Usage Control A Vision for Next Generation Access


![Prior Work n Incrementally enhanced models n n Provisional authorization [Kudo & Hada, 2000] Prior Work n Incrementally enhanced models n n Provisional authorization [Kudo & Hada, 2000]](https://slidetodoc.com/presentation_image/58691add324c58907ad311432d37770f/image-4.jpg)












- Slides: 32

Usage Control: A Vision for Next Generation Access Control Oct 14, 2003 Ravi Sandhu and Jaehong Park (www. list. gmu. edu) Laboratory for Information Security Technology (LIST) George Mason University © 2003 GMU LIST

Problem Statement n Traditional access control models are not adequate for today’s distributed, networkconnected digital environment. n n Authorization only – No obligation or condition based control Decision is made before access – No ongoing control No consumable rights - No mutable attributes Rights are pre-defined and granted to subjects © 2003 GMU LIST 2

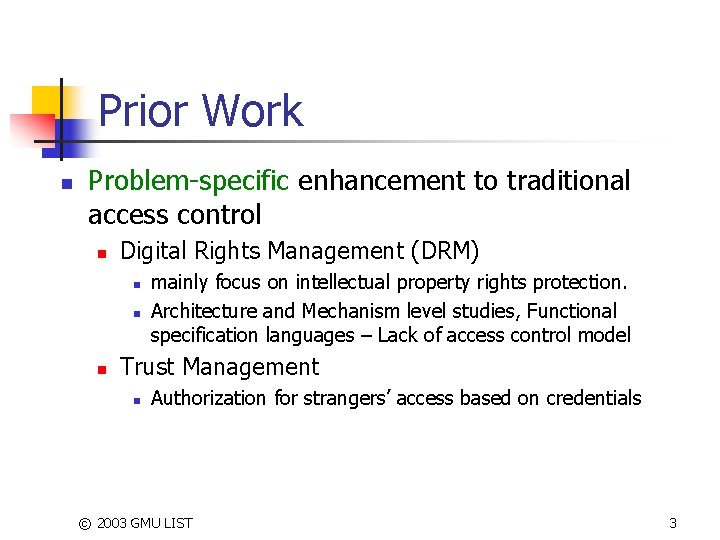
Prior Work n Problem-specific enhancement to traditional access control n Digital Rights Management (DRM) n n n mainly focus on intellectual property rights protection. Architecture and Mechanism level studies, Functional specification languages – Lack of access control model Trust Management n Authorization for strangers’ access based on credentials © 2003 GMU LIST 3
![Prior Work n Incrementally enhanced models n n Provisional authorization Kudo Hada 2000 Prior Work n Incrementally enhanced models n n Provisional authorization [Kudo & Hada, 2000]](https://slidetodoc.com/presentation_image/58691add324c58907ad311432d37770f/image-4.jpg)
Prior Work n Incrementally enhanced models n n Provisional authorization [Kudo & Hada, 2000] EACL [Ryutov & Neuman, 2001] Task-based Access Control [Thomas & Sandhu, 1997] Ponder [Damianou et al. , 2001] © 2003 GMU LIST 4

Problem Statement n n Traditional access control models are not adequate for today’s distributed, network-connected digital environment. No access control models available for DRM. Recently enhanced models are not comprehensive enough to resolve various shortcomings. Need for a unified model that can encompass traditional access control models, DRM and other enhanced access control models from recent literature © 2003 GMU LIST 5

