Network Reconnaissance What is n Military reconnaissance n







![Tool: ping n n n ping [hostname|ip_address] ping 6 [hostname|ip_address] ping -R [hostname|ip_address] 16 Tool: ping n n n ping [hostname|ip_address] ping 6 [hostname|ip_address] ping -R [hostname|ip_address] 16](https://slidetodoc.com/presentation_image_h2/6539780b4c076672b29a31cbade6df4d/image-16.jpg)







- Slides: 34

Network Reconnaissance

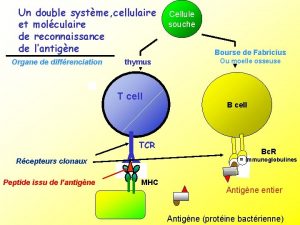
What is? n Military reconnaissance n n a mission conducted to confirm or deny prior intelligence (if any) about enemy threat and or the terrain of a given area. Network reconnaissance n process of acquiring information about a network 2

Why? n n n Hackers use reconnaissance as the first step in an effective attack Seeing what is on the "other side of the hill" is crucial to decide what type of attack to launch Generally, goals of reconnaissance on a target network are to discover: n n n IP addresses of hosts Accessible UDP and TCP ports OS type 3

Footprinting/Fingerprinting steps n Information Gathering n n Locate the network n n Which ports and applications are accessible OS Fingerprinting n n Which machine is actively connected to the network and reachable Open ports and underlying applications n n What addresses can be targeted and are available for additional scanning and analysis Identify active machines n n accumulating data regarding a specific network environment, usually for the purpose of finding ways to intrude into the environment Identifying targeted Oss as well as systems response Network mapping n Create blueprint of organization 4

Information Gathering n Get data regarding network environment such as n n Organization web site, Location, contact person, Phone number Common Tools n n n Registrar query : whois Domain name and resource lookup Search Tools 5

Locate the network range n n What range of IP addresses are available for scanning and further enumeration Common Tools : whois 6

Tool: WHOIS Search n Who. Is – Query of Internet Registries n Ref: http: //www. arin. net/community/rirs. html n Afri. NIC – Africa n APNIC - Asia/Pacific n ARIN – North America n LACNIC - Central and South America n RIPE NCC – Europe, Middle East, Central Asia n Inter. NIC– ICANN Public Domain Name Registration Info n 3 rd Party Whois Tools n Geektools - http: //www. geektools. com/whois. php n Domain. Tools – http: //www. domaintools. com/ n DNSStuff – http: //www. dnsstuff. com 7

Tool: WHOIS web interface 8

Tool: - Google n Google, Yahoo, Live. com, etc. n n n Gather information about a targeted organization Evaluate web sites for known security issues Identify files that are accidentally exposed to the public 9

Tool: - Google search n Helpful Google Queries n Related sites: n n Search a specific site: n n related: www. someaddr. com site: www. someaddr. com search_terms Use Google to search group or blog postings 10

Tool: – Google operators Google Advanced Operators AND: “+” OR: “|” Synonym: “~” site: www. jeffersonwells. com inurl: robots. txt link: www. jeffersonwells. com intitle: “jefferson wells” filetype: xls 11

Tool: NSLOOKUP n Queries Domain Name Server information n IP and Domain Name Mapping n Zone Transfer – Dumps entire table n Check mail server 12

Tool: NSLOOKUP n Zone Transfer – Dumps entire table $ nslookup > server = A. B. C. D > ls somedomain. com 13

Tool: NSLOOKUP n MX record $ nslookup > set type = MX > somedomain. com 14

Network Identifier Tools n n Identifying active computers and services Common Tools n ping, ping 6 n n help verifying whether a host is active traceroute, traceroute 6 n determine the route to a node 15
![Tool ping n n n ping hostnameipaddress ping 6 hostnameipaddress ping R hostnameipaddress 16 Tool: ping n n n ping [hostname|ip_address] ping 6 [hostname|ip_address] ping -R [hostname|ip_address] 16](https://slidetodoc.com/presentation_image_h2/6539780b4c076672b29a31cbade6df4d/image-16.jpg)
Tool: ping n n n ping [hostname|ip_address] ping 6 [hostname|ip_address] ping -R [hostname|ip_address] 16

