Application and OS Attacks 1 Attack Phases Phase






![Buffer Overflow int main(){ int buffer[10]; buffer[20] = 37; } Q: What happens when Buffer Overflow int main(){ int buffer[10]; buffer[20] = 37; } Q: What happens when](https://slidetodoc.com/presentation_image/a084fee4cd21336f66681a2a3e82dd01/image-19.jpg)
![Simplified Stack Example low : : void func(int a, int b){ char buffer[10]; } Simplified Stack Example low : : void func(int a, int b){ char buffer[10]; }](https://slidetodoc.com/presentation_image/a084fee4cd21336f66681a2a3e82dd01/image-22.jpg)










![Input Validation Consider: strcpy(buffer, argv[1]) q A buffer overflow occurs if len(buffer) < len(argv[1]) Input Validation Consider: strcpy(buffer, argv[1]) q A buffer overflow occurs if len(buffer) < len(argv[1])](https://slidetodoc.com/presentation_image/a084fee4cd21336f66681a2a3e82dd01/image-41.jpg)
















































- Slides: 110

Application and OS Attacks 1

Attack Phases Phase 1: Reconnaissance q Phase 2: Scanning q Phase 3: Gaining access q o Application/OS attacks o Network attacks/Do. S attacks Phase 4: Maintaining access q Phase 5: Covering tracks and hiding q Application and OS Attacks 2

So Far… q Recon and Scanning completed q Attacker has inventory of target system and possible vulnerabilities q How to exploit vulnerabilities? o Application & OS attacks (this chapter) o Network-based attacks (next chapter) Application and OS Attacks 3

Main Topics q Buffer Overflow o Stack, heap, and integer overflow q Passwords q Web-based attacks o Session tracking, SQL injection, … o Browser flaws Application and OS Attacks 4

Script Kiddies q Attacks o o are widely available French Security Response Team (Fr. SIRT) Packet Storm Security Bugtraq Archives Metasploit Project q Little or no knowledge required Application and OS Attacks 5

Fr. SIRT Application and OS Attacks 6

Sophisticated Attacks q Next, we consider common attacks q Useful to understand how attacks work q Advanced attackers can use these for o Original attacks o More clever uses of existing attacks Application and OS Attacks 7

Buffer Overflow Application and OS Attacks 8

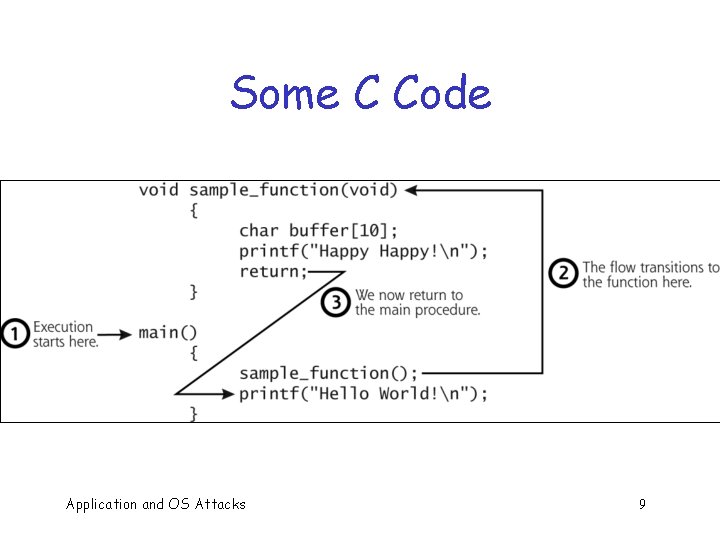
Some C Code Application and OS Attacks 9

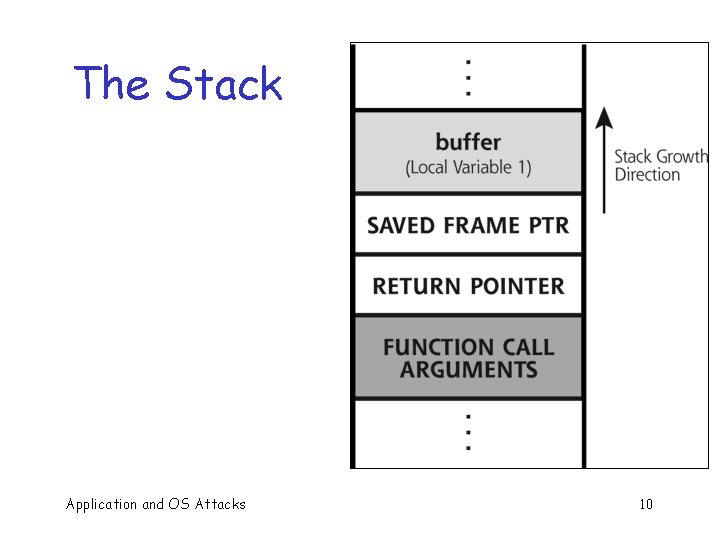
The Stack Application and OS Attacks 10

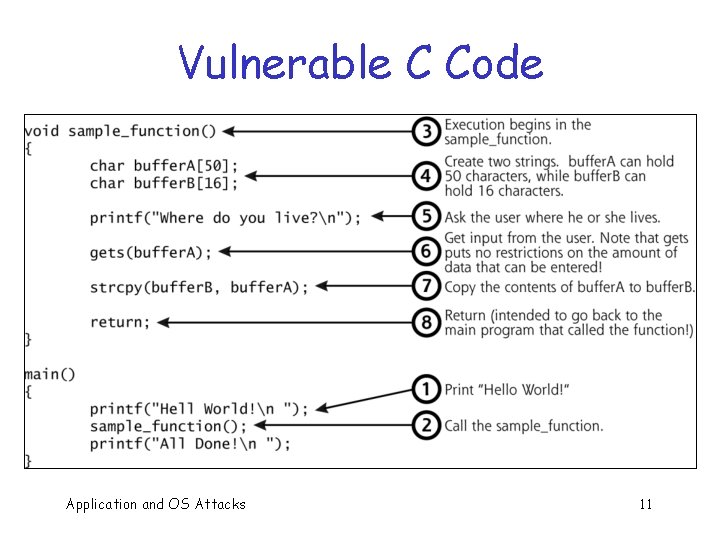
Vulnerable C Code Application and OS Attacks 11

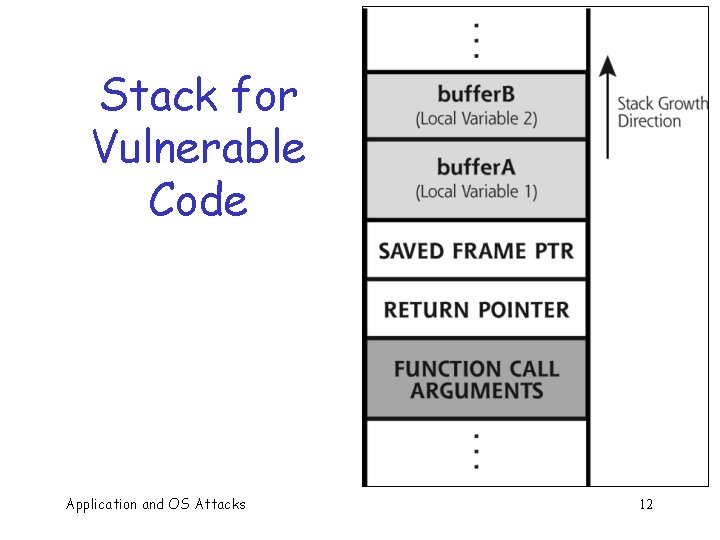
Stack for Vulnerable Code Application and OS Attacks 12

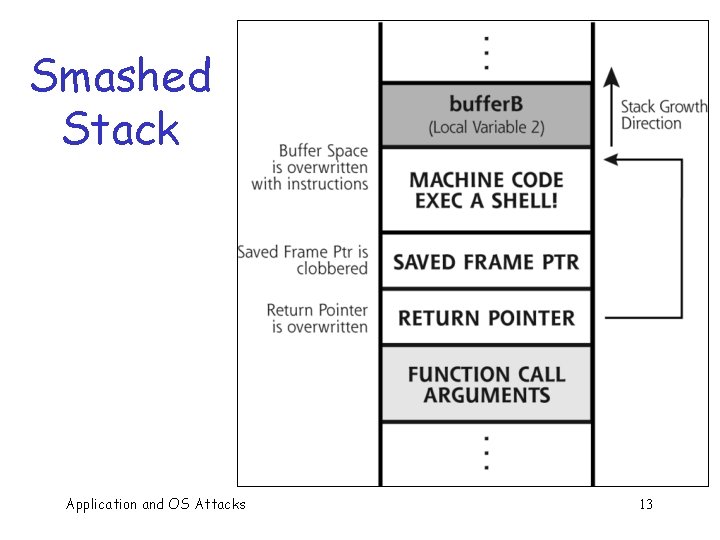
Smashed Stack Application and OS Attacks 13

