PALO ALTO NETWORKS NEXT GENERATION SECURITY PLATFORM FOR








- Slides: 15

PALO ALTO NETWORKS NEXT GENERATION SECURITY PLATFORM FOR FINANCIAL SERVICES Dharminder Debisarun, Cloud Security Lead 1 | © 2015, Palo Alto Networks. Confidential and Proprietary.

Agenda • Palo Alto Networks Corporate Overview • Financial Services Challenges and Landscape • Reference Blueprint • Act as a leader 2 | © 2015, Palo Alto Networks, Inc. Confidential and Proprietary.

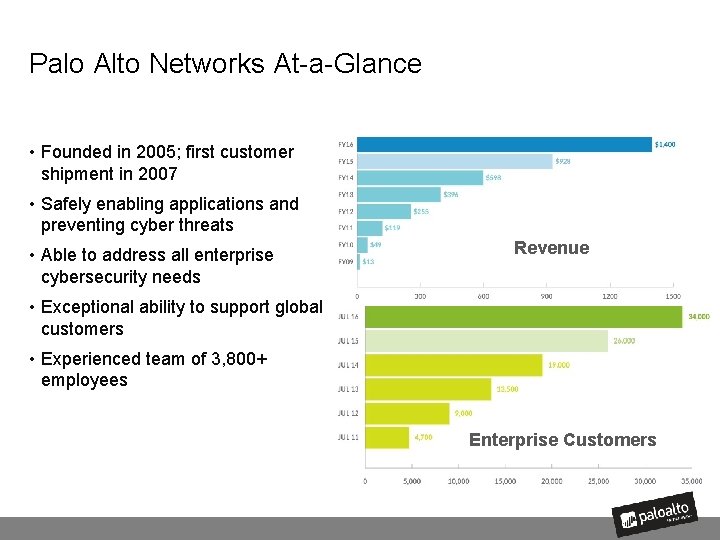
Palo Alto Networks At-a-Glance • Founded in 2005; first customer shipment in 2007 • Safely enabling applications and preventing cyber threats • Able to address all enterprise cybersecurity needs Revenue • Exceptional ability to support global customers • Experienced team of 3, 800+ employees Enterprise Customers 3 | © 2016, Palo Alto Networks. Confidential and Proprietary.

Business Challenges in Financial Services • Improve customer experience and increase revenues • • Generate structural cost savings • • • Business model transformations Global operating models for consistency Improve IT efficiency for competitive advantage Higher productivity, lower cost Regulatory Changes • • Process improvements and standardizations Data analytics and personalized interactions (key differentiator) Faster time-to-market for new products/services Increasing capital requirements EU Network Information Security (NIS) Directive EU General Data Protection Regulation (GDPR) Customer Behavior • Mobile/web engagements continue to grow 4 | © 2016, Palo Alto Networks. All Rights Reserved.

IT Priorities in Financial Services • Cost Optimization • • Operational Excellence • • Maintain uptime (availability, resiliency) Competitive Advantages • • • Consolidation (e. g. , data center, internal platforms, organizations) Retail bank branch reduction or efficiencies Automation Cross-selling Improved time-to-market Preserve brand (reputation) 5 | © 2016, Palo Alto Networks. All Rights Reserved.

Financial Services is Still a Target Among Top 3 Industries for Security Incidents Only behind Public and Entertainment Similar position in previous years Top Industry for Confirmed Data Loss Accounted for 35% across all industries Almost as many as next 4 industries combined 6 | © 2016, Palo Alto Networks. Confidential and Proprietary. Source: 2016 Verizon Data Breach Incident Report

