Chapter 1 Modern Network Security Threats CCNA Security






























- Slides: 67

Chapter 1: Modern Network Security Threats CCNA Security v 2. 0

1. 0 Introduction 1. 1 Securing Networks 1. 2 Network Threats 1. 3 Mitigating Threats 1. 4 Summary © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 2

Upon completion of this section, you should be able to: • Describe the current network security landscape. • Explain how all types of networks need to be protected. © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 3

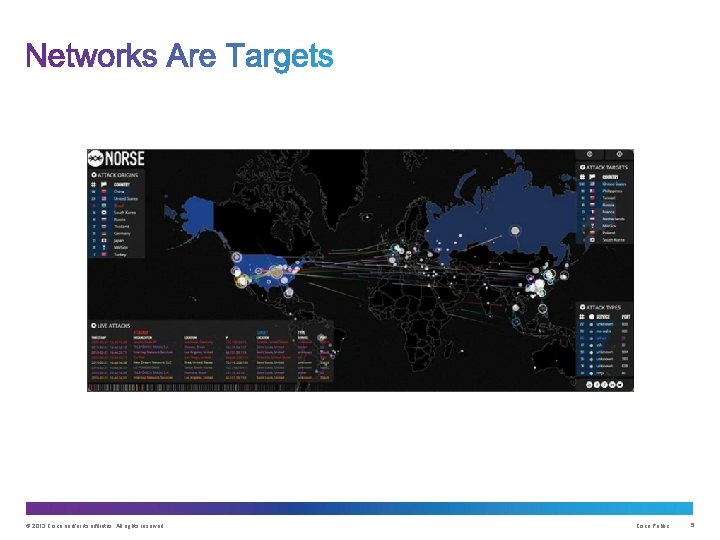
© 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 4

© 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 5

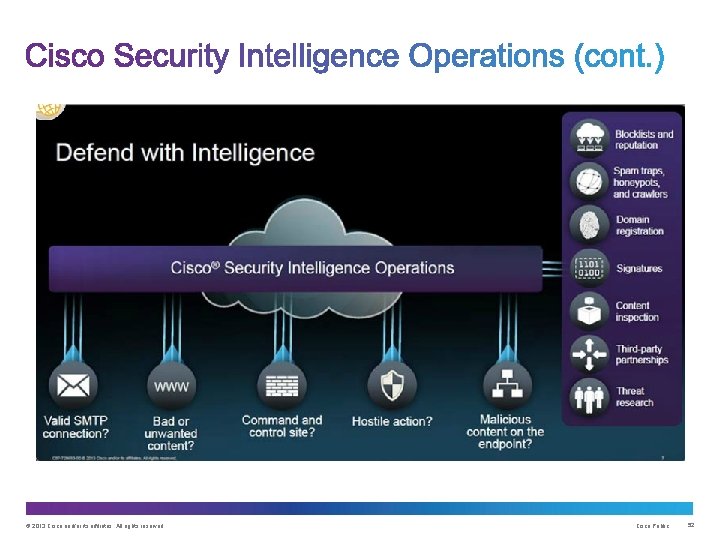
Common network security terms: • Threat • Vulnerability • Mitigation • Risk © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Security Intelligence Operations Cisco Public 6

© 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 7

Vectors of data loss: • Email/Webmail • Unencrypted Devices • Cloud Storage Devices • Removable Media • Hard Copy • Improper Access Control © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 8

© 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 9

© 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 10

© 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 11

© 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 12

Outside perimeter security: • On-premise security officers • Fences and gates • Continuous video surveillance • Security breach alarms Inside perimeter security: • Electronic motion detectors • Security traps • Continuous video surveillance • Biometric access and exit sensors © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 13

