Security Analysis of Network Protocols Anupam Datta Stanford


![IEEE 802. 11 i wireless security [2004] Wireless Device Uses crypto: encryption , hash, IEEE 802. 11 i wireless security [2004] Wireless Device Uses crypto: encryption , hash,](https://slidetodoc.com/presentation_image/c7b71b5c62e8d2d3c61b5a750c2d4317/image-5.jpg)
![Divide-and-Conquer paradigm Central Problem 1 Result: Protocol Derivation System [DDMP 03 -05] • Incremental Divide-and-Conquer paradigm Central Problem 1 Result: Protocol Derivation System [DDMP 03 -05] • Incremental](https://slidetodoc.com/presentation_image/c7b71b5c62e8d2d3c61b5a750c2d4317/image-6.jpg)
![Combining logic and cryptography Symbolic model [NS 78, DY 84] Central Problem 2 - Combining logic and cryptography Symbolic model [NS 78, DY 84] Central Problem 2 -](https://slidetodoc.com/presentation_image/c7b71b5c62e8d2d3c61b5a750c2d4317/image-7.jpg)
![Applied to industrial protocols IEEE 802. 11 i authentication protocol [IEEE Standards; 2004] (Attack! Applied to industrial protocols IEEE 802. 11 i authentication protocol [IEEE Standards; 2004] (Attack!](https://slidetodoc.com/presentation_image/c7b71b5c62e8d2d3c61b5a750c2d4317/image-8.jpg)



![Challenge Response: Property Modal form: [ actions ]P • precondition: Fresh(A, m) • actions: Challenge Response: Property Modal form: [ actions ]P • precondition: Fresh(A, m) • actions:](https://slidetodoc.com/presentation_image/c7b71b5c62e8d2d3c61b5a750c2d4317/image-15.jpg)
![Proof System Sample Axioms: • Reasoning about possession: – [receive m ]A Has(A, m) Proof System Sample Axioms: • Reasoning about possession: – [receive m ]A Has(A, m)](https://slidetodoc.com/presentation_image/c7b71b5c62e8d2d3c61b5a750c2d4317/image-16.jpg)



![Composition Rules Invariant weakening rule |- […]P ’ |- […]P Sequential Composition |- [ Composition Rules Invariant weakening rule |- […]P ’ |- […]P Sequential Composition |- [](https://slidetodoc.com/presentation_image/c7b71b5c62e8d2d3c61b5a750c2d4317/image-21.jpg)

![Two worlds Symbolic model [NS 78, DY 84, …] Complexity-theoretic model [GM 84, …] Two worlds Symbolic model [NS 78, DY 84, …] Complexity-theoretic model [GM 84, …]](https://slidetodoc.com/presentation_image/c7b71b5c62e8d2d3c61b5a750c2d4317/image-24.jpg)
![Soundness of proof system Information-theoretic reasoning [new u]X (Y X) Indistinguishable(Y, u) Complexity-theoretic reductions Soundness of proof system Information-theoretic reasoning [new u]X (Y X) Indistinguishable(Y, u) Complexity-theoretic reductions](https://slidetodoc.com/presentation_image/c7b71b5c62e8d2d3c61b5a750c2d4317/image-26.jpg)


- Slides: 30

Security Analysis of Network Protocols Anupam Datta Stanford University May 18, 2005

This talk is about… Industrial network security protocols • Internet Engineering Task Force (IETF) Standards – – – SSL/TLS - web authentication IPSec - corporate VPNs Mobile IPv 6 – routing security Kerberos - network authentication GDOI – secure group communication • IEEE Standards Working Group – 802. 11 i - wireless security And methods for their security analysis • Security proof in some model; or • Identify attacks Earlier talk by John Mitchell

Outline Part I: Overview • Motivation • Central problems – Divide and Conquer paradigm – Combining logic and cryptography • Results Part II: Protocol Composition Logic • Compositional Reasoning • Complexity-theoretic foundations