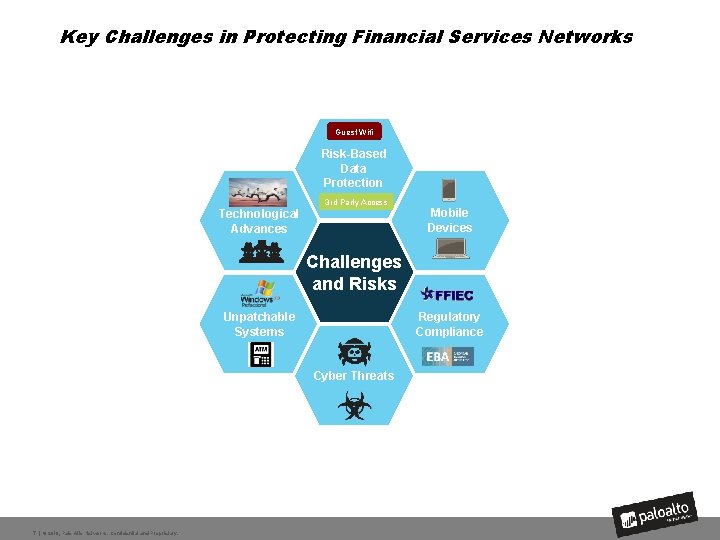
Key Challenges in Protecting Financial Services Networks Guest Wifi Risk-Based Data Protection 3 rd Party Access Technological Advances Mobile Devices Challenges and Risks Regulatory Compliance Unpatchable Systems Cyber Threats 7 | © 2016, Palo Alto Networks. Confidential and Proprietary.

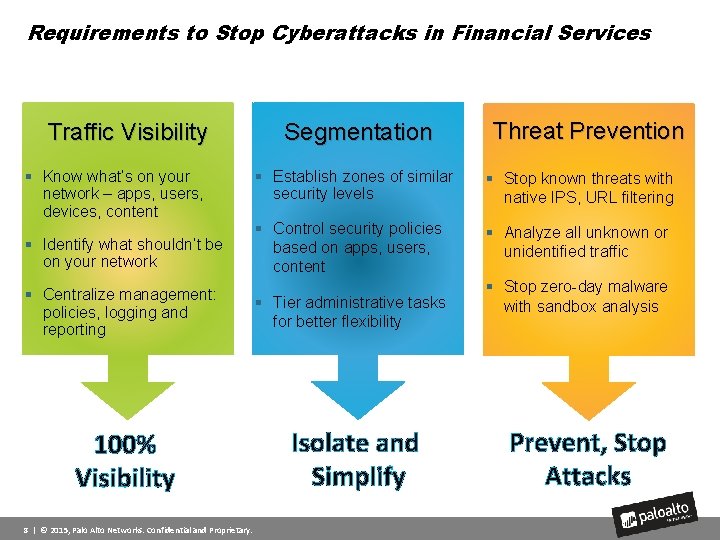
Requirements to Stop Cyberattacks in Financial Services Traffic Visibility § Know what’s on your network – apps, users, devices, content Segmentation Threat Prevention § Establish zones of similar security levels § Stop known threats with native IPS, URL filtering § Identify what shouldn’t be on your network § Control security policies based on apps, users, content § Analyze all unknown or unidentified traffic § Centralize management: policies, logging and reporting § Tier administrative tasks for better flexibility 100% Visibility Isolate and Simplify 8 | © 2015, Palo Alto Networks. Confidential and Proprietary. § Stop zero-day malware with sandbox analysis Prevent, Stop Attacks

Palo Alto Networks Next-Generation Security Platform Threat Intelligence Cloud § Gathers potential threats from network and endpoints § Analyzes and correlates threat intelligence § Disseminates threat intelligence to network and endpoints § Threat Prevention § Sandboxing (Wildfire) § URL Filtering § Mobile VPN (Global. Protect) § SAAS Protection (Aperture) TRAPS Next-Generation Network Security Advanced Endpoint Protection § Inspects all traffic, detects applications, users § Inspects all processes and files § Blocks known threats § Prevents both known & unknown exploits § Sends unknown to cloud § Integrates with cloud to prevent known & unknown malware