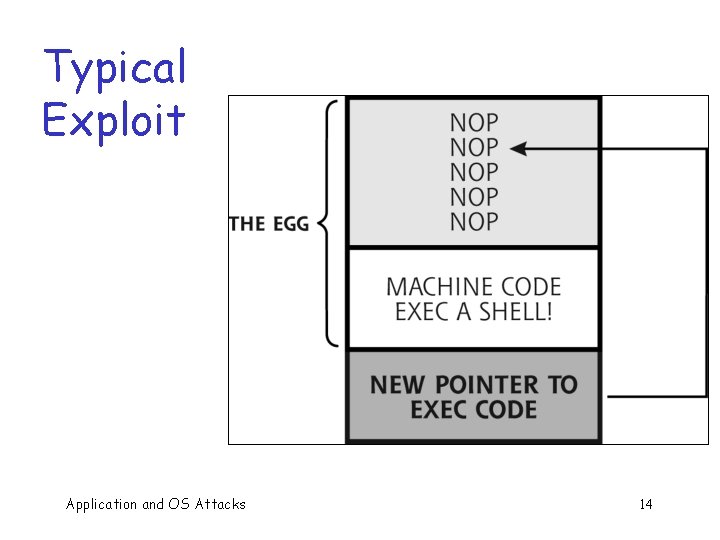
Typical Exploit Application and OS Attacks 14

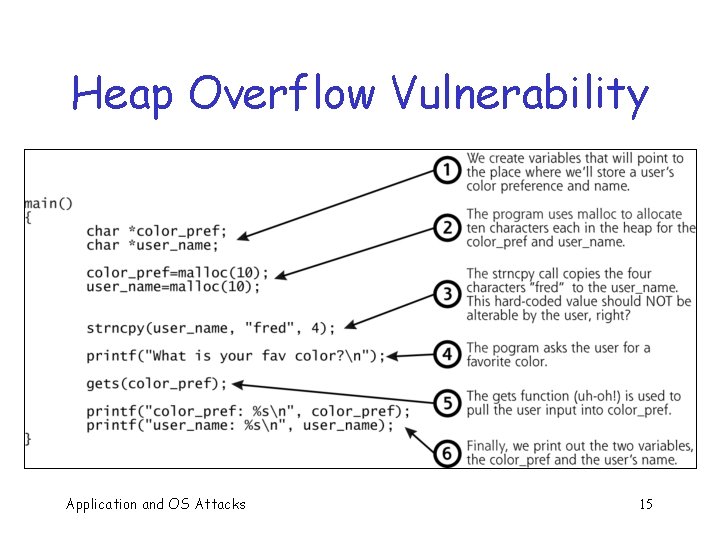
Heap Overflow Vulnerability Application and OS Attacks 15

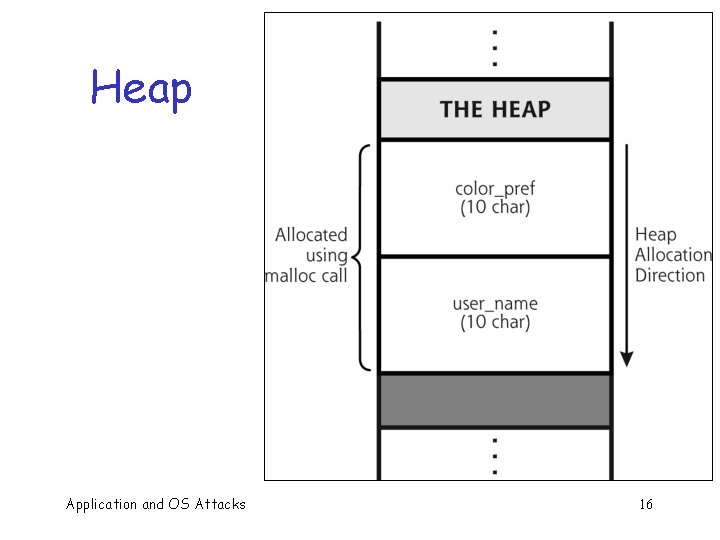
Heap Application and OS Attacks 16

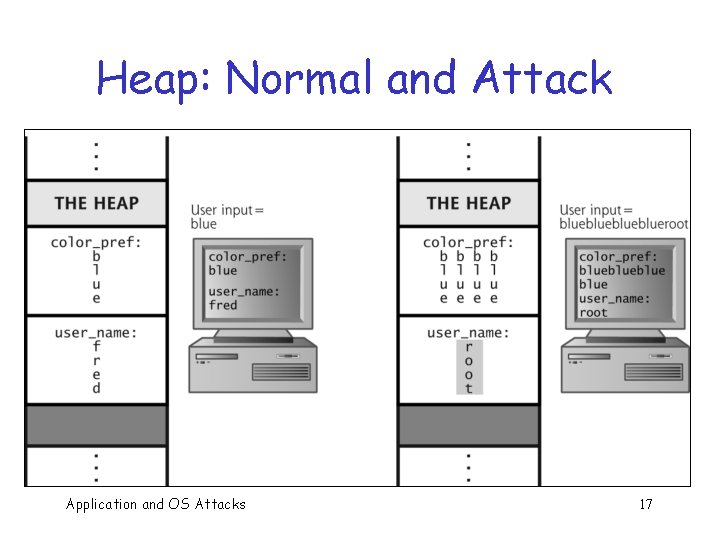
Heap: Normal and Attack Application and OS Attacks 17

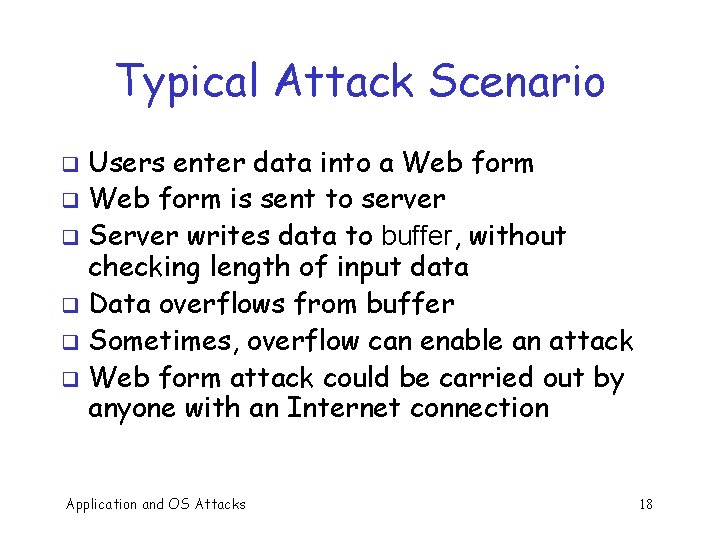
Typical Attack Scenario Users enter data into a Web form q Web form is sent to server q Server writes data to buffer, without checking length of input data q Data overflows from buffer q Sometimes, overflow can enable an attack q Web form attack could be carried out by anyone with an Internet connection q Application and OS Attacks 18
![Buffer Overflow int main int buffer10 buffer20 37 Q What happens when Buffer Overflow int main(){ int buffer[10]; buffer[20] = 37; } Q: What happens when](https://slidetodoc.com/presentation_image/a084fee4cd21336f66681a2a3e82dd01/image-19.jpg)
Buffer Overflow int main(){ int buffer[10]; buffer[20] = 37; } Q: What happens when this is executed? q A: Depending on what resides in memory at location “buffer[20]” q o Might overwrite user data or code o Might overwrite system data or code Application and OS Attacks 19

