System and Network Threats System and Network Threats





- Slides: 8

System and Network Threats

System and Network Threats � � Some systems “open” rather than secure by default � Reduce attack surface � But harder to use, more knowledge needed to administer Network threats harder to detect, prevent � Protection systems weaker � More difficult to have a shared secret on which to base access � No physical limits once system attached to internet � Or on network with system attached to internet � Even determining location of connecting system difficult � IP address is only knowledge

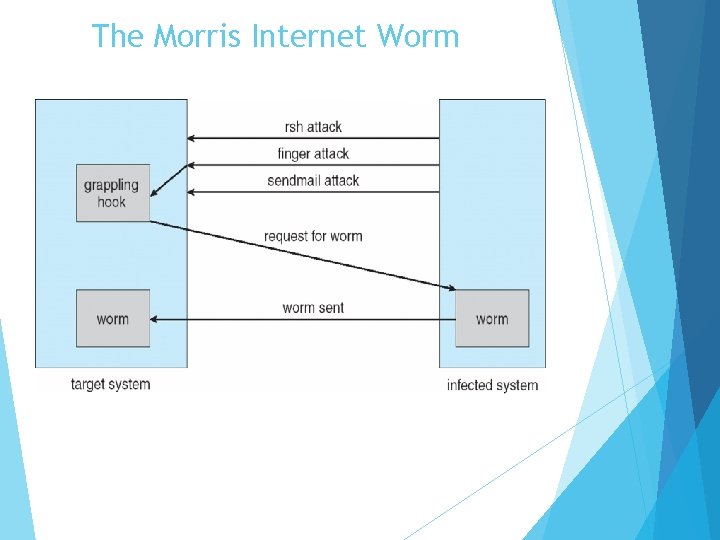
System and Network Threats (Cont. ) � Worms – use spawn mechanism; standalone program � Internet worm � Exploited UNIX networking features (remote access) and bugs in finger and sendmail programs � Exploited trust-relationship mechanism used by rsh to access friendly systems without use of password � Grappling hook program uploaded main worm program � 99 lines of C code � Hooked system then uploaded main code, tried to attack connected systems � Also tried to break into other users accounts on local system via password guessing � If target system already infected, abort, except for every 7 th time

The Morris Internet Worm

System and Network Threats (Cont. ) � Port scanning � Automated attempt to connect to a range of ports on one or a range of IP addresses � Detection of answering service protocol � Detection of OS and version running on system � nmap scans all ports in a given IP range for a response � nessus has a database of protocols and bugs (and exploits) to apply against a system � Frequently launched from zombie systems � To decrease trace-ability

System and Network Threats (Cont. ) � Denial of Service � Overload the targeted computer preventing it from doing any useful work � Distributed denial-of-service (DDOS) come from multiple sites at once � Consider the start of the IP-connection handshake (SYN) � How many started-connections can the OS handle? � Consider traffic to a web site � How can you tell the difference between being a target and being really popular? � Accidental – CS students writing bad fork() code � Purposeful – extortion, punishment

Sobig. F Worm � More modern example � Disguised as a photo uploaded to adult newsgroup via account created with stolen credit card � Targeted Windows systems � Had own SMTP engine to mail itself as attachment to everyone in infect system’s address book � Disguised with innocuous subject lines, looking like it came from someone known � Attachment was executable program that created WINPPR 23. EXE in default Windows system directory Plus the Windows Registry [HKCUSOFTWAREMicrosoftWindowsCurrent. VersionRun] "Tray. X" = %windir%winppr 32. exe /sinc [HKLMSOFTWAREMicrosoftWindowsCurrent. VersionRun] "Tray. X" = %windir%winppr 32. exe /sinc

References � “Operating System Concepts, " by Abraham Silberschatz, et al, 9 th Edition, 2012, John Wiley & Sons Inc. � Operating Systems: A Spiral Approach 1 st Edition by Ramez Elmasri , A Carrick , David Levine