Network security Cs 634 IS 605 1 Agenda




































- Slides: 47

Network security Cs 634 IS 605 1

Agenda Course Content Materials Assessment 2

Course Content Introduction of computer security Cryptology Public key infrastructure Authentication and Authorization Search Topics 3

Materials Lecture note : http: //scholar. cu. edu. eg/? q=nermin-hamza/ Research Documents Book 1 : Jie Wang, “Computer Network Security -Theory and Practice”, @2009 Higher Education Press Book 2 S. K. PARMAR, Cst , “INFORMATION RESOURCE GUIDE- Computer, Internet and Network Systems Security”, Book 3 William Stallings, “ Cryptography and Network Security - principles 4 and practice” , 5 th edition

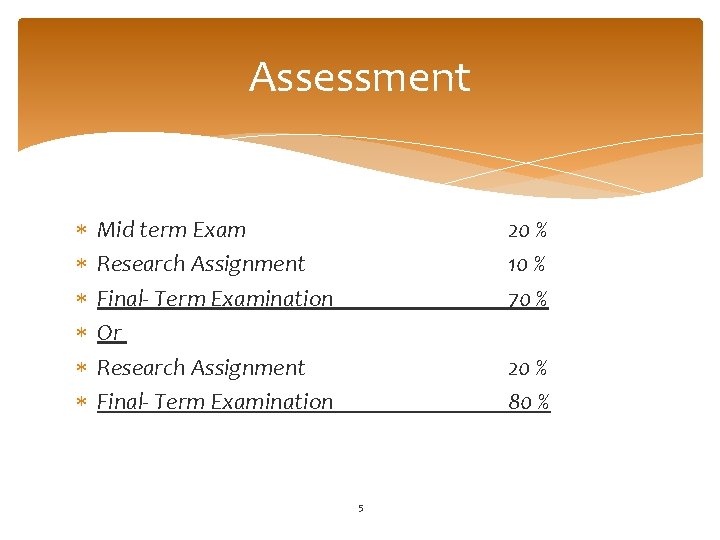
Assessment Mid term Exam Research Assignment Final- Term Examination Or Research Assignment Final- Term Examination 20 % 10 % 70 % 20 % 80 % 5

Let’s start Introduction 6

Attacks, services and mechanisms Security attacks Security services Methods of Defense A model for Internetwork Security 7

Attacks, Services and Mechanisms Security Attack: Any action that compromises the security of information. Security Mechanism: A mechanism that is designed to detect, prevent, or recover from a security attack. Security Service: A service that enhances the security of data processing systems and information transfers. A security service makes use of one or more security mechanisms 8

Security Attack Definition: Any action that compromises the security of information owned by an organization Information security is about how to prevent attacks, or failing that, to detect attacks on information-based systems 9

Security Attack Threats ﺗﻬﺪﻳﺪ mean anything that can interrupt the operation, functioning, integrity, or availability of a network or system, these can take any forms. Vulnerabilities ﺛﻐﺮﻩ are inherent weakness in the design, configuration, implementation, or management of the network or the system that renders it to be susceptible to threats. Attacks ﻫﺠﻮﻡ are a specific technique used to exploit the vulnerabilities 10

Purpose of attacking? Sometimes the damage is done on purpose Malicious attacks from disgruntled people (e. g. ex-employees) Snoop attacks from nosey co-workers Acts of vandalism Espionage ﺗﺠﺴﺲ 11

Purpose of attacking? What do they hope to gain? bragging rights, simply to say “I did it!” theft of information theft of service theft of real assets/money defacement/vandalism destruction of data corruption of data 12

Purpose of attacking? corruption of operational systems controlled by computers (phone system, TV systems, etc. ) denial of service plant ‘bots which can be remotely activated and controlled to accomplish any of the attacks listed above using your machine as the host 13

General Attacks 14

Insider and ousider � Insider attack The insider is already an authorized user Insider acquires privileged access exploiting bugs in privileged system programs Install backdoors/Trojan horses to facilitate subsequent acquisition of privileged access Outsider attack � Acquire access to an authorized account � Perpetrate an insider attack 15

