CS 259 Protocol Composition Logic PCL Anupam Datta



![Protocol Composition Logic: PCL u. Intuition u. Formalism [Datta, Derek, Durgin, Mitchell, Pavlovic] • Protocol Composition Logic: PCL u. Intuition u. Formalism [Datta, Derek, Durgin, Mitchell, Pavlovic] •](https://slidetodoc.com/presentation_image_h2/0e2d101352a0cf30e5495bd7c295955b/image-6.jpg)






![Sample axioms about actions u. New data • true [ new x ]P Has(P, Sample axioms about actions u. New data • true [ new x ]P Has(P,](https://slidetodoc.com/presentation_image_h2/0e2d101352a0cf30e5495bd7c295955b/image-20.jpg)


![Sample inference rules u. First-order logic rules u. Generic rules [ actions ]P Sample inference rules u. First-order logic rules u. Generic rules [ actions ]P](https://slidetodoc.com/presentation_image_h2/0e2d101352a0cf30e5495bd7c295955b/image-23.jpg)










- Slides: 44

CS 259 Protocol Composition Logic (PCL) Anupam Datta

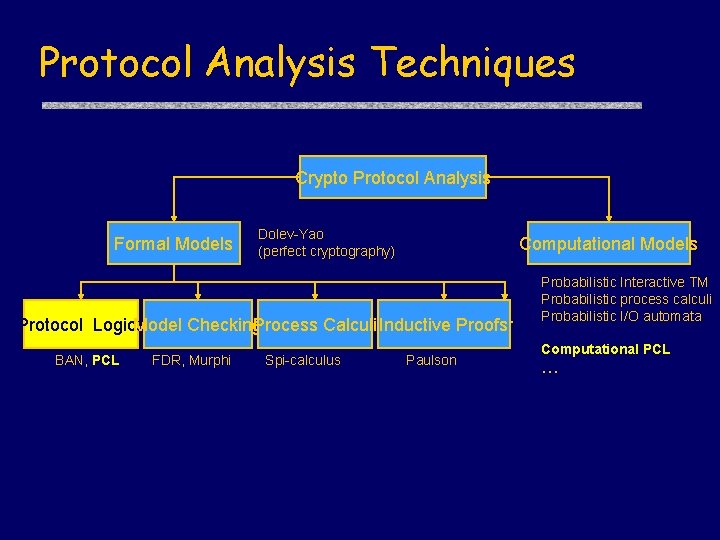
Protocol Analysis Techniques Crypto Protocol Analysis Formal Models Dolev-Yao (perfect cryptography) Computational Models … Protocol Logics Model Checking Process Calculi Inductive Proofs BAN, PCL FDR, Murphi Spi-calculus Paulson Probabilistic Interactive TM Probabilistic process calculi Probabilistic I/O automata Computational PCL …

PCL Highlights u. Mechanizable proofs of security for unbounded number of protocol runs • Similar guarantees as Paulson’s Method; better than finite-state model-checking • Codifies high-level reasoning principles used in protocol design, cf. Kaufman. Perlman-Speciner, Network Security u. Modular proof methods u. Cryptographic soundness

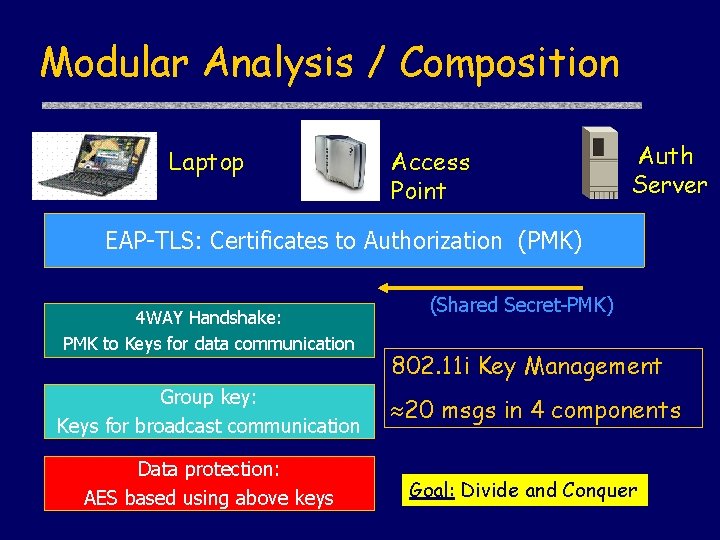
Modular Analysis / Composition Laptop Access Point Auth Server EAP-TLS: Certificates to Authorization (PMK) 4 WAY Handshake: PMK to Keys for data communication Group key: Keys for broadcast communication Data protection: AES based using above keys (Shared Secret-PMK) 802. 11 i Key Management 20 msgs in 4 components Goal: Divide and Conquer

Cryptographic Soundness Cryptographers and logicians working in computer security don’t talk to each other (Disclaimer: Examples not representative) Goal: Logical methods for complexity-theoretic model of cryptography
![Protocol Composition Logic PCL u Intuition u Formalism Datta Derek Durgin Mitchell Pavlovic Protocol Composition Logic: PCL u. Intuition u. Formalism [Datta, Derek, Durgin, Mitchell, Pavlovic] •](https://slidetodoc.com/presentation_image_h2/0e2d101352a0cf30e5495bd7c295955b/image-6.jpg)
Protocol Composition Logic: PCL u. Intuition u. Formalism [Datta, Derek, Durgin, Mitchell, Pavlovic] • Protocol programming language • Protocol logic – Syntax – Semantics • Proof System u. Example • Signature-based challenge-response u. Composition [Datta, Derek, Mitchell, Pavlovic] u. Cryptographic Soundness [Datta, Derek, Mitchell, Shmatikov, Turuani]