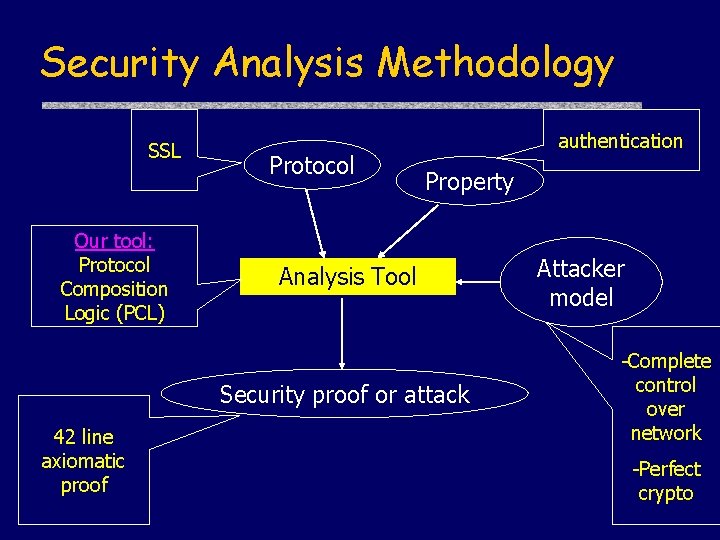
Security Analysis Methodology SSL Our tool: Protocol Composition Logic (PCL) Protocol authentication Property Analysis Tool Security proof or attack 42 line axiomatic proof Attacker model -Complete control over network -Perfect crypto
![IEEE 802 11 i wireless security 2004 Wireless Device Uses crypto encryption hash IEEE 802. 11 i wireless security [2004] Wireless Device Uses crypto: encryption , hash,](https://slidetodoc.com/presentation_image/c7b71b5c62e8d2d3c61b5a750c2d4317/image-5.jpg)
IEEE 802. 11 i wireless security [2004] Wireless Device Uses crypto: encryption , hash, … Access Point Authentication Server 802. 11 Association EAP/802. 1 X/RADIUS Authentication 4 -way handshake Group key handshake Data communication • Divide-and-conquer paradigm • Combining logic and cryptography
![DivideandConquer paradigm Central Problem 1 Result Protocol Derivation System DDMP 03 05 Incremental Divide-and-Conquer paradigm Central Problem 1 Result: Protocol Derivation System [DDMP 03 -05] • Incremental](https://slidetodoc.com/presentation_image/c7b71b5c62e8d2d3c61b5a750c2d4317/image-6.jpg)
Divide-and-Conquer paradigm Central Problem 1 Result: Protocol Derivation System [DDMP 03 -05] • Incremental protocol construction Result: Protocol Composition Logic (PCL) [DDDMP 01 -05] • Compositional correctness proofs Related work: [Heintze-Tygar 96], [Lynch 99], [Sheyner. Wing 00], [Canetti 01], [Pfitzmann-Waidner 01], … Composition is a hard problem in security
![Combining logic and cryptography Symbolic model NS 78 DY 84 Central Problem 2 Combining logic and cryptography Symbolic model [NS 78, DY 84] Central Problem 2 -](https://slidetodoc.com/presentation_image/c7b71b5c62e8d2d3c61b5a750c2d4317/image-7.jpg)
Combining logic and cryptography Symbolic model [NS 78, DY 84] Central Problem 2 - Perfect cryptography assumption + Idealization => tools and techniques Complexity-theoretic model [GM 84] + More detailed model; probabilistic guarantees - Hand-proofs very hard; no automation Result: Computational PCL + Logical proof methods + Complexity-theoretic crypto model Related work: [DDMST 05] [Mitchell-Scedrov et al 98 -04], [Abadi. Rogaway 00], [Backes-Pfitzmann-Waidner 03 -04], [Micciancio. Warinschi 04]
![Applied to industrial protocols IEEE 802 11 i authentication protocol IEEE Standards 2004 Attack Applied to industrial protocols IEEE 802. 11 i authentication protocol [IEEE Standards; 2004] (Attack!](https://slidetodoc.com/presentation_image/c7b71b5c62e8d2d3c61b5a750c2d4317/image-8.jpg)
Applied to industrial protocols IEEE 802. 11 i authentication protocol [IEEE Standards; 2004] (Attack! Fix adopted by IEEE WG) [He et al] IKEv 2 [IETF Internet Draft; 2004] [Aron et al] TLS/SSL [RFC 2246; 1999] [He et al] Mobile IPv 6 [RFC 3775; 2004] (New Attack!) [Roy et al] Kerberos V 5 [IETF Internet Draft; 2004] [Cervasato et al] GDOI Secure Group Communication protocol [RFC 3547; 2003] (Attack! Fix adopted by IETF WG) [Meadows et al]

