The Id M Identity Conundrum Strategies in identity




























- Slides: 35

The (Id. M) Identity Conundrum Strategies in identity management

What is identity management? Important delineation : Ø Two groups of entities Ø Internal staff Ø Customers, business partners Ø Different challenges, different deliverables, may need different solutions

What is identity management? Identity management is the ability to define and control the security characteristics and credentials of : Ø many users Ø on many systems Ø spanning a variety of different roles Ø inside and outside the organisation Ø while accessing content, applications, and services Ø in a manner which is sensitive to the context of the interaction

What is identity management? So identity is the abstract representation that links a real person to their capabilities in an IT system The process of identity management requires a system which: Ø Ø distinguishes a person defines them in terms of their security personas and specifies their access rights within the various contexts which characterise their interaction with the organisation

What is identity management? But isn’t that just security administration? Ø True to a degree, BUT Ø Formerly one person, one account, one system Ø NOW, one person, 20 accounts, 100 systems Ø An example

What is identity management? Example Ø Mid-Size corporation Ø 5, 000 staff Ø 220, 000 userids Ø 374 security domains Ø With this level of complexity it’s not “just” security administration

What is identity management? So Identity Management is actually the integration of products such as directories, single sign-on, security services applications and provisioning applications into a unified framework for managing user information and access. It’s about convergence of the multitude of points of authentication, authorisation and administration to provide a more coherent view and management platform for security.

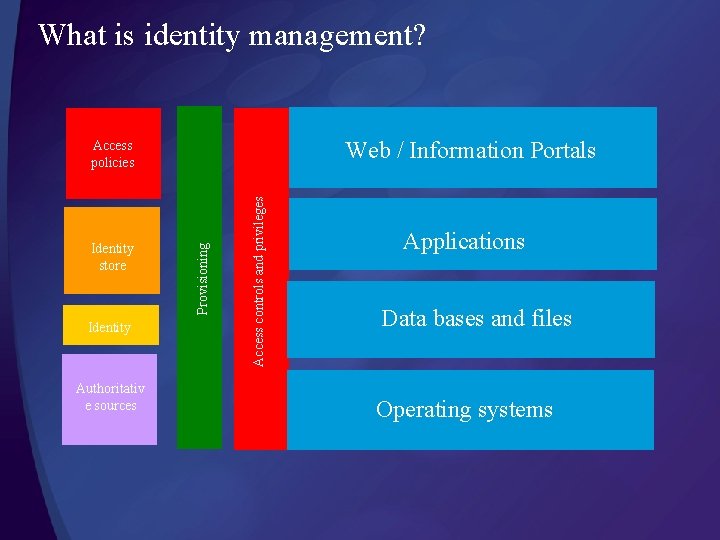
An architectural view of Identity Management

What is identity management? Web / Information Portals Identity Authoritativ e sources Access controls and privileges Identity store Provisioning Access policies Applications Data bases and files Operating systems

Drivers to Identity Management (internal staff) • Increasing complexity (servers, operating systems, data bases, applications) • Increasing administration costs • Declining security quality = rising security risk • Declining quality of service

Drivers to Identity Management (customers) • Need to do business regardless of location • Need to identify a web customer as the same customer using IVR or counter services • Customer single web sign-on in complex server/database/application environment • Need unified authentication for web portals • Access rights change with the business context • Personalise web content based on identity and current activity • Interface to CRM applications • Delegated administration for business areas, partners

What value can Identity Management create? • Identity Management is the philosophy of a centralised security architecture using an identity centric approach • Single user profile for user identification and marketing purposes • Stops proliferation of passwords • Increased customer and employee satisfaction • Faster deployment of new applications • Cost reduction through centralised user management, user self service and process optimisation • Link between business processes, workflow and technology • Centralised point of control for security and audit processes.