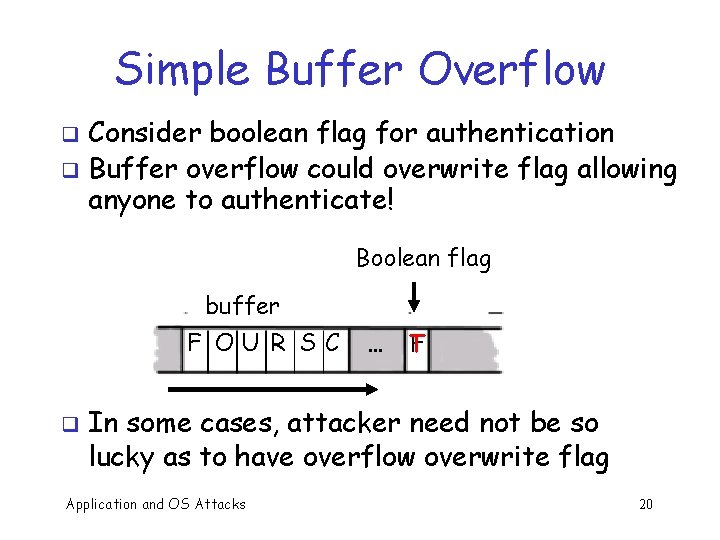
Simple Buffer Overflow Consider boolean flag for authentication q Buffer overflow could overwrite flag allowing anyone to authenticate! q Boolean flag buffer F OU R S C q … T F In some cases, attacker need not be so lucky as to have overflow overwrite flag Application and OS Attacks 20

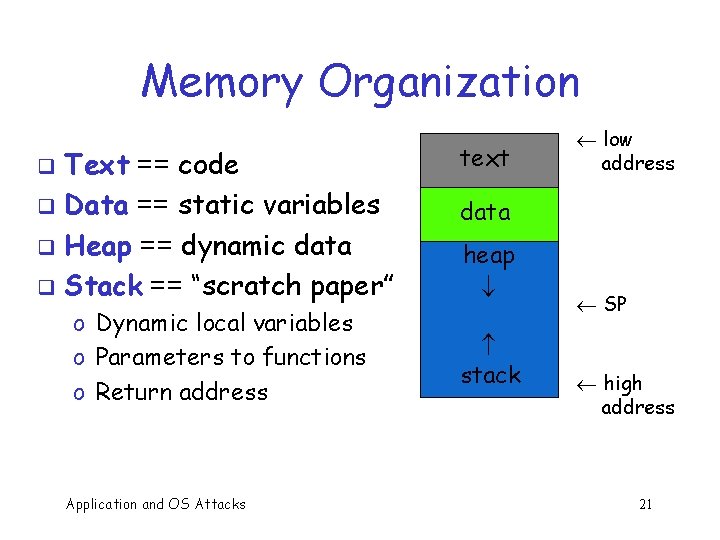
Memory Organization Text == code q Data == static variables q Heap == dynamic data q Stack == “scratch paper” q o Dynamic local variables o Parameters to functions o Return address Application and OS Attacks text ¬ low address data heap stack ¬ SP ¬ high address 21
![Simplified Stack Example low void funcint a int b char buffer10 Simplified Stack Example low : : void func(int a, int b){ char buffer[10]; }](https://slidetodoc.com/presentation_image/a084fee4cd21336f66681a2a3e82dd01/image-22.jpg)
Simplified Stack Example low : : void func(int a, int b){ char buffer[10]; } void main(){ func(1, 2); } buffer high Application and OS Attacks ret a b ¬ SP ¬ return SP address ¬ SP 22

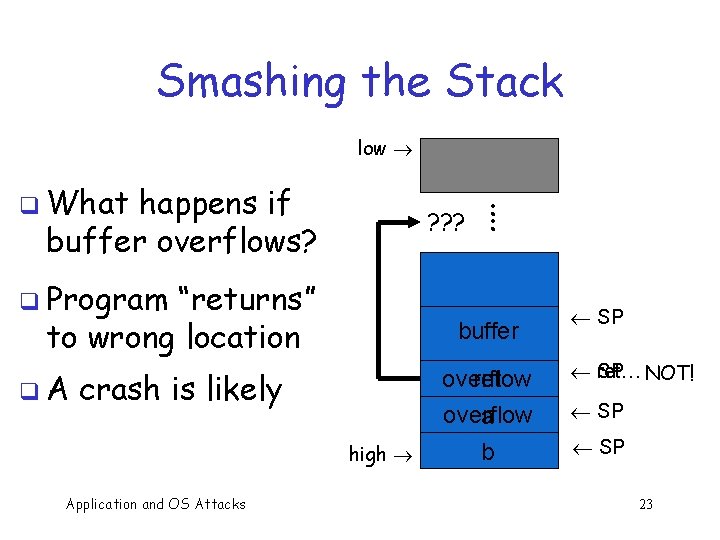
Smashing the Stack low q What happens if buffer overflows? : ? ? ? : q Program “returns” to wrong location q. A buffer crash is likely overflow ret overflow a high Application and OS Attacks b ¬ SP ret… NOT! ¬ SP 23

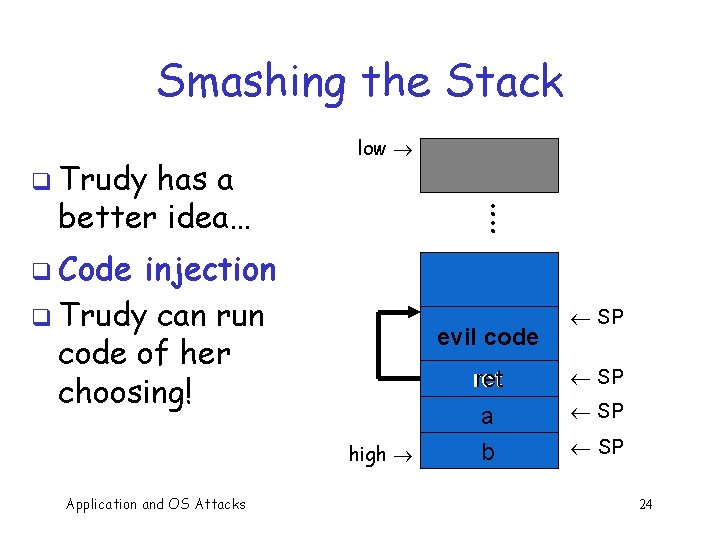
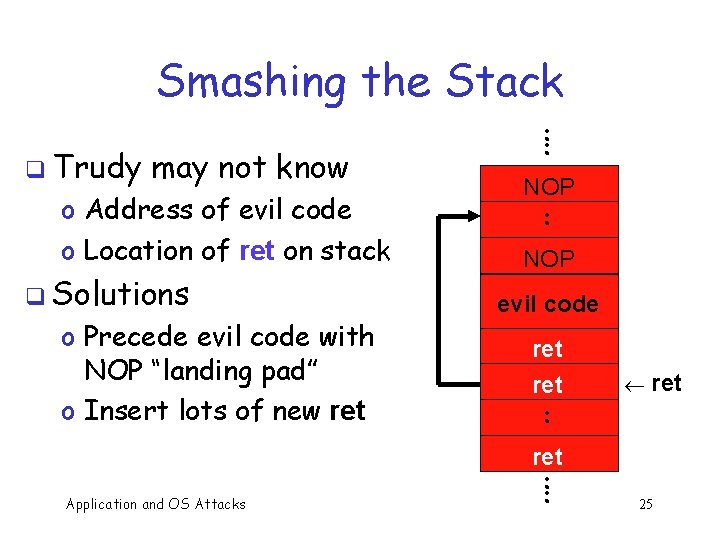
Smashing the Stack q Trudy has a better idea… low : : q Code injection q Trudy can run code of her choosing! evil code high Application and OS Attacks ¬ SP ret ¬ SP a b ¬ SP 24

Smashing the Stack q Trudy may not know o Address of evil code o Location of ret on stack q Solutions o Precede evil code with NOP “landing pad” o Insert lots of new ret Application and OS Attacks : : NOP evil code ret : : ¬ ret 25

Stack Smashing Summary A buffer overflow must exist in the code q Not all buffer overflows are exploitable q o Things must line up just right If exploitable, attacker can inject code q Trial and error likely required q o Lots of help available online o Smashing the Stack for Fun and Profit, Aleph One Also heap overflow, integer overflow, etc. q Stack smashing is “attack of the decade” q Application and OS Attacks 26

Stack Smashing Example Program asks for a serial number that the attacker does not know q Attacker does not have source code q Attacker does have the executable (exe) q q Program quits on incorrect serial number Application and OS Attacks 27

Example q By trial and error, attacker discovers an apparent buffer overflow Note that 0 x 41 is “A” q Looks like ret overwritten by 2 bytes! q Application and OS Attacks 28

Example q Next, disassemble bo. exe to find q The goal is to exploit buffer overflow to jump to address 0 x 401034 Application and OS Attacks 29

Example q Find that 0 x 401034 is “@^P 4” in ASCII Byte order is reversed? Why? q X 86 processors are “little-endian” q Application and OS Attacks 30

Example q Reverse the byte order to “ 4^P@” and… Success! We’ve bypassed serial number check by exploiting a buffer overflow q Overwrote the return address on the stack q Application and OS Attacks 31

