Active Directory and Dynamic Access Control Pete Calvert


































































- Slides: 108

Active Directory and Dynamic Access Control Pete Calvert (@erucsbo)




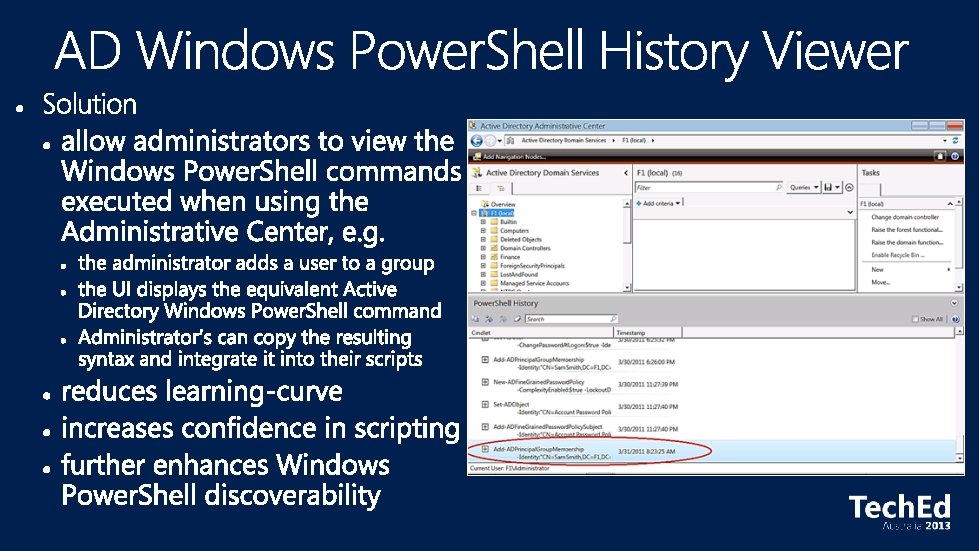
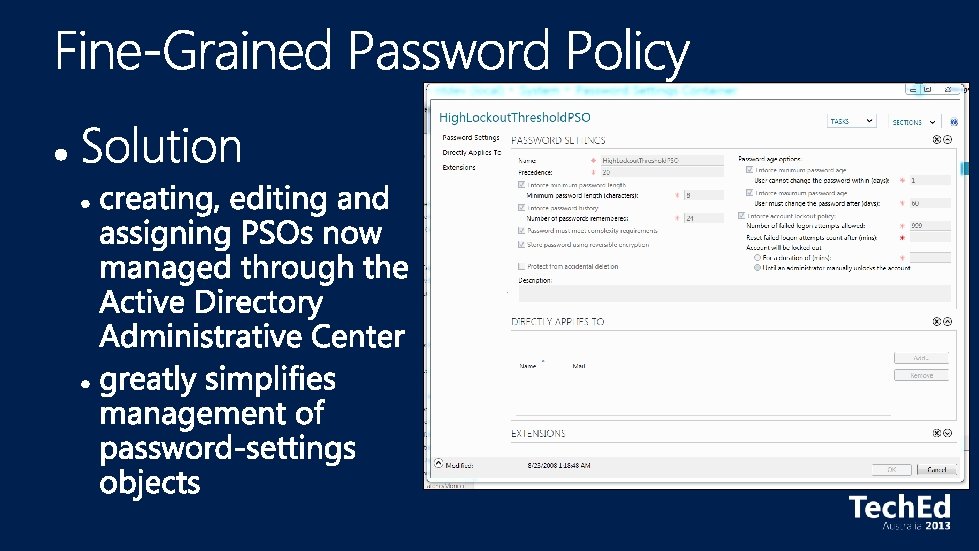
Virtualization That Just Works • All Active Directory features work equally well in physical, virtual or mixed environments Simplified Deployment of Active Directory • • Complete integration of environment preparation, role installation and DC promotion into a single UI DCs can be deployed rapidly to ease disaster recovery and workload balancing DCs can be deployed remotely on multiple machines from a single Windows 8 machine Consistent command-line experience through Windows Power. Shell enables automation of deployment tasks Simplified Management of Active Directory • • GUI that simplifies complex tasks such as recovering a deleted object or managing password policies Active Directory Windows Power. Shell viewer shows the commands for actions performed in the GUI Active Directory Windows Power. Shell support for managing replication and topology data Simplify delegation and management of service accounts

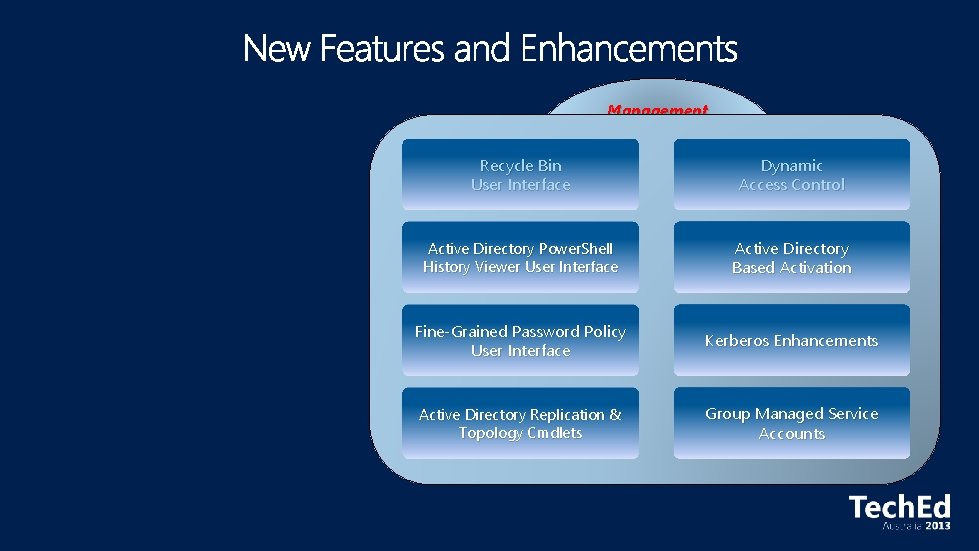
Miscellaneous Management Simplified Deployment Recycle Bin User Interface Dynamic Access Control Virtualization-Safe Technology Active Directory Power. Shell History Viewer User Interface Active Directory Based Activation Rapid Deployment Fine-Grained Password Policy User Interface Kerberos Enhancements Active Directory Platform Changes Active Directory Replication & Topology Cmdlets Group Managed Service Accounts

Miscellaneous Simplified Deployment Virtualization-Safe Technology Rapid Deployment Active Directory Platform Changes