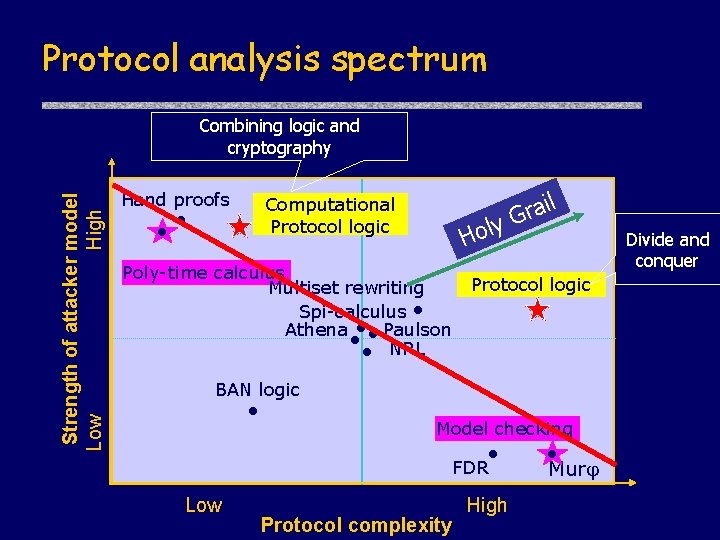
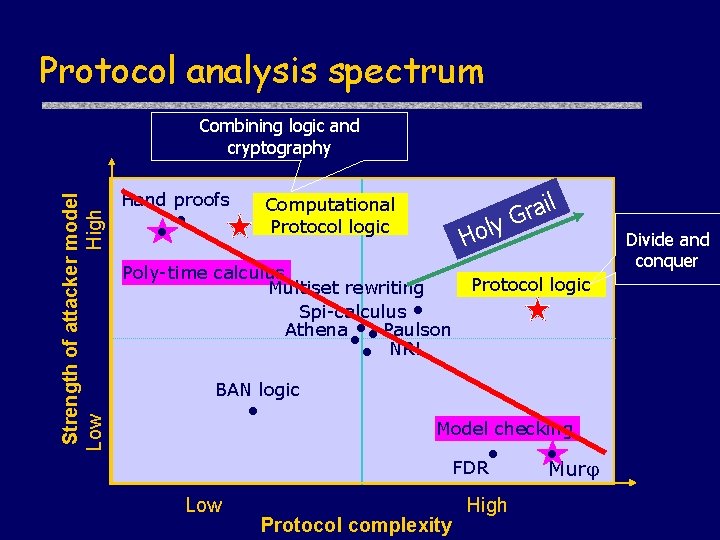
Protocol analysis spectrum Strength of attacker model Low High Combining logic and cryptography Hand proofs Computational Protocol logic y Hol Poly-time calculus Multiset rewriting Spi-calculus Athena Paulson NRL il a r G Protocol logic BAN logic Model checking FDR Low Protocol complexity High Mur Divide and conquer

Outline Part I: Overview Part II: Protocol Composition Logic • Compositional Reasoning • Complexity-theoretic foundations