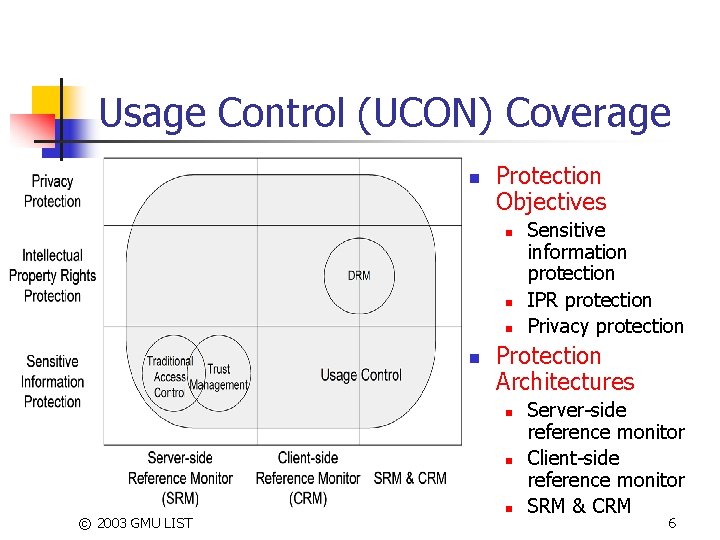
Usage Control (UCON) Coverage n Protection Objectives n n Protection Architectures n n © 2003 GMU LIST Sensitive information protection IPR protection Privacy protection n Server-side reference monitor Client-side reference monitor SRM & CRM 6

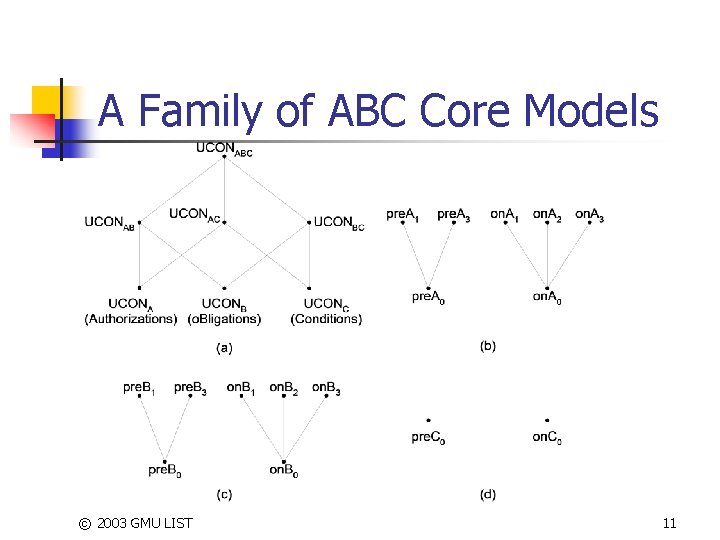
OM-AM layered Approach n ABC core models for UCON © 2003 GMU LIST 7

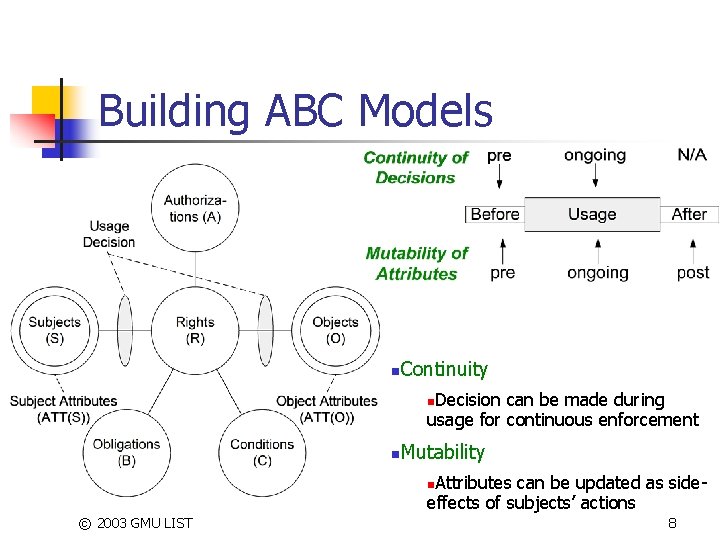
Building ABC Models n Continuity Decision can be made during usage for continuous enforcement n n Mutability Attributes can be updated as sideeffects of subjects’ actions n © 2003 GMU LIST 8

Examples n n n Long-distance phone (pre-authorization with post-update) Pre-paid phone card (ongoing-authorization with ongoing-update) Pay-per-view (pre-authorization with preupdates) Click Ad within every 30 minutes (ongoingobligation with ongoing-updates) Business Hour (pre-/ongoing-condition) © 2003 GMU LIST 9

