Internet security threats Countermeasures Internet security threats Mapping







- Slides: 16

Internet security threats Countermeasures

Internet security threats Mapping: – before attacking: “case the joint” – find out what services are implemented on network – Use ping to determine what hosts have addresses on network – Port-scanning: try to establish TCP connection to each port in sequence (see what happens) – nmap (http: //www. insecure. org/nmap/) mapper: “network exploration and security auditing” Countermeasures?

Internet security threats Mapping: countermeasures – record traffic entering network – look for suspicious activity (IP addresses, pots being scanned sequentially)

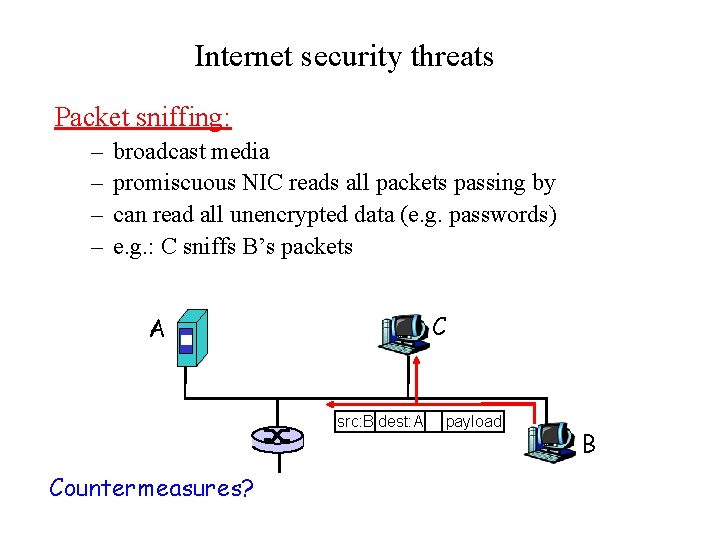
Internet security threats Packet sniffing: – – broadcast media promiscuous NIC reads all packets passing by can read all unencrypted data (e. g. passwords) e. g. : C sniffs B’s packets C A src: B dest: A Countermeasures? payload B

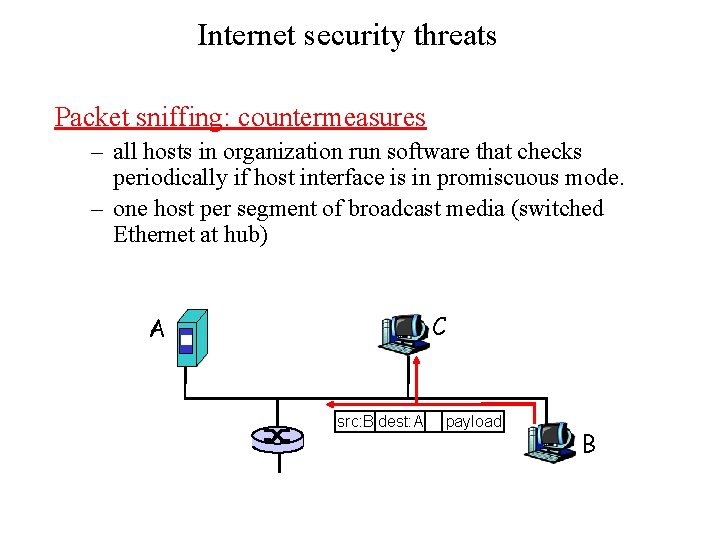
Internet security threats Packet sniffing: countermeasures – all hosts in organization run software that checks periodically if host interface is in promiscuous mode. – one host per segment of broadcast media (switched Ethernet at hub) C A src: B dest: A payload B

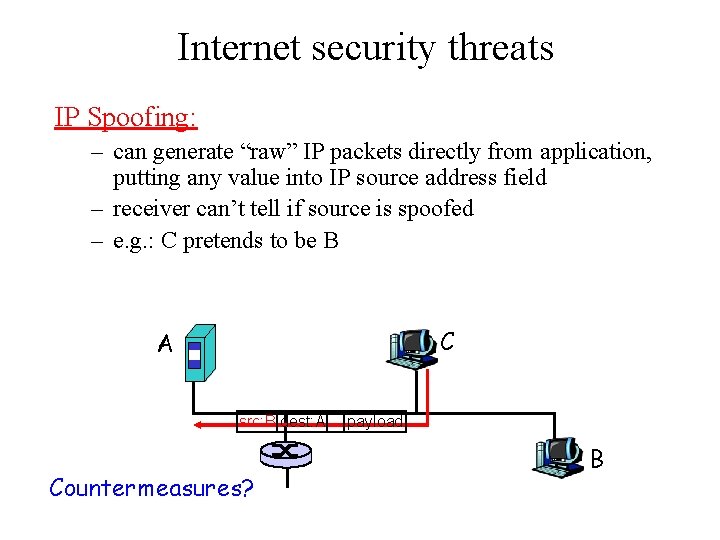
Internet security threats IP Spoofing: – can generate “raw” IP packets directly from application, putting any value into IP source address field – receiver can’t tell if source is spoofed – e. g. : C pretends to be B C A src: B dest: A Countermeasures? payload B

