ICMP Redirection Introduction ICMP route redirect message is













- Slides: 22

ICMP Redirection

Introduction • ICMP route redirect message is normally sent by the default router to the system to indicate that there’s a shorter route to some particular destination. • Hacker can forge an ICMP redirect message to achieve a similar effect of ARP cache poisoning.

Internet Control Message Protocol (ICMP) • ICMP is designed to compensate for the deficiencies of IP protocol – IP protocol has no error-reporting or errorcorrecting mechanism. • E. g. drop a datagram because no router is found or time-to-live field has a zero value. – IP protocol also lacks a mechanism for host and management queries. • E. g. need information from other host or router.

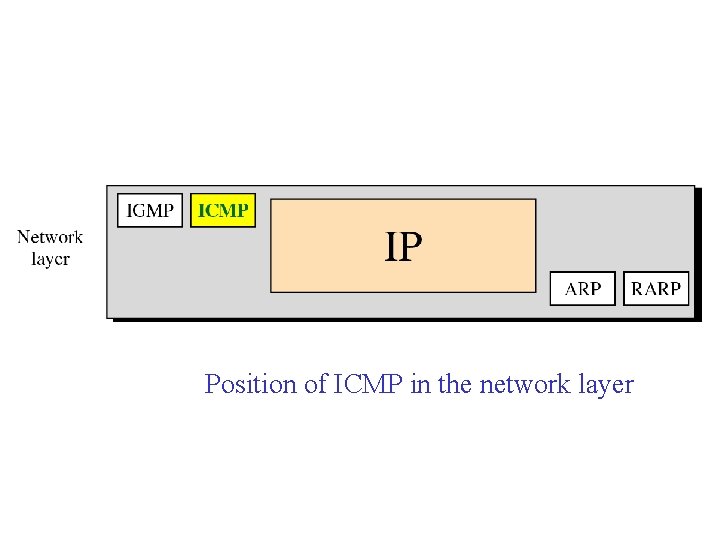
Position of ICMP in the network layer

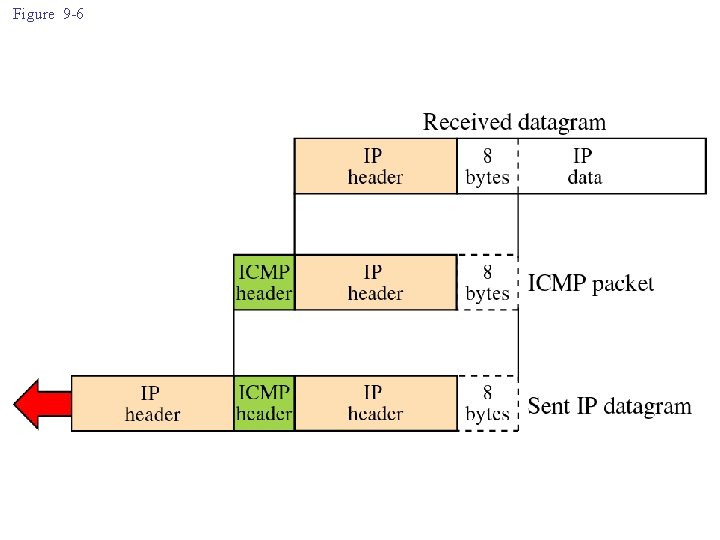
ICMP itself is a network layer protocol. However, its messages are not passed directly to the data link layer. Instead, the messages are first encapsulated inside IP datagrams.

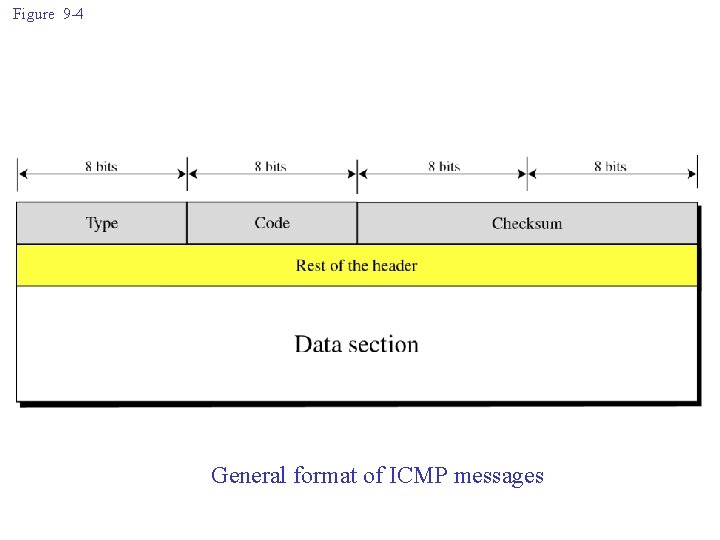
Figure 9 -4 General format of ICMP messages

