PCL A Logic for Security Protocols Anupam Datta



![Why prove security? Examples of protocol flaws • IKE [Meadows; 1999] – Reflection attack; Why prove security? Examples of protocol flaws • IKE [Meadows; 1999] – Reflection attack;](https://slidetodoc.com/presentation_image_h2/7b42c895ce7c28350b48b750590ca09a/image-5.jpg)






![Logical assertions Modal operator • [ actions ] P - if holds and P Logical assertions Modal operator • [ actions ] P - if holds and P](https://slidetodoc.com/presentation_image_h2/7b42c895ce7c28350b48b750590ca09a/image-22.jpg)

![Security Properties Authentication for Initiator CR | true [ Init. CR(A, B) ] A Security Properties Authentication for Initiator CR | true [ Init. CR(A, B) ] A](https://slidetodoc.com/presentation_image_h2/7b42c895ce7c28350b48b750590ca09a/image-25.jpg)

![Sample axioms about actions New data • true [ new x ]P Has(P, x) Sample axioms about actions New data • true [ new x ]P Has(P, x)](https://slidetodoc.com/presentation_image_h2/7b42c895ce7c28350b48b750590ca09a/image-27.jpg)

![Sample inference rules First-order logic rules Generic rules [ actions ]P Sample inference rules First-order logic rules Generic rules [ actions ]P](https://slidetodoc.com/presentation_image_h2/7b42c895ce7c28350b48b750590ca09a/image-30.jpg)











![Diffie-Hellman: Property Formula true [ new a ] A Fresh(A, ga) Diffie-Hellman property: Can Diffie-Hellman: Property Formula true [ new a ] A Fresh(A, ga) Diffie-Hellman property: Can](https://slidetodoc.com/presentation_image_h2/7b42c895ce7c28350b48b750590ca09a/image-52.jpg)
![Challenge Response: Property Modal form: [ actions ]P • precondition: Fresh(A, m) • actions: Challenge Response: Property Modal form: [ actions ]P • precondition: Fresh(A, m) • actions:](https://slidetodoc.com/presentation_image_h2/7b42c895ce7c28350b48b750590ca09a/image-53.jpg)
![Composition Rules Invariant weakening rule |- […]P ’ |- […]P Sequential Composition |- [ Composition Rules Invariant weakening rule |- […]P ’ |- […]P Sequential Composition |- [](https://slidetodoc.com/presentation_image_h2/7b42c895ce7c28350b48b750590ca09a/image-56.jpg)
![802. 11 i Proof Structure Step 1. i, j |- θi [Pi]X i Separate 802. 11 i Proof Structure Step 1. i, j |- θi [Pi]X i Separate](https://slidetodoc.com/presentation_image_h2/7b42c895ce7c28350b48b750590ca09a/image-59.jpg)


![Two worlds Symbolic model [NS 78, DY 84, …] Complexity-theoretic model [GM 84, …] Two worlds Symbolic model [NS 78, DY 84, …] Complexity-theoretic model [GM 84, …]](https://slidetodoc.com/presentation_image_h2/7b42c895ce7c28350b48b750590ca09a/image-62.jpg)




![Inductive Semantics [[ 1 2]] (T, D, ) = [[ 1]] (T, D, ) Inductive Semantics [[ 1 2]] (T, D, ) = [[ 1]] (T, D, )](https://slidetodoc.com/presentation_image_h2/7b42c895ce7c28350b48b750590ca09a/image-72.jpg)


- Slides: 76

PCL: A Logic for Security Protocols Anupam Datta Stanford University Secure Software Systems, CMU October 3, 5, 2005

Computer Security Cryptography • Encryption, signatures, cryptographic hash, … Security mechanisms • Access control policy • Network protocols Implementation • Cryptographic library • Code implementing mechanisms – Reference monitor and TCB – Protocol • Runs under OS, uses program library, network protocol stack Analyze protocols, assuming crypto, implementation, OS correct

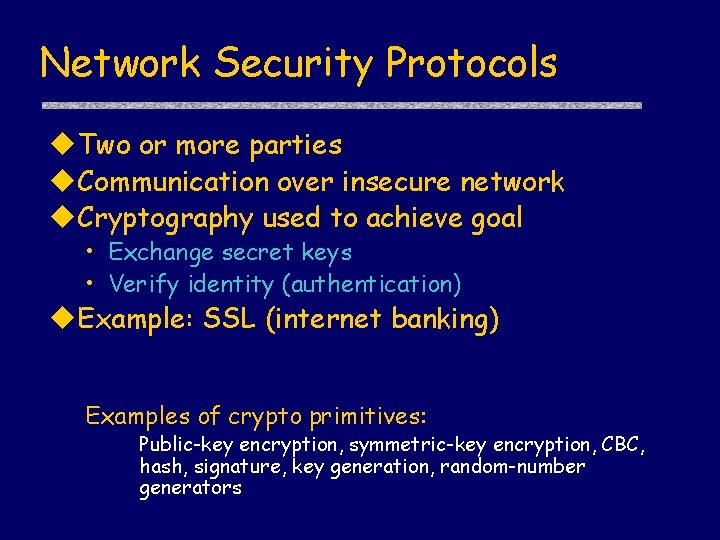
Network Security Protocols Two or more parties Communication over insecure network Cryptography used to achieve goal • Exchange secret keys • Verify identity (authentication) Example: SSL (internet banking) Examples of crypto primitives: Public-key encryption, symmetric-key encryption, CBC, hash, signature, key generation, random-number generators

This lecture is about… Network security protocols • Internet Engineering Task Force (IETF) Standards – – – SSL/TLS - web authentication IPSec - corporate VPNs Mobile IPv 6 – routing security Kerberos - network authentication GDOI – secure group communication • IEEE Standards Working Groups – 802. 11 i - wireless LAN security – 802. 16 e – wireless MAN security And methods for their security analysis • Security proof in some model; or • Identify attacks
![Why prove security Examples of protocol flaws IKE Meadows 1999 Reflection attack Why prove security? Examples of protocol flaws • IKE [Meadows; 1999] – Reflection attack;](https://slidetodoc.com/presentation_image_h2/7b42c895ce7c28350b48b750590ca09a/image-5.jpg)
Why prove security? Examples of protocol flaws • IKE [Meadows; 1999] – Reflection attack; fix adopted by IETF WG • IEEE 802. 11 i [He, Mitchell; 2004] – Do. S attack; fix adopted by IEEE WG • GDOI [Meadows, Pavlovic; 2004] – Composition attack; fix adopted by IETF WG • Kerberos V 5 [Scedrov et al; 2005] – Identity misbinding attack; fix adopted by IETF WG

Security Analysis Model system Model adversary Identify security properties See if properties preserved under attack Result • No “absolute security” • Security means: under given assumptions about system, no attack of a certain form will destroy specified properties.

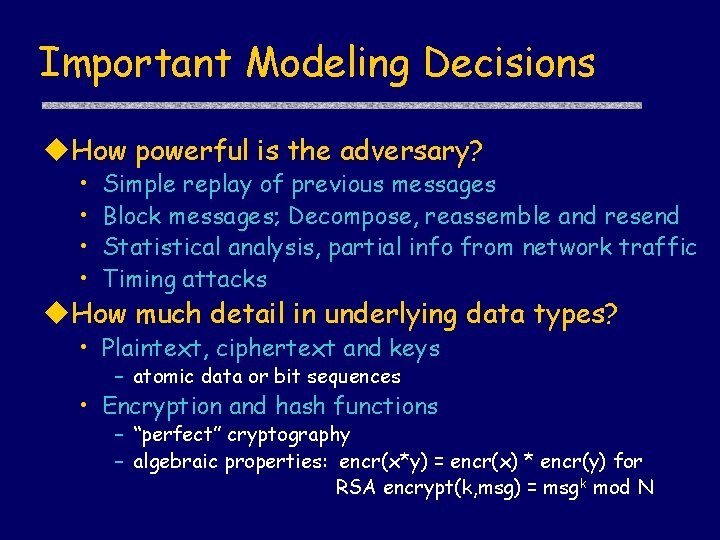
Important Modeling Decisions How powerful is the adversary? • • Simple replay of previous messages Block messages; Decompose, reassemble and resend Statistical analysis, partial info from network traffic Timing attacks How much detail in underlying data types? • Plaintext, ciphertext and keys – atomic data or bit sequences • Encryption and hash functions – “perfect” cryptography – algebraic properties: encr(x*y) = encr(x) * encr(y) for RSA encrypt(k, msg) = msg k mod N

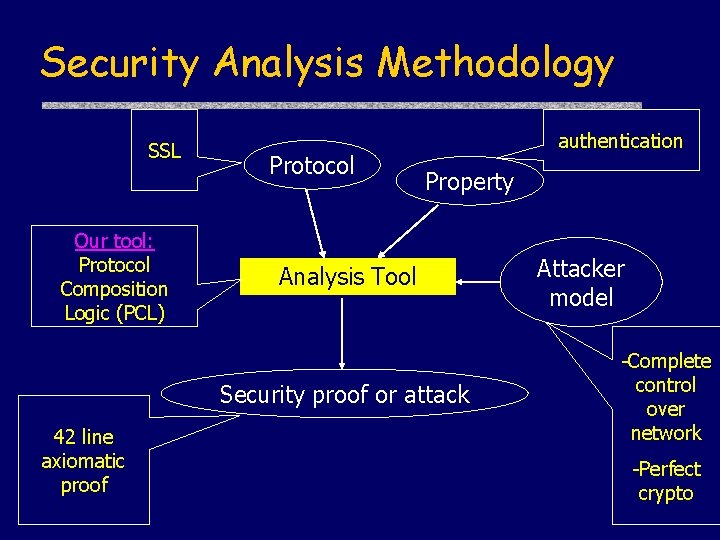
Security Analysis Methodology SSL Our tool: Protocol Composition Logic (PCL) Protocol authentication Property Analysis Tool Security proof or attack 42 line axiomatic proof Attacker model -Complete control over network -Perfect crypto