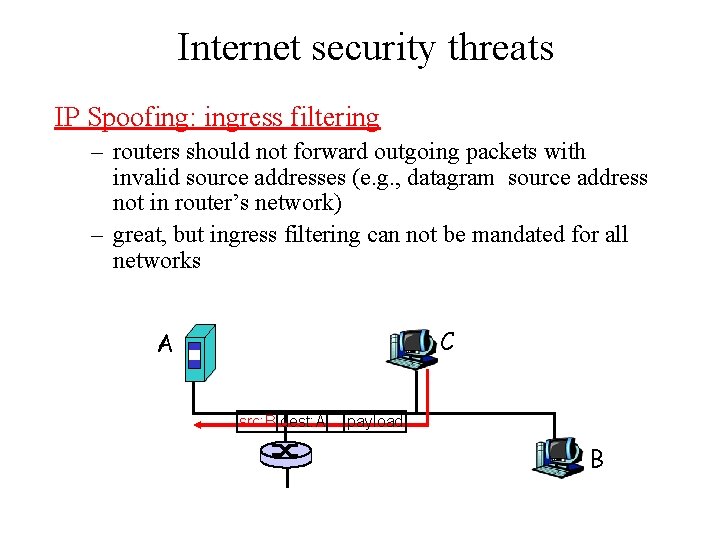
Internet security threats IP Spoofing: ingress filtering – routers should not forward outgoing packets with invalid source addresses (e. g. , datagram source address not in router’s network) – great, but ingress filtering can not be mandated for all networks C A src: B dest: A payload B

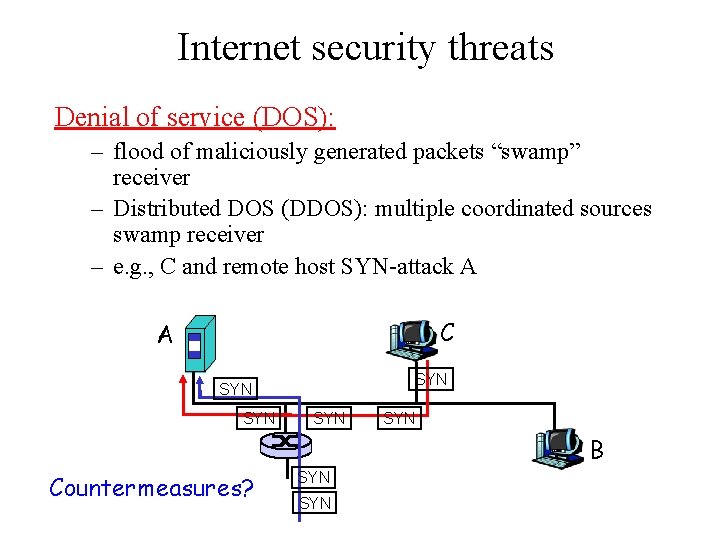
Internet security threats Denial of service (DOS): – flood of maliciously generated packets “swamp” receiver – Distributed DOS (DDOS): multiple coordinated sources swamp receiver – e. g. , C and remote host SYN-attack A C A SYN SYN SYN B Countermeasures? SYN

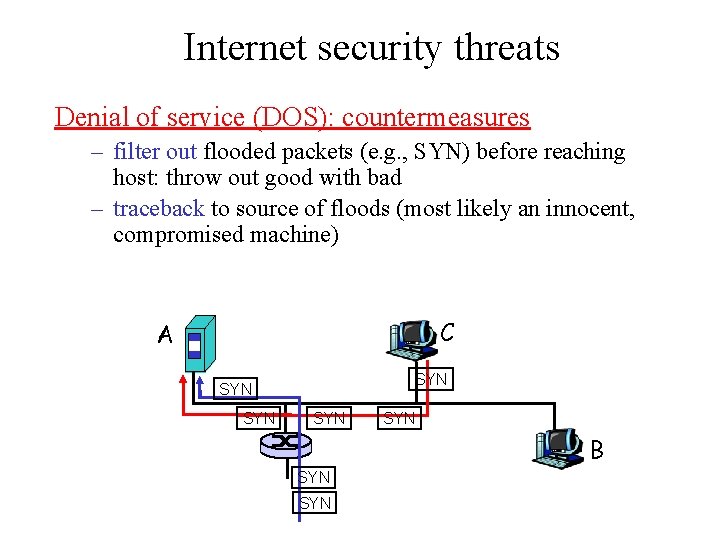
Internet security threats Denial of service (DOS): countermeasures – filter out flooded packets (e. g. , SYN) before reaching host: throw out good with bad – traceback to source of floods (most likely an innocent, compromised machine) C A SYN SYN SYN B SYN