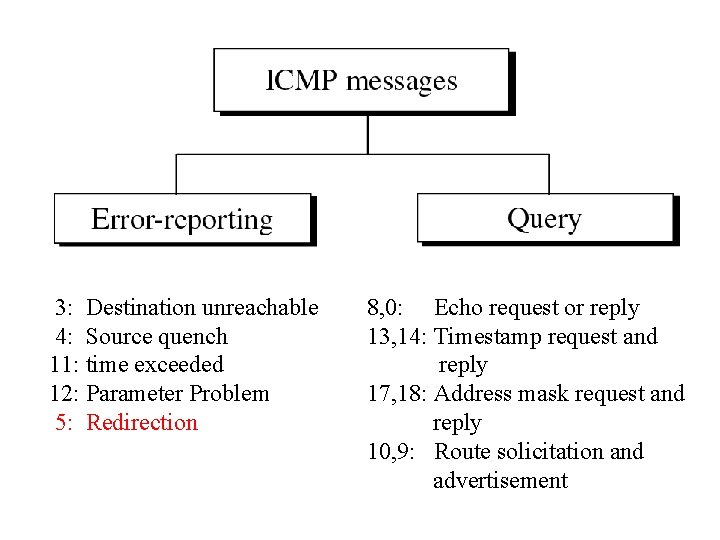
3: Destination unreachable 4: Source quench 11: time exceeded 12: Parameter Problem 5: Redirection 8, 0: Echo request or reply 13, 14: Timestamp request and reply 17, 18: Address mask request and reply 10, 9: Route solicitation and advertisement

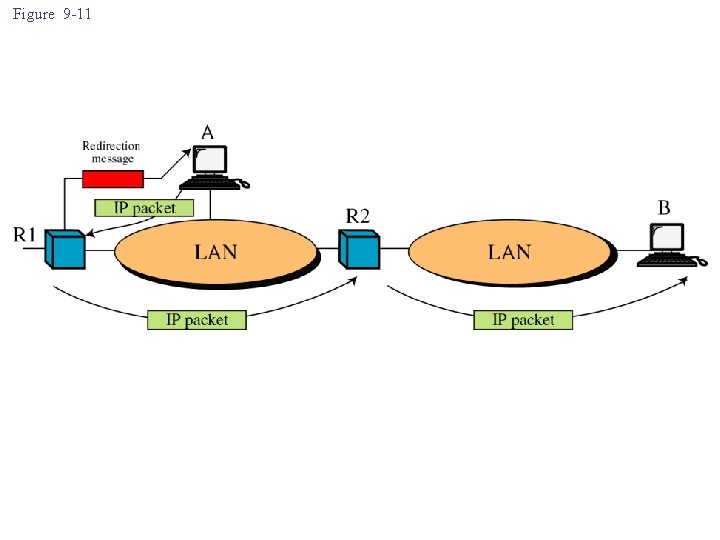
Redirection • When a router or host needs to send a packet destined for another network, it must know the IP address of the next appropriate router. • Router and host must have a routing table. • For efficiency hosts usually do not take part in the routing update process. – Static routing.

• The routing table of a host usually has a limited number of entries. – Knows the IP of only one router, the default router. • Host may send a datagram (to another network) to a wrong router. • The router that receives these datagram will – forward the datagram to a correct router. – update the routing table of the host by sending a redirection message.

Figure 9 -11

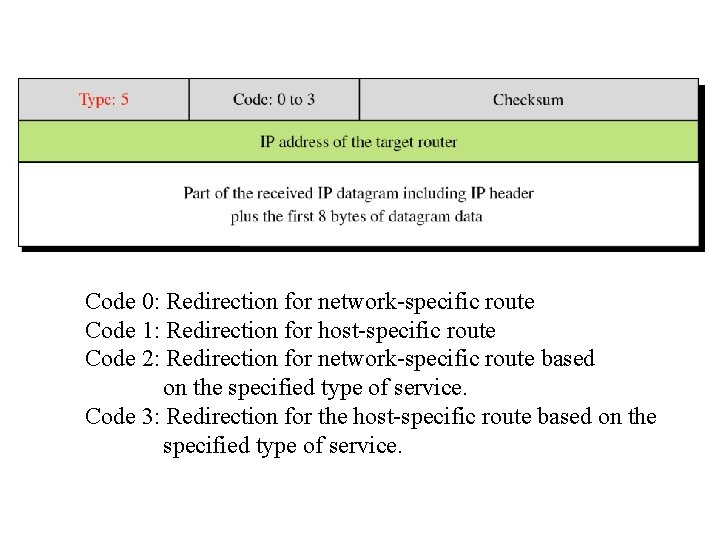
Code 0: Redirection for network-specific route Code 1: Redirection for host-specific route Code 2: Redirection for network-specific route based on the specified type of service. Code 3: Redirection for the host-specific route based on the specified type of service.