Tool: traceroute n tracert n n Windows traceroute n Unix 17

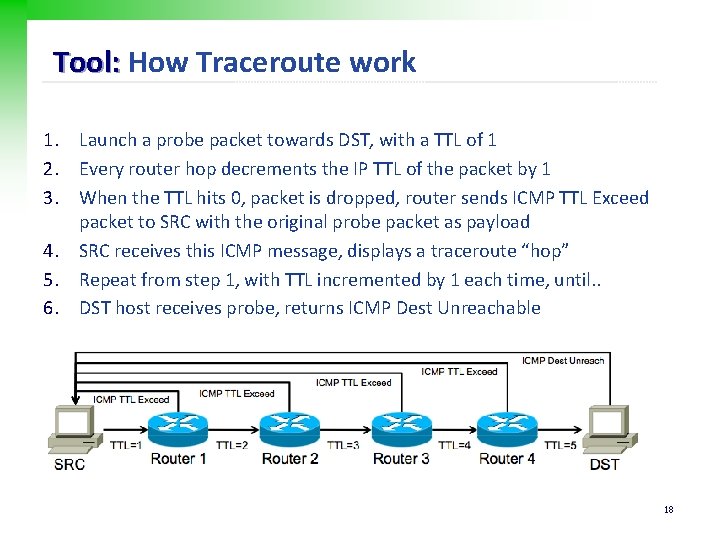
Tool: How Traceroute work 1. Launch a probe packet towards DST, with a TTL of 1 2. Every router hop decrements the IP TTL of the packet by 1 3. When the TTL hits 0, packet is dropped, router sends ICMP TTL Exceed packet to SRC with the original probe packet as payload 4. SRC receives this ICMP message, displays a traceroute “hop” 5. Repeat from step 1, with TTL incremented by 1 each time, until. . 6. DST host receives probe, returns ICMP Dest Unreachable 18

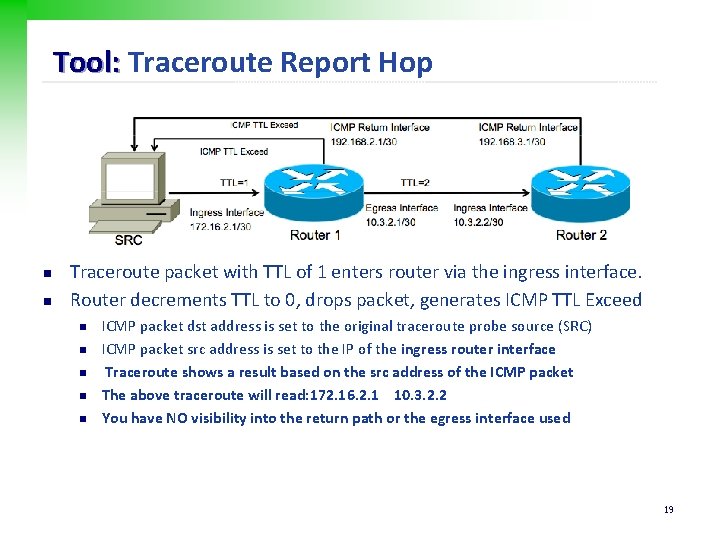
Tool: Traceroute Report Hop n n Traceroute packet with TTL of 1 enters router via the ingress interface. Router decrements TTL to 0, drops packet, generates ICMP TTL Exceed n n n ICMP packet dst address is set to the original traceroute probe source (SRC) ICMP packet src address is set to the IP of the ingress router interface Traceroute shows a result based on the src address of the ICMP packet The above traceroute will read: 172. 16. 2. 1 10. 3. 2. 2 You have NO visibility into the return path or the egress interface used 19