Resources: Protocols & Tools IETF Security Area http: //www. ietf. org/html. charters/wg-dir. html IEEE Security Working Groups http: //grouper. ieee. org/groups/802/11/ Stanford CS 259: Security Analysis of Network Protocols http: //www. stanford. edu/class/cs 259/ Will focus today on one tool: Protocol Composition Logic (PCL)

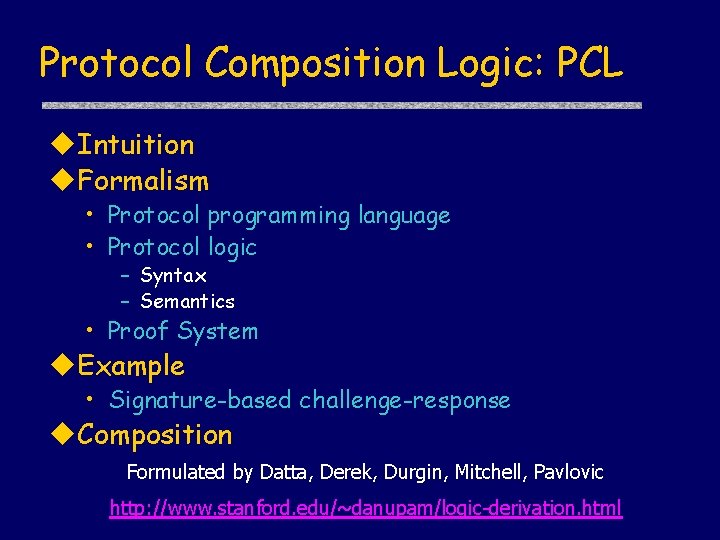
Protocol Composition Logic: PCL Intuition Formalism • Protocol programming language • Protocol logic – Syntax – Semantics • Proof System Example • Signature-based challenge-response Composition Formulated by Datta, Derek, Durgin, Mitchell, Pavlovic http: //www. stanford. edu/~danupam/logic-derivation. html

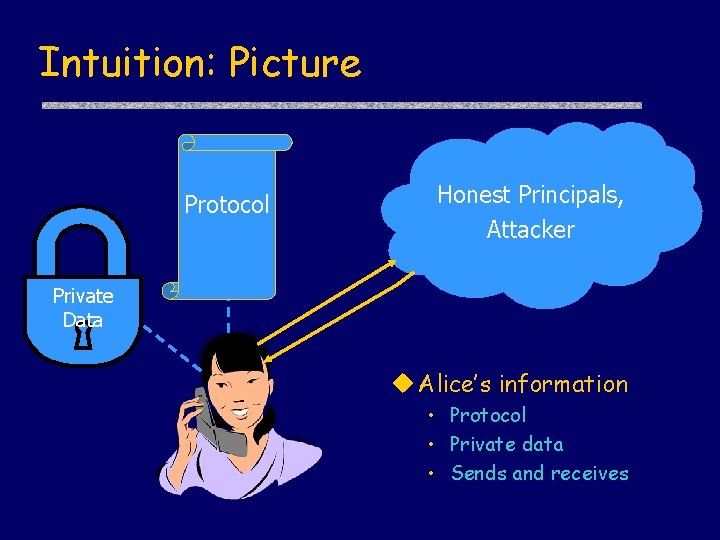
Intuition Reason about local information • • I chose a new number I sent it out encrypted I received it decrypted Therefore: someone decrypted it Incorporate knowledge about protocol • Protocol: Server only sends m if it received m’ • If server not corrupt and I receive m signed by server, then server received m’

Intuition: Picture Protocol Honest Principals, Attacker Private Data Alice’s information • Protocol • Private data • Sends and receives

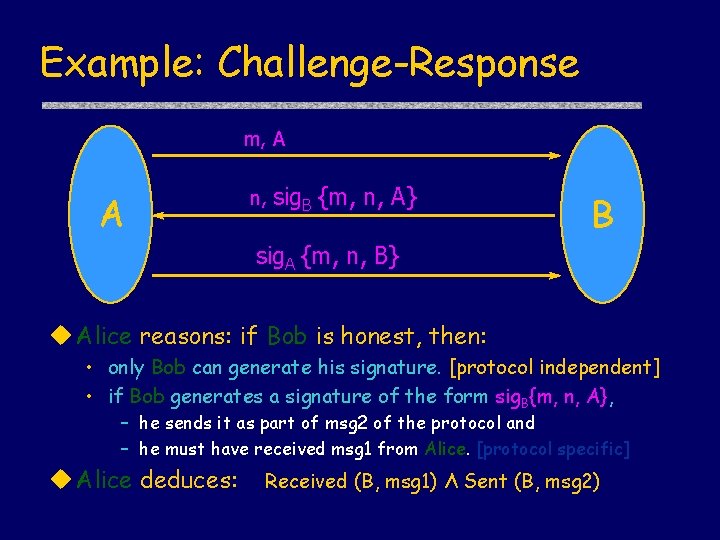
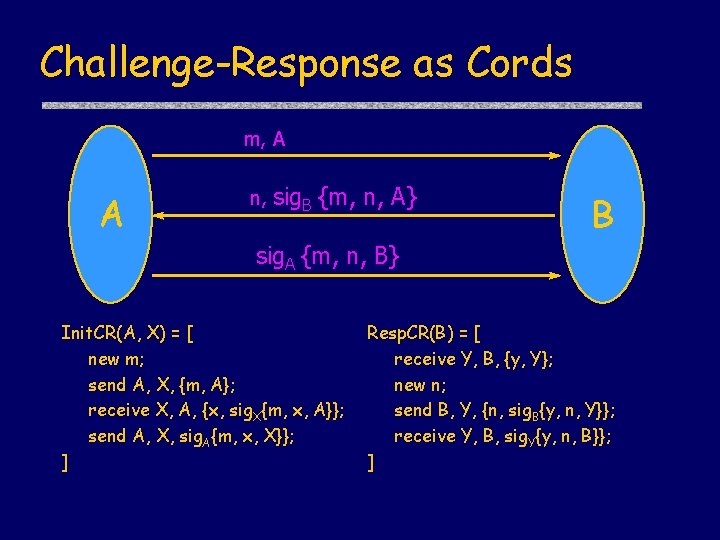
Example: Challenge-Response m, A A n, sig. B {m, n, A} B sig. A {m, n, B} Alice reasons: if Bob is honest, then: • only Bob can generate his signature. [protocol independent] • if Bob generates a signature of the form sig. B{m, n, A}, – he sends it as part of msg 2 of the protocol and – he must have received msg 1 from Alice. [protocol specific] Alice deduces: Received (B, msg 1) Λ Sent (B, msg 2)

Formalizing the Approach Language for protocol description • Arrows-and-messages are informal. Protocol Semantics • How does the protocol execute? Protocol logic • Stating security properties. Proof system • Formally proving security properties. (User view of the logic)

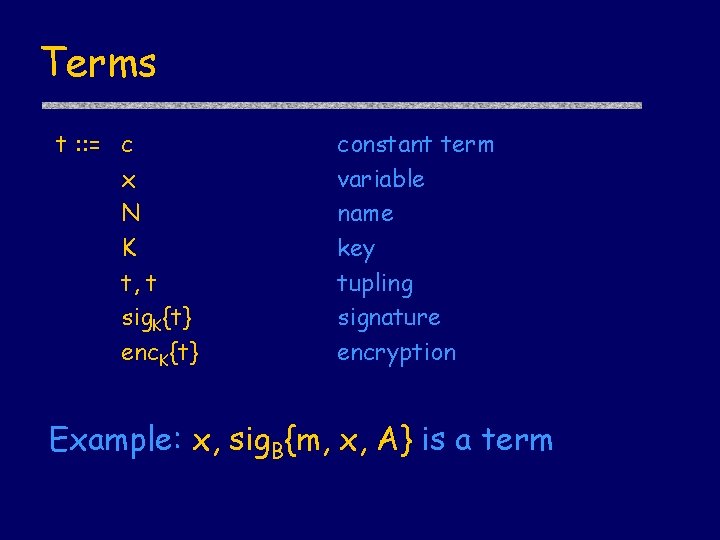
Cords “protocol programming language” • A protocol is described by specifying a “program” for each role – Server = [receive x; new n; send {x, n}] Building blocks • Terms (think “messages”) – names, nonces, keys, encryption, … • Actions (operations on terms) – send, receive, pattern match, …

Terms t : : = c x N K t, t sig. K{t} enc. K{t} constant term variable name key tupling signature encryption Example: x, sig. B{m, x, A} is a term