Figure 9 -6

• Some hosts that receives an ICMP redirect performs some checks before modifying its routing table. • These are to prevent a misbehaving router or host, or a malicious user, from incorrectly, modifying a system's routing table. • However, it is not difficult to create a bogus ICMP message, which can pass all these tests.

• Common items that may be verified. 1. The new router must be on a directly connected network. 2. The redirect message must be sent from the current router for that destination. 3. The redirect message cannot tell the host to use the sender of the redirect message as the router. 4. The route that's being modified must be an indirect route.

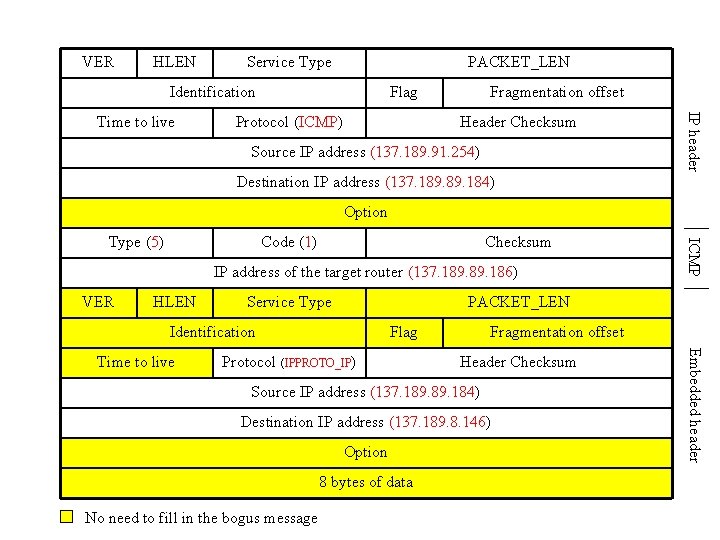
ICMP Spoofing • A hacker can fake an ICMP redirect message to achieve a similar effect of ARP cache poisoning. • Suppose the hacker (137. 189. 186) try to convince the target (137. 189. 184) that the shortest path to 137. 189. 8. 146 is through 137. 189. 186. Assume the original default router is 137. 189. 91. 254. • The following bogus packet will be sent.

VER HLEN Service Type PACKET_LEN Identification Protocol (ICMP) Fragmentation offset Header Checksum Source IP address (137. 189. 91. 254) IP header Time to live Flag Destination IP address (137. 189. 184) Option Code (1) Checksum IP address of the target router (137. 189. 186) VER HLEN Service Type PACKET_LEN Identification Flag Protocol (IPPROTO_IP) Fragmentation offset Header Checksum Source IP address (137. 189. 184) Destination IP address (137. 189. 8. 146) Option 8 bytes of data No need to fill in the bogus message Embedded header Time to live ICMP Type (5)

• Some Properties of ICMP redirect – Unlike ARP cache entries, those host routes won’t expire with time. • for some systems, they do expire • In our redhat 7. 3 system, the udpated entries are stored in cache, and these entries will be expired. – Attack can be launched from anywhere. – The target can be stopped from talking to any particular address not on the same subnet. (Do. S)

Possible types of attacks • • Sniffing Man-in-the-middle attack Session hijack Do. S – Nameserver – Router

Demonstration • We will discuss the program “icmp_redir. c” • Experiment – Use Ethereal to capture the spoofed icmp redirect message. – Use the command “route -n. C” to show that the target machine will accept the redirect and updates its routing cache table. – We can further show that subsequence packets sent to the original destination will be redirected to the “dummy host”.

Preventions • Firewall – Block all the ICMP redirect messages coming outside the LAN. – It is not wise to rely on the firewall only. – Cannot block those hackers that can access your LAN. • Simply stop the ICMP redirect features – Disable your host to accept any ICMP redirect message.

• For redhat 6. 1 for f in /proc/sys/net/ipv 4/conf/*/accept_redirects; do echo 0 > $f done • For redhat 6. 2 or above Edit the /etc/sysctl. conf file and add the following line: # Disable ICMP Redirect Acceptance net. ipv 4. conf. all. accept_redirects = 0 net. ipv 4. conf. eth 0. accept_redirects = 0 • You must restart your network for the change to take effect /etc/rc. d/init. d/network restart

References • Yuri Volobuev, “Playing redir games with ARP and ICMP”, it doesn’t seem to be published formally. • Forouzan, “TCP/IP protocol Suite”. , Chapter 9. (Introduction to ICMP)