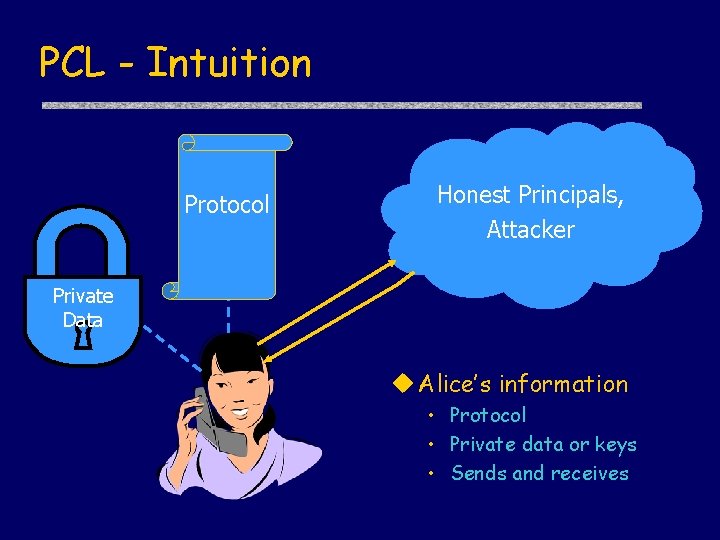
PCL - Intuition Protocol Honest Principals, Attacker Private Data u Alice’s information • Protocol • Private data or keys • Sends and receives

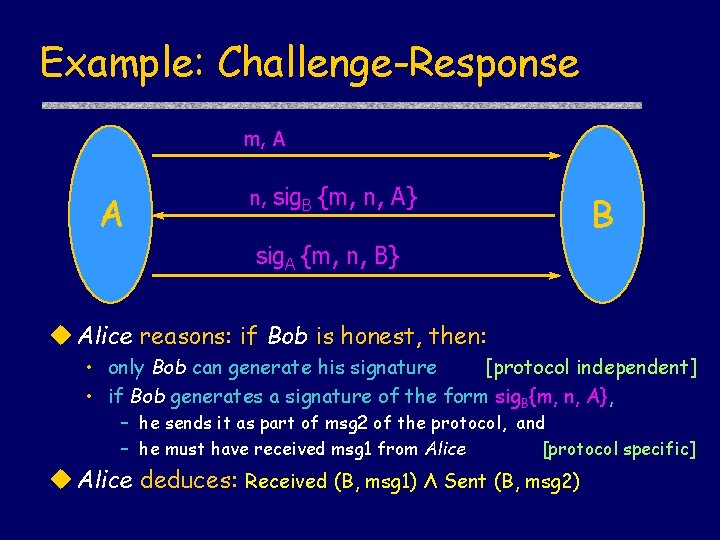
Example: Challenge-Response m, A A n, sig. B {m, n, A} B sig. A {m, n, B} u Alice reasons: if Bob is honest, then: • only Bob can generate his signature [protocol independent] • if Bob generates a signature of the form sig. B{m, n, A}, – he sends it as part of msg 2 of the protocol, and – he must have received msg 1 from Alice [protocol specific] u Alice deduces: Received (B, msg 1) Λ Sent (B, msg 2)

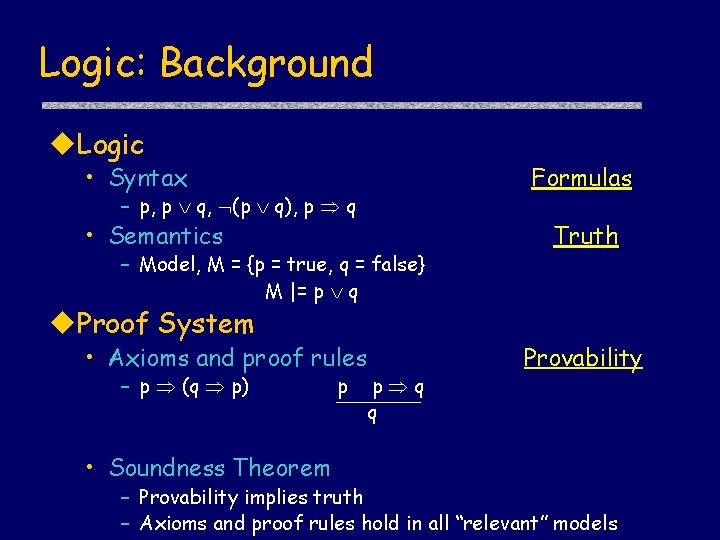
Logic: Background u. Logic • Syntax Formulas – p, p q, (p q), p q • Semantics – Model, M = {p = true, q = false} M |= p q u. Proof System • Axioms and proof rules – p (q p) • Soundness Theorem p p q q Truth Provability – Provability implies truth – Axioms and proof rules hold in all “relevant” models