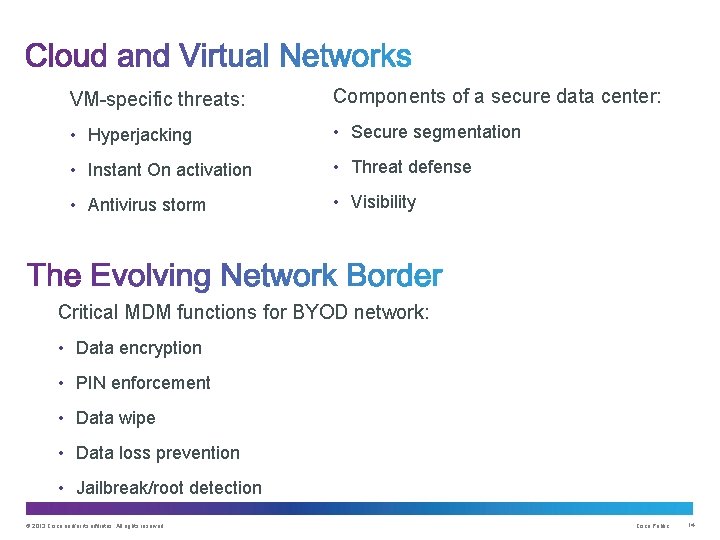
VM-specific threats: Components of a secure data center: • Hyperjacking • Secure segmentation • Instant On activation • Threat defense • Antivirus storm • Visibility Critical MDM functions for BYOD network: • Data encryption • PIN enforcement • Data wipe • Data loss prevention • Jailbreak/root detection © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 14

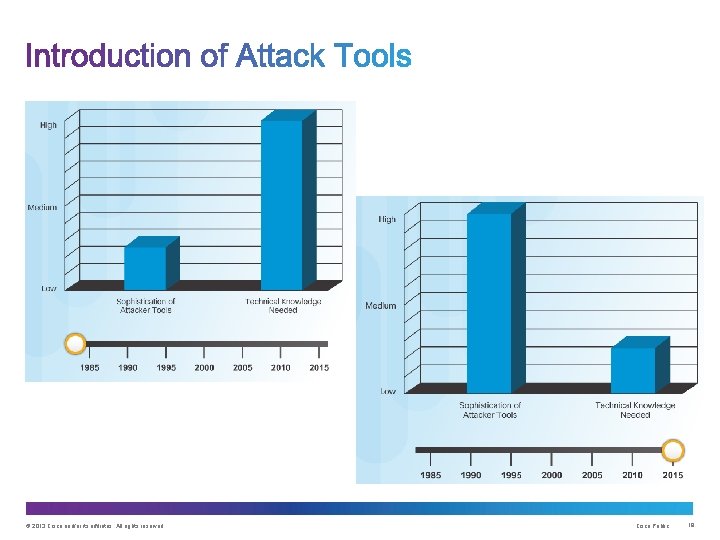
Upon completion of the section, you should be able to: • Describe the evolution of network security. • Describe the various types of attack tools used by hackers. • Describe malware. • Explain common network attacks. © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 15

© 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 16

Modern hacking titles: • Script Kiddies • Vulnerability Brokers • Hacktivists • Cyber Criminals • State-Sponsored Hackers © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 17

© 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 18

© 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 19

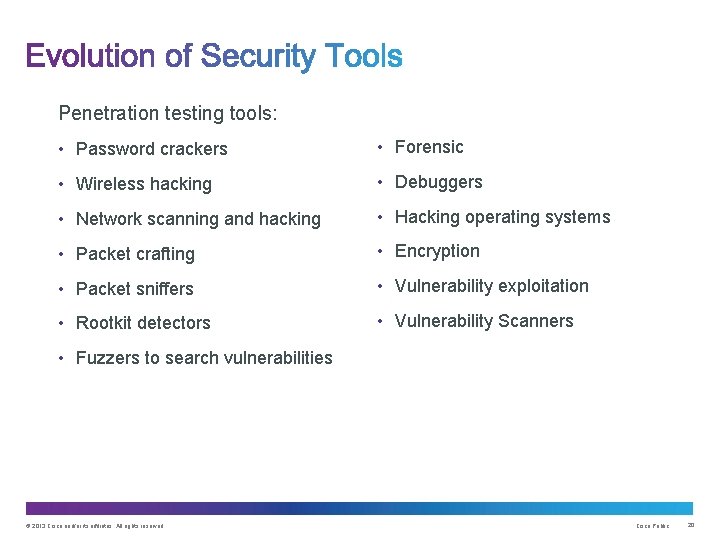
Penetration testing tools: • Password crackers • Forensic • Wireless hacking • Debuggers • Network scanning and hacking • Hacking operating systems • Packet crafting • Encryption • Packet sniffers • Vulnerability exploitation • Rootkit detectors • Vulnerability Scanners • Fuzzers to search vulnerabilities © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 20