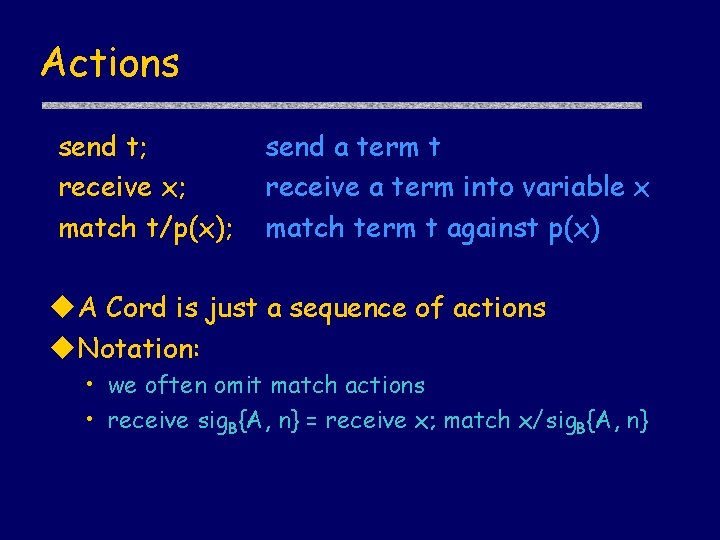
Actions send t; receive x; match t/p(x); send a term t receive a term into variable x match term t against p(x) A Cord is just a sequence of actions Notation: • we often omit match actions • receive sig. B{A, n} = receive x; match x/sig. B{A, n}

Challenge-Response as Cords m, A A n, sig. B {m, n, A} B sig. A {m, n, B} Init. CR(A, X) = [ new m; send A, X, {m, A}; receive X, A, {x, sig. X{m, x, A}}; send A, X, sig. A{m, x, X}}; ] Resp. CR(B) = [ receive Y, B, {y, Y}; new n; send B, Y, {n, sig. B{y, n, Y}}; receive Y, B, sig. Y{y, n, B}}; ]

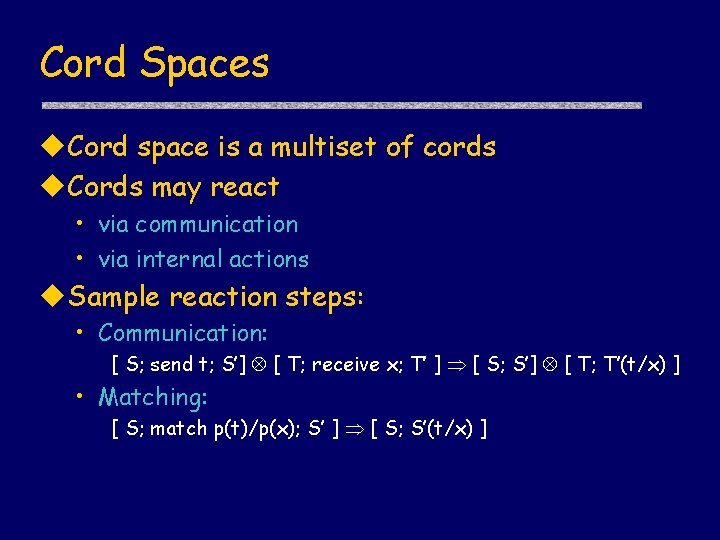
Cord Spaces Cord space is a multiset of cords Cords may react • via communication • via internal actions Sample reaction steps: • Communication: [ S; send t; S’] [ T; receive x; T’ ] [ S; S’] [ T; T’(t/x) ] • Matching: [ S; match p(t)/p(x); S’ ] [ S; S’(t/x) ]

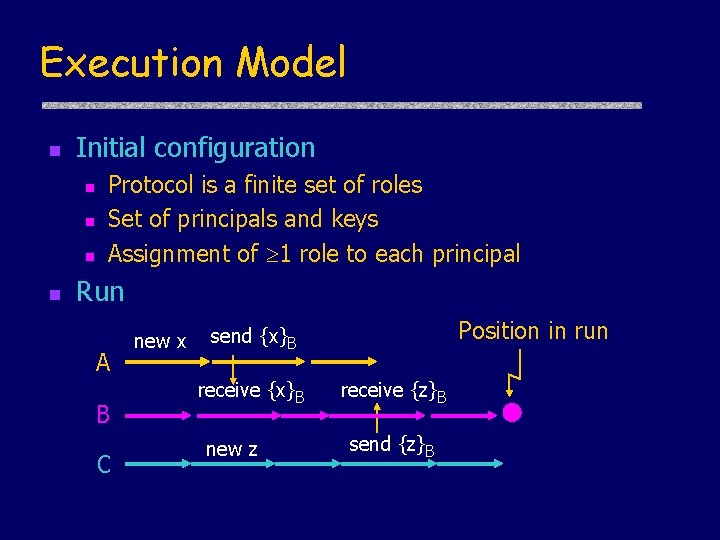
Execution Model n Initial configuration n n Protocol is a finite set of roles Set of principals and keys Assignment of 1 role to each principal Run A B C new x Position in run send {x}B receive {x}B new z receive {z}B send {z}B

Attacker capabilities Controls complete network • Can read, remove, inject messages Fixed set of operations on terms • • • Pairing Projection Encryption with known key Decryption with known key … Commonly referred to as “Dolev-Yao” attacker Next lecture: more powerful “crypto-style” attacker
![Logical assertions Modal operator actions P if holds and P Logical assertions Modal operator • [ actions ] P - if holds and P](https://slidetodoc.com/presentation_image_h2/7b42c895ce7c28350b48b750590ca09a/image-22.jpg)
Logical assertions Modal operator • [ actions ] P - if holds and P executes actions, then holds Predicates in • • Send(X, m) Receive(X, m) Verify(X, m) Has(X, m) - principal X sent message m – principal X received message m - X verified signature m - X created m or received msg containing m and has keys to extract m from msg • Honest(X) – X follows rules of protocol

Formulas true at a position in run n Action formulas a : : = Send(P, m) | Receive (P, m) | New(P, t) | Decrypt (P, t) | Verify (P, t) n Formulas : : = a | Has(P, t) | Fresh(P, t) | Honest(N) | Contains(t 1, t 2) | | 1 2 | x | | n Example After(a, b) = (b a)

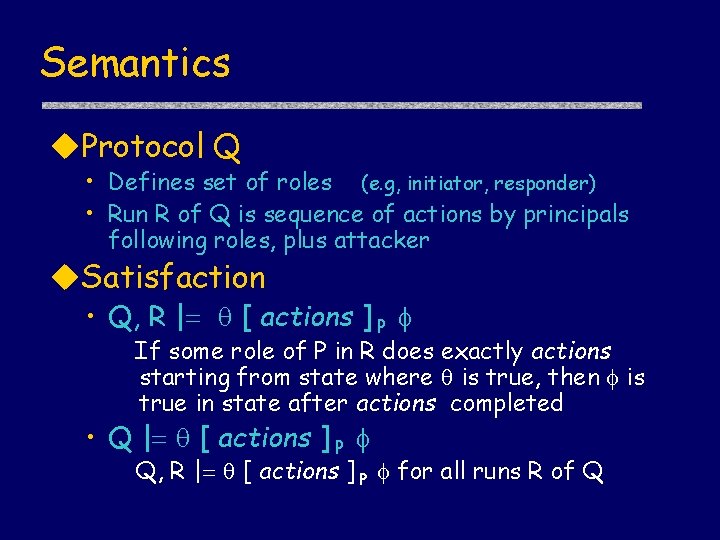
Semantics Protocol Q • Defines set of roles (e. g, initiator, responder) • Run R of Q is sequence of actions by principals following roles, plus attacker Satisfaction • Q, R | [ actions ] P If some role of P in R does exactly actions starting from state where is true, then is true in state after actions completed • Q | [ actions ] P Q, R | [ actions ] P for all runs R of Q
![Security Properties Authentication for Initiator CR true Init CRA B A Security Properties Authentication for Initiator CR | true [ Init. CR(A, B) ] A](https://slidetodoc.com/presentation_image_h2/7b42c895ce7c28350b48b750590ca09a/image-25.jpg)
Security Properties Authentication for Initiator CR | true [ Init. CR(A, B) ] A Honest(B) Actions. In. Order( Send(A, {A, B, m}), Receive(B, {A, B, m}), Send(B, {B, A, {n, sig. B {m, n, A}}}), Receive(A, {B, A, {n, sig. B {m, n, A}}}) )

Proof System Goal: formally prove security properties Axioms • Simple formulas provable by hand Inference rules • Proof steps Theorem • Formula obtained from axioms by application of inference rules This is what you will do!
![Sample axioms about actions New data true new x P HasP x Sample axioms about actions New data • true [ new x ]P Has(P, x)](https://slidetodoc.com/presentation_image_h2/7b42c895ce7c28350b48b750590ca09a/image-27.jpg)
Sample axioms about actions New data • true [ new x ]P Has(P, x) • true [ new x ]P Has(Y, x) Y=P Actions • true [ send m ]P Send(P, m) Knowledge • true [receive m ]P Has(P, m) Verify • true [ match x/sig. X{m} ] P Verify(P, m)

Reasoning about knowledge Pairing • Has(X, {m, n}) Has(X, m) Has(X, n) Encryption • Has(X, enc. K(m)) Has(X, K-1) Has(X, m)