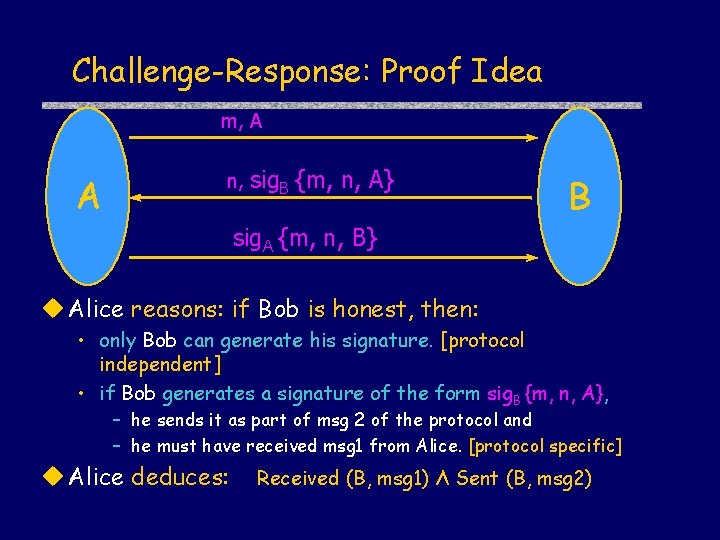
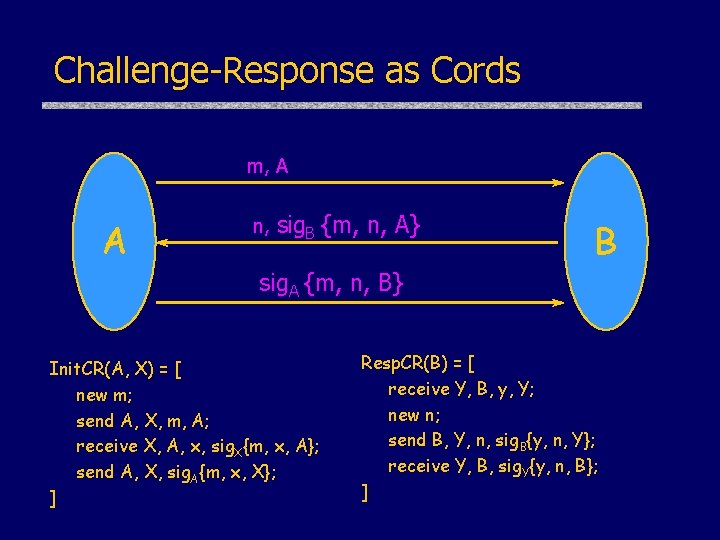
Challenge-Response: Proof Idea m, A A n, sig. B {m, n, A} B sig. A {m, n, B} Alice reasons: if Bob is honest, then: • only Bob can generate his signature. [protocol independent] • if Bob generates a signature of the form sig. B {m, n, A}, – he sends it as part of msg 2 of the protocol and – he must have received msg 1 from Alice. [protocol specific] Alice deduces: Received (B, msg 1) Λ Sent (B, msg 2)

Reasoning method Reason about local information • I know my own actions Incorporate knowledge of protocol • Honest people faithfully follow protocol No explicit reasoning about intruder • Absence of bad action expressed as a positive property of good actions – E. g. , honest agent’s signature can be produced only by the agent Distinguishes our method from existing techniques

Formalism Cord calculus • Protocol programming language • Execution model (Symbolic/“Dolev-Yao”) Protocol logic • Expressing protocol properties Proof system • Proving protocol properties • Soundness theorem

