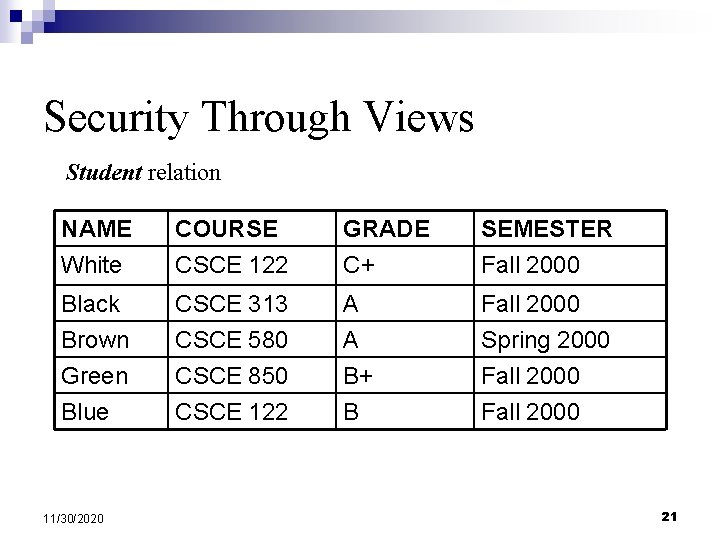
Security Through Views Student relation NAME White COURSE CSCE 122 GRADE C+ SEMESTER Fall 2000 Black Brown CSCE 313 CSCE 580 A A Fall 2000 Spring 2000 Green Blue CSCE 850 CSCE 122 B+ B Fall 2000 11/30/2020 21

Security Through Views CREATE VIEW Outstanding-Student AS SELECT NAME, COURSE, GRADE FROM Student WHERE GRADE > B Outstanding-Student NAME Black Brown Green 11/30/2020 COURSE CSCE 313 CSCE 580 CSCE 850 GRADE A A B+ 22

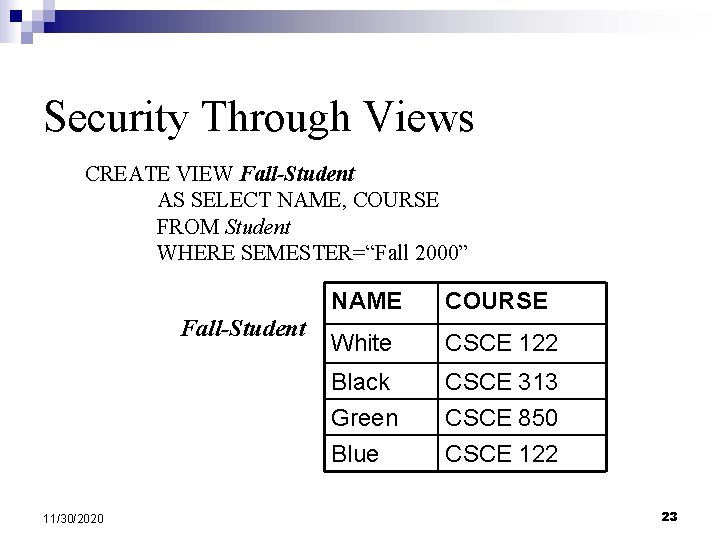
Security Through Views CREATE VIEW Fall-Student AS SELECT NAME, COURSE FROM Student WHERE SEMESTER=“Fall 2000” Fall-Student 11/30/2020 NAME COURSE White CSCE 122 Black Green CSCE 313 CSCE 850 Blue CSCE 122 23

Stored Procedures n n Assign rights to execute compiled programs GRANT RUN ON <program> TO <user> Problem: Programs may access resources for which the user who runs the program does not have permission. 11/30/2020 24
![Grant and Revoke GRANT privilege ON relation To user WITH GRANT OPTION n Grant and Revoke GRANT <privilege> ON <relation> To <user> [WITH GRANT OPTION] ------------------------------------------------------------------ n](https://slidetodoc.com/presentation_image_h/c8b5e0c98052203e1ee4fa031926ca7d/image-25.jpg)
Grant and Revoke GRANT <privilege> ON <relation> To <user> [WITH GRANT OPTION] ------------------------------------------------------------------ n n n GRANT SELECT * ON Student TO Matthews GRANT SELECT *, UPDATE(GRADE) ON Student TO FARKAS GRANT SELECT(NAME) ON Student TO Brown GRANT command applies to base relations as well as views 11/30/2020 25
![Grant and Revoke REVOKE privileges ON relation FROM user n n n REVOKE Grant and Revoke REVOKE <privileges> [ON <relation>] FROM <user> ------------------------------------------------------------- n n n REVOKE](https://slidetodoc.com/presentation_image_h/c8b5e0c98052203e1ee4fa031926ca7d/image-26.jpg)
Grant and Revoke REVOKE <privileges> [ON <relation>] FROM <user> ------------------------------------------------------------- n n n REVOKE SELECT* ON Student FROM Blue REVOKE UPDATE ON Student FROM Black REVOKE SELECT(NAME) ON Student FROM Brown 11/30/2020 26

