Module 3 Identifying Threats to Network Security Overview





- Slides: 15

Module 3: Identifying Threats to Network Security

Overview Introduction to Security Threats Predicting Threats to Security

Lesson 1: Introduction to Security Threats Why Network Attacks Occur Who Attacks Networks? Typical Anatomy of an Attack Common Types of Network Attacks Common Types of Network Vulnerabilities Practice: Exploiting Vulnerabilities in an Insecurely Configured Network Host

Why Network Attacks Occur The reasons that network attacks occur include: Revenge Espionage Publicity Personal satisfaction Terrorism

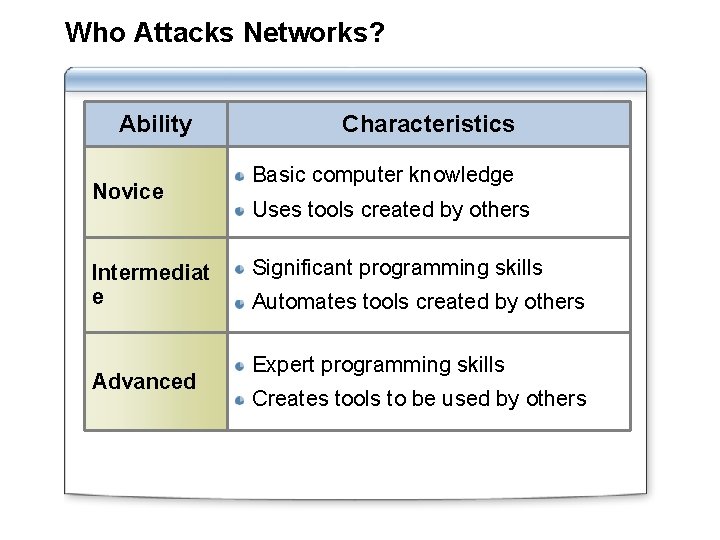
Who Attacks Networks? Ability Novice Intermediat e Advanced Characteristics Basic computer knowledge Uses tools created by others Significant programming skills Automates tools created by others Expert programming skills Creates tools to be used by others

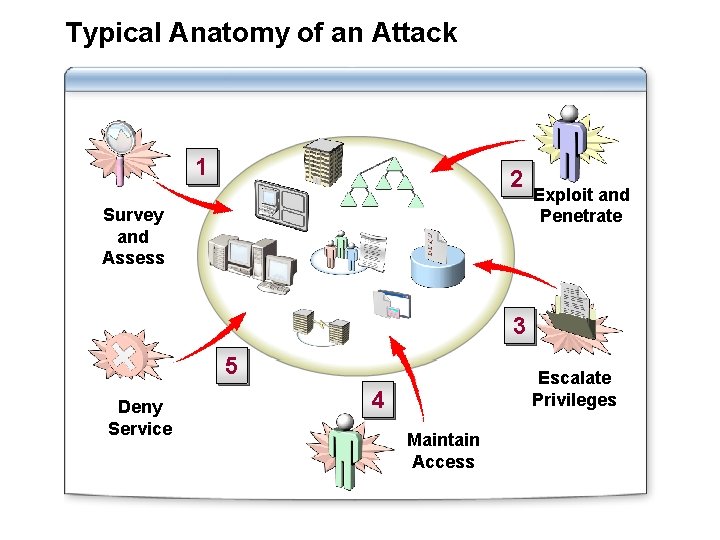
Typical Anatomy of an Attack 1 2 Survey and Assess Exploit and Penetrate 3 5 Deny Service Escalate Privileges 4 Maintain Access