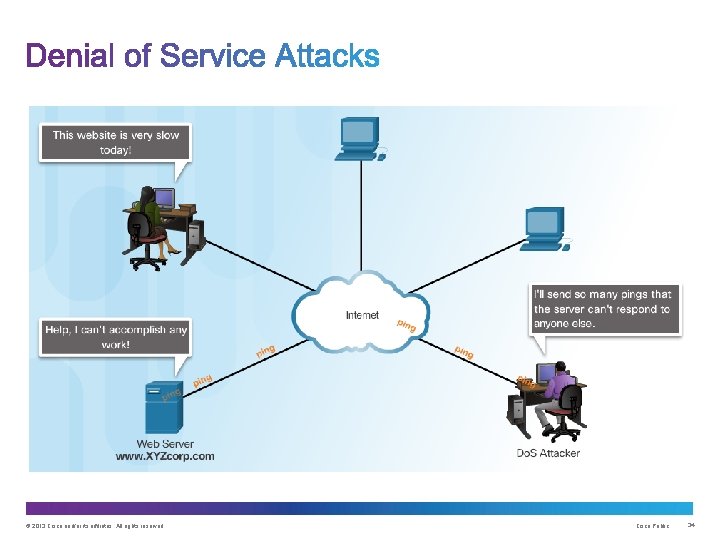
Network hacking attacks: • Eavesdropping • Data modification • IP address spoofing • Password-based • Denial-of-service • Man-in-the-middle • Compromised-key • Sniffer © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 21

© 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 22

© 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 23

© 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 24

Classifications: • Security software disabler • Remote-access • Data-sending • Destructive • Proxy • FTP • Do. S © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 25

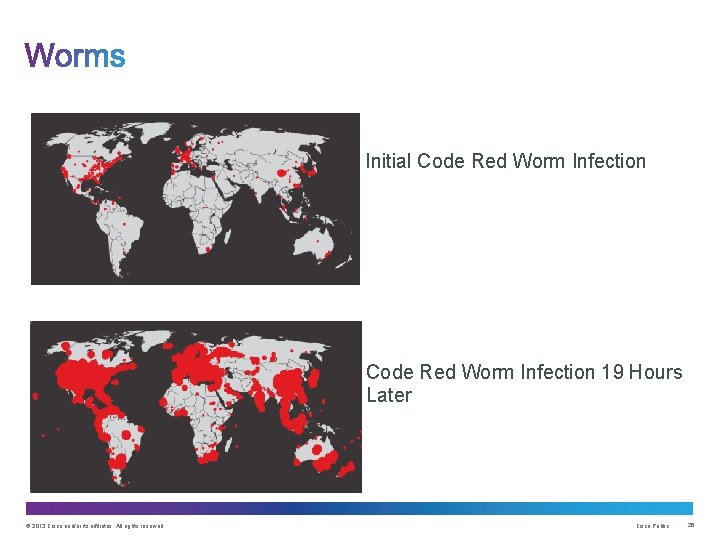
Initial Code Red Worm Infection 19 Hours Later © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 26