Formalizing the Approach u. Protocol Programming Language • Syntax for writing protocol code • Precise description of protocol execution u. Protocol Composition Logic (PCL) • Syntax for stating security properties • Trace-based semantics u. Proof system • Formally proving security properties • Soundness Theorem First logic for security protocols Related to: BAN, Floyd-Hoare, CSP/CCS, temporal logic, NPATRL

Protocol programming language u. A protocol is described by specifying a program for each role – Server = [receive x; new n; send {x, n}] u. Building blocks • Terms (think “messages”) – names, nonces, keys, encryption, … • Actions (operations on terms) – send, receive, pattern match, …

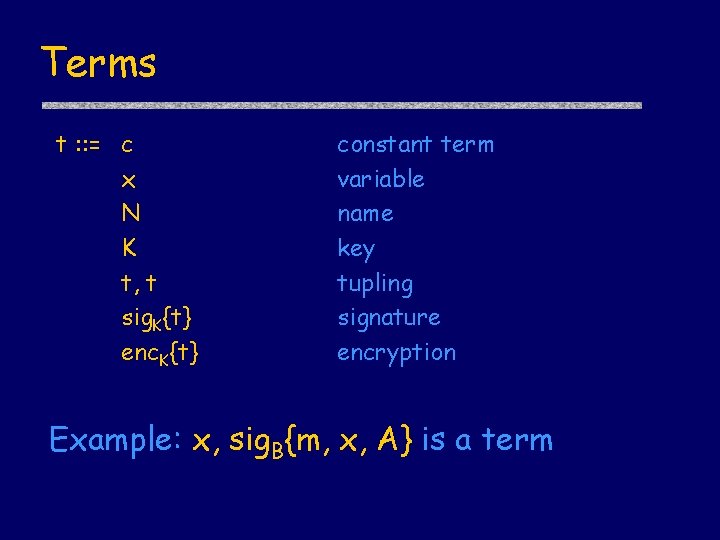
Terms t : : = c x N K t, t sig. K{t} enc. K{t} constant term variable name key tupling signature encryption Example: x, sig. B{m, x, A} is a term

Actions send t; receive x; match t/p(x); send a term t receive a term into variable x match term t against p(x) u. A program is just a sequence of actions u. Notation: • we often omit match actions • receive sig. B{A, n} = receive x; match x/sig. B{A, n}

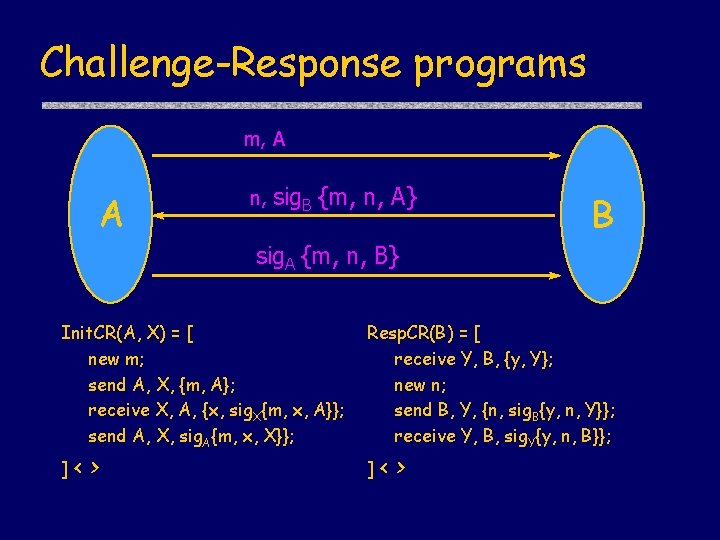
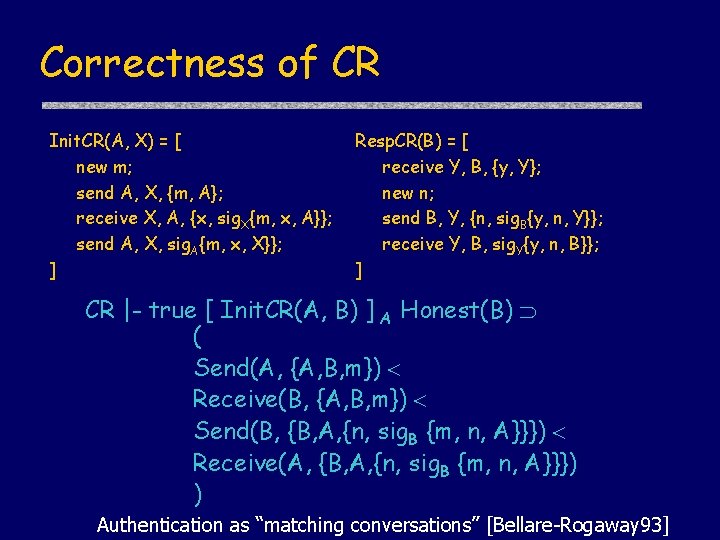
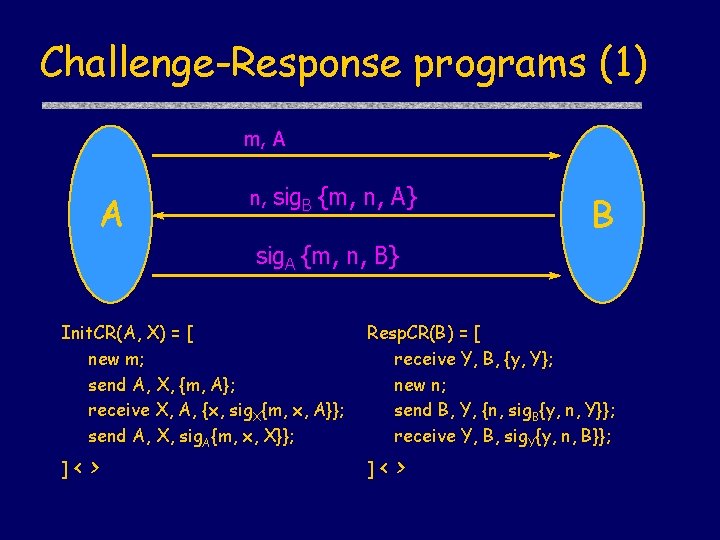
Challenge-Response programs m, A A n, sig. B {m, n, A} B sig. A {m, n, B} Init. CR(A, X) = [ new m; send A, X, {m, A}; receive X, A, {x, sig. X{m, x, A}}; send A, X, sig. A{m, x, X}}; ]< > Resp. CR(B) = [ receive Y, B, {y, Y}; new n; send B, Y, {n, sig. B{y, n, Y}}; receive Y, B, sig. Y{y, n, B}}; ]< >

