CS 259 Protocol Composition Logic PCL Part II








![Diffie-Hellman: Property u. Formula utrue [ new a ] A Fresh(A, ga) Diffie-Hellman: Property u. Formula utrue [ new a ] A Fresh(A, ga)](https://slidetodoc.com/presentation_image_h/9a846fa0b9ce31d4a79e5342ba269695/image-20.jpg)

![Sequencing Rule [S]P [ T ] P [ ST ] P u. Is this Sequencing Rule [S]P [ T ] P [ ST ] P u. Is this](https://slidetodoc.com/presentation_image_h/9a846fa0b9ce31d4a79e5342ba269695/image-22.jpg)


![Two worlds Symbolic model [NS 78, DY 84, …] Complexity-theoretic model [GM 84, …] Two worlds Symbolic model [NS 78, DY 84, …] Complexity-theoretic model [GM 84, …]](https://slidetodoc.com/presentation_image_h/9a846fa0b9ce31d4a79e5342ba269695/image-27.jpg)




![Inductive Semantics u [[ 1 2]] (T, D, ) = [[ 1]] (T, D, Inductive Semantics u [[ 1 2]] (T, D, ) = [[ 1]] (T, D,](https://slidetodoc.com/presentation_image_h/9a846fa0b9ce31d4a79e5342ba269695/image-37.jpg)


- Slides: 41

CS 259 Protocol Composition Logic (PCL): Part II Anupam Datta

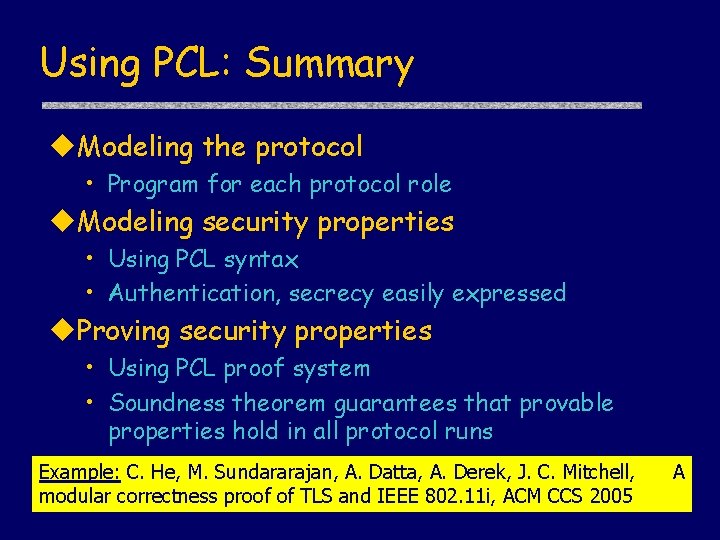
Using PCL: Summary u. Modeling the protocol • Program for each protocol role u. Modeling security properties • Using PCL syntax • Authentication, secrecy easily expressed u. Proving security properties • Using PCL proof system • Soundness theorem guarantees that provable properties hold in all protocol runs Example: C. He, M. Sundararajan, A. Datta, A. Derek, J. C. Mitchell, modular correctness proof of TLS and IEEE 802. 11 i, ACM CCS 2005 A

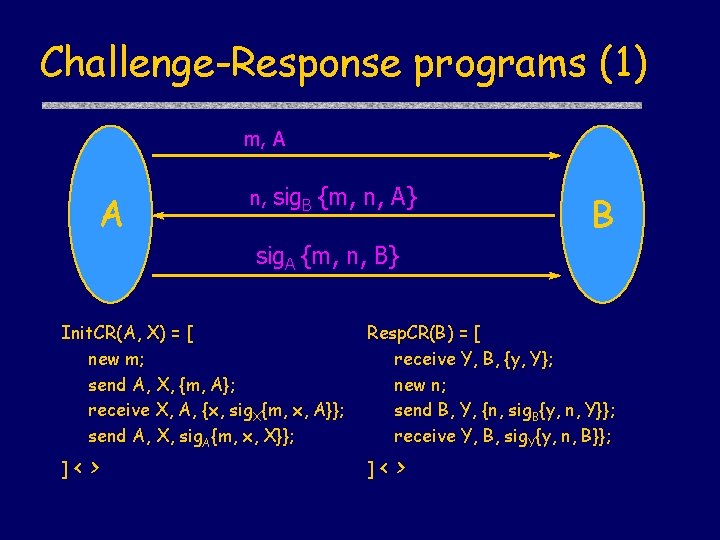
Challenge-Response programs (1) m, A A n, sig. B {m, n, A} B sig. A {m, n, B} Init. CR(A, X) = [ new m; send A, X, {m, A}; receive X, A, {x, sig. X{m, x, A}}; send A, X, sig. A{m, x, X}}; ]< > Resp. CR(B) = [ receive Y, B, {y, Y}; new n; send B, Y, {n, sig. B{y, n, Y}}; receive Y, B, sig. Y{y, n, B}}; ]< >