Encryption and signature Public key encryption Honest(X) Decrypt(Y, enc. X{m}) X=Y Signature Honest(X) Verify(Y, sig. X{m}) m’ ( Send(X, m’) Contains(m’, sig. X{m})
![Sample inference rules Firstorder logic rules Generic rules actions P Sample inference rules First-order logic rules Generic rules [ actions ]P](https://slidetodoc.com/presentation_image_h2/7b42c895ce7c28350b48b750590ca09a/image-30.jpg)
Sample inference rules First-order logic rules Generic rules [ actions ]P

Bidding conventions (motivation) Blackwood response to 4 NT – 5§ : – 5¨ : – 5© : – 5ª : 0 or 4 aces 1 ace 2 aces 3 aces Reasoning • If my partner is following Blackwood, then if she bid 5©, she must have 2 aces

Honesty rule (rule scheme) roles R of Q. protocol steps A of R. Start(X) [ ]X [ A ]X Q |- Honest(X) • This is a finitary rule: – Typical protocol has 2 -3 roles – Typical role has 1 -3 receives – Only need to consider A waiting to receive

Honesty rule (example use) roles R of Q. protocol steps A of R. Start(X) [ ]X [ A ]X Q |- Honest(X) • Example use: – If Y receives a message m from X, and – Honest(X) (Sent(X, m) Received(X, m’)) – then Y can conclude Honest(X) Received(X, m’)) Proved using honesty rule

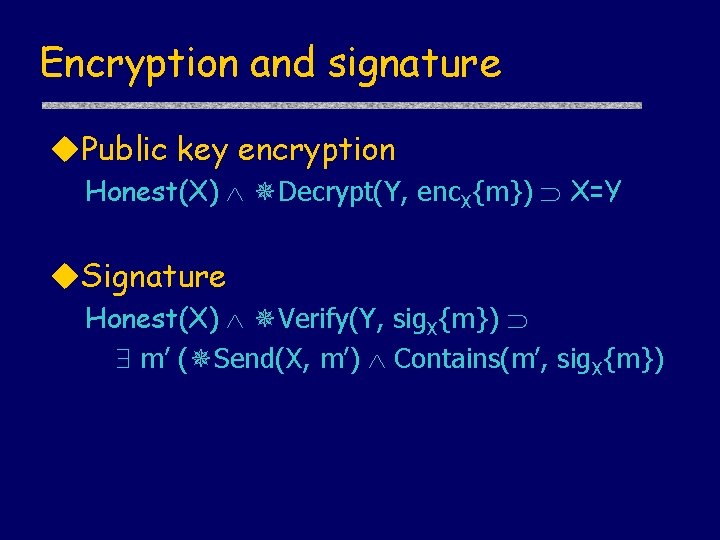
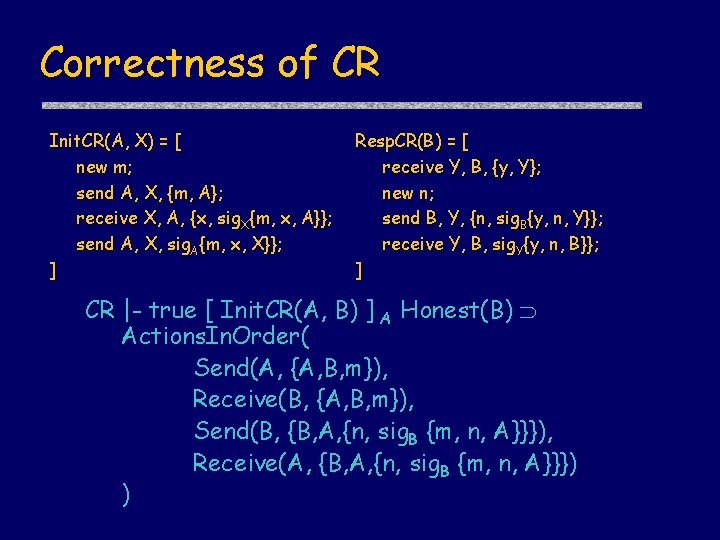
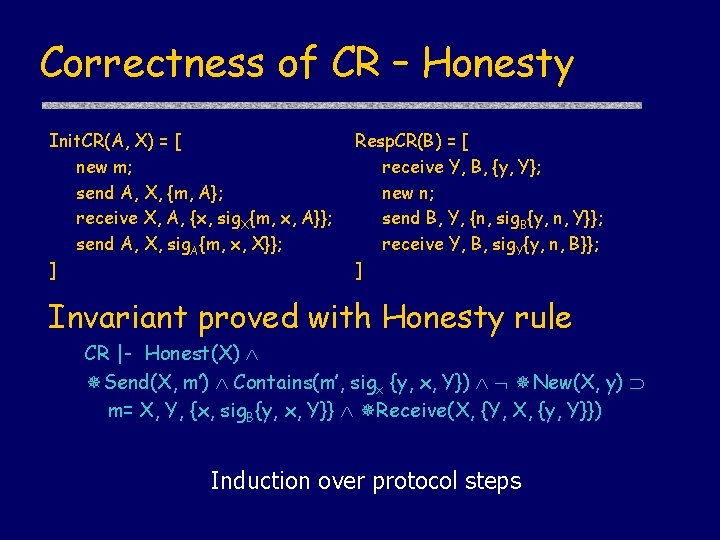
Correctness of CR Init. CR(A, X) = [ new m; send A, X, {m, A}; receive X, A, {x, sig. X{m, x, A}}; send A, X, sig. A{m, x, X}}; ] Resp. CR(B) = [ receive Y, B, {y, Y}; new n; send B, Y, {n, sig. B{y, n, Y}}; receive Y, B, sig. Y{y, n, B}}; ] CR |- true [ Init. CR(A, B) ] A Honest(B) Actions. In. Order( Send(A, {A, B, m}), Receive(B, {A, B, m}), Send(B, {B, A, {n, sig. B {m, n, A}}}), Receive(A, {B, A, {n, sig. B {m, n, A}}}) )

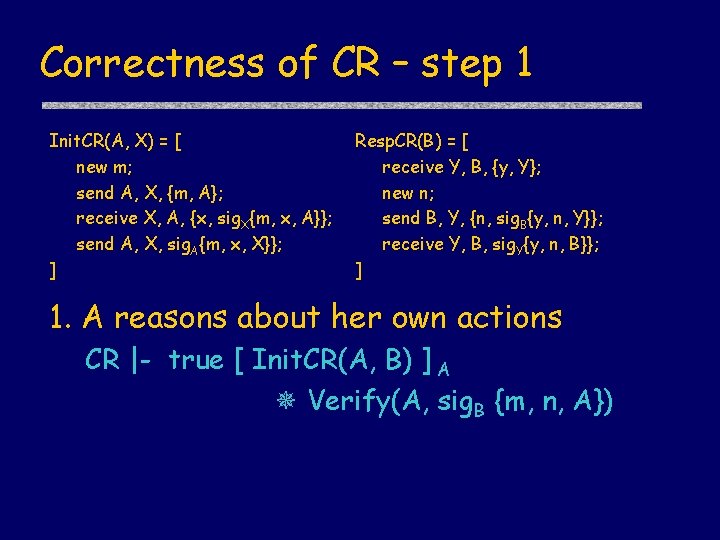
Correctness of CR – step 1 Init. CR(A, X) = [ new m; send A, X, {m, A}; receive X, A, {x, sig. X{m, x, A}}; send A, X, sig. A{m, x, X}}; ] Resp. CR(B) = [ receive Y, B, {y, Y}; new n; send B, Y, {n, sig. B{y, n, Y}}; receive Y, B, sig. Y{y, n, B}}; ] 1. A reasons about her own actions CR |- true [ Init. CR(A, B) ] A Verify(A, sig. B {m, n, A})

Correctness of CR – step 2 Init. CR(A, X) = [ new m; send A, X, {m, A}; receive X, A, {x, sig. X{m, x, A}}; send A, X, sig. A{m, x, X}}; ] Resp. CR(B) = [ receive Y, B, {y, Y}; new n; send B, Y, {n, sig. B{y, n, Y}}; receive Y, B, sig. Y{y, n, B}}; ] 2. Properties of signatures CR |- true [ Init. CR(A, B) ] A Honest(B) m’ ( Send(B, m’) Contains(m’, sig. B {m, n, A}) Recall signature axiom

Correctness of CR – Honesty Init. CR(A, X) = [ new m; send A, X, {m, A}; receive X, A, {x, sig. X{m, x, A}}; send A, X, sig. A{m, x, X}}; ] Resp. CR(B) = [ receive Y, B, {y, Y}; new n; send B, Y, {n, sig. B{y, n, Y}}; receive Y, B, sig. Y{y, n, B}}; ] Invariant proved with Honesty rule CR |- Honest(X) Send(X, m’) Contains(m’, sigx {y, x, Y}) New(X, y) m= X, Y, {x, sig. B{y, x, Y}} Receive(X, {Y, X, {y, Y}}) Induction over protocol steps