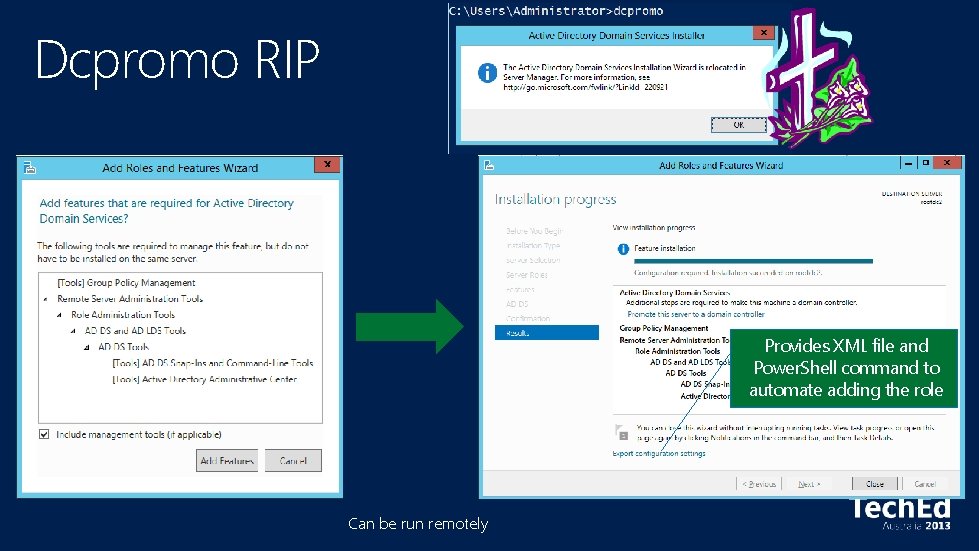
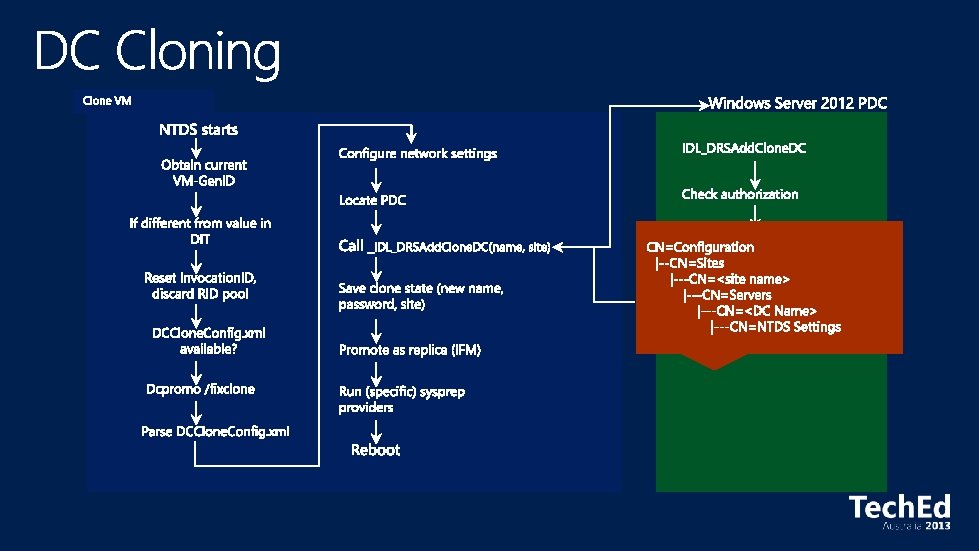
Dcpromo RIP Provides XML file and Power. Shell command to automate adding the role Can be run remotely

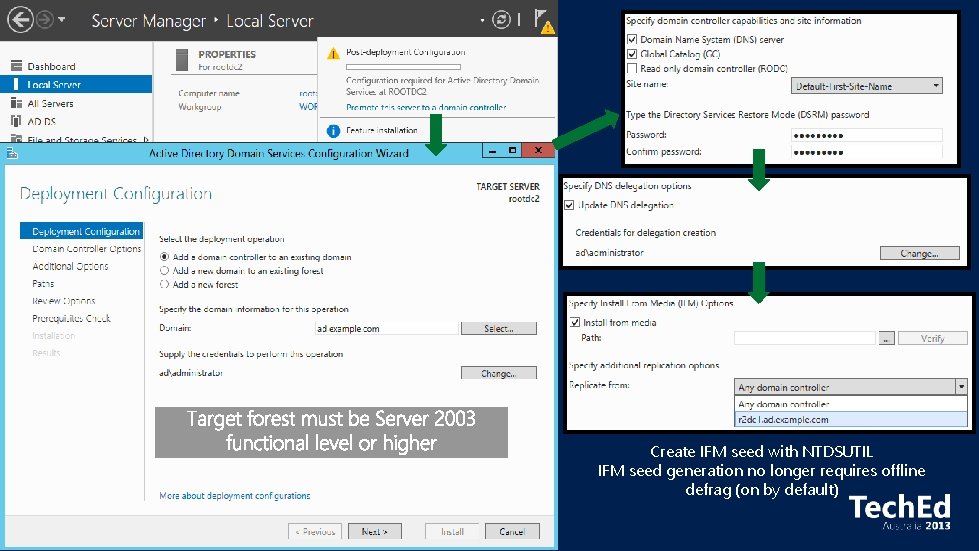
Create IFM seed with NTDSUTIL IFM seed generation no longer requires offline defrag (on by default)

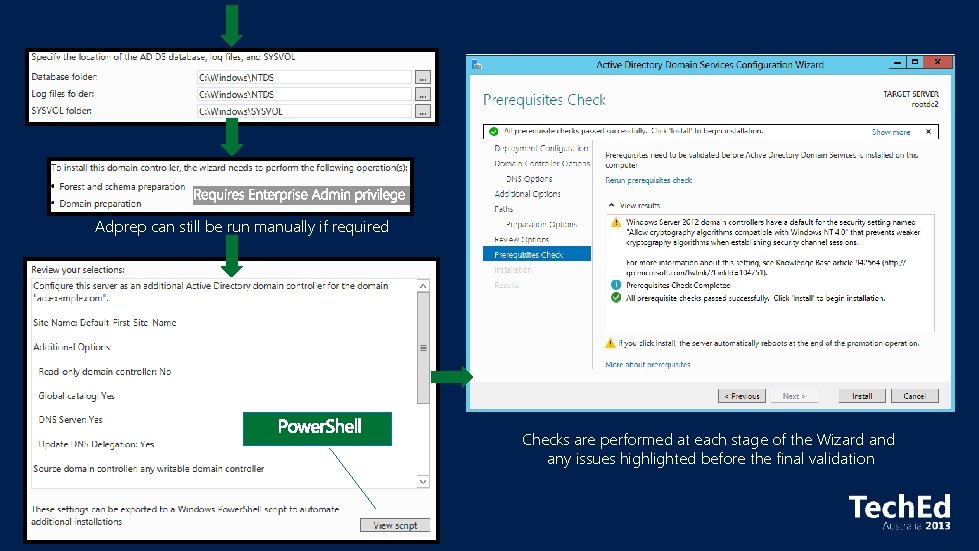
Adprep can still be run manually if required Checks are performed at each stage of the Wizard any issues highlighted before the final validation



http: //microsoft. com

Miscellaneous Simplified Deployment Virtualization-Safe Technology Rapid Deployment Active Directory Platform Changes

Any problems?