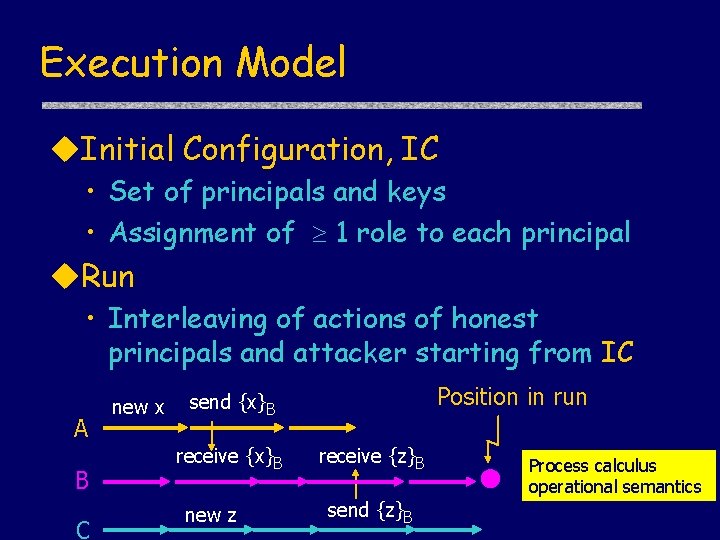
Execution Model u. Initial Configuration, IC • Set of principals and keys • Assignment of 1 role to each principal u. Run • Interleaving of actions of honest principals and attacker starting from IC A B C new x Position in run send {x}B receive {x}B new z receive {z}B send {z}B Process calculus operational semantics

Formulas true at a position in run u. Action formulas a : : = Send(P, t) | Receive (P, t) | New(P, t) | Decrypt (P, t) | Verify (P, t) u. Formulas : : = a | Has(P, t) | Fresh(P, t) | Honest(N) | Contains(t 1, t 2) | | 1 2 | x | a<a u. Modal formula [ actions ] P u. Example Has(X, secret) ( X = A X = B) Specifying secrecy

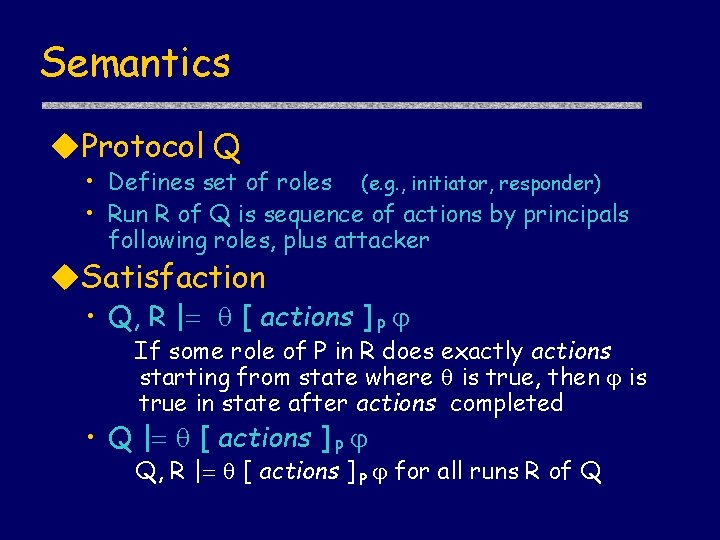
Semantics u. Protocol Q • Defines set of roles (e. g. , initiator, responder) • Run R of Q is sequence of actions by principals following roles, plus attacker u. Satisfaction • Q, R | [ actions ] P If some role of P in R does exactly actions starting from state where is true, then is true in state after actions completed • Q | [ actions ] P Q, R | [ actions ] P for all runs R of Q