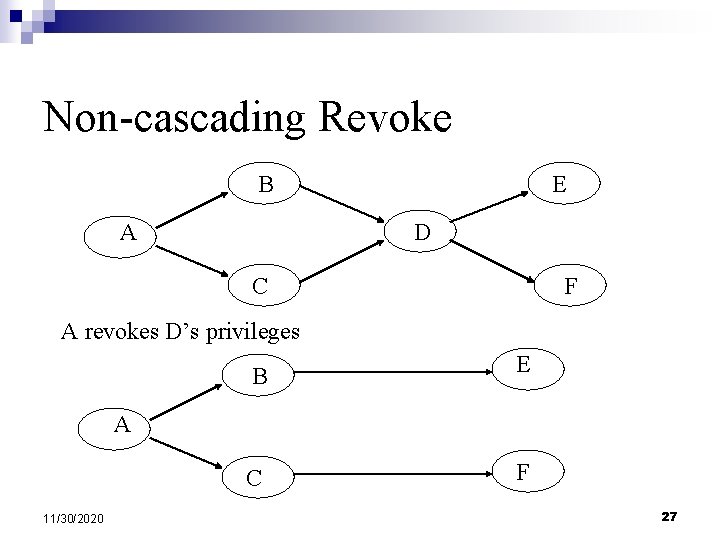
Non-cascading Revoke B A E D C F A revokes D’s privileges B E C F A 11/30/2020 27

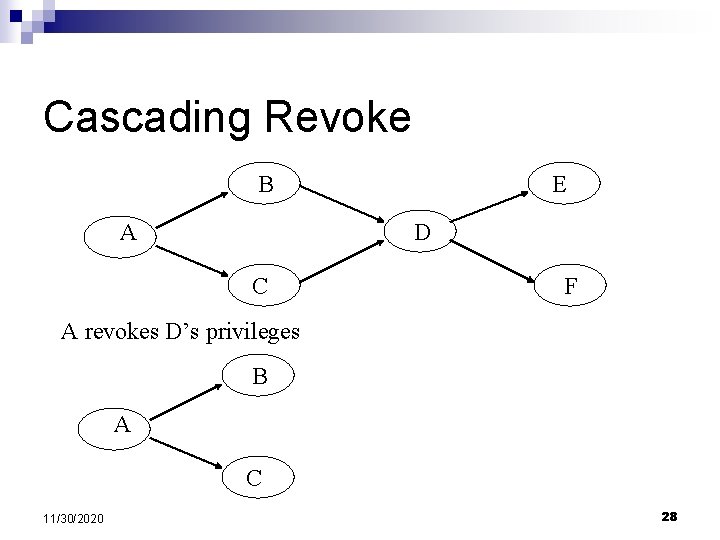
Cascading Revoke B A E D C F A revokes D’s privileges B A C 11/30/2020 28

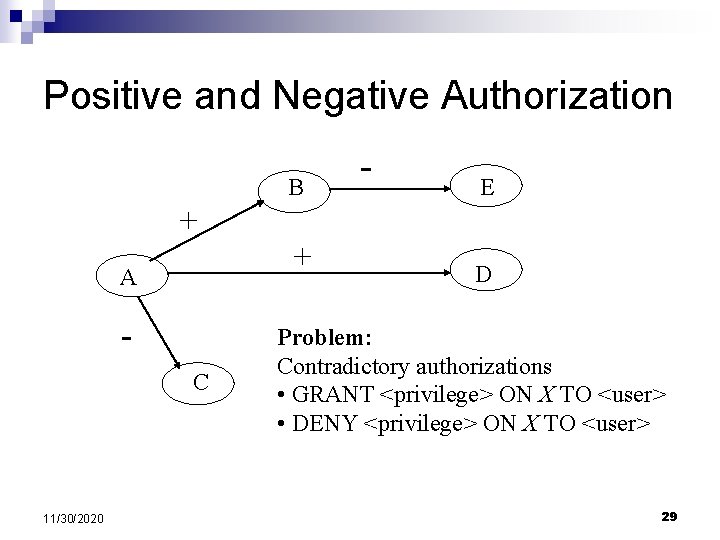
Positive and Negative Authorization B - E + + A C 11/30/2020 D Problem: Contradictory authorizations • GRANT <privilege> ON X TO <user> • DENY <privilege> ON X TO <user> 29