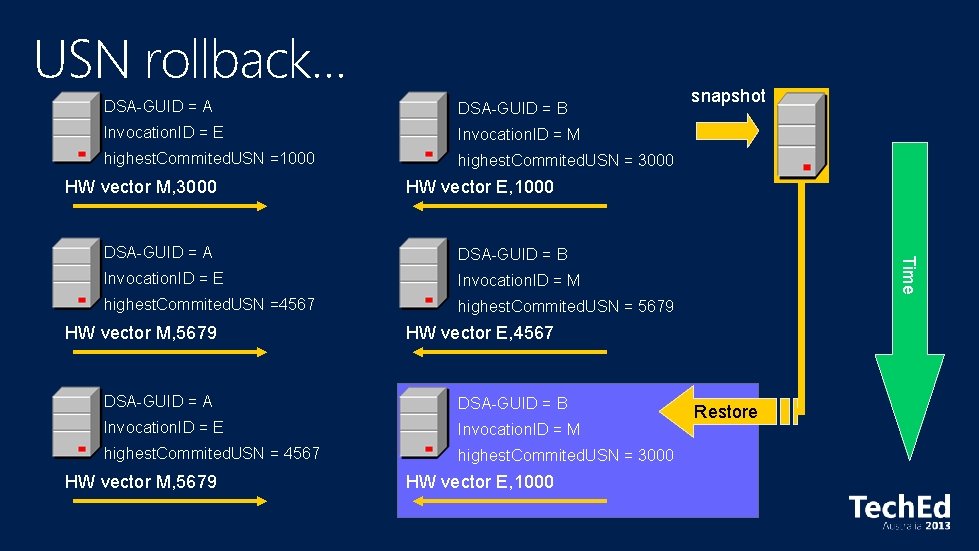
USN rollback… DSA-GUID = A DSA-GUID = B Invocation. ID = E Invocation. ID = M highest. Commited. USN =1000 highest. Commited. USN = 3000 HW vector M, 3000 HW vector E, 1000 DSA-GUID = B Invocation. ID = E Invocation. ID = M highest. Commited. USN =4567 highest. Commited. USN = 5679 HW vector E, 4567 DSA-GUID = A DSA-GUID = B Invocation. ID = E Invocation. ID = M highest. Commited. USN = 4567 highest. Commited. USN = 3000 HW vector M, 5679 Time DSA-GUID = A HW vector M, 5679 snapshot HW vector E, 1000 Restore

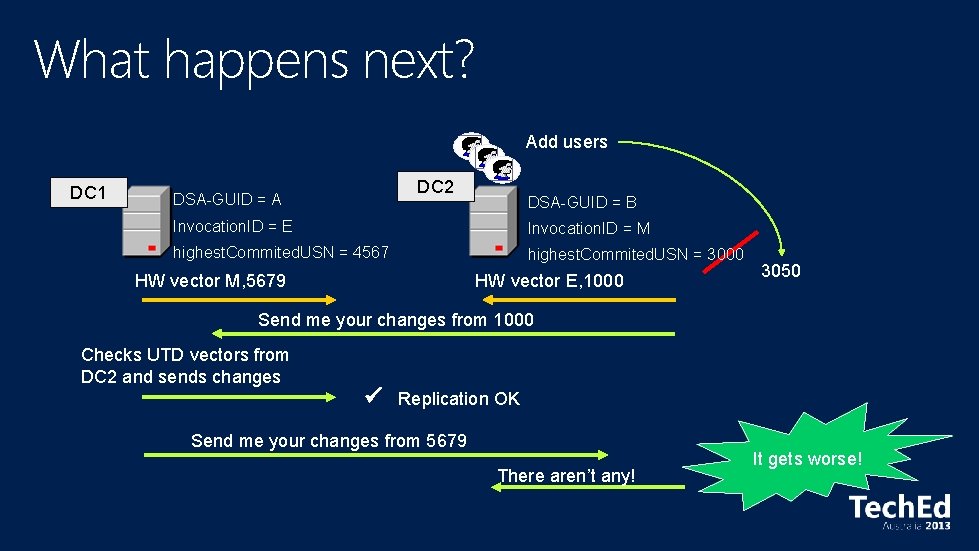
What happens next? Add users DC 1 DC 2 DSA-GUID = A DSA-GUID = B Invocation. ID = E Invocation. ID = M highest. Commited. USN = 4567 highest. Commited. USN = 3000 HW vector M, 5679 HW vector E, 1000 3050 Send me your changes from 1000 Checks UTD vectors from DC 2 and sends changes Replication OK Send me your changes from 5679 There aren’t any! It gets worse!

DSA-GUID = A DSA-GUID = B Invocation. ID = E Invocation. ID = M highest. Commited. USN = 4567 highest. Commited. USN = 3050 HW vector M, 5679 HW vector E, 1000 Send me your changes from 5679 There aren’t any! Appears more up to date than me, that’s not right! Replication log Write event log messages Disable inbound and outbound replication Stop Netlogon service


e ch t a W ac p s this

Miscellaneous Simplified Deployment Virtualization-Safe Technology Rapid Deployment Active Directory Platform Changes


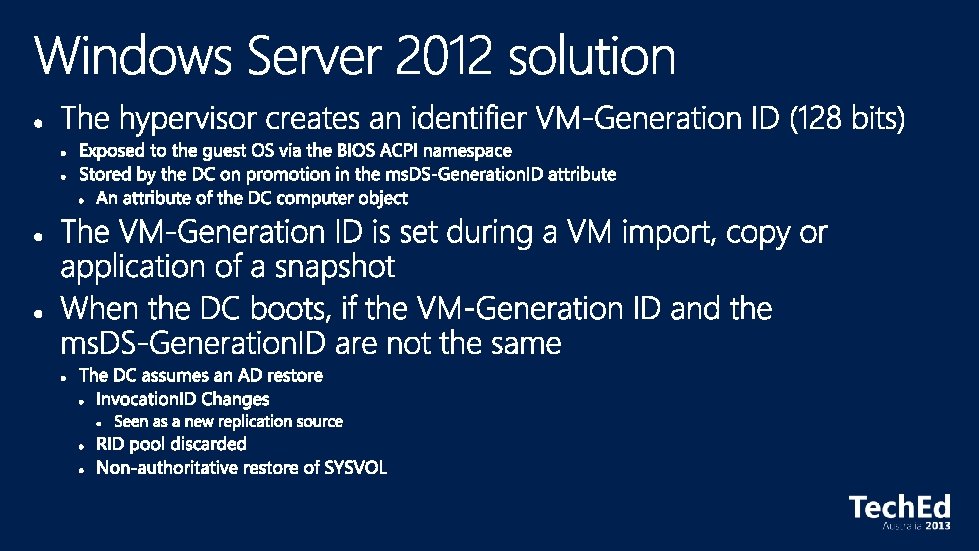
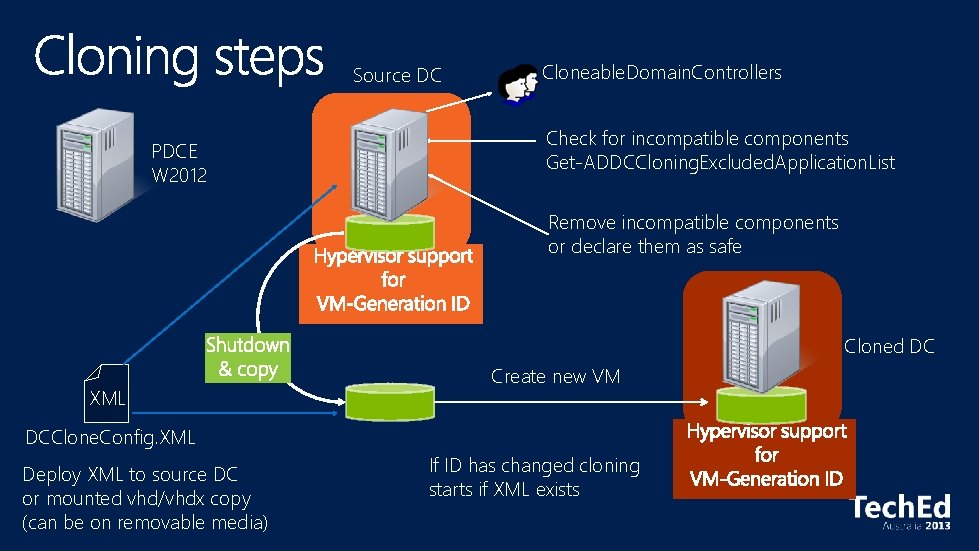
Source DC PDCE W 2012 Cloneable. Domain. Controllers Check for incompatible components Get-ADDCCloning. Excluded. Application. List Remove incompatible components or declare them as safe Cloned DC XML Create new VM DCClone. Config. XML Deploy XML to source DC or mounted vhd/vhdx copy (can be on removable media) If ID has changed cloning starts if XML exists