Challenge-Response Property u. Specifying authentication for Initiator CR | true [ Init. CR(A, B) ] A Honest(B) ( Send(A, {A, B, m}) Receive(B, {A, B, m}) Send(B, {B, A, {n, sig. B {m, n, A}}}) Receive(A, {B, A, {n, sig. B {m, n, A}}}) ) Authentication as “matching conversations” [Bellare-Rogaway 93]

Proof System u. Goal: Formally prove security properties u. Axioms • Simple formulas provable by hand u. Inference rules • Proof steps u. Theorem • Formula obtained from axioms by application of inference rules
![Sample axioms about actions u New data true new x P HasP Sample axioms about actions u. New data • true [ new x ]P Has(P,](https://slidetodoc.com/presentation_image_h2/0e2d101352a0cf30e5495bd7c295955b/image-20.jpg)
Sample axioms about actions u. New data • true [ new x ]P Has(P, x) • true [ new x ]P Has(Y, x) Y=P u. Actions • true [ send m ]P Send(P, m) u. Knowledge • true [receive m ]P Has(P, m) u. Verify • true [ match x/sig. X{m} ] P Verify(P, m)

Reasoning about knowledge u. Pairing • Has(X, {m, n}) Has(X, m) Has(X, n) u. Encryption • Has(X, enc. K(m)) Has(X, K-1) Has(X, m)

Encryption and signature u. Public key encryption Honest(X) Decrypt(Y, enc. X{m}) X=Y u. Signature Honest(X) Verify(Y, sig. X{m}) m’ (Send(X, m’) Contains(m’, sig. X{m})
![Sample inference rules u Firstorder logic rules u Generic rules actions P Sample inference rules u. First-order logic rules u. Generic rules [ actions ]P](https://slidetodoc.com/presentation_image_h2/0e2d101352a0cf30e5495bd7c295955b/image-23.jpg)
Sample inference rules u. First-order logic rules u. Generic rules [ actions ]P

Bidding conventions (motivation) u. Blackwood response to 4 NT – 5§ : – 5¨ : – 5© : – 5ª : 0 or 4 aces 1 ace 2 aces 3 aces u. Reasoning • If my partner is following Blackwood, then if she bid 5©, she must have 2 aces

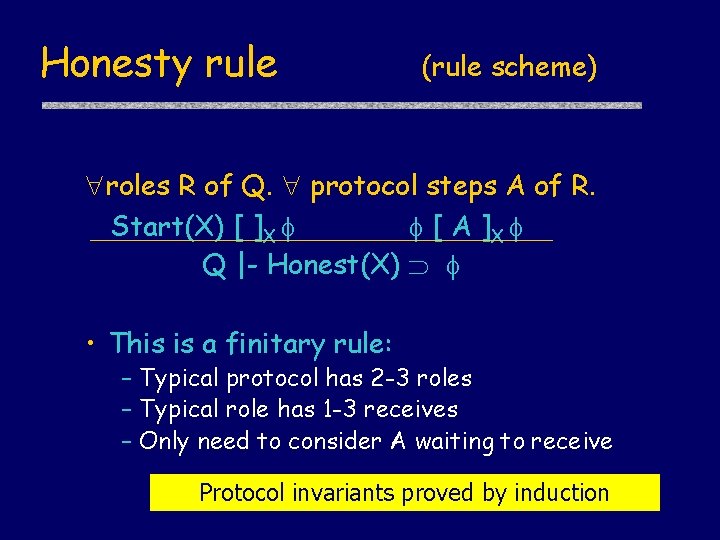
Honesty rule (rule scheme) roles R of Q. protocol steps A of R. Start(X) [ ]X [ A ]X Q |- Honest(X) • This is a finitary rule: – Typical protocol has 2 -3 roles – Typical role has 1 -3 receives – Only need to consider A waiting to receive Protocol invariants proved by induction

Honesty rule (example use) roles R of Q. protocol steps A of R. Start(X) [ ]X [ A ]X Q |- Honest(X) • Example use: – If Y receives a message m from X, and – Honest(X) (Sent(X, m) Received(X, m’)) – then Y can conclude Honest(X) Received(X, m’)) Proved using honesty rule

Correctness of CR Init. CR(A, X) = [ new m; send A, X, {m, A}; receive X, A, {x, sig. X{m, x, A}}; send A, X, sig. A{m, x, X}}; ] Resp. CR(B) = [ receive Y, B, {y, Y}; new n; send B, Y, {n, sig. B{y, n, Y}}; receive Y, B, sig. Y{y, n, B}}; ] CR |- true [ Init. CR(A, B) ] A Honest(B) ( Send(A, {A, B, m}) Receive(B, {A, B, m}) Send(B, {B, A, {n, sig. B {m, n, A}}}) Receive(A, {B, A, {n, sig. B {m, n, A}}}) ) Authentication as “matching conversations” [Bellare-Rogaway 93]

Correctness of CR – step 1 Init. CR(A, X) = [ new m; send A, X, {m, A}; receive X, A, {x, sig. X{m, x, A}}; send A, X, sig. A{m, x, X}}; ] Resp. CR(B) = [ receive Y, B, {y, Y}; new n; send B, Y, {n, sig. B{y, n, Y}}; receive Y, B, sig. Y{y, n, B}}; ] 1. A reasons about her own actions CR |- true [ Init. CR(A, B) ] A Verify(A, sig. B {m, n, A})