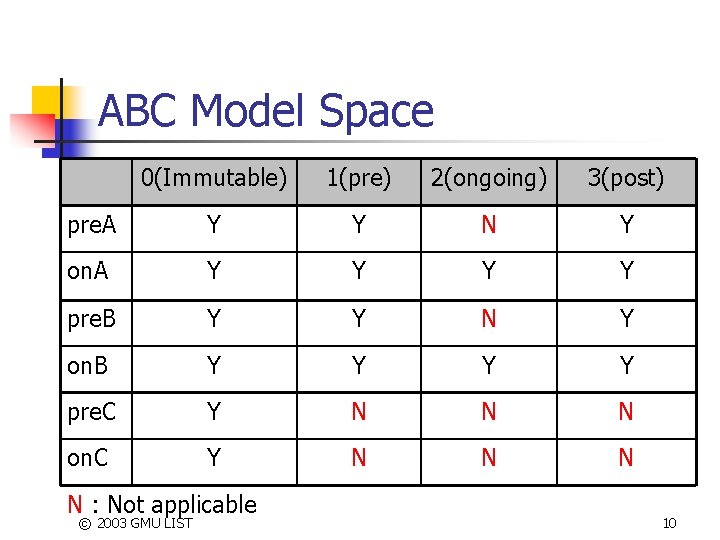
ABC Model Space 0(Immutable) 1(pre) 2(ongoing) 3(post) pre. A Y Y N Y on. A Y Y pre. B Y Y N Y on. B Y Y pre. C Y N N N on. C Y N N : Not applicable © 2003 GMU LIST 10

A Family of ABC Core Models © 2003 GMU LIST 11

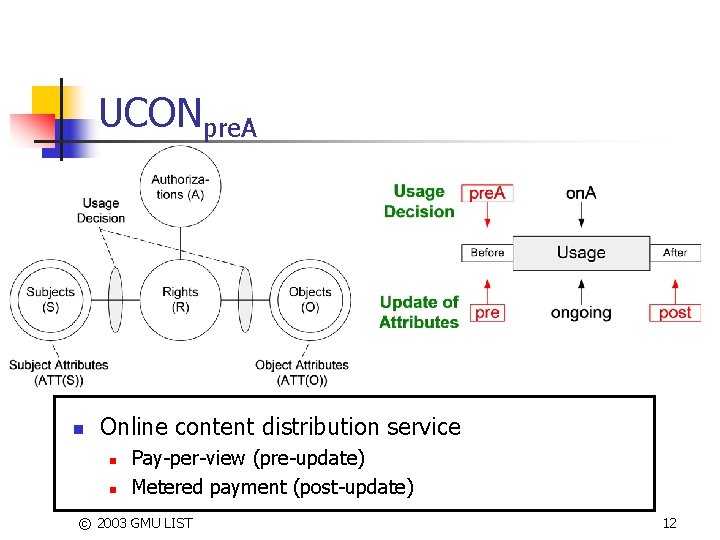
UCONpre. A n Online content distribution service n n Pay-per-view (pre-update) Metered payment (post-update) © 2003 GMU LIST 12

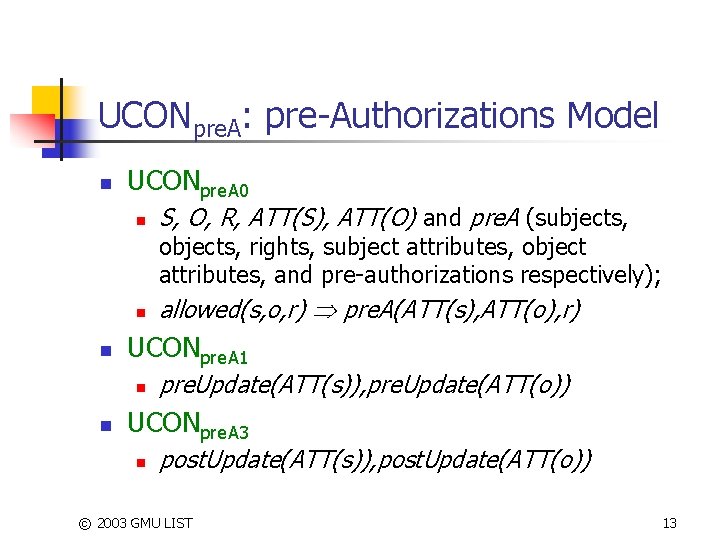
UCONpre. A: pre-Authorizations Model n UCONpre. A 0 n S, O, R, ATT(S), ATT(O) and pre. A (subjects, objects, rights, subject attributes, object attributes, and pre-authorizations respectively); n n UCONpre. A 1 n n allowed(s, o, r) pre. A(ATT(s), ATT(o), r) pre. Update(ATT(s)), pre. Update(ATT(o)) UCONpre. A 3 n post. Update(ATT(s)), post. Update(ATT(o)) © 2003 GMU LIST 13