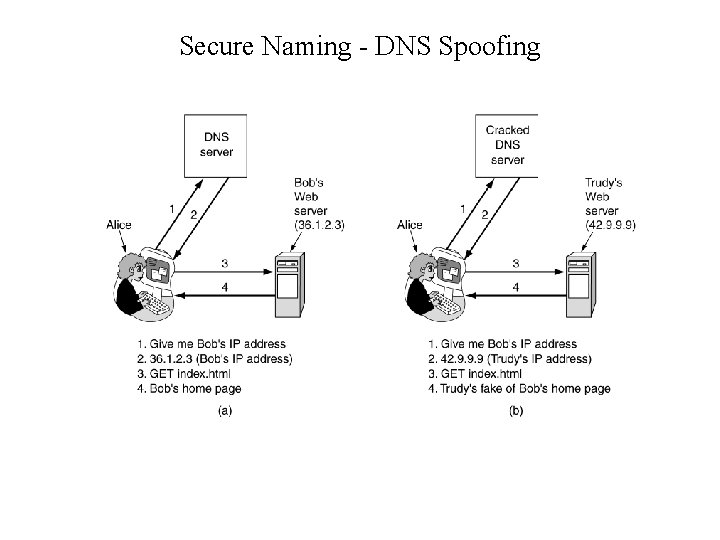
DNS Spoofing • Tricking a DNS server into installing a false IP address is called DNS spoofing • A cache that holds an intentionally false IP address is called a poisoned cache

Secure Naming - DNS Spoofing • (a) Normal situation. (b) An attack based on breaking into DNS and modifying Bob's record.

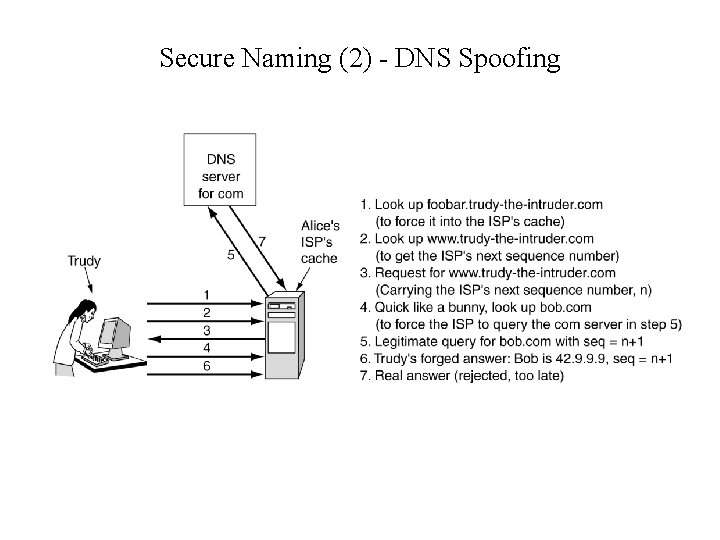
Secure Naming (2) - DNS Spoofing • How Trudy spoofs Alice's ISP.

Secure DNS • Based on public key cryptography, • Every DNS zone has a public/private key pair • All information sent by a DNS server is signed with the originating zone’s private key, so the receiver can verify its authenticity • DNSsec offers three fundamental services: - Proof of where data originated, - Public Key Distribution - Transaction and request authentication Not yet implemented everywhere

Secure DNS • DNSsec records are grouped into RRSets (Resource Record Sets), with all the records having the same name, class and type and which may contain multiple A records • New records types - KEY (public key of the zone, user, host, or other principal, the algorithm used for signing, the protocol used for transmission etc), - SIG (signed hash using algorithm specified in the KEY),

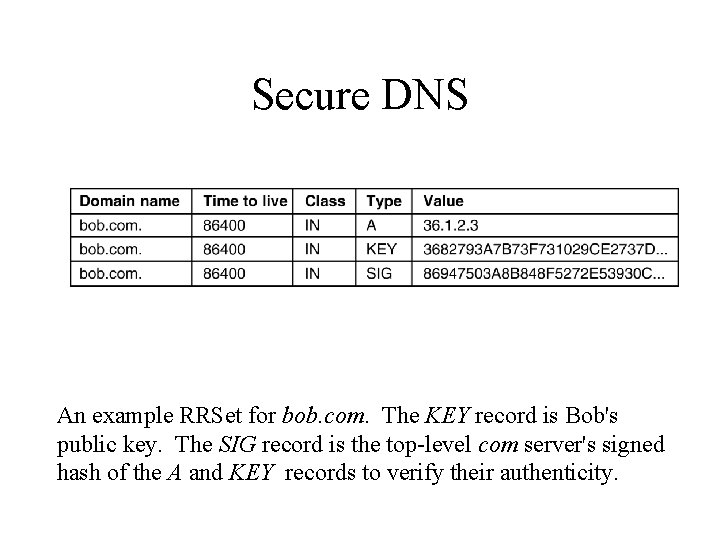
Secure DNS An example RRSet for bob. com. The KEY record is Bob's public key. The SIG record is the top-level com server's signed hash of the A and KEY records to verify their authenticity.

Secure DNS • Alice asks DNS for the RRSet of bob. com – she gets among others Bob’s public key; • Then she asks Bob’s DNS server for the IP address of the Bob’s web page; She can verify it because it is signed with Bob’s private key; If Trudy injected a false RRSet into any cache, its lack of authenticity will easily be detected; DNS may (optionally) use cryptography to bind a response to a specific query to prevent spoofing.