Challenge-Response as Cords m, A A n, sig. B {m, n, A} B sig. A {m, n, B} Init. CR(A, X) = [ new m; send A, X, m, A; receive X, A, x, sig. X{m, x, A}; send A, X, sig. A{m, x, X}; ] Resp. CR(B) = [ receive Y, B, y, Y; new n; send B, Y, n, sig. B{y, n, Y}; receive Y, B, sig. Y{y, n, B}; ]
![Challenge Response Property Modal form actions P precondition FreshA m actions Challenge Response: Property Modal form: [ actions ]P • precondition: Fresh(A, m) • actions:](https://slidetodoc.com/presentation_image/c7b71b5c62e8d2d3c61b5a750c2d4317/image-15.jpg)
Challenge Response: Property Modal form: [ actions ]P • precondition: Fresh(A, m) • actions: [ Initiator role actions ]A • postcondition: Honest(B) Actions. In. Order( send(A, {A, B, m}), receive(B, {A, B, m}), send(B, {B, A, {n, sig. B {m, n, A}}}), receive(A, {B, A, {n, sig. B {m, n, A}}}) )
![Proof System Sample Axioms Reasoning about possession receive m A HasA m Proof System Sample Axioms: • Reasoning about possession: – [receive m ]A Has(A, m)](https://slidetodoc.com/presentation_image/c7b71b5c62e8d2d3c61b5a750c2d4317/image-16.jpg)
Proof System Sample Axioms: • Reasoning about possession: – [receive m ]A Has(A, m) – Has(A, {m, n}) Has(A, m) Has(A, n) • Reasoning about crypto primitives: – Honest(X) Decrypt(Y, enc. X{m}) X=Y – Honest(X) Verify(Y, sig. X{m}) m’ (Send(X, m’) Contains(m’, sig. X{m}) Soundness Theorem: Every provable formula is valid

Outline Part I: Overview Part II: Protocol Composition Logic • Compositional Reasoning • Complexity-theoretic foundations

Reasoning about Composition Non-destructive Combination: Ensure combined parts do not interfere – In logic: invariance assertions Additive Combination: Accumulate security properties of combined parts, assuming they do not interfere – In logic: before-after assertions

Proof steps (Intuition) Protocol independent reasoning • Has(A, {m, n}) Has(A, m) Has(A, n) • Still good: unaffected by composition Protocol specific reasoning • “if honest Bob generates a signature of the form sig. B {m, n, A}, – he sends it as part of msg 2 of the protocol and – he must have received msg 1 from Alice” • Could break: Bob’s signature from one protocol could be used to attack another Technically: • Protocol-specific proof steps use invariants • Invariants must be preserved for safe composition

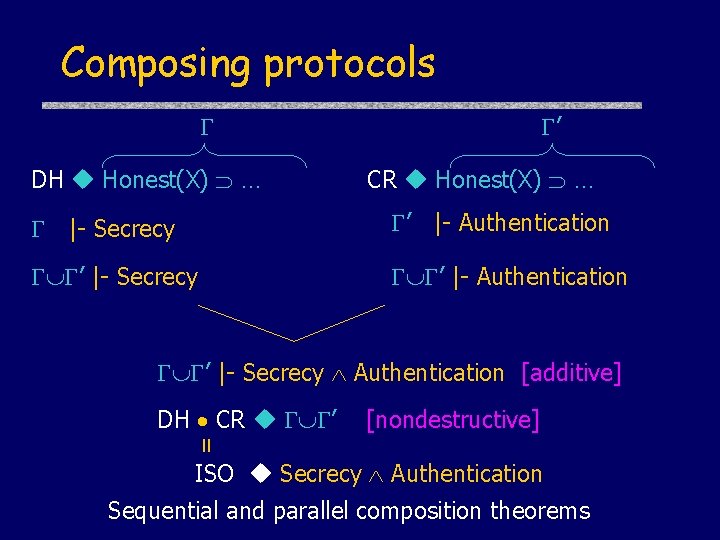
Composing protocols DH Honest(X) … ’ CR Honest(X) … |- Secrecy ’ |- Authentication ’ |- Secrecy Authentication [additive] [nondestructive] = DH CR ’ ISO Secrecy Authentication Sequential and parallel composition theorems
![Composition Rules Invariant weakening rule P P Sequential Composition Composition Rules Invariant weakening rule |- […]P ’ |- […]P Sequential Composition |- [](https://slidetodoc.com/presentation_image/c7b71b5c62e8d2d3c61b5a750c2d4317/image-21.jpg)
Composition Rules Invariant weakening rule |- […]P ’ |- […]P Sequential Composition |- [ S ] P |- [ T ] P |- [ ST ] P Prove invariants from protocol Q Q’