UCONpre. A 0: MAC Example n L is a lattice of security labels with dominance relation n n n clearance: S L classification: O L ATT(S) = {clearance} ATT(O) = {classification} allowed(s, o, read) clearance(s) classification(o) allowed(s, o, write) clearance(s) classification(o) © 2003 GMU LIST 14

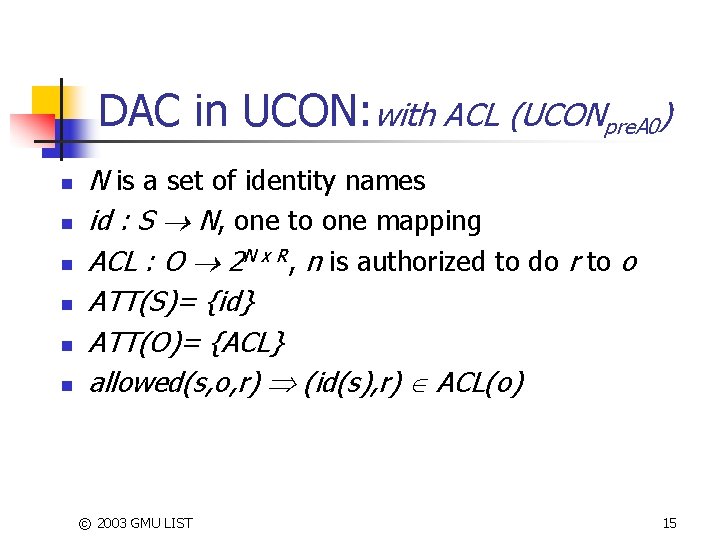
DAC in UCON: with ACL (UCONpre. A 0) n n n N is a set of identity names id : S N, one to one mapping ACL : O 2 N x R, n is authorized to do r to o ATT(S)= {id} ATT(O)= {ACL} allowed(s, o, r) (id(s), r) ACL(o) © 2003 GMU LIST 15

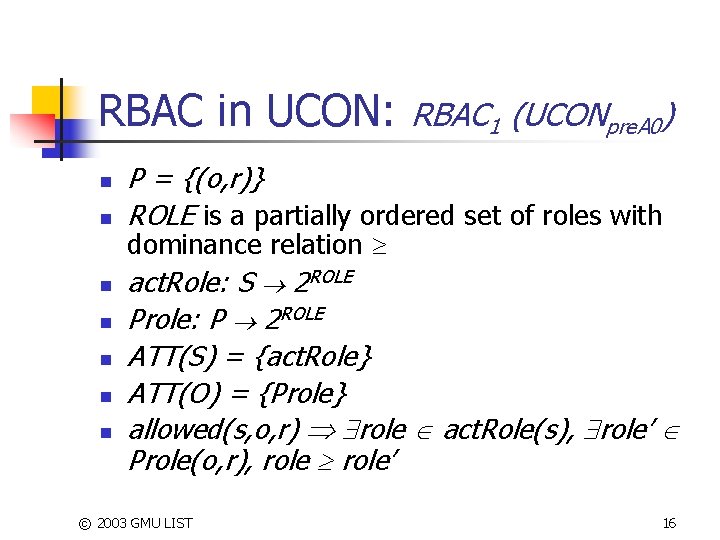
RBAC in UCON: n n n n RBAC 1 (UCONpre. A 0) P = {(o, r)} ROLE is a partially ordered set of roles with dominance relation act. Role: S 2 ROLE Prole: P 2 ROLE ATT(S) = {act. Role} ATT(O) = {Prole} allowed(s, o, r) role act. Role(s), role’ Prole(o, r), role’ © 2003 GMU LIST 16

