Reconnaissance Recon 1 Attack Phases Phase 1 Reconnaissance















![Google Search Directives q site: [domain] o Searches particular domain o site: cs. sjsu. Google Search Directives q site: [domain] o Searches particular domain o site: cs. sjsu.](https://slidetodoc.com/presentation_image_h2/caa30dd12519a6b7ea58c551cdd173eb/image-19.jpg)
![Google Search Directives q related: [site] o Similar sites, based on Google’s indexing o Google Search Directives q related: [site] o Similar sites, based on Google’s indexing o](https://slidetodoc.com/presentation_image_h2/caa30dd12519a6b7ea58c551cdd173eb/image-20.jpg)
![Google Search Directives q rphonebook: [name and city or state] q bphonebook: [name and Google Search Directives q rphonebook: [name and city or state] q bphonebook: [name and](https://slidetodoc.com/presentation_image_h2/caa30dd12519a6b7ea58c551cdd173eb/image-21.jpg)






















- Slides: 57

Reconnaissance Recon 1

Attack Phases Phase 1: Reconnaissance q Phase 2: Scanning q Phase 3: Gaining access q o Application/OS attacks o Network attacks/Do. S attacks Phase 4: Maintaining access q Phase 5: Covering tracks and hiding q Recon 2

Recon q Before bank robber robs a bank… o Visit the bank o Make friends with an employee (inside info) o Study alarm system, vault, security guard’s routine, security cameras plscement, etc. o Plan arrival and get away Most of this is not high tech q Similar ideas hold for info security q Recon 3

Social Engineering q Hypothetical examples o New “admin” asks secretary for help o Angry “manager” calls employee/admin asking for password o “Employee” in the field calls another employee for help with remote access q Real-world examples o Employees help white hat guy steal company IP o Person turns over secrets to trusted “friend” Recon 4

Social Engineering q Social engineering o Defeats strongest crypto, best access control, protocols, IDS, firewalls, software security, etc. q Attacker may not even touch keyboard q Ultimate low-tech recon/attack method Recon 5

Social Engineering q Telephone based attacks o Company phone number may give attacker instant credibility Attacker might ask for voice mail service q Spoofed caller ID q o o Recon Appears attacker has company phone number Online services: Telespoof, Camophone Some Vo. IP software Phone companies also sell such services 6

Camophone q Spoofed caller ID q Cost? q 5 cents per minute Recon 7

Social Engineering Defenses q Hard to defend against o Rooted in human nature o Many legitimate uses of “social engineering” (police, sales people, etc. ) q User education helps o Do not give out sensitive info (passwords) o Do not trust caller ID, etc. q May not want totally paranoid employees Recon 8

Physical Security q If Trudy gets physical access… q Might find logged in computer, post-it note with passwords, etc. q Might install back door, keystroke logger, access point to LAN, etc. q Could steal USB drives, laptop, computers, CDs, etc. Recon 9

Physical Access q How can attacker gain physical access? o Ask for it o Fake it o Physical break in q Or attacker might be employee o Then Trudy already has access o Limit employee’s physical access? Recon 10

Defenses q Require badges for entry o What if someone forgets badge? q Biometrics for entry are useful o Iris scan, hand geometry, … q Monitor what people take in/out o Laptop, USB drive, CD, Furby? o Miniaturization makes this difficult Recon 11

Defenses q Use locks on file cabinets o Don’t leave key in the lock… q Automatic screen saver with pwd q Encrypted hard drives o Especially for those who travel o Need a way to recover encrypted files o But there attacks… Recon 12

Dumpster Diving q What might Trudy find in trash? o CDs, DVDs, discarded machines, USB, … o Diagrams of network architecture q Defenses o Destroy hard drive before discarding o Destroy media (degaussing is not enough) o Shred paper, etc. Recon 13

Search the “Fine” Web q “Fine” is placeholder for another word o As in “Read the ‘Fine’ Documentation” q Huge amount of info available on Web q Google it! o For example Google the MD 5 hash value o 20 f 1 aeb 7819 d 7858684 c 898 d 1 e 98 c 1 bb Recon 14

Google Hacking q Using Google to help in attacks o Not “hacking Google” q See, for example o Johnny Long’s Website o Google hacking 101 q Google selected as “favorite hacking tool” by some infamous hackers Recon 15

Google Four important elements of Google bot q 1. o Crawls Web looking for info to index o o o Billions served… Ranked using (secretive) algorithm Why so secretive? 2. Recon Google index 16

