Network Security Design and Implementation Unit 9 Chapter























- Slides: 36

Network Security, Design and Implementation Unit 9, Chapter 17 & 19

Objectives Describe the various threats to network security and the technologies that are used to counter those threats. – – – Explain the need for network security. Describe the key elements of a network security policy. Describe the types of security threats to a network. Explain the need for disaster recovery planning. Describe the functioning of a firewall. Describe the design, implementation, and management of networks. – Describe the network design statement of requirements. – Explain the importance of a Request for Proposal. – Describe the benefits and difficulties of using a simulation model during the network design process.

Network Security, Why Do We Need it? Networks have become assets like computers and servers Most companies cannot survive without their network Value of the data on the network is more valuable than cost of the network Laptops are being stolen today not for the equipment but for the data We must protect our networks

Management’s Responsibility Management is responsible for ensuring that network security is taken seriously They can do this by authorizing specific policies for network security Clearly defined roles and responsibilities Security implementation plan Clearly defined incident response plan Management review or certification and accreditation of the network based on required and implemented controls

Types of Threats – Active Security Attacks Altering Message Content – Changing the contents of a message Masquerading – pretending to be someone else on the network Denial of Service – flooding site with messages rendering it inoperative, applies to any type of service Planting Viruses – through email, internet or local media Physical Damage Nonmalicious disruptions – Circuit failures, server failures, software bugs Disasters – floods, fires, tornadoes………. .

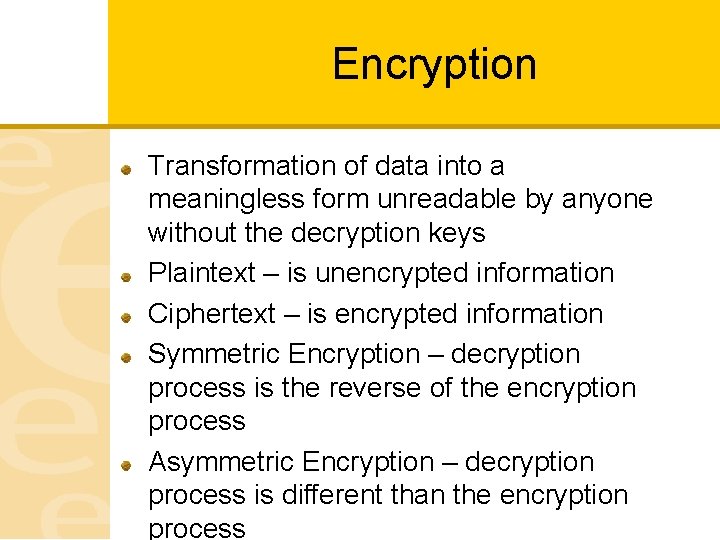
Encryption Transformation of data into a meaningless form unreadable by anyone without the decryption keys Plaintext – is unencrypted information Ciphertext – is encrypted information Symmetric Encryption – decryption process is the reverse of the encryption process Asymmetric Encryption – decryption process is different than the encryption process

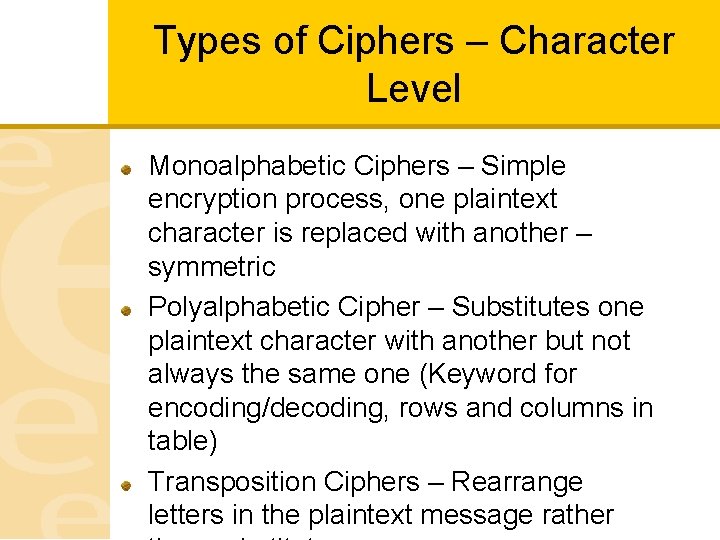
Types of Ciphers – Character Level Monoalphabetic Ciphers – Simple encryption process, one plaintext character is replaced with another – symmetric Polyalphabetic Cipher – Substitutes one plaintext character with another but not always the same one (Keyword for encoding/decoding, rows and columns in table) Transposition Ciphers – Rearrange letters in the plaintext message rather