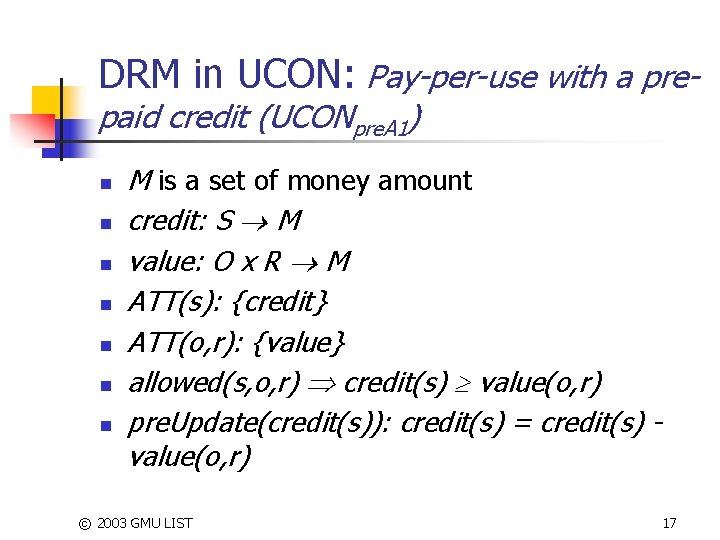
DRM in UCON: Pay-per-use with a prepaid credit (UCONpre. A 1) n n n n M is a set of money amount credit: S M value: O x R M ATT(s): {credit} ATT(o, r): {value} allowed(s, o, r) credit(s) value(o, r) pre. Update(credit(s)): credit(s) = credit(s) value(o, r) © 2003 GMU LIST 17

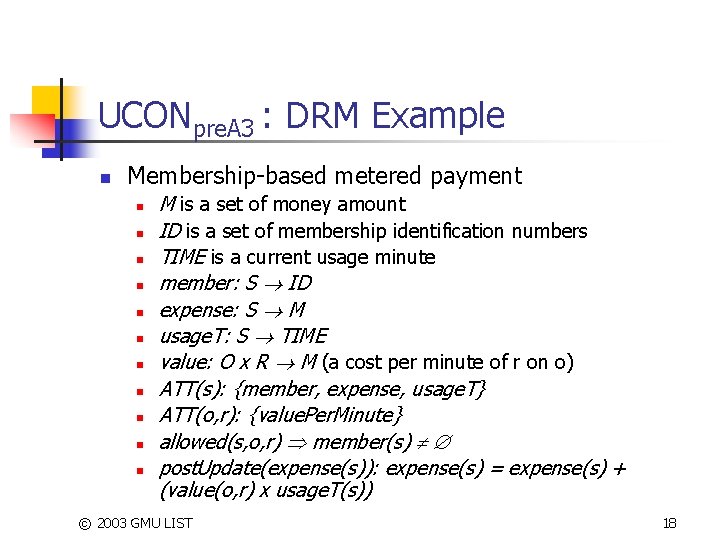
UCONpre. A 3 : DRM Example n Membership-based metered payment n n n M is a set of money amount ID is a set of membership identification numbers TIME is a current usage minute member: S ID expense: S M usage. T: S TIME value: O x R M (a cost per minute of r on o) ATT(s): {member, expense, usage. T} ATT(o, r): {value. Per. Minute} allowed(s, o, r) member(s) post. Update(expense(s)): expense(s) = expense(s) + (value(o, r) x usage. T(s)) © 2003 GMU LIST 18