Example q Attacker did not require access to the source code q Only tool used was a disassembler to determine address to jump to q May be possible to find address by trial and error o Necessary if attacker does not have exe Application and OS Attacks 32

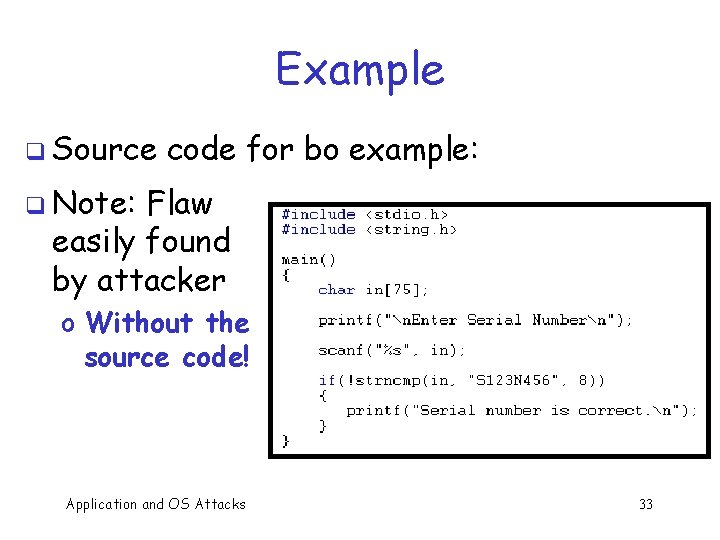
Example q Source code for bo example: q Note: Flaw easily found by attacker o Without the source code! Application and OS Attacks 33

Stack Smashing Prevention q Employ non-executable stack o “No execute” NX bit (if available) o Seems like the logical thing to do, but some real code executes on the stack (Java does this) Use safe languages (Java, C#) q Use safer C functions q o For unsafe functions, there are safer versions o For example, strncpy instead of strcpy Application and OS Attacks 34

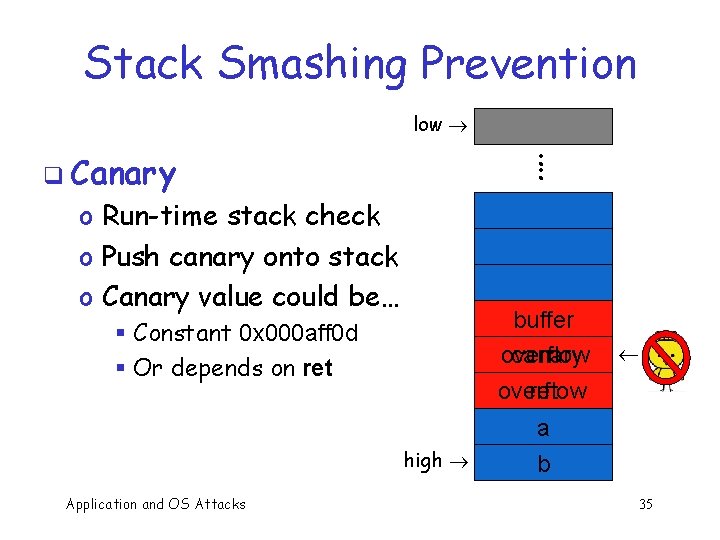
Stack Smashing Prevention low : : q Canary o Run-time stack check o Push canary onto stack o Canary value could be… buffer overflow canary overflow ret § Constant 0 x 000 aff 0 d § Or depends on ret high Application and OS Attacks ¬ a b 35

Microsoft’s Canary Microsoft added buffer security check feature to C++ with /GS compiler flag q Uses canary (or “security cookie”) q Q: What to do when canary dies? q A: Check for user-supplied handler q Handler may be subject to attack q o Claimed that attacker can specify handler code o If so, “safe” buffer overflows become exploitable when /GS is used! Application and OS Attacks 36

ASLR q Address Space Layout Randomization o Randomize location of code in memory q Makes buffer overflow attacks probabilistic o Address to jump to is “random” q Vista uses ASLR o With 256 “random” layouts (roughly) o So only 1/256 chance attack succeeds q Similar thing is done in Mac OS X Application and OS Attacks 37

ASLR A form of computing “diversity” q Works well with NX q Tricky to implement q Not a panacea q o There is no substitute for correct code q For more info… o See slides here Application and OS Attacks 38

Buffer Overflow q The “attack of the decade” for 90’s o Will be the attack of the decade for 00’s q Can be greatly reduced o ASLR, NX, etc. o Use safe languages/safer functions o Educate developers, use tools, etc. q Buffer overflows will exist for a long time o Legacy code o Bad software development Application and OS Attacks 39

Incomplete Mediation Application and OS Attacks 40
![Input Validation Consider strcpybuffer argv1 q A buffer overflow occurs if lenbuffer lenargv1 Input Validation Consider: strcpy(buffer, argv[1]) q A buffer overflow occurs if len(buffer) < len(argv[1])](https://slidetodoc.com/presentation_image/a084fee4cd21336f66681a2a3e82dd01/image-41.jpg)
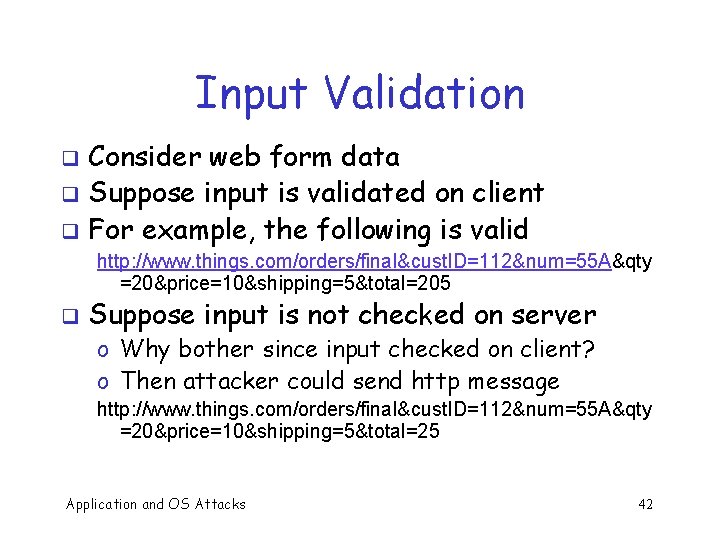
Input Validation Consider: strcpy(buffer, argv[1]) q A buffer overflow occurs if len(buffer) < len(argv[1]) q Software must validate the input by checking the length of argv[1] q Failure to do so is an example of a more general problem: incomplete mediation q Application and OS Attacks 41

Input Validation Consider web form data q Suppose input is validated on client q For example, the following is valid q http: //www. things. com/orders/final&cust. ID=112&num=55 A&qty =20&price=10&shipping=5&total=205 q Suppose input is not checked on server o Why bother since input checked on client? o Then attacker could send http message http: //www. things. com/orders/final&cust. ID=112&num=55 A&qty =20&price=10&shipping=5&total=25 Application and OS Attacks 42

Incomplete Mediation q Linux kernel o Research has revealed many buffer overflows o Many of these are due to incomplete mediation q Linux kernel is “good” software since o Open-source o Kernel written by coding gurus q Tools exist to help find such problems o But errors can be subtle o And tools useful to attackers too! Application and OS Attacks 43

Race Conditions Application and OS Attacks 44

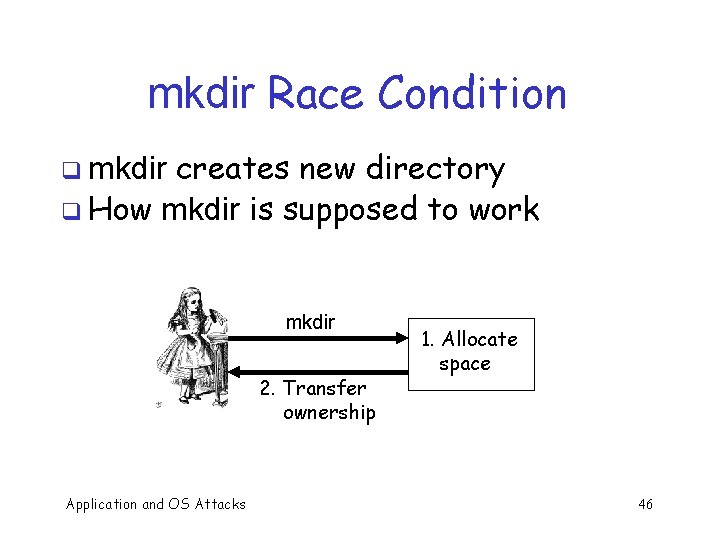
Race Condition q Security processes should be atomic o Occur “all at once” Race conditions can arise when securitycritical process occurs in stages q Attacker makes change between stages q o Often, between stage that gives authorization, but before stage that transfers ownership q Example: Unix mkdir Application and OS Attacks 45

mkdir Race Condition creates new directory q How mkdir is supposed to work q mkdir 2. Transfer ownership Application and OS Attacks 1. Allocate space 46

