Countermeasures for Recent Attack Trends II Countermeasures 2016







- Slides: 14

Countermeasures for Recent Attack Trends II. Countermeasures 2016. 9. 22 Copyright © LG CNS It is strictly prohibited to copy, distribute, or use this document, in part or in whole, without the prior consent of LG CNS

I. Recent Attack Trends 1. Changing Trends of Cyber Attack How have cyber attacks been evolved in recent? ① Increase of crime-type and intelligent personalized attack : Ransomware 1), APT 2) ② Easier hacking due to the black market activation ③ Attacks in targeting certain individuals, companies, and the national ④ Emergence of the new type attacks : Cloud, Io. T Devices ⑤ Physical damage caused by cyber attacks on life, equipment, etc. 1) Ransomware : Ransom + Software, attacks requiring money for decrypting after encrypting information in files 2) APT(Advanced Persistent Threat) : Sophisticated forms of cyber-attacks combining various techniques utilizing the collected information for a specific long-term for certain targets 1 / 12

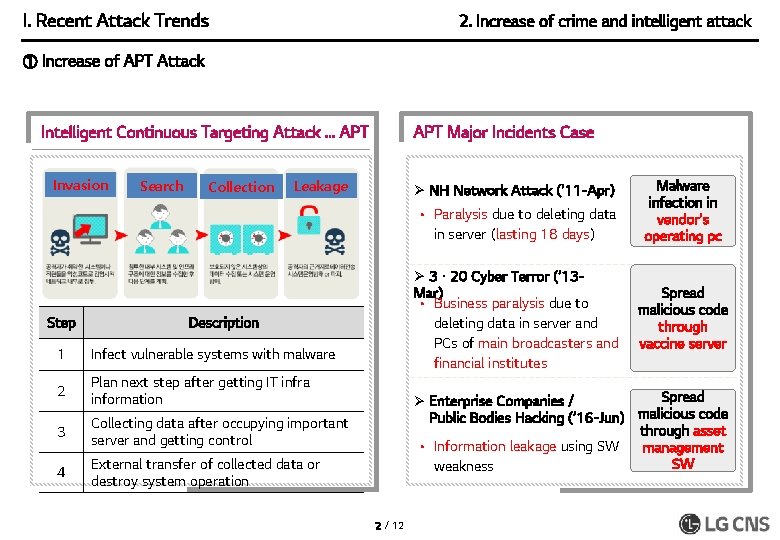
I. Recent Attack Trends 2. Increase of crime and intelligent attack ① Increase of APT Attack Intelligent Continuous Targeting Attack … APT Invasion Search Collection APT Major Incidents Case Leakage Ø NH Network Attack (’ 11 -Apr) • Paralysis due to deleting data in server (lasting 18 days) Step Ø 3ㆍ20 Cyber Terror (’ 13 Mar) • Business paralysis due to deleting data in server and PCs of main broadcasters and financial institutes Description 1 Infect vulnerable systems with malware 2 Plan next step after getting IT infra information 3 Collecting data after occupying important server and getting control 4 External transfer of collected data or destroy system operation Malware infection in vendor’s operating pc Spread malicious code through vaccine server Spread Ø Enterprise Companies / Public Bodies Hacking (’ 16 -Jun) malicious code through asset • Information leakage using SW management SW weakness 2 / 12