Google 3. 4. Google cache o o Copy of data that bots found Includes html, doc, pdf, ppt, etc. Up to 101 k of text each, no images See also, Wayback Machine o o o Program need to Google too Requires API “key” (free from Google) Limited to 1 k searches per day Google API Recon 17

Google q For any Google search… o Max number of results limited to 1, 000 o Limits data mining capabilities q So searches must be precise q Use “search directives” o No space after directive, searches case insensitive, max of 10 search terms Recon 18
![Google Search Directives q site domain o Searches particular domain o site cs sjsu Google Search Directives q site: [domain] o Searches particular domain o site: cs. sjsu.](https://slidetodoc.com/presentation_image_h2/caa30dd12519a6b7ea58c551cdd173eb/image-19.jpg)
Google Search Directives q site: [domain] o Searches particular domain o site: cs. sjsu. edu stamp q link: [web page] o All sites linked to a given web page o link: www. cs. sjsu. edu q intitle: [term(s)] o Web sites that include “term(s)” in title o site: cs. sjsu. edu intitle: ”index of” stamp Recon 19
![Google Search Directives q related site o Similar sites based on Googles indexing o Google Search Directives q related: [site] o Similar sites, based on Google’s indexing o](https://slidetodoc.com/presentation_image_h2/caa30dd12519a6b7ea58c551cdd173eb/image-20.jpg)
Google Search Directives q related: [site] o Similar sites, based on Google’s indexing o related: www. cs. sjsu. edu q cache: [page] o Display Web page from Google’s cache o cache: www. cs. sjsu. edu q filetype: [suffix] o Like ppt, doc, etc. o filetype: ppt site: cs. sjsu. edu stamp Recon 20
![Google Search Directives q rphonebook name and city or state q bphonebook name and Google Search Directives q rphonebook: [name and city or state] q bphonebook: [name and](https://slidetodoc.com/presentation_image_h2/caa30dd12519a6b7ea58c551cdd173eb/image-21.jpg)
Google Search Directives q rphonebook: [name and city or state] q bphonebook: [name and city or state] o Residential phone book o rphonebook: Mark Stamp Los Gatos o Business phone book q phonebook: [name and city or state] o Residential and business phone books Recon 21

Other Search Operations q Literal match (“ ”) o “metamorphic engines” site: cs. sjsu. edu q Not (-) o Filter out sites that include term o site: cs. sjsu. edu -ty -lin q Plus (+) o Include (normally filtered) term o Not the opposite of “+” o site: cs. sjsu. edu stamp +the Recon 22

Interesting Searches q From the text o o o o Recon site: mybank. com filetype: xls ssn site: mybank. com ssn -filetype: pdf site: mybank. com filetype: asp site: mybank. com filetype: cgi site: mybank. com filetype: php site: mybank. com filetype: jsp site: cs. sjsu. edu filetype: xls 23

Google Hacking Database q Google Hacking Database (GHDB) q Interesting searches o o Recon intitle: ”index of” finance. xls “welcome to intranet” intitle: ”gateway configuration menu” intitle: ”samba web administration tool” intext: ”help workgroup” 24

GHDB Intitle: ”welcome to IIS 4. 0” q “… we find that even if they've taken the time to change q their main page, some dorks forget to change the titles of their default-installed web pages. This is an indicator that their web server is most likely running … the now considered OLD IIS 4. 0 and that at least portions of their main pages are still exactly the same as they were out of the box. Conclusion? The rest of the factory-installed stuff is most likely lingering around on these servers as well. … Factory-installed default scripts: FREE with operating system. Getting hacked by a script kiddie that found you on Google: PRICELESS. For all the things money can't buy, there's a google. Dork award. ” Recon 25

Google q Suppose sensitive data is accessible o Removing it does not remove problem o Google cache, Wayback Machine q What about automated searches? o Google API o Site. Digger and Wikto Recon 26

Site. Digger User provides Google API key q One search… q o Uses GHDB o Does 1 k Google searches o Your daily limit o There’s always tomorrow… Recon 27

Google q Lots of other interesting Google searches o Track current flights o Look up auto VIN o Look up product UPC q Google filters some sensitive data o SSNs, for example q Yahoo and MSN Search do less filtering Recon 28

Newsgroups “Listening in at the virtual water cooler” q Employees submit detailed questions q o How to configure something o How to code something o How to troubleshoot a problem q Reveals info about products, config, etc. o “sensitive information leakage on a grand scale” q Attacker could even play active role o Give bad/incorrect advice Recon 29