Benefits from Identity Management Cost reduction – Decreased maintenance of security on a business unit level – Staff and customer access available more quickly – Internal costs reduced through cross platform centralised password management and synchronisation – External help desk costs reduced by improved password management – Reduction in development costs for web applications – no need to rebuild a bespoke security solution

Benefits from Identity Management Revenue – Move complete value chains to the digital world – Provide a mechanism to quickly and efficiently migrate users and applications from acquisitions – Staff productive more quickly – Offer 24/7 self service – Competitive advantage, strategic positioning and corporate brand/image

Benefits from Identity Management Risk reduction § § § § Only appropriate users have access Risk of obsolete user accounts reduced Change of position results in change of permissions Ability to evaluate regulatory compliance Ability to audit and track user accounts. Ability to automatically lock out users Central point of control for security and audit processes. Single view of user’s access

Competing technologies

Competing technologies • We now look at security infrastructure solutions. ERP and CRM feed into Identity Management, but are out of scope for this discussion Custom applications – Directory services – Web Access Control (aka Extranet Access Management) – Provisioning –

Custom applications • While not high on most people’s agenda, building custom applications for IM is possible and has been done • Enables very specific requirements to be built in – Inherently expensive to build and maintain – Requires deep technical skills in some of the target platforms, not normally held by developers Usually one way – does not pick up manual changes Sits on critical path for technology upgrades (e. g. new versions of operating system or data base) Most very large organisations have put in a bespoke provisioning application of some sort • Example : large bank built online access control manager 15 years ago Becomes too difficult for complex technology mix – –

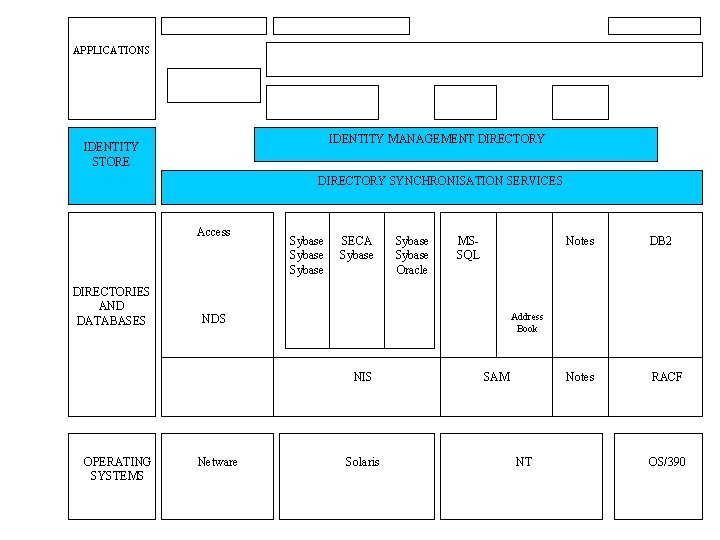
Directory services • Directory Services terminology is ambiguous, and not used consistently • A “directory” is a specialised data base used for repetitive high speed access to relatively static data. • “Directory Services” is a blanket term used to describe the use of directories to service this data to applications. Security credentials are frequently provided to applications in this way. • Metadirectory” is a term used to describe a directory which is comprised of data synchronised from other directories. • It is very important to recognise that many people do not understand these concepts, and use the term “Directory Services” or “metadirectory” when they simply mean the desire to use a directory instead of a data base.

Directory services • A directory services solution comprises a set of tools and processes • A core directory such as Active Directory, Novell e. Directory, i. Planet • Directory synchronisation tool such as Dir. XML, Sun ONE Meta. Directory, Active Directory Connector • Connector to ERP or CRM • Object and property mapping tools (probably XML) • Optionally front-end self service directory enabled applications