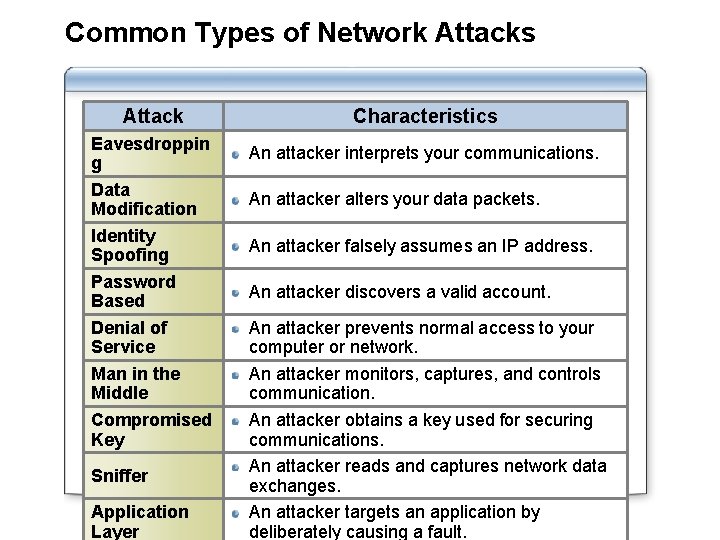
Common Types of Network Attacks Attack Eavesdroppin g Data Modification Identity Spoofing Password Based Denial of Service Man in the Middle Compromised Key Sniffer Application Layer Characteristics An attacker interprets your communications. An attacker alters your data packets. An attacker falsely assumes an IP address. An attacker discovers a valid account. An attacker prevents normal access to your computer or network. An attacker monitors, captures, and controls communication. An attacker obtains a key used for securing communications. An attacker reads and captures network data exchanges. An attacker targets an application by deliberately causing a fault.

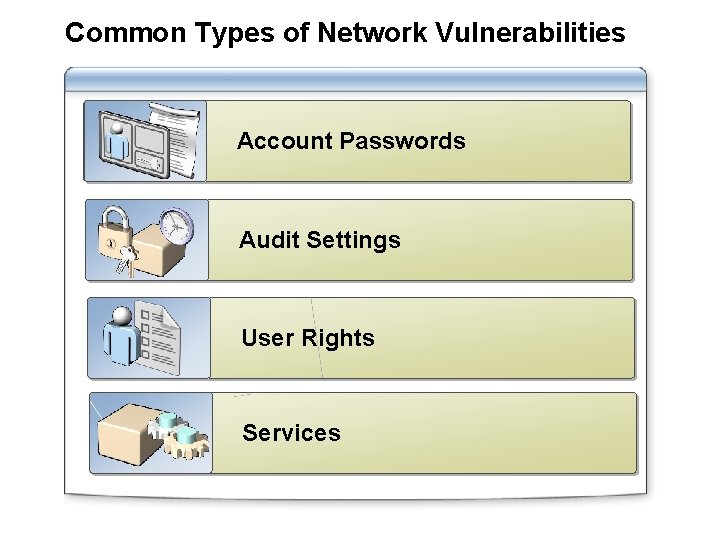
Common Types of Network Vulnerabilities Account Passwords Audit Settings User Rights Services

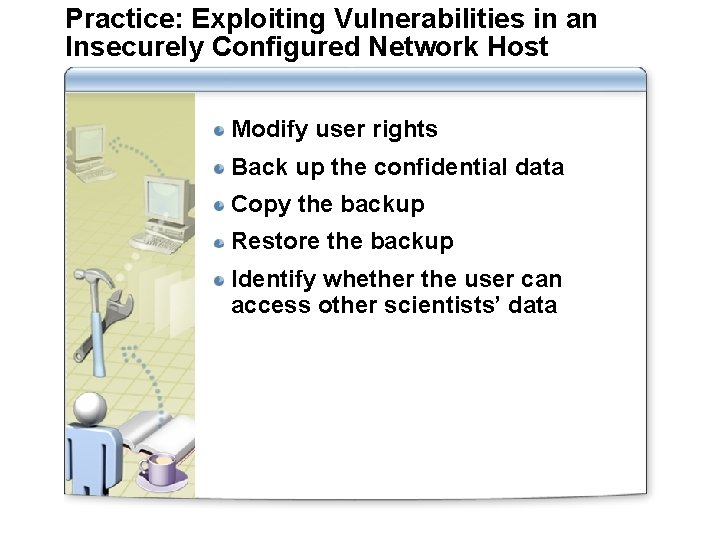
Practice: Exploiting Vulnerabilities in an Insecurely Configured Network Host Modify user rights Back up the confidential data Copy the backup Restore the backup Identify whether the user can access other scientists’ data

Lesson 2: Predicting Threats to Security What Is a Threat Model? Predicting Network Threats by Using a Threat Model Countering Network Threats by Using a Threat Model Guidelines for Modeling Threats