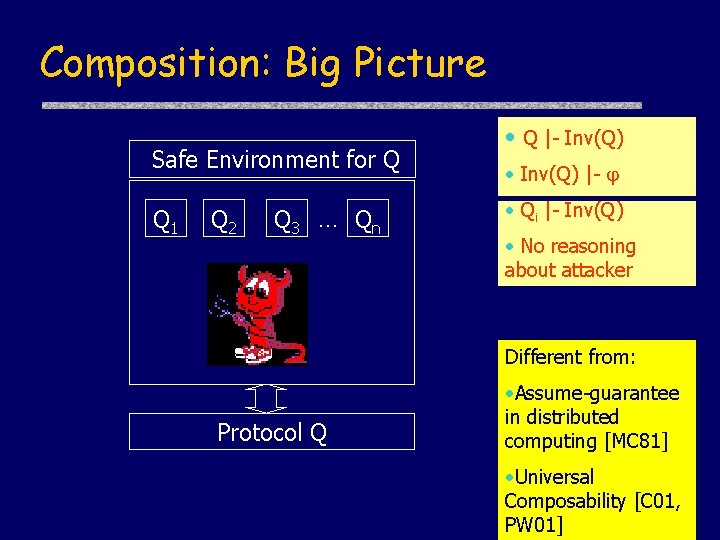
Composition: Big Picture Safe Environment for Q Q 1 Q 2 Q 3 … Qn • Q |- Inv(Q) • Inv(Q) |- • Qi |- Inv(Q) • No reasoning about attacker Different from: Protocol Q • Assume-guarantee in distributed computing [MC 81] • Universal Composability [C 01, PW 01]

Outline Part I: Overview Part II: Protocol Composition Logic • Compositional Reasoning • Complexity-theoretic foundations
![Two worlds Symbolic model NS 78 DY 84 Complexitytheoretic model GM 84 Two worlds Symbolic model [NS 78, DY 84, …] Complexity-theoretic model [GM 84, …]](https://slidetodoc.com/presentation_image/c7b71b5c62e8d2d3c61b5a750c2d4317/image-24.jpg)
Two worlds Symbolic model [NS 78, DY 84, …] Complexity-theoretic model [GM 84, …] Attacker actions -Fixed set of actions, e. g. , decryption with known key (ABSTRACTION) + Any probabilistic polytime computation Security properties -Idealized, e. g. , secret message = not possessing atomic term representing message (ABSTRACTION) + Fine-grained, e. g. , secret message = no partial information about bitstring representation Analysis methods + Successful array of tools and techniques; automation - Hand-proofs are difficult, error-prone; no automation Can we get the best of both worlds?

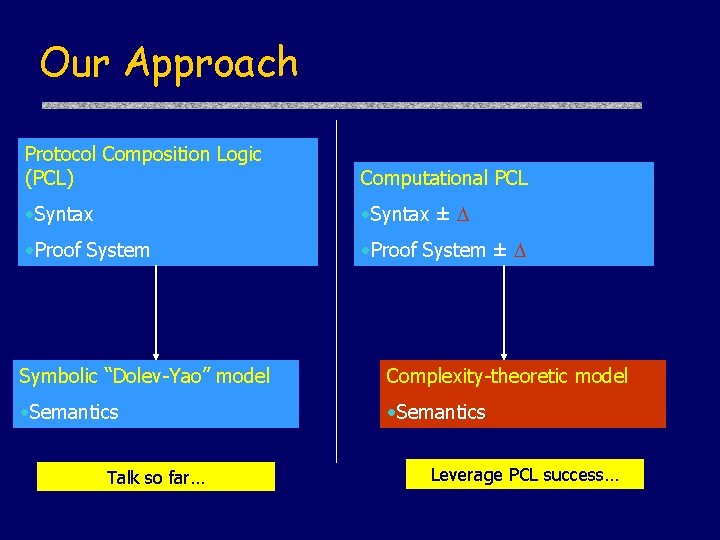
Our Approach Protocol Composition Logic (PCL) Computational PCL • Syntax ± • Proof System ± Symbolic “Dolev-Yao” model Complexity-theoretic model • Semantics Talk so far… Leverage PCL success…
![Soundness of proof system Informationtheoretic reasoning new uX Y X IndistinguishableY u Complexitytheoretic reductions Soundness of proof system Information-theoretic reasoning [new u]X (Y X) Indistinguishable(Y, u) Complexity-theoretic reductions](https://slidetodoc.com/presentation_image/c7b71b5c62e8d2d3c61b5a750c2d4317/image-26.jpg)
Soundness of proof system Information-theoretic reasoning [new u]X (Y X) Indistinguishable(Y, u) Complexity-theoretic reductions Source(Y, u, {m}X) Decrypts(X, {m}X) Honest(X, Y) (Z X, Y) Indistinguishable(Z, u) Reduction to IND-CCA 2 -secure encryption scheme Asymptotic calculations Sum of two negligible functions is a negligible function