Bit Level Encryption Works with the bits of the message and also uses a key(string of bits) which is applied to the bits to encrypt the message Common key lengths are 64 and 128 bits. It is best to use 256 bits Message is broken into pieces the length of the key and Exclusive ORed (XOR) with the Key. XOR = Either A or B but not both, result is a 1 if only one of the bits is on XORing encryption key against encrypted message will provide the original message How do you communicate the key?

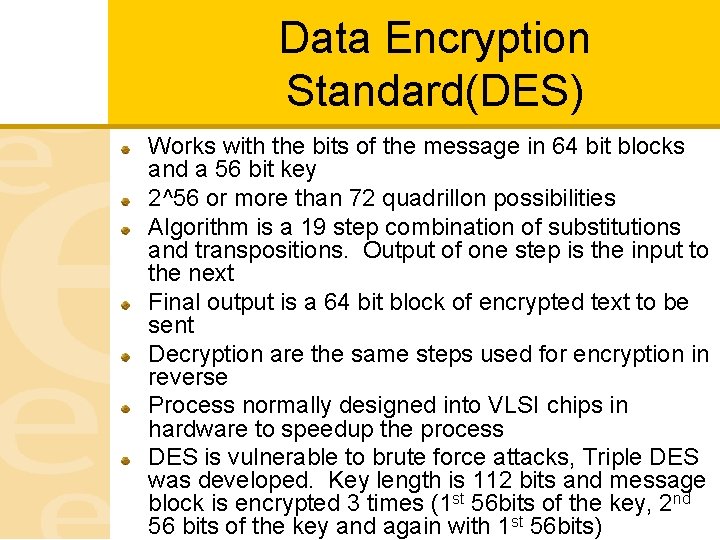
Data Encryption Standard(DES) Works with the bits of the message in 64 bit blocks and a 56 bit key 2^56 or more than 72 quadrillon possibilities Algorithm is a 19 step combination of substitutions and transpositions. Output of one step is the input to the next Final output is a 64 bit block of encrypted text to be sent Decryption are the same steps used for encryption in reverse Process normally designed into VLSI chips in hardware to speedup the process DES is vulnerable to brute force attacks, Triple DES was developed. Key length is 112 bits and message block is encrypted 3 times (1 st 56 bits of the key, 2 nd 56 bits of the key and again with 1 st 56 bits)