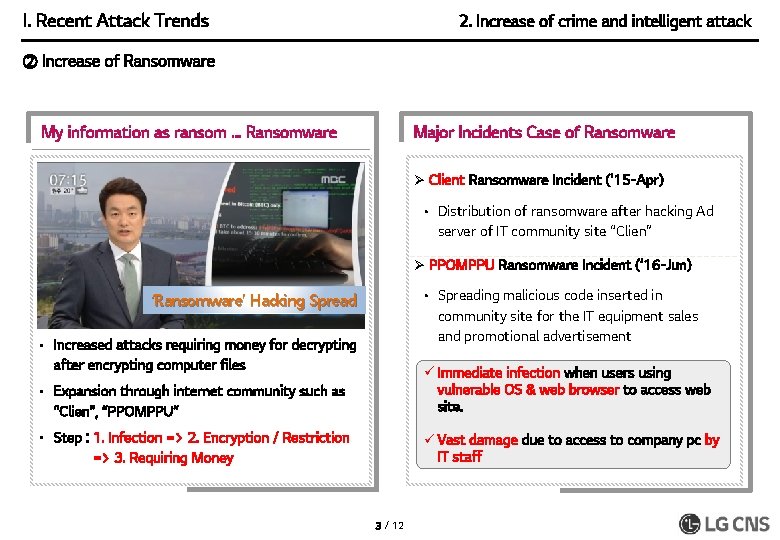
I. Recent Attack Trends 2. Increase of crime and intelligent attack ② Increase of Ransomware My information as ransom … Ransomware Major Incidents Case of Ransomware Ø Client Ransomware Incident (’ 15 -Apr) • Distribution of ransomware after hacking Ad server of IT community site “Clien” Ø PPOMPPU Ransomware Incident (’ 16 -Jun) • Spreading malicious code inserted in community site for the IT equipment sales and promotional advertisement ‘Ransomware’ Hacking Spread • Increased attacks requiring money for decrypting after encrypting computer files • Expansion through internet community such as “Clien”, “PPOMPPU” ü Immediate infection when users using vulnerable OS & web browser to access web site. • Step : 1. Infection => 2. Encryption / Restriction => 3. Requiring Money ü Vast damage due to access to company pc by IT staff 3 / 12

I. Recent Attack Trends 3. Black market activation Anyone can hack easily by using various kinds of hacking tools and hacking knowledge sharing over the Internet. Hacking Ad on Web Board DDo. S Attack Tool Sales Site 4 / 12

I. Recent Attack Trends 4. Attacks in targeting certain individuals, companies, and the national are increasing. Major Case in Korea (’ 13 6. 25 Cyber Terror) 1 Increase of Hacktivism = Hacker + Activism Falsification of The Blue House Ø Using vulnerability of file upload in home page Ø Estimated to be preparing a long period of time 2 Major Government Site Shut Down • Invading Indonesian government network and shutting down servers by Portugal hackers to aim independence of East Timor Ø Using the way to attack through malicious script installed in web site 3 • After rejecting the request for closing Ashley Madison which encourages extra marital affairs, hackers have posted on the internet the personal data of some 32 million. Data Spill (with home page falsification) Ø Saenuri Party Members : about 2. 5 million Ø Military Personnel : about 0. 3 million 5 / 12

I. Recent Attack Trends 5. New type attacks Io. T device is emerging as a target of cyber attacks, and the attack is getting diversified as Io. T devices are increasing. Device, Fetch / Update Difficulty Used by Infection Route for Malicious Code • Finding Iron Hacking Tool – ’ 13 -Oct. • Kettle Hacking Tool after Iron – ’ 13 -Nov. Security Defenseless Free Wi-Fi • ‘Vulnerability' Wi-FI, Defenseless against Hacking – ’ 15 -March • Malicious Code Infection during charging electronic cigarette – ’ 14 -Nov. • Security comprehensive countermeasures KISA Manufacturer ISP User providing security weakness Fetch / Update 6 / 12

