Module 2 Creating a Plan for Network Security







- Slides: 19

Module 2: Creating a Plan for Network Security

Overview Introduction to Security Policies Designing Security by Using a Framework Creating a Security Design Team

Lesson 1: Introduction to Security Policies What Are Security Policies? The Relationship Between Policies and Procedures Typical Reasons Why Security Policies Fail? Guidelines for Creating Policies and Procedures

What Are Security Policies? Security policies: Are documents Explain how an organization implements security Administrative Policies Technical Policies Physical Policies

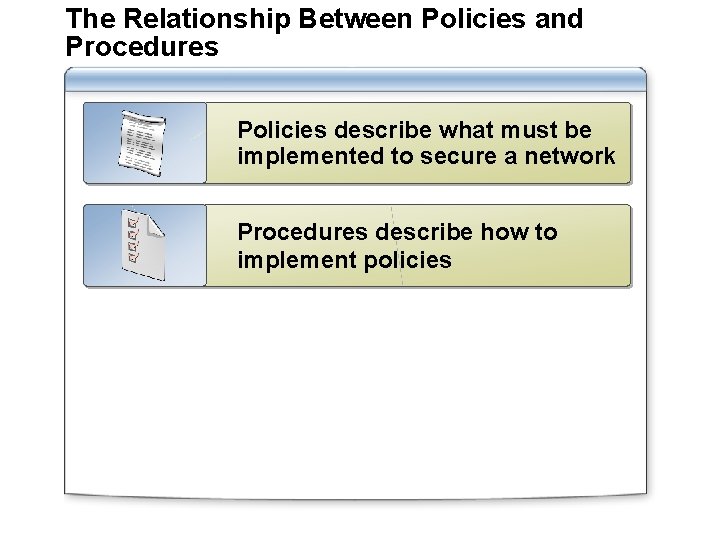
The Relationship Between Policies and Procedures Policies describe what must be implemented to secure a network Procedures describe how to implement policies

Typical Reasons Why Security Policies Fail Security policies often fail because they are: Not enforced Difficult to read Difficult to find Outdated Too vague Too strict Not supported by management

Guidelines for Creating Policies and Procedures Guidelines for creating a security plan include: ü Write clear and concise policies ü Write simple procedures ü Obtain management support ü Ensure employees can find and refer to them ü ü ü easily Ensure no disruption to business processes Use technology to enforce Ensure consequence of violating policy is ü consistent Create incentives for following security

Lesson 2: Designing Security by Using a Framework What Are the Benefits of MSF When Designing a Security Plan? The Envisioning Phase for Network Security The Planning Phase for Network Security The Developing Phase for Network Security The Stabilizing Phase for Network Security The Deploying Phase for Network Security

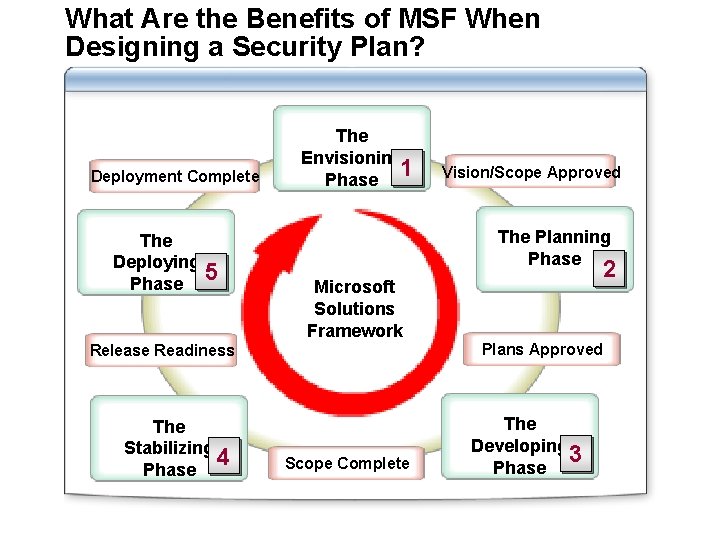
What Are the Benefits of MSF When Designing a Security Plan? Deployment Complete The Deploying 5 Phase The Envisioning 1 Phase The Planning Phase 2 Microsoft Solutions Framework Plans Approved Release Readiness The Stabilizing 4 Phase Vision/Scope Approved Scope Complete The Developing 3 Phase