Tool: Traceroute Latency Calculation n How is traceroute latency calculated? n n Timestamp when the probe packet is launched Timestamp when the ICMP response is received Calculate the difference to determine round-trip time Routers along the path donot do anytime “processing” n n n They simply reflect the original packet’s data back to the SRC Many implementations encode the original launch timestamp into the probe packet, to increase accuracy and reduce state Most Importantly: only the ROUNDTRIP is measured n n Traceroute is showing you the hops on the forward path But showing you latency based on the forward PLUS reverse path. Any delays on the reverse path will affect your results! 20

Tool: Interprete Traceroute DNS n n Interpreting DNS is one of the most important aspects of correctly using traceroute Information you can uncover includes: n n Physical Router Locations Interface Types and Capacities Router Type and Roles Network Boundaries and Relationships 21

Tool: Traceroute Reading Tips n Router’s name may include Exchange Point n n n Router names may be the IATA 3 -letter code of the nearest airport or CLLI code in their node name Other abbreviation n n MAE, NAP, PAIX http: //www. sarangworld. com/TRACEROUTE/showdb-2. php 3 Interface name 22

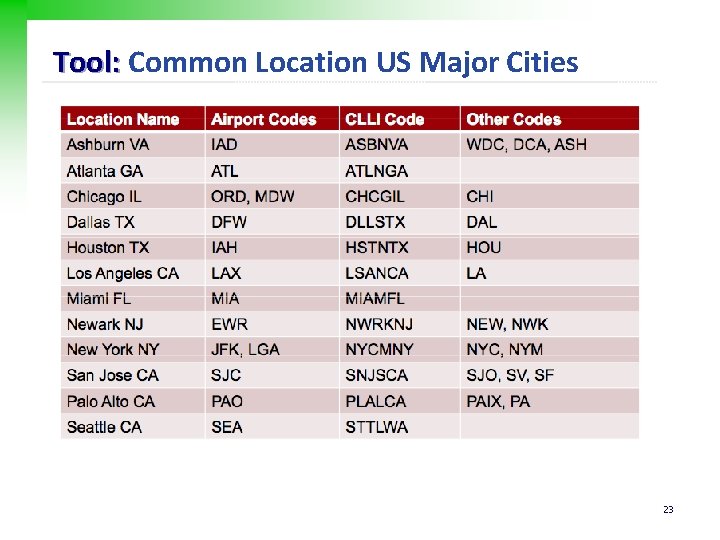
Tool: Common Location US Major Cities 23