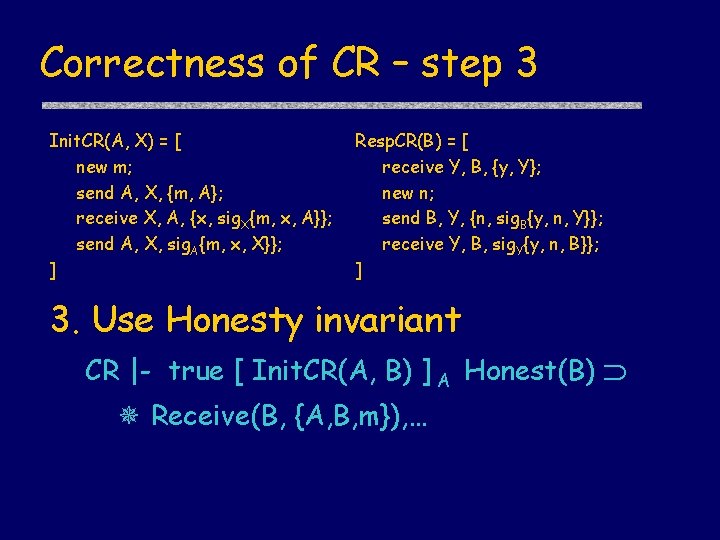
Correctness of CR – step 3 Init. CR(A, X) = [ new m; send A, X, {m, A}; receive X, A, {x, sig. X{m, x, A}}; send A, X, sig. A{m, x, X}}; ] Resp. CR(B) = [ receive Y, B, {y, Y}; new n; send B, Y, {n, sig. B{y, n, Y}}; receive Y, B, sig. Y{y, n, B}}; ] 3. Use Honesty invariant CR |- true [ Init. CR(A, B) ] A Honest(B) Receive(B, {A, B, m}), …

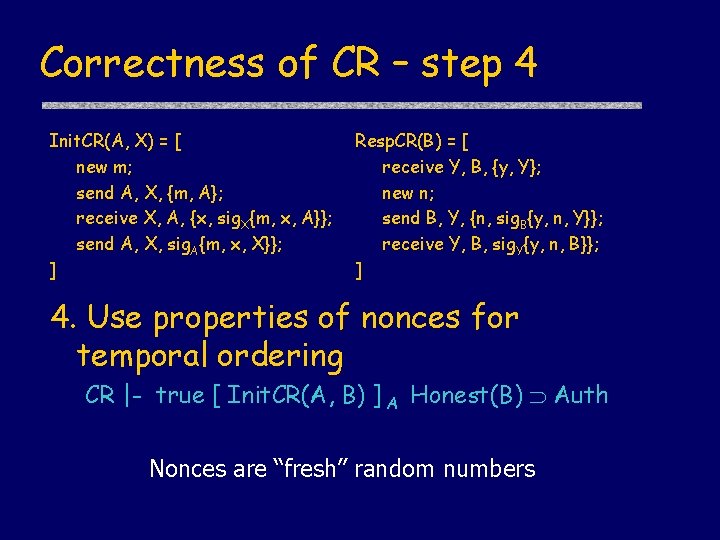
Correctness of CR – step 4 Init. CR(A, X) = [ new m; send A, X, {m, A}; receive X, A, {x, sig. X{m, x, A}}; send A, X, sig. A{m, x, X}}; ] Resp. CR(B) = [ receive Y, B, {y, Y}; new n; send B, Y, {n, sig. B{y, n, Y}}; receive Y, B, sig. Y{y, n, B}}; ] 4. Use properties of nonces for temporal ordering CR |- true [ Init. CR(A, B) ] A Honest(B) Auth Nonces are “fresh” random numbers

Complete proof

We have a proof. So what? Soundness Theorem: • if Q |- then Q |= • If is a theorem then is a valid formula holds in any step in any run of protocol Q • Unbounded number of participants • Dolev-Yao intruder

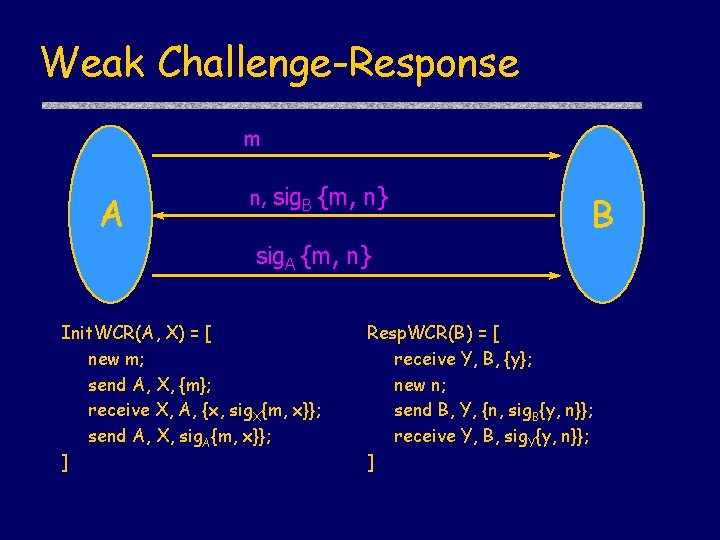
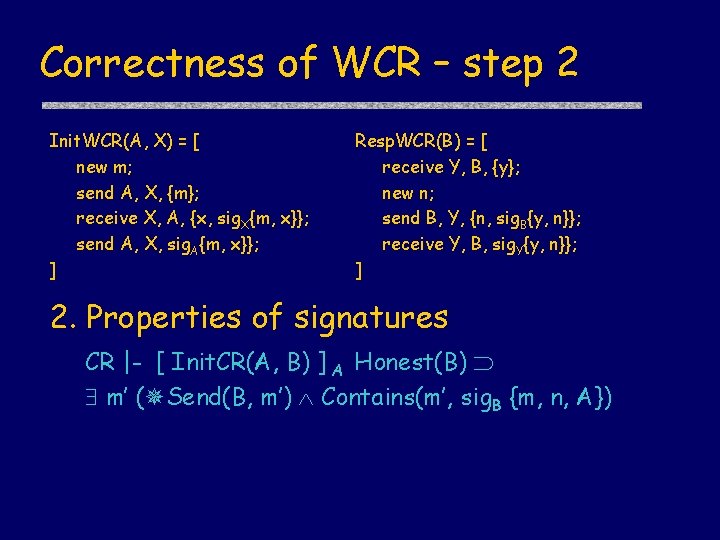
Weak Challenge-Response m A n, sig. B {m, n} B sig. A {m, n} Init. WCR(A, X) = [ new m; send A, X, {m}; receive X, A, {x, sig. X{m, x}}; send A, X, sig. A{m, x}}; ] Resp. WCR(B) = [ receive Y, B, {y}; new n; send B, Y, {n, sig. B{y, n}}; receive Y, B, sig. Y{y, n}}; ]

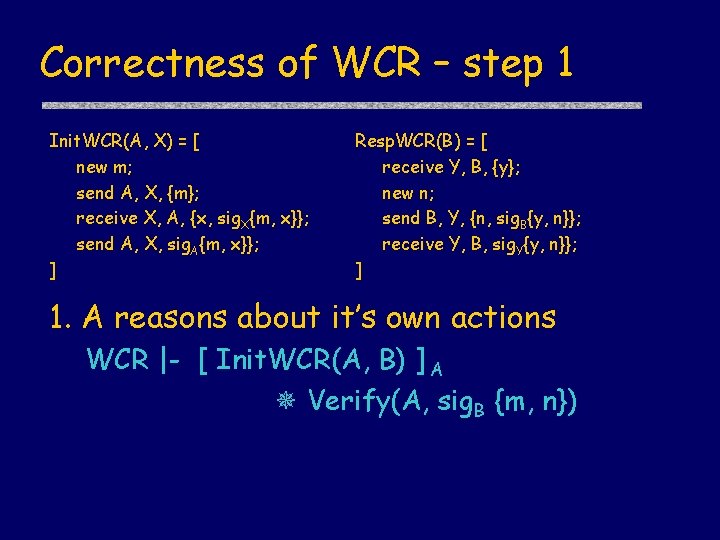
Correctness of WCR – step 1 Init. WCR(A, X) = [ new m; send A, X, {m}; receive X, A, {x, sig. X{m, x}}; send A, X, sig. A{m, x}}; ] Resp. WCR(B) = [ receive Y, B, {y}; new n; send B, Y, {n, sig. B{y, n}}; receive Y, B, sig. Y{y, n}}; ] 1. A reasons about it’s own actions WCR |- [ Init. WCR(A, B) ] A Verify(A, sig. B {m, n})

Correctness of WCR – step 2 Init. WCR(A, X) = [ new m; send A, X, {m}; receive X, A, {x, sig. X{m, x}}; send A, X, sig. A{m, x}}; ] Resp. WCR(B) = [ receive Y, B, {y}; new n; send B, Y, {n, sig. B{y, n}}; receive Y, B, sig. Y{y, n}}; ] 2. Properties of signatures CR |- [ Init. CR(A, B) ] A Honest(B) m’ ( Send(B, m’) Contains(m’, sig. B {m, n, A})