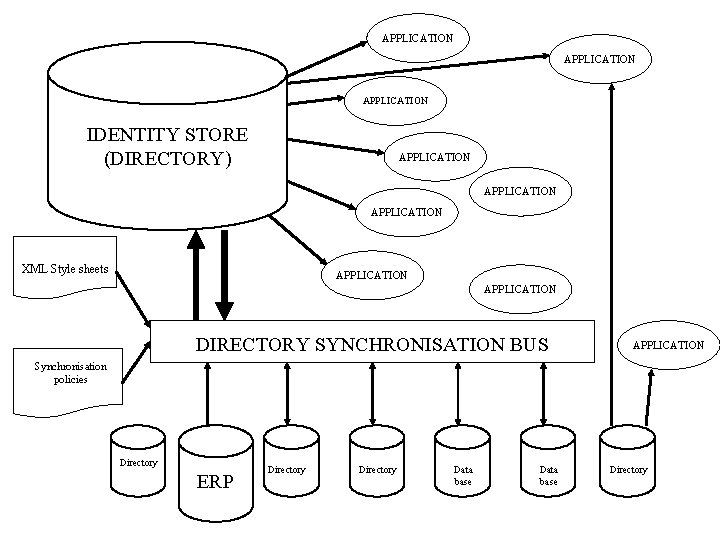
APPLICATIONS IDENTITY MANAGEMENT DIRECTORY IDENTITY STORE DIRECTORY SYNCHRONISATION SERVICES Access DIRECTORIES AND DATABASES Sybase SECA Sybase MSSQL Netware Notes DB 2 Notes RACF Address Book NDS NIS OPERATING SYSTEMS Sybase Oracle Solaris SAM NT OS/390

APPLICATION IDENTITY STORE (DIRECTORY) APPLICATION XML Style sheets APPLICATION DIRECTORY SYNCHRONISATION BUS APPLICATION Synchronisation policies Directory ERP Directory Data base Directory

Directory Services Authentication § User profiles can be stored in a manner which can be accessed by applications to authenticate the user. The term describing it is “Directory Enabled Application”, and the protocol for accessing the directory is LDAP. Access control § If the directory is the native security mechanism for the operating system it controls access to resources (e. g. e. Directory on Netware) § Otherwise there is no active access control. Passive access control can be achieved by directory enabling applications § Group memberships and custom objects can help § CAVEAT! Passive security depends on developers implementing security correctly in the application.

Directory Services Provisioning § Directories can be updated as a result of changes in other directories, or changes in the HR system § Key technique is directory synchronisation using products like Dir. XML § Synchronisation tool maps object types and properties to their equivalent in the target system (e. g. userid=logonid=UID, Last Name=Surname=Name) § Also allows scripting to achieve non-directory functions (e. g. copying files, archiving), or scheduling subsequent events

Extranet Access Management Web applications bring new challenges. There are numerous data sources, and new resource types not protected by traditional processing platforms § Native operating system security can’t protect pages, URLs, Objects, methods, applets, servlets § Products include Oblix, Tivoli Identity Manager, RSA Clear. Trust, Netegrity Site. Minder. Many more. § Provides a callable security service with support for new resource types, and custom objects § Primarily for browser applications, but some can be called by traditional applications § Particularly relevant for JAVA – JAAS and J 2 EE § EAMs often use a directory as their identity store

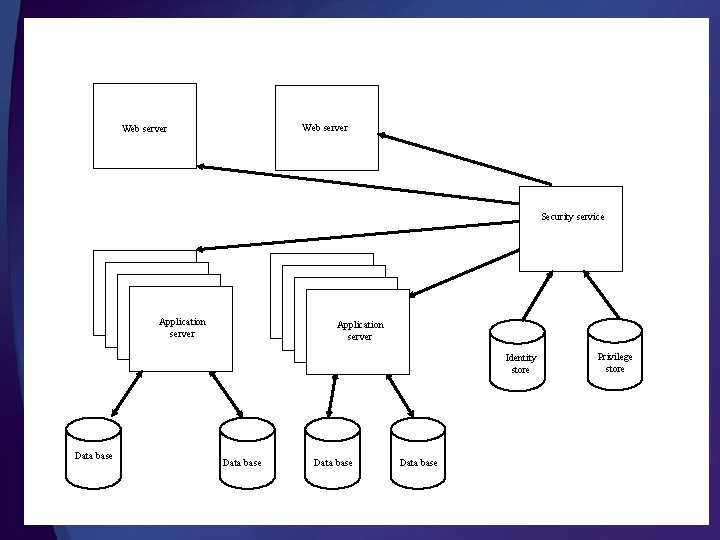
Security service Identity store Browser Web server Application server Data base Operating systems