Correctness of CR – step 2 Init. CR(A, X) = [ new m; send A, X, {m, A}; receive X, A, {x, sig. X{m, x, A}}; send A, X, sig. A{m, x, X}}; ] Resp. CR(B) = [ receive Y, B, {y, Y}; new n; send B, Y, {n, sig. B{y, n, Y}}; receive Y, B, sig. Y{y, n, B}}; ] 2. Properties of signatures CR |- true [ Init. CR(A, B) ] A Honest(B) m’ (Send(B, m’) Contains(m’, sig. B {m, n, A}) Recall signature axiom

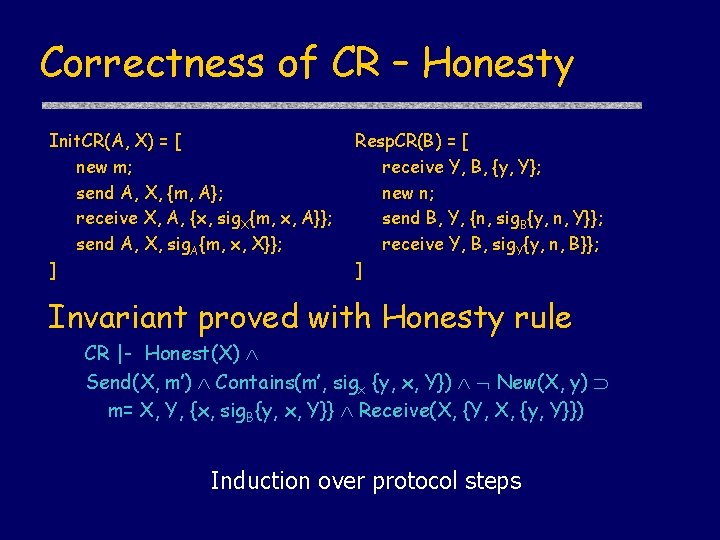
Correctness of CR – Honesty Init. CR(A, X) = [ new m; send A, X, {m, A}; receive X, A, {x, sig. X{m, x, A}}; send A, X, sig. A{m, x, X}}; ] Resp. CR(B) = [ receive Y, B, {y, Y}; new n; send B, Y, {n, sig. B{y, n, Y}}; receive Y, B, sig. Y{y, n, B}}; ] Invariant proved with Honesty rule CR |- Honest(X) Send(X, m’) Contains(m’, sigx {y, x, Y}) New(X, y) m= X, Y, {x, sig. B{y, x, Y}} Receive(X, {Y, X, {y, Y}}) Induction over protocol steps

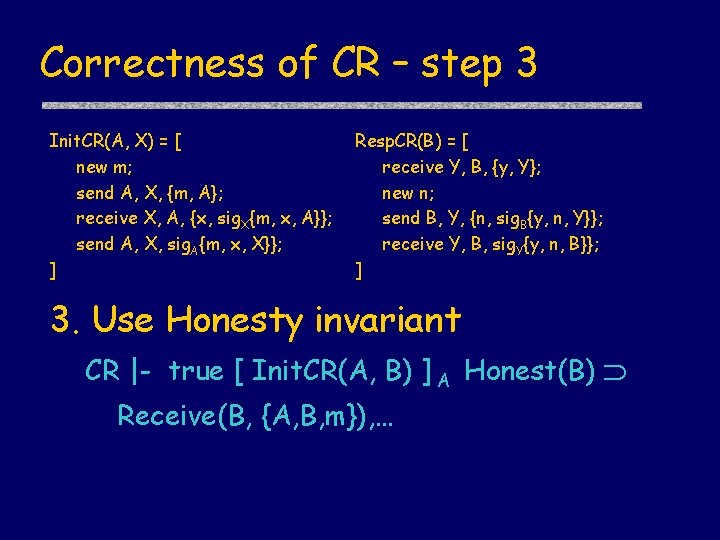
Correctness of CR – step 3 Init. CR(A, X) = [ new m; send A, X, {m, A}; receive X, A, {x, sig. X{m, x, A}}; send A, X, sig. A{m, x, X}}; ] Resp. CR(B) = [ receive Y, B, {y, Y}; new n; send B, Y, {n, sig. B{y, n, Y}}; receive Y, B, sig. Y{y, n, B}}; ] 3. Use Honesty invariant CR |- true [ Init. CR(A, B) ] A Honest(B) Receive(B, {A, B, m}), …