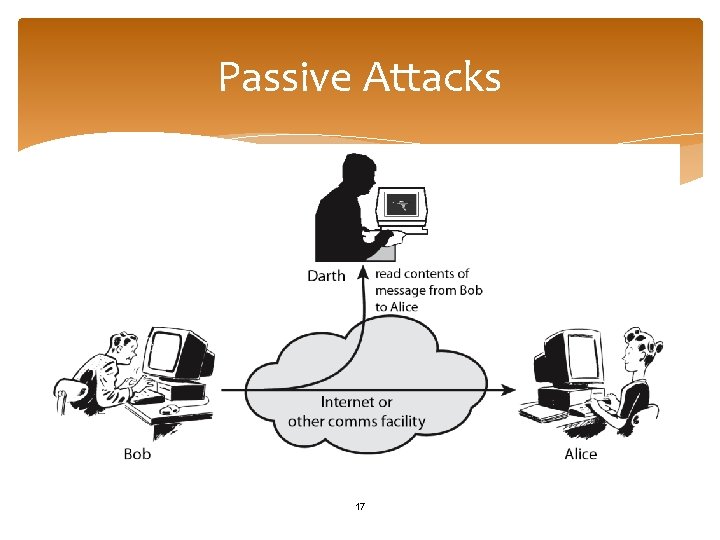
Passive and Active Attack Passive Attack: when the attacked entity is unaware of the attack, hence called PASSIVE e. g. the attacker is just trying to listen or observer you. Active attack: is an attack which the attacked entity gets aware of when attacked. That is the interruption from the attacker is of such kind that he gets aware of the attack, hence called active attack. For example trying to steal some info 16

Passive Attacks 17

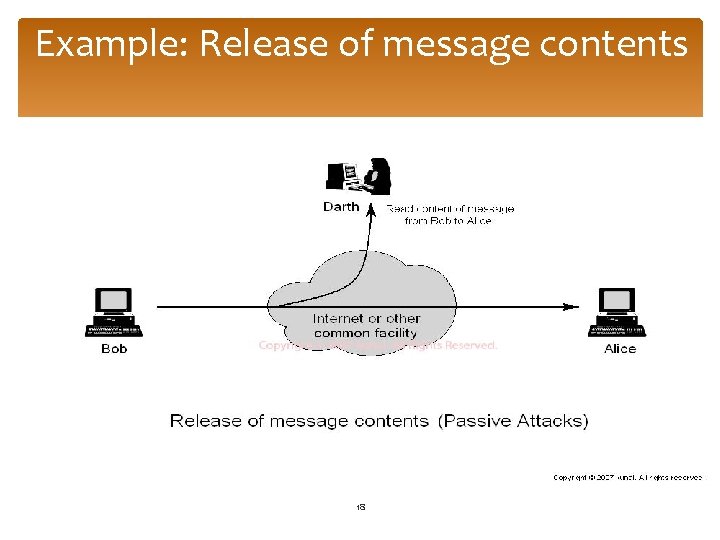
Example: Release of message contents 18

Passive Attacks Release of message contents A telephone conversation, an E-mail messages, and file transfer can be easily accessed without effecting the message. Traffic analysis To observe pattern of messages from sender and receiver. 19

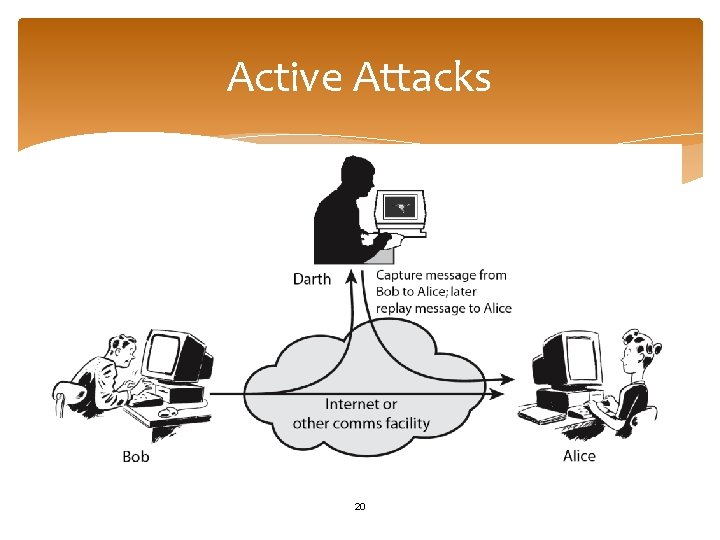
Active Attacks 20

Active Attacks Replay Attack: A hacker executes a replay attack by intercepting and storing a legitimate transmission between two systems and retransmitting it at a later time. Denial-of-Service (Do. S) Attacks: attempt to exhaust the network or server resources in order to render it useless for legitimate hosts and users. Masquerading server attack in which an attacker pretends to be as a legal server by creating a valid responding message from an eavesdropped communication between the remote server S and a user A 21