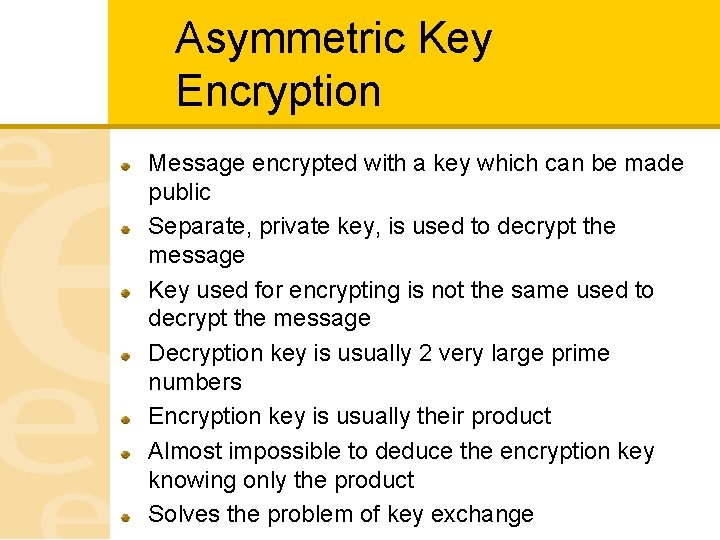
Asymmetric Key Encryption Message encrypted with a key which can be made public Separate, private key, is used to decrypt the message Key used for encrypting is not the same used to decrypt the message Decryption key is usually 2 very large prime numbers Encryption key is usually their product Almost impossible to deduce the encryption key knowing only the product Solves the problem of key exchange

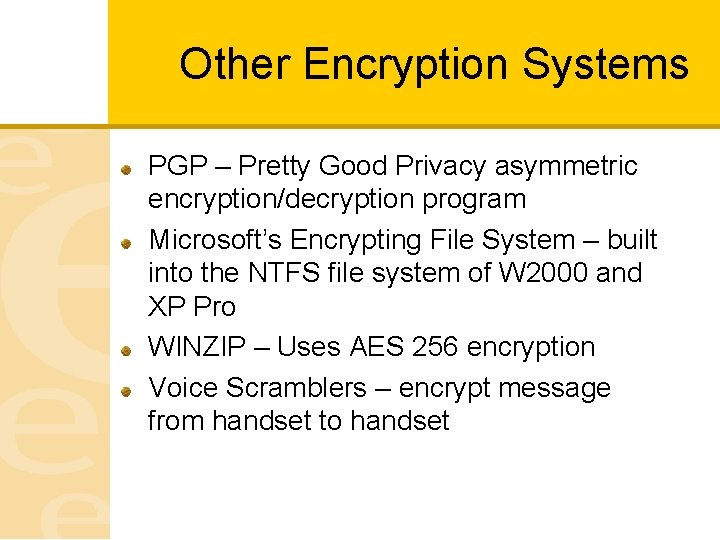
Other Encryption Systems PGP – Pretty Good Privacy asymmetric encryption/decryption program Microsoft’s Encrypting File System – built into the NTFS file system of W 2000 and XP Pro WINZIP – Uses AES 256 encryption Voice Scramblers – encrypt message from handset to handset

Digital Signatures & Certificates Electronically signing a message and guaranteeing that the contents have not been changed Uses hash calculation which crunches data and calculates a unique value for the document (message digest or hash) Digital Certificate – password protected data file that identifies an entity and certifies who they are – important in commercial dealings and allow verification of the parties Digital Certificate Authorities – Are trusted entities who maintain these certificates and allow users to validate a certificate, on-line registry. Verisign is a big player here.

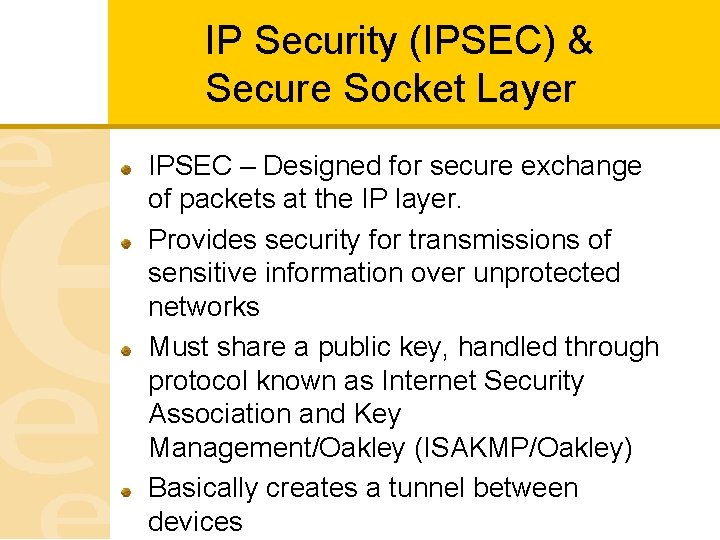
IP Security (IPSEC) & Secure Socket Layer IPSEC – Designed for secure exchange of packets at the IP layer. Provides security for transmissions of sensitive information over unprotected networks Must share a public key, handled through protocol known as Internet Security Association and Key Management/Oakley (ISAKMP/Oakley) Basically creates a tunnel between devices