Challenge-Response Property (2) u. Specifying authentication for Initiator CR | true [ Init. CR(A, B) ] A Honest(B) ( Send(A, {A, B, m}) Receive(B, {A, B, m}) Send(B, {B, A, {n, sig. B {m, n, A}}}) Receive(A, {B, A, {n, sig. B {m, n, A}}}) )

Challenge-Response Proof (3)

Protocol Composition Logic: PCL u. Intuition u. Formalism • Protocol programming language • Protocol logic – Syntax – Semantics • Proof System u. Example • Signature-based challenge-response u. Composition u. Computational Soundness

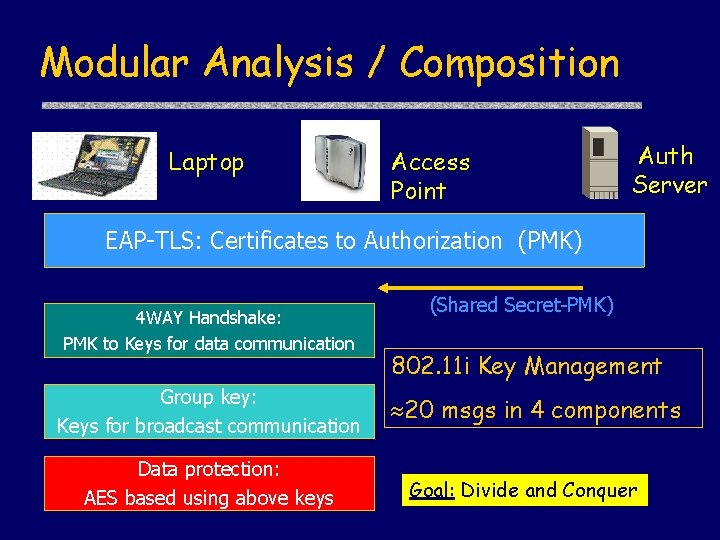
Modular Analysis / Composition Laptop Access Point Auth Server EAP-TLS: Certificates to Authorization (PMK) 4 WAY Handshake: PMK to Keys for data communication Group key: Keys for broadcast communication Data protection: AES based using above keys (Shared Secret-PMK) 802. 11 i Key Management 20 msgs in 4 components Goal: Divide and Conquer

Desiderata u. Non-destructive combination • Security guarantee for TLS in isolation must be preserved when run simultaneously with 4 WAY • Formalized as parallel composition u Additive combination • Prove 4 WAY security guarantee assuming TLS provides shared secret. Combine with separate proof of TLS guarantee. • Formalized as sequential composition

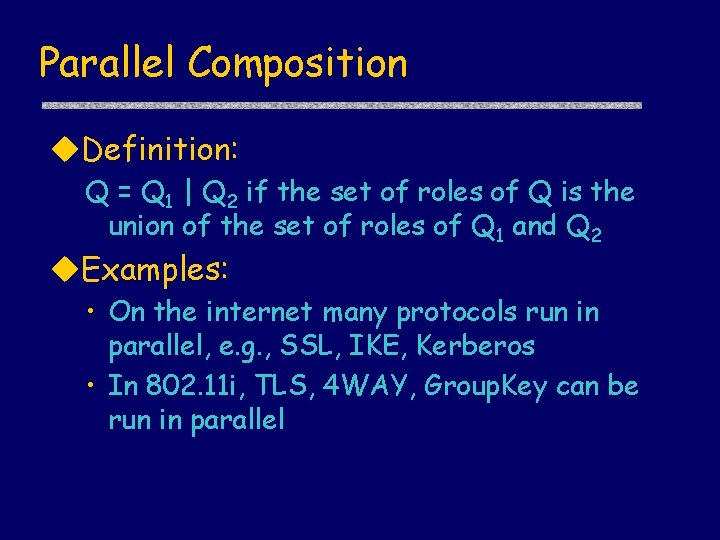
Parallel Composition u. Definition: Q = Q 1 | Q 2 if the set of roles of Q is the union of the set of roles of Q 1 and Q 2 u. Examples: • On the internet many protocols run in parallel, e. g. , SSL, IKE, Kerberos • In 802. 11 i, TLS, 4 WAY, Group. Key can be run in parallel

Compositional Proofs: Intuition u. Protocol specific reasoning • “if honest Bob generates a signature of the form sig. B {m, n, A}, – he sends it as part of msg 2 of the protocol and – he must have received msg 1 from Alice” • Could break: Bob’s signature from one protocol could be used to attack another • PCL proof system: Honesty rule u. Protocol independent reasoning • Has(A, {m, n}) Has(A, m) Has(A, n) • Still good: unaffected by composition • All other axioms and proof rules for PCL