Miscellaneous Simplified Deployment Virtualization-Safe Technology Rapid Deployment Active Directory Platform Changes




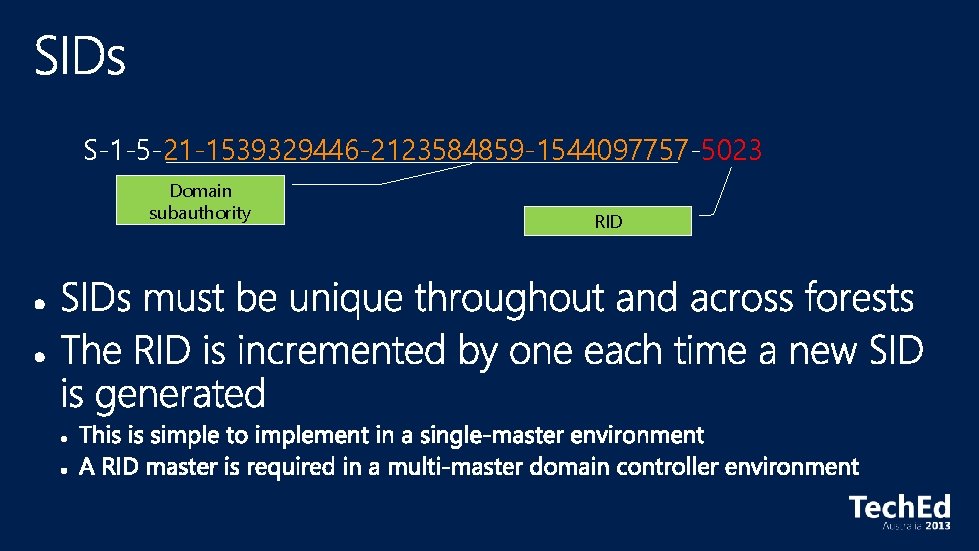
S-1 -5 -21 -1539329446 -2123584859 -1544097757 -5023 Domain subauthority RID















Miscellaneous Management Simplified Deployment Recycle Bin User Interface Dynamic Access Control Virtualization-Safe Technology Active Directory Power. Shell History Viewer User Interface Active Directory Based Activation Rapid Deployment Fine-Grained Password Policy User Interface Kerberos Enhancements Active Directory Platform Changes Active Directory Replication & Topology Cmdlets Group Managed Service Accounts

Management Recycle Bin User Interface Dynamic Access Control Active Directory Power. Shell History Viewer User Interface Active Directory Based Activation Fine-Grained Password Policy User Interface Kerberos Enhancements Active Directory Replication & Topology Cmdlets Group Managed Service Accounts




Management Recycle Bin User Interface Dynamic Access Control Active Directory Power. Shell History Viewer User Interface Active Directory Based Activation Fine-Grained Password Policy User Interface Kerberos Enhancements Active Directory Replication & Topology Cmdlets Group Managed Service Accounts



File Access Share Permissions NTFS Permissions Access Control Decision

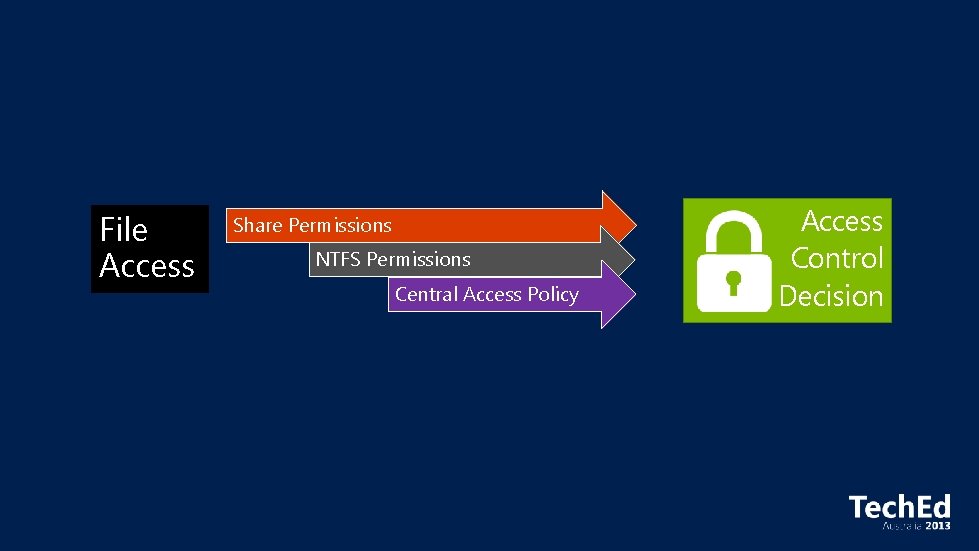
File Access Share Permissions NTFS Permissions Central Access Policy Access Control Decision


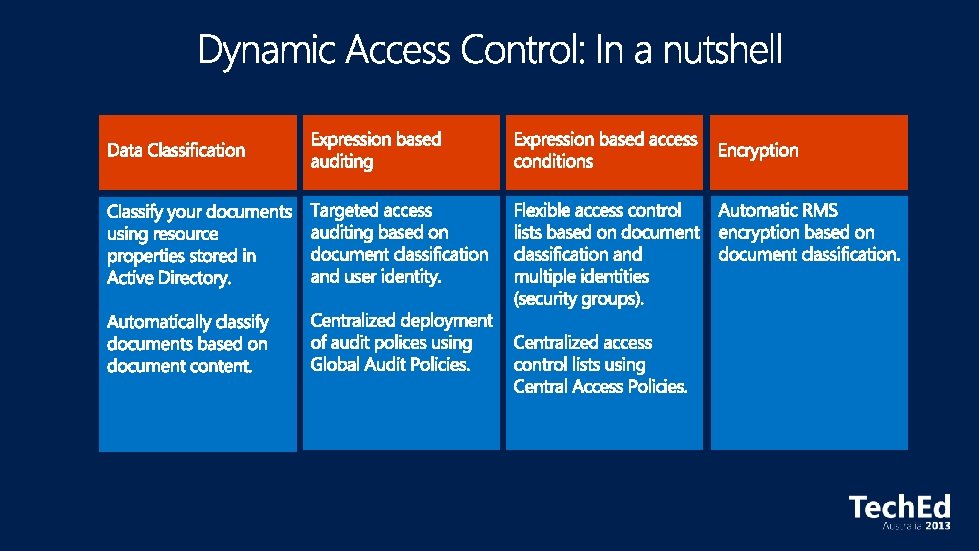
User and Device Claims • User and computer attributes can be used in ACEs Expression-Based ACEs • ACEs with conditions, including Boolean logic and relative operators Classification Enhancements • File classifications can be used in authorization decisions • Continuous automatic classification • Automatic RMS encryption based on classification Central Access and Audit Policies • Central authorization/audit rules defined in AD and applied across multiple file servers Access Denied Assistance • Allow users to request access • Provide detailed troubleshooting info to admins

Pre-2012: Security Principals Only • • • Restricted to making policy decisions based on the user’s group memberships Shadow groups are often created to reflect existing attributes as groups Groups have rules around who can be members of which types of groups No way to transform groups across AD trust boundaries No way to control access based on characteristics of user’s device Windows Server 2012: Security Principals, User Claims, Device Claims • • • Selected AD user/computer attributes are included in the security token Claims can be used directly in file server permissions Claims are consistently issued to all users in a forest Claims can be transformed across trust boundaries Enables newer types of policies that weren’t possible before: • Example: Allow Write if User. Member. Of(Finance) and User. Employee. Type=Full. Time and Device. Managed=True