Web server Security service Application server Application server Identity store Data base Privilege store

Extranet access manager Authentication § User profiles and passwords are stored in the EAM’s identity store and accessed via the EAM’s API. Typically an encrypted cookie is created to provide single signon during the period of interaction. Access control § § Many different ways to store permissions Typically defined by group membership Can be a simple ACL for a resource Some products allow business logic to be included in the security credentials (e. g. allow access if account balance > $100, 000) § Some products have active security for certain resource types (e. g. page, method). Passive access control always possible by calling security from the application. Can be called from legacy apps. § Group memberships and custom objects can help § CAVEAT! Passive security depends on developers implementing security correctly in the application.

Extranet access manager Provisioning § Not typically used as a provisioning service. However, can be linked to CRM feed for automatic account creation § Some provisioning products can link into some EAMs (must be purpose written interface) § Provisioning can be direct to the identity/privilege stores via say LDAP

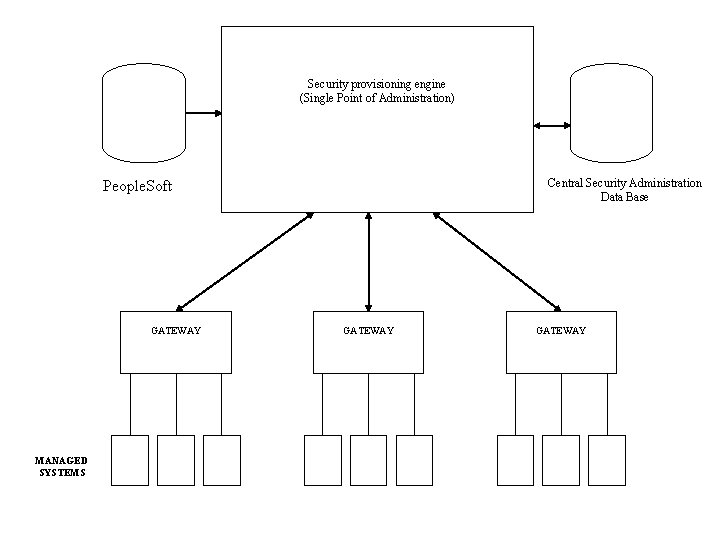
Security provisioning Proliferation of servers, accounts and passwords is making traditional security administration practices ineffective. There are pure plays provisioning products on the market § New users may need 10 or more accounts provided by several different administrators § Great scope for error (wrong access) and delay § Security administration costs rising because growing infrastructure complexity dramatically increases the number of security admin tasks § Provisioning products automate standard security tasks so they can be carried out without a security administrator’s intervention § Examples include BMC Control-SA, Access 360 (now Tivoli Access Manager), Waveset Provisioning Manager, CA e. Trust. Others

Access policies Authoritativ e sources Access controls and privileges Identity Provisioning Identity store Portals Applications Data bases and files Operating systems

Security provisioning engine (Single Point of Administration) Central Security Administration Data Base People. Soft GATEWAY MANAGED SYSTEMS GATEWAY

Provisioning Authentication § NOT interactive security manager § Provisioning solutions play no direct role in authentication § Can facilitate password synchronisation Access control § NOT interactive security manager § Puts access control settings in place to facilitate access to target § Can perform complex tasks with some intelligent rule processing facilitated by scripting § Can implement role based access control, so complex combinations of access can be assigned to a user based on their position, or specified function within work place (e. g. teller, help desk)

Provisioning § § § Replicates local security credentials in a central repository Changes to the repository are executed in the managed domain Changes made in managed domain also applied to repository Every person added to the role will get correct access Deleting the central entity deletes all associated accounts Needs workflow to achieve maximum gains and include online authorisation of requests § Not a panacea § Expect to automate 30 -50% of access types § However only limited by your commitment and resources