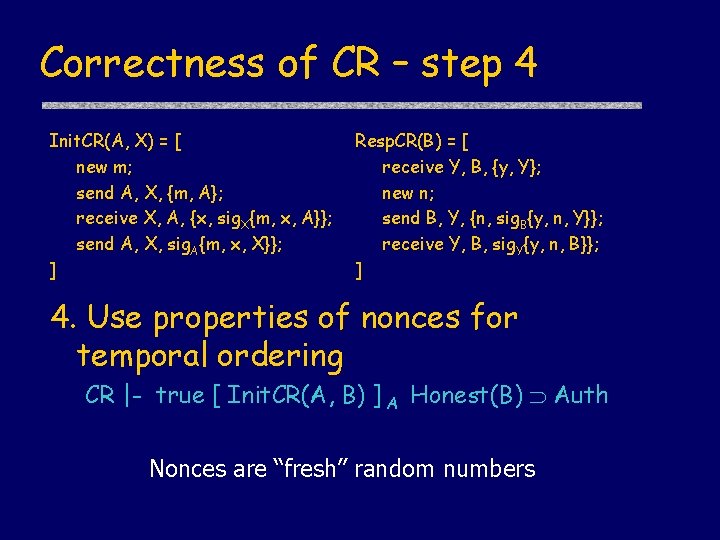
Correctness of CR – step 4 Init. CR(A, X) = [ new m; send A, X, {m, A}; receive X, A, {x, sig. X{m, x, A}}; send A, X, sig. A{m, x, X}}; ] Resp. CR(B) = [ receive Y, B, {y, Y}; new n; send B, Y, {n, sig. B{y, n, Y}}; receive Y, B, sig. Y{y, n, B}}; ] 4. Use properties of nonces for temporal ordering CR |- true [ Init. CR(A, B) ] A Honest(B) Auth Nonces are “fresh” random numbers

Complete proof

We have a proof. So what? u Soundness Theorem: • If Q |- then Q |= • If is a theorem then is a valid formula u holds in any step in any run of protocol Q • Unbounded number of participants • Dolev-Yao intruder

Using PCL: Summary u. Modeling the protocol • Program for each protocol role u. Modeling security properties • Using PCL syntax • Authentication, secrecy easily expressed u. Proving security properties • Using PCL proof system • Soundness theorem guarantees that provable properties hold in all protocol runs Example: C. He, M. Sundararajan, A. Datta, A. Derek, J. C. Mitchell, modular correctness proof of TLS and IEEE 802. 11 i, ACM CCS 2005 A

Challenge-Response programs (1) m, A A n, sig. B {m, n, A} B sig. A {m, n, B} Init. CR(A, X) = [ new m; send A, X, {m, A}; receive X, A, {x, sig. X{m, x, A}}; send A, X, sig. A{m, x, X}}; ]< > Resp. CR(B) = [ receive Y, B, {y, Y}; new n; send B, Y, {n, sig. B{y, n, Y}}; receive Y, B, sig. Y{y, n, B}}; ]< >

Challenge-Response Property (2) u. Specifying authentication for Initiator CR | true [ Init. CR(A, B) ] A Honest(B) ( Send(A, {A, B, m}) Receive(B, {A, B, m}) Send(B, {B, A, {n, sig. B {m, n, A}}}) Receive(A, {B, A, {n, sig. B {m, n, A}}}) )

Challenge-Response Proof (3)

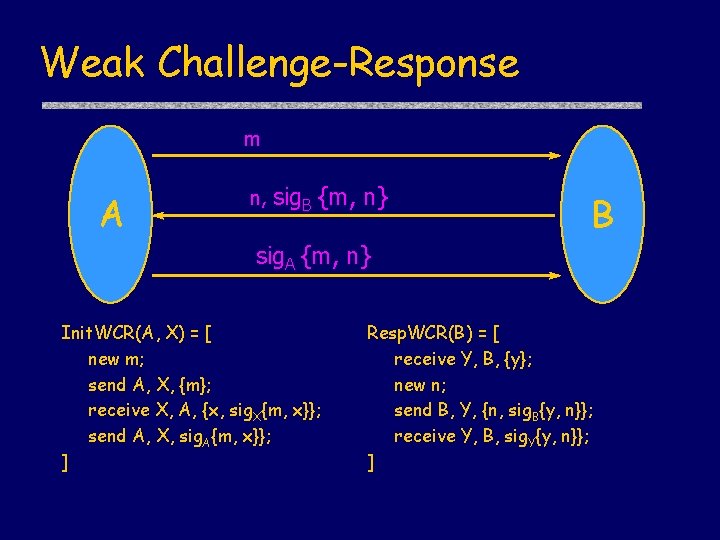
Weak Challenge-Response m A n, sig. B {m, n} B sig. A {m, n} Init. WCR(A, X) = [ new m; send A, X, {m}; receive X, A, {x, sig. X{m, x}}; send A, X, sig. A{m, x}}; ] Resp. WCR(B) = [ receive Y, B, {y}; new n; send B, Y, {n, sig. B{y, n}}; receive Y, B, sig. Y{y, n}}; ]

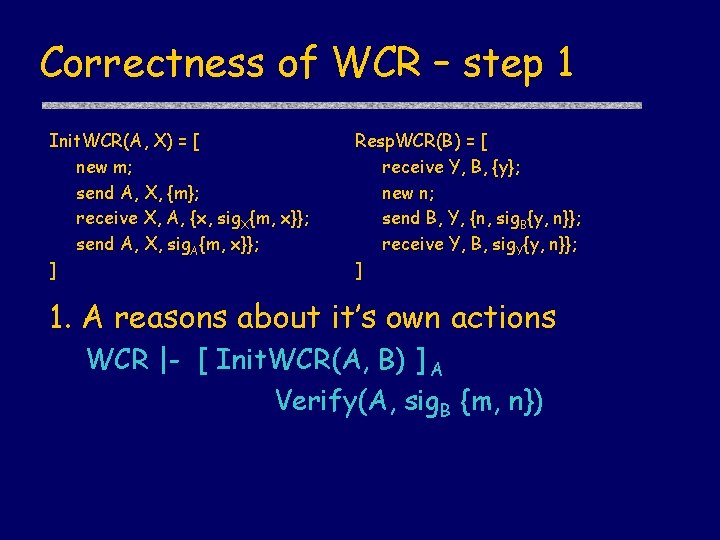
Correctness of WCR – step 1 Init. WCR(A, X) = [ new m; send A, X, {m}; receive X, A, {x, sig. X{m, x}}; send A, X, sig. A{m, x}}; ] Resp. WCR(B) = [ receive Y, B, {y}; new n; send B, Y, {n, sig. B{y, n}}; receive Y, B, sig. Y{y, n}}; ] 1. A reasons about it’s own actions WCR |- [ Init. WCR(A, B) ] A Verify(A, sig. B {m, n})