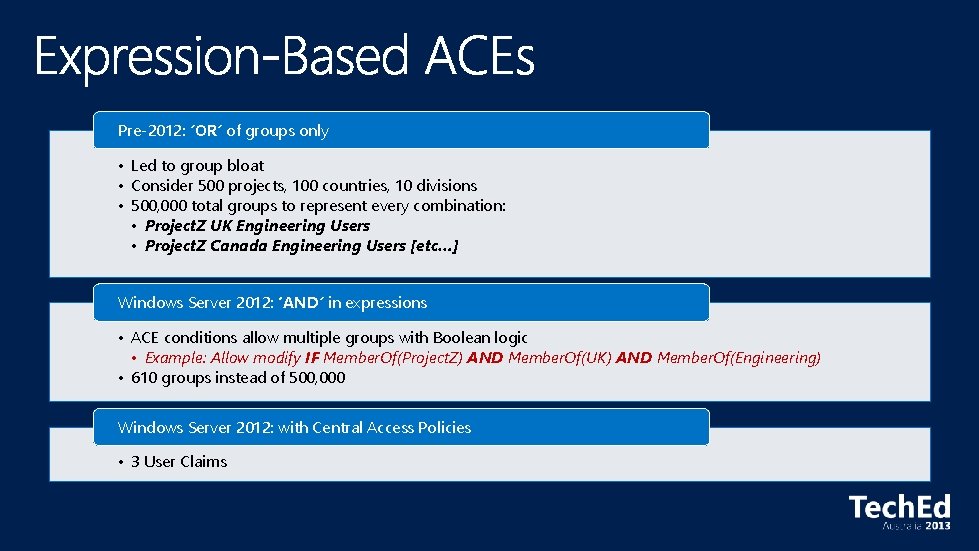
Pre-2012: ’OR’ of groups only • Led to group bloat • Consider 500 projects, 100 countries, 10 divisions • 500, 000 total groups to represent every combination: • Project. Z UK Engineering Users • Project. Z Canada Engineering Users [etc…] Windows Server 2012: ‘AND’ in expressions • ACE conditions allow multiple groups with Boolean logic • Example: Allow modify IF Member. Of(Project. Z) AND Member. Of(UK) AND Member. Of(Engineering) • 610 groups instead of 500, 000 Windows Server 2012: with Central Access Policies • 3 User Claims

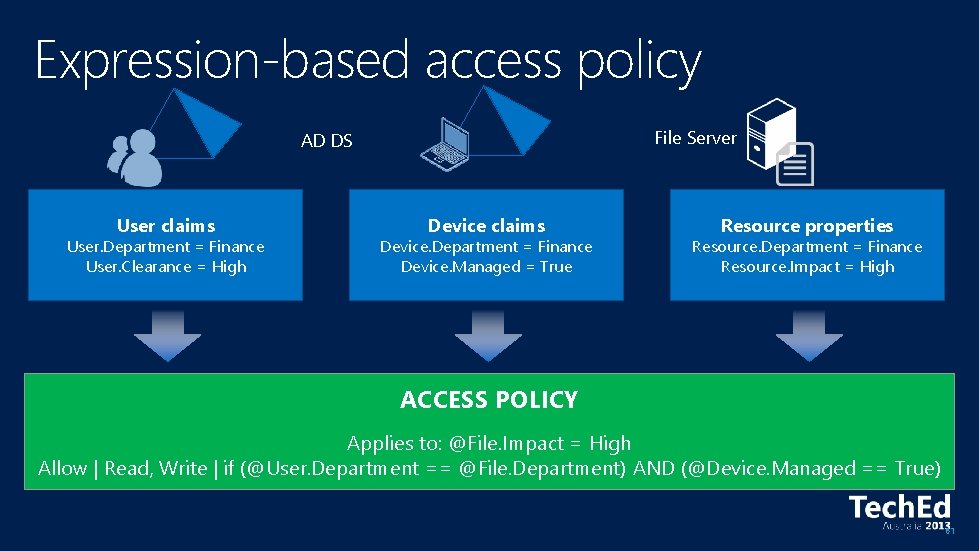
Expression-based access policy File Server AD DS User claims User. Department = Finance User. Clearance = High Device claims Device. Department = Finance Device. Managed = True Resource properties Resource. Department = Finance Resource. Impact = High ACCESS POLICY Applies to: @File. Impact = High Allow | Read, Write | if (@User. Department == @File. Department) AND (@Device. Managed == True) 61


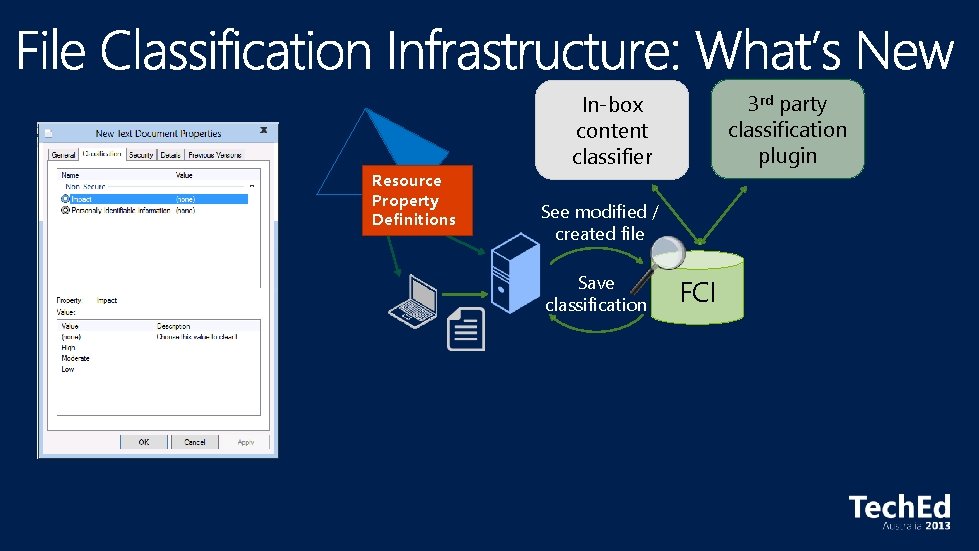
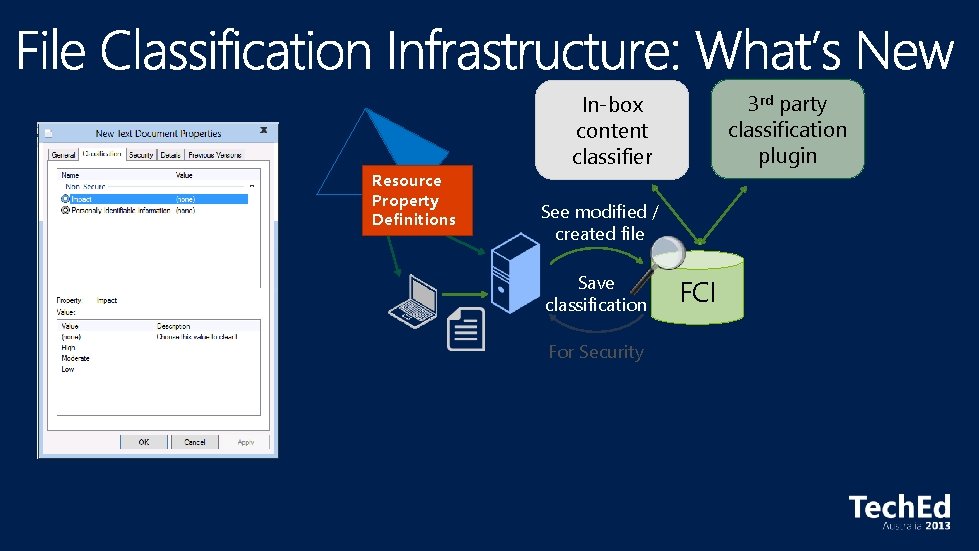
Resource Property Definitions