Proof Tree Proof step might fail Axiom Security property HON rule Other rules

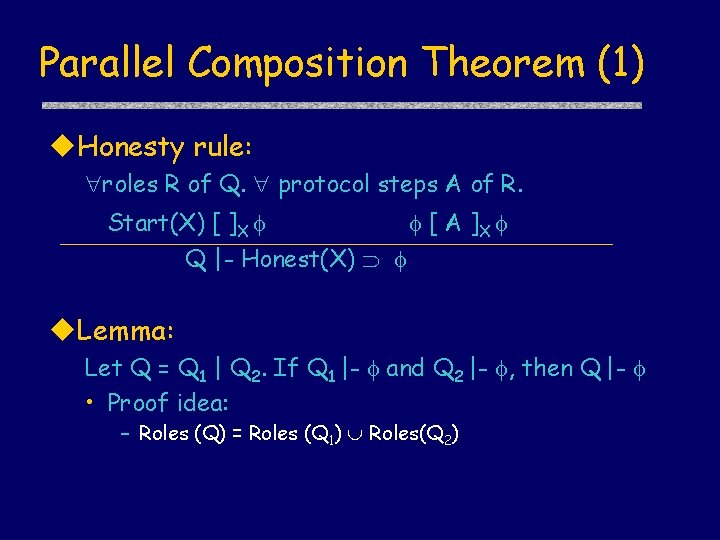
Parallel Composition Theorem (1) u. Honesty rule: roles R of Q. protocol steps A of R. Start(X) [ ]X [ A ]X Q |- Honest(X) u. Lemma: Let Q = Q 1 | Q 2. If Q 1 |- and Q 2 |- , then Q |- • Proof idea: – Roles (Q) = Roles (Q 1) Roles(Q 2)

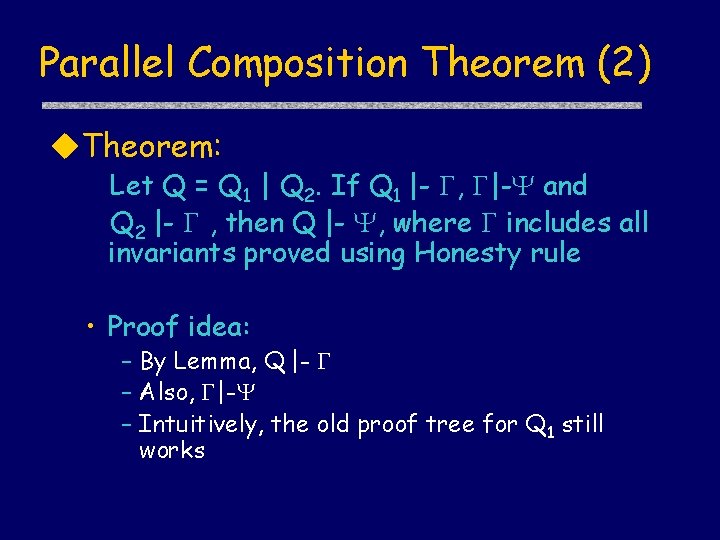
Parallel Composition Theorem (2) u. Theorem: Let Q = Q 1 | Q 2. If Q 1 |- , |- and Q 2 |- , then Q |- , where includes all invariants proved using Honesty rule • Proof idea: – By Lemma, Q |- – Also, |- – Intuitively, the old proof tree for Q 1 still works

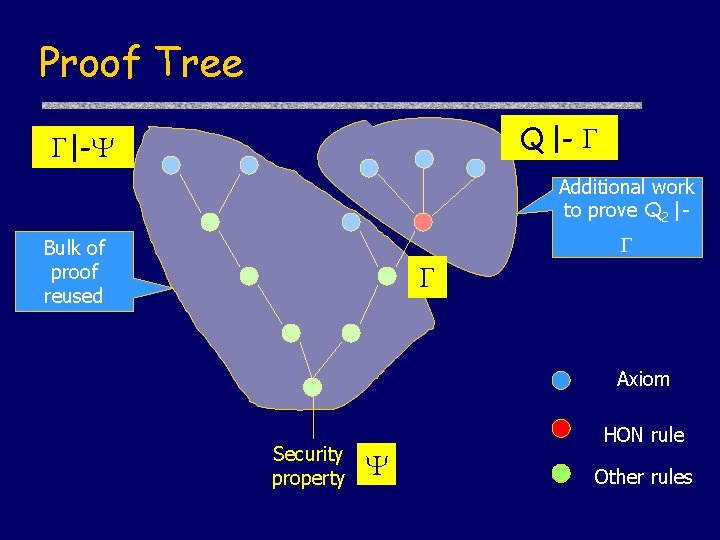
Proof Tree Q |- Q 1 |- Additional work to prove Q 2 | Bulk of proof reused Axiom Security property HON rule Other rules

Example: Challenge-Response Init. CR(A, X) = [ new m; send A, X, {m, A}; receive X, A, {x, sig. X{m, x, A}}; send A, X, sig. A{m, x, X}}; ] Resp. CR(B) = [ receive Y, B, {y, Y}; new n; send B, Y, {n, sig. B{y, n, Y}}; receive Y, B, sig. Y{y, n, B}}; ] u. Invariant proved with Honesty rule CR |- Honest(X) Send(X, m’) Contains(m’, sigx {y, x, Y}) New(X, y) m= X, Y, {x, sig. B{y, x, Y}} Receive(X, {Y, X, {y, Y}}) u. Authentication property of CR is preserved under parallel composition with any Q which satisfies this invariant