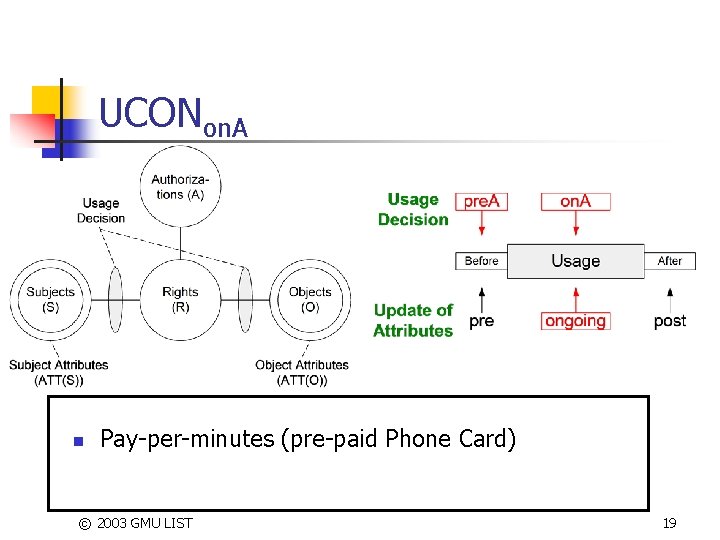
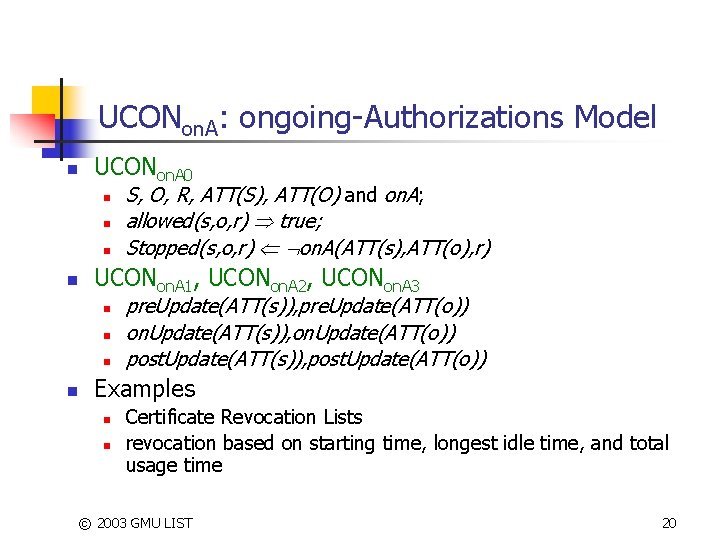
UCONon. A n Pay-per-minutes (pre-paid Phone Card) © 2003 GMU LIST 19

UCONon. A: ongoing-Authorizations Model n UCONon. A 0 n n UCONon. A 1, UCONon. A 2, UCONon. A 3 n n S, O, R, ATT(S), ATT(O) and on. A; allowed(s, o, r) true; Stopped(s, o, r) on. A(ATT(s), ATT(o), r) pre. Update(ATT(s)), pre. Update(ATT(o)) on. Update(ATT(s)), on. Update(ATT(o)) post. Update(ATT(s)), post. Update(ATT(o)) Examples n n Certificate Revocation Lists revocation based on starting time, longest idle time, and total usage time © 2003 GMU LIST 20

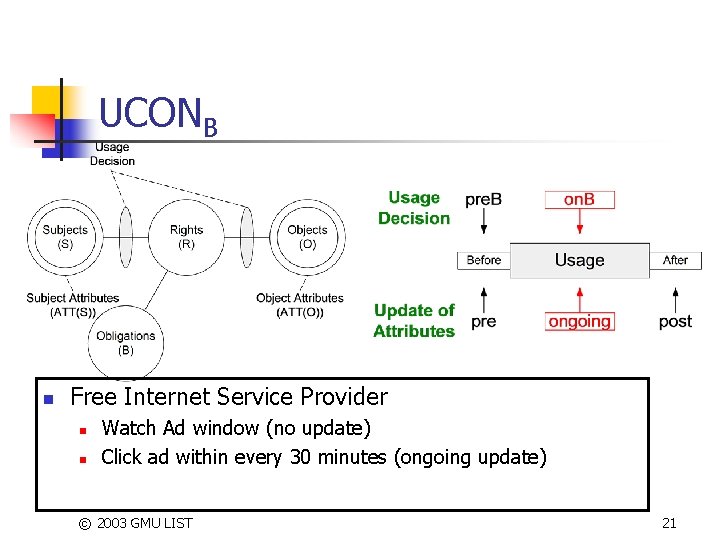
UCONB n Free Internet Service Provider n n Watch Ad window (no update) Click ad within every 30 minutes (ongoing update) © 2003 GMU LIST 21