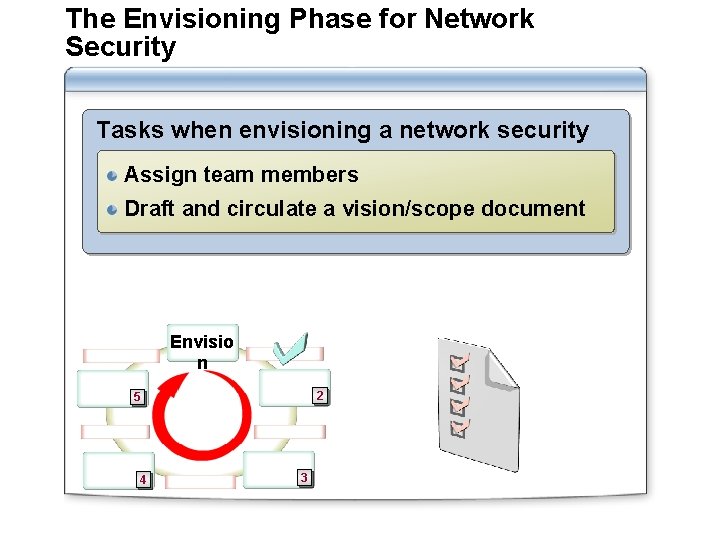
The Envisioning Phase for Network Security Tasks when envisioning a network security plan: Assign team members Draft and circulate a vision/scope document Envisio n 2 5 4 3

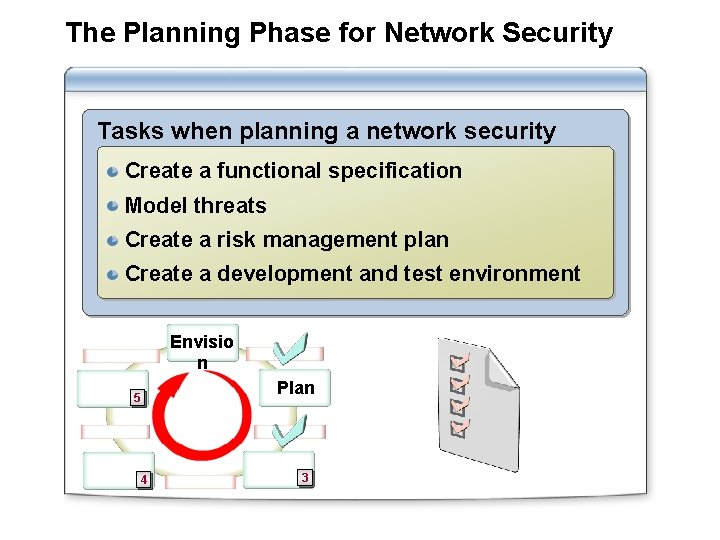
The Planning Phase for Network Security Tasks when planning a network security plan: Create a functional specification Model threats Create a risk management plan Create a development and test environment Envisio n 5 4 Plan 3

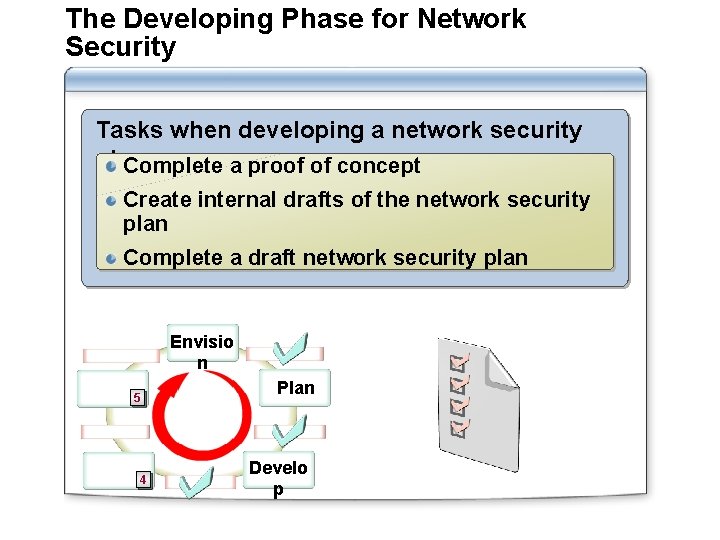
The Developing Phase for Network Security Tasks when developing a network security plan: Complete a proof of concept Create internal drafts of the network security plan Complete a draft network security plan Envisio n 5 4 Plan Develo p