Resource Property Definitions 3 rd party classification plugin In-box content classifier See modified / created file Save classification FCI

Resource Property Definitions 3 rd party classification plugin In-box content classifier See modified / created file Save classification For Security FCI

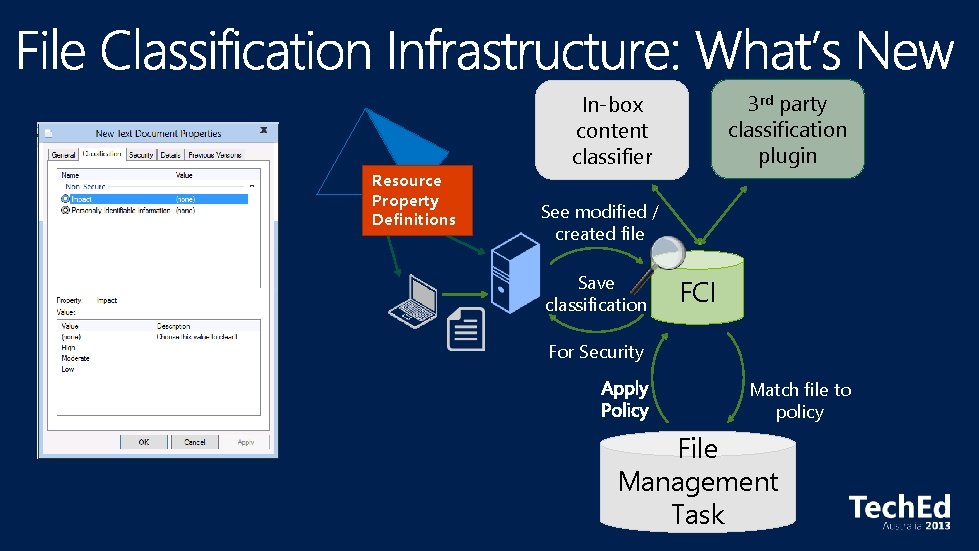
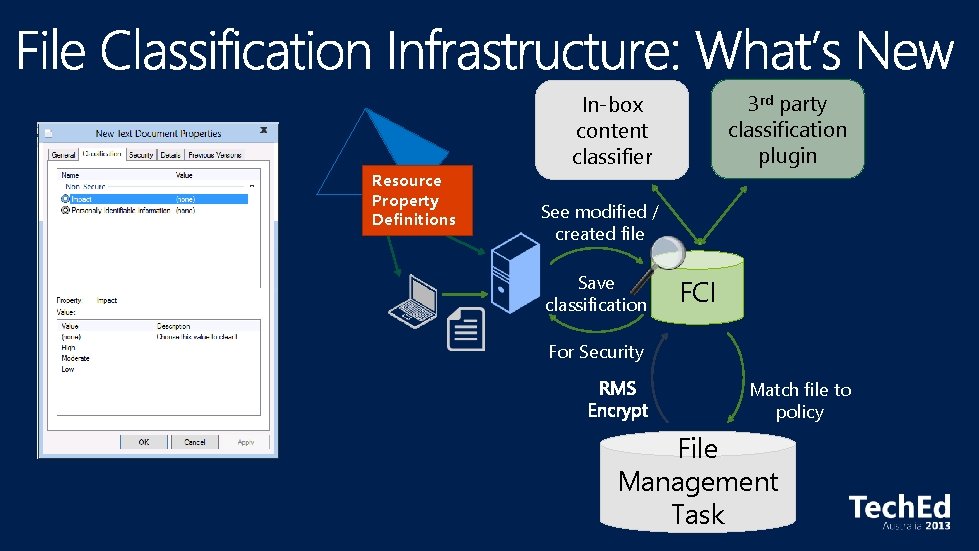
Resource Property Definitions 3 rd party classification plugin In-box content classifier See modified / created file Save classification FCI For Security Match file to policy File Management Task

Resource Property Definitions 3 rd party classification plugin In-box content classifier See modified / created file Save classification FCI For Security Match file to policy File Management Task

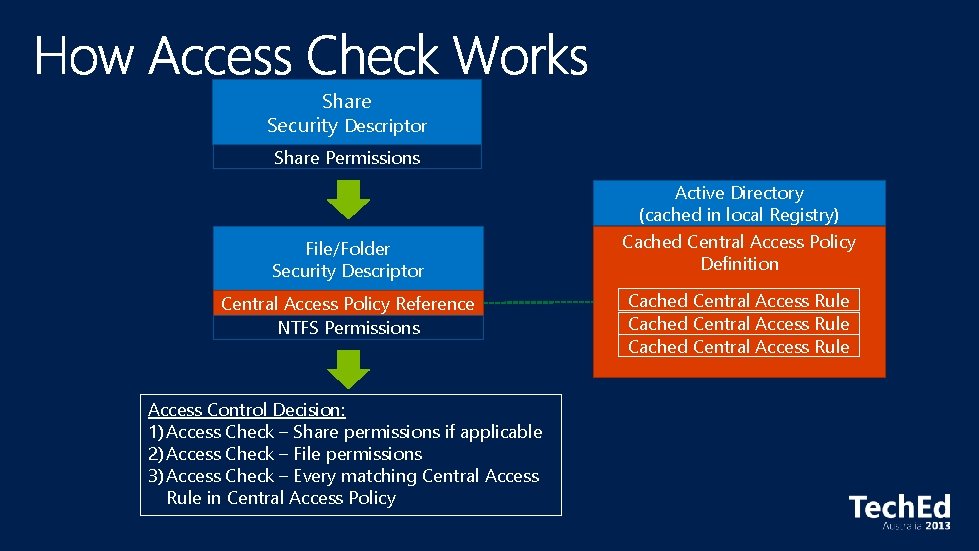
Share Security Descriptor Share Permissions File/Folder Security Descriptor Central Access Policy Reference NTFS Permissions Access Control Decision: 1) Access Check – Share permissions if applicable 2) Access Check – File permissions 3) Access Check – Every matching Central Access Rule in Central Access Policy Active Directory (cached in local Registry) Cached Central Access Policy Definition Cached Central Access Rule