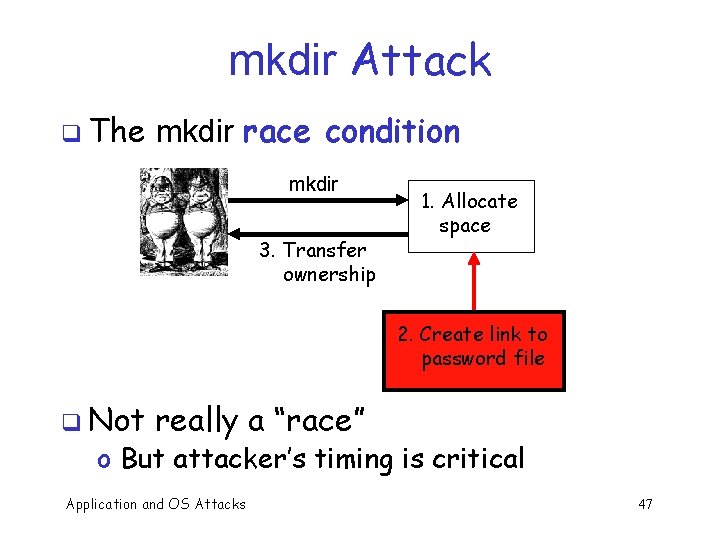
mkdir Attack q The mkdir race condition mkdir 3. Transfer ownership 1. Allocate space 2. Create link to password file q Not really a “race” o But attacker’s timing is critical Application and OS Attacks 47

Race Conditions q Race conditions appear to be common o May be more common than buffer overflows q But race conditions harder to exploit o Buffer overflow is “low hanging fruit” today q To prevent race conditions… o Make security-critical processes atomic o Occur all at once, not in stages o Not easy to accomplish in practice Application and OS Attacks 48

Heap Overflow q Heap used for dynamic variables o For example, malloc in C q Can overflow one array into another q Makes it possible to change data o Like simpleminded example given earlier Application and OS Attacks 49

Heap Overflow Example q First print o buf 2 = 2222 q Second print o buf 2 = 11122222 Application and OS Attacks 50

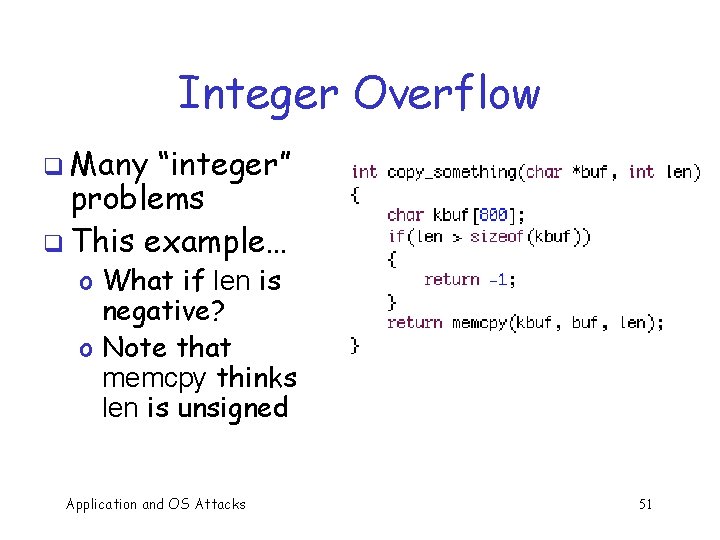
Integer Overflow q Many “integer” problems q This example… o What if len is negative? o Note that memcpy thinks len is unsigned Application and OS Attacks 51

Exploitation Engines q Developing a buffer overflow attack o Tedious, lots of trial and error o Until Metasploit… q Metasploit o Knows about lots of attacks o Has lots of payloads Application and OS Attacks 52

Metasploit q Payloads include o o o o Bind shell to current port Bind shell to arbitrary port Reverse shell Windows VNC Server DLL inject Reverse VNC DLL inject Inject DLL into running application Create local admin user The Meterpreter (run command of attacker’s choosing) Application and OS Attacks 53

Metasploit Web Interface Application and OS Attacks 54

Metasploit q Advantages for attackers? o Reduces “development cycle” o Resulting attacks much more reliable q Advantages for good guys? o o Helps identify false positives Help improve IDS Improved penetration testing Improved management awareness Application and OS Attacks 55

Buffer Overflow Defenses q NX, safe languages, safer functions (in C), canary, ASLR q Better software development o o Use tools, such as ITS 4 RATS Flawfinder Application and OS Attacks 56

Authentication Application and OS Attacks 57

Who Goes There? How to authenticate a human to a machine? q Can be based on… q o Something you know § For example, a password o Something you have § For example, a smartcard o Something you are § For example, your fingerprint Application and OS Attacks 58

Something You Know q Passwords q Lots o o of things act as passwords! PIN Social security number Mother’s maiden name Date of birth Name of your pet, etc. Application and OS Attacks 59

Trouble with Passwords q q “Passwords are one of the biggest practical problems facing security engineers today. ” “Humans are incapable of securely storing highquality cryptographic keys, and they have unacceptable speed and accuracy when performing cryptographic operations. (They are also large, expensive to maintain, difficult to manage, and they pollute the environment. It is astonishing that these devices continue to be manufactured and deployed. )” Application and OS Attacks 60

Why Passwords? q Why is “something you know” more popular than “something you have” and “something you are”? q Cost: passwords are free q Convenience: easier for SA to reset pwd than to issue user a new thumb Application and OS Attacks 61

Keys vs Passwords Crypto keys q Spse key is 64 bits q Then 264 keys q Choose key at random… q …then attacker must try about 263 keys q Application and OS Attacks q q q Passwords Spse passwords are 8 characters, and 256 different characters Then 2568 = 264 pwds Users do not select passwords at random Attacker has far less than 263 pwds to try (dictionary attack) 62

Good and Bad Passwords q Bad passwords o o o o frank Fido password 4444 Pikachu 102560 Austin. Stamp Application and OS Attacks q Good Passwords? o o o jf. Iej, 43 j-Emm. L+y 09864376537263 P 0 kem 0 N FSa 7 Yago 0 nceu. P 0 n. At 1 m 8 Poke. GCTall 150 63

Password Experiment q Three groups of users each group advised to select passwords as follows o Group A: At least 6 chars, 1 non-letter winner o Group B: Password based on passphrase o Group C: 8 random characters q Results o o o Group A: About 30% of pwds easy to crack Group B: About 10% cracked § Passwords easy to remember § Passwords hard to remember Group C: About 10% cracked Application and OS Attacks 64

Password Experiment User compliance hard to achieve q In each case, 1/3 rd did not comply (and about 1/3 rd of those easy to crack!) q Assigned passwords sometimes best q If passwords not assigned, best advice is q o Choose passwords based on passphrase o Use pwd cracking tool to test for weak pwds o Require periodic password changes? Application and OS Attacks 65

Attacks on Passwords q Attacker could… o o q Target one particular account Target any account on system Target any account on any system Attempt denial of service (Do. S) attack Common attack path o Outsider normal user administrator o May only require one weak password! Application and OS Attacks 66

Password Retry q Suppose system locks after 3 bad passwords. How long should it lock? o 5 seconds o 5 minutes o Until SA restores service q What are +’s and -’s of each? Application and OS Attacks 67

Password File Bad idea to store passwords in a file q But need a way to verify passwords q Cryptographic solution: hash the passwords q o Store y = h(password) o Can verify entered password by hashing o If attacker obtains password file, he does not obtain passwords o But attacker with password file can guess x and check whether y = h(x) o If so, attacker has found password! Application and OS Attacks 68

Dictionary Attacker pre-computes h(x) for all x in a dictionary of common passwords q Suppose attacker gets access to password file containing hashed passwords q o Attacker only needs to compare hashes to his pre-computed dictionary o Same attack will work each time q Can we prevent this attack? Or at least make attacker’s job more difficult? Application and OS Attacks 69