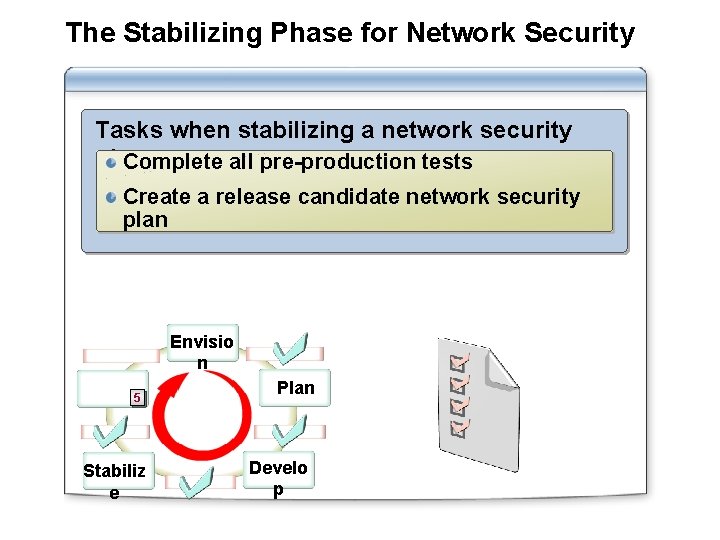
The Stabilizing Phase for Network Security Tasks when stabilizing a network security plan: Complete all pre-production tests Create a release candidate network security plan Envisio n 5 Stabiliz e Plan Develo p

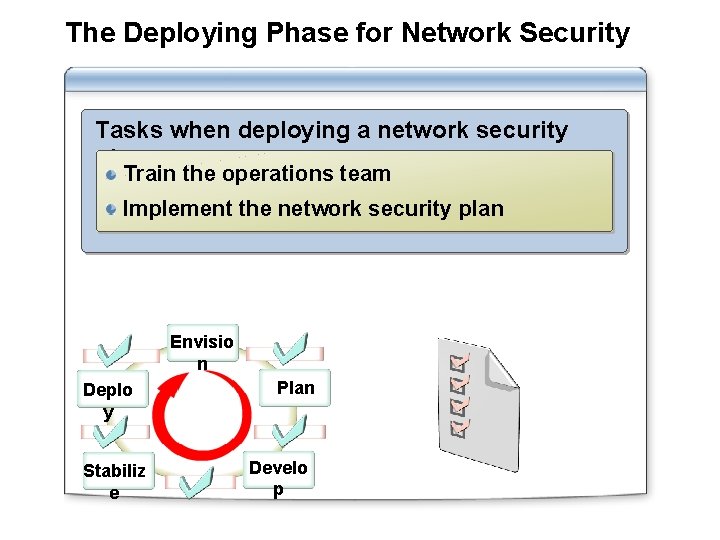
The Deploying Phase for Network Security Tasks when deploying a network security plan: Train the operations team Implement the network security plan Envisio n Deplo y Stabiliz e Plan Develo p

Lesson 3: Creating a Security Design Team Core Team Members Extended Team Members Guidelines for Creating a Security Design Team

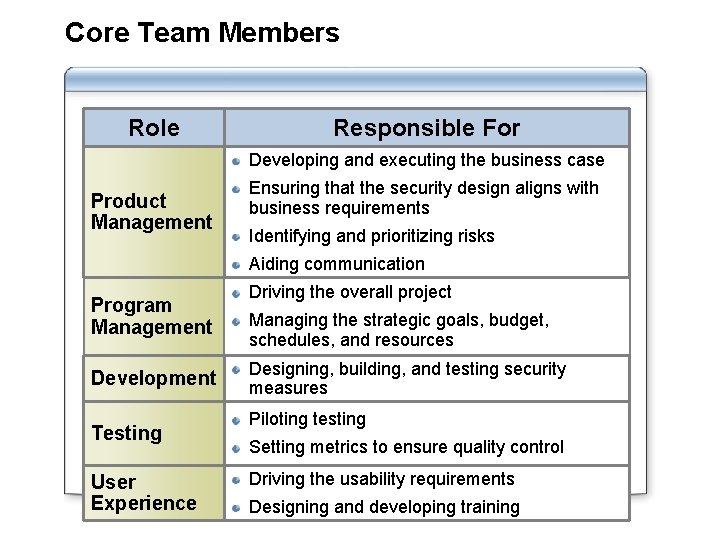
Core Team Members Role Responsible For Developing and executing the business case Product Management Ensuring that the security design aligns with business requirements Identifying and prioritizing risks Aiding communication Program Management Development Testing User Experience Driving the overall project Managing the strategic goals, budget, schedules, and resources Designing, building, and testing security measures Piloting testing Setting metrics to ensure quality control Driving the usability requirements Designing and developing training