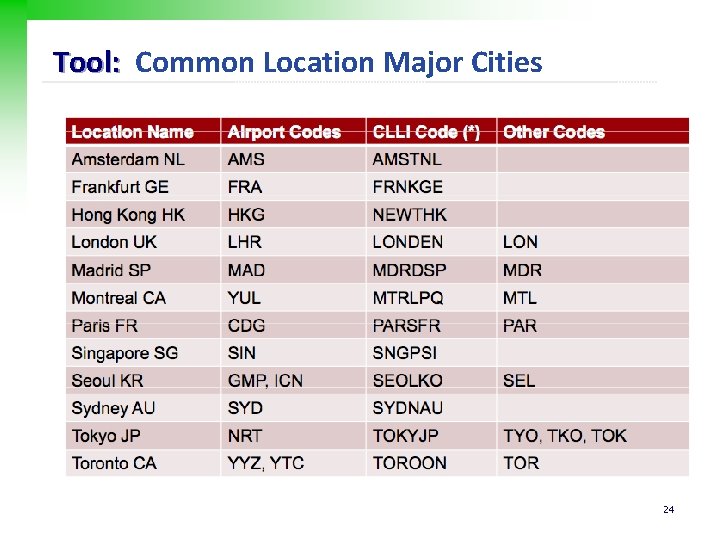
Tool: Common Location Major Cities 24

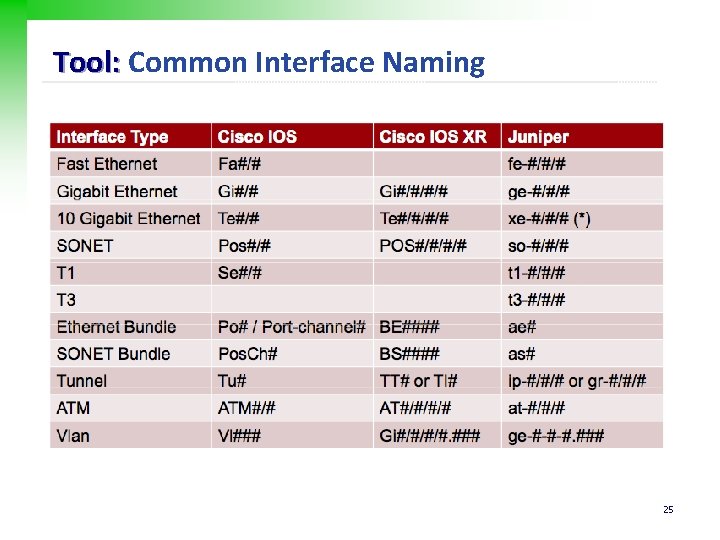
Tool: Common Interface Naming 25

Tool: Router Type/Role n n Knowing the role of a router can be useful But every network is different, and uses different naming conventions May not always follow naming rules Generally speaking, May need guessing the context and get a basic understanding of the roles n n n Core routers–CR, Core, GBR, BB Peering routers–BR, Border, Edge, IGR, Peer Customer routers–AR, Aggr, Cust, CAR, GW 26

Tool: DNS Interface type n n n Most networks will try to put interface info into DNS Though this many not always be up to date Many large networks use automatically generated DNS As well as capacity, and maybe even the make/model of router Examples: n xe-11 -1 -0. edge 1. Washington 1. Level 2. net n n n XE-#/#/# is Juniper 10 GE port. The device has at least 12 slots It’s at least a 40 G/slot router since it has a 10 GE PIC in slot 1 It must be Juniper MX 960, no other device could fit this profile 27

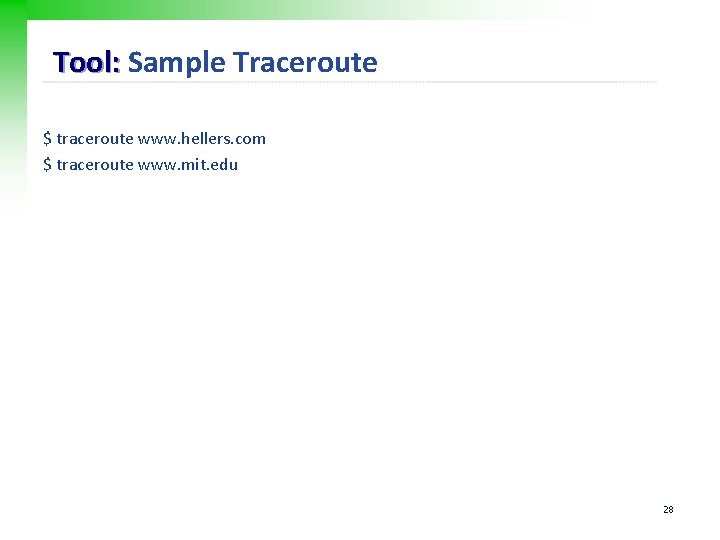
Tool: Sample Traceroute $ traceroute www. hellers. com $ traceroute www. mit. edu 28

Identifying Active Machines n n Attackers will want to know if machines are alive before they attempt to attack. One of the most basic methods of identifying active machines is to perform a sweep Common Tools n n ping, traceroute Network scanning tools n nmap, superscan 29

Finding Open Ports n Open services n Common tools n Port scanning tools n nmap, superscan 30