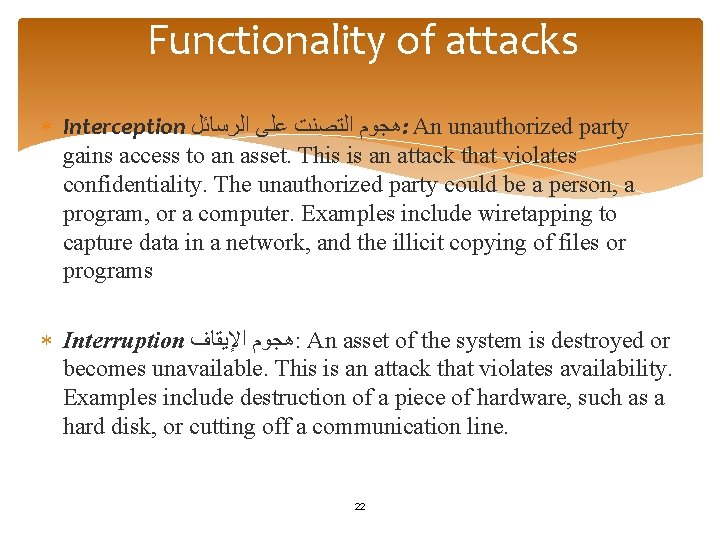
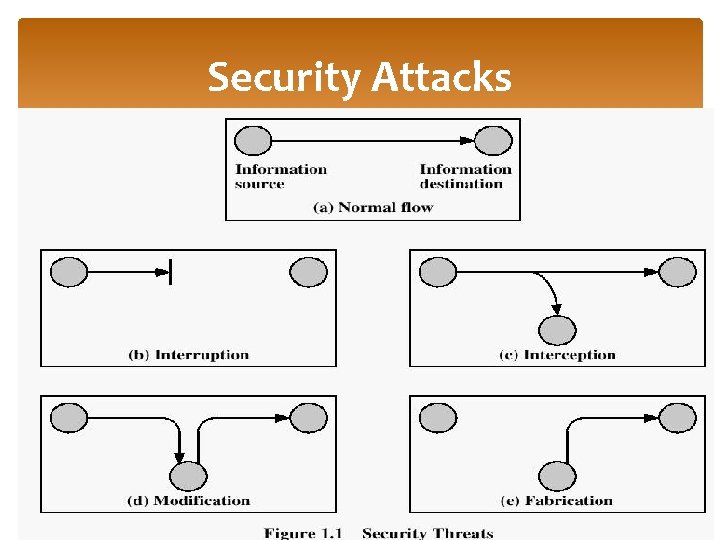
Functionality of attacks Interception ﻫﺠﻮﻡ ﺍﻟﺘﺼﻨﺖ ﻋﻠﻰ ﺍﻟﺮﺳﺎﺋﻞ : An unauthorized party gains access to an asset. This is an attack that violates confidentiality. The unauthorized party could be a person, a program, or a computer. Examples include wiretapping to capture data in a network, and the illicit copying of files or programs Interruption ﻫﺠﻮﻡ ﺍﻹﻳﻘﺎﻑ : An asset of the system is destroyed or becomes unavailable. This is an attack that violates availability. Examples include destruction of a piece of hardware, such as a hard disk, or cutting off a communication line. 22

Active Attacks Modification ﻫﺠﻮﻡ ﻳﻌﺪﻝ ﻋﻠﻰ ﻣﺤﺘﻮﻯ ﺍﻟﺮﺳﺎﻟﺔ : An unauthorized party does not only gain access to the asset, but also tampers it. This is an attack that violates integrity. Examples include value manipulation in the date file, and modifying the content of messages being transmitted in a network. Fabrication ﻟﻬﺠﻮﻡ ﺍﻟﻤﺰﻭﺭ ﺃﻮ ﺍﻟﻤﻔﺒﺮﻙ : An unauthorized party installing a malicious object or program on the system. This is an attack that violates authenticity. Examples include the insertion of spurious messages in a network or the addition of records to a file. 23

Security Attacks 24

What are the kinds of attacks? Denial of Service (Do. S) attacks Do. S attacks have one goal – to knock your service off the net. Crash your host Flood the network connecting to your host 25