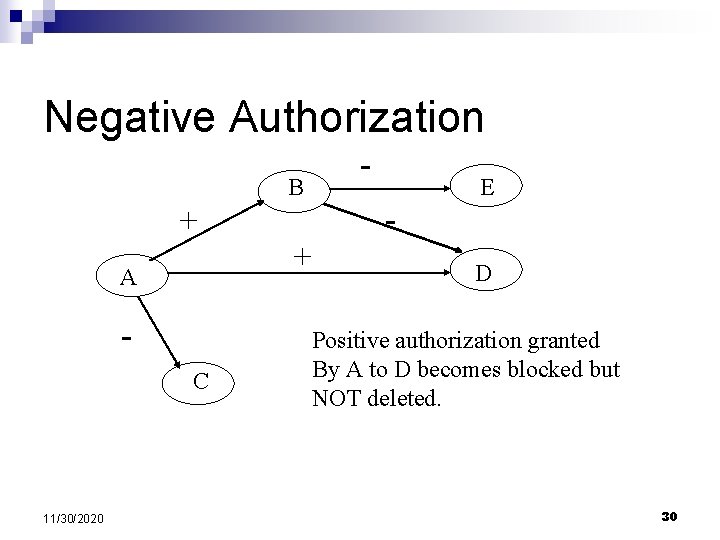
Negative Authorization - B + + A C 11/30/2020 - E D Positive authorization granted By A to D becomes blocked but NOT deleted. 30

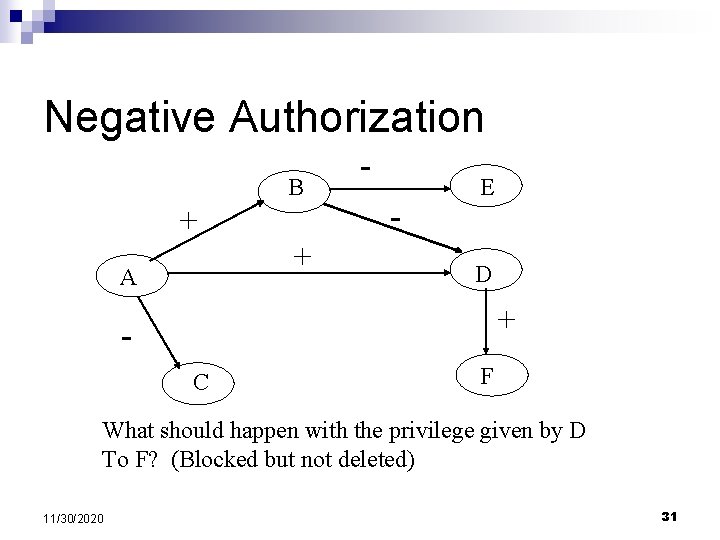
Negative Authorization B + + A - E D + C F What should happen with the privilege given by D To F? (Blocked but not deleted) 11/30/2020 31

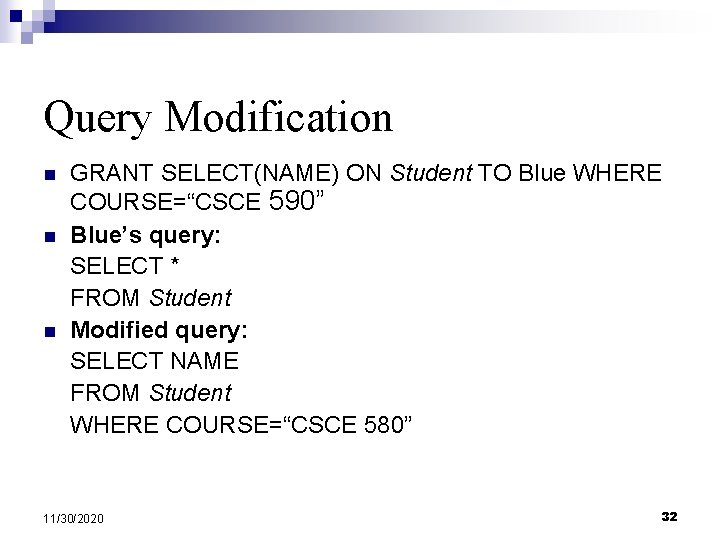
Query Modification n GRANT SELECT(NAME) ON Student TO Blue WHERE COURSE=“CSCE 590” Blue’s query: SELECT * FROM Student Modified query: SELECT NAME FROM Student WHERE COURSE=“CSCE 580” 11/30/2020 32