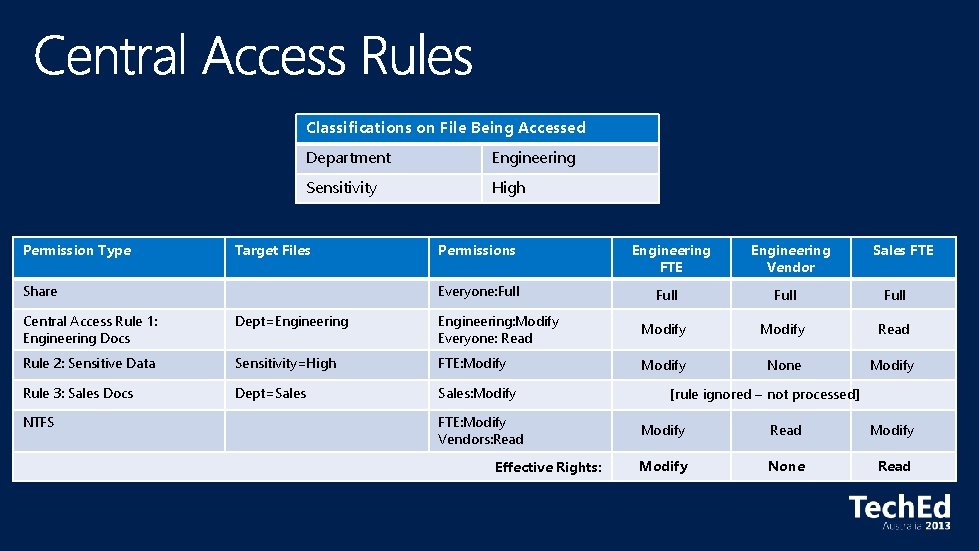
Classifications on File Being Accessed Permission Type Department Engineering Sensitivity High Target Files Share Permissions Everyone: Full Engineering FTE Engineering Vendor Sales FTE Full Central Access Rule 1: Engineering Docs Dept=Engineering: Modify Everyone: Read Modify Read Rule 2: Sensitive Data Sensitivity=High FTE: Modify None Modify Rule 3: Sales Docs Dept=Sales: Modify NTFS FTE: Modify Vendors: Read Effective Rights: [rule ignored – not processed] Modify Read Modify None Read

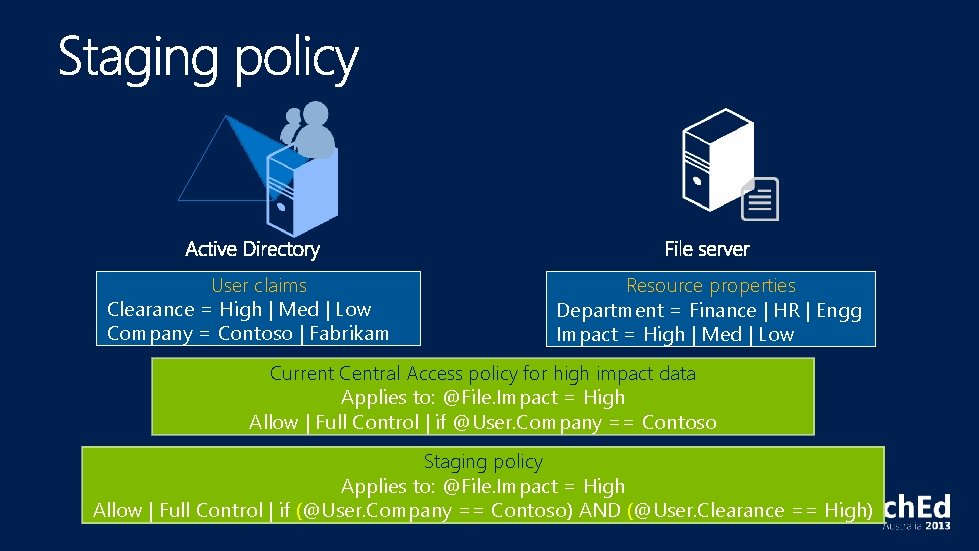
Staging Policies

User claims Clearance = High | Med | Low Company = Contoso | Fabrikam Resource properties Department = Finance | HR | Engg Impact = High | Med | Low Current Central Access policy for high impact data Applies to: @File. Impact = High Allow | Full Control | if @User. Company == Contoso Staging policy Applies to: @File. Impact = High Allow | Full Control | if (@User. Company == Contoso) AND (@User. Clearance == High)

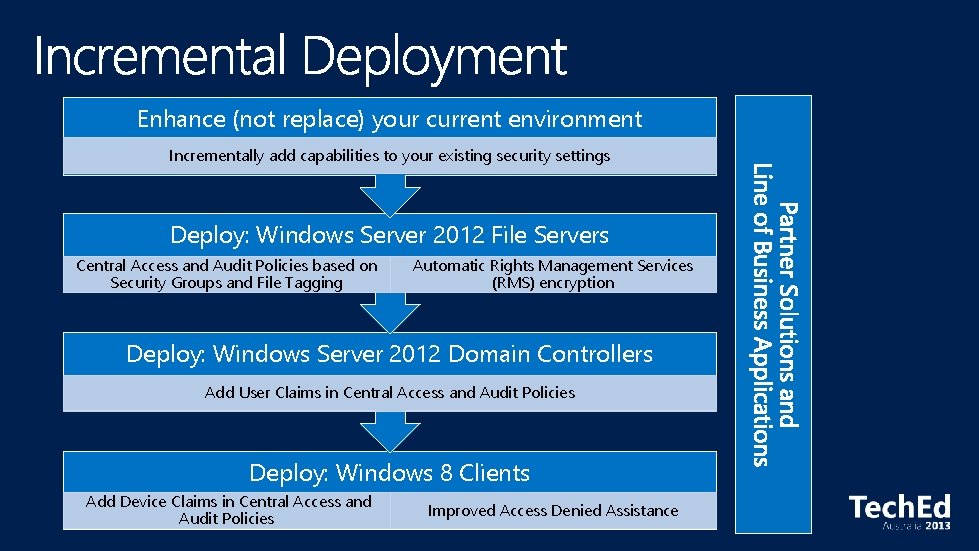
Enhance (not replace) your current environment Incrementally add capabilities to your existing security settings Deploy: Windows Server 2012 File Servers Central Access and Audit Policies based on Security Groups and File Tagging Automatic Rights Management Services (RMS) encryption Deploy: Windows Server 2012 Domain Controllers Add User Claims in Central Access and Audit Policies Deploy: Windows 8 Clients Add Device Claims in Central Access and Audit Policies Improved Access Denied Assistance


Management Recycle Bin User Interface Dynamic Access Control Active Directory Power. Shell History Viewer User Interface Active Directory Based Activation Fine-Grained Password Policy User Interface Kerberos Enhancements Active Directory Replication & Topology Cmdlets Group Managed Service Accounts




Management Recycle Bin User Interface Dynamic Access Control Active Directory Windows Power. Shell History Viewer Active Directory Based Activation Fine-Grained Password Policy User Interface Kerberos Enhancements Active Directory Replication & Topology Cmdlets Group Managed Service Accounts




Management Recycle Bin User Interface Dynamic Access Control Active Directory Windows Power. Shell History Viewer Active Directory Based Activation Fine-Grained Password Policy User Interface Kerberos Enhancements Active Directory Replication & Topology Cmdlets Group Managed Service Accounts




Management Recycle Bin User Interface Dynamic Access Control Active Directory Windows Power. Shell History Viewer Active Directory Based Activation Fine-Grained Password Policy User Interface Kerberos Enhancements Active Directory Replication & Topology Cmdlets Group Managed Service Accounts