Password File Store hashed passwords q Better to hash with salt q Given password, choose random s, compute y = h(password, s) and store the pair (s, y) in the password file q Note: The salt s is not secret q Easy to verify password q Attacker must recompute dictionary hashes for each user lots more work! q Application and OS Attacks 70

Password Cracking: Do the Math Assumptions q Pwds are 8 chars, 128 choices per character q o Then 1288 = 256 possible passwords There is a password file with 210 pwds q Attacker has dictionary of 220 common pwds q Probability of 1/4 that a pwd is in dictionary q Work is measured by number of hashes q Application and OS Attacks 71

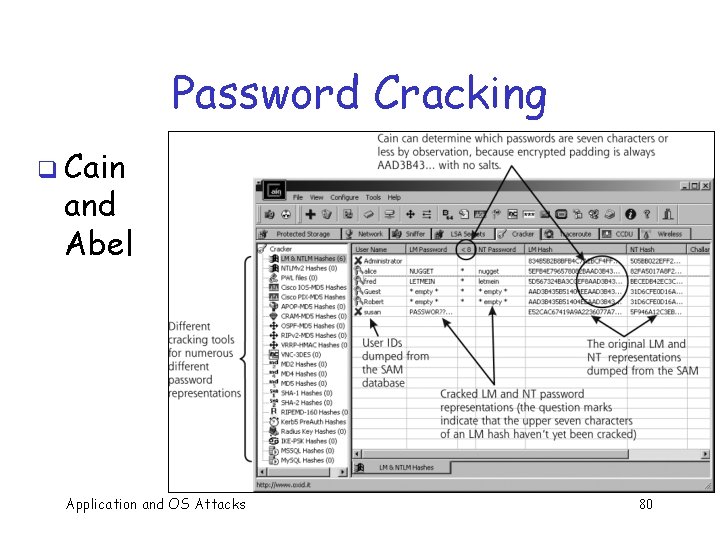
Password Cracking q Attack 1 password without dictionary o Must try 256/2 = 255 on average o Just like exhaustive key search q Attack 1 password with dictionary o Expected work is about 1/4 (219) + 3/4 (255) = 254. 6 o But in practice, try all in dictionary and quit if not found work is at most 220 and probability of success is 1/4 Application and OS Attacks 72

Password Cracking Attack any of 1024 passwords in file q Without dictionary q o Assume all 210 passwords are distinct o Need 255 comparisons before expect to find password o If no salt, each hash computation gives 210 comparisons the expected work (number of hashes) is 255/210 = 245 o If salt is used, expected work is 255 since each comparison requires a new hash computation Application and OS Attacks 73

Password Cracking Attack any of 1024 passwords in file q With dictionary q o Probability at least one password is in dictionary is 1 – (3/4)1024 = 1 o We ignore case where no pwd is in dictionary o If no salt, work is about 219/210 = 29 o If salt, expected work is less than 222 o Note: If no salt, we can precompute all dictionary hashes and amortize the work Application and OS Attacks 74

Other Password Issues q Too many passwords to remember o Results in password reuse o Why is this a problem? q Who suffers from bad password? o Login password vs ATM PIN Failure to change default passwords q Social engineering q Error logs may contain “almost” passwords q Bugs, keystroke logging, spyware, etc. q Application and OS Attacks 75

Passwords The bottom line q Password cracking is too easy! q o One weak password may break security o Users choose bad passwords o Social engineering attacks, etc. The bad guy has all of the advantages q All of the math favors bad guys q Passwords are a big security problem q Application and OS Attacks 76

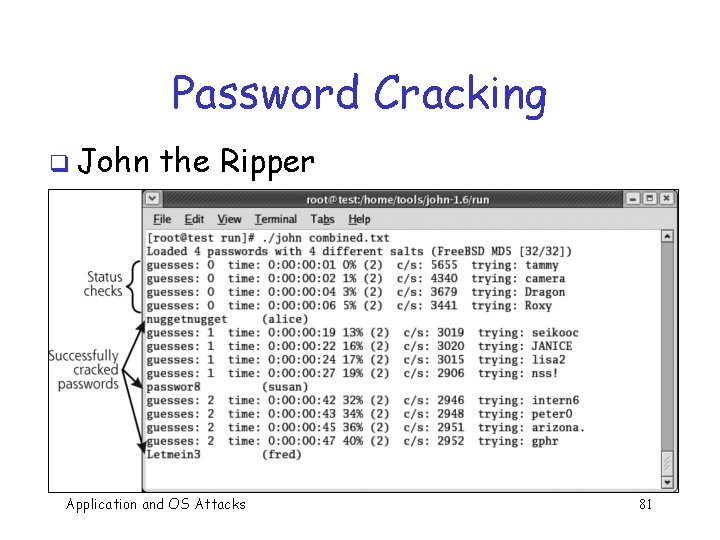
Password Cracking Tools q Popular password cracking tools o o Password Crackers Password Portal L 0 pht. Crack and LC 4 (Windows) John the Ripper (Unix) Admins should use these tools to test for weak passwords since attackers will! q Good article on password cracking q o Passwords - Conerstone of Computer Security Application and OS Attacks 77

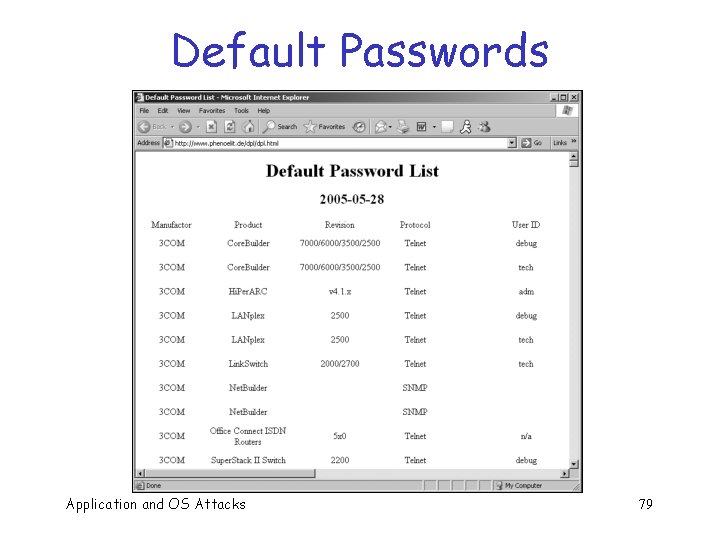
Password Problems q Weak passwords q Too many passwords q Default passwords q And so on… Application and OS Attacks 78

Default Passwords Application and OS Attacks 79

Password Cracking q Cain and Abel Application and OS Attacks 80

Password Cracking q John the Ripper Application and OS Attacks 81

Password Cracking Defenses Strong password policy q User awareness q Pwd filtering software q o Password Guardian, Strongpass Use other forms of authentication q Try password cracking q Protect password files q Application and OS Attacks 82

Web-Related Attacks q Rapidly growing area of interest q For up-to-date info, see, for example, The Ghost in the Browser o Slides are here Application and OS Attacks 83

Web Application Attacks q Book discusses… q Account harvesting q Session tracking issues q SQL injection Application and OS Attacks 84

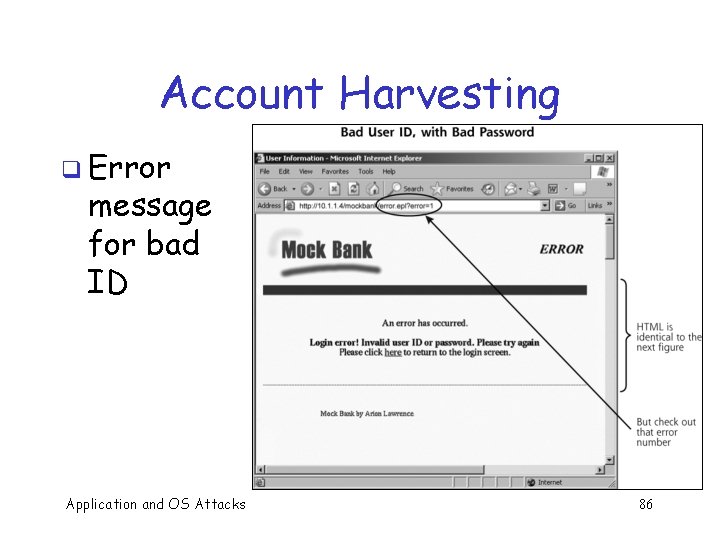
Account Harvesting q Targets authentication process when application requests ID/password q Attacker can collect IDs o And sometimes passwords too q. A simple concept q Very effective in some Web apps Application and OS Attacks 85