What Is a Threat Model? Spoofing Attempting to gain access to a system by using a false identity Tampering Unauthorized modification of data Repudiatio n Ability of users (legitimate or otherwise) to deny that they performed specific actions or transactions Informatio n disclosure Denial of service Elevation of privilege Unwanted exposure of private data The process of making a system or application unavailable A user with limited privileges assumes the identity of a privileged user

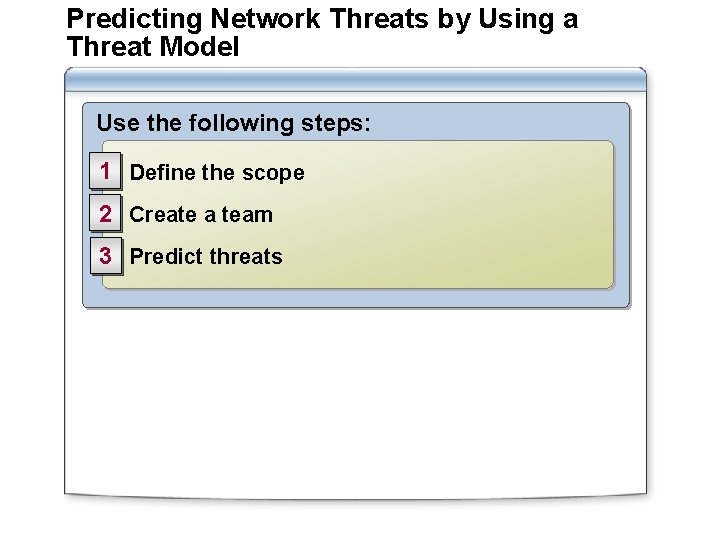
Predicting Network Threats by Using a Threat Model Use the following steps: 1 Define the scope 2 Create a team 3 Predict threats

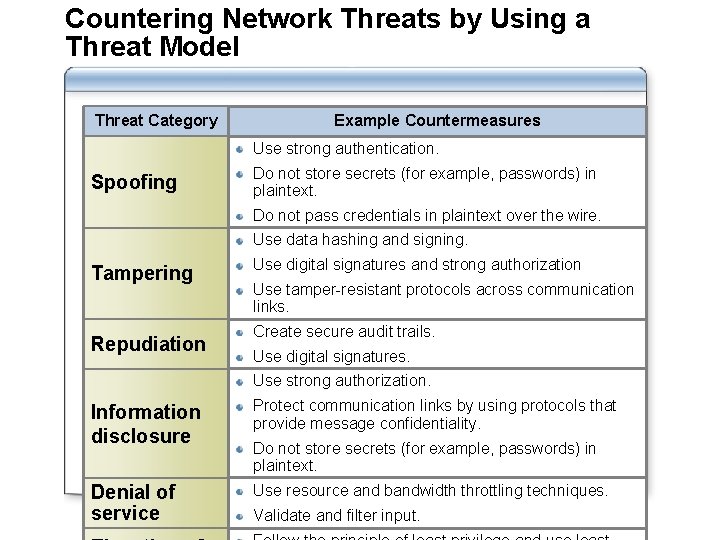
Countering Network Threats by Using a Threat Model Threat Category Example Countermeasures Use strong authentication. Spoofing Do not store secrets (for example, passwords) in plaintext. Do not pass credentials in plaintext over the wire. Use data hashing and signing. Tampering Repudiation Use digital signatures and strong authorization Use tamper-resistant protocols across communication links. Create secure audit trails. Use digital signatures. Use strong authorization. Information disclosure Protect communication links by using protocols that provide message confidentiality. Denial of service Use resource and bandwidth throttling techniques. Do not store secrets (for example, passwords) in plaintext. Validate and filter input.

Guidelines for Modeling Threats Use the following guidelines when modeling threats to your network: ü Encourage creative thinking among team ü ü members Ensure that you have all of the information Manage discussions about the validity of a ü threat ü Include specialized network penetration testers Use caution regarding conflicts of interest

Lab: Identifying Threats to Network Security Exercise 1 Identifying and Categorizing Security Threats by Using a Threat Model Exercise 2 Documenting Security Threats