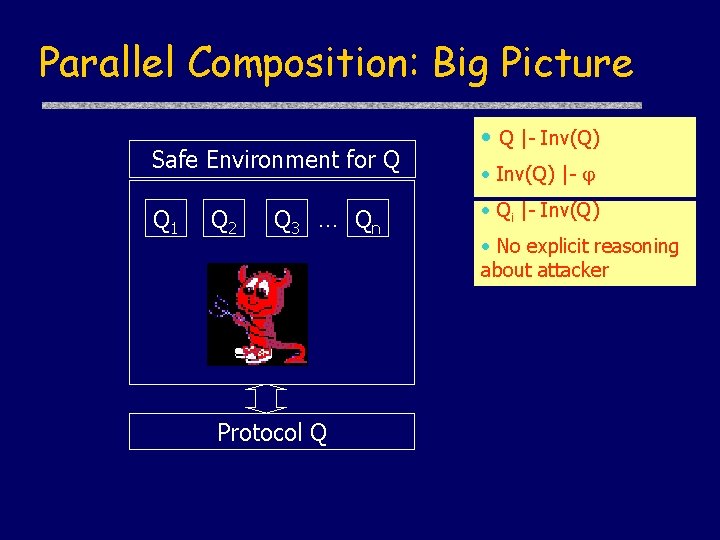
Parallel Composition: Big Picture Safe Environment for Q Q 1 Q 2 Q 3 … Qn Protocol Q • Q |- Inv(Q) • Inv(Q) |- • Qi |- Inv(Q) • No explicit reasoning about attacker

Desiderata u. Non-destructive combination • Security guarantee for TLS in isolation must be preserved when run simultaneously with 4 WAY • Formalized as parallel composition u Additive combination • Prove 4 WAY security guarantee assuming TLS provides shared secret. Combine with separate proof of TLS guarantee. • Formalized as sequential composition

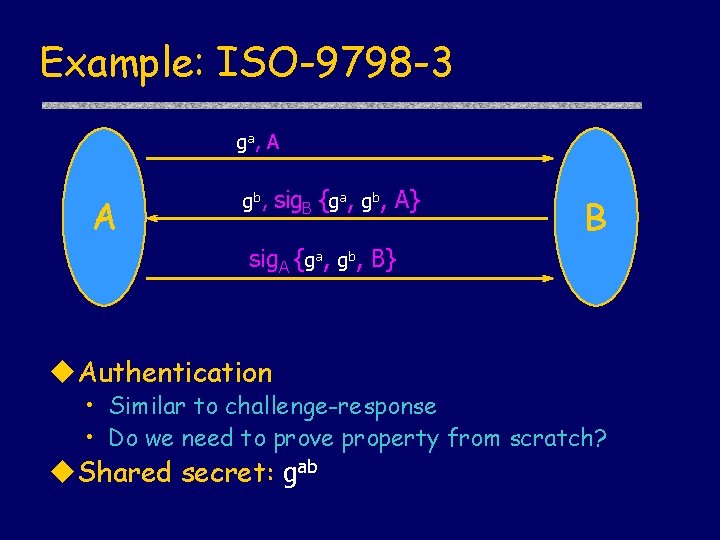
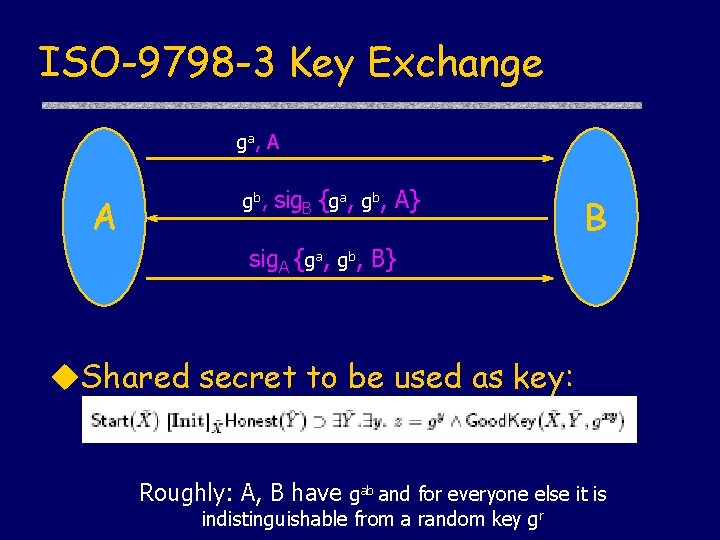
Example: ISO-9798 -3 ga, A A gb, sig. B {ga, gb, A} B sig. A {ga, gb, B} u. Authentication • Similar to challenge-response • Do we need to prove property from scratch? u. Shared secret: gab