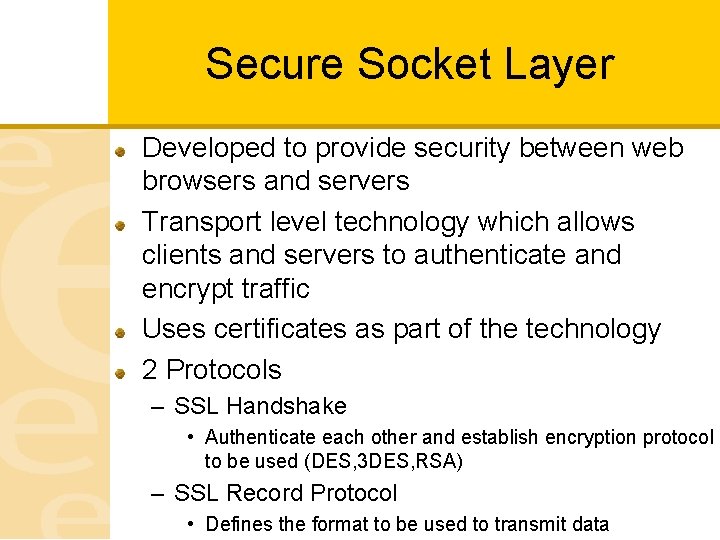
Secure Socket Layer Developed to provide security between web browsers and servers Transport level technology which allows clients and servers to authenticate and encrypt traffic Uses certificates as part of the technology 2 Protocols – SSL Handshake • Authenticate each other and establish encryption protocol to be used (DES, 3 DES, RSA) – SSL Record Protocol • Defines the format to be used to transmit data

Viruses attach themselves to a system System can be infected in many ways. Internet, email, local media Use Antivirus software to mitigate problems – Regular signature updates ( 3 – 4 times per day) – System scans weekly Use a centrally managed solution which allows the network operations team to monitor and manage from one point

Network Access Control 3 Primary Ways to gain access – Accessing from another network, like the Internet – Dialing directly into the network – Using a Workstation located within the organization Ensure ALL users have a user ID and a password – Password should be a strong password (>7 chars, upper, lower, numbers, special characters) – Passwords should be changed regularly – 60

Network Access Control Dialup Accounts and lines should be monitored. Better yet, they should be disabled until needed then activated and secured once work is complete Firewalls should be used to allow only required sites who need access, all others should be blocked Proxy servers should be used in a DMZ area. They allow the outside world to connect to them and then pass the traffic

Physical & Personnel Security and Disaster Recovery Plans Physical security is concerned with ensuring that access to networking equipment is allowed only to technicians requiring it. This is the main computer room as well as the intermediate data frames Personnel security involves screening or security checks for new employees, controlling access to areas using badges, for contract labor as well. Training employees in security Disaster recovery – Plan should be created which analyzes the companies needs and requirements for systems and applications to determine the importance of each system and its priority in disaster recovery. Plan should also include a risk and impact assessment of various scenarios and situations for the likelihood of each. This plan should be reviewed by management and approved. At a minimum, this plan should be reviewed and