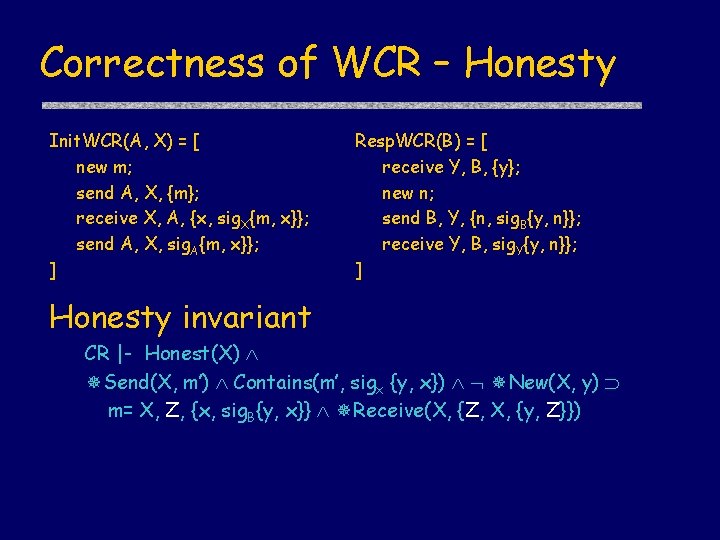
Correctness of WCR – Honesty Init. WCR(A, X) = [ new m; send A, X, {m}; receive X, A, {x, sig. X{m, x}}; send A, X, sig. A{m, x}}; ] Resp. WCR(B) = [ receive Y, B, {y}; new n; send B, Y, {n, sig. B{y, n}}; receive Y, B, sig. Y{y, n}}; ] Honesty invariant CR |- Honest(X) Send(X, m’) Contains(m’, sigx {y, x}) New(X, y) m= X, Z, {x, sig. B{y, x}} Receive(X, {Z, X, {y, Z}})

Correctness of WCR – step 3 Init. WCR(A, X) = [ new m; send A, X, {m}; receive X, A, {x, sig. X{m, x}}; send A, X, sig. A{m, x}}; ] Resp. WCR(B) = [ receive Y, B, {y}; new n; send B, Y, {n, sig. B{y, n}}; receive Y, B, sig. Y{y, n}}; ] 3. Use Honesty rule WCR |- [ Init. WCR(A, B) ] A Honest(B) Receive(B, {Z, B, m}),

Result WCR does not have the strong authentication property for the initiator Counterexample • Intruder can forge senders and receivers identity in first two messages – A -> X(B) – X(C) -> B – B -> X(C) – X(B) ->A m m n, sig. B(m, n)

Protocol Composition Logic: PCL Intuition Formalism • Protocol programming language • Protocol logic – Syntax – Semantics • Proof System Example • Signature-based challenge-response Composition Computational Soundness

Compositional Security Assigned readings: • A. Datta, A. Derek, J. C. Mitchell, D. Pavlovic. A derivation system and compositional logic for security protocols • C. He, M. Sundararajan, A. Datta, A. Derek, J. C. Mitchell. A Modular Correctness Proof of TLS and IEEE 802. 11 i Perspective: • C. Meadows. Open issues in formal methods for cryptographic protocol analysis. • J. M. Wing. Beyond the horizon: A call to arms.

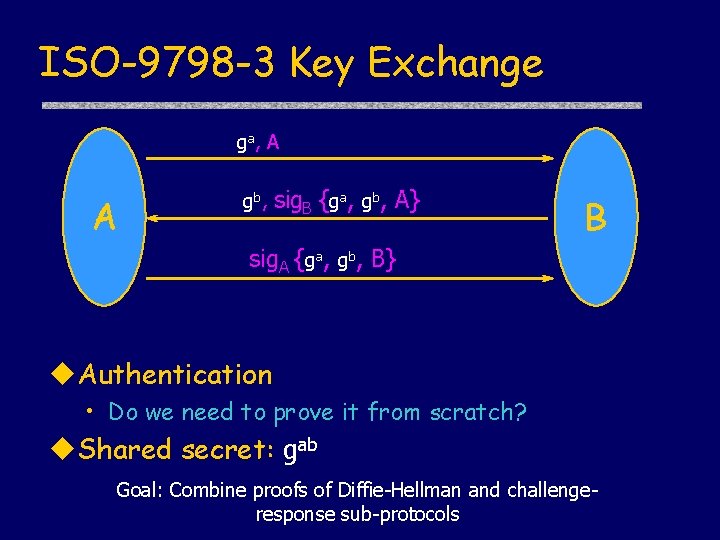
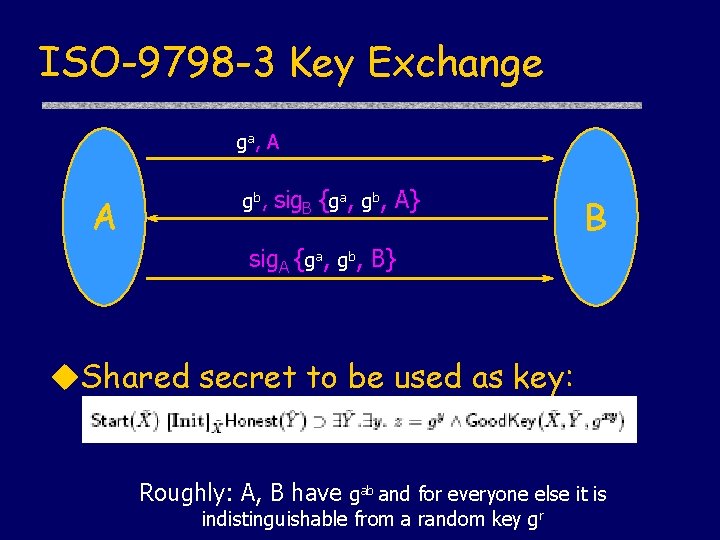
ISO-9798 -3 Key Exchange ga, A A gb, sig. B {ga, gb, A} B sig. A {ga, gb, B} Authentication • Do we need to prove it from scratch? Shared secret: gab Goal: Combine proofs of Diffie-Hellman and challengeresponse sub-protocols

Abstract challenge response Init. ACR(A, X, m) = [ send A, X, {m}; receive X, A, {x, sig. X{m, x}}; send A, X, sig. A{m, x}}; ] Resp. ACR(B, n) = [ receive Y, B, {y}; send B, Y, {n, sig. B{y, n}}; receive Y, B, sig. Y{y, n}}; ] Free variables m and n instead of nonces Modal form: [ actions ] • • • precondition: actions: postcondition: Fresh(A, m) [ Init. ACR ]A Honest(B) Authentication Secrecy is proved from properties of Diffie-Hellman
![DiffieHellman Property Formula true new a A FreshA ga DiffieHellman property Can Diffie-Hellman: Property Formula true [ new a ] A Fresh(A, ga) Diffie-Hellman property: Can](https://slidetodoc.com/presentation_image_h2/7b42c895ce7c28350b48b750590ca09a/image-52.jpg)
Diffie-Hellman: Property Formula true [ new a ] A Fresh(A, ga) Diffie-Hellman property: Can compute gab given ga and b or gb and a Cannot compute gab given ga and gb
![Challenge Response Property Modal form actions P precondition FreshA m actions Challenge Response: Property Modal form: [ actions ]P • precondition: Fresh(A, m) • actions:](https://slidetodoc.com/presentation_image_h2/7b42c895ce7c28350b48b750590ca09a/image-53.jpg)
Challenge Response: Property Modal form: [ actions ]P • precondition: Fresh(A, m) • actions: [ Initiator role actions ]A • postcondition: Honest(B) Actions. In. Order( send(A, {A, B, m}), receive(B, {A, B, m}), send(B, {B, A, {n, sig. B {m, n, A}}}), receive(A, {B, A, {n, sig. B {m, n, A}}}) )

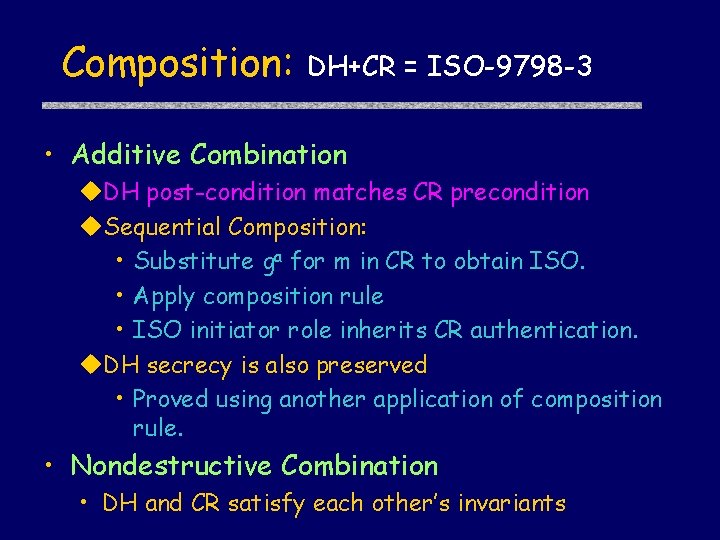
Composition: DH+CR = ISO-9798 -3 • Additive Combination DH post-condition matches CR precondition Sequential Composition: • Substitute ga for m in CR to obtain ISO. • Apply composition rule • ISO initiator role inherits CR authentication. DH secrecy is also preserved • Proved using another application of composition rule. • Nondestructive Combination • DH and CR satisfy each other’s invariants