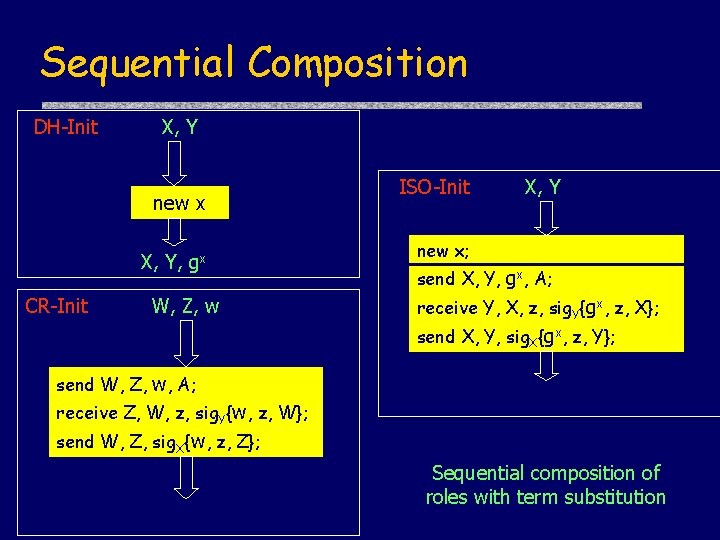
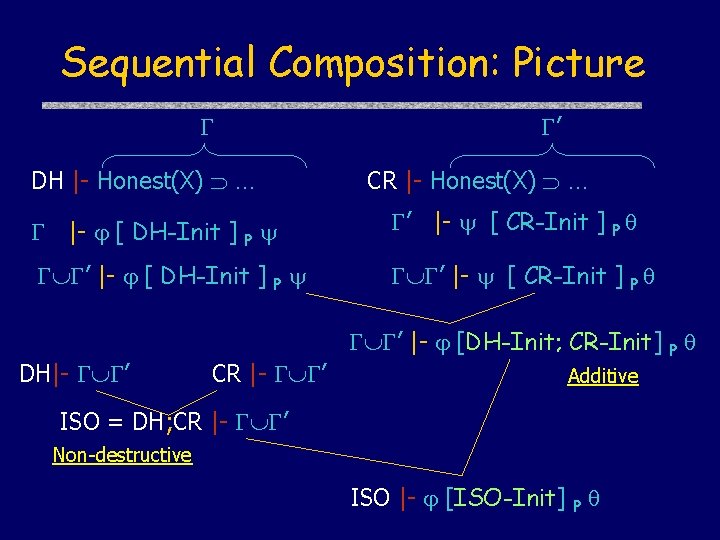
Sequential Composition DH-Init X, Y new x X, Y, gx CR-Init W, Z, w ISO-Init X, Y new x; send X, Y, gx, A; receive Y, X, z, sig. Y{gx, z, X}; send X, Y, sig. X{gx, z, Y}; send W, Z, w, A; receive Z, W, z, sig. Y{w, z, W}; send W, Z, sig. X{w, z, Z}; Sequential composition of roles with term substitution
![DiffieHellman Property u Formula utrue new a A FreshA ga Diffie-Hellman: Property u. Formula utrue [ new a ] A Fresh(A, ga)](https://slidetodoc.com/presentation_image_h/9a846fa0b9ce31d4a79e5342ba269695/image-20.jpg)
Diffie-Hellman: Property u. Formula utrue [ new a ] A Fresh(A, ga)

Abstract challenge response Init. ACR(A, X, m) = [ send A, X, {m}; receive X, A, {x, sig. X{m, x}}; send A, X, sig. A{m, x}}; ] Resp. ACR(B, n) = [ receive Y, B, {y}; send B, Y, {n, sig. B{y, n}}; receive Y, B, sig. Y{y, n}}; ] u Free variables m and n instead of nonces u Modal form: [ actions ] • • • precondition: actions: postcondition: Fresh(A, m) [ Init. ACR ]A Honest(B) Authentication Same proof as previous lecture!
![Sequencing Rule SP T P ST P u Is this Sequencing Rule [S]P [ T ] P [ ST ] P u. Is this](https://slidetodoc.com/presentation_image_h/9a846fa0b9ce31d4a79e5342ba269695/image-22.jpg)
Sequencing Rule [S]P [ T ] P [ ST ] P u. Is this rule sound?