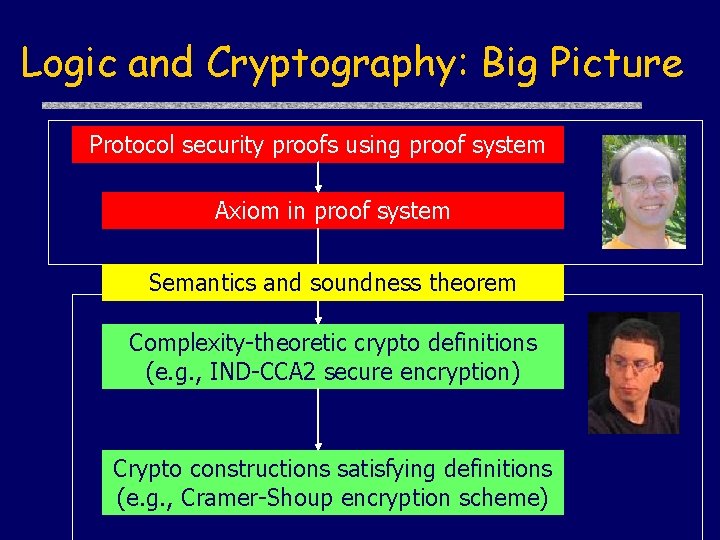
Logic and Cryptography: Big Picture Protocol security proofs using proof system Axiom in proof system Semantics and soundness theorem Complexity-theoretic crypto definitions (e. g. , IND-CCA 2 secure encryption) Crypto constructions satisfying definitions (e. g. , Cramer-Shoup encryption scheme)

Summary Methodology: • Divide-and-conquer paradigm in security • Combining logic and cryptography Applications: • IEEE 802. 11 i (Attack! Fix adopted by IEEE WG) • GDOI Secure Group Communication protocol [RFC 3547; 2003] • • (Composition Attack! Fix adopted by IETF WG) IKEv 2 [IETF Internet Draft; 2004] TLS [RFC 2246; 1999] Kerberos V 5 [IETF Internet Draft; 2004] Mobile IPv 6 [RFC 3775; 2004] (New Attack!)

Protocol analysis spectrum Strength of attacker model Low High Combining logic and cryptography Hand proofs Computational Protocol logic y Hol Poly-time calculus Multiset rewriting Spi-calculus Athena Paulson NRL il a r G Protocol logic BAN logic Model checking FDR Low Protocol complexity High Mur Divide and conquer

Selected Publications A. Datta, A. Derek, J. C. Mitchell, D. Pavlovic • A derivation system and compositional logic for security protocols [CSFW 03, JCS 05 special issue] • Secure Protocol Composition [MFPS 03] • Abstraction and refinement in protocol derivation [CSFW 04] A. Datta, A. Derek, J. C. Mitchell, V. Shmatikov, M. Turuani. Probabilistic polynomial time semantics for a protocol security logic [ICALP 05] C. He, M. Sundararajan, A. Datta, A. Derek, J. C. Mitchell. A Modular Correctness Proof of TLS and IEEE 802. 11 i [In submission] www. stanford. edu/~danupam