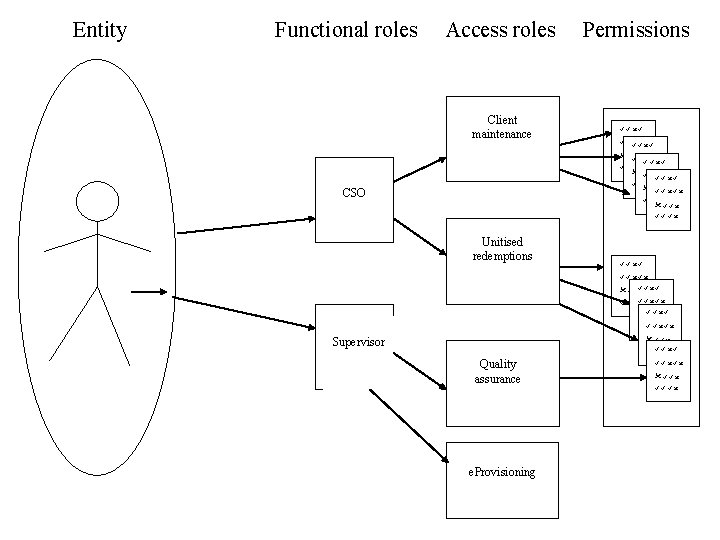
Entity Functional roles Access roles Permissions Client maintenance CSO Unitised redemptions Supervisor Quality assurance e. Provisioning
 Explain mario cuomo's conundrum
Explain mario cuomo's conundrum Countdown conundrum examples
Countdown conundrum examples Kovac's conundrum
Kovac's conundrum Identity mapping activity
Identity mapping activity Khi nào hổ con có thể sống độc lập
Khi nào hổ con có thể sống độc lập Diễn thế sinh thái là
Diễn thế sinh thái là Thế nào là hệ số cao nhất
Thế nào là hệ số cao nhất Vẽ hình chiếu vuông góc của vật thể sau
Vẽ hình chiếu vuông góc của vật thể sau 101012 bằng
101012 bằng Lời thề hippocrates
Lời thề hippocrates Vẽ hình chiếu đứng bằng cạnh của vật thể
Vẽ hình chiếu đứng bằng cạnh của vật thể Chụp phim tư thế worms-breton
Chụp phim tư thế worms-breton đại từ thay thế
đại từ thay thế Quá trình desamine hóa có thể tạo ra
Quá trình desamine hóa có thể tạo ra Khi nào hổ mẹ dạy hổ con săn mồi
Khi nào hổ mẹ dạy hổ con săn mồi Thế nào là mạng điện lắp đặt kiểu nổi
Thế nào là mạng điện lắp đặt kiểu nổi Các châu lục và đại dương trên thế giới
Các châu lục và đại dương trên thế giới Dạng đột biến một nhiễm là
Dạng đột biến một nhiễm là Bổ thể
Bổ thể Biện pháp chống mỏi cơ
Biện pháp chống mỏi cơ Phản ứng thế ankan
Phản ứng thế ankan Thiếu nhi thế giới liên hoan
Thiếu nhi thế giới liên hoan Vẽ hình chiếu vuông góc của vật thể sau
Vẽ hình chiếu vuông góc của vật thể sau Hát lên người ơi
Hát lên người ơi điện thế nghỉ
điện thế nghỉ Một số thể thơ truyền thống
Một số thể thơ truyền thống Trời xanh đây là của chúng ta thể thơ
Trời xanh đây là của chúng ta thể thơ Sơ đồ cơ thể người
Sơ đồ cơ thể người Công của trọng lực
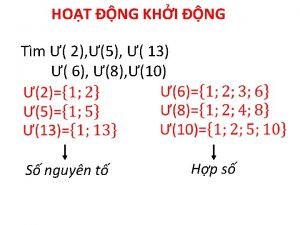
Công của trọng lực Số nguyên tố là gì
Số nguyên tố là gì Tỉ lệ cơ thể trẻ em
Tỉ lệ cơ thể trẻ em đặc điểm cơ thể của người tối cổ
đặc điểm cơ thể của người tối cổ Các châu lục và đại dương trên thế giới
Các châu lục và đại dương trên thế giới ưu thế lai là gì
ưu thế lai là gì Môn thể thao bắt đầu bằng chữ đua
Môn thể thao bắt đầu bằng chữ đua