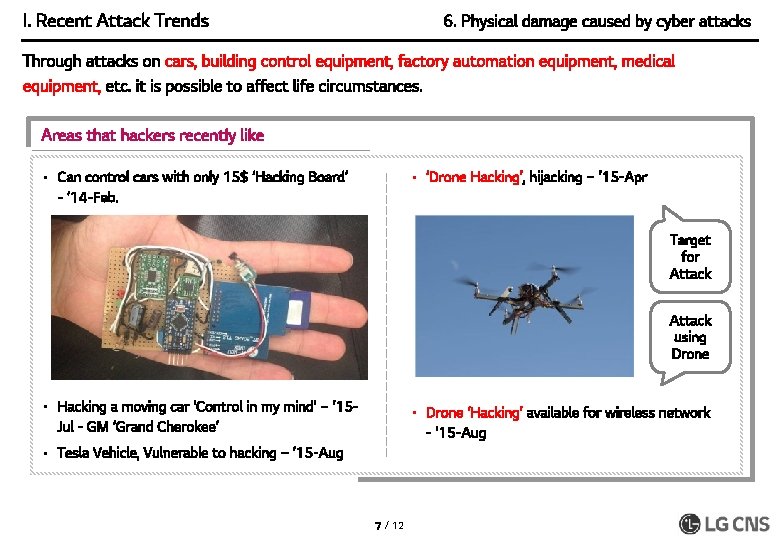
I. Recent Attack Trends 6. Physical damage caused by cyber attacks Through attacks on cars, building control equipment, factory automation equipment, medical equipment, etc. it is possible to affect life circumstances. Areas that hackers recently like • Can control cars with only 15$ ‘Hacking Board’ - ’ 14 -Feb. • ‘Drone Hacking’, hijacking – ’ 15 -Apr Target for Attack using Drone • Hacking a moving car ‘Control in my mind’ – ’ 15 Jul - GM ‘Grand Cherokee’ • Drone ‘Hacking’ available for wireless network - ’ 15 -Aug • Tesla Vehicle, Vulnerable to hacking – ’ 15 -Aug 7 / 12

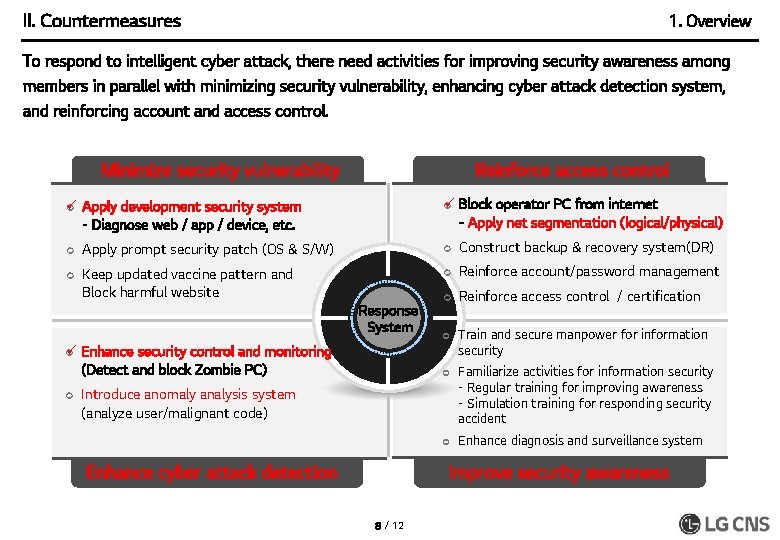
II. Countermeasures 1. Overview To respond to intelligent cyber attack, there need activities for improving security awareness among members in parallel with minimizing security vulnerability, enhancing cyber attack detection system, and reinforcing account and access control. Minimize security vulnerability Reinforce access control ü ¢ Apply development security system - Diagnose web / app / device, etc. ü ¢ Block operator PC from internet - Apply net segmentation (logical/physical) ¢ Apply prompt security patch (OS & S/W) ¢ Construct backup & recovery system(DR) ¢ Keep updated vaccine pattern and Block harmful website ¢ Reinforce account/password management ¢ Reinforce access control / certification ¢ Train and secure manpower for information security ¢ Familiarize activities for information security - Regular training for improving awareness - Simulation training for responding security accident ¢ Enhance diagnosis and surveillance system Response System ¢ ü ¢ Enhance security control and monitoring (Detect and block Zombie PC) Introduce anomaly analysis system (analyze user/malignant code) Improve security awareness Enhance cyber attack detection 8 / 12