UCONpre. B 0: pre-o. Bligations w/ no update n n n S, O, R, ATT(S), and ATT(O); OBS, OBO and OB (obligation subjects, obligation objects, and obligation actions, respectively); pre. B and pre. OBL (pre-obligations predicates and pre-obligation elements, respectively); pre. OBL OBS x OBO x OB; pre. Fulfilled: OBS x OBO x OB {true, false}; get. Pre. OBL: S x O x R 2 pre. OBL, a function to select pre-obligations for a requested usage; n pre. B(s, o, r) = (obs_i, obo_i, ob_i) get. Pre. OBL(s, o, r) pre. Fulfilled(obsi, oboi, obi); pre. B(s, o, r) = true by definition if get. Pre. OBL(s, o, r)= ; n allowed(s, o, r) n Example: License agreement for a whitepaper download n © 2003 GMU LIST pre. B(s, o, r). 22

UCONon. B 0: ongoing-o. Bligations w/ no update n n n S, O, R, ATT(S), ATT(O), OBS, OBO and OB; T, a set of time or event elements; on. B and on. OBL (on-obligations predicates and ongoing-obligation elements, respectively); on. OBL OBS x OBO x OB x T; on. Fulfilled: OBS x OBO x OB x T {true, false}; get. On. OBL: S x O x R 2 on. OBL, a function to select ongoingobligations for a requested usage; n on. B(s, o, r) = (obs_i, obo_i, ob_i, t_i) get. On. OBL(s, o, r) on. Fulfilled(obsi, oboi, obi , ti); on. B(s, o, r) = true by definition if get. On. OBL(s, o, r)= ; allowed(s, o, r) true; Stopped(s, o, r) on. B(s, o, r). n Example: Free ISP with mandatory ad window n n n © 2003 GMU LIST 23

UCONC n n Location check at the time of access request Accessible only during business hours © 2003 GMU LIST 24

UCONpre. C 0: pre-Condition model n S, O, R, ATT(S), and ATT(O); pre. CON (a set of pre-condition elements); pre. Con. Checked: pre. CON {true, false}; get. Pre. CON: S x O x R 2 pre. CON; pre. C(s, o, r) = pre. Con_i get. Pre. CON(s, o, r) pre. Con. Checked(pre. Coni); n allowed(s, o, r) n Example: location checks at the time of access requests n n © 2003 GMU LIST pre. C(s, o, r). 25

UCONon. C 0: ongoing-Condition model n S, O, R, ATT(S), and ATT(O); on. CON (a set of on-condition elements); on. Checked: on. CON {true, false}; get. On. CON: S x O x R 2 on. CON; on. C(s, o, r) = on. Con_i get. On. CON(s, o, r) on. Checked(on. Coni); allowed(s, o, r) true; Stopped(s, o, r) on. C(s, o, r) n Example: accessible during office hour n n n © 2003 GMU LIST 26