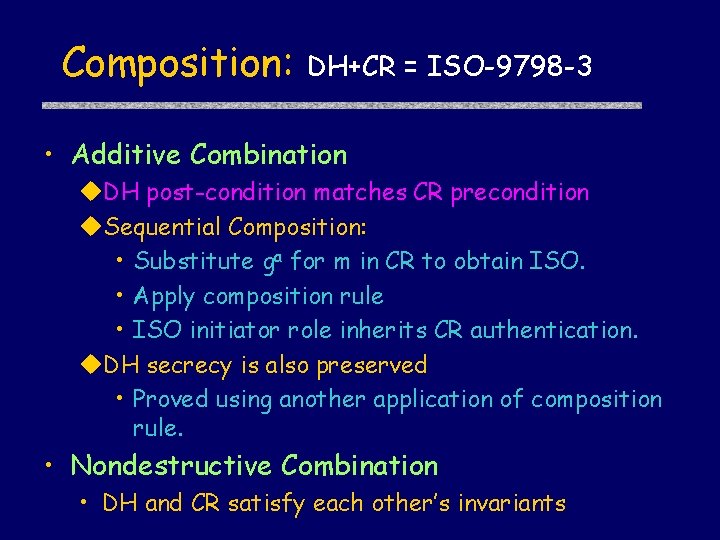
Composition: DH+CR = ISO-9798 -3 • Additive Combination u. DH post-condition matches CR precondition u. Sequential Composition: • Substitute ga for m in CR to obtain ISO. • Apply composition rule • ISO initiator role inherits CR authentication. u. DH secrecy is also preserved • Proved using another application of composition rule. • Nondestructive Combination • DH and CR satisfy each other’s invariants

Sequential Composition: Picture DH |- Honest(X) … ’ CR |- Honest(X) … |- [ DH-Init ] P ’ |- [ CR-Init ] P ’ |- [ DH-Init ] P ’ |- [ CR-Init ] P DH|- ’ CR |- ’ ’ |- [DH-Init; CR-Init] P Additive ISO = DH; CR |- ’ Non-destructive ISO |- [ISO-Init] P

Protocol Composition Logic: PCL u. Intuition u. Formalism • Protocol programming language • Protocol logic – Syntax – Semantics • Proof System u. Example • Signature-based challenge-response u. Composition u. Computational Soundness

Computational PCL u. Symbolic proofs about complexitytheoretic model of cryptographic protocols
![Two worlds Symbolic model NS 78 DY 84 Complexitytheoretic model GM 84 Two worlds Symbolic model [NS 78, DY 84, …] Complexity-theoretic model [GM 84, …]](https://slidetodoc.com/presentation_image_h/9a846fa0b9ce31d4a79e5342ba269695/image-27.jpg)
Two worlds Symbolic model [NS 78, DY 84, …] Complexity-theoretic model [GM 84, …] Attacker actions -Fixed set of actions, e. g. , decryption with known key (ABSTRACTION) + Any probabilistic polytime computation Security properties -Idealized, e. g. , secret message = not possessing atomic term representing message (ABSTRACTION) + Fine-grained, e. g. , secret message = no partial information about bitstring representation Analysis methods + Successful array of tools and techniques; automation - Hand-proofs are difficult, error-prone; no automation Can we get the best of both worlds?

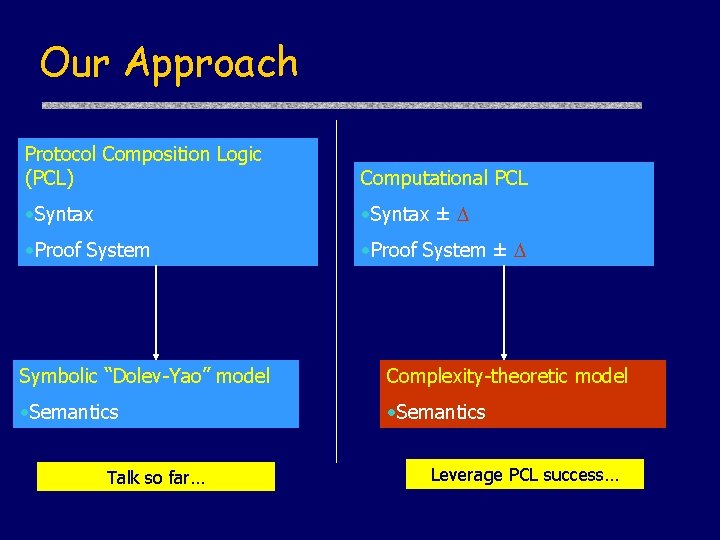
Our Approach Protocol Composition Logic (PCL) Computational PCL • Syntax ± • Proof System ± Symbolic “Dolev-Yao” model Complexity-theoretic model • Semantics Talk so far… Leverage PCL success…

Main Result u. Computational PCL • Symbolic logic for proving security properties of network protocols using public-key encryption u. Soundness Theorem: • If a property is provable in CPCL, then property holds in computational model with overwhelming asymptotic probability. u. Benefits • Symbolic proofs about computational model • Computational reasoning in soundness proof (only!) • Different axioms rely on different crypto assumptions

ISO-9798 -3 Key Exchange ga, A A gb, sig. B {ga, gb, A} B sig. A {ga, gb, B} u. Shared secret to be used as key: Roughly: A, B have gab and for everyone else it is indistinguishable from a random key gr

Central axioms u. Cryptographic security property of signature scheme • Unforgeability (used for authentication) u. Cryptographic security property of Diffie-Hellman function • DDH (used to prove secrecy)