What are the kinds of attacks? Viruses A computer virus attaches itself to files on the target machine Master Boot Sector/Boot Sector viruses File viruses, Macro viruses Stealth viruses, Polymorphic viruses Hoax Viruses 26

What are the kinds of attacks? Trojans, Worms and Backdoors Trojans are programs that appear to perform a desirable and necessary function that perform functions unknown to (and probably unwanted by) the user. Worms are memory resident viruses. Unlike a virus, which seeds itself in the computer's hard disk or file system, a worm will only maintain a functional copy of itself in active memory. 27

What are the kinds of attacks? Worms frequently “sleep” until some event triggers their activity - send password file to hacker, send copy of registry to hacker. Worms and Trojans are frequently methods by which Backdoors are enabled on a system. Backdoors allow hidden access and control of a system (e. g. Back Orifice, BO 2 K, Sub. Seven). 28

What are the kinds of attacks? Scanners Programs that automatically detect security weaknesses in remote or local hosts. Tells the hacker: What services are currently running What users own those services Whether anonymous logins are supported Whether certain network services require authentication 29

What are the kinds of attacks? Password Crackers Some actually try to decrypt. . Most simply try “brute force” or intelligent “brute force” Dictionary words, days of year, initials 30

What are the kinds of attacks? Sniffers monitor network data. Devices that capture network packets Extremely difficult to detect because they are passive 31

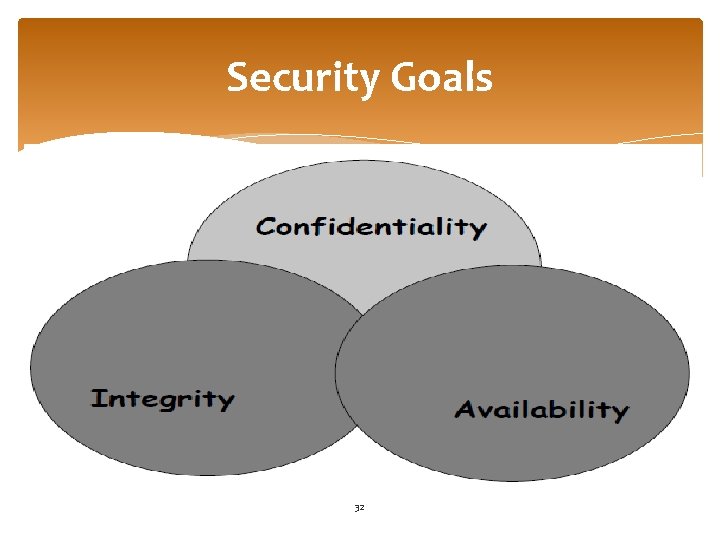
Security Goals 32

Security Service Enhance security of data processing systems and information transfers of an organization Intended to counter security attacks Using one or more security mechanisms Often replicates functions normally associated with physical documents Which, for example, have signatures, dates; need protection from disclosure, tampering, or destruction; be notarized or witnessed; be recorded or licensed 33

Security Services: Authentication Concerned with assuring that a communication is authentic. Confidentiality : ◦ Preventing the sensitive information from unauthorized user. Integrity : ◦ Preventing the information from modification by unauthorized users. Availability: ◦ Assuring that the authorized users have timely access to the information in the system and to the network. Access Control: ◦ Ability to limit and control the access to the host systems and applications via communication links. Non-repudiation: ◦ Preventing either sender or receiver from denying a transmitted message. 34

Security Mechanism A process that is designed to detect, prevent or recover from a security attack No single mechanism that will support all services required However one particular element underlies many of the security mechanisms in use: cryptographic techniques 35

Methods of Defense Encryption Software Controls (access limitations in a data base, in operating system protect each user from other users) Hardware Controls (smartcard) Policies (frequent changes of passwords) Physical Controls 36

Methods of Defense 1. Encryption is the formal name for the scrambling process. We take data in their normal, unscrambled state, called cleartext, and transform them so that they are unintelligible to the outside observer; the transformed data are called enciphered text or ciphertext. Using encryption, security professionals can virtually nullify the value of an interception and the possibility of effective modification or fabrication. 37

Methods of Defense 2. Software Controls If encryption is the primary way of protecting valuables, programs themselves are the second facet of computer security. Programs must be secure enough to prevent outside attack. They must also be developed and maintained so that we can be confident of the programs' dependability. 38