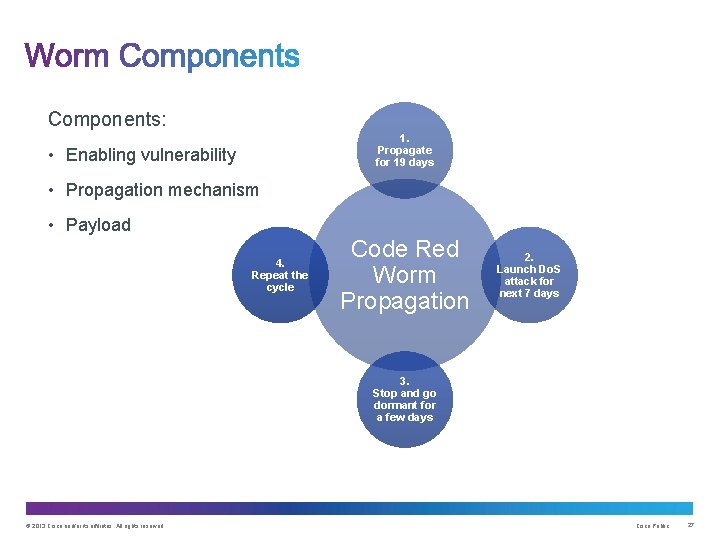
Components: 1. Propagate for 19 days • Enabling vulnerability • Propagation mechanism • Payload 4. Repeat the cycle Code Red Worm Propagation 2. Launch Do. S attack for next 7 days 3. Stop and go dormant for a few days © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 27

Ransomware Scareware Spyware Phishing Adware Rootkits © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 28

© 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 29

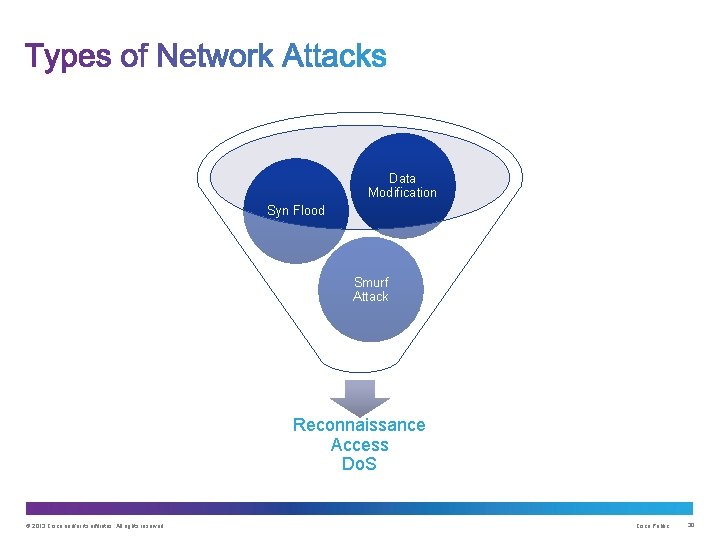
Data Modification Syn Flood Smurf Attack Reconnaissance Access Do. S © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 30

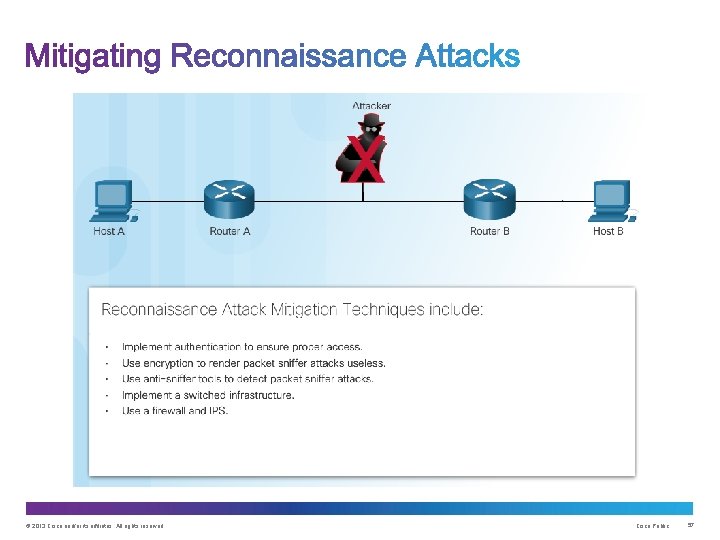
• Initial query of a target • Ping sweep of the target network • Port scan of active IP addresses • Vulnerability scanners • Exploitation tools © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 31

A few reasons why hackers use access attacks: • To retrieve data • To gain access • To escalate access privileges A few types of access attacks include: • Password • Trust exploitation • Port redirection • Man-in-the-middle • Buffer overflow • IP, MAC, DHCP spoofing © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 32