Correctness of WCR – step 2 Init. WCR(A, X) = [ new m; send A, X, {m}; receive X, A, {x, sig. X{m, x}}; send A, X, sig. A{m, x}}; ] Resp. WCR(B) = [ receive Y, B, {y}; new n; send B, Y, {n, sig. B{y, n}}; receive Y, B, sig. Y{y, n}}; ] 2. Properties of signatures WCR |- [ Init. CR(A, B) ] A Honest(B) m’ (Send(B, m’) Contains(m’, sig. B {m, n, A})

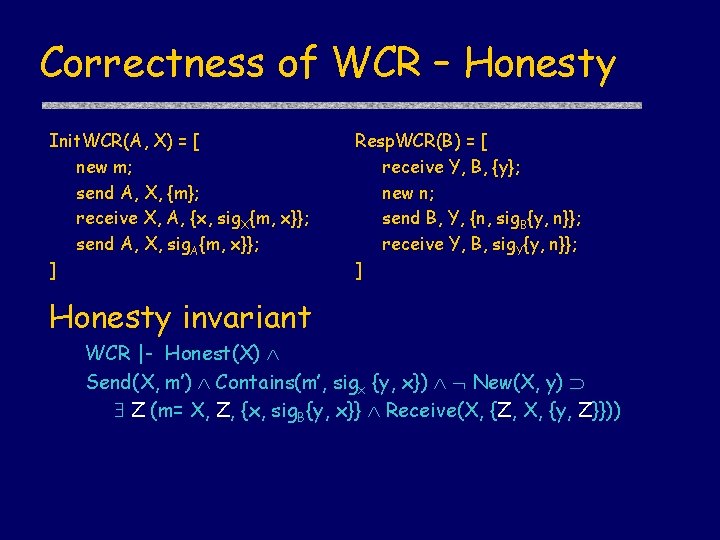
Correctness of WCR – Honesty Init. WCR(A, X) = [ new m; send A, X, {m}; receive X, A, {x, sig. X{m, x}}; send A, X, sig. A{m, x}}; ] Resp. WCR(B) = [ receive Y, B, {y}; new n; send B, Y, {n, sig. B{y, n}}; receive Y, B, sig. Y{y, n}}; ] Honesty invariant WCR |- Honest(X) Send(X, m’) Contains(m’, sigx {y, x}) New(X, y) Z (m= X, Z, {x, sig. B{y, x}} Receive(X, {Z, X, {y, Z}}))

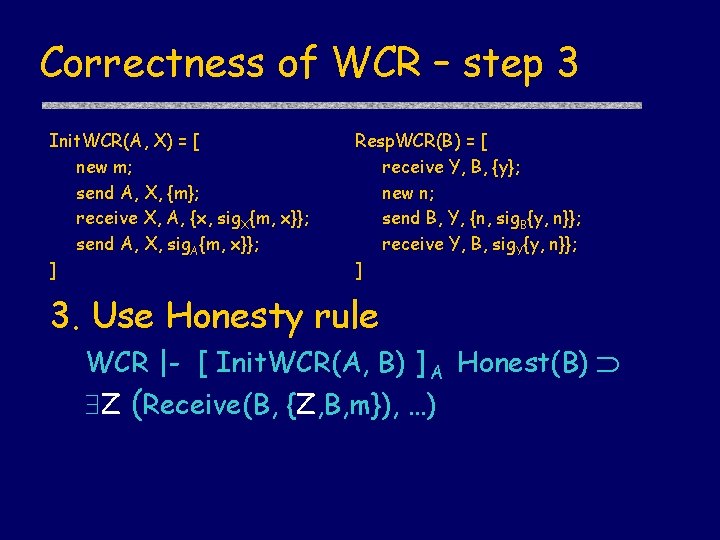
Correctness of WCR – step 3 Init. WCR(A, X) = [ new m; send A, X, {m}; receive X, A, {x, sig. X{m, x}}; send A, X, sig. A{m, x}}; ] Resp. WCR(B) = [ receive Y, B, {y}; new n; send B, Y, {n, sig. B{y, n}}; receive Y, B, sig. Y{y, n}}; ] 3. Use Honesty rule WCR |- [ Init. WCR(A, B) ] A Honest(B) Z (Receive(B, {Z, B, m}), …)

Result u. WCR does not have the strong authentication property for the initiator u. Counterexample • Intruder can forge sender’s and receiver’s identity in first two messages – A -> X(B) – X(C) -> B – B -> X(C) – X(B) ->A m m n, sig. B(m, n)