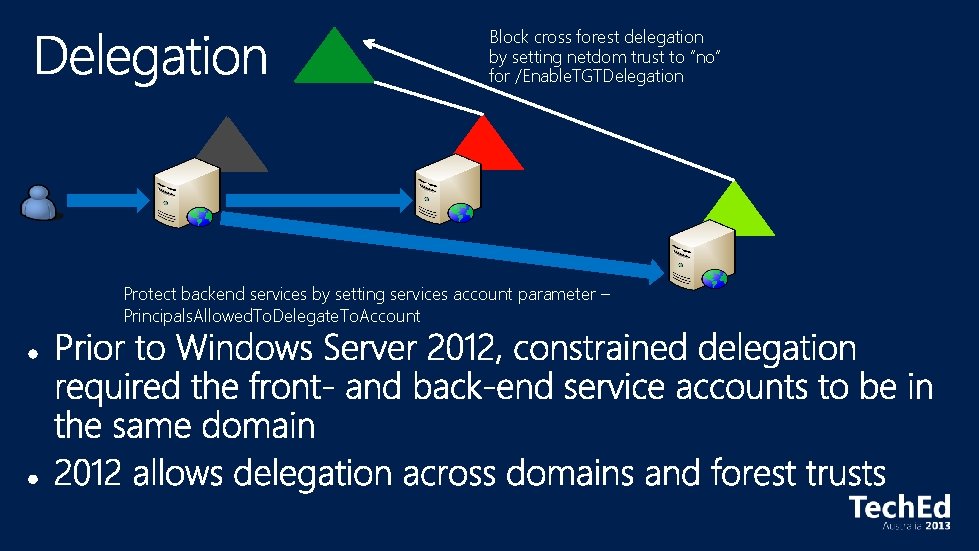
Block cross forest delegation by setting netdom trust to “no” for /Enable. TGTDelegation Protect backend services by setting services account parameter – Principals. Allowed. To. Delegate. To. Account

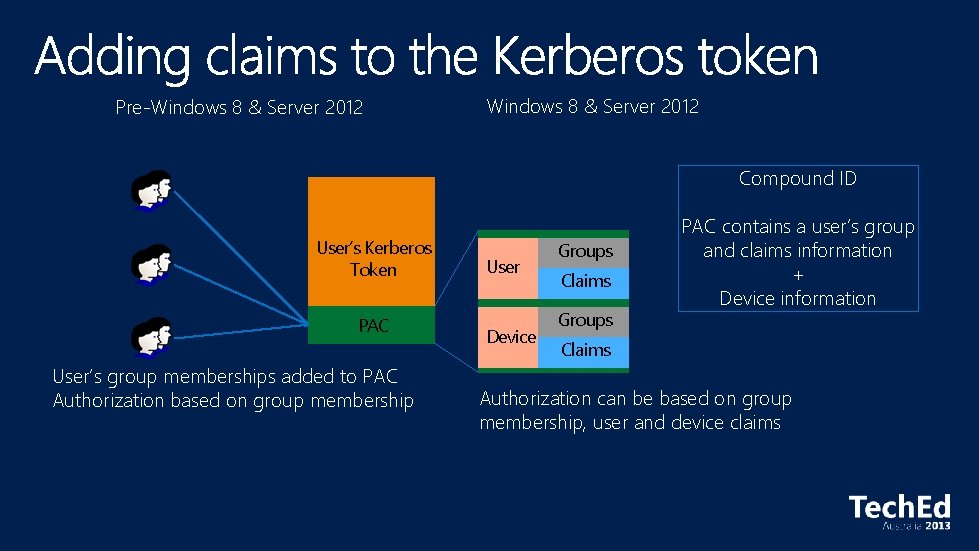
Pre-Windows 8 & Server 2012 Compound ID User’s Kerberos Token PAC User’s group memberships added to PAC Authorization based on group membership User Device Groups Claims Groups PAC contains a user’s group and claims information + Device information Claims Authorization can be based on group membership, user and device claims




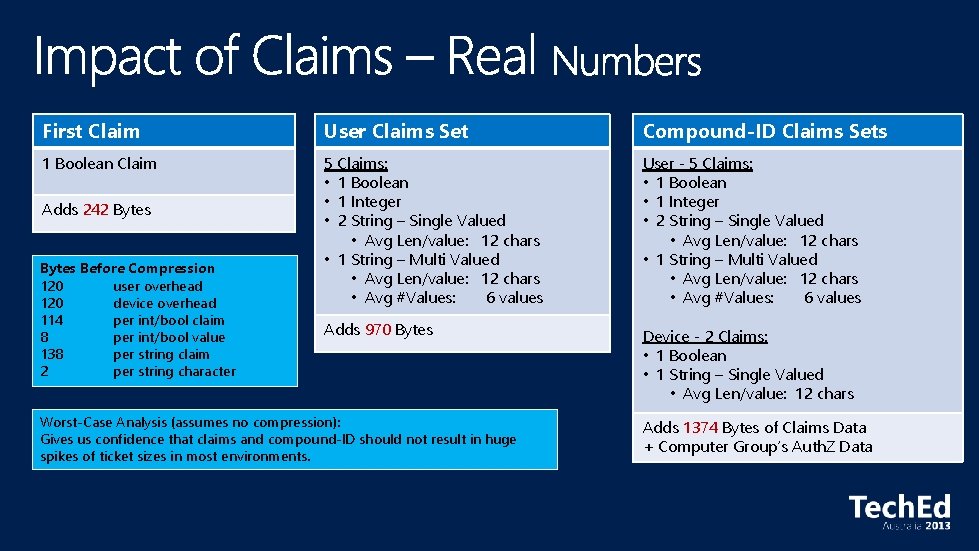
First Claim User Claims Set Compound-ID Claims Sets 1 Boolean Claim 5 Claims: • 1 Boolean • 1 Integer • 2 String – Single Valued • Avg Len/value: 12 chars • 1 String – Multi Valued • Avg Len/value: 12 chars • Avg #Values: 6 values User - 5 Claims: • 1 Boolean • 1 Integer • 2 String – Single Valued • Avg Len/value: 12 chars • 1 String – Multi Valued • Avg Len/value: 12 chars • Avg #Values: 6 values Adds 970 Bytes Device - 2 Claims: • 1 Boolean • 1 String – Single Valued • Avg Len/value: 12 chars Adds 242 Bytes Before Compression 120 user overhead 120 device overhead 114 per int/bool claim 8 per int/bool value 138 per string claim 2 per string character Worst-Case Analysis (assumes no compression): Gives us confidence that claims and compound-ID should not result in huge spikes of ticket sizes in most environments. Adds 1374 Bytes of Claims Data + Computer Group’s Auth. Z Data

Management Recycle Bin User Interface Dynamic Access Control Active Directory Windows Power. Shell History Viewer Active Directory Based Activation Fine-Grained Password Policy User Interface Kerberos Enhancements Active Directory Replication & Topology Cmdlets Group Managed Service Accounts




Management Recycle Bin User Interface Dynamic Access Control Active Directory Windows Power. Shell History Viewer Active Directory Based Activation Fine-Grained Password Policy User Interface Kerberos Enhancements Active Directory Replication & Topology Cmdlets Group Managed Service Accounts


Workplace Join using Device Registration Service Connecting to Applications and Services from anywhere Web Application Proxy Managing Risk with Multi-Factor Access Control Managing Risk with Additional Multi-Factor Authentication for Sensitive Applications

• You host it, on-premises / Cloud • You manage the infrastructure and the data • Services: • AD Directory Services (AD DS) • Kerberos authentication • NTLM authentication • • AD Lightweight Directory Services (AD LDS) AD Federation Services (AD FS) AD Certificate Services (AD CS) AD Rights Management Services (AD RMS) • • Microsoft hosts it in their datacenters Microsoft manages the infrastructure You manage the data Services: • Directory Services • Federated authentication • Access Control Services (ACS)

In Summary…. .

Leverage new technologies

Extend Identity governance reach

Implement effective access control

What’s New in Active Directory 2012 R 2 Intro to Dynamic Access Control

http: //channel 9. msdn. com/Events/Tech. Ed/Australia/2013 http: //www. microsoftvirtualacademy. com/ http: //technet. microsoft. com/en-au/ http: //msdn. microsoft. com/en-au/