• Pretexting • Phishing • Spearphishing • Spam • Tailgating • Something for Something • Baiting © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 33

© 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 34

1. Hacker builds a network of infected machines • A network of infected hosts is called a botnet. • The compromised computers are called zombies. • Zombies are controlled by handler systems. 2. Zombie computers continue to scan and infect more targets 3. Hacker instructs handler system to make the botnet of zombies carry out the DDo. S attack © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 35

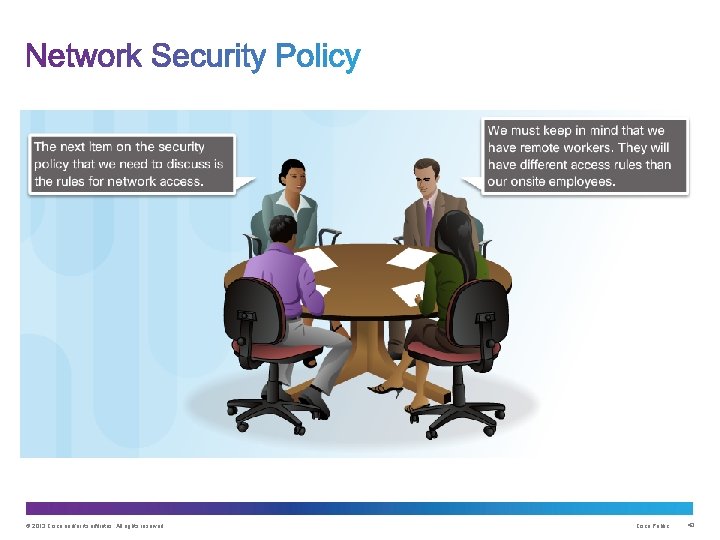
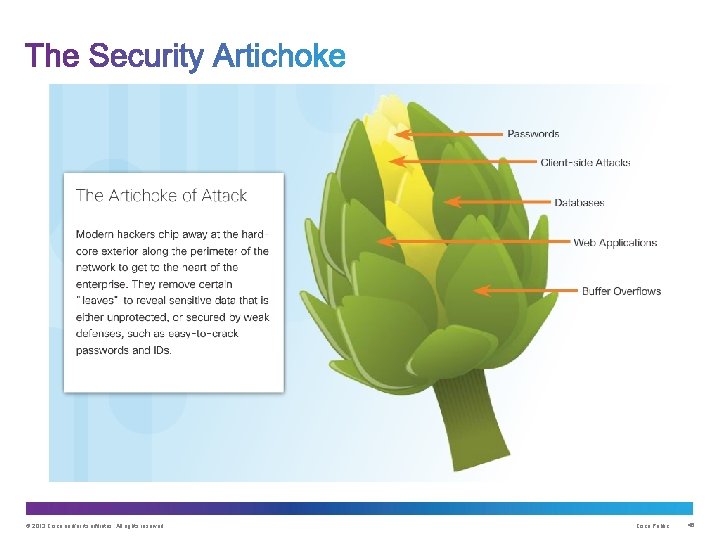
Upon completion of this section, you should be able to: : • Describe methods and resources to protect the networks. • Describe a collection of domains for network security. • Explain the purpose of the Cisco Secure. X Architecture. • Describe the techniques used to mitigate common network attacks. • Explain how to secure three functional areas of Cisco routers and switches. © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 36