Wireless Security Wireless security is a major issue, do not just think that you are safe. These signals are out there for all to see Adjust signal strength to reduce distance your signal travels Use strong passwords for each access points Do not broadcast your SSID (service set identifier) At a minimum use WEP 128 bit, but it is highly recommended to use WPA 2 and AES 256 bit Limit access rights to those who need it Authenticate users by using a firewall that supports VPN

Network Management & Operations Network Management – activities that direct the resources required to keep a network operating over the long term. Network Operations – activities required to keep a network operating on a short term basis (dayto-day) Scope of network management and operations – – – – – Workstations Modems Routers Switches Multiplexers Communication Software Communication lines Vendors Servers

Network Management Functions Staffing – Ensuring the proper number of trained personnel are available to do the job Organizing – Grouping personnel to accomplish the mission of the department. Regular day-today organization and project work Planning – Reviewing managements plans to determine what needs to be considered in the network area to support them. This should be a yearly event which corresponds with

Network Management Functions Directing – Ensuring that the mission and plans are executed in a timely manner Controlling – Financial and quality controls come into play here. Reviewing budgets and actuals to ensure that you are on track. As well as reviewing installs and day-to-day operations to ensure that quality or the level of service is being maintained

Network Operations Activities Day-to-day operations – These are the activities that are required regularly, like changing tapes, reviewing logs…………. Problem Management – Expeditiously handling problems. Should use a helpdesk/trouble ticket system that allows the issue to be defined and tracked. Allows the ability to escalate problems and can be used for metrics and for future reference Performance Measurement – Measure and correct network performance

Network Operations Activities Configuration Control – Management and tracking of all equipment in the network on how it is used and documentation on how it is connected ( Equipment inventory, network diagrams…. ) Change Management – Process to document, track and approve all changes to network systems. There should be a policy and procedure defined for this. Management Reporting – Summarization of network stats in a brief document to management on a regular basis. This allows management to be aware of the key indicators that you track and make them aware of any issues coming up.

Network Management Software Network Management Protocols – SNMP defacto standard for network devices – Common Management Information Protocol ISO standard Software is used as the collecting agent, devices Management Information Base are configured to allow server to collect specific data from the devices Data is kept on server side in a database, log viewing and graphing is the general useage for this data

Review Questions 1. Wireless network security can be implemented by _____. a. using strong passwords b. authenticating users c. encrypting transmissions d. all of the above

Review Questions 2. Bypassing a problem caused by a piece of equipment includes ______. a. ignoring the problem until is gets fixed b. reconfiguring the network c. all of the above d. none of the above

Review Questions 3. Management’s statement of the importance of and their commitment to network security is called the _______. a. network security standard b. network security strategy c. network security policy d. statement of network intent

Review Questions 4. An example of a passive security attack is ________. a. altering message contents b. masquerading c. all of the above d. none of the above

Review Questions 5. Voice scrambling _________. a. makes the voice transmission unintelligible to anyone who does not have a descrambler b. can be circumvented by wiretapping c. all of the above d. none of the above

Review Questions 6. Finding qualified people to fill networking positions is a management function called _______. a. recruiting b. staffing c. organizing d. controlling

Review Questions 7. Asking another company to take over the design, implementation, and operation of a network is called _______. a. retrenching b. outplacing c. insourcing d. outsourcing

Review Questions 8. Performance reporting should _______. a. look at current performance but not historical performance b. provide data so performance trends can be seen c. provide detailed data to senior management d. only be done monthly

Review Questions 9. The shielding on UTP wire is typically made from ______. a. Kevlar b. Teflon c. PCBs d. none of the above

Review Questions 10. As of 2008, the most popular networking cable to install in new office buildings is _______. a. optical fiber b. CAT 1 c. CAT 3 d. CAT 5

Homework – Assignment: Due Next Week • Review: – – • Read: – – • Chapter 17, pp. 488 -515 Chapter 19, pp. 544 -573 Chapter 6, pp. 108 -152 Chapter 8, pp. 188 -207 Complete: – Multiple Choice Questions 1 -8 on pp. 575 -576