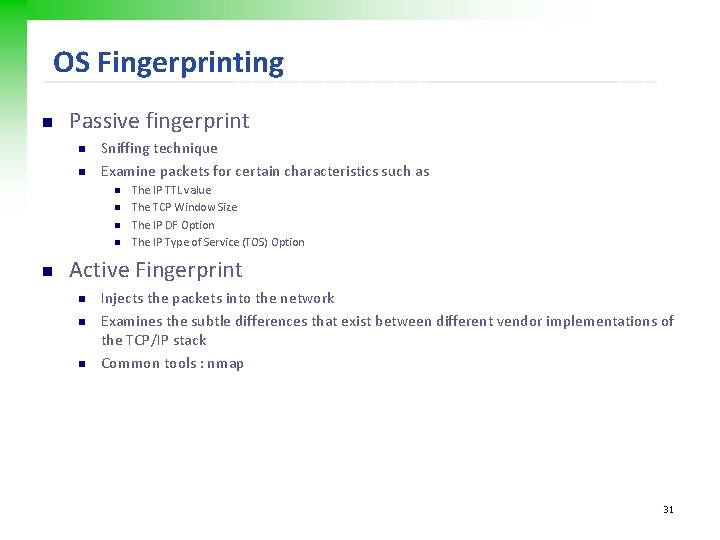
OS Fingerprinting n Passive fingerprint n n Sniffing technique Examine packets for certain characteristics such as n n n The IP TTL value The TCP Window Size The IP DF Option The IP Type of Service (TOS) Option Active Fingerprint n n n Injects the packets into the network Examines the subtle differences that exist between different vendor implementations of the TCP/IP stack Common tools : nmap 31

Mapping the Network n n n Gained enough information to build network map Network mapping provides the hacker with a blueprint of the organization. May use manual or automated ways to compile this information 32

Summary Method Technique Common Tools Information gathering Passive Whois, nslookup Determining network range Passive RIPE, LACNIC, APNIC, ARIN Identify active machines Active ping, hping, traceroute, nmap, Super. Scan Finding open ports/applications Active nmap, Amap, Super. Scan Active/passive nmap, Winfigerprint, P 0 f, Xprobe 2, ettercap OS fingerprinting Mapping the network Active Carto. Reso, traceroute, Neo. Trace 33

Q&A 34
 Network mapping reconnaissance
Network mapping reconnaissance Network reconnaissance tools
Network reconnaissance tools Military training network bls
Military training network bls Reconnaissance tih
Reconnaissance tih Types of patrols
Types of patrols Textbook reconnaissance
Textbook reconnaissance Reconnaissance intelligente de caractères
Reconnaissance intelligente de caractères Prc-137 hf radio
Prc-137 hf radio Reconnaissance visuelle des objets
Reconnaissance visuelle des objets Reconnaissance in to kill a mockingbird
Reconnaissance in to kill a mockingbird Double reconnaissance
Double reconnaissance Mounim el yacoubi
Mounim el yacoubi Reconnaissance strike group
Reconnaissance strike group Special amphibious reconnaissance corpsman
Special amphibious reconnaissance corpsman Reconnaissance magnetic
Reconnaissance magnetic Aircraft reconnaissance
Aircraft reconnaissance La reconnaissance du travail bien fait
La reconnaissance du travail bien fait Lunaf.com 14.01.2004
Lunaf.com 14.01.2004 Lspcc reconnaissance d'appartement
Lspcc reconnaissance d'appartement Features of peer to peer network and client server network
Features of peer to peer network and client server network Network systems design using network processors
Network systems design using network processors Datagram switching
Datagram switching Network centric computing
Network centric computing Network topology in computer network
Network topology in computer network Packet switching advantages and disadvantages
Packet switching advantages and disadvantages Custom fabric solutions for military use
Custom fabric solutions for military use The crusades were military expeditions undertaken by
The crusades were military expeditions undertaken by Military arms race
Military arms race Cal maritime tuition
Cal maritime tuition Which egyptian ruler avoided military conquests
Which egyptian ruler avoided military conquests Military branches
Military branches Sbp military cost
Sbp military cost Us military marking system for hazardous materials
Us military marking system for hazardous materials What time is 1805 in military hours
What time is 1805 in military hours Military customs and courtesies
Military customs and courtesies