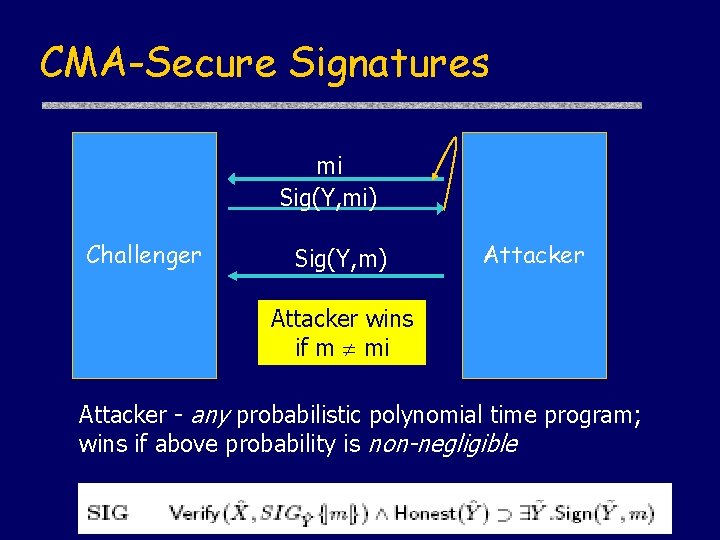
CMA-Secure Signatures mi Sig(Y, mi) Challenger Sig(Y, m) Attacker wins if m mi Attacker - any probabilistic polynomial time program; wins if above probability is non-negligible

Decisional Diffie-Hellman Let a, b, c be chosen at random from a group G with generator g. Then the two distributions <ga, gb, gab> and <ga, gb, gc> are computationally indistinguishable (no polynomial time attacker can tell them apart)

Complete Proof

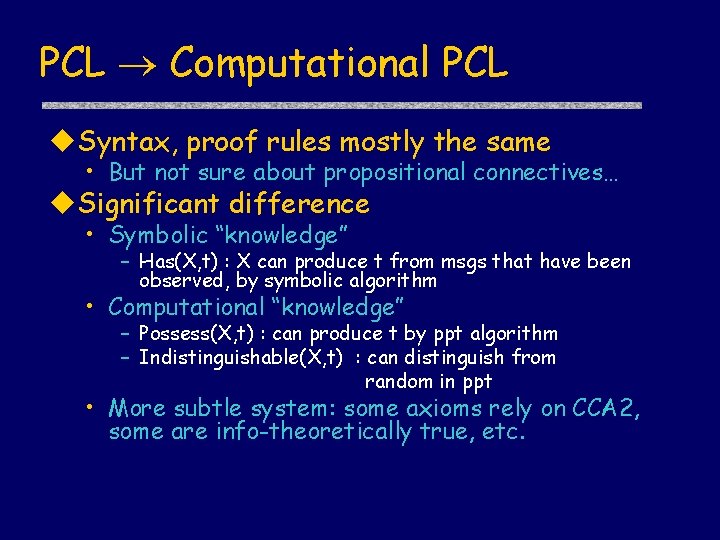
PCL Computational PCL u. Syntax, proof rules mostly the same • But not sure about propositional connectives… u. Significant difference • Symbolic “knowledge” – Has(X, t) : X can produce t from msgs that have been observed, by symbolic algorithm • Computational “knowledge” – Possess(X, t) : can produce t by ppt algorithm – Indistinguishable(X, t) : can distinguish from random in ppt • More subtle system: some axioms rely on CCA 2, some are info-theoretically true, etc.

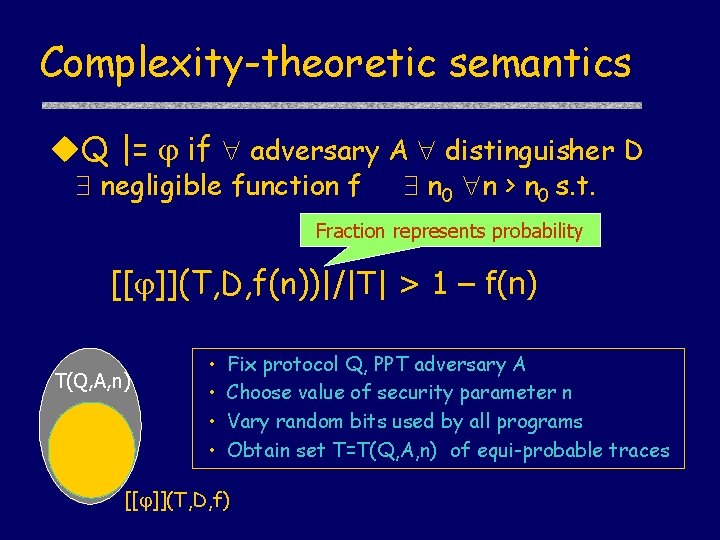
Complexity-theoretic semantics u. Q |= if adversary A distinguisher D negligible function f n 0 n > n 0 s. t. Fraction represents probability [[ ]](T, D, f(n))|/|T| > 1 – f(n) T(Q, A, n) • • Fix protocol Q, PPT adversary A Choose value of security parameter n Vary random bits used by all programs Obtain set T=T(Q, A, n) of equi-probable traces [[ ]](T, D, f)
![Inductive Semantics u 1 2 T D 1 T D Inductive Semantics u [[ 1 2]] (T, D, ) = [[ 1]] (T, D,](https://slidetodoc.com/presentation_image_h/9a846fa0b9ce31d4a79e5342ba269695/image-37.jpg)
Inductive Semantics u [[ 1 2]] (T, D, ) = [[ 1]] (T, D, ) [[ 2]] (T, D, ) u [[ 1 2]] (T, D, ) = [[ 1]] (T, D, ) [[ 2]] (T, D, ) u [[ ]] (T, D, ) = T - [[ ]] (T, D, ) Implication uses conditional probability u [[ 1 2]] (T, D, ) = [[ 1]] (T, D, ) [[ 2]] (T’, D, ) where T’ = [[ 1]] (T, D, ) Formula defines transformation on probability distributions over traces