Methods of Defense Program controls include the following: internal program controls: parts of the program that enforce security restrictions, such as access limitations in a database management program operating system and network system controls: limitations enforced by the operating system or network to protect each user from all other users independent control programs: application programs, such as password checkers, intrusion detection utilities, or virus scanners, that protect against certain types of vulnerabilities development controls: quality standards under which a program is designed, coded, tested, and maintained to prevent software faults from becoming exploitable vulnerabilities. 39

Methods of Defense 3. Hardware Controls Numerous hardware devices have been created to assist in providing computer security. These devices include a variety of means, such as hardware or smart card implementations of encryption locks or cables limiting access or deterring theft devices to verify users' identities firewalls intrusion detection systems 40

Methods of Defense 4. Policies and Procedures Sometimes, we can rely on agreed-on procedures or policies among users rather than enforcing security through hardware or software means. In fact, some of the simplest controls, such as frequent changes of passwords, can be achieved at essentially no cost but with tremendous effect. Training and administration follow immediately after establishment of policies, to reinforce the importance of security policy and to ensure their proper use. 41

Methods of Defense 5. Physical Controls Some of the easiest, most effective, and least expensive controls are physical controls. Physical controls include locks on doors, guards at entry points, backup copies of important software and data, and physical site planning that reduces the risk of natural disasters. Often the simple physical controls are overlooked while we seek more sophisticated approaches. 42

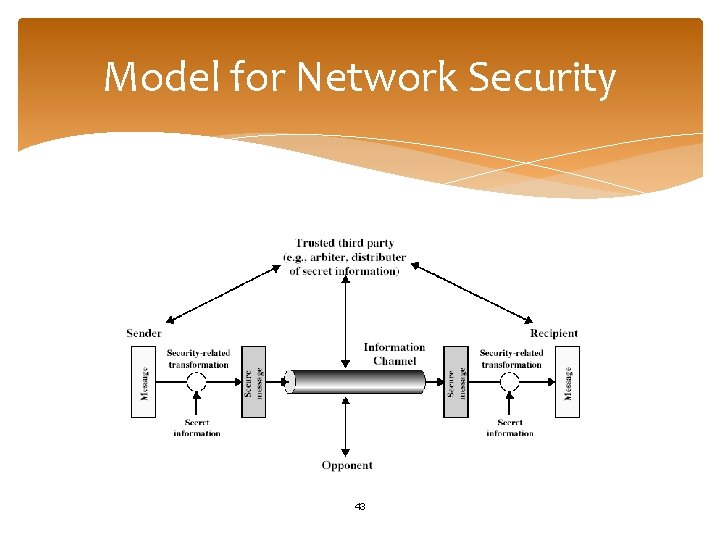
Model for Network Security 43

Model for Network Security Using this model requires us to: 1. design a suitable algorithm for the security transformation 2. generate the secret information (keys) used by the algorithm 3. develop methods to distribute and share the secret information 4. specify a protocol enabling the principals to use the transformation and secret information for a security service 44

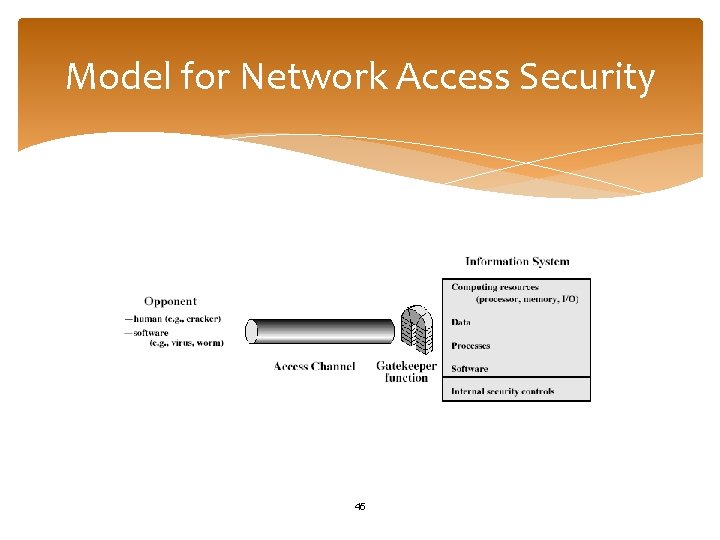
Model for Network Access Security 45

Model for Network Access Security Using this model requires us to: 1. select appropriate gatekeeper functions to identify users 2. implement security controls to ensure only authorised users access designated information or resources trusted computer systems may be useful to help implement this model 46

First Assignment Summary of the first Lecture