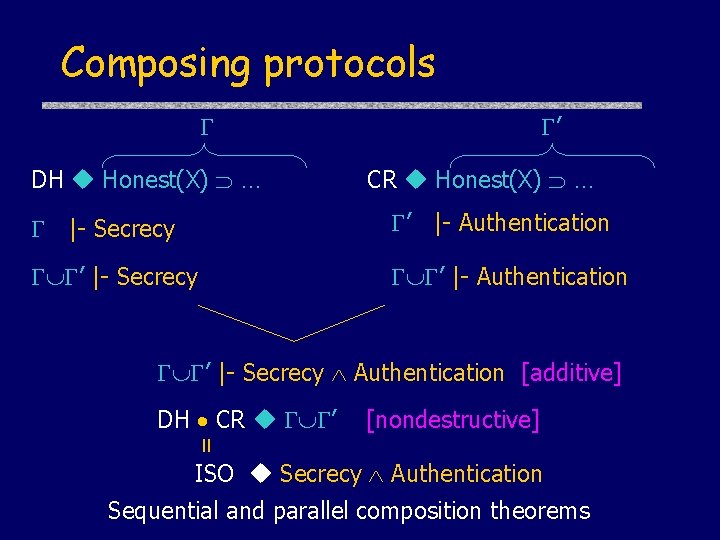
Composing protocols DH Honest(X) … ’ CR Honest(X) … |- Secrecy ’ |- Authentication ’ |- Secrecy Authentication [additive] [nondestructive] = DH CR ’ ISO Secrecy Authentication Sequential and parallel composition theorems
![Composition Rules Invariant weakening rule P P Sequential Composition Composition Rules Invariant weakening rule |- […]P ’ |- […]P Sequential Composition |- [](https://slidetodoc.com/presentation_image_h2/7b42c895ce7c28350b48b750590ca09a/image-56.jpg)
Composition Rules Invariant weakening rule |- […]P ’ |- […]P Sequential Composition |- [ S ] P |- [ T ] P |- [ ST ] P Prove invariants from protocol Q Q’

Composition: Big Picture Safe Environment for Q Q 1 Q 2 Q 3 … Qn Protocol Q • Q |- Inv(Q) • Inv(Q) |- • Qi |- Inv(Q) • No reasoning about attacker

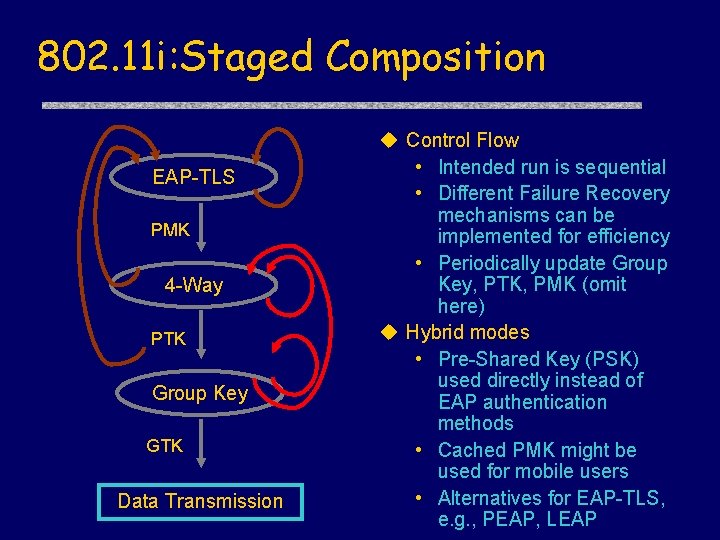
802. 11 i: Staged Composition EAP-TLS PMK 4 -Way PTK Group Key GTK Data Transmission Control Flow • Intended run is sequential • Different Failure Recovery mechanisms can be implemented for efficiency • Periodically update Group Key, PTK, PMK (omit here) Hybrid modes • Pre-Shared Key (PSK) used directly instead of EAP authentication methods • Cached PMK might be used for mobile users • Alternatives for EAP-TLS, e. g. , PEAP, LEAP
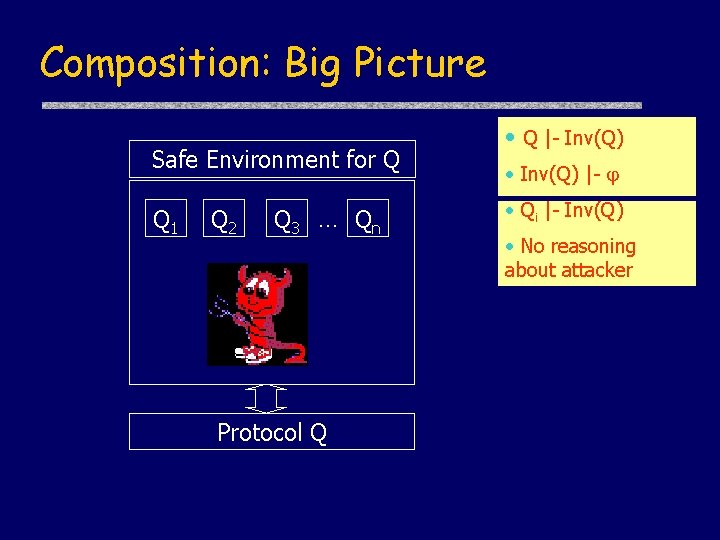
![802 11 i Proof Structure Step 1 i j θi PiX i Separate 802. 11 i Proof Structure Step 1. i, j |- θi [Pi]X i Separate](https://slidetodoc.com/presentation_image_h2/7b42c895ce7c28350b48b750590ca09a/image-59.jpg)
802. 11 i Proof Structure Step 1. i, j |- θi [Pi]X i Separate proof of individual components TLS, 4 -Way, and Group Key Handshake; Step 2. i, j, Qi |- j Necessary invariants are satisfied by all components; Step 3. i, i θi+1 The postcondition of TLS implies precondition of 4 -Way; postcondition of 4 -Way implies precondition of Group Key; Step 4. i, θi [B]X θi The preconditions of each component are preserved by subsequent components. Applying the Staged Composition Theorem, 802. 11 i is secure

Protocol Composition Logic: PCL Intuition Formalism • Protocol programming language • Protocol logic – Syntax – Semantics • Proof System Example • Signature-based challenge-response Composition Computational Soundness

Computational PCL Symbolic proofs about complexitytheoretic model of cryptographic protocols!
![Two worlds Symbolic model NS 78 DY 84 Complexitytheoretic model GM 84 Two worlds Symbolic model [NS 78, DY 84, …] Complexity-theoretic model [GM 84, …]](https://slidetodoc.com/presentation_image_h2/7b42c895ce7c28350b48b750590ca09a/image-62.jpg)
Two worlds Symbolic model [NS 78, DY 84, …] Complexity-theoretic model [GM 84, …] Attacker actions -Fixed set of actions, e. g. , decryption with known key (ABSTRACTION) + Any probabilistic polytime computation Security properties -Idealized, e. g. , secret message = not possessing atomic term representing message (ABSTRACTION) + Fine-grained, e. g. , secret message = no partial information about bitstring representation Analysis methods + Successful array of tools and techniques; automation - Hand-proofs are difficult, error-prone; no automation Can we get the best of both worlds?

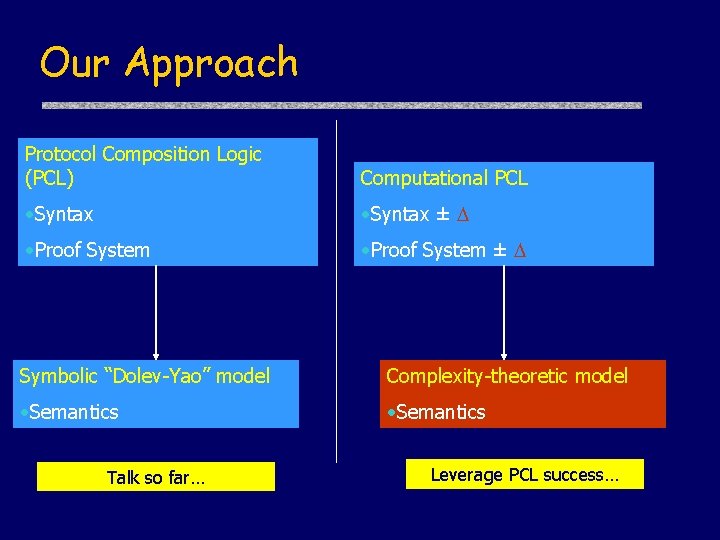
Our Approach Protocol Composition Logic (PCL) Computational PCL • Syntax ± • Proof System ± Symbolic “Dolev-Yao” model Complexity-theoretic model • Semantics Talk so far… Leverage PCL success…

Main Result Computational PCL • Symbolic logic for proving security properties of network protocols using public-key encryption Soundness Theorem: • If a property is provable in CPCL, then property holds in computational model with overwhelming asymptotic probability. Benefits • Symbolic proofs about computational model • Computational reasoning in soundness proof (only!) • Different axioms rely on different crypto assumptions

ISO-9798 -3 Key Exchange ga, A A gb, sig. B {ga, gb, A} B sig. A {ga, gb, B} Shared secret to be used as key: Roughly: A, B have gab and for everyone else it is indistinguishable from a random key gr

Central axioms Cryptographic security property of signature scheme • Unforgeability (used for authentication) Cryptographic security property of Diffie-Hellman function • DDH (used to prove secrecy)