© 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 37

© 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 38

© 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 39

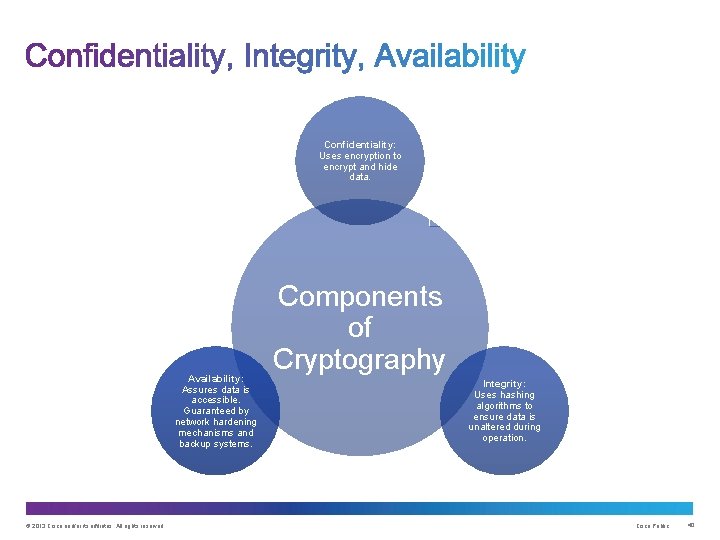
Confidentiality: Uses encryption to encrypt and hide data. Availability: Assures data is accessible. Guaranteed by network hardening mechanisms and backup systems. © 2013 Cisco and/or its affiliates. All rights reserved. Components of Cryptography Integrity: Uses hashing algorithms to ensure data is unaltered during operation. Cisco Public 40

© 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 41

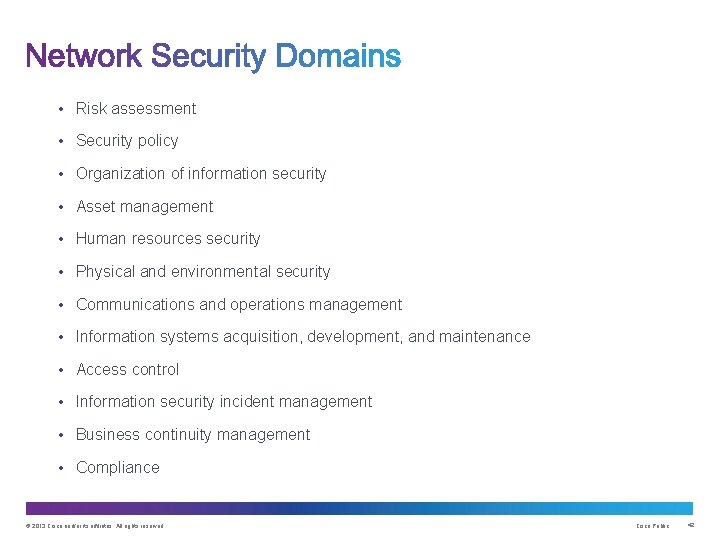
• Risk assessment • Security policy • Organization of information security • Asset management • Human resources security • Physical and environmental security • Communications and operations management • Information systems acquisition, development, and maintenance • Access control • Information security incident management • Business continuity management • Compliance © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 42

© 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 43

© 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 44

© 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 45

© 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 46

© 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 47

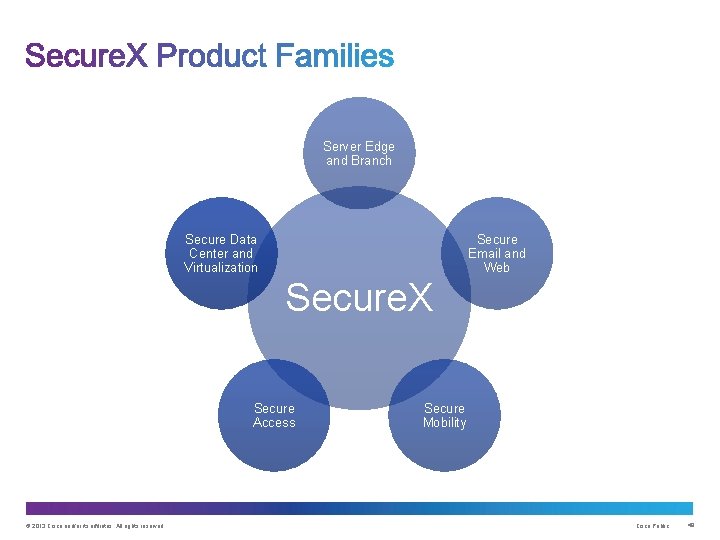
Server Edge and Branch Secure Data Center and Virtualization Secure Email and Web Secure. X Secure Access © 2013 Cisco and/or its affiliates. All rights reserved. Secure Mobility Cisco Public 48