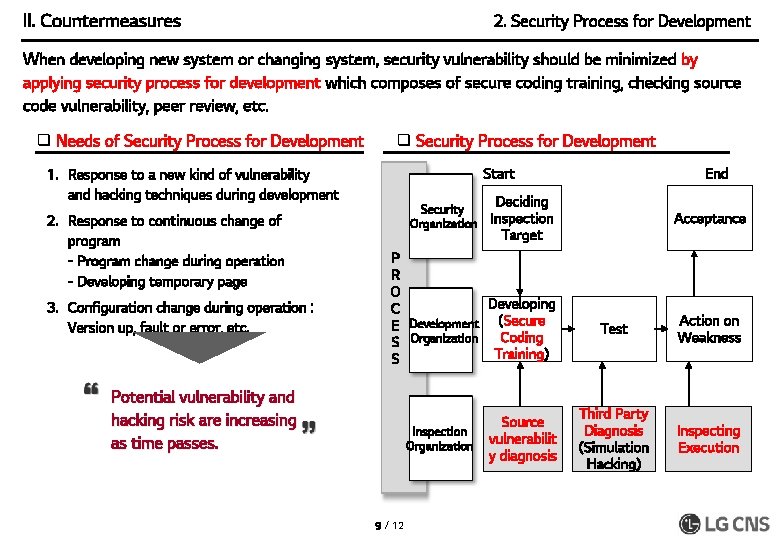
II. Countermeasures 2. Security Process for Development When developing new system or changing system, security vulnerability should be minimized by applying security process for development which composes of secure coding training, checking source code vulnerability, peer review, etc. q Needs of Security Process for Development q Security Process for Development Start 1. Response to a new kind of vulnerability and hacking techniques during development 2. Response to continuous change of program - Program change during operation - Developing temporary page 3. Configuration change during operation : Version up, fault or error, etc. Security Organization Deciding Inspection Target P R O Developing C E Development (Secure Coding S Organization Training) S Potential vulnerability and hacking risk are increasing as time passes. Inspection Organization 9 / 12 End Source vulnerabilit y diagnosis Acceptance Test Action on Weakness Third Party Diagnosis (Simulation Hacking) Inspecting Execution

II. Countermeasures 3. Network segmentation is becoming increasingly necessary as the threats of data theft and attacks on critical systems such as APT continue to grow. Either physical or logical segmentation with the technology of virtualization can be adoptable for network segmentation. q Needs üTo prevent data theft q Methods ü Physical segmentation • Prevent data theft and attacks through internet by segmentation between trusted and untrusted network area. üTo prevent APT attacks • Separate network physically between trusted and un trusted network area. • Method : 2 computers (each connected separated network) per an operator w/ a KVM switch. ü Logical segmentation • Separate network logically by virtualization • Minimize spreading malicious code by network segmentation. Attacks such as APT through internet cannot affect to the trusted network. • Methods Type Description Remark • Multiple OS PC Implement • Apply solution virtualization on each for tion PC virtualization Server Generate computers • Normal PC virtualiza from a server with • Zero Client tion VDI technology ü To support Compliance • Comply regulations such as “Korea Information Communications Network Act”. PC which can access individual data have to have a isolated network from the internet by the Act. 10 / 12

II. Countermeasures 4. Enhanced Security Detection System for APT Attack It is possible to rapidly detect new malware infection PC, which is the main cause for recent cyber attack, by deploying detection and response system for unknown malware. q APT Detection System Malicious Code Blocking Malicious Code Internal N/W Area Internet Detecting Zombie PC N/W Forensic 1 Monitoring Malware Infection PC 2 • Monitoring and Analyzing Malicious Code • Detecting Zero-Day Malicious Code by analyzing behavior through virtualization technology • Tracking Infection PC • Detailed analysis of invasion accident signs and abnormal traffic Network Forensic 11 / 12 Infection PCs with Malicious Code 3 Malicious Code Blocking • Blocking flow of malicious code and controlling web traffic • Blocking flow from messenger, P 2 P, etc.

Better if there were a cure-all. . . ¢ Prevention : Exercise, Eating Habits, ¢ Prevention : Train/Promotion, Continuous Fetch/Update … Stop smoking/drinking … ¢ Detection : Checkup ¢ Detection : Security Control, Monitoring … ¢ Action : Medicine, Surgery, Injection. . . ¢ Action : Access Control, Account Management … 12 / 12

Q&A hoh@lgcns. com - / 11 -