Soundness of proof system u. Example axiom • Source(Y, u, {m}X) Decrypts(X, {m}X) Honest(X, Y) (Z X, Y) Indistinguishable(Z, u) u. Proof idea: crypto-style reduction • Assume axiom not valid: A D negligible f n 0 n > n 0 s. t. • [[ ]](T, D, f)|/|T| < 1 –f(n) • Construct attacker A’ that uses A, D to break IND-CCA 2 secure encryption scheme • Conditional implication essential

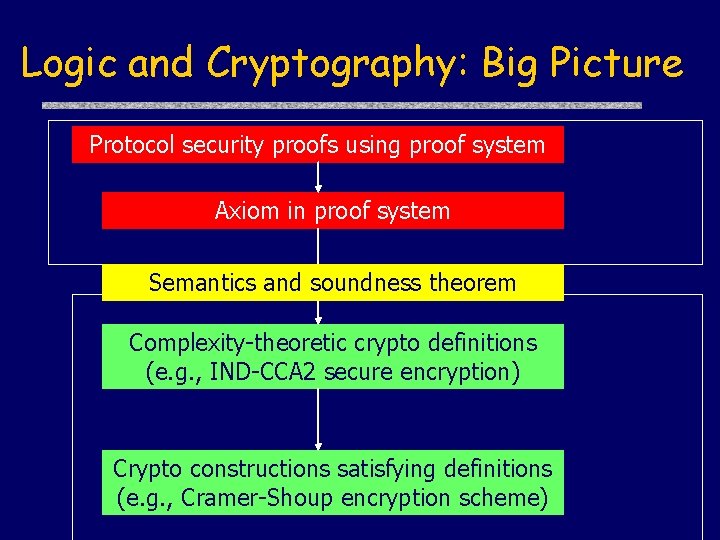
Logic and Cryptography: Big Picture Protocol security proofs using proof system Axiom in proof system Semantics and soundness theorem Complexity-theoretic crypto definitions (e. g. , IND-CCA 2 secure encryption) Crypto constructions satisfying definitions (e. g. , Cramer-Shoup encryption scheme)

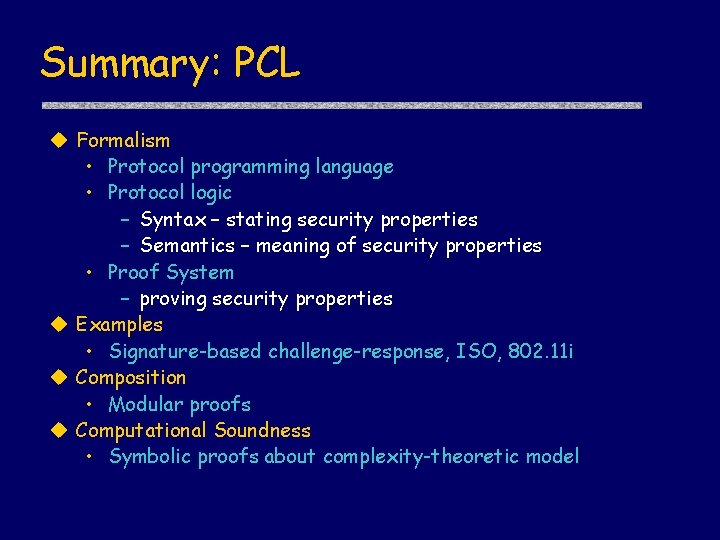
Summary: PCL u Formalism • Protocol programming language • Protocol logic – Syntax – stating security properties – Semantics – meaning of security properties • Proof System – proving security properties u Examples • Signature-based challenge-response, ISO, 802. 11 i u Composition • Modular proofs u Computational Soundness • Symbolic proofs about complexity-theoretic model

Thanks Questions?