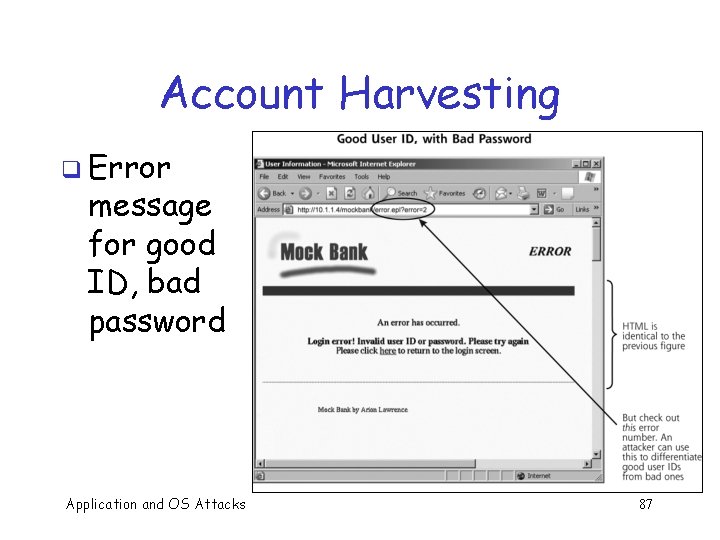
Account Harvesting q Error message for bad ID Application and OS Attacks 86

Account Harvesting q Error message for good ID, bad password Application and OS Attacks 87

Account Harvesting Defense q Have consistent error messages q Other? Application and OS Attacks 88

Session Tracking Issues q Authenticate to Web application o Use a password q Then often use a session ID to connect traffic to authenticated user o Session ID is given to client browser o Usually independent of SSL connection o Bottom line: ID can be changed by client Application and OS Attacks 89

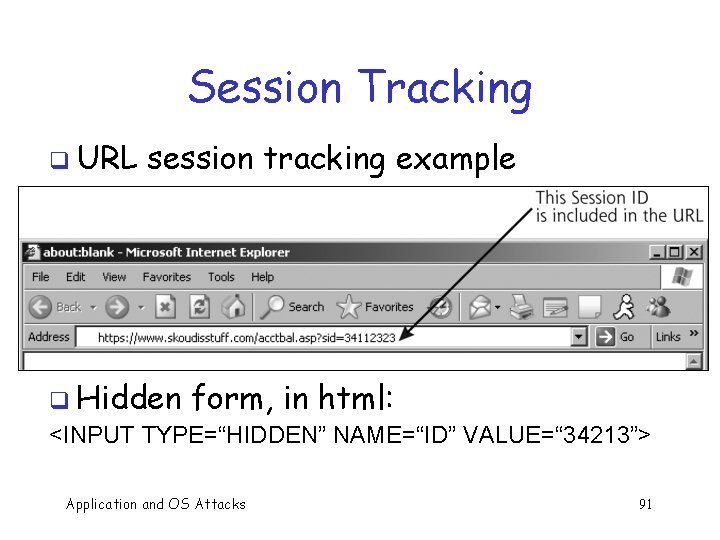
Attacking Session Tracking q Session ID can be implemented using o URL session tracking (next slide) o Hidden form elements (next slide) o Nonpersistent cookies (most common) Application and OS Attacks 90

Session Tracking q URL session tracking example q Hidden form, in html: <INPUT TYPE=“HIDDEN” NAME=“ID” VALUE=“ 34213”> Application and OS Attacks 91

Session Tracking Attacks q Might be able to alter session ID o If so, can hijack an active session o Called “session cloning” q Why doesn’t Web application connect session ID to IP address? Application and OS Attacks 92

Session Tracking Attacks q Attacker first needs to find valid ID q How to do so? o Collect a bunch of IDs o Try to see how they change o Then make educated guesses… Application and OS Attacks 93

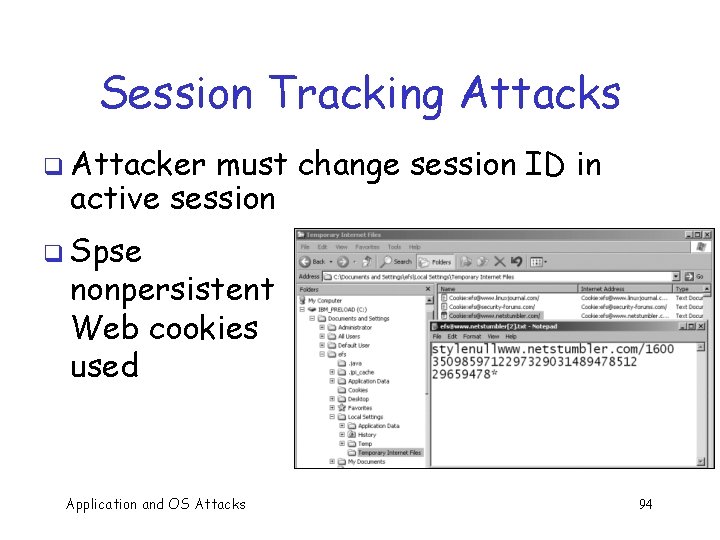
Session Tracking Attacks q Attacker must change session ID in active session q Spse nonpersistent Web cookies used Application and OS Attacks 94

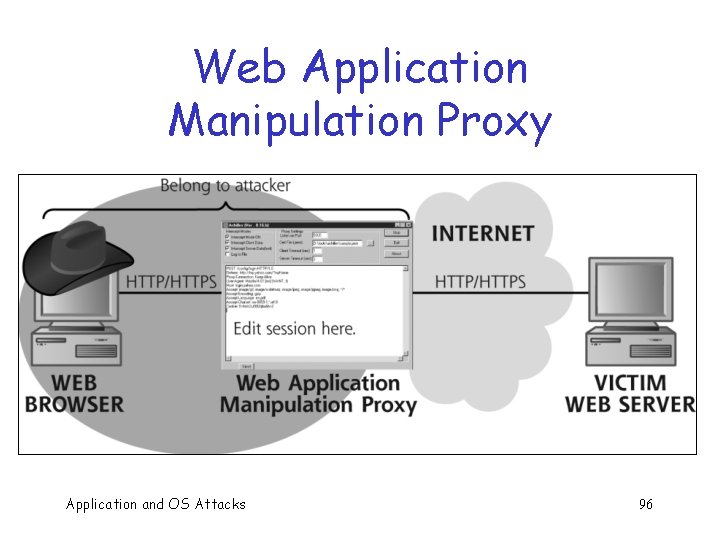
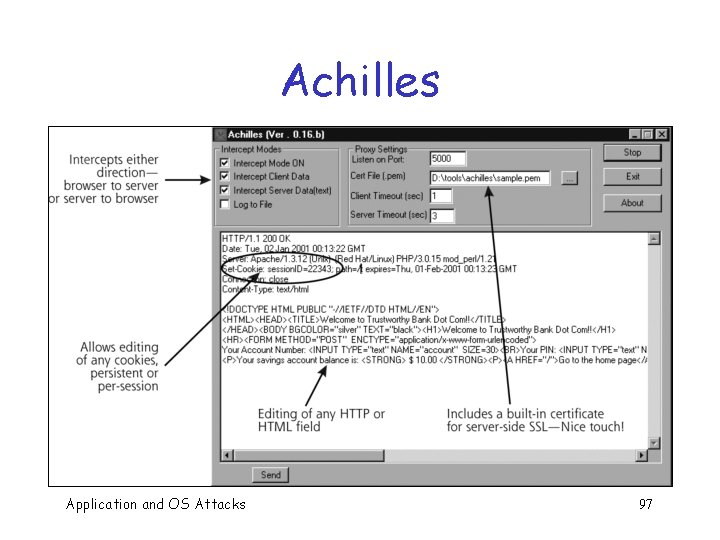
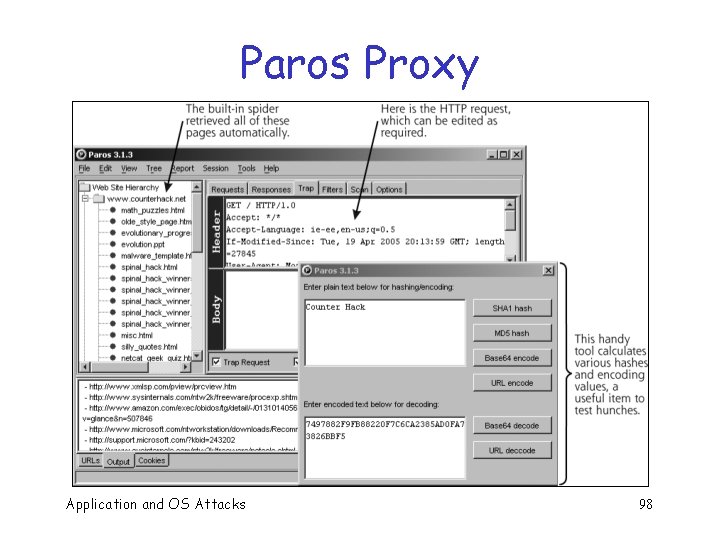
Session Tracking Attacks q Can use a “Web application manipulation proxy” to change session ID in active session q Web app manipulation proxies include o Achilles, Paros Proxy, Web. Scarab, Web Sleuth, etc. Application and OS Attacks 95