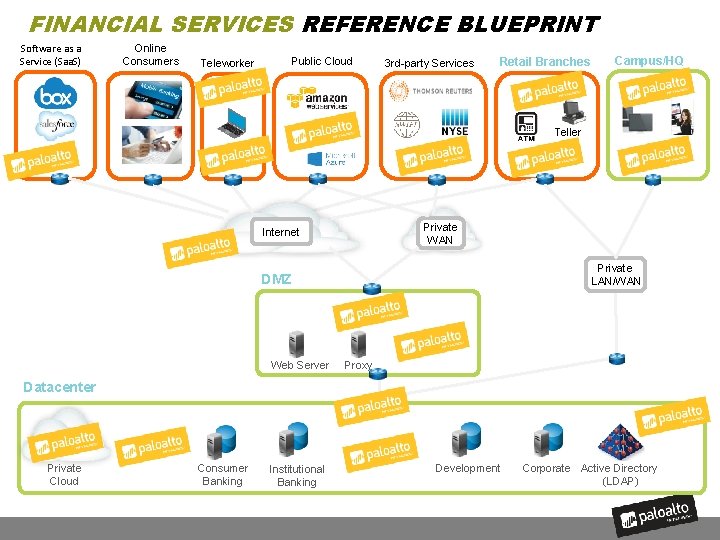
FINANCIAL SERVICES REFERENCE BLUEPRINT Software as a Service (Saa. S) Online Consumers Public Cloud Teleworker s 3 rd-party Services Retail Branches Campus/HQ Wi-Fi Teller Private WAN Internet Private LAN/WAN DMZ Web Server Proxy Datacenter Private Cloud Consumer Banking Institutional Banking Development Corporate Active Directory (LDAP)

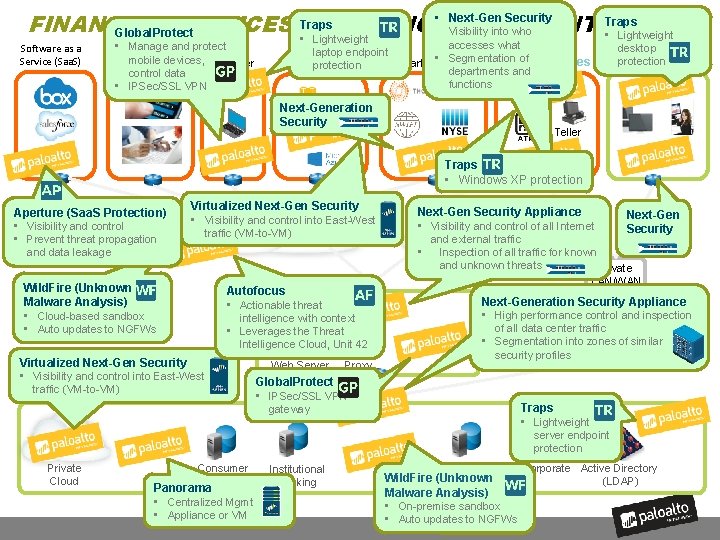
• Next-Gen Security Traps FINANCIAL SERVICES REFERENCE BLUEPRINT Visibility into who Global. Protect • Lightweight Software as a Service (Saa. S) accesses what laptop endpoint • Segmentation of Branches Public Cloud Retail 3 rd-party Services protection departments and functions • Manage Online and protect mobile devices, Teleworker Consumers control data s • IPSec/SSL VPN Next-Generation Security Traps • Lightweight desktop Campus/HQ protection Wi-Fi Teller Traps • Windows XP protection Aperture (Saa. S Protection) • Visibility and control • Prevent threat propagation Virtualized Next-Gen Security • Visibility and control into East-West Internet traffic (VM-to-VM) DMZ Autofocus • Actionable threat intelligence with context • Leverages the Threat Intelligence Cloud, Unit 42 Virtualized Next-Gen Security • Visibility and control into East-West Datacenter traffic (VM-to-VM) Web Server Next-Gen Security and external traffic WAN • Inspection of all traffic for known and unknown threats Private LAN/WAN and data leakage Wild. Fire (Unknown Malware Analysis) • Cloud-based sandbox • Auto updates to NGFWs Next-Gen Security Appliance • Private Visibility and control of all Internet Proxy Next-Generation Security Appliance • High performance control and inspection of all data center traffic • Segmentation into zones of similar security profiles Global. Protect • IPSec/SSL VPN Traps • Lightweight gateway server endpoint protection Private Cloud Consumer Banking Panorama • Centralized Mgmt • Appliance or VM Institutional Banking Development Wild. Fire (Unknown Malware Analysis) • On-premise sandbox • Auto updates to NGFWs Corporate Active Directory (LDAP)