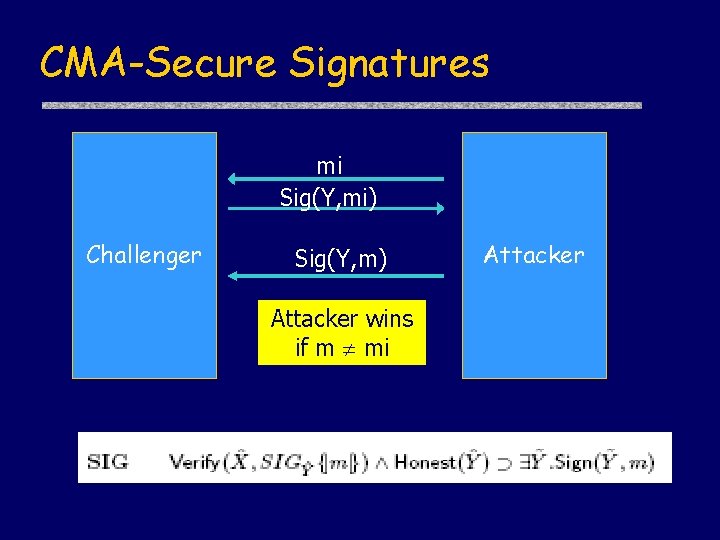
CMA-Secure Signatures mi Sig(Y, mi) Challenger Sig(Y, m) Attacker wins if m mi Attacker

Decisional Diffie-Hellman Let a, b, c be chosen at random from a group G with generator g. Then the two distributions <ga, gb, gab> and <ga, gb, gc> are computationally indistinguishable (no polynomial time attacker can tell them apart)

Complete Proof

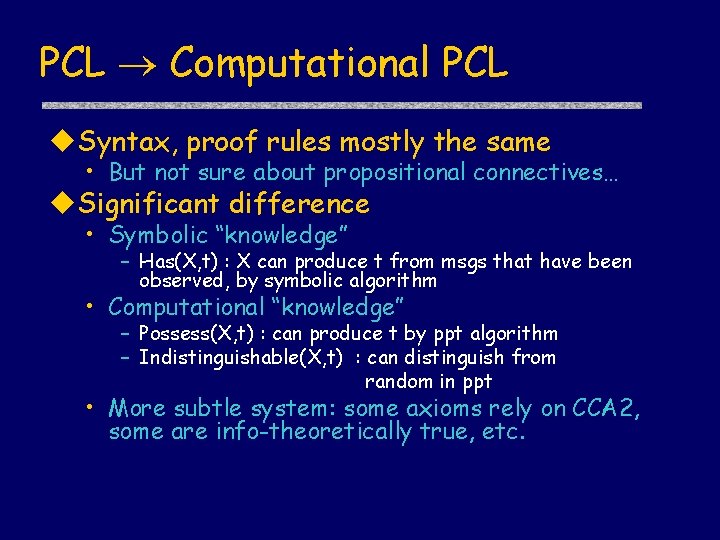
PCL Computational PCL Syntax, proof rules mostly the same • But not sure about propositional connectives… Significant difference • Symbolic “knowledge” – Has(X, t) : X can produce t from msgs that have been observed, by symbolic algorithm • Computational “knowledge” – Possess(X, t) : can produce t by ppt algorithm – Indistinguishable(X, t) : can distinguish from random in ppt • More subtle system: some axioms rely on CCA 2, some are info-theoretically true, etc.

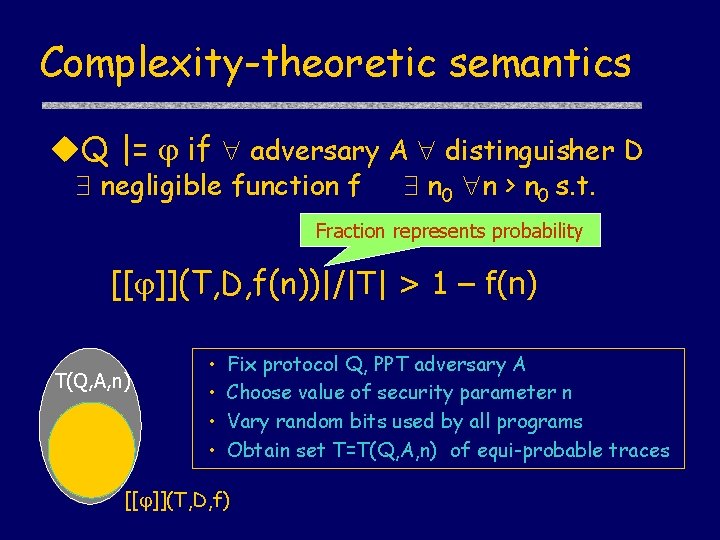
Complexity-theoretic semantics Q |= if adversary A distinguisher D negligible function f n 0 n > n 0 s. t. Fraction represents probability [[ ]](T, D, f(n))|/|T| > 1 – f(n) T(Q, A, n) • • Fix protocol Q, PPT adversary A Choose value of security parameter n Vary random bits used by all programs Obtain set T=T(Q, A, n) of equi-probable traces [[ ]](T, D, f)
![Inductive Semantics 1 2 T D 1 T D Inductive Semantics [[ 1 2]] (T, D, ) = [[ 1]] (T, D, )](https://slidetodoc.com/presentation_image_h2/7b42c895ce7c28350b48b750590ca09a/image-72.jpg)
Inductive Semantics [[ 1 2]] (T, D, ) = [[ 1]] (T, D, ) [[ 2]] (T, D, ) [[ 1 2]] (T, D, ) = [[ 1]] (T, D, ) [[ 2]] (T, D, ) [[ ]] (T, D, ) = T - [[ ]] (T, D, ) Implication uses conditional probability [[ 1 2]] (T, D, ) = [[ 1]] (T, D, ) [[ 2]] (T’, D, ) where T’ = [[ 1]] (T, D, ) Formula defines transformation on probability distributions over traces

Soundness of proof system Example axiom • Source(Y, u, {m}X) Decrypts(X, {m}X) Honest(X, Y) (Z X, Y) Indistinguishable(Z, u) Proof idea: crypto-style reduction • Assume axiom not valid: A D negligible f n 0 n > n 0 s. t. • [[ ]](T, D, f)|/|T| < 1 –f(n) • Construct attacker A’ that uses A, D to break IND-CCA 2 secure encryption scheme • Conditional implication essential

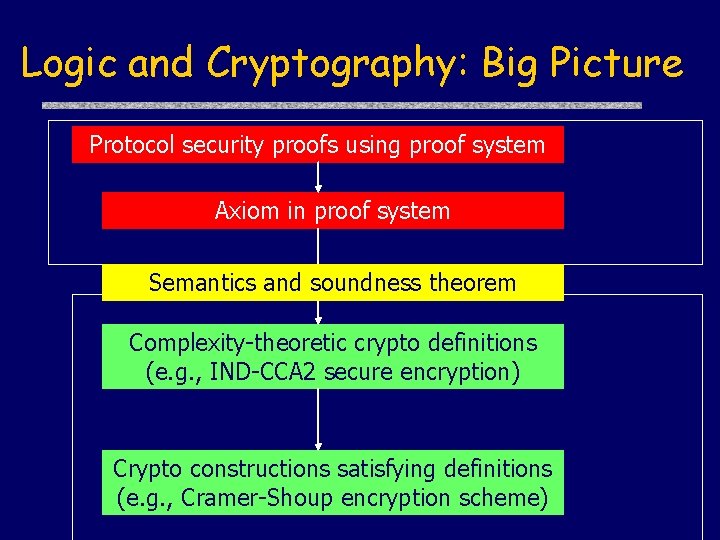
Logic and Cryptography: Big Picture Protocol security proofs using proof system Axiom in proof system Semantics and soundness theorem Complexity-theoretic crypto definitions (e. g. , IND-CCA 2 secure encryption) Crypto constructions satisfying definitions (e. g. , Cramer-Shoup encryption scheme)

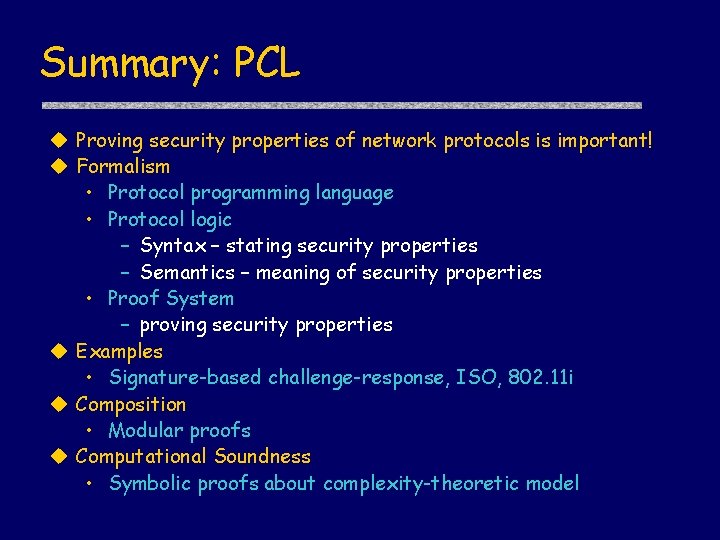
Summary: PCL Proving security properties of network protocols is important! Formalism • Protocol programming language • Protocol logic – Syntax – stating security properties – Semantics – meaning of security properties • Proof System – proving security properties Examples • Signature-based challenge-response, ISO, 802. 11 i Composition • Modular proofs Computational Soundness • Symbolic proofs about complexity-theoretic model

Thanks ! Questions?