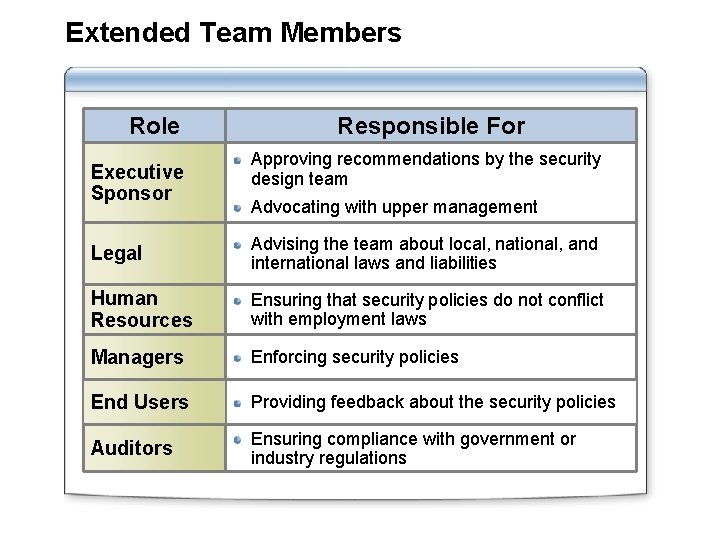
Extended Team Members Role Executive Sponsor Responsible For Approving recommendations by the security design team Advocating with upper management Legal Advising the team about local, national, and international laws and liabilities Human Resources Ensuring that security policies do not conflict with employment laws Managers Enforcing security policies End Users Providing feedback about the security policies Auditors Ensuring compliance with government or industry regulations

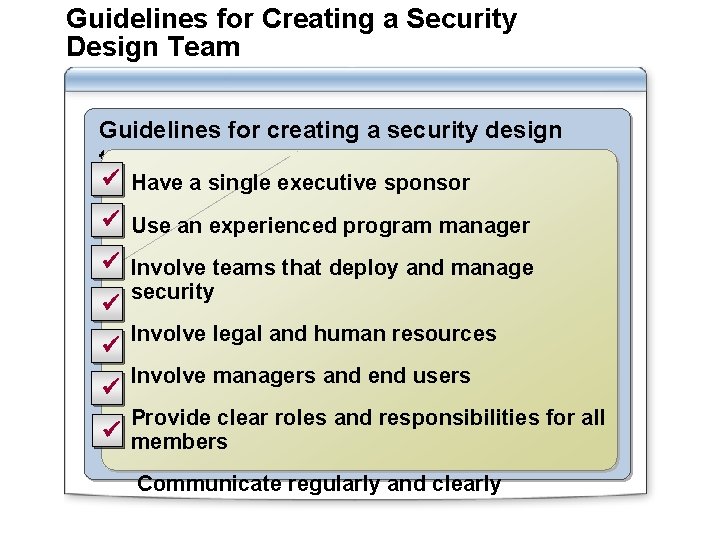
Guidelines for Creating a Security Design Team Guidelines for creating a security design team include: ü Have a single executive sponsor ü Use an experienced program manager ü Involve teams that deploy and manage ü ü ü security Involve legal and human resources Involve managers and end users Provide clear roles and responsibilities for all ü members Communicate regularly and clearly

Lab: Creating a Plan for Network Security Exercise 1 Identifying Reasons Why Security Policies Fail Exercise 2 Determining the Members of a Security Design Team