Newsgroups q To search groups o groups. google. com o Repackaged version of Deja. News Recon 30

Organization’s Website q Web o o o Recon site might reveal useful info Employee contact info Clues about corporate culture/language Business partners Recent mergers and acquisitions Technology in use Open jobs 31

Defenses Against Web Recon q Limit what goes on Web pages o No sensitive info o Limit info about products, configuration, … q Security by obscurity? o “…no sense putting an expensive lock on your door and leaving milk and cookies outside so the lock picker can have a snack” while he breaks in Recon 32

Defenses Against Web Recon Have a policy on use of newsgroups q Monitor publicly available info q Google/Wayback will remove sensitive data q Use robots. txt so Web pages not indexed q o Tags: noindex, nofollow, noarchive, nosnippet o Well-behaved crawlers will respect these, but… o …a sign to bad guys of sensitive data Recon 33

Whois Databases q Internet “white pages” listing o Domain names, contact info, IP addresses o. com, . net, . org, . edu q ICANN oversees registration process o Hundreds of actual registrars Recon 34

Inter. NIC q Inter. NIC (Internet Network Info Center) o First place to look o Info on domain name registration services Recon 35

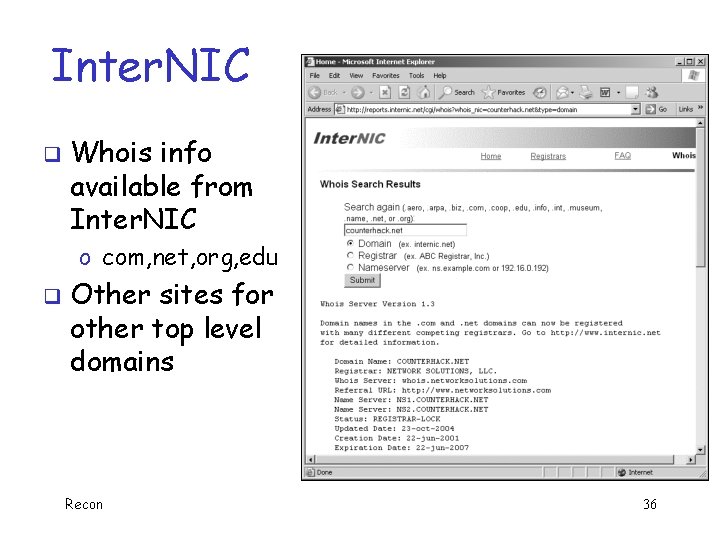
Inter. NIC q Whois info available from Inter. NIC o com, net, org, edu q Other sites for other top level domains Recon 36

Whois q Once registrar is known, attacker can contact it o More detailed Whois info o Network Solutions in this example Recon 37

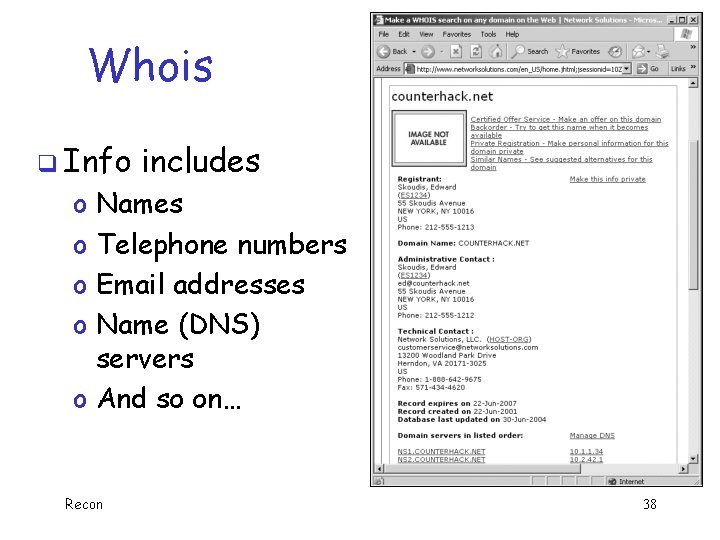
Whois q Info includes Names Telephone numbers Email addresses Name (DNS) servers o And so on… o o Recon 38

IP Address Assignment q ARIN (American Registry for Internet Numbers) o Info about who owns IP address or range of addresses q Similar organizations for Europe, Asia, Latin America, … Recon 39

Defense Against Whois Search q Bad idea to put false info into databases o Important that people can contact you o For example, if attack launched from your site No real defense against Whois q Anonymous registration services exist q o Author is not fond of these o Better to train against social engineering Recon 40