Web Application Manipulation Proxy Application and OS Attacks 96

Achilles Application and OS Attacks 97

Paros Proxy Application and OS Attacks 98

Defenses q Integrity protect session ID o Sign/MAC/HMAC o Then, only legitimate user can properly sign/MAC/HMAC q Note that this is separate from SSL q Is this really necessary? ? ? Application and OS Attacks 99

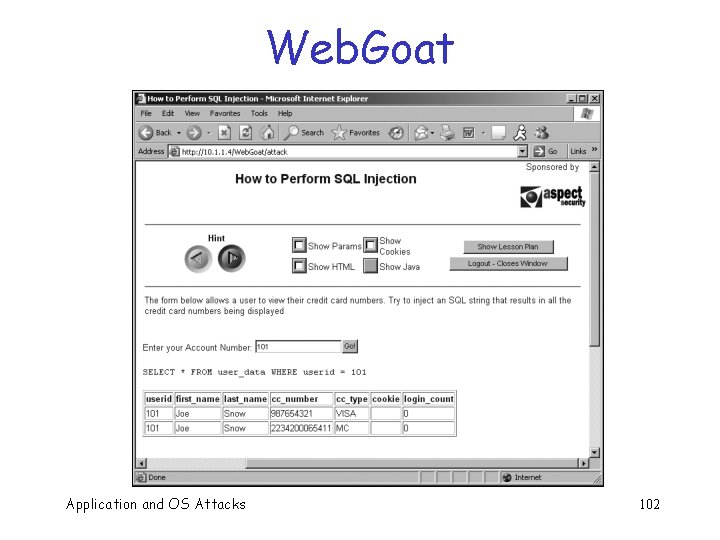
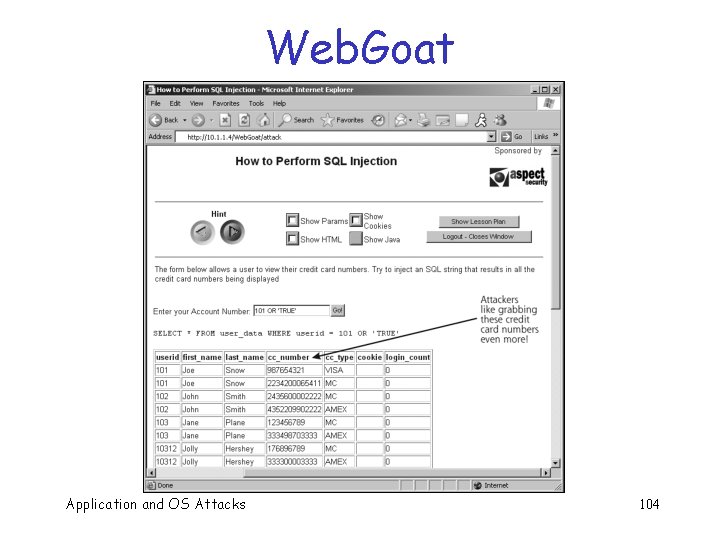
SQL Injection q Structured Query Language (SQL) o Used by web application to communicate with back-end database q By manipulating SQL, attacker may o Get access to info o Change data q We’ve seen this before Application and OS Attacks 100

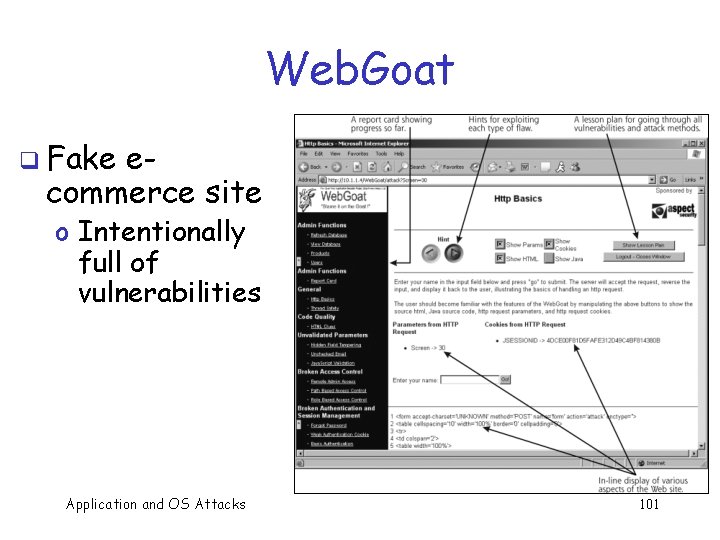
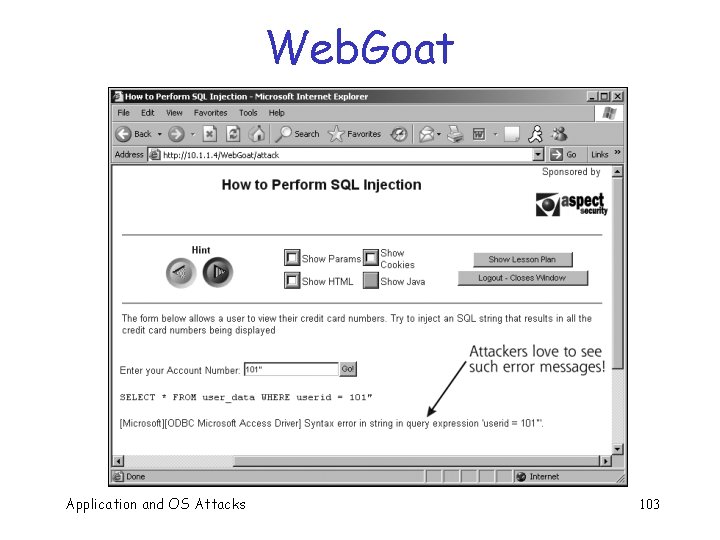
Web. Goat q Fake ecommerce site o Intentionally full of vulnerabilities Application and OS Attacks 101

Web. Goat Application and OS Attacks 102

Web. Goat Application and OS Attacks 103

Web. Goat Application and OS Attacks 104

SQL Injection Defenses q Complete mediation o Filter all user-supplied info q Limit permissions of Web app when accessing database q “Parameterized stored procedures” o I. e. , do not compose queries on the fly Application and OS Attacks 105

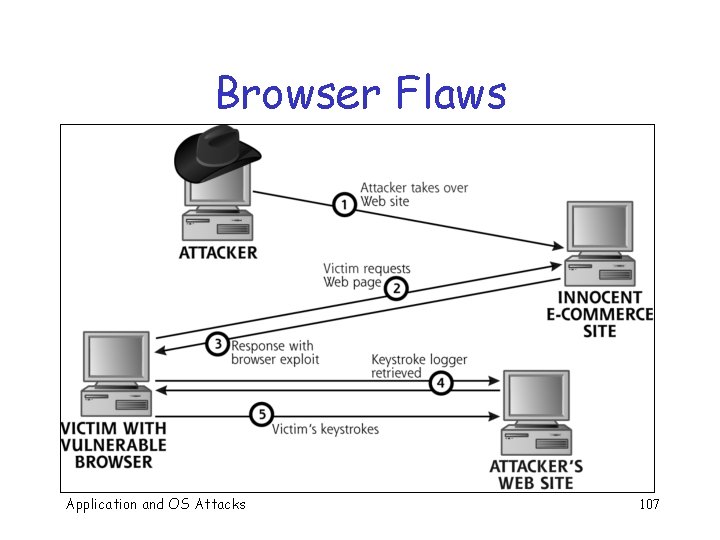
Browser Flaws q Browsers software complex pieces of o Lots of flaws have been found o Buffer overflows, for example q For example, buffer overflow in Safari (related to tiff files) used to break i. Phone restrictions Application and OS Attacks 106

Browser Flaws Application and OS Attacks 107

Defenses q Use antivirus q “…consider using a browser other than Internet Explorer” Application and OS Attacks 108

Conclusions Application and OS Attacks 109

Summary Application and OS Attacks 110