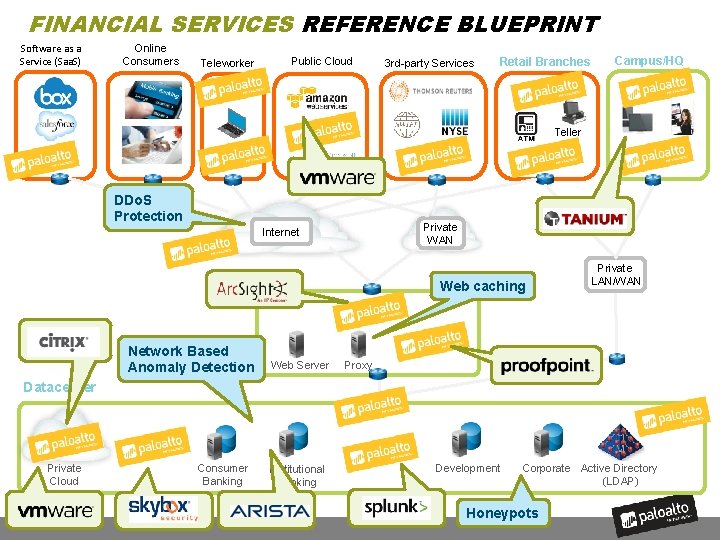
FINANCIAL SERVICES REFERENCE BLUEPRINT Software as a Service (Saa. S) Online Consumers Public Cloud Teleworker s 3 rd-party Services Retail Branches Campus/HQ Wi-Fi Teller DDo. S Protection Private WAN Internet DMZ Network Based Anomaly Detection Web Server Web caching Private LAN/WAN Proxy Datacenter Private Cloud Consumer Banking Institutional Banking Development Corporate Active Directory (LDAP) Honeypots

Act as a leader 13 | © 2015, Palo Alto Networks. Confidential and Proprietary.

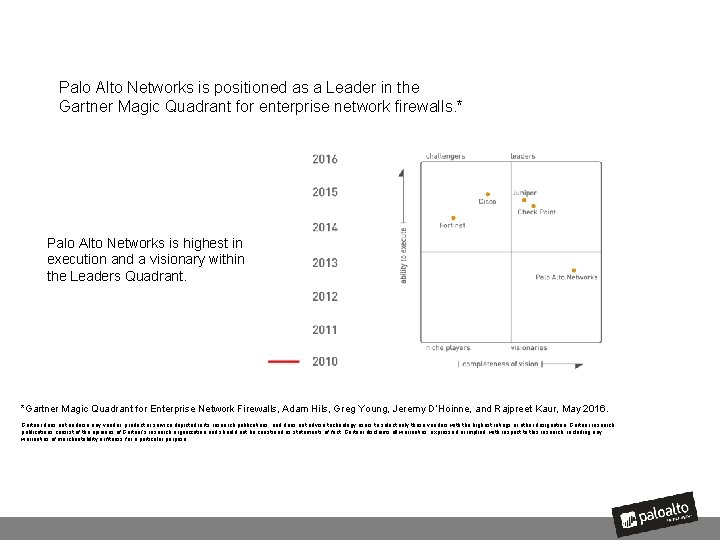
Palo Alto Networks is positioned as a Leader in the Gartner Magic Quadrant for enterprise network firewalls. * Palo Alto Networks is highest in execution and a visionary within the Leaders Quadrant. *Gartner Magic Quadrant for Enterprise Network Firewalls, Adam Hils, Greg Young, Jeremy D’Hoinne, and Rajpreet Kaur, May 2016. Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner's research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose. 14 | © 2016, Palo Alto Networks. Confidential and Proprietary.

15 | © 2015, Palo Alto Networks. Confidential and Proprietary.