Cisco Secure. X Architecture: • Scanning engines • Delivery mechanisms • Security intelligence operations (SIO) • Policy management consoles • Next-generation endpoint © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 49

Defines security policies based on five parameters: • Type of device being used for access • Person’s identity • Application in use • Location • Time of access © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 50

© 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 51

© 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 52

© 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 53

Best practices: • Develop a written security policy. • Educate employees about the risks of social engineering, and develop strategies to validate identities over the phone, via email, or in person. • Control physical access to systems. • Use strong passwords and change them often. • Encrypt and password-protect sensitive data. • Implement security hardware and software. • Perform backups and test the backed up files on a regular basis. • Shut down unnecessary services and ports. • Keep patches up-to-date by installing them weekly or daily to prevent buffer overflow and privilege escalation attacks. • Perform security audits to test the network. © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 54

© 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 55

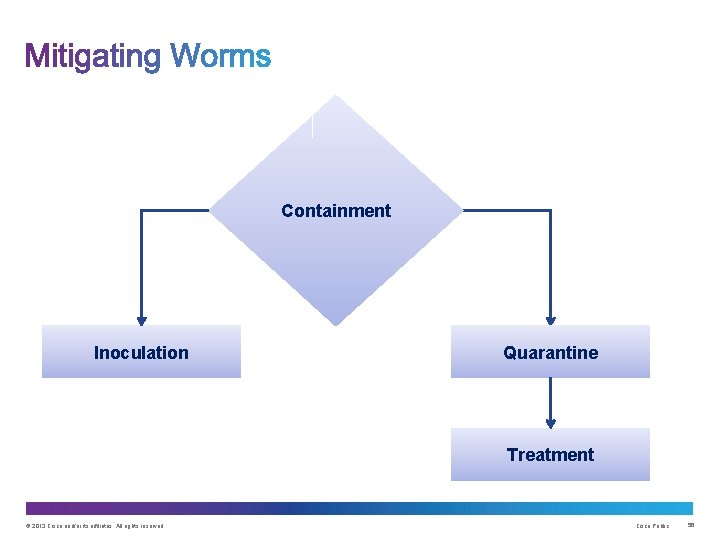
Containment Inoculation Quarantine Treatment © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 56

© 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 57

© 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 58

© 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 59

© 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 60

© 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 61

© 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 62

© 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 63

© 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 64

Chapter Objectives: • Explain network security. • Describe various types of threats and attacks. • Explain tools and procedures to mitigate the effects of malware and common network attacks. © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 65

Thank you.

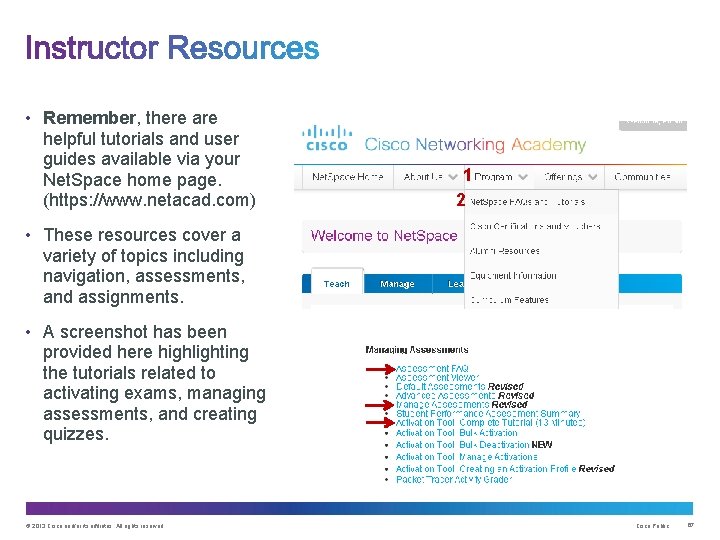
• Remember, there are helpful tutorials and user guides available via your Net. Space home page. (https: //www. netacad. com) 1 2 • These resources cover a variety of topics including navigation, assessments, and assignments. • A screenshot has been provided here highlighting the tutorials related to activating exams, managing assessments, and creating quizzes. © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 67