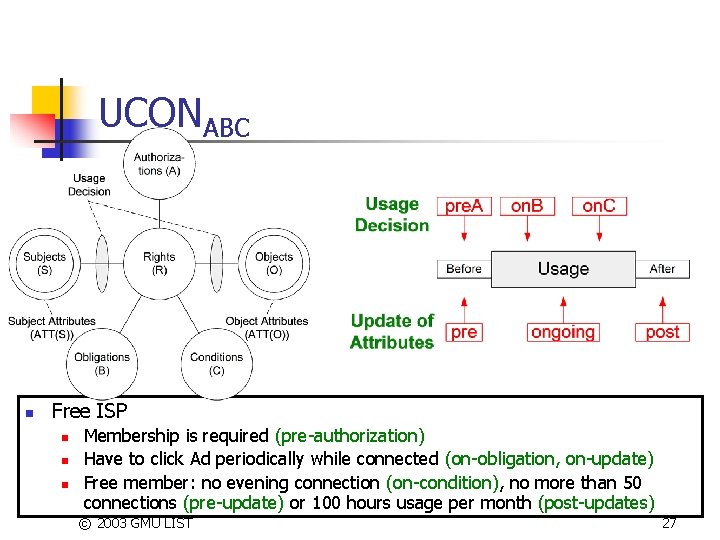
UCONABC n Free ISP n n n Membership is required (pre-authorization) Have to click Ad periodically while connected (on-obligation, on-update) Free member: no evening connection (on-condition), no more than 50 connections (pre-update) or 100 hours usage per month (post-updates) © 2003 GMU LIST 27

ABC Models © 2003 GMU LIST 28

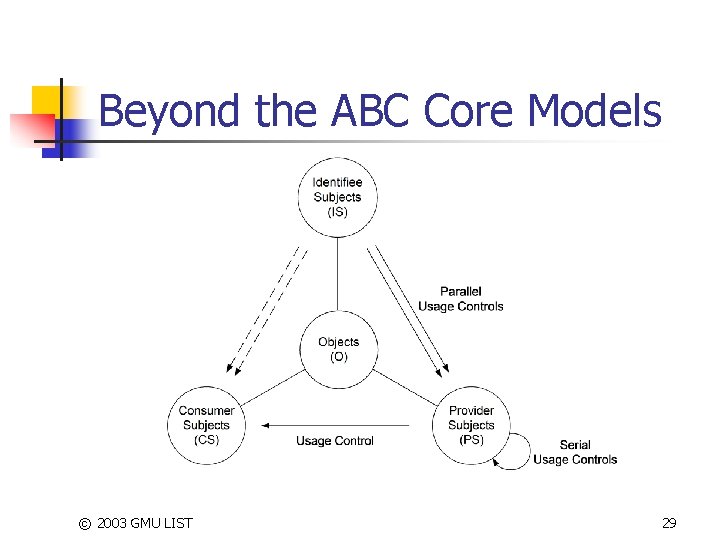
Beyond the ABC Core Models © 2003 GMU LIST 29

Conclusion n n Developed A family of ABC core models for Usage Control (UCON) to unify traditional access control models, DRM, and other modern enhanced models. ABC model integrates authorizations, obligations, conditions, as well as continuity and mutability properties. © 2003 GMU LIST 30

Future Research n Enhance the model n n Develop Architectures and Mechanisms n n UCON administration or management Detail of update procedure in ABC model Delegation of usage rights Payment-based architectures CRM and SRM Architectures for multi-organizations (B 2 B) UCON Engineering n n Analysis of policy Designing/modeling rules and Attributes © 2003 GMU LIST 31

Publications n n n Jaehong Park and Ravi Sandhu, “The ABC Core Model for Usage Control: Integrating Authorizations, o. Bligations, and Conditions” to appear on ACM Transactions on Information and System Security (TISSEC), 2004 Ravi Sandhu and Jaehong Park, “Usage Control: A vision for Next Generation Access Control” to appear on The Second International Workshop "Mathematical Methods, Models and Architectures for Computer Networks Security (MMM-ACNS), Sep. 2003. Jaehong Park and Ravi Sandhu, “Towards Usage Control Models: Beyond Traditional Access Control” In Proceedings of 7 th ACM Symposium on Access Control Models and Technologies, Jun. 2002 Jaehong Park and Ravi Sandhu, “Originator Control in Usage Control” In Proceedings of 3 rd International Workshop on Policies for Distributed Systems and Networks, pp. 60 -66, IEEE, Jun. 2002 Jaehong Park, Ravi Sandhu, and James Schifalacqua, “Security Architectures for Controlled Digital information Dissemination. ” In Proceedings of Annual Computer Security Applications Conference (ACSAC), pp. 224 -233, Dec. 2000 © 2003 GMU LIST 32