Domain Name System q DNS o A hierarchical distributed database o Like a (hierarchical distributed) telephone directory o Converts human-friendly names into computer-friendly IP addresses q Internet Recon is impossible without DNS 41

DNS q 13 root DNS servers o A “single point” of failure for Internet Recon 42

q DNS example DNS o Recursive and iterative searches o Resolved locally, if possible o Lots and lots of caching Recon 43

DNS q DNS Recon cache on Windows machine 44

DNS Gives IP address of a domain q Lots of other info q DNS record types q o o o Recon Address: domain name/IP address (or vice-versa) Host information: info about system Mail exchange: mail system info Name server: DNS servers Text: arbitrary text string 45

Interrogating DNS q Attacker determines DNS servers o From registrar’s Whois database q Use nslookup (or dig in Linux) to interrogate name servers o Zone transfer (all info about domain) o See example from text --- IP addresses, mail server names, OS types, etc. Recon 46

DNS Recon Defenses Remove info on OS types, etc. q Restrict zone transfers q o To primary and secondary name servers q Employ “split DNS” o Allow outside DNS activity related to Web, mail, FTP, …, servers o No outside DNS directly from internal network Recon 47

Split DNS q Internal DNS server acts as proxy o Relays requests to external DNS o Internal users can resolve internal and external Recon 48

General-Purpose Recon Tools q Sam Spade o Detective character in Dashiell Hammett’s novel, The Maltese Falcon o Humphrey Bogart o Also a general Web-based recon tool q Research and attack portals o For more specific info Recon 49

Sam Spade All the bells and whistles q Some of Sam Spade’s capabilities q o ping, whois lookups, IP block whois, nslookup, DNS zone transfer, traceroute, finger o SMTP VRFY --- is given email address valid? o Web browser --- view raw HTTP interaction o Web crawler --- grab entire web site Recon 50

Sam Spade q “The incredibly useful Sam Spade user interface” Recon 51

Other General Recon Tools q Active Whois Browser o Whois and DNS tool, $19. 95 q Net. Scan. Tools Pro o Costs $249+ q i. Net. Tools o Feature-limited, but free Recon 52

Web-based Recon Tools q Some o o o o Recon “run by rather shady operators” www. samspade. org www. dnsstuff. com www. traceroute. org www. networktools. com www. cotse. com/refs. htm www. securityspace. com www. dlsreports. com 53

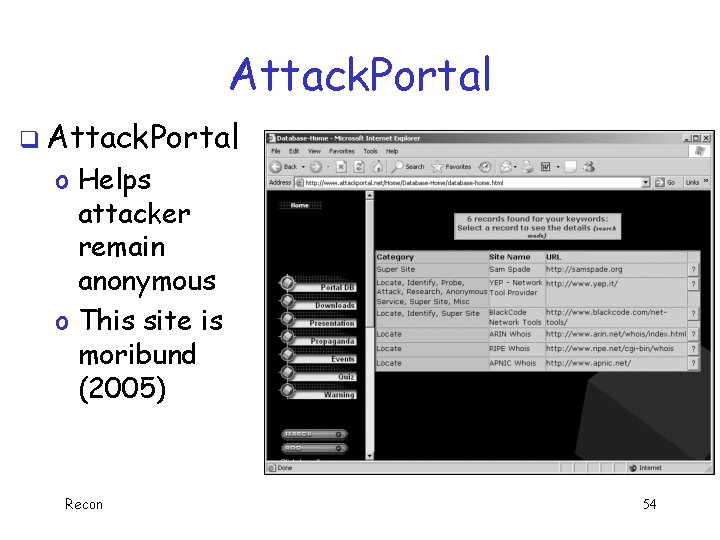
Attack. Portal q Attack. Portal o Helps attacker remain anonymous o This site is moribund (2005) Recon 54

Conclusion q Attacker can gain useful info from variety of sources o From social engineering to automated tools… o …and everything in between q Useful info might include o Contact info, IP addresses, domain names o Possibly system details, technologies used, … q Building blocks for actual attacks Recon 55

Summary q Sophisticated attacks likely to start with recon phase q Low-tech recon techniques o o Recon Social engineering Spoofed caller ID Physical access Dumpster diving 56

Summary q Higher-tech o o o Recon techniques Google hacking, Site. Digger, GHDB Whois databases, Inter. NIC, ARIN DNS, nslookup, dig Sam Spade